34a25671f238bd325b1ff941c902ea40.ppt
- Количество слайдов: 41
 Making Digital Security a Reality With PKI Nicholas A. Davis, UW-Madison November 28, 2006
Making Digital Security a Reality With PKI Nicholas A. Davis, UW-Madison November 28, 2006
 Overview • • • PKI 101 – Intro to digital certificates History of PKI at UW-Madison IT environment Why UW-Madison is interested in PKI cost and model comparison What it all actually looks like in reality Our experience so far and our future plans Universal truths What we have learned Final thoughts How to get started today! Questions
Overview • • • PKI 101 – Intro to digital certificates History of PKI at UW-Madison IT environment Why UW-Madison is interested in PKI cost and model comparison What it all actually looks like in reality Our experience so far and our future plans Universal truths What we have learned Final thoughts How to get started today! Questions
 Public Key Infrastructure (PKI) 101 • PKI = System to manage digital certificates • Digital Passport • Digital key to unlock encrypted Data • Digital pen to sign
Public Key Infrastructure (PKI) 101 • PKI = System to manage digital certificates • Digital Passport • Digital key to unlock encrypted Data • Digital pen to sign
 PKI 101 (Continued) • Digitally sign Microsoft Office documents, spreadsheets, email, PDF files, etc. • Encrypt email in transit and storage, end to end • Authenticate with a much stronger credential than username & password
PKI 101 (Continued) • Digitally sign Microsoft Office documents, spreadsheets, email, PDF files, etc. • Encrypt email in transit and storage, end to end • Authenticate with a much stronger credential than username & password
 History of PKI at UWMadison • October 2000 – UW-Madison and Dartmouth get together • June 2004 – Requirements gathering • May 2005 – Geotrust selected
History of PKI at UWMadison • October 2000 – UW-Madison and Dartmouth get together • June 2004 – Requirements gathering • May 2005 – Geotrust selected
 UW-Madison IT Landcscape • • Faculty, Staff, Students Highly decentralized Public institution Research driven environment
UW-Madison IT Landcscape • • Faculty, Staff, Students Highly decentralized Public institution Research driven environment
 Communities Served by UWMadison Auth. NZ It’s Not Just About Us Anymore
Communities Served by UWMadison Auth. NZ It’s Not Just About Us Anymore
 Why the UW-Madison is interested in digital security solutions • Threat of identity theft (Authentication) – Alice and Bob story • More university businesses conducted via the Internet (encryption) • Non-repudiation (signing)
Why the UW-Madison is interested in digital security solutions • Threat of identity theft (Authentication) – Alice and Bob story • More university businesses conducted via the Internet (encryption) • Non-repudiation (signing)
 Up Front Development Costs • Gartner Group estimates that the average commercial PKI system costs $1 million to implement • 80% of PKI systems never get beyond “pilot” status • Our estimated first year costs are substantially less than this
Up Front Development Costs • Gartner Group estimates that the average commercial PKI system costs $1 million to implement • 80% of PKI systems never get beyond “pilot” status • Our estimated first year costs are substantially less than this
 PKI Models Under Consideration • In-House Commercial • In-House Open Source • Co-managed
PKI Models Under Consideration • In-House Commercial • In-House Open Source • Co-managed
 Time to Implement • Feature Set • Cost of establishing sandbox, QA and production environments • Hardware acquisition • CP and CPS statements • Open Source, 12 months • In-House Commercial, 9 months • Co-Managed Commercial, 1 month
Time to Implement • Feature Set • Cost of establishing sandbox, QA and production environments • Hardware acquisition • CP and CPS statements • Open Source, 12 months • In-House Commercial, 9 months • Co-Managed Commercial, 1 month
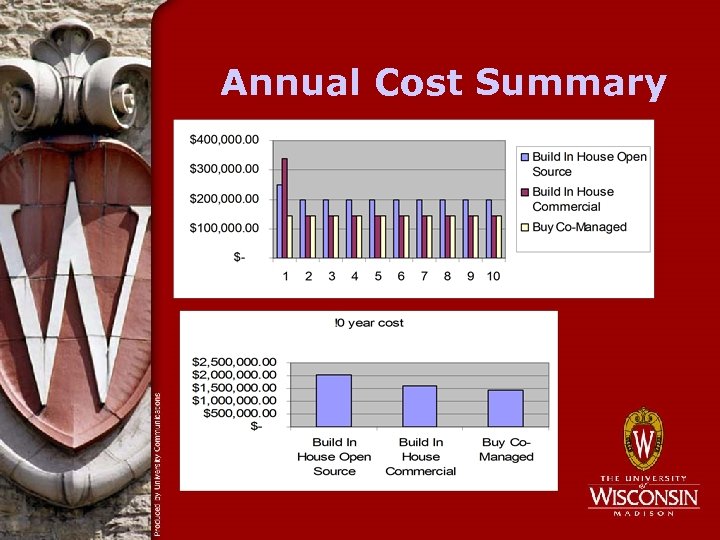 Annual Cost Summary
Annual Cost Summary
 Geotrust Selected as UW -Madison PKI • Lower upfront fixed costs • Lower 10 year costs • Faster road to implementation • Trusted Root • Off Site Key Escrow • Automated certificate delivery • UW-Madison common look and feel • No long term lock in
Geotrust Selected as UW -Madison PKI • Lower upfront fixed costs • Lower 10 year costs • Faster road to implementation • Trusted Root • Off Site Key Escrow • Automated certificate delivery • UW-Madison common look and feel • No long term lock in
 No Trusted Root With Open Source Unsigned Root means distrust both within and outside our core universe
No Trusted Root With Open Source Unsigned Root means distrust both within and outside our core universe
 Certificate Storage • Aladdin Etoken • USB based for ease of integration • Excellent customer support • Enhanced platform support
Certificate Storage • Aladdin Etoken • USB based for ease of integration • Excellent customer support • Enhanced platform support
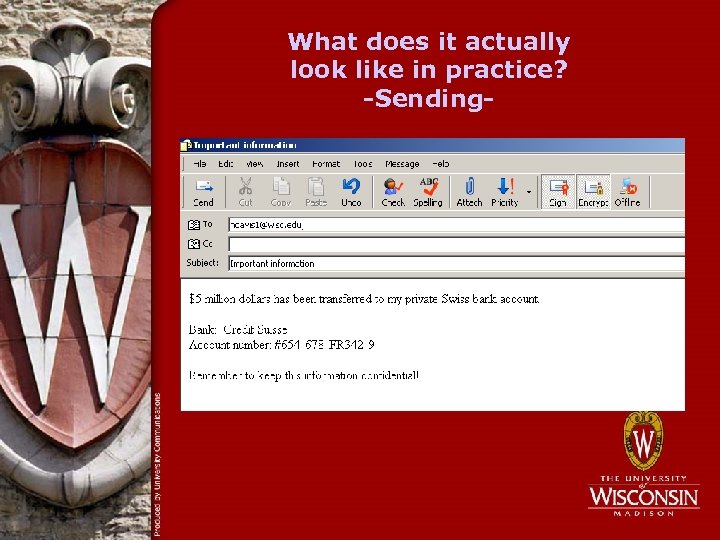 What does it actually look like in practice? -Sending-
What does it actually look like in practice? -Sending-
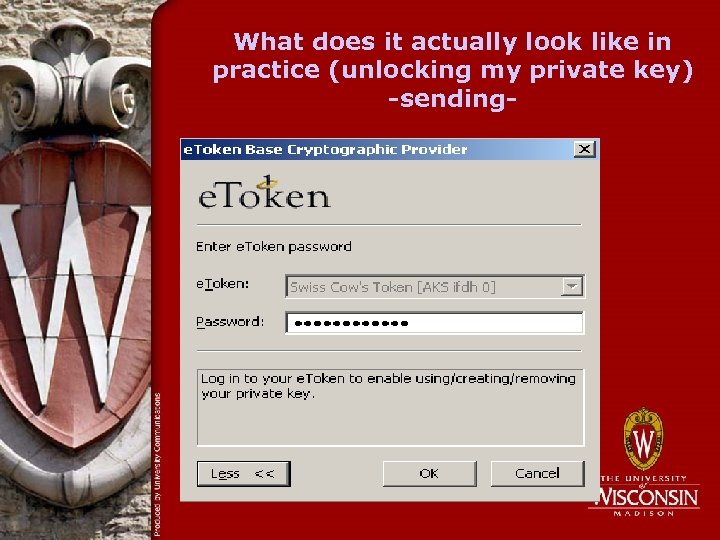 What does it actually look like in practice (unlocking my private key) -sending-
What does it actually look like in practice (unlocking my private key) -sending-
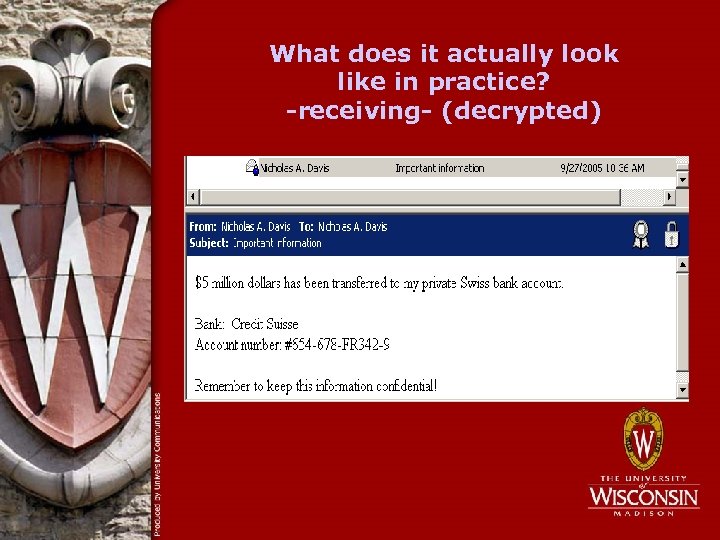 What does it actually look like in practice? -receiving- (decrypted)
What does it actually look like in practice? -receiving- (decrypted)
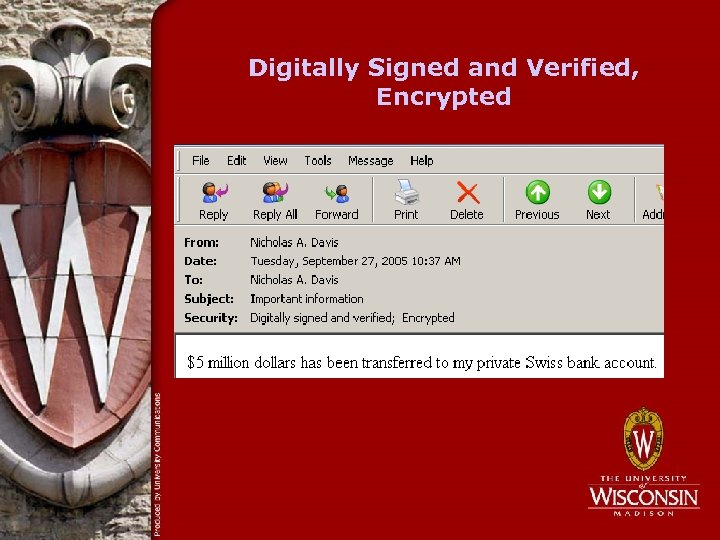 Digitally Signed and Verified, Encrypted
Digitally Signed and Verified, Encrypted
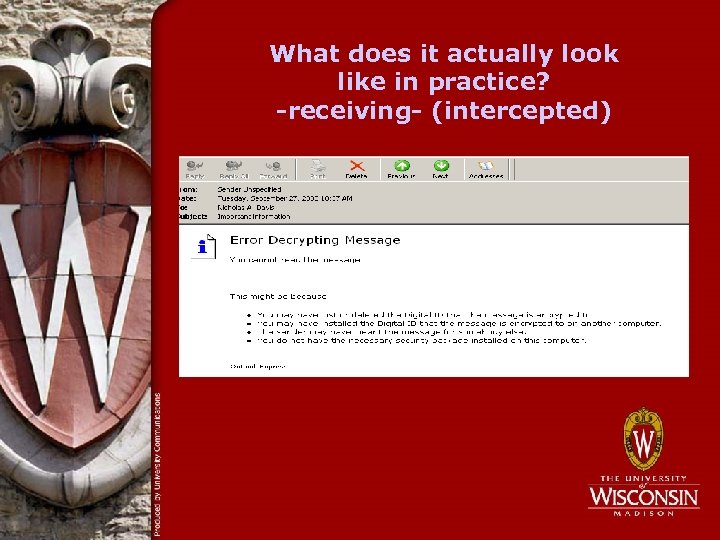 What does it actually look like in practice? -receiving- (intercepted)
What does it actually look like in practice? -receiving- (intercepted)
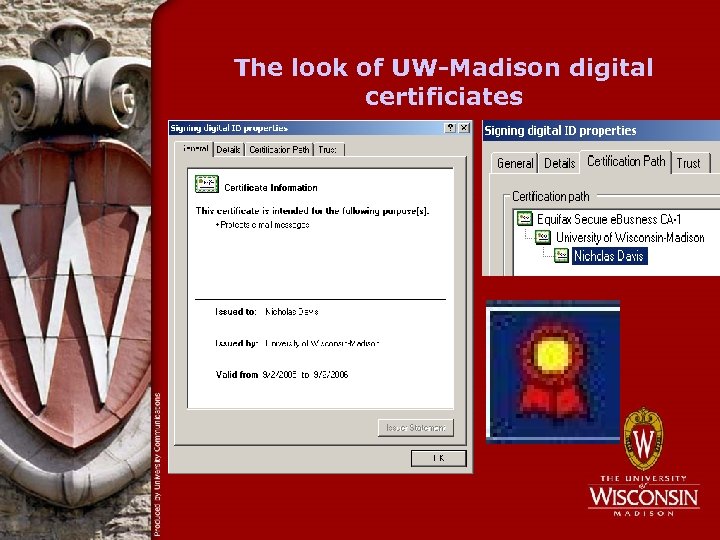 The look of UW-Madison digital certificiates
The look of UW-Madison digital certificiates
 Feature Set Trusted Root Seamless trust let’s us play globally via the Equifax Secure e. Business CA 1
Feature Set Trusted Root Seamless trust let’s us play globally via the Equifax Secure e. Business CA 1
 Feature Set Key Escrow Is Big Brother watching? Who do the keys belong to anyway?
Feature Set Key Escrow Is Big Brother watching? Who do the keys belong to anyway?
 Feature Set – Distance Users – Co-Managed All the user needs is a web browser in order to get their certificate
Feature Set – Distance Users – Co-Managed All the user needs is a web browser in order to get their certificate
 Our Experience So Far Customers appreciate: • Automated certificate delivery • Trusted Root • Key Escrow Uses: • Using certificates for digital signing • Using certificates for encrypted email • Digital signing of mass email to campus
Our Experience So Far Customers appreciate: • Automated certificate delivery • Trusted Root • Key Escrow Uses: • Using certificates for digital signing • Using certificates for encrypted email • Digital signing of mass email to campus
 So Now What? • Digital certificate management model proven • Low hanging digital fruit has been harvested • Is it time for me to retire?
So Now What? • Digital certificate management model proven • Low hanging digital fruit has been harvested • Is it time for me to retire?
 Leveraging Our Existing System • The UW-Madison PKI is in place today for signing and encryption • Encourage others to change their way of doing business • Integration with our current Web ISO for authentication
Leveraging Our Existing System • The UW-Madison PKI is in place today for signing and encryption • Encourage others to change their way of doing business • Integration with our current Web ISO for authentication
 Example of Business Process Change • UW-Madison Police and Security • Building access: New centralized system • Same historically weak business processes • FERPA issues • PKI to the rescue! • 110 new users
Example of Business Process Change • UW-Madison Police and Security • Building access: New centralized system • Same historically weak business processes • FERPA issues • PKI to the rescue! • 110 new users
 Universal Truths • People are not interested in vaporware to solve their problems • Administrative controls don’t work • If you don’t trust anyone, nobody will trust you. You have to play by the rules, even if you don’t like them
Universal Truths • People are not interested in vaporware to solve their problems • Administrative controls don’t work • If you don’t trust anyone, nobody will trust you. You have to play by the rules, even if you don’t like them
 The Secret is Evolution, Not Revolutions are bloody! Evolution lets you gain immediate benefit today while planning for a better tomorrow without throwing away all your current systems
The Secret is Evolution, Not Revolutions are bloody! Evolution lets you gain immediate benefit today while planning for a better tomorrow without throwing away all your current systems
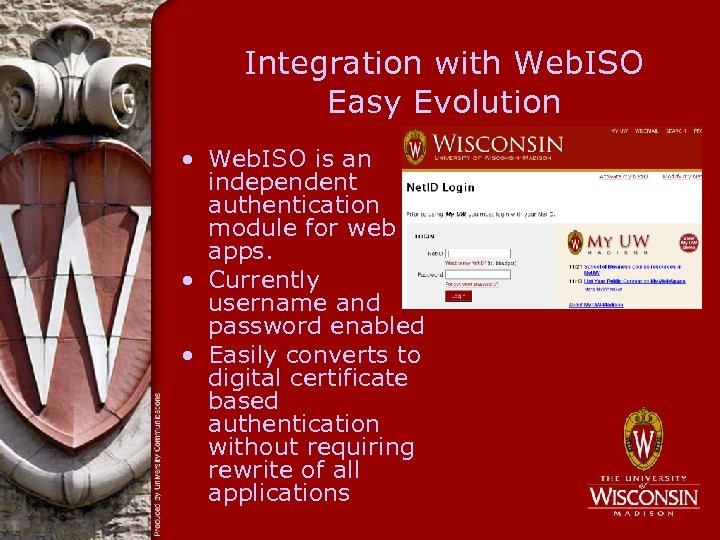 Integration with Web. ISO Easy Evolution • Web. ISO is an independent authentication module for web apps. • Currently username and password enabled • Easily converts to digital certificate based authentication without requiring rewrite of all applications
Integration with Web. ISO Easy Evolution • Web. ISO is an independent authentication module for web apps. • Currently username and password enabled • Easily converts to digital certificate based authentication without requiring rewrite of all applications
 But What About Secur. ID? • Secur. ID = One Time Password authentication device (OTP) • Great for authentication! • What else does it do? • Cost! • Vendor Lock-in! • Good point solution, but hardly forward thinking
But What About Secur. ID? • Secur. ID = One Time Password authentication device (OTP) • Great for authentication! • What else does it do? • Cost! • Vendor Lock-in! • Good point solution, but hardly forward thinking
 Critical Success factors for the UW-Madison • A focus on the customer requirements is of pinnacle importance • Financial lifecycle modeling for both short and long term • Being careful not to reinvent the wheel simply for the sake of pride • Top down support from the CIO’s office
Critical Success factors for the UW-Madison • A focus on the customer requirements is of pinnacle importance • Financial lifecycle modeling for both short and long term • Being careful not to reinvent the wheel simply for the sake of pride • Top down support from the CIO’s office
 What We Have Learned • A certificate is a certificate • What matters most is what your organization does with the certificate once it is issued • The challenge of implementing PKI is 30% technical and 70% user education, marketing and acceptance
What We Have Learned • A certificate is a certificate • What matters most is what your organization does with the certificate once it is issued • The challenge of implementing PKI is 30% technical and 70% user education, marketing and acceptance
 Final Thoughts • The key to success in a decentralized environment lies in motivating your users, not obligating your users • Whether you choose to build or buy, remember to keep it simple for the customers • Don’t spend time on duplication of effort
Final Thoughts • The key to success in a decentralized environment lies in motivating your users, not obligating your users • Whether you choose to build or buy, remember to keep it simple for the customers • Don’t spend time on duplication of effort
 “But We Are Different…. . ” • We all like to think we are different • Setup a content filtering device with 100 keywords on your outgoing email • Let me know what you discover • Ignorance is not an excuse for weak security practices
“But We Are Different…. . ” • We all like to think we are different • Setup a content filtering device with 100 keywords on your outgoing email • Let me know what you discover • Ignorance is not an excuse for weak security practices
 Audience Question How is PKI similar to a Telephone network? The value of the system is proportional to the number of people who have a phone or a digital certificate!
Audience Question How is PKI similar to a Telephone network? The value of the system is proportional to the number of people who have a phone or a digital certificate!
 “It can happen to you, it can happen to me, it can happen to everyone eventually…. . ”
“It can happen to you, it can happen to me, it can happen to everyone eventually…. . ”
 The First Taste is Free! Download a FREE email digitial certificate www. ascertia. com www. thawte. com Perform inter-institutional testing with your organization and UW-Madison! Digital certificates are inherently supported in: Outlook, Outlook Express, Thunderbird, Mail. app, Mulberry, Eudora 7. 0
The First Taste is Free! Download a FREE email digitial certificate www. ascertia. com www. thawte. com Perform inter-institutional testing with your organization and UW-Madison! Digital certificates are inherently supported in: Outlook, Outlook Express, Thunderbird, Mail. app, Mulberry, Eudora 7. 0
 Questions and Comments Nicholas Davis PKI Project Leader UW-Madison ndavis 1@wisc. edu 608 -262 -3837 www. doit. wisc. edu/middleware/pki PLEASE PARTNER WITH US AS WE MOVE FORWARD WITH PKI! -----BEGIN CERTIFICATE----MIIDLj. CCApeg. Aw. IBAg. ICAdkw. DQYJKo. ZIhvc. NAQEFBQAwg. Ykx. Cz. AJBg. NVBAYTAl. VT MSsw. KQYDVQQKEy. JEa. XZpc 2 lvbi. Bv. Zi. BJbm. Zvcm 1 hd. Glvbi. BUZWNobm 9 sb 2 d 5 MSMw IQYDVQQLExp. GYWN 1 b. HR 5 IC 0 g. U 3 Rh. Zm. Yg. LSBTd. HVk. ZW 50 cz. Eo. MCYGA 1 UEAx. Mf. VW 5 p dm. Vyc 2 l 0 e. SBv. Zi. BXa. XNjb 25 za. W 4 t. TWFka. XNvbj. Ae. Fw 0 w. Nj. A 5 MDYx. Nj. Uz. Mj. Ja. Fw 0 w Nz. A 5 MDYx. Nj. Uz. Mj. Ja. MIG 8 MQsw. CQYDVQQGEw. JVUz. ESMBAGA 1 UECBMJV 2 lz. Y 29 uc 2 lu MRAw. Dg. YDVQQHEwd. NYWRpc 29 u. MSgw. Jg. YDVQQKEx 9 Vbml 2 ZXJza. XR 5 IG 9 m. IFdpc 2 Nv bn. Npbi 1 NYWRpc 29 u. MSMw. IQYDVQQLExp. GYWN 1 b. HR 5 IC 0 g. U 3 Rh. Zm. Yg. LSBTd. HVk. ZW 50 cz. EXMBUGA 1 UEAx. MOTmlja. G 9 s. YXMg. RGF 2 a. XMx. Hz. Ad. Bgkqhki. G 9 w 0 BCQEWEG 5 k. YXZp cz. FAd 2 lz. Yy 5 l. ZHUwg. Z 8 w. DQYJKo. ZIhvc. NAQEBBQADg. Y 0 AMIGJAo. GBAJECUO 2/k. Nde rq 9 BXL 9 c 60 k 7 gl. XKSil. VTS 2 h. Wf. I 7 OVr. VVVp. Sd. OOVwd 2 dj. Z 4 Efuu. JTmvw. MRWdn. U 3 h 124 g. FZWO+Li. Dh. Lx+i. LC 1 b. Cw. Vbv. UJPyfj. Viq. XMo. Kg. UNx 7 NStt 6 Ylntqxv. Nfz. W 5 Lxq NQ 2 VCu 23 AFqczm. Gxv. X 27 M 2 Vt. SPg 1 o. CWf. Ag. MBAAGjc. DBu. MA 4 GA 1 Ud. Dw. EB/w. QEAw. IF 4 DA 7 Bg. NVHR 8 ENDAy. MDCg. Lq. Ashipod. HRw. Oi 8 v. Y 3 Js. Lmdlb 3 Ryd. XN 0 Lm. Nvb. S 9 jcmxz L 3 dpc 2 Nvbn. Npbi 5 jcmww. Hw. YDVR 0 j. BBgw. Fo. AUHJ 5 SUhs. EYkcsayw. Bu. Gnxq. Tcs. Iy. Qw DQYJKo. ZIhvc. NAQEFBQADg. YEADgrw. XFZy. VWce. Ihbro 0 l. R 2 Nfdwqbk. Y 1 p 1 ywr 9 v 8 lf JGUf. Z 0 sc. Axa. Nfdfk. XMHJv. MK 7 MZCQ 65 v. XEO 9 Yw. TFAfug. XK+AAFot 0 Hh. Nv. WMwv. BLq. X c. YKps+A 5 VU 9 Jnh. NAKZJRIImi. GCKjz 2 e+ZARm 6 fj. Txhe. W 5 q. Jy. Jq 30 sbwuk. G/tsb. XT jnw= -----END CERTIFICATE-----
Questions and Comments Nicholas Davis PKI Project Leader UW-Madison ndavis 1@wisc. edu 608 -262 -3837 www. doit. wisc. edu/middleware/pki PLEASE PARTNER WITH US AS WE MOVE FORWARD WITH PKI! -----BEGIN CERTIFICATE----MIIDLj. CCApeg. Aw. IBAg. ICAdkw. DQYJKo. ZIhvc. NAQEFBQAwg. Ykx. Cz. AJBg. NVBAYTAl. VT MSsw. KQYDVQQKEy. JEa. XZpc 2 lvbi. Bv. Zi. BJbm. Zvcm 1 hd. Glvbi. BUZWNobm 9 sb 2 d 5 MSMw IQYDVQQLExp. GYWN 1 b. HR 5 IC 0 g. U 3 Rh. Zm. Yg. LSBTd. HVk. ZW 50 cz. Eo. MCYGA 1 UEAx. Mf. VW 5 p dm. Vyc 2 l 0 e. SBv. Zi. BXa. XNjb 25 za. W 4 t. TWFka. XNvbj. Ae. Fw 0 w. Nj. A 5 MDYx. Nj. Uz. Mj. Ja. Fw 0 w Nz. A 5 MDYx. Nj. Uz. Mj. Ja. MIG 8 MQsw. CQYDVQQGEw. JVUz. ESMBAGA 1 UECBMJV 2 lz. Y 29 uc 2 lu MRAw. Dg. YDVQQHEwd. NYWRpc 29 u. MSgw. Jg. YDVQQKEx 9 Vbml 2 ZXJza. XR 5 IG 9 m. IFdpc 2 Nv bn. Npbi 1 NYWRpc 29 u. MSMw. IQYDVQQLExp. GYWN 1 b. HR 5 IC 0 g. U 3 Rh. Zm. Yg. LSBTd. HVk. ZW 50 cz. EXMBUGA 1 UEAx. MOTmlja. G 9 s. YXMg. RGF 2 a. XMx. Hz. Ad. Bgkqhki. G 9 w 0 BCQEWEG 5 k. YXZp cz. FAd 2 lz. Yy 5 l. ZHUwg. Z 8 w. DQYJKo. ZIhvc. NAQEBBQADg. Y 0 AMIGJAo. GBAJECUO 2/k. Nde rq 9 BXL 9 c 60 k 7 gl. XKSil. VTS 2 h. Wf. I 7 OVr. VVVp. Sd. OOVwd 2 dj. Z 4 Efuu. JTmvw. MRWdn. U 3 h 124 g. FZWO+Li. Dh. Lx+i. LC 1 b. Cw. Vbv. UJPyfj. Viq. XMo. Kg. UNx 7 NStt 6 Ylntqxv. Nfz. W 5 Lxq NQ 2 VCu 23 AFqczm. Gxv. X 27 M 2 Vt. SPg 1 o. CWf. Ag. MBAAGjc. DBu. MA 4 GA 1 Ud. Dw. EB/w. QEAw. IF 4 DA 7 Bg. NVHR 8 ENDAy. MDCg. Lq. Ashipod. HRw. Oi 8 v. Y 3 Js. Lmdlb 3 Ryd. XN 0 Lm. Nvb. S 9 jcmxz L 3 dpc 2 Nvbn. Npbi 5 jcmww. Hw. YDVR 0 j. BBgw. Fo. AUHJ 5 SUhs. EYkcsayw. Bu. Gnxq. Tcs. Iy. Qw DQYJKo. ZIhvc. NAQEFBQADg. YEADgrw. XFZy. VWce. Ihbro 0 l. R 2 Nfdwqbk. Y 1 p 1 ywr 9 v 8 lf JGUf. Z 0 sc. Axa. Nfdfk. XMHJv. MK 7 MZCQ 65 v. XEO 9 Yw. TFAfug. XK+AAFot 0 Hh. Nv. WMwv. BLq. X c. YKps+A 5 VU 9 Jnh. NAKZJRIImi. GCKjz 2 e+ZARm 6 fj. Txhe. W 5 q. Jy. Jq 30 sbwuk. G/tsb. XT jnw= -----END CERTIFICATE-----



