0f3bf05b2786a943d28fbdc9cd580892.ppt
- Количество слайдов: 77
 Malicious Software (long version) Nicolas T. Courtois - University College London
Malicious Software (long version) Nicolas T. Courtois - University College London
 Comp. Sec Malware Sources of Problems 2 Nicolas T. Courtois, December 2009
Comp. Sec Malware Sources of Problems 2 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Technology Failures Security as an afterthought. • Programming developed with absence of security. • C/C++ is unsafe (Microsoft is currently blacklisting big chunks of standard C, could have happened 10 years ago). • Security/cryptography research developed with obsession with security. Both never met. • Windows developed first, – networking developed later… • Structural defects in the OS design – lack of multi-layer defense strategy [Unix not better] 3 Nicolas T. Courtois, December 2009
Comp. Sec Malware Technology Failures Security as an afterthought. • Programming developed with absence of security. • C/C++ is unsafe (Microsoft is currently blacklisting big chunks of standard C, could have happened 10 years ago). • Security/cryptography research developed with obsession with security. Both never met. • Windows developed first, – networking developed later… • Structural defects in the OS design – lack of multi-layer defense strategy [Unix not better] 3 Nicolas T. Courtois, December 2009
 Comp. Sec Malware + Failures In Operation • Over-privileged users – Windows 98: all users can modify system files and system memory – Unix – over-powerful root, >21 critical capabilities in one entity • Over-privileged code – code executed by a user to access all rights of that user – Windows Vista: worse than that: built-in privilege escalation: • if name contains setup, will run with many admin-level capabilities 4 Nicolas T. Courtois, December 2009
Comp. Sec Malware + Failures In Operation • Over-privileged users – Windows 98: all users can modify system files and system memory – Unix – over-powerful root, >21 critical capabilities in one entity • Over-privileged code – code executed by a user to access all rights of that user – Windows Vista: worse than that: built-in privilege escalation: • if name contains setup, will run with many admin-level capabilities 4 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Human Cognitive Failures • Mystified: – security issues are probably always exaggerated and distorted, one way or another (downplayed OR exaggerated, Ross Anderson: “hypertrophy” of security – Also a huge demand, but both don’t meet to frequently). • Lack of people that would defend the public interest + corruption of the scientific establishment by special interests… 5 Nicolas T. Courtois, December 2009
Comp. Sec Malware Human Cognitive Failures • Mystified: – security issues are probably always exaggerated and distorted, one way or another (downplayed OR exaggerated, Ross Anderson: “hypertrophy” of security – Also a huge demand, but both don’t meet to frequently). • Lack of people that would defend the public interest + corruption of the scientific establishment by special interests… 5 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Market Failures • Economics/Business: – many things just don’t matter at all! – customers do not see => do not care about security • “market for lemons” – externalities, cost shifting • losses affect many “small” people that don’t react… – people will not even switch to another software… – unable to defend themselves – 1 billion x very small loss • usability: user burden, businesses don’t care 6 Nicolas T. Courtois, December 2009
Comp. Sec Malware Market Failures • Economics/Business: – many things just don’t matter at all! – customers do not see => do not care about security • “market for lemons” – externalities, cost shifting • losses affect many “small” people that don’t react… – people will not even switch to another software… – unable to defend themselves – 1 billion x very small loss • usability: user burden, businesses don’t care 6 Nicolas T. Courtois, December 2009
![Comp. Sec Malware **Why So Bad? “[…] Why do so many vulnerabilities exist in Comp. Sec Malware **Why So Bad? “[…] Why do so many vulnerabilities exist in](https://present5.com/presentation/0f3bf05b2786a943d28fbdc9cd580892/image-7.jpg) Comp. Sec Malware **Why So Bad? “[…] Why do so many vulnerabilities exist in the first place? […]” Cf. Ross Anderson, Tyler Moore et al: 1. “The Economics of Information Security” In Science, October 2006. 2. “Security Economics and the Internal Market”: public report for ENISA (European Network and Information Security Agency), March 2008. 7 Nicolas T. Courtois, December 2009
Comp. Sec Malware **Why So Bad? “[…] Why do so many vulnerabilities exist in the first place? […]” Cf. Ross Anderson, Tyler Moore et al: 1. “The Economics of Information Security” In Science, October 2006. 2. “Security Economics and the Internal Market”: public report for ENISA (European Network and Information Security Agency), March 2008. 7 Nicolas T. Courtois, December 2009
 Comp. Sec Malware ***Why Commercial Security Fails? Claim: the link between “money” and security is frequently broken today: – Security is a public good. • “private” incentives are weak. – Worse than “market for lemons”: • not only that the customer cannot see the difference between good security and bad. – Frequently the manufacturer cannot either. Too frequently security remains something that money cannot buy. 8 Nicolas T. Courtois, December 2009
Comp. Sec Malware ***Why Commercial Security Fails? Claim: the link between “money” and security is frequently broken today: – Security is a public good. • “private” incentives are weak. – Worse than “market for lemons”: • not only that the customer cannot see the difference between good security and bad. – Frequently the manufacturer cannot either. Too frequently security remains something that money cannot buy. 8 Nicolas T. Courtois, December 2009
 Comp. Sec Malware **Questions: Schneier: http: //www. schneier. com/essay-005. html “History has taught us: never underestimate the amount of money, time, and effort someone will expend to thwart a security system. No valid economical argument…. Social phenomenon [hacking]. Courtois: Why is it so that today: • 90 % of energy nowadays goes into hacking. • 10 % to research and development of secure products… Don’t believe it? • Check out: hacking the i. Phone, Microsoft XBOX, etc… • • 9 people work for free, governments or private employers sponsor them willingly or unwillingly, press presents hackers as heroes etc… Nicolas T. Courtois, December 2009
Comp. Sec Malware **Questions: Schneier: http: //www. schneier. com/essay-005. html “History has taught us: never underestimate the amount of money, time, and effort someone will expend to thwart a security system. No valid economical argument…. Social phenomenon [hacking]. Courtois: Why is it so that today: • 90 % of energy nowadays goes into hacking. • 10 % to research and development of secure products… Don’t believe it? • Check out: hacking the i. Phone, Microsoft XBOX, etc… • • 9 people work for free, governments or private employers sponsor them willingly or unwillingly, press presents hackers as heroes etc… Nicolas T. Courtois, December 2009
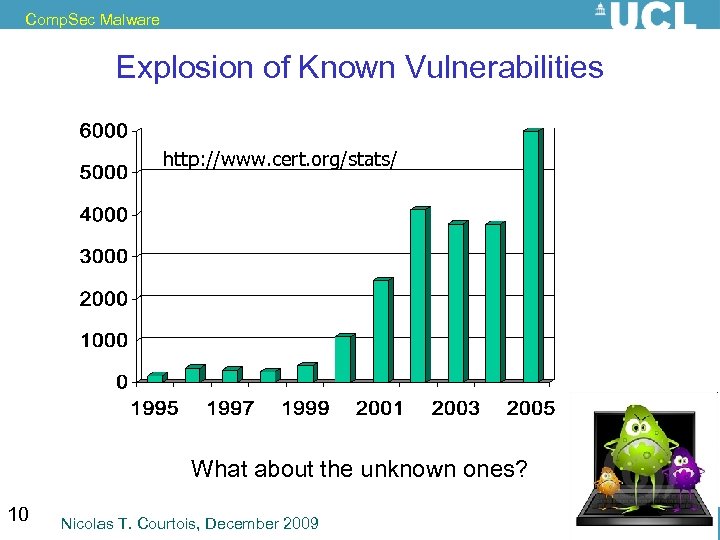 Comp. Sec Malware Explosion of Known Vulnerabilities http: //www. cert. org/stats/ What about the unknown ones? 10 Nicolas T. Courtois, December 2009
Comp. Sec Malware Explosion of Known Vulnerabilities http: //www. cert. org/stats/ What about the unknown ones? 10 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Taxonomy of Malicious Software 11 Nicolas T. Courtois, December 2009
Comp. Sec Malware Taxonomy of Malicious Software 11 Nicolas T. Courtois, December 2009
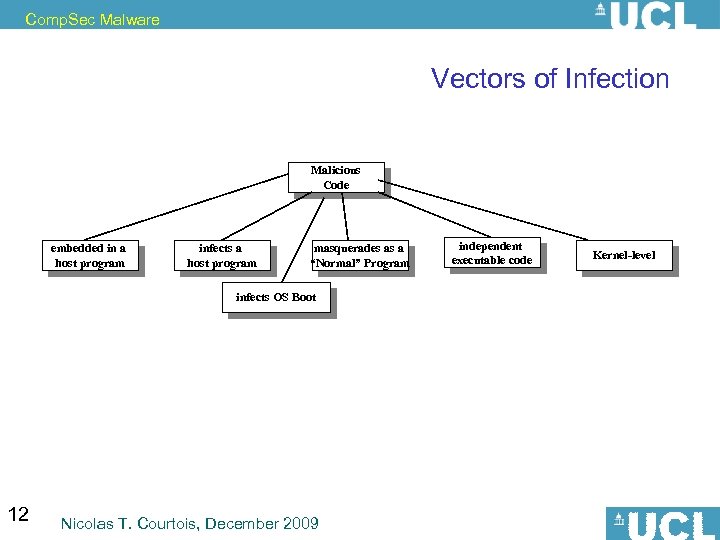 Comp. Sec Malware Vectors of Infection Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program infects OS Boot 12 Nicolas T. Courtois, December 2009 independent executable code Kernel-level
Comp. Sec Malware Vectors of Infection Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program infects OS Boot 12 Nicolas T. Courtois, December 2009 independent executable code Kernel-level
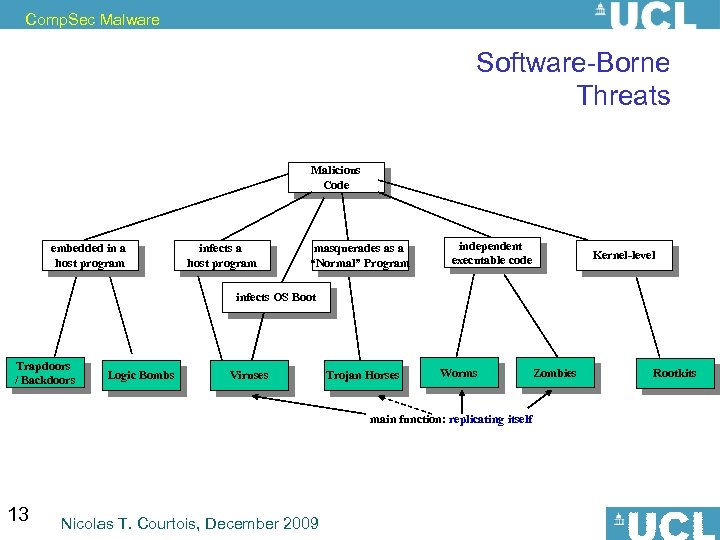 Comp. Sec Malware Software-Borne Threats Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent executable code Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms main function: replicating itself 13 Nicolas T. Courtois, December 2009 Zombies Rootkits
Comp. Sec Malware Software-Borne Threats Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent executable code Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms main function: replicating itself 13 Nicolas T. Courtois, December 2009 Zombies Rootkits
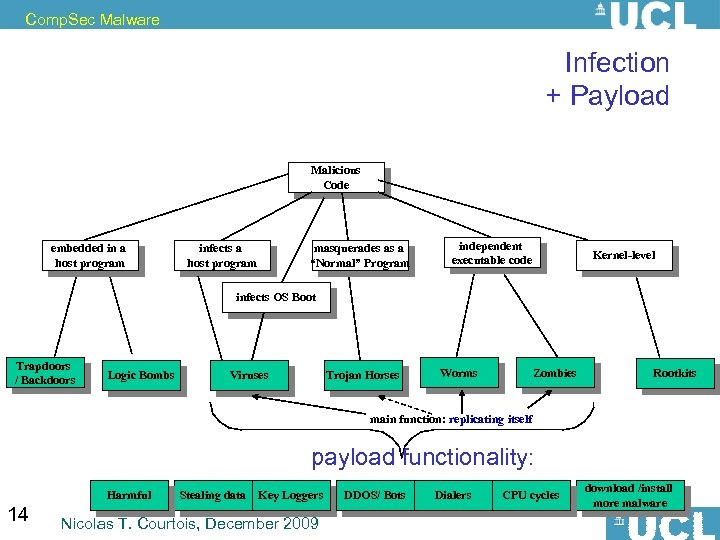 Comp. Sec Malware Infection + Payload Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent executable code Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms Zombies Rootkits main function: replicating itself payload functionality: 14 Harmful Stealing data Key Loggers Nicolas T. Courtois, December 2009 DDOS/ Bots Dialers CPU cycles download /install more malware
Comp. Sec Malware Infection + Payload Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent executable code Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms Zombies Rootkits main function: replicating itself payload functionality: 14 Harmful Stealing data Key Loggers Nicolas T. Courtois, December 2009 DDOS/ Bots Dialers CPU cycles download /install more malware
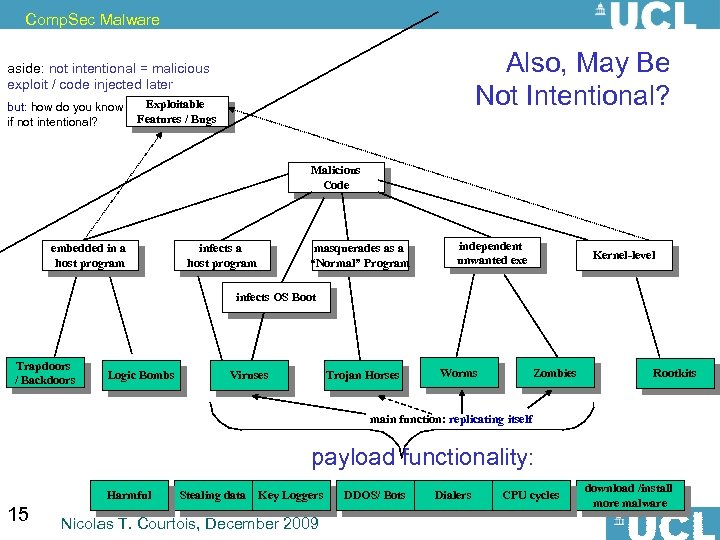 Comp. Sec Malware Also, May Be Not Intentional? aside: not intentional = malicious exploit / code injected later but: how do you know if not intentional? Exploitable Features / Bugs Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent unwanted exe Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms Zombies Rootkits main function: replicating itself payload functionality: 15 Harmful Stealing data Key Loggers Nicolas T. Courtois, December 2009 DDOS/ Bots Dialers CPU cycles download /install more malware
Comp. Sec Malware Also, May Be Not Intentional? aside: not intentional = malicious exploit / code injected later but: how do you know if not intentional? Exploitable Features / Bugs Malicious Code embedded in a host program infects a host program masquerades as a “Normal” Program independent unwanted exe Kernel-level infects OS Boot Trapdoors / Backdoors Logic Bombs Viruses Trojan Horses Worms Zombies Rootkits main function: replicating itself payload functionality: 15 Harmful Stealing data Key Loggers Nicolas T. Courtois, December 2009 DDOS/ Bots Dialers CPU cycles download /install more malware
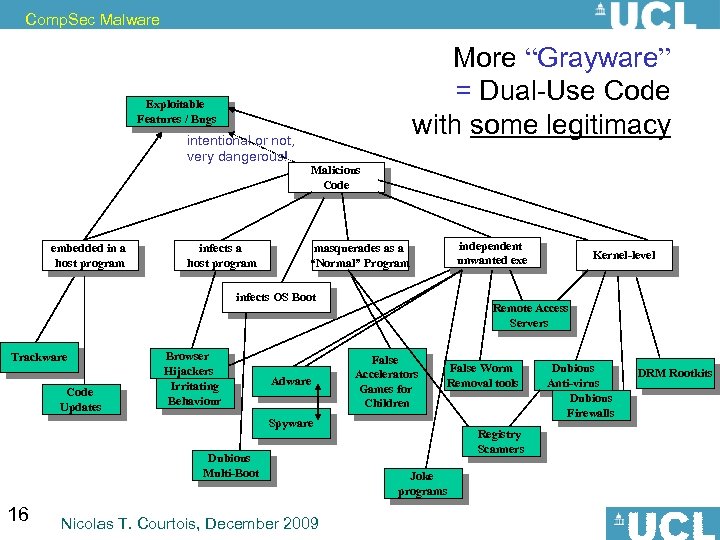 Comp. Sec Malware More “Grayware” = Dual-Use Code with some legitimacy Exploitable Features / Bugs intentional or not, very dangerous! embedded in a host program infects a host program Malicious Code independent unwanted exe masquerades as a “Normal” Program infects OS Boot Trackware Code Updates Browser Hijackers Irritating Behaviour Adware Remote Access Servers False Accelerators Games for Children False Worm Removal tools Spyware Dubious Multi-Boot 16 Nicolas T. Courtois, December 2009 Kernel-level Registry Scanners Joke programs Dubious Anti-virus Dubious Firewalls DRM Rootkits
Comp. Sec Malware More “Grayware” = Dual-Use Code with some legitimacy Exploitable Features / Bugs intentional or not, very dangerous! embedded in a host program infects a host program Malicious Code independent unwanted exe masquerades as a “Normal” Program infects OS Boot Trackware Code Updates Browser Hijackers Irritating Behaviour Adware Remote Access Servers False Accelerators Games for Children False Worm Removal tools Spyware Dubious Multi-Boot 16 Nicolas T. Courtois, December 2009 Kernel-level Registry Scanners Joke programs Dubious Anti-virus Dubious Firewalls DRM Rootkits
 Comp. Sec Malware Crimeware Malware vs. Crimeware: 1. same infection methods, 2. different goals, Þ more specific forms of payload, Þ automation of crime, Þ malware as illegal business venture: Example: Keyloggers and Spyware Þ but tailored for stealing passwords and credit card numbers 17 Nicolas T. Courtois, December 2009
Comp. Sec Malware Crimeware Malware vs. Crimeware: 1. same infection methods, 2. different goals, Þ more specific forms of payload, Þ automation of crime, Þ malware as illegal business venture: Example: Keyloggers and Spyware Þ but tailored for stealing passwords and credit card numbers 17 Nicolas T. Courtois, December 2009
 Comp. Sec Malware ****Cryptography: Disruptive Technology for Crime Example: – Extortion: encrypt data, ask for $$$. – Impossible without public key cryptography… • which is VERY difficult to make… as difficult as going to the moon, >30 years of research, 100 s of researchers… 18 Nicolas T. Courtois, December 2009
Comp. Sec Malware ****Cryptography: Disruptive Technology for Crime Example: – Extortion: encrypt data, ask for $$$. – Impossible without public key cryptography… • which is VERY difficult to make… as difficult as going to the moon, >30 years of research, 100 s of researchers… 18 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Detailed Definitions 19 Nicolas T. Courtois, December 2009
Comp. Sec Malware Detailed Definitions 19 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Hidden Mechanisms Embedded in Original Software 20 Nicolas T. Courtois, December 2009
Comp. Sec Malware Hidden Mechanisms Embedded in Original Software 20 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Trapdoor, Backdoor Hidden function that can be used to circumvent normal security. A hidden entry point into a system. – also, can be a hidden feature leaking some data… (backdoor). • Examples: – Special user id or special password – Special instruction / option / keyboard sequence – Etc… • Commonly used by developers • “insecurity by obscurity” • hard to distinguish legitimate reasons (testing, debugging, circumventing some bug, jokes and Easter Eggs) from intentional security compromise • beware: can be included in a compiler as well… – source code will not help then… 21 – Rice Theorem : source code will not always help… Nicolas T. Courtois, December 2009 this way
Comp. Sec Malware Trapdoor, Backdoor Hidden function that can be used to circumvent normal security. A hidden entry point into a system. – also, can be a hidden feature leaking some data… (backdoor). • Examples: – Special user id or special password – Special instruction / option / keyboard sequence – Etc… • Commonly used by developers • “insecurity by obscurity” • hard to distinguish legitimate reasons (testing, debugging, circumventing some bug, jokes and Easter Eggs) from intentional security compromise • beware: can be included in a compiler as well… – source code will not help then… 21 – Rice Theorem : source code will not always help… Nicolas T. Courtois, December 2009 this way
 Comp. Sec Malware Electronic Subversion Programs can conceal an intentional subversive functionality: – a bug, backdoor, covert channel Mitigation measures [Schneier-Shostack’ 99]: • fewer security perimeter splits: – • there is and optimal number, splits impair operation and will be circumvented, too many points of failure… more transparency. – but secrecy is here to stay. • 100 % open source == utopia and a fallacy. The hidden powers of crypto developers are particularly dangerous: • large scale compromise and undetected for years • impossibility to prove intentionality: perfect crime • sometimes impossibility to prove fraud, no forensic traces whatsoever if one updates a simple component remotely… 22 Nicolas T. Courtois, December 2009
Comp. Sec Malware Electronic Subversion Programs can conceal an intentional subversive functionality: – a bug, backdoor, covert channel Mitigation measures [Schneier-Shostack’ 99]: • fewer security perimeter splits: – • there is and optimal number, splits impair operation and will be circumvented, too many points of failure… more transparency. – but secrecy is here to stay. • 100 % open source == utopia and a fallacy. The hidden powers of crypto developers are particularly dangerous: • large scale compromise and undetected for years • impossibility to prove intentionality: perfect crime • sometimes impossibility to prove fraud, no forensic traces whatsoever if one updates a simple component remotely… 22 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Application Development Management Goals: • Avoid backdoors, Trojans, covert channels, bugs etc. • Kleptography: techniques to leak keys to the attacker, • form of perfect crime. There are various forms of leaking keys: • intentionality impossible to prove • intentionality provable ONLY with source code 23 Nicolas T. Courtois, December 2009
Comp. Sec Malware Application Development Management Goals: • Avoid backdoors, Trojans, covert channels, bugs etc. • Kleptography: techniques to leak keys to the attacker, • form of perfect crime. There are various forms of leaking keys: • intentionality impossible to prove • intentionality provable ONLY with source code 23 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Logic Bomb • A malicious feature that will be activated when certain conditions are met • e. g. , presence/absence of some file; • particular date/time • particular user • when triggered, typically will do some harm – modify/corrupt/delete files/OS, etc. 24 Nicolas T. Courtois, December 2009
Comp. Sec Malware Logic Bomb • A malicious feature that will be activated when certain conditions are met • e. g. , presence/absence of some file; • particular date/time • particular user • when triggered, typically will do some harm – modify/corrupt/delete files/OS, etc. 24 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Trojan Horse • Program has an overt (expected) and covert (malicious and unexpected) effect such that – works / appears to be a normal program, – covert effect violates the given security policy • User is tricked into executing a Trojan – does the usual (overt) job – covert effect is performed with user’s rights/authorization level. 25 Nicolas T. Courtois, December 2009
Comp. Sec Malware Trojan Horse • Program has an overt (expected) and covert (malicious and unexpected) effect such that – works / appears to be a normal program, – covert effect violates the given security policy • User is tricked into executing a Trojan – does the usual (overt) job – covert effect is performed with user’s rights/authorization level. 25 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Virusology 26 Nicolas T. Courtois, December 2009
Comp. Sec Malware Virusology 26 Nicolas T. Courtois, December 2009
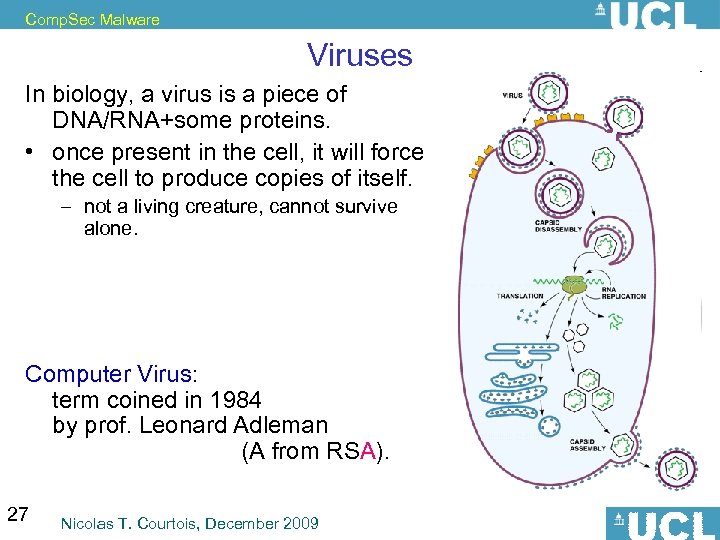 Comp. Sec Malware Viruses In biology, a virus is a piece of DNA/RNA+some proteins. • once present in the cell, it will force the cell to produce copies of itself. – not a living creature, cannot survive alone. – antibiotics have no effect on viruses Computer Virus: term coined in 1984 by prof. Leonard Adleman (A from RSA). 27 Nicolas T. Courtois, December 2009
Comp. Sec Malware Viruses In biology, a virus is a piece of DNA/RNA+some proteins. • once present in the cell, it will force the cell to produce copies of itself. – not a living creature, cannot survive alone. – antibiotics have no effect on viruses Computer Virus: term coined in 1984 by prof. Leonard Adleman (A from RSA). 27 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Viruses – Main types 1. Add-On Virus = Appending Virus => most viruses 2. Shell Virus (nothing to do with Unix shell) 3. Intrusive Virus 28 Nicolas T. Courtois, December 2009
Comp. Sec Malware Viruses – Main types 1. Add-On Virus = Appending Virus => most viruses 2. Shell Virus (nothing to do with Unix shell) 3. Intrusive Virus 28 Nicolas T. Courtois, December 2009
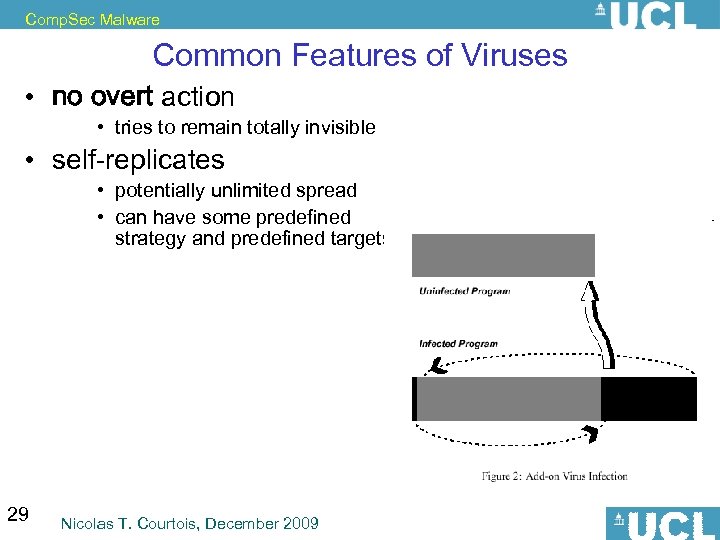 Comp. Sec Malware Common Features of Viruses • no overt action • tries to remain totally invisible • self-replicates • potentially unlimited spread • can have some predefined strategy and predefined targets 29 Nicolas T. Courtois, December 2009
Comp. Sec Malware Common Features of Viruses • no overt action • tries to remain totally invisible • self-replicates • potentially unlimited spread • can have some predefined strategy and predefined targets 29 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Payload: frequently a virus performs additional malicious actions • except “zero payload” viruses • just harmful actions • execute / download additional code 30 Nicolas T. Courtois, December 2009
Comp. Sec Malware Payload: frequently a virus performs additional malicious actions • except “zero payload” viruses • just harmful actions • execute / download additional code 30 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Virus Life Cycle Elements • • 31 Dormant phase: idle Propagation phase Triggering phase: the virus is activated to: Execution phase: perform the payload functions Nicolas T. Courtois, December 2009
Comp. Sec Malware Virus Life Cycle Elements • • 31 Dormant phase: idle Propagation phase Triggering phase: the virus is activated to: Execution phase: perform the payload functions Nicolas T. Courtois, December 2009
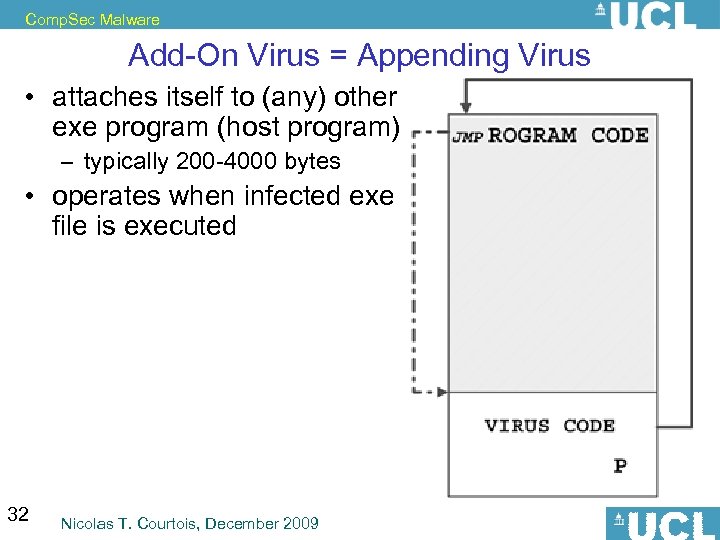 Comp. Sec Malware Add-On Virus = Appending Virus • attaches itself to (any) other exe program (host program) – typically 200 -4000 bytes • operates when infected exe file is executed 32 Nicolas T. Courtois, December 2009
Comp. Sec Malware Add-On Virus = Appending Virus • attaches itself to (any) other exe program (host program) – typically 200 -4000 bytes • operates when infected exe file is executed 32 Nicolas T. Courtois, December 2009
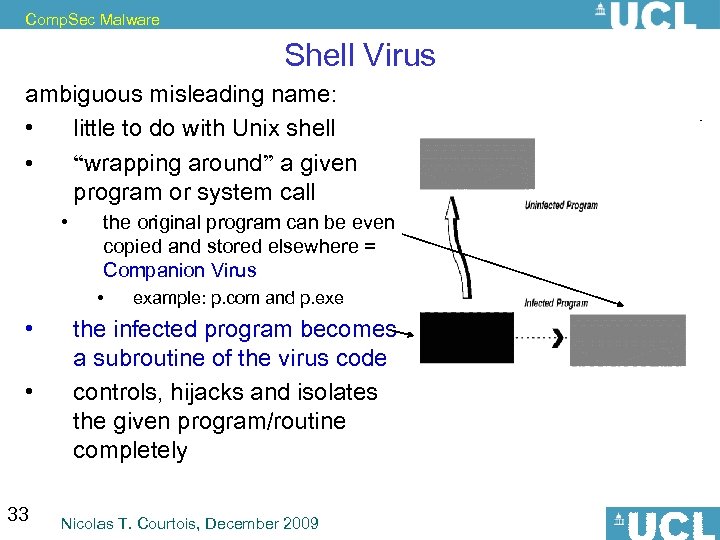 Comp. Sec Malware Shell Virus ambiguous misleading name: • little to do with Unix shell • “wrapping around” a given program or system call • the original program can be even copied and stored elsewhere = Companion Virus • • • 33 example: p. com and p. exe the infected program becomes a subroutine of the virus code controls, hijacks and isolates the given program/routine completely Nicolas T. Courtois, December 2009
Comp. Sec Malware Shell Virus ambiguous misleading name: • little to do with Unix shell • “wrapping around” a given program or system call • the original program can be even copied and stored elsewhere = Companion Virus • • • 33 example: p. com and p. exe the infected program becomes a subroutine of the virus code controls, hijacks and isolates the given program/routine completely Nicolas T. Courtois, December 2009
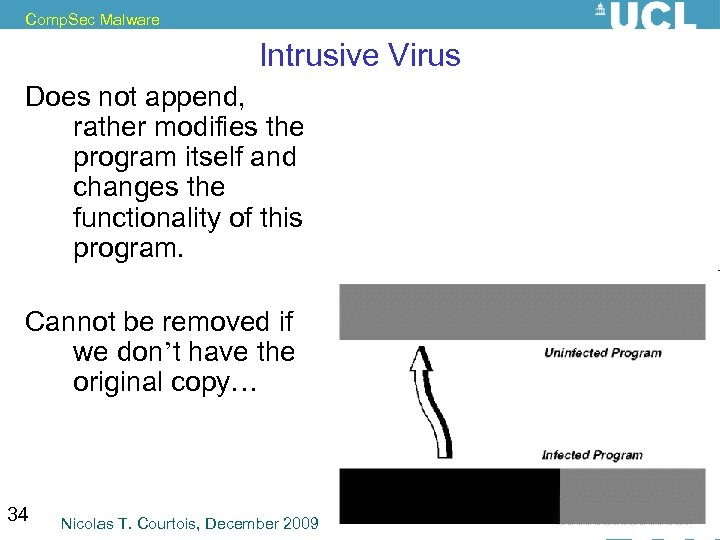 Comp. Sec Malware Intrusive Virus Does not append, rather modifies the program itself and changes the functionality of this program. Cannot be removed if we don’t have the original copy… 34 Nicolas T. Courtois, December 2009
Comp. Sec Malware Intrusive Virus Does not append, rather modifies the program itself and changes the functionality of this program. Cannot be removed if we don’t have the original copy… 34 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Viruses by Medium of Infection • • 35 • • • Exe file infectors => most viruses Boot infectors hard drive boot • • CDROM autorun hijackers USB stick autorun hijackers Half way before system starts: • • master boot record (MBR) OS loader hijack OS libraries hijack (e. g. some dll loaded early) driver hijackers Data file infectors Macro Viruses format string exploits (not called viruses) Nicolas T. Courtois, December 2009
Comp. Sec Malware Viruses by Medium of Infection • • 35 • • • Exe file infectors => most viruses Boot infectors hard drive boot • • CDROM autorun hijackers USB stick autorun hijackers Half way before system starts: • • master boot record (MBR) OS loader hijack OS libraries hijack (e. g. some dll loaded early) driver hijackers Data file infectors Macro Viruses format string exploits (not called viruses) Nicolas T. Courtois, December 2009
 Comp. Sec Malware Viruses by Medium of Infection • • 36 • • • Exe file infectors Boot infectors hard drive boot • • CDROM autorun hijackers USB stick autorun hijackers Half way before system starts: • • master boot record (MBR), OS indep OS loader hijack, 1 partition OS libraries hijack (e. g. some dll loaded early) driver hijackers Data file infectors Macro Viruses format string exploits (not called viruses) Nicolas T. Courtois, December 2009 load before any anti-virus software
Comp. Sec Malware Viruses by Medium of Infection • • 36 • • • Exe file infectors Boot infectors hard drive boot • • CDROM autorun hijackers USB stick autorun hijackers Half way before system starts: • • master boot record (MBR), OS indep OS loader hijack, 1 partition OS libraries hijack (e. g. some dll loaded early) driver hijackers Data file infectors Macro Viruses format string exploits (not called viruses) Nicolas T. Courtois, December 2009 load before any anti-virus software
 Comp. Sec Malware Additional Infection Mechanisms • Terminate and Stay Resident = TSR – since MS-DOS. . – stays active in memory after application exits – can then infect other targets, for example • can trap OS calls that execute any program… 37 Nicolas T. Courtois, December 2009
Comp. Sec Malware Additional Infection Mechanisms • Terminate and Stay Resident = TSR – since MS-DOS. . – stays active in memory after application exits – can then infect other targets, for example • can trap OS calls that execute any program… 37 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Virus Defenses More about this later. Oldest methods: • Black-list: – signature-based detection. • Track changes to executables: – Tripwire, hash functions, MACs etc… 38 Nicolas T. Courtois, December 2009
Comp. Sec Malware Virus Defenses More about this later. Oldest methods: • Black-list: – signature-based detection. • Track changes to executables: – Tripwire, hash functions, MACs etc… 38 Nicolas T. Courtois, December 2009
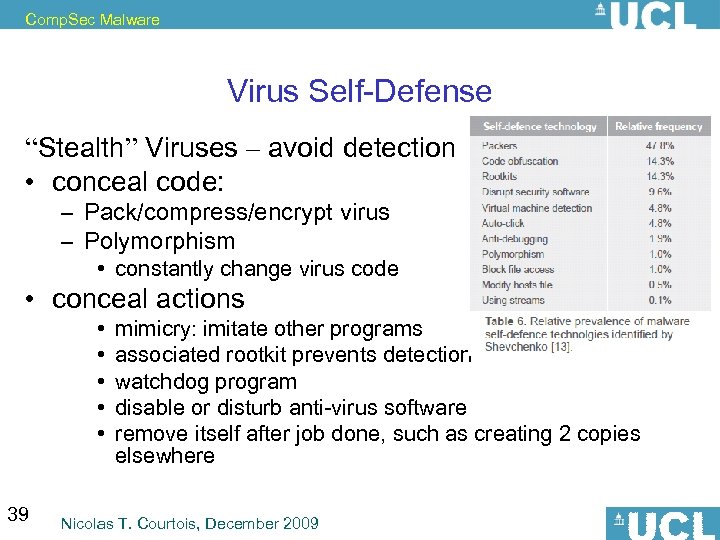 Comp. Sec Malware Virus Self-Defense “Stealth” Viruses – avoid detection • conceal code: – Pack/compress/encrypt virus – Polymorphism • constantly change virus code • conceal actions • • • 39 mimicry: imitate other programs associated rootkit prevents detection watchdog program disable or disturb anti-virus software remove itself after job done, such as creating 2 copies elsewhere Nicolas T. Courtois, December 2009
Comp. Sec Malware Virus Self-Defense “Stealth” Viruses – avoid detection • conceal code: – Pack/compress/encrypt virus – Polymorphism • constantly change virus code • conceal actions • • • 39 mimicry: imitate other programs associated rootkit prevents detection watchdog program disable or disturb anti-virus software remove itself after job done, such as creating 2 copies elsewhere Nicolas T. Courtois, December 2009
 Comp. Sec Malware Macro Viruses • infected a data file (e. g. word) – relies on macros interpreted by some application • application-dependent • can be OS-independent – Example: Microsoft Word: MAC and Windows 40 Nicolas T. Courtois, December 2009
Comp. Sec Malware Macro Viruses • infected a data file (e. g. word) – relies on macros interpreted by some application • application-dependent • can be OS-independent – Example: Microsoft Word: MAC and Windows 40 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Independent / “More Sophisticated Forms of Life” 41 Nicolas T. Courtois, December 2009
Comp. Sec Malware Independent / “More Sophisticated Forms of Life” 41 Nicolas T. Courtois, December 2009
 Comp. Sec Malware *Bacteria: simple functionality, program that replicates until it fills all disk space, all memory, all CPU cycles 42 Nicolas T. Courtois, December 2009
Comp. Sec Malware *Bacteria: simple functionality, program that replicates until it fills all disk space, all memory, all CPU cycles 42 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Worms • introduced by Shoch and Hupp in 1982. • runs independently, – no host program – infects a host machine – propagates in a network • a fully working version of itself copied to another host machine • spreads totally without human intervention virus 43 Nicolas T. Courtois, December 2009
Comp. Sec Malware Worms • introduced by Shoch and Hupp in 1982. • runs independently, – no host program – infects a host machine – propagates in a network • a fully working version of itself copied to another host machine • spreads totally without human intervention virus 43 Nicolas T. Courtois, December 2009
 Comp. Sec Malware more worms A worm has two main components: • an exploit – usually exploits web servers • or other exposed “DMZ-style” components • a “payload” of hidden tasks – backdoors, spam relays, DDo. S agents, etc. Life cycle phases: probing exploitation replication running the payload 44 Nicolas T. Courtois, December 2009
Comp. Sec Malware more worms A worm has two main components: • an exploit – usually exploits web servers • or other exposed “DMZ-style” components • a “payload” of hidden tasks – backdoors, spam relays, DDo. S agents, etc. Life cycle phases: probing exploitation replication running the payload 44 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Zombie Network = Botnet • Secretly takes over another networked computer by exploiting software flaws • Connect the compromised computers into a zombie network or botnet = – a collection of compromised machines • running programs such as worms, Trojan horses, or backdoors, • under a common command control infrastructure. • Uses it to indirectly launch attacks – e. g. , spamming, phishing , DDo. S, password cracking etc. • very frequently sold or rented, – about 0. 05 $ / host / week 45 Nicolas T. Courtois, December 2009
Comp. Sec Malware Zombie Network = Botnet • Secretly takes over another networked computer by exploiting software flaws • Connect the compromised computers into a zombie network or botnet = – a collection of compromised machines • running programs such as worms, Trojan horses, or backdoors, • under a common command control infrastructure. • Uses it to indirectly launch attacks – e. g. , spamming, phishing , DDo. S, password cracking etc. • very frequently sold or rented, – about 0. 05 $ / host / week 45 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Rootkits • Software used after system compromise to: – – Hide the attacker’s presence Provide backdoors for easy reentry • Simple rootkits: – Modify user programs (ls, ps) – Modify a compiler – Detectable by tools like Tripwire (stores hashes of files). • Sophisticated rootkits: – – 46 Modify the kernel itself Hard to detect from userland Nicolas T. Courtois, December 2009
Comp. Sec Malware Rootkits • Software used after system compromise to: – – Hide the attacker’s presence Provide backdoors for easy reentry • Simple rootkits: – Modify user programs (ls, ps) – Modify a compiler – Detectable by tools like Tripwire (stores hashes of files). • Sophisticated rootkits: – – 46 Modify the kernel itself Hard to detect from userland Nicolas T. Courtois, December 2009
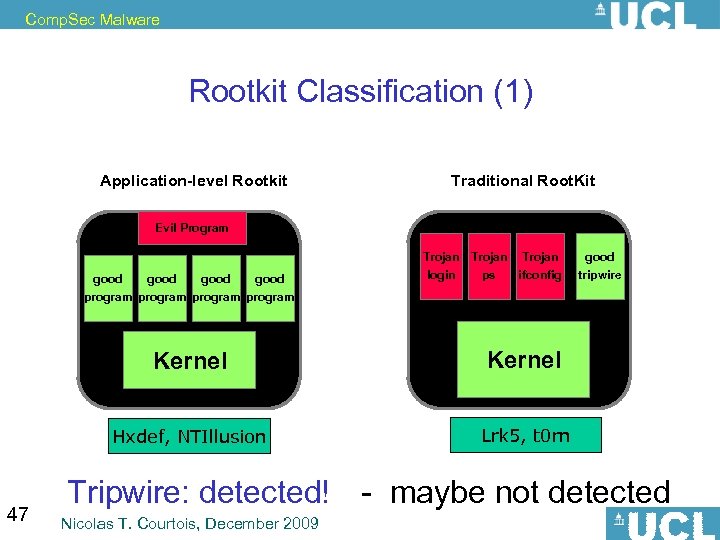 Comp. Sec Malware Rootkit Classification (1) Application-level Rootkit Traditional Root. Kit Evil Program good program Trojan login ps ifconfig Kernel 47 Kernel Hxdef, NTIllusion good tripwire Lrk 5, t 0 rn Tripwire: detected! - maybe not detected Nicolas T. Courtois, December 2009
Comp. Sec Malware Rootkit Classification (1) Application-level Rootkit Traditional Root. Kit Evil Program good program Trojan login ps ifconfig Kernel 47 Kernel Hxdef, NTIllusion good tripwire Lrk 5, t 0 rn Tripwire: detected! - maybe not detected Nicolas T. Courtois, December 2009
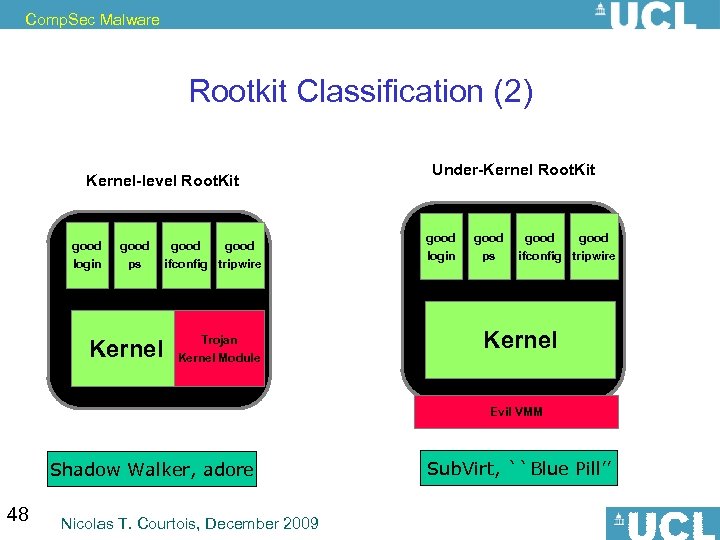 Comp. Sec Malware Rootkit Classification (2) Kernel-level Root. Kit good login good ps Kernel good ifconfig tripwire Trojan Kernel Module Under-Kernel Root. Kit good login good ps good ifconfig tripwire Kernel Evil VMM Shadow Walker, adore 48 Nicolas T. Courtois, December 2009 Sub. Virt, ``Blue Pill’’
Comp. Sec Malware Rootkit Classification (2) Kernel-level Root. Kit good login good ps Kernel good ifconfig tripwire Trojan Kernel Module Under-Kernel Root. Kit good login good ps good ifconfig tripwire Kernel Evil VMM Shadow Walker, adore 48 Nicolas T. Courtois, December 2009 Sub. Virt, ``Blue Pill’’
 Comp. Sec Malware What’s Going On? 49 Nicolas T. Courtois, December 2009
Comp. Sec Malware What’s Going On? 49 Nicolas T. Courtois, December 2009
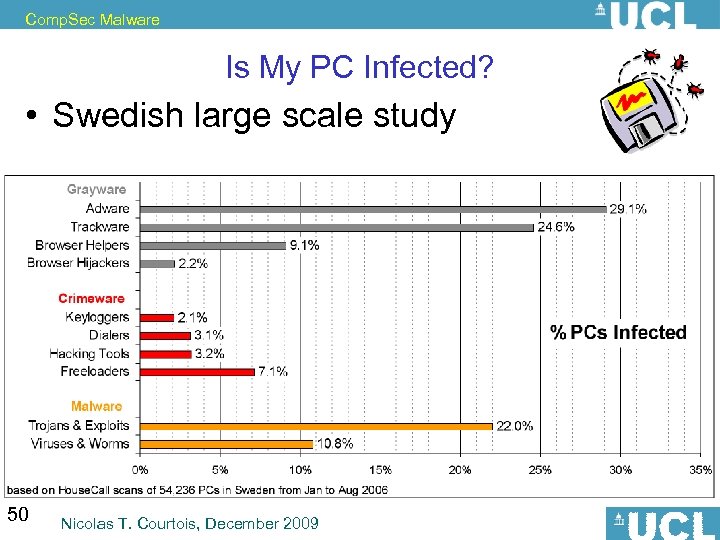 Comp. Sec Malware Is My PC Infected? • Swedish large scale study 50 Nicolas T. Courtois, December 2009
Comp. Sec Malware Is My PC Infected? • Swedish large scale study 50 Nicolas T. Courtois, December 2009
![Comp. Sec Malware Another Study PCs infected [source: Trend Micro] 51 Nicolas T. Courtois, Comp. Sec Malware Another Study PCs infected [source: Trend Micro] 51 Nicolas T. Courtois,](https://present5.com/presentation/0f3bf05b2786a943d28fbdc9cd580892/image-51.jpg) Comp. Sec Malware Another Study PCs infected [source: Trend Micro] 51 Nicolas T. Courtois, December 2009
Comp. Sec Malware Another Study PCs infected [source: Trend Micro] 51 Nicolas T. Courtois, December 2009
 Comp. Sec Malware According to experts: • Today’s malware is designed to remain undetected for months. – do not get famous, get rich! – zero-day malware 52 Nicolas T. Courtois, December 2009
Comp. Sec Malware According to experts: • Today’s malware is designed to remain undetected for months. – do not get famous, get rich! – zero-day malware 52 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Our Focus In Comp. Sec 1 we spend more time on worms than any other malware? Why? • Viruses and Trojans require some human actions, such as sharing a USB stick, clicking on web sites, opening ; doc email attachments etc. – spread is slow. • Worms don’t require human presence. – Spread is MUCH faster Moreover worms do hack/break into computers, viruses and Trojans they use legitimate access channels and just abuse these privileges. 53 Nicolas T. Courtois, December 2009
Comp. Sec Malware Our Focus In Comp. Sec 1 we spend more time on worms than any other malware? Why? • Viruses and Trojans require some human actions, such as sharing a USB stick, clicking on web sites, opening ; doc email attachments etc. – spread is slow. • Worms don’t require human presence. – Spread is MUCH faster Moreover worms do hack/break into computers, viruses and Trojans they use legitimate access channels and just abuse these privileges. 53 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Famous Historical Worms - Unix 54 Nicolas T. Courtois, December 2009
Comp. Sec Malware Famous Historical Worms - Unix 54 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Morris Worm (first major network attack) • Released November 1988 – spreading on Digital and Sun workstations – exploited several Unix security vulnerabilities • Consequences – no immediate damage – replication • load on network, • load on CPUs – many systems were shut down • fearing damage (only later people found it was not harmful) 55 Nicolas T. Courtois, December 2009
Comp. Sec Malware Morris Worm (first major network attack) • Released November 1988 – spreading on Digital and Sun workstations – exploited several Unix security vulnerabilities • Consequences – no immediate damage – replication • load on network, • load on CPUs – many systems were shut down • fearing damage (only later people found it was not harmful) 55 Nicolas T. Courtois, December 2009
 Comp. Sec Malware ***Morris - Author Robert T. Morris, released it November 1988 • His father, another Robert Morris was – a cryptologist and code-breaker (broke codes for the FBI), – worked for the NSA “National Computer Security Center”, – wrote a book about UNIX Operating System Security (1984). 56 Nicolas T. Courtois, December 2009
Comp. Sec Malware ***Morris - Author Robert T. Morris, released it November 1988 • His father, another Robert Morris was – a cryptologist and code-breaker (broke codes for the FBI), – worked for the NSA “National Computer Security Center”, – wrote a book about UNIX Operating System Security (1984). 56 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Morris Worm – program to spread worm • looks for other machines that could be infected, several methods used: 'netstat -r -n‘, /etc/hosts, • when worm successfully connects, forks a child to continue the infection while the parent keeps trying new hosts – vector program (99 lines of C) • re-compiled and run on the infected machines 57 Nicolas T. Courtois, December 2009
Comp. Sec Malware Morris Worm – program to spread worm • looks for other machines that could be infected, several methods used: 'netstat -r -n‘, /etc/hosts, • when worm successfully connects, forks a child to continue the infection while the parent keeps trying new hosts – vector program (99 lines of C) • re-compiled and run on the infected machines 57 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Three ways the worm spread • Sendmail – exploited debug option in sendmail to allow shell access • Fingerd – exploited a buffer overflow in the fgets function • Remote shell – reading list of trusted hosts known to local OS – password cracking 58 Nicolas T. Courtois, December 2009
Comp. Sec Malware Three ways the worm spread • Sendmail – exploited debug option in sendmail to allow shell access • Fingerd – exploited a buffer overflow in the fgets function • Remote shell – reading list of trusted hosts known to local OS – password cracking 58 Nicolas T. Courtois, December 2009
 Comp. Sec Malware *sendmail • Worm used debug feature – – opens TCP connection to machine's SMTP port invokes debug mode sends a RCPT TO that pipes data through shell script retrieves worm main program • places 40 -line C program in temporary file called x$$, l 1. c where $$ is current process ID • compiles and executes this program • opens socket to machine that sent script • retrieves worm main program, compiles it and runs 59 Nicolas T. Courtois, December 2009
Comp. Sec Malware *sendmail • Worm used debug feature – – opens TCP connection to machine's SMTP port invokes debug mode sends a RCPT TO that pipes data through shell script retrieves worm main program • places 40 -line C program in temporary file called x$$, l 1. c where $$ is current process ID • compiles and executes this program • opens socket to machine that sent script • retrieves worm main program, compiles it and runs 59 Nicolas T. Courtois, December 2009
 Comp. Sec Malware *fingerd • written in C and runs continuously • Array bounds attack – Fingerd expects an input string – Worm writes long string to internal 512 -byte buffer • Attack string – – 60 Includes machine instructions Overwrites return address Invokes a remote shell Executes privileged commands Nicolas T. Courtois, December 2009
Comp. Sec Malware *fingerd • written in C and runs continuously • Array bounds attack – Fingerd expects an input string – Worm writes long string to internal 512 -byte buffer • Attack string – – 60 Includes machine instructions Overwrites return address Invokes a remote shell Executes privileged commands Nicolas T. Courtois, December 2009
 Comp. Sec Malware *remote shell • Unix trust information – /etc/host. equiv – system wide trusted hosts file – /. rhosts and ~/. rhosts – users’ trusted hosts file • Worm exploited this information – assumed reciprocal trust: maybe Y trusts X as well. . • Password cracking • worm was running as daemon (not root) so needed to break into accounts to use. rhosts feature • read /etc/passwd, used 400 common password strings & local dictionary to do a dictionary attack 61 Nicolas T. Courtois, December 2009
Comp. Sec Malware *remote shell • Unix trust information – /etc/host. equiv – system wide trusted hosts file – /. rhosts and ~/. rhosts – users’ trusted hosts file • Worm exploited this information – assumed reciprocal trust: maybe Y trusts X as well. . • Password cracking • worm was running as daemon (not root) so needed to break into accounts to use. rhosts feature • read /etc/passwd, used 400 common password strings & local dictionary to do a dictionary attack 61 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Not so bad… • Morris worm did not: – – delete system's files, modify user files, install Trojans, make any other use of cracked passwords • e. g. record or re-transmit elsewhere – it never took superuser privileges… 62 Nicolas T. Courtois, December 2009
Comp. Sec Malware Not so bad… • Morris worm did not: – – delete system's files, modify user files, install Trojans, make any other use of cracked passwords • e. g. record or re-transmit elsewhere – it never took superuser privileges… 62 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Detecting Morris Internet Worm • Files – Strange files appeared in infected systems – Strange log messages for certain programs • System load – Infection generates a number of processes – Password cracking uses lots of resources – Systems were reinfected => number of processes grew and systems became overloaded • Apparently not intended by worm’s creator Thousands of systems were shut down 63 Nicolas T. Courtois, December 2009
Comp. Sec Malware Detecting Morris Internet Worm • Files – Strange files appeared in infected systems – Strange log messages for certain programs • System load – Infection generates a number of processes – Password cracking uses lots of resources – Systems were reinfected => number of processes grew and systems became overloaded • Apparently not intended by worm’s creator Thousands of systems were shut down 63 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Famous Windows Worms 64 Nicolas T. Courtois, December 2009
Comp. Sec Malware Famous Windows Worms 64 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Increasing propagation speed • Code Red, July 2001 – fascinating story, see Brad Karp slides • Released AFTER Microsoft released the patch • affecting like 500 000 hosts in hours • SQL Slammer, January 2003 – See Brad Karp too. • vulnerable population infected in less than 10 minutes • its growth was limited… by the speed of the Internet Remark: both exploited an already known and already patched buffer overflow vulnerability! 65 Nicolas T. Courtois, December 2009
Comp. Sec Malware Increasing propagation speed • Code Red, July 2001 – fascinating story, see Brad Karp slides • Released AFTER Microsoft released the patch • affecting like 500 000 hosts in hours • SQL Slammer, January 2003 – See Brad Karp too. • vulnerable population infected in less than 10 minutes • its growth was limited… by the speed of the Internet Remark: both exploited an already known and already patched buffer overflow vulnerability! 65 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Nimda worm • Spreads via 5 methods to Windows PCs and servers – e-mails itself as an attachment (every 10 days) • runs once viewed in preview plane (due to bugs in IE) – scans for and infects vulnerable MS IIS servers • exploits various IIS directory traversal vulnerabilities – copies itself to shared disk drives on networked PCs – appends Java. Script code to Web pages • surfers pick up worm when they view the page. – scans for the back doors left behind by the "Code Red II" and "sadmind/IIS" worms 66 Nicolas T. Courtois, December 2009
Comp. Sec Malware Nimda worm • Spreads via 5 methods to Windows PCs and servers – e-mails itself as an attachment (every 10 days) • runs once viewed in preview plane (due to bugs in IE) – scans for and infects vulnerable MS IIS servers • exploits various IIS directory traversal vulnerabilities – copies itself to shared disk drives on networked PCs – appends Java. Script code to Web pages • surfers pick up worm when they view the page. – scans for the back doors left behind by the "Code Red II" and "sadmind/IIS" worms 66 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Nimda worm • Nimda worm also – enables the sharing of the c: drive as C$ – creates a "Guest" account on Windows NT and 2000 systems – adds this account to the "Administrator" group. 67 Nicolas T. Courtois, December 2009
Comp. Sec Malware Nimda worm • Nimda worm also – enables the sharing of the c: drive as C$ – creates a "Guest" account on Windows NT and 2000 systems – adds this account to the "Administrator" group. 67 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Cost of worm attacks • Morris worm, November 1988 – Infected approximately 6, 000 machines • was 10% of all computers connected to the Internet! – cost ~ $10 million in downtime and cleanup • Code Red worm, July 16 2001 – Direct descendant of Morris’ worm – Infected more than 500, 000 servers – Caused ~ $2. 6 Billion in damages, • Love Bug worm: May 3, 2000, $8. 75 billion Statistics: Computer Economics Inc. , Carlsbad, California 68 Nicolas T. Courtois, December 2009
Comp. Sec Malware Cost of worm attacks • Morris worm, November 1988 – Infected approximately 6, 000 machines • was 10% of all computers connected to the Internet! – cost ~ $10 million in downtime and cleanup • Code Red worm, July 16 2001 – Direct descendant of Morris’ worm – Infected more than 500, 000 servers – Caused ~ $2. 6 Billion in damages, • Love Bug worm: May 3, 2000, $8. 75 billion Statistics: Computer Economics Inc. , Carlsbad, California 68 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Defences 69 Nicolas T. Courtois, December 2009
Comp. Sec Malware Defences 69 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Virus Defenses Today’s “anti-virus software”: Just a name. Virus + firewall + etc… Defends against all sorts of malware. classical viruses are only about 5% nowadays… 70 Nicolas T. Courtois, December 2009
Comp. Sec Malware Virus Defenses Today’s “anti-virus software”: Just a name. Virus + firewall + etc… Defends against all sorts of malware. classical viruses are only about 5% nowadays… 70 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Tips • do not execute programs obtained by email • maybe do not install any new software – ? ? ? • very few software companies can be trusted to care about their customers, – lack of liability, lack of legal obligations, culture of irresponsibility, need to renew products range etc… – do they even understand how secure is their own software? 71 Nicolas T. Courtois, December 2009
Comp. Sec Malware Tips • do not execute programs obtained by email • maybe do not install any new software – ? ? ? • very few software companies can be trusted to care about their customers, – lack of liability, lack of legal obligations, culture of irresponsibility, need to renew products range etc… – do they even understand how secure is their own software? 71 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Automated Virus Defenses White list: accept only trusted digitally signed programs. Examples: Nokia Symbian software Microsoft: OS updates, drivers, anti-virus Prevalent methods in PCs: • Black-list, signature-based detection. • Networks firewalls • control application calls and IPC • monitor and prevent “privileged” system calls, e. g. registry modification, plug-ins install etc. • track changes to executables (hash/MAC/sign) 72 Nicolas T. Courtois, December 2009
Comp. Sec Malware Automated Virus Defenses White list: accept only trusted digitally signed programs. Examples: Nokia Symbian software Microsoft: OS updates, drivers, anti-virus Prevalent methods in PCs: • Black-list, signature-based detection. • Networks firewalls • control application calls and IPC • monitor and prevent “privileged” system calls, e. g. registry modification, plug-ins install etc. • track changes to executables (hash/MAC/sign) 72 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Network Defences 73 Nicolas T. Courtois, December 2009
Comp. Sec Malware Network Defences 73 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Internet-Wide Defences Cyberspace: • a new dimension of national defense. • a critical infrastructure Goal: monitor the Internet at a larger scale, detect anomalies. 74 Nicolas T. Courtois, December 2009
Comp. Sec Malware Internet-Wide Defences Cyberspace: • a new dimension of national defense. • a critical infrastructure Goal: monitor the Internet at a larger scale, detect anomalies. 74 Nicolas T. Courtois, December 2009
 Comp. Sec Malware *Traditional Military Doctrine • Each country has 3 frontiers: • land • sea • air, space as a consequence they have 3 armies. Now, we have a new frontier, the digital frontier. Shouldn’t we have a fourth army? • It would be totally useless and waste of money? • Arguably less than the 3 above (better technical education for young people). 75 Nicolas T. Courtois, December 2009
Comp. Sec Malware *Traditional Military Doctrine • Each country has 3 frontiers: • land • sea • air, space as a consequence they have 3 armies. Now, we have a new frontier, the digital frontier. Shouldn’t we have a fourth army? • It would be totally useless and waste of money? • Arguably less than the 3 above (better technical education for young people). 75 Nicolas T. Courtois, December 2009
 Comp. Sec Malware Network Telescopes Monitor traffic arriving at large sizeable regions of Internet address space. Reveals, e. g. , : – “Backscatter” = responses to randomly source-spoofed DDo. S attacks – Worms’ random scanning of IP addresses – Attackers randomly scanning for a particular port, servers running a particular service, etc… Examples: – LBNL: 1/215 of Internet address space – UCSD/Univ. Wisconsin: covers 1/28. 76 Nicolas T. Courtois, December 2009
Comp. Sec Malware Network Telescopes Monitor traffic arriving at large sizeable regions of Internet address space. Reveals, e. g. , : – “Backscatter” = responses to randomly source-spoofed DDo. S attacks – Worms’ random scanning of IP addresses – Attackers randomly scanning for a particular port, servers running a particular service, etc… Examples: – LBNL: 1/215 of Internet address space – UCSD/Univ. Wisconsin: covers 1/28. 76 Nicolas T. Courtois, December 2009
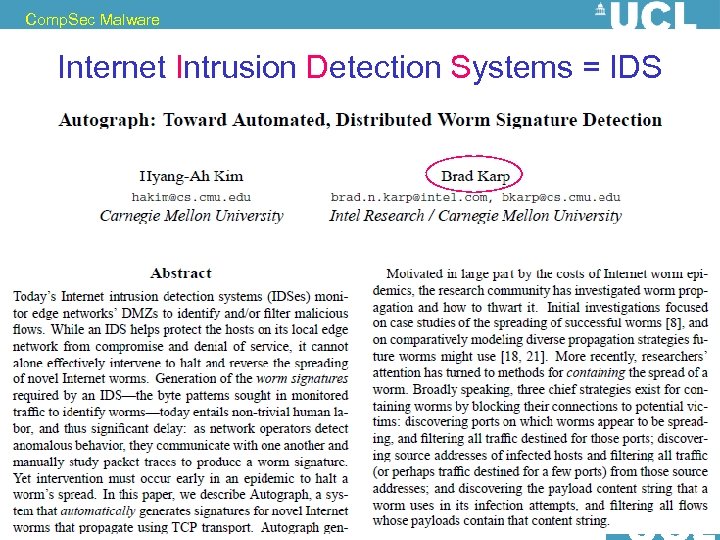 Comp. Sec Malware Internet Intrusion Detection Systems = IDS 77 Nicolas T. Courtois, December 2009
Comp. Sec Malware Internet Intrusion Detection Systems = IDS 77 Nicolas T. Courtois, December 2009


