8fa7a6f12df4140577ce528ccffdf6be.ppt
- Количество слайдов: 19
 Make Secure Information Sharing (SIS) Easy and an Reality C. Edward Chow, PI Osama Khaleel Bill Kretschmer Sponsored by TTO Proof of Concept grant
Make Secure Information Sharing (SIS) Easy and an Reality C. Edward Chow, PI Osama Khaleel Bill Kretschmer Sponsored by TTO Proof of Concept grant
 Agenda Status of the SIS “porting” project SIS 0. 2 Software Architecture. Technologies and Tools/Modules SIS 0. 2 prototype Demo of SIS 0. 2 prototype Discussion on what to do next. 6/26/2006 SIS 0. 2 2
Agenda Status of the SIS “porting” project SIS 0. 2 Software Architecture. Technologies and Tools/Modules SIS 0. 2 prototype Demo of SIS 0. 2 prototype Discussion on what to do next. 6/26/2006 SIS 0. 2 2
 What We Have Achieved Develop SIS on Windows Platform. Add new capability on policy management Follow XACML access control standard. Specify/Enforce policies for accessing secure web sites based on role info in attribute certificate For certificates management, develop tools for Create digital and attribute certificates Update/revoke roles by updating certificates in Active Directory Integrate these software modules and demonstrate features on a prototype. 6/26/2006 SIS 0. 2 3
What We Have Achieved Develop SIS on Windows Platform. Add new capability on policy management Follow XACML access control standard. Specify/Enforce policies for accessing secure web sites based on role info in attribute certificate For certificates management, develop tools for Create digital and attribute certificates Update/revoke roles by updating certificates in Active Directory Integrate these software modules and demonstrate features on a prototype. 6/26/2006 SIS 0. 2 3
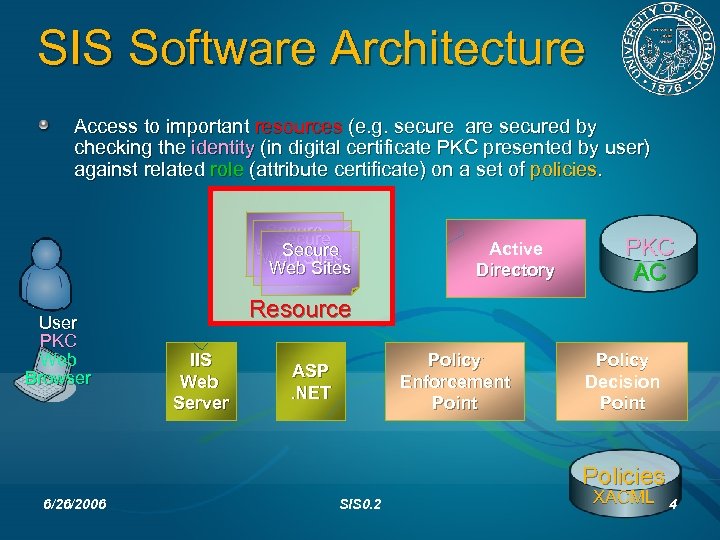 SIS Software Architecture Access to important resources (e. g. secure are secured by checking the identity (in digital certificate PKC presented by user) against related role (attribute certificate) on a set of policies. Secure Web Sites User PKC Web Browser Active Directory PKC AC Resource IIS Web Server Policy Enforcement Point ASP. NET Policy Decision Point Policies 6/26/2006 SIS 0. 2 XACML 4
SIS Software Architecture Access to important resources (e. g. secure are secured by checking the identity (in digital certificate PKC presented by user) against related role (attribute certificate) on a set of policies. Secure Web Sites User PKC Web Browser Active Directory PKC AC Resource IIS Web Server Policy Enforcement Point ASP. NET Policy Decision Point Policies 6/26/2006 SIS 0. 2 XACML 4
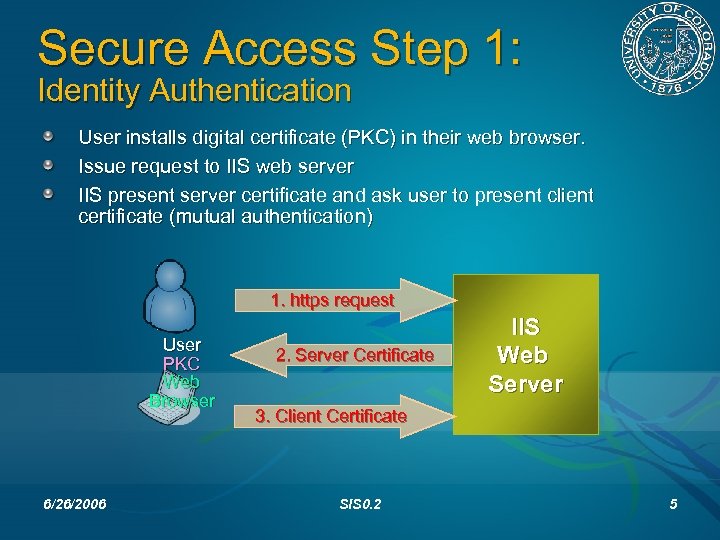 Secure Access Step 1: Identity Authentication User installs digital certificate (PKC) in their web browser. Issue request to IIS web server IIS present server certificate and ask user to present client certificate (mutual authentication) 1. https request User PKC Web Browser 6/26/2006 2. Server Certificate IIS Web Server 3. Client Certificate SIS 0. 2 5
Secure Access Step 1: Identity Authentication User installs digital certificate (PKC) in their web browser. Issue request to IIS web server IIS present server certificate and ask user to present client certificate (mutual authentication) 1. https request User PKC Web Browser 6/26/2006 2. Server Certificate IIS Web Server 3. Client Certificate SIS 0. 2 5
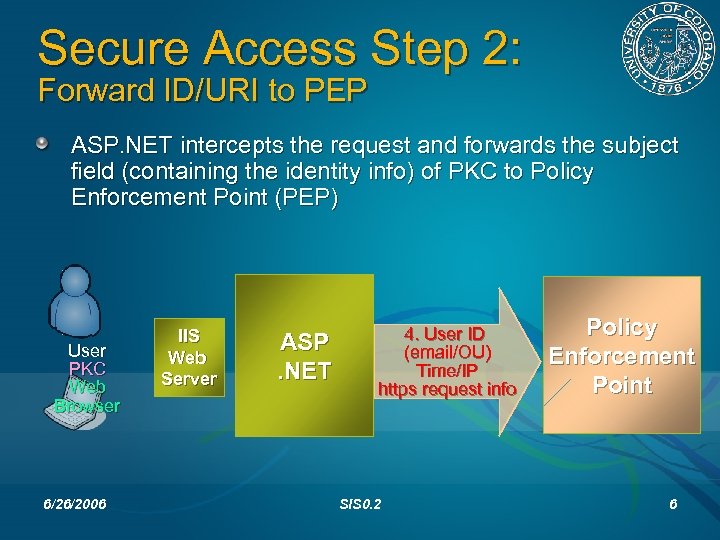 Secure Access Step 2: Forward ID/URI to PEP ASP. NET intercepts the request and forwards the subject field (containing the identity info) of PKC to Policy Enforcement Point (PEP) User PKC Web Browser 6/26/2006 IIS Web Server ASP. NET 4. User ID (email/OU) Time/IP https request info SIS 0. 2 Policy Enforcement Point 6
Secure Access Step 2: Forward ID/URI to PEP ASP. NET intercepts the request and forwards the subject field (containing the identity info) of PKC to Policy Enforcement Point (PEP) User PKC Web Browser 6/26/2006 IIS Web Server ASP. NET 4. User ID (email/OU) Time/IP https request info SIS 0. 2 Policy Enforcement Point 6
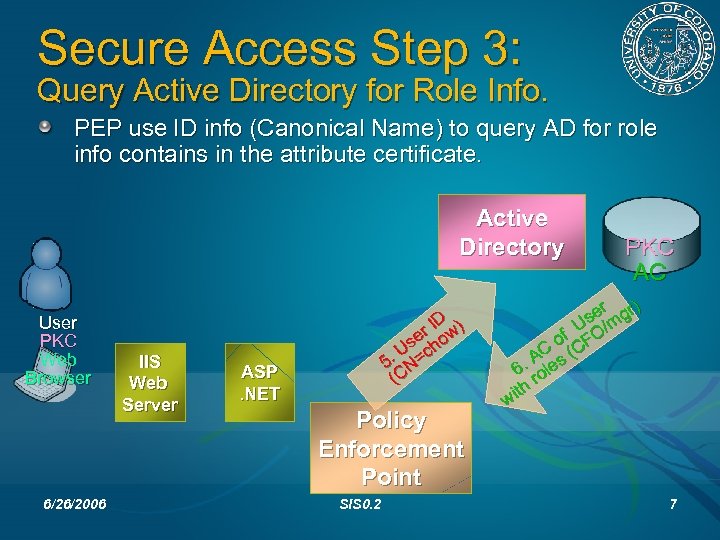 Secure Access Step 3: Query Active Directory for Role Info. PEP use ID info (Canonical Name) to query AD for role info contains in the attribute certificate. Active Directory User PKC Web Browser 6/26/2006 IIS Web Server D r I w) se ho U c 5. N= (C ASP. NET Policy Enforcement Point SIS 0. 2 PKC AC er gr) Us /m of CFO C (. A les 6 ro th wi 7
Secure Access Step 3: Query Active Directory for Role Info. PEP use ID info (Canonical Name) to query AD for role info contains in the attribute certificate. Active Directory User PKC Web Browser 6/26/2006 IIS Web Server D r I w) se ho U c 5. N= (C ASP. NET Policy Enforcement Point SIS 0. 2 PKC AC er gr) Us /m of CFO C (. A les 6 ro th wi 7
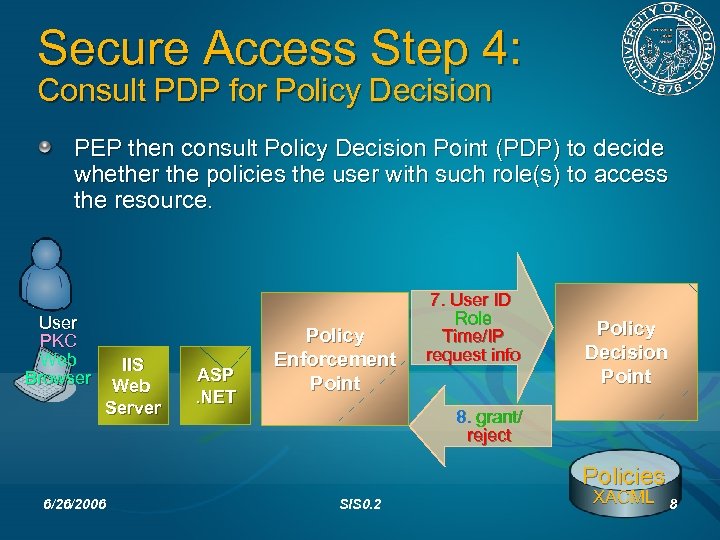 Secure Access Step 4: Consult PDP for Policy Decision PEP then consult Policy Decision Point (PDP) to decide whether the policies the user with such role(s) to access the resource. User PKC Web Browser IIS Web Server ASP. NET Policy Enforcement Point 7. User ID Role Time/IP request info Policy Decision Point 8. grant/ reject Policies 6/26/2006 SIS 0. 2 XACML 8
Secure Access Step 4: Consult PDP for Policy Decision PEP then consult Policy Decision Point (PDP) to decide whether the policies the user with such role(s) to access the resource. User PKC Web Browser IIS Web Server ASP. NET Policy Enforcement Point 7. User ID Role Time/IP request info Policy Decision Point 8. grant/ reject Policies 6/26/2006 SIS 0. 2 XACML 8
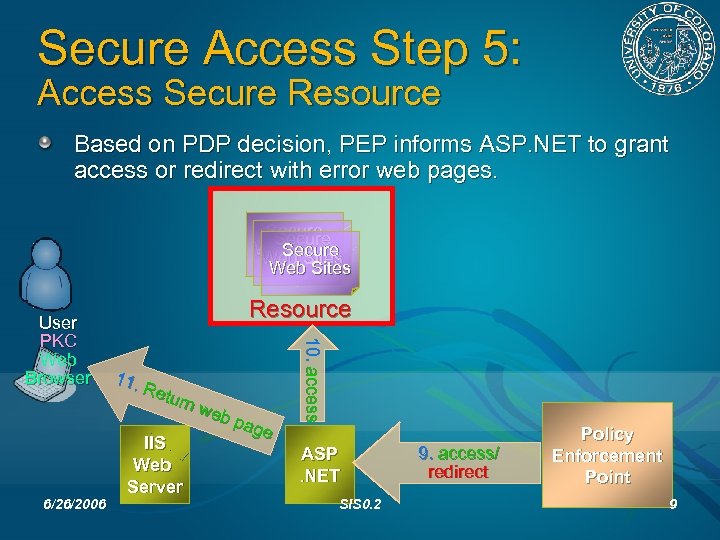 Secure Access Step 5: Access Secure Resource Based on PDP decision, PEP informs ASP. NET to grant access or redirect with error web pages. Secure Web Sites 6/26/2006 Resource 11. Ret urn web pag e IIS Web Server 10. access User PKC Web Browser ASP. NET SIS 0. 2 9. access/ redirect Policy Enforcement Point 9
Secure Access Step 5: Access Secure Resource Based on PDP decision, PEP informs ASP. NET to grant access or redirect with error web pages. Secure Web Sites 6/26/2006 Resource 11. Ret urn web pag e IIS Web Server 10. access User PKC Web Browser ASP. NET SIS 0. 2 9. access/ redirect Policy Enforcement Point 9
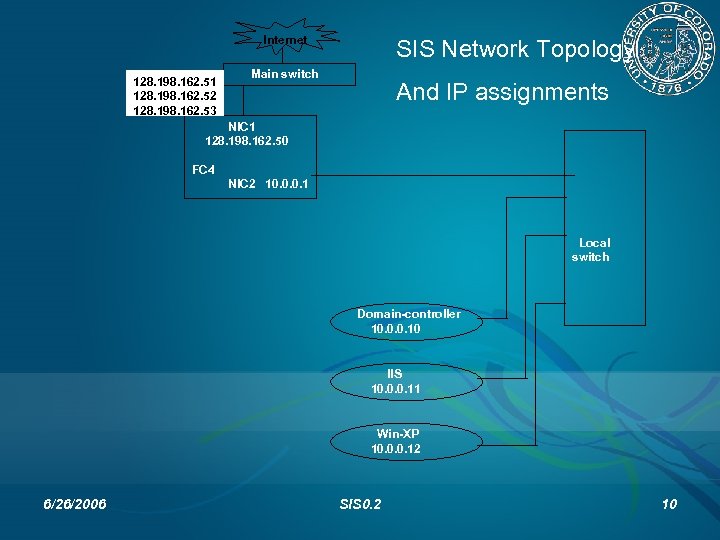 Internet 128. 198. 162. 51 128. 198. 162. 52 128. 198. 162. 53 SIS Network Topology Main switch And IP assignments NIC 1 128. 198. 162. 50 FC 4 NIC 2 10. 0. 0. 1 Local switch Domain-controller 10. 0. 0. 10 IIS 10. 0. 0. 11 Win-XP 10. 0. 0. 12 6/26/2006 SIS 0. 2 10
Internet 128. 198. 162. 51 128. 198. 162. 52 128. 198. 162. 53 SIS Network Topology Main switch And IP assignments NIC 1 128. 198. 162. 50 FC 4 NIC 2 10. 0. 0. 1 Local switch Domain-controller 10. 0. 0. 10 IIS 10. 0. 0. 11 Win-XP 10. 0. 0. 12 6/26/2006 SIS 0. 2 10
 The Testbed A 4 -machine testbed has been built. It contains the following: Windows server 2003 with AD (The Domain Controller). Windows server 2003 with IIS 6. 0 (The web server). Windows XP (a client). Fedora Core 4 with IPtables-based firewall (A Gateway). 6/26/2006 SIS 0. 2 11
The Testbed A 4 -machine testbed has been built. It contains the following: Windows server 2003 with AD (The Domain Controller). Windows server 2003 with IIS 6. 0 (The web server). Windows XP (a client). Fedora Core 4 with IPtables-based firewall (A Gateway). 6/26/2006 SIS 0. 2 11
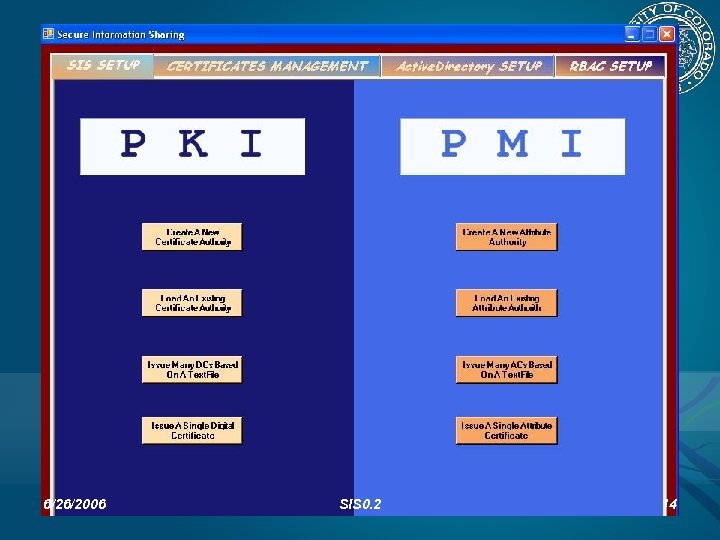
 The SIS Admin Tool An admin tool is being developed to provide an easy-to-use GUI for setting up the SIS environment. C# (C# Express 2005 IDE) has been used. The main three components that we have so far are: Public Key Infrastructure (PKI) setup. Privilege Management Infrastructure (PMI) setup. Certificates Management. 6/26/2006 SIS 0. 2 12
The SIS Admin Tool An admin tool is being developed to provide an easy-to-use GUI for setting up the SIS environment. C# (C# Express 2005 IDE) has been used. The main three components that we have so far are: Public Key Infrastructure (PKI) setup. Privilege Management Infrastructure (PMI) setup. Certificates Management. 6/26/2006 SIS 0. 2 12
 PKI PMI Features: Creating new Certificate Authorities (CAs). Loading an existing CAs. Issuing a single digital cert (DC) and storing it in the AD, based on a GUI form. Issuing a bunch of DCs and storing them in the AD, based on a simple text file. 6/26/2006 Features: Creating new Attribute Authorities (AAs). Loading an existing AA. Issuing a single attribute cert (AC) and storing it in the AD, based on a GUI form. Issuing a bunch of ACs and storing them in the AD, based on a simple text file. SIS 0. 2 13
PKI PMI Features: Creating new Certificate Authorities (CAs). Loading an existing CAs. Issuing a single digital cert (DC) and storing it in the AD, based on a GUI form. Issuing a bunch of DCs and storing them in the AD, based on a simple text file. 6/26/2006 Features: Creating new Attribute Authorities (AAs). Loading an existing AA. Issuing a single attribute cert (AC) and storing it in the AD, based on a GUI form. Issuing a bunch of ACs and storing them in the AD, based on a simple text file. SIS 0. 2 13
 6/26/2006 SIS 0. 2 14
6/26/2006 SIS 0. 2 14
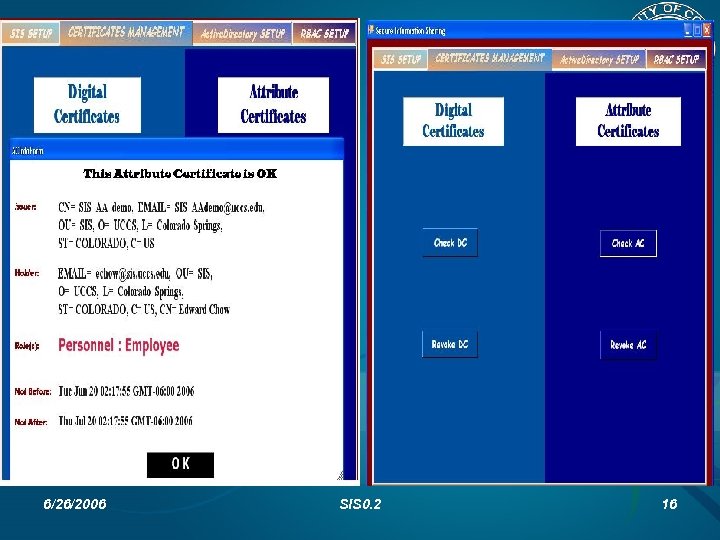
 Certificates Management Check & validate a digital certificate. Revoke a digital certificate. Check & validate an attribute certificate. Revoke an attribute certificate. 6/26/2006 SIS 0. 2 15
Certificates Management Check & validate a digital certificate. Revoke a digital certificate. Check & validate an attribute certificate. Revoke an attribute certificate. 6/26/2006 SIS 0. 2 15
 6/26/2006 SIS 0. 2 16
6/26/2006 SIS 0. 2 16
![Packages & techniques Open. SSL [http: //www. stunnel. org/download/binaries. html]: A wrapper compiled in Packages & techniques Open. SSL [http: //www. stunnel. org/download/binaries. html]: A wrapper compiled in](https://present5.com/presentation/8fa7a6f12df4140577ce528ccffdf6be/image-17.jpg) Packages & techniques Open. SSL [http: //www. stunnel. org/download/binaries. html]: A wrapper compiled in binaries (exe file) has been used to implement the PKI part. JCE-IAIK[http: //jce. iaik. tugraz. at/]: A set of java APIs and implementations of cryptographic functionality that has been used to implement the PMI part. IKVM. NET [http: //www. ikvm. net]: an implementation of Java for the Microsoft. NET Framework that has been used to allow us using the IAIK javabased package in the. NET. Crypt. Lib [http: //www. cs. auckland. ac. nz/~pgut 001/cryptlib/] or [http: //www. cryptlib. com]: a security toolkit that allows adding encryption and authentication services. * (We faced problems with it [files format & AC errors], therefore, we replaced it with the Open. SSL solution). XACML Open Source from Sun [http: //sunxacml. sourceforge. net]: Sun’s open source implementation of the OASIS XACML standard, written in the Java. TM programming language. 6/26/2006 SIS 0. 2 17
Packages & techniques Open. SSL [http: //www. stunnel. org/download/binaries. html]: A wrapper compiled in binaries (exe file) has been used to implement the PKI part. JCE-IAIK[http: //jce. iaik. tugraz. at/]: A set of java APIs and implementations of cryptographic functionality that has been used to implement the PMI part. IKVM. NET [http: //www. ikvm. net]: an implementation of Java for the Microsoft. NET Framework that has been used to allow us using the IAIK javabased package in the. NET. Crypt. Lib [http: //www. cs. auckland. ac. nz/~pgut 001/cryptlib/] or [http: //www. cryptlib. com]: a security toolkit that allows adding encryption and authentication services. * (We faced problems with it [files format & AC errors], therefore, we replaced it with the Open. SSL solution). XACML Open Source from Sun [http: //sunxacml. sourceforge. net]: Sun’s open source implementation of the OASIS XACML standard, written in the Java. TM programming language. 6/26/2006 SIS 0. 2 17
 Demo Secure web access based on role in attribute certificate Update AC when a person gets promoted Revoke AC when a person leaves the company PKC/AC management tool 6/26/2006 SIS 0. 2 18
Demo Secure web access based on role in attribute certificate Update AC when a person gets promoted Revoke AC when a person leaves the company PKC/AC management tool 6/26/2006 SIS 0. 2 18
 Discussion What are our next steps? 6/26/2006 SIS 0. 2 19
Discussion What are our next steps? 6/26/2006 SIS 0. 2 19


