b39deaec009e923b2a3f687a1e4076e4.ppt
- Количество слайдов: 56

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Information Systems Challenges: Ethical, Social, Security and Global Issues Lecture 4 Prof. Eusebio Scornavacca (escornavacca@ubalt. edu)

Management Information Systems Prof. Eusebio Scornavacca • John and Margaret Thompson Professor in MIS • Dean Clifford C. James Chair for Distinguished Teaching • Merrick School of Business , University of Baltimore, USA. Professor Scornavacca’s research interests include mobile and ubiquitous information systems and disruptive ICT innovation. During the past 15 years he has conducted qualitative and quantitative research in a wide range of industries, including research sponsored by the private sector. 2

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION OVERVIEW OF TODAY - SECURING INFORMATION SYSTEMS - CH 8 - ETHICAL & SOCIAL ISSUES IN IS – CH 4 - MANAGING GLOBAL SYSTEMS - CH 15

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Chapter 8 SECURING INFORMATION SYSTEMS - Prof. Eusebio Scornavacca (escornavacca@ubalt. edu)

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Learning Objectives • Why are information systems vulnerable to destruction, error, and abuse? • What is the business value of security and control? • What are the components of an organizational framework for security and control? • What are the most important tools and technologies for safeguarding information resources? 5

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Why are systems vulnerable? – Accessibility of networks – Hardware problems (breakdowns, configuration errors, damage from improper use or crime) – Software problems (programming errors, installation errors, unauthorized changes) – Disasters – Use of networks/computers outside of firm’s control – Loss and theft of portable devices 6
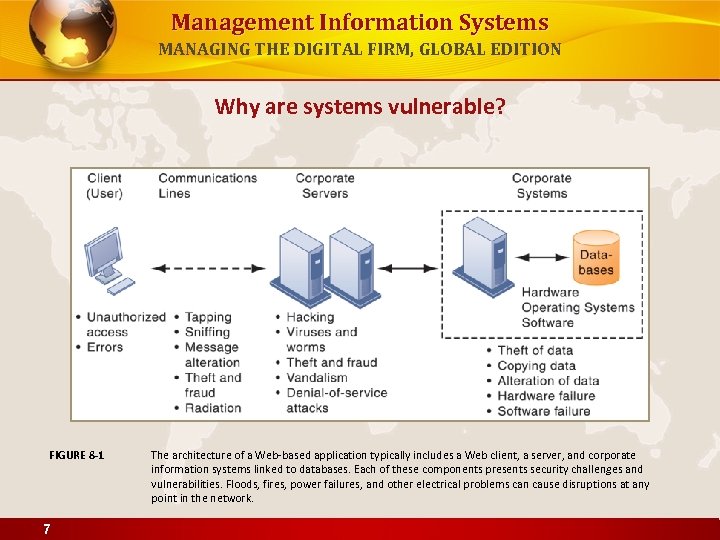
Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Why are systems vulnerable? FIGURE 8 -1 7 The architecture of a Web-based application typically includes a Web client, a server, and corporate information systems linked to databases. Each of these components presents security challenges and vulnerabilities. Floods, fires, power failures, and other electrical problems can cause disruptions at any point in the network.

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION System Vulnerability and Abuse • Security: – Policies, procedures and technical measures used to prevent unauthorized access, alteration, theft, or physical damage to information systems • Controls: – Methods, policies, and organizational procedures that ensure safety of organization’s assets; accuracy and reliability of its accounting records; and operational adherence to management standards 8

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION • Hackers (& crackers) and computer crime • System intrusion • System damage • Cybervandalism • Internal threats: employees – Security threats often originate inside an organization – Inside knowledge – Sloppy security procedures – Social engineering (Tricking employees) 9

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Computer crime – “any violations of criminal law that involve a knowledge of computer technology for their perpetration, investigation, or prosecution” – Computer may be target of crime, e. g. : • Breaching confidentiality of protected computerized data • Accessing a computer system without authority – Computer may be instrument of crime, e. g. : • Theft of trade secrets • Using e-mail for threats or harassment 10

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Business Value of Security and Control • Significant or total loss of business function • Firms now more vulnerable than ever – Confidential personal and financial data – Trade secrets, new products, strategies • Immediate threat for a firm’s market value • Inadequate security and controls bring forth issues of liability (electronic evidence) 11

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Towards a Framework for Security and Control General controls – Govern design, security, and use of computer programs and security of data files in general throughout organization’s information technology infrastructure. – Apply to all computerized applications – Combination of hardware, software, and manual procedures to create overall control environment – Include: Software; Hardware; Computer operations; Data security; Implementation; Administrative controls 12

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Establishing a Framework for Security and Control Application controls – Specific controls unique to each computerized application, such as payroll or order processing – Include both automated and manual procedures – Ensure that only authorized data are completely and accurately processed by that application – Include: • Input controls • Processing controls • Output controls 13

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Establishing a Framework for Security and Control Risk assessment: Level of risk if specific activity/process is not properly controlled • • Types of threat Probability of occurrence during year Potential losses, value of threat Expected annual loss EXPOSURE PROBABILITY LOSS RANGE (AVG) Power failure 30% $5 K - $200 K ($102, 500) EXPECTED ANNUAL LOSS $30, 750 Embezzlement 5% $1, 275 User error 14 $1 K - $50 K ($25, 500) $200 - $40 K ($20, 100) $19, 698 98%

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Establishing a Framework for Security and Control • Security policy – Ranks information risks, identifies acceptable security goals, and identifies mechanisms for achieving these goals – Drives other policies • Acceptable use policy (AUP) – Defines acceptable uses of firm’s information resources and computing equipment • Authorization policies – Determine differing levels of user access to information assets 15
Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Establishing a Framework for Security and Control • Identity management – Business processes and tools to identify valid users of system and control access • Identifies and authorizes different categories of users • Specifies which portion of system users can access • Authenticating users and protects identities – Identity management systems • Captures access rules for different levels of users 16

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Establishing a Framework for Security and Control Disaster recovery planning: Devises plans for restoration of disrupted services Business continuity planning: Focuses on restoring business operations after disaster – Both types of plans needed to identify firm’s most critical systems – Business impact analysis to determine impact of an outage – Management must determine which systems restored first 17

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Technologies and Tools for Protecting Information Resources • Identity management software • Authentication • Firewalls • Intrusion detection systems • Antivirus and antispyware software • Unified threat management (UTM) systems • WAP 2 specification for wireless networks • Encryption 18

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Security in contemporary computing environments • Security in the cloud – Responsibility for security resides with company owning the data – Firms must ensure providers provides adequate protection – Service level agreements (SLAs) • Securing mobile platforms – Security policies should include and cover any special requirements for mobile devices • E. g. updating smart phones with latest security patches, etc. 19

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Chapter 8 ETHICAL & SOCIAL ISSUES IN IS Prof. Eusebio Scornavacca (escornavacca@ubalt. edu)

Management Information Systems Learning Objectives • What ethical, social, and political issues are raised by information systems? • What specific principles for conduct can be used to guide ethical decisions? • Why do contemporary information systems technology and the Internet pose challenges to the protection of individual privacy and intellectual property? • How have information systems affected everyday life? 21

Management Information Systems • Ethics – Principles of right and wrong that individuals, acting as free moral agents, use to make choices to guide their behaviors • Information systems and ethics Information systems raise new ethical questions because they create opportunities for: • Intense social change, threatening existing distributions of power, money, rights, and obligations • New kinds of crime 22

Management Information Systems Moral dimensions of the information age 1. 2. 3. 4. 5. 23 Information rights and obligations Property rights and obligations Accountability and control System quality Quality of life

Management Information Systems • Basic concepts for ethical analysis – Responsibility: • Accepting the potential costs, duties, and obligations for decisions – Accountability: • Mechanisms for identifying responsible parties – Liability: • Permits individuals (and firms) to recover damages done to them – Due process: • Laws are well known and understood, with an ability to appeal to higher authorities 24

Management Information Systems • Ethical analysis: A five-step process 1. Identify and clearly describe the facts 2. Define the conflict or dilemma and identify the higher-order values involved 3. Identify the stakeholders 4. Identify the options that you can reasonably take 5. Identify the potential consequences of your options 25

Management Information Systems • Professional codes of conduct – Promulgated by associations of professionals • E. g. AMA, ABA, AITP, ACM, AIS (www. aisnet. org) – Promises by professions to regulate themselves in the general interest of society • Real-world ethical dilemmas – One set of interests pitted against another – E. g. Right of company to maximize productivity of workers vs. workers right to use Internet for short personal tasks 26

Management Information Systems • Privacy: – Claim of individuals to be left alone, free from surveillance or interference from other individuals, organizations, or state. Claim to be able to control information about yourself • Diverse rules and understanding of concept in different countries (esp. USA vs. Europe) 27

Management Information Systems • Internet Challenges to Privacy: – Cookies • Tiny files downloaded by Web site to visitor’s hard drive to help identify visitor’s browser and track visits to site • Allow Web sites to develop profiles on visitors – Web beacons/bugs • Tiny graphics embedded in e-mail and Web pages to monitor who is reading message – Spyware • Surreptitiously installed on user’s computer • May transmit user’s keystrokes or display unwanted ads • Google’s collection of private data; behavioral targeting 28

Management Information Systems • Property rights: Intellectual property – Intellectual property: Intangible property of any kind created by individuals or corporations – Three main ways that protect intellectual property 1. Trade secret: Intellectual work or product belonging to business, not in the public domain 2. Copyright: Statutory grant protecting intellectual property from being copied for the life of the author, plus 70 years 3. Patents: Grants creator of invention an exclusive monopoly on ideas behind invention for 20 years 29

Management Information Systems • Challenges to intellectual property rights – Digital media different from physical media (e. g. books) • • • Ease of replication Ease of transmission (networks, Internet) Difficulty in classifying software Compactness Difficulties in establishing uniqueness • Digital Millennium Copyright Act (DMCA) – Makes it illegal to circumvent technology-based protections of copyrighted materials 30

Management Information Systems • Accountability, Liability, Control – Computer-related liability problems • If software fails, who is responsible? – If seen as part of machine that injures or harms, software producer and operator may be liable – If seen as similar to book, difficult to hold author/publisher responsible – What should liability be if software seen as service? Would this be similar to telephone systems not being liable for transmitted messages? 31

Management Information Systems • Quality of life: Equity, access, and boundaries Negative social consequences of systems • Balancing power: Although computing power decentralizing, key decision-making remains centralized • Rapidity of change: Businesses may not have enough time to respond to global competition • Maintaining boundaries: Computing, Internet use lengthens work-day, infringes on family, personal time • Dependence and vulnerability: Public and private organizations ever more dependent on computer systems 32

Management Information Systems • Employment: – Reengineering work resulting in lost jobs • Equity and access – the digital divide: – Certain ethnic and income groups in the United States less likely to have computers or Internet access • Computer crime and abuse – Computer crime: Commission of illegal acts through use of compute or against a computer system – computer may be object or instrument of crime – Computer abuse: Unethical acts, not illegal • Spam: High costs for businesses in dealing with spam 33

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Chapter 15 MANAGING GLOBAL SYSTEMS Prof. Eusebio Scornavacca (escornavacca@ubalt. edu)

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Learning Objectives • What major factors are driving the internationalization of business? • What are the alternative strategies for developing global businesses? • How can information systems support different global business strategies? • What are the challenges posed by global information systems and management solutions for these challenges? • What are the issues and technical alternatives to be considered when developing international information systems? 35

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • Global economic system and global world order driven by advanced networks and information systems • Growth of international trade has radically altered domestic economies around the globe • For example, production of many high-end electronic products parceled out to multiple countries – E. g. , Hewlett-Packard laptop computer 36

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • Strategy when building international systems 1. Understand global environment • Business drivers pushing your industry toward global competition • Inhibitors creating management challenges 2. Develop corporate strategy for competition • How firm should respond to global competition 3. Develop organization structure and division of labor • Where will production, marketing, sales, etc. , be located 4. Consider management issues • Design of business procedures, reengineering, managing change 5. Consider technology platform 37
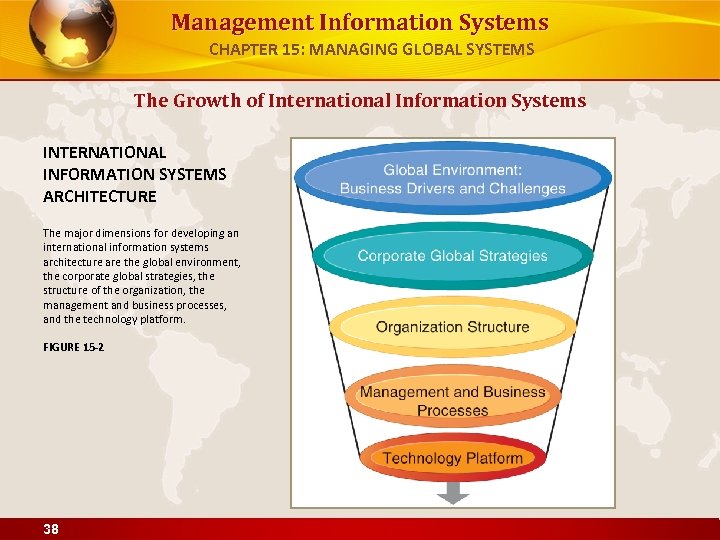
Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems INTERNATIONAL INFORMATION SYSTEMS ARCHITECTURE The major dimensions for developing an international information systems architecture are the global environment, the corporate global strategies, the structure of the organization, the management and business processes, and the technology platform. FIGURE 15 -2 38

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • Global business drivers: – General cultural factors lead toward internationalization and result in specific business globalization factors GENERAL CULTURAL FACTORS SPECIFIC BUSINESS FACTORS Global communication and transportation technologies Development of global culture Emergence of global social norms Political stability Global knowledge base Global markets Global production and operations Global coordination Global workforce Global economies of scale 39

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • Challenges and obstacles to global business systems – General cultural challenges • Cultural particularism – Regionalism, nationalism, language differences • Social expectations: – Brand-name expectations, work hours • Political laws – Transborder data flow – Transborder data and privacy laws, commercial regulations 40

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • Challenges to global business systems (cont. ) – Specific challenges • Standards – Different EDI, e-mail, telecommunication standards • Reliability – Phone networks not uniformly reliable • Speed – Different data transfer speeds, many slower than U. S. • Personnel – Shortages of skilled consultants 41

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS The Growth of International Information Systems • State of the art – Most companies have inherited patchwork international systems using 1960 s-era batch-oriented reporting, manual entry of data from one legacy system to another, and little online control and communication – Significant difficulties in building appropriate international architectures • • 42 Planning a system appropriate to firm’s global strategy Structuring organization of systems and business units Solving implementation issues Choosing right technical platform

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Organizing International Information Systems • Global strategies and business organization – Three main kinds of organizational structure • Centralized: In the home country • Decentralized/dispersed: To local foreign units • Coordinated: All units participate as equals – Four main global strategies • • 43 Domestic exporter Multinational Franchisers Transnational

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Organizing International Information Systems • Global systems to fit the strategy – Configuration, management, and development of systems tend to follow global strategy chosen – Four main types of systems configuration 1. Centralized: Systems development and operation occur totally at domestic home base 2. Duplicated: Development occurs at home base but operations are handed over to autonomous units in foreign locations 3. Decentralized: Each foreign unit designs own solutions and systems 4. Networked: Development and operations occur in coordinated fashion across all units 44
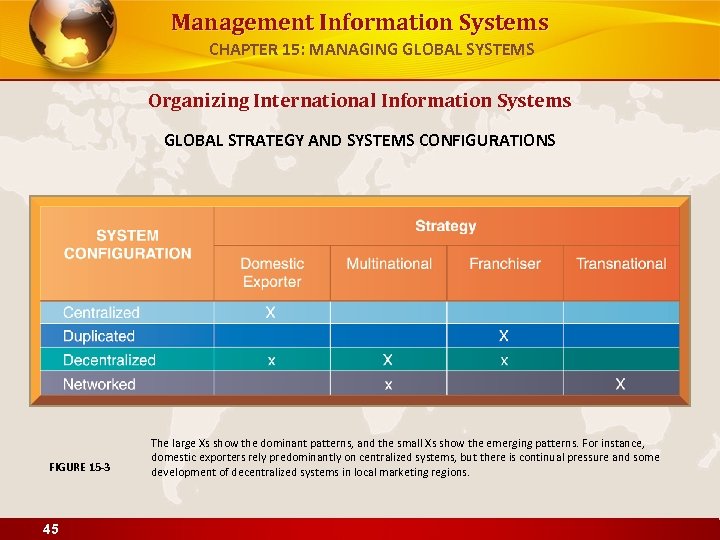
Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Organizing International Information Systems GLOBAL STRATEGY AND SYSTEMS CONFIGURATIONS FIGURE 15 -3 45 The large Xs show the dominant patterns, and the small Xs show the emerging patterns. For instance, domestic exporters rely predominantly on centralized systems, but there is continual pressure and some development of decentralized systems in local marketing regions.

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Organizing International Information Systems • To develop a global company and information systems support structure: 1. Organize value-adding activities along lines of comparative advantage • E. g. , Locate functions where they can best be performed, for least cost and maximum impact 2. Develop and operate systems units at each level of corporate activity—regional, national, and international 3. Establish at world headquarters: • Single office responsible for development of international systems • Global CIO position 46

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems • Principle management challenges in developing global systems – Agreeing on common user requirements – Introducing changes in business processes – Coordinating application development – Coordinating software releases – Encouraging local users to support global systems 47

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems • Global systems strategy – Share only core systems • Core systems support functionality critical to firm – Partially coordinate systems that share some key elements • Do not have to be totally common across national boundaries • Local variation desirable – Peripheral systems • Need to suit local requirements only 48
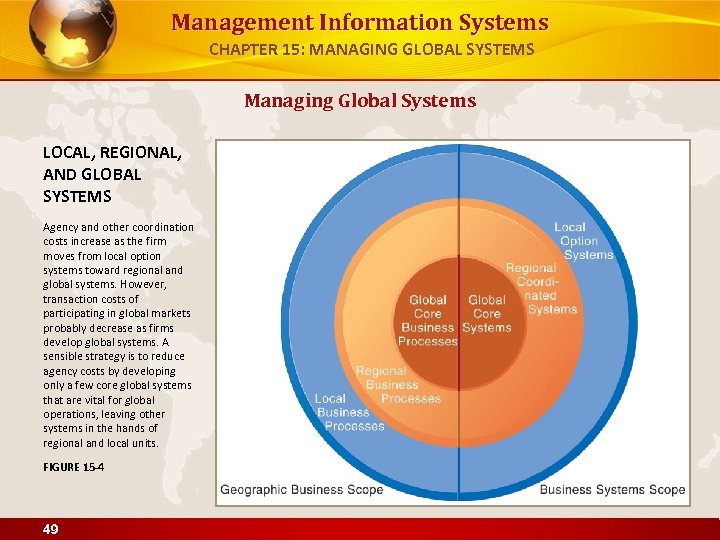
Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems LOCAL, REGIONAL, AND GLOBAL SYSTEMS Agency and other coordination costs increase as the firm moves from local option systems toward regional and global systems. However, transaction costs of participating in global markets probably decrease as firms develop global systems. A sensible strategy is to reduce agency costs by developing only a few core global systems that are vital for global operations, leaving other systems in the hands of regional and local units. FIGURE 15 -4 49

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems 1. Define core business processes 2. Identify core systems to coordinate centrally 3. Choose an approach – Piecemeal and grand design approaches tend to fail – Evolve transnational applications incrementally from existing applications 4. Make benefits clear – Global flexibility – Gains in efficiency – Global markets and larger customer base unleash new economies of scale at production facilities – Optimizing corporate funds over much larger capital base 50

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems • The management solution: Implementation – Agreeing on common user requirements • Short list of core business processes • Develop common language, understanding of common elements and unique local qualities – Introducing changes in business processes • Success depends on legitimacy, authority, ability to involve users in change design process – Coordinating applications development • Coordinate change through incremental steps • Reduce set of transnational systems to bare minimum 51

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Managing Global Systems • The management solution (cont. ) – Coordinating software releases • Institute procedures to ensure all operating units update at the same time – Encouraging local users to support global systems • Cooptation: Bringing the opposition into design and implementation process without giving up control over direction and nature of the change – Permit each country unit to develop one transnational application – Develop new transnational centers of excellence 52

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Technology Issues and Opportunities for Global Value Chains • Technology challenges of global systems – Computing platforms and systems integration • How new core systems will fit in with existing suite of applications developed around globe by different divisions • Standardization: Data standards, interfaces, software, etc. – Connectivity • Internet does not guarantee any level of service • Many firms use private networks and VPNs • Low penetration of PCs, outdated infrastructures in developing countries 53

Management Information Systems CHAPTER 15: MANAGING GLOBAL SYSTEMS Technology Issues and Opportunities for Global Value Chains • Technology challenges of global systems (cont. ) – Software • Integrating new systems with old • Human interface design issues, languages • Software localization: converting software to operate in second language • Most important software applications: – TPS and MIS – Increasingly, SCM and enterprise systems to standardize business processes – Applications that enhance productivity of international teams 54

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION OVERVIEW OF TODAY - SECURING INFORMATION SYSTEMS - CH 8 - ETHICAL & SOCIAL ISSUES IN IS – CH 4 - MANAGING GLOBAL SYSTEMS - CH 15

Management Information Systems MANAGING THE DIGITAL FIRM, GLOBAL EDITION Information Systems Challenges: Ethical, Social, Security and Global Issues Lecture 4 Prof. Eusebio Scornavacca (escornavacca@ubalt. edu)
b39deaec009e923b2a3f687a1e4076e4.ppt