b72ef592565e3ff3e657e3aa2b92bf5b.ppt
- Количество слайдов: 40
 Making Your IP Communications Implementation Secure and Resilient Kevin Flynn Senior Manager March, 2006 JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 1
Making Your IP Communications Implementation Secure and Resilient Kevin Flynn Senior Manager March, 2006 JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 1
 Agenda • Issues & Challenges • Cisco Self-Defending Network • IP Communications Security • Getting Started JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 2
Agenda • Issues & Challenges • Cisco Self-Defending Network • IP Communications Security • Getting Started JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 2
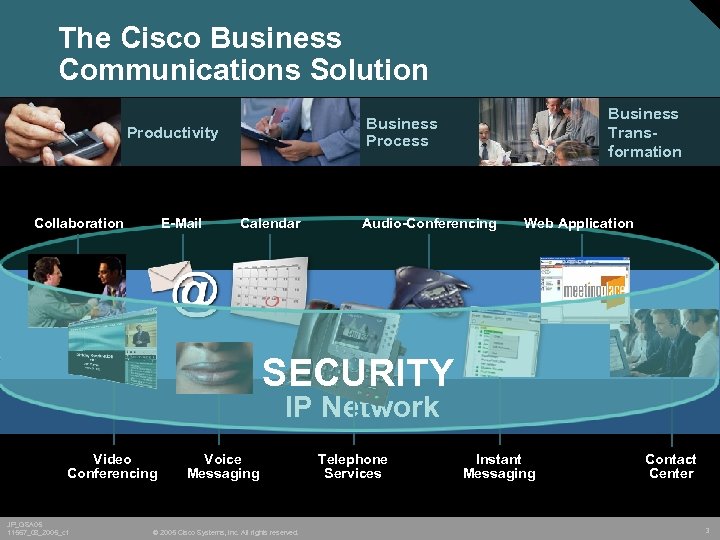 The Cisco Business Communications Solution Productivity Collaboration E-Mail Business Transformation Business Process Calendar Audio-Conferencing Web Application SECURITY IP Network Video Conferencing JP_GSA 05 11567_08_2005_c 1 Voice Messaging © 2005 Cisco Systems, Inc. All rights reserved. Telephone Services Instant Messaging Contact Center 3
The Cisco Business Communications Solution Productivity Collaboration E-Mail Business Transformation Business Process Calendar Audio-Conferencing Web Application SECURITY IP Network Video Conferencing JP_GSA 05 11567_08_2005_c 1 Voice Messaging © 2005 Cisco Systems, Inc. All rights reserved. Telephone Services Instant Messaging Contact Center 3
 A Tale of Two Cities Secure Network JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Secure IPC 4
A Tale of Two Cities Secure Network JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Secure IPC 4
 A Tale of Many Fiefdoms Net. OPs Sec. Ops Secure IP Voice BDMs JP_GSA 05 11567_08_2005_c 1 Tel. Ops © 2005 Cisco Systems, Inc. All rights reserved. 5
A Tale of Many Fiefdoms Net. OPs Sec. Ops Secure IP Voice BDMs JP_GSA 05 11567_08_2005_c 1 Tel. Ops © 2005 Cisco Systems, Inc. All rights reserved. 5
 Secure IPC – Integrated & Systemic • IP Communications solutions from Cisco can be as secure, or more secure, than traditional PBX systems Key is integrated approach – IPC + Secure Infrastructure Cisco is committed to delivering the most secure, reliable solution possible – at all layers of the network Recent enhancements further increase the security capabilities of the industry leading Cisco Unified Communications system Independent testing says Cisco provides the most secure IP Communications solution available* *As tested by Miercom Labs and reported by Network World JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 6
Secure IPC – Integrated & Systemic • IP Communications solutions from Cisco can be as secure, or more secure, than traditional PBX systems Key is integrated approach – IPC + Secure Infrastructure Cisco is committed to delivering the most secure, reliable solution possible – at all layers of the network Recent enhancements further increase the security capabilities of the industry leading Cisco Unified Communications system Independent testing says Cisco provides the most secure IP Communications solution available* *As tested by Miercom Labs and reported by Network World JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 6
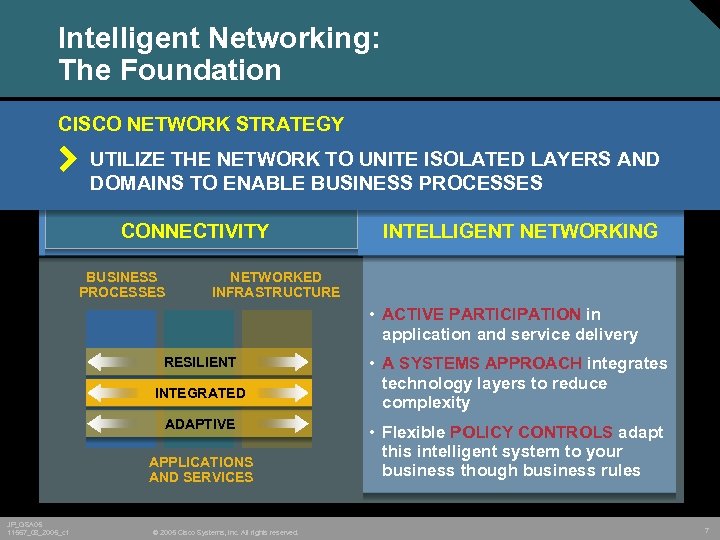 Intelligent Networking: The Foundation CISCO NETWORK STRATEGY UTILIZE THE NETWORK TO UNITE ISOLATED LAYERS AND DOMAINS TO ENABLE BUSINESS PROCESSES CONNECTIVITY BUSINESS PROCESSES INTELLIGENT NETWORKING NETWORKED INFRASTRUCTURE • ACTIVE PARTICIPATION in application and service delivery RESILIENT INTEGRATED ADAPTIVE APPLICATIONS AND SERVICES JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • A SYSTEMS APPROACH integrates technology layers to reduce complexity • Flexible POLICY CONTROLS adapt this intelligent system to your business though business rules 7
Intelligent Networking: The Foundation CISCO NETWORK STRATEGY UTILIZE THE NETWORK TO UNITE ISOLATED LAYERS AND DOMAINS TO ENABLE BUSINESS PROCESSES CONNECTIVITY BUSINESS PROCESSES INTELLIGENT NETWORKING NETWORKED INFRASTRUCTURE • ACTIVE PARTICIPATION in application and service delivery RESILIENT INTEGRATED ADAPTIVE APPLICATIONS AND SERVICES JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • A SYSTEMS APPROACH integrates technology layers to reduce complexity • Flexible POLICY CONTROLS adapt this intelligent system to your business though business rules 7
 Benefits of a Systems Approach • • • Complex environment Gaps & inconsistency Lower visibility More difficult to manage Higher TCO JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • Simplified environment • Tighter integration = tighter security • Greater visibility • Easier to deploy & manage • Lower TCO 8
Benefits of a Systems Approach • • • Complex environment Gaps & inconsistency Lower visibility More difficult to manage Higher TCO JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • Simplified environment • Tighter integration = tighter security • Greater visibility • Easier to deploy & manage • Lower TCO 8
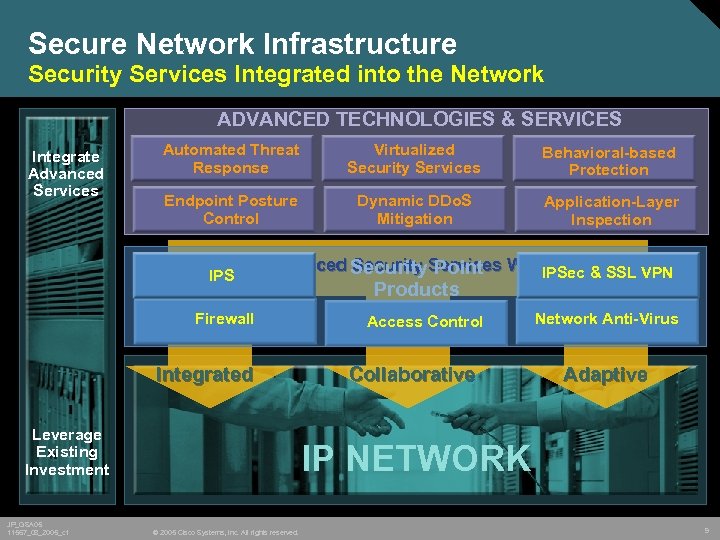 Secure Network Infrastructure Security Services Integrated into the Network ADVANCED TECHNOLOGIES & SERVICES Integrate Advanced Services Automated Threat Response Virtualized Security Services Behavioral-based Protection Endpoint Posture Control Dynamic DDo. S Mitigation Application-Layer Inspection Integrate Advanced Security. Services Where Needed VPN Security Point IPSec & SSL IPS Firewall Integrated Leverage Existing Investment JP_GSA 05 11567_08_2005_c 1 Products Access Control Collaborative Network Anti-Virus Adaptive IP NETWORK © 2005 Cisco Systems, Inc. All rights reserved. 9
Secure Network Infrastructure Security Services Integrated into the Network ADVANCED TECHNOLOGIES & SERVICES Integrate Advanced Services Automated Threat Response Virtualized Security Services Behavioral-based Protection Endpoint Posture Control Dynamic DDo. S Mitigation Application-Layer Inspection Integrate Advanced Security. Services Where Needed VPN Security Point IPSec & SSL IPS Firewall Integrated Leverage Existing Investment JP_GSA 05 11567_08_2005_c 1 Products Access Control Collaborative Network Anti-Virus Adaptive IP NETWORK © 2005 Cisco Systems, Inc. All rights reserved. 9
 The IP Communications Conundrum • The same IP technology that enables IP Communications solutions to: Boost productivity Increase mobility Enhance flexibility Also creates additional MANAGEABLE challenges for information security • These new challenges exist whether the IP upgrade is incremental or total JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 10
The IP Communications Conundrum • The same IP technology that enables IP Communications solutions to: Boost productivity Increase mobility Enhance flexibility Also creates additional MANAGEABLE challenges for information security • These new challenges exist whether the IP upgrade is incremental or total JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 10
 The Challenge of Securing IP Voice • The threats are familiar to both voice and data professionals: Denial of service Privacy Impersonation Toll fraud • Both “phreakers” (voice) and “hackers” (data) are lurking • The protection of both voice and data communication is critical to the business 11 JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 11
The Challenge of Securing IP Voice • The threats are familiar to both voice and data professionals: Denial of service Privacy Impersonation Toll fraud • Both “phreakers” (voice) and “hackers” (data) are lurking • The protection of both voice and data communication is critical to the business 11 JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 11
 IP Communications Threats • Toll fraud Unauthorized or unbillable resource utilization • Eavesdropping Listening to another’s call • Learning private information caller ID, DTMF password/accounts, calling patterns • Session replay Replay a session, such as a bank transaction JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • Fake identity • Media tampering • Denial of service Hanging up other people's conversations Contributing to other DOS attacks • Impersonating others • Hijacking calls • SPAM SPIM, SPIT, and more SPAM 12
IP Communications Threats • Toll fraud Unauthorized or unbillable resource utilization • Eavesdropping Listening to another’s call • Learning private information caller ID, DTMF password/accounts, calling patterns • Session replay Replay a session, such as a bank transaction JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. • Fake identity • Media tampering • Denial of service Hanging up other people's conversations Contributing to other DOS attacks • Impersonating others • Hijacking calls • SPAM SPIM, SPIT, and more SPAM 12
 Evaluate the Threats Objectively • Understand the costs of security incidents: Measurable: fraud, downtime, man-hours, physical destruction, intellectual property, lawsuits Non-measurable: reputation, customer privacy, medical information, loss of life • Assign risk and quantify the costs • Determine appropriate levels of protection JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 13
Evaluate the Threats Objectively • Understand the costs of security incidents: Measurable: fraud, downtime, man-hours, physical destruction, intellectual property, lawsuits Non-measurable: reputation, customer privacy, medical information, loss of life • Assign risk and quantify the costs • Determine appropriate levels of protection JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 13
 Reality Check Before After JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 14
Reality Check Before After JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 14
 Comparison to PSTN • In many ways PSTN is good with respect to toll fraud Still a very large amount of toll fraud on PSTN • No voice crypto Person in wiring closet can listen to calls Anyone willing to poke around can listen to calls • Caller ID is bogus Anyone can produce fake caller id for a few hundred dollars • Is the security of the PSTN good enough? Will you give you credit card number over the telephone? Discuss a merger? JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 15
Comparison to PSTN • In many ways PSTN is good with respect to toll fraud Still a very large amount of toll fraud on PSTN • No voice crypto Person in wiring closet can listen to calls Anyone willing to poke around can listen to calls • Caller ID is bogus Anyone can produce fake caller id for a few hundred dollars • Is the security of the PSTN good enough? Will you give you credit card number over the telephone? Discuss a merger? JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 15
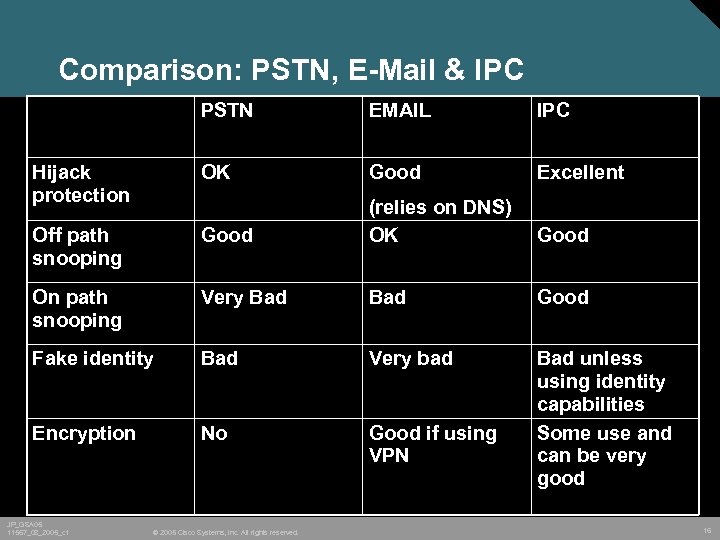 Comparison: PSTN, E-Mail & IPC PSTN EMAIL IPC Hijack protection OK Good Excellent Off path snooping Good (relies on DNS) OK Good On path snooping Very Bad Good Fake identity Bad Very bad Encryption No Good if using VPN Bad unless using identity capabilities Some use and can be very good JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 16
Comparison: PSTN, E-Mail & IPC PSTN EMAIL IPC Hijack protection OK Good Excellent Off path snooping Good (relies on DNS) OK Good On path snooping Very Bad Good Fake identity Bad Very bad Encryption No Good if using VPN Bad unless using identity capabilities Some use and can be very good JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 16
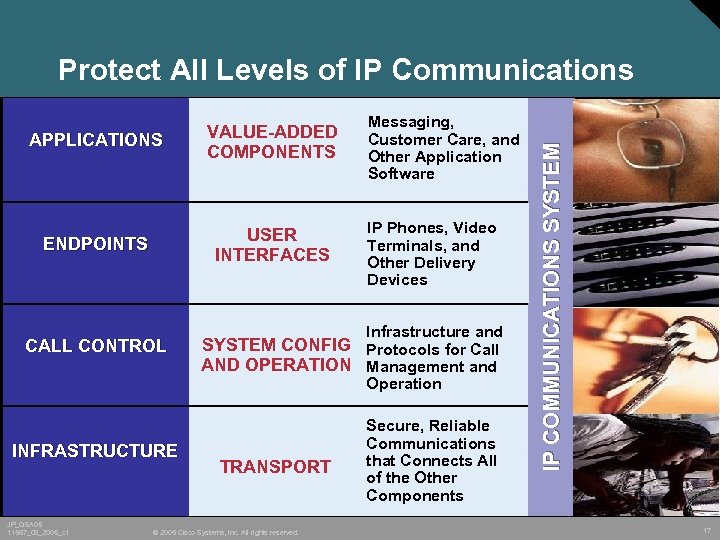 APPLICATIONS VALUE-ADDED COMPONENTS ENDPOINTS USER INTERFACES CALL CONTROL Messaging, Customer Care, and Other Application Software IP Phones, Video Terminals, and Other Delivery Devices Infrastructure and SYSTEM CONFIG Protocols for Call AND OPERATION Management and Operation INFRASTRUCTURE JP_GSA 05 11567_08_2005_c 1 TRANSPORT © 2005 Cisco Systems, Inc. All rights reserved. Secure, Reliable Communications that Connects All of the Other Components IP COMMUNICATIONS SYSTEM Protect All Levels of IP Communications 17
APPLICATIONS VALUE-ADDED COMPONENTS ENDPOINTS USER INTERFACES CALL CONTROL Messaging, Customer Care, and Other Application Software IP Phones, Video Terminals, and Other Delivery Devices Infrastructure and SYSTEM CONFIG Protocols for Call AND OPERATION Management and Operation INFRASTRUCTURE JP_GSA 05 11567_08_2005_c 1 TRANSPORT © 2005 Cisco Systems, Inc. All rights reserved. Secure, Reliable Communications that Connects All of the Other Components IP COMMUNICATIONS SYSTEM Protect All Levels of IP Communications 17
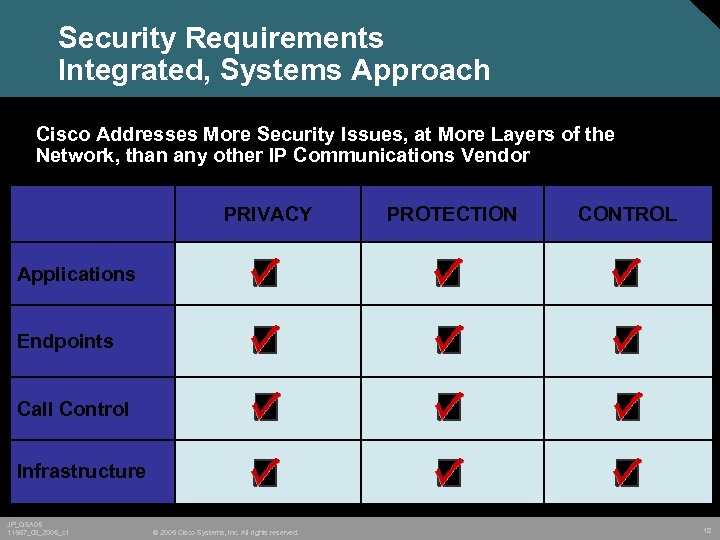 Security Requirements Integrated, Systems Approach Cisco Addresses More Security Issues, at More Layers of the Network, than any other IP Communications Vendor PRIVACY PROTECTION CONTROL Applications X X X Endpoints X X X Call Control X X X Infrastructure X X X JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 18
Security Requirements Integrated, Systems Approach Cisco Addresses More Security Issues, at More Layers of the Network, than any other IP Communications Vendor PRIVACY PROTECTION CONTROL Applications X X X Endpoints X X X Call Control X X X Infrastructure X X X JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 18
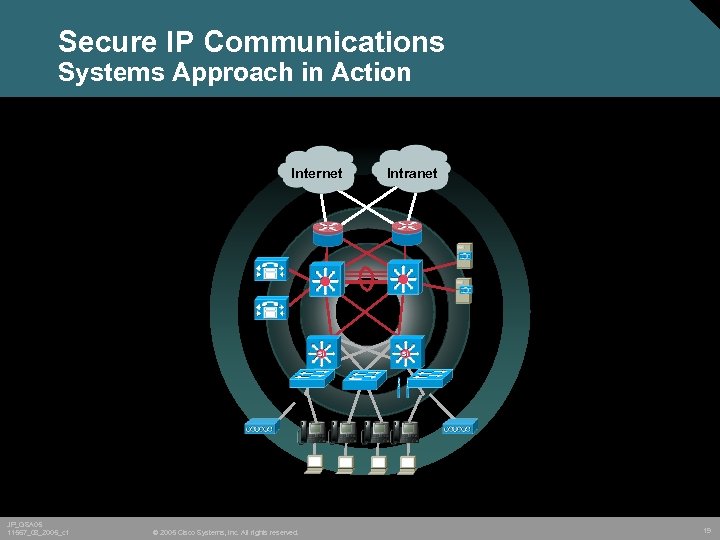 Secure IP Communications Systems Approach in Action Internet JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet 19
Secure IP Communications Systems Approach in Action Internet JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet 19
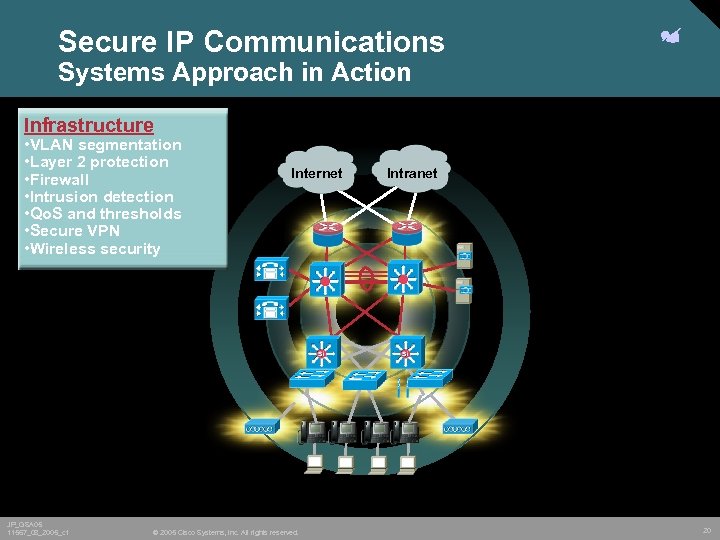 Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security JP_GSA 05 11567_08_2005_c 1 Internet © 2005 Cisco Systems, Inc. All rights reserved. Intranet 20
Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security JP_GSA 05 11567_08_2005_c 1 Internet © 2005 Cisco Systems, Inc. All rights reserved. Intranet 20
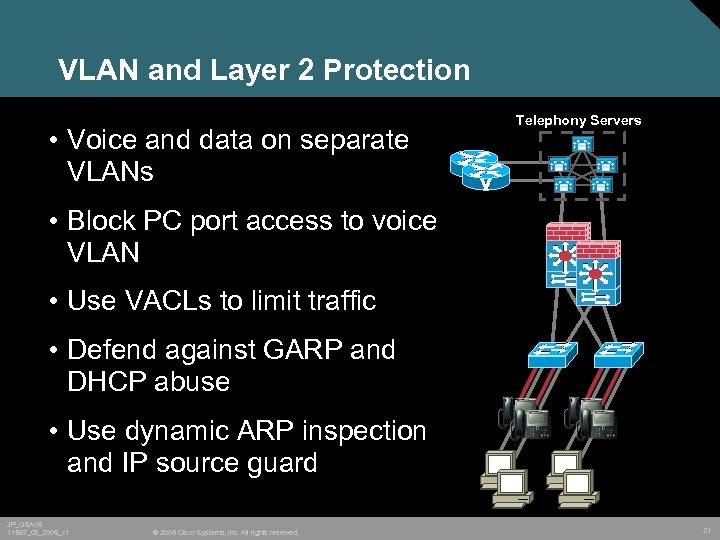 VLAN and Layer 2 Protection • Voice and data on separate VLANs Telephony Servers • Block PC port access to voice VLAN • Use VACLs to limit traffic • Defend against GARP and DHCP abuse • Use dynamic ARP inspection and IP source guard JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 21
VLAN and Layer 2 Protection • Voice and data on separate VLANs Telephony Servers • Block PC port access to voice VLAN • Use VACLs to limit traffic • Defend against GARP and DHCP abuse • Use dynamic ARP inspection and IP source guard JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 21
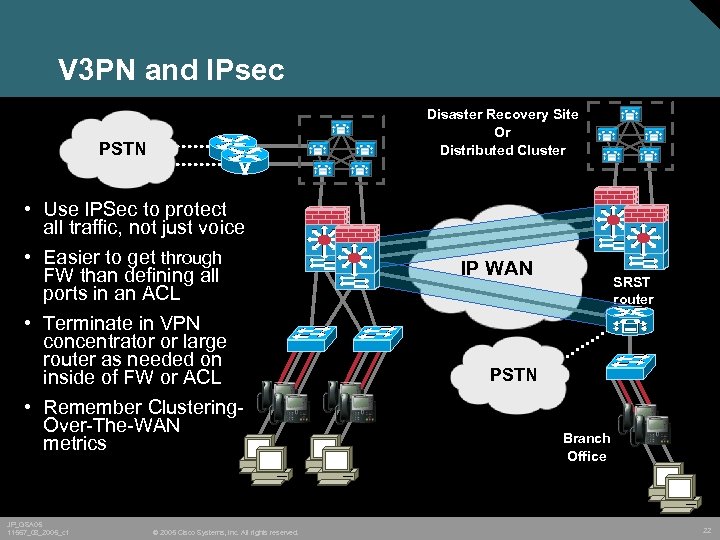 V 3 PN and IPsec Disaster Recovery Site Or Distributed Cluster PSTN • Use IPSec to protect all traffic, not just voice • Easier to get through FW than defining all ports in an ACL • Terminate in VPN concentrator or large router as needed on inside of FW or ACL • Remember Clustering. Over-The-WAN metrics JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. IP WAN SRST router PSTN Branch Office 22
V 3 PN and IPsec Disaster Recovery Site Or Distributed Cluster PSTN • Use IPSec to protect all traffic, not just voice • Easier to get through FW than defining all ports in an ACL • Terminate in VPN concentrator or large router as needed on inside of FW or ACL • Remember Clustering. Over-The-WAN metrics JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. IP WAN SRST router PSTN Branch Office 22
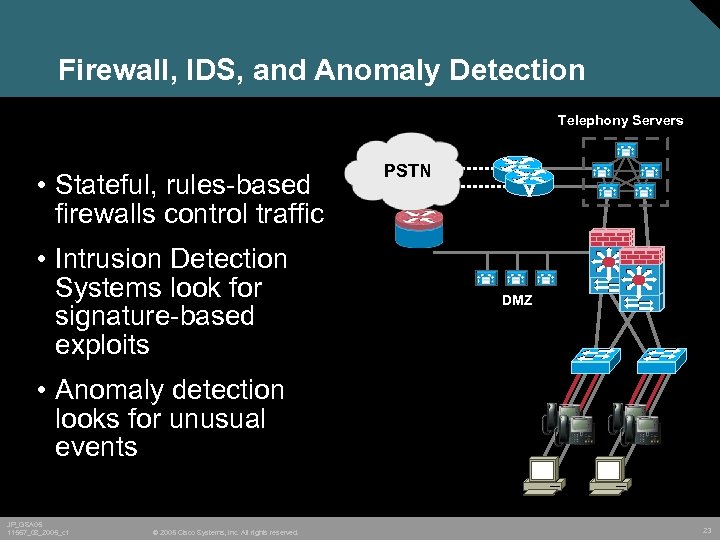 Firewall, IDS, and Anomaly Detection Telephony Servers • Stateful, rules-based firewalls control traffic • Intrusion Detection Systems look for signature-based exploits PSTN DMZ • Anomaly detection looks for unusual events JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 23
Firewall, IDS, and Anomaly Detection Telephony Servers • Stateful, rules-based firewalls control traffic • Intrusion Detection Systems look for signature-based exploits PSTN DMZ • Anomaly detection looks for unusual events JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 23
 Using Qo. S and Thresholds • Quality of Service enables clear voice connections during congestion • Rate limiting thwarts Do. S and DDo. S attacks from impacting voice • Processor thresholds protect routers and switches from overload JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 24
Using Qo. S and Thresholds • Quality of Service enables clear voice connections during congestion • Rate limiting thwarts Do. S and DDo. S attacks from impacting voice • Processor thresholds protect routers and switches from overload JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 24
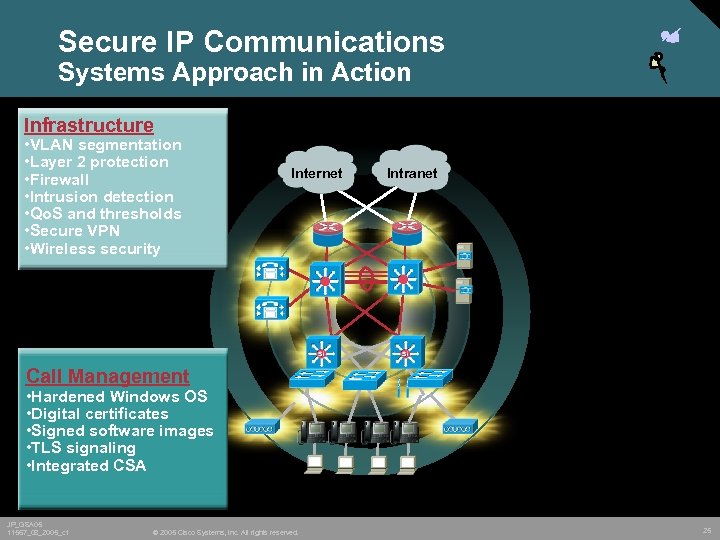 Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Internet Intranet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 25
Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Internet Intranet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 25
 Hardened Call Management Platform • Hardened Win 2 K OS Shipped By Default, and downloadable from Cisco Connection Online • Aggressive Security Patch and Hotfix Policy Critical: Tested and posted to CCO within 24 hours Others: Consolidated and posted once per month New email alias tells you when new patches are available (http: //www. cisco. com/warp/public/779/largeent/software_patch. html) • Install Mc. Afee 7. 1, Symantec 8. 1, or Trend Micro Server. Protect 5 Anti-Virus Protection JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 26
Hardened Call Management Platform • Hardened Win 2 K OS Shipped By Default, and downloadable from Cisco Connection Online • Aggressive Security Patch and Hotfix Policy Critical: Tested and posted to CCO within 24 hours Others: Consolidated and posted once per month New email alias tells you when new patches are available (http: //www. cisco. com/warp/public/779/largeent/software_patch. html) • Install Mc. Afee 7. 1, Symantec 8. 1, or Trend Micro Server. Protect 5 Anti-Virus Protection JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 26
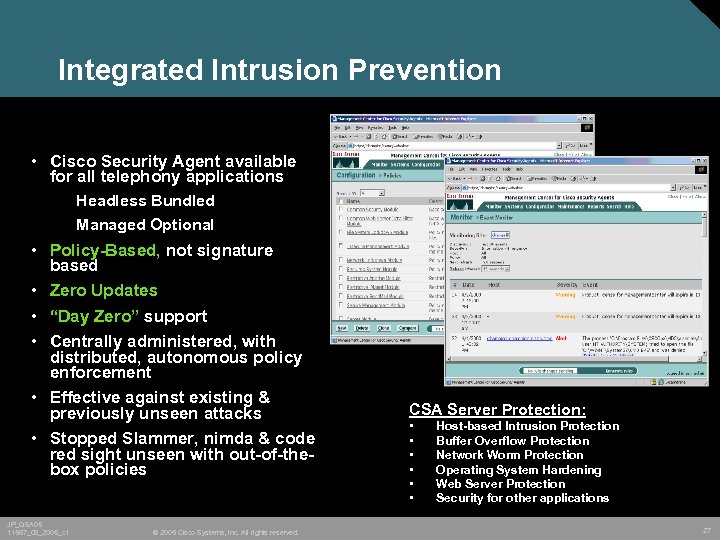 Integrated Intrusion Prevention • Cisco Security Agent available for all telephony applications Headless Bundled Managed Optional • Policy-Based, not signature based • Zero Updates • “Day Zero” support • Centrally administered, with distributed, autonomous policy enforcement • Effective against existing & previously unseen attacks • Stopped Slammer, nimda & code red sight unseen with out-of-thebox policies JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. CSA Server Protection: • • • Host-based Intrusion Protection Buffer Overflow Protection Network Worm Protection Operating System Hardening Web Server Protection Security for other applications 27
Integrated Intrusion Prevention • Cisco Security Agent available for all telephony applications Headless Bundled Managed Optional • Policy-Based, not signature based • Zero Updates • “Day Zero” support • Centrally administered, with distributed, autonomous policy enforcement • Effective against existing & previously unseen attacks • Stopped Slammer, nimda & code red sight unseen with out-of-thebox policies JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. CSA Server Protection: • • • Host-based Intrusion Protection Buffer Overflow Protection Network Worm Protection Operating System Hardening Web Server Protection Security for other applications 27
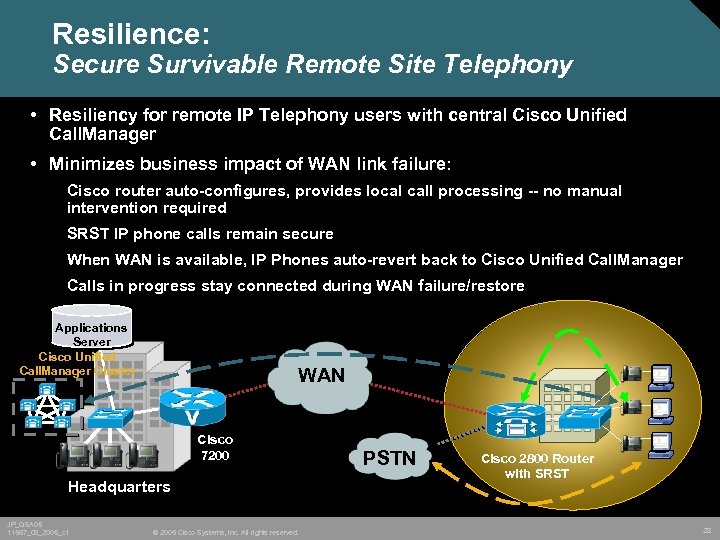 Resilience: Secure Survivable Remote Site Telephony • Resiliency for remote IP Telephony users with central Cisco Unified Call. Manager • Minimizes business impact of WAN link failure: Cisco router auto-configures, provides local call processing -- no manual intervention required SRST IP phone calls remain secure When WAN is available, IP Phones auto-revert back to Cisco Unified Call. Manager Calls in progress stay connected during WAN failure/restore Applications Server Cisco Unified Call. Manager Cluster X WAN A Cisco 7200 Headquarters JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. PSTN Cisco 2800 Router with SRST 28
Resilience: Secure Survivable Remote Site Telephony • Resiliency for remote IP Telephony users with central Cisco Unified Call. Manager • Minimizes business impact of WAN link failure: Cisco router auto-configures, provides local call processing -- no manual intervention required SRST IP phone calls remain secure When WAN is available, IP Phones auto-revert back to Cisco Unified Call. Manager Calls in progress stay connected during WAN failure/restore Applications Server Cisco Unified Call. Manager Cluster X WAN A Cisco 7200 Headquarters JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. PSTN Cisco 2800 Router with SRST 28
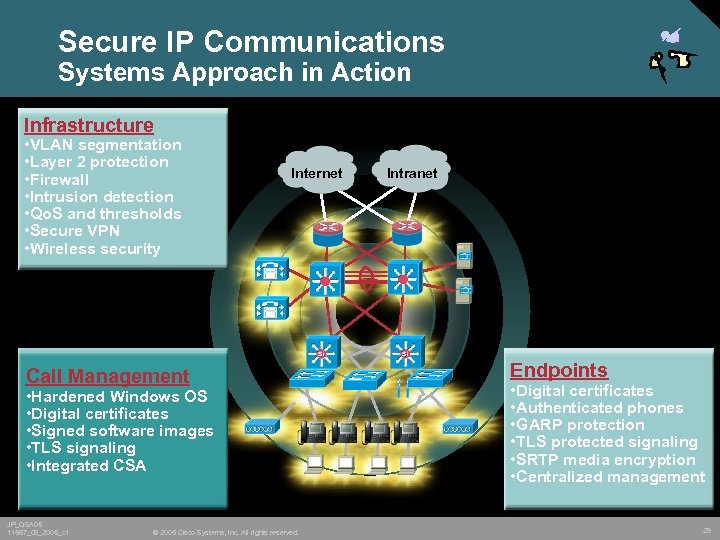 Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 29
Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 29
 Authenticated Endpoints • X. 509 v. 3 certificates in Cisco Unified IP Phones and Cisco Unified Call. Manager • Certificates ensure reliable device authentication • Scalable solution JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 30
Authenticated Endpoints • X. 509 v. 3 certificates in Cisco Unified IP Phones and Cisco Unified Call. Manager • Certificates ensure reliable device authentication • Scalable solution JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 30
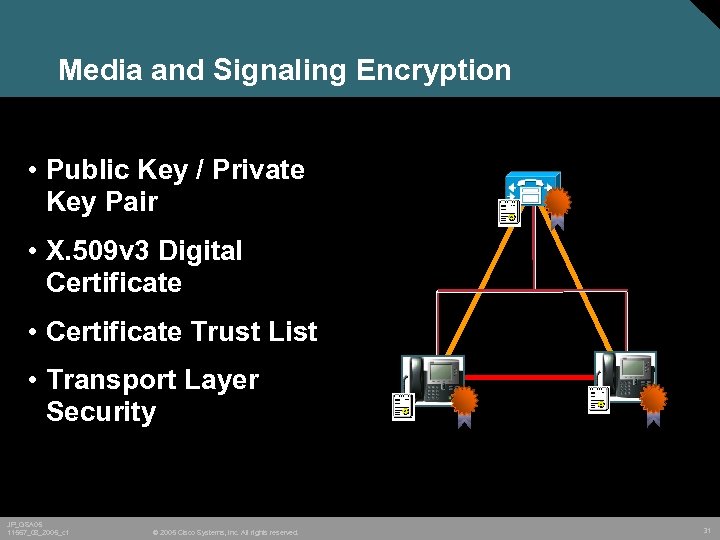 Media and Signaling Encryption • Public Key / Private Key Pair • X. 509 v 3 Digital Certificate • Certificate Trust List • Transport Layer Security JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 31
Media and Signaling Encryption • Public Key / Private Key Pair • X. 509 v 3 Digital Certificate • Certificate Trust List • Transport Layer Security JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 31
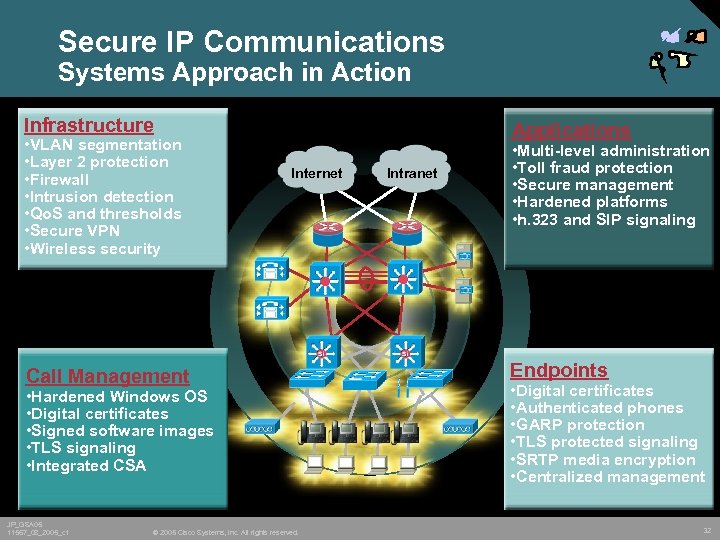 Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Applications Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet • Multi-level administration • Toll fraud protection • Secure management • Hardened platforms • h. 323 and SIP signaling Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 32
Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Applications Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet • Multi-level administration • Toll fraud protection • Secure management • Hardened platforms • h. 323 and SIP signaling Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 32
 Secure Private Messaging • Private Only intended recipients can listen to a private message addressed to them Messages marked private, if (accidentally or intentionally) forwarded, cannot be listened to Messages forwarded to internet email addresses or 3 rd party voice mail systems (VPIM/AMIS/Octel. Net) cannot be listened to • Secure Actual message content is protected using public-key encryption Unauthorized users will hear a warning message Can be set on a per subscriber (all messages from John Chambers) or system-wide (legal firms) basis JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 33
Secure Private Messaging • Private Only intended recipients can listen to a private message addressed to them Messages marked private, if (accidentally or intentionally) forwarded, cannot be listened to Messages forwarded to internet email addresses or 3 rd party voice mail systems (VPIM/AMIS/Octel. Net) cannot be listened to • Secure Actual message content is protected using public-key encryption Unauthorized users will hear a warning message Can be set on a per subscriber (all messages from John Chambers) or system-wide (legal firms) basis JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 33
 Application Platform Protection • Carefully hardened platforms • Control access to admin functions • Cisco Security Agent host-based protection • Secure remote management via https JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 34
Application Platform Protection • Carefully hardened platforms • Control access to admin functions • Cisco Security Agent host-based protection • Secure remote management via https JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 34
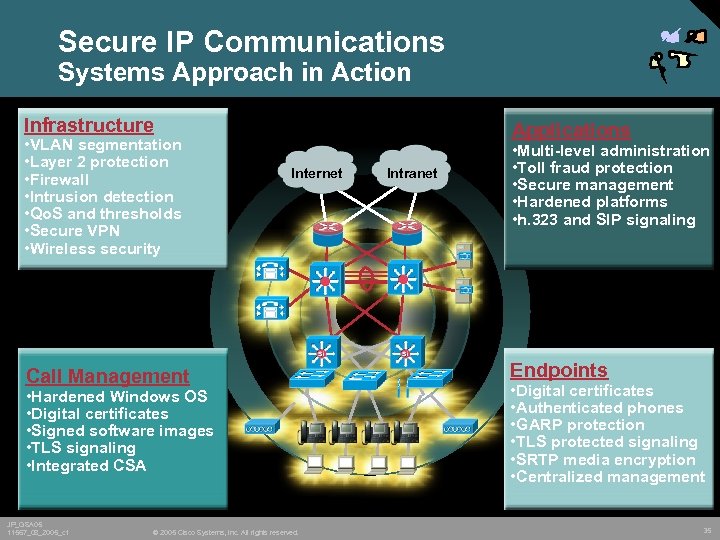 Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Applications Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet • Multi-level administration • Toll fraud protection • Secure management • Hardened platforms • h. 323 and SIP signaling Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 35
Secure IP Communications Systems Approach in Action Infrastructure • VLAN segmentation • Layer 2 protection • Firewall • Intrusion detection • Qo. S and thresholds • Secure VPN • Wireless security Applications Internet Call Management • Hardened Windows OS • Digital certificates • Signed software images • TLS signaling • Integrated CSA JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. Intranet • Multi-level administration • Toll fraud protection • Secure management • Hardened platforms • h. 323 and SIP signaling Endpoints • Digital certificates • Authenticated phones • GARP protection • TLS protected signaling • SRTP media encryption • Centralized management 35
 Cisco – Independently Recognized as the Secure IP Communications Solution • Cisco is the only vendor to earn Miercom/Network World’s highest security rating—May 2004 • BCR – Most secure Large IP-PBX, January, 2005 • BCR – Most secure Mid-Size IPPBX, February, 2005 • Only fully IP-PBX system to achieve Do. D PBX-1 certification 2005 Most Secure IP-PBX Large-Size Most Secure Mid. Size IP-PBX Do. D JITC PBX 1 Certification JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 36
Cisco – Independently Recognized as the Secure IP Communications Solution • Cisco is the only vendor to earn Miercom/Network World’s highest security rating—May 2004 • BCR – Most secure Large IP-PBX, January, 2005 • BCR – Most secure Mid-Size IPPBX, February, 2005 • Only fully IP-PBX system to achieve Do. D PBX-1 certification 2005 Most Secure IP-PBX Large-Size Most Secure Mid. Size IP-PBX Do. D JITC PBX 1 Certification JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 36
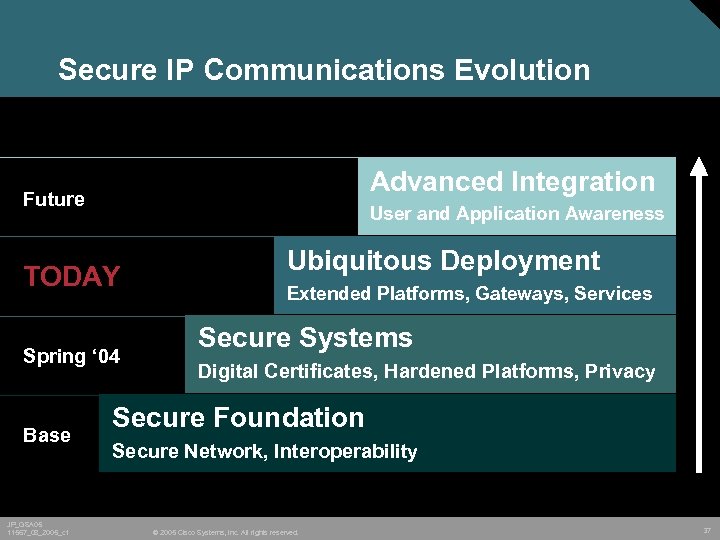 Secure IP Communications Evolution Advanced Integration Future User and Application Awareness TODAY Spring ‘ 04 Base JP_GSA 05 11567_08_2005_c 1 Ubiquitous Deployment Extended Platforms, Gateways, Services Secure Systems Digital Certificates, Hardened Platforms, Privacy Secure Foundation Secure Network, Interoperability © 2005 Cisco Systems, Inc. All rights reserved. 37
Secure IP Communications Evolution Advanced Integration Future User and Application Awareness TODAY Spring ‘ 04 Base JP_GSA 05 11567_08_2005_c 1 Ubiquitous Deployment Extended Platforms, Gateways, Services Secure Systems Digital Certificates, Hardened Platforms, Privacy Secure Foundation Secure Network, Interoperability © 2005 Cisco Systems, Inc. All rights reserved. 37
 Cisco Self-Defending Network Integrated, Collaborative, Adaptive Helping Our Customers Make the Journey From Point Solutions to Proactive, End-to-End Security ENABLING BUSINESS-DRIVEN SECURITY PRACTICES RISK GAPS ARE REDUCED, COMPLEXITY IS REDUCED, TOTAL COST OF OWNERSHIP IS LOWER PROTECT, OPTIMIZE, AND GROW YOUR BUSINESS JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 38
Cisco Self-Defending Network Integrated, Collaborative, Adaptive Helping Our Customers Make the Journey From Point Solutions to Proactive, End-to-End Security ENABLING BUSINESS-DRIVEN SECURITY PRACTICES RISK GAPS ARE REDUCED, COMPLEXITY IS REDUCED, TOTAL COST OF OWNERSHIP IS LOWER PROTECT, OPTIMIZE, AND GROW YOUR BUSINESS JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 38
 Resources • Cisco. com/go/security • Cisco. com/go/ipcsecurity • Cisco. com/go/netpro JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 39
Resources • Cisco. com/go/security • Cisco. com/go/ipcsecurity • Cisco. com/go/netpro JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 39
 JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 40
JP_GSA 05 11567_08_2005_c 1 © 2005 Cisco Systems, Inc. All rights reserved. 40


