241303aa9664611d38c637f181ba0b89.ppt
- Количество слайдов: 50
 Maintaining Access 1
Maintaining Access 1
 In This Chapter… q Trojans q Backdoors q Rootkits Maintaining Access 2
In This Chapter… q Trojans q Backdoors q Rootkits Maintaining Access 2
 Trojan Horses q The original Trojan Horse o Used by Greeks attacking Troy q Trojan rabbit o Monty Python and the Holy Grail q Modern trojan horse o Software that appears to be something that it is not --- hidden malicious function Maintaining Access 3
Trojan Horses q The original Trojan Horse o Used by Greeks attacking Troy q Trojan rabbit o Monty Python and the Holy Grail q Modern trojan horse o Software that appears to be something that it is not --- hidden malicious function Maintaining Access 3
 Trojan q Perhaps most common form of malware o Any “innocent” program can be a trojan q Example o Free DVD ripping software! o In reality, deleted content of hard drive q Trojan Maintaining Access could be much more clever… 4
Trojan q Perhaps most common form of malware o Any “innocent” program can be a trojan q Example o Free DVD ripping software! o In reality, deleted content of hard drive q Trojan Maintaining Access could be much more clever… 4
 Backdoors q “Alternative” access to machine o Front door: username and password o Backdoor: unauthorized access q Note: once backdoor is established, improved authentication is useless Maintaining Access 5
Backdoors q “Alternative” access to machine o Front door: username and password o Backdoor: unauthorized access q Note: once backdoor is established, improved authentication is useless Maintaining Access 5
 Backdoor q Suppose Trudy installs backdoor q What’s next? q Trudy likely to “harden” system o Fix vulnerabilities, apply patches, … Why? q “ 0 wned” system likely more “secure” q Trudy may use strong authentication! Maintaining Access 6
Backdoor q Suppose Trudy installs backdoor q What’s next? q Trudy likely to “harden” system o Fix vulnerabilities, apply patches, … Why? q “ 0 wned” system likely more “secure” q Trudy may use strong authentication! Maintaining Access 6
 Netcat Backdoor q Install Netcat listener o Must compile Netcat with its GAPING_SECURITY_HOLE option q In UNIX: nc victim_machine 12345 o Starts Netcat in client mode with listener on TCP port 12345 o No authentication required of attacker Maintaining Access 7
Netcat Backdoor q Install Netcat listener o Must compile Netcat with its GAPING_SECURITY_HOLE option q In UNIX: nc victim_machine 12345 o Starts Netcat in client mode with listener on TCP port 12345 o No authentication required of attacker Maintaining Access 7
 Backdoors q Trojan backdoor appears to be “good” o But actually installs backdoor Three types of trojans (soup analogy) q Application level: separate application q o Trudy adds poison to your soup q User-mode rootkit: replace system stuff o Trudy switched potatoes for poisonous potatoes q Kernel-mode rootkit: OS itself is modified o Trudy replaces your tongue with “poison” tongue Maintaining Access 8
Backdoors q Trojan backdoor appears to be “good” o But actually installs backdoor Three types of trojans (soup analogy) q Application level: separate application q o Trudy adds poison to your soup q User-mode rootkit: replace system stuff o Trudy switched potatoes for poisonous potatoes q Kernel-mode rootkit: OS itself is modified o Trudy replaces your tongue with “poison” tongue Maintaining Access 8
 Application Level Trojans q Separate application o Gives attacker access o Most prevalent on Windows q Remote-control backdoor o Can control system across network o Microsoft itself supposedly attacked in 2000 Maintaining Access 9
Application Level Trojans q Separate application o Gives attacker access o Most prevalent on Windows q Remote-control backdoor o Can control system across network o Microsoft itself supposedly attacked in 2000 Maintaining Access 9
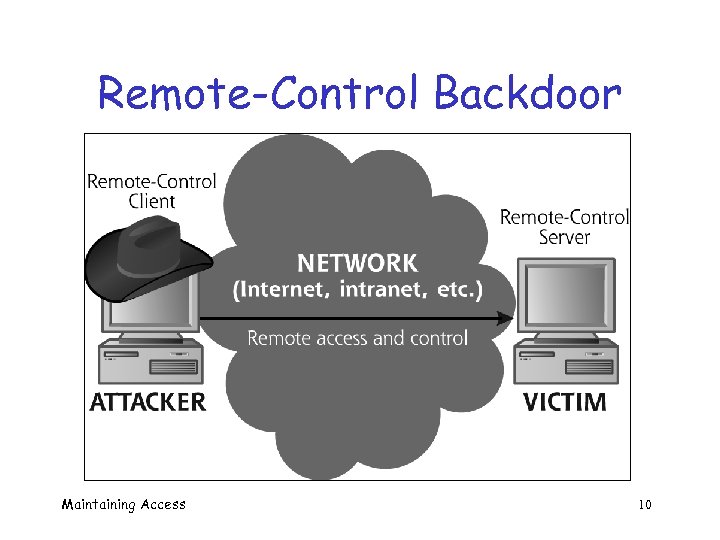 Remote-Control Backdoor Maintaining Access 10
Remote-Control Backdoor Maintaining Access 10
 Remote-Control Backdoor q Thousands of such backdoors o See www. megasecurity. org q Some months, 50 or more released o Eventually, detectable by antivirus q Popular remote-control tools o VNC, Dameware, Back Orifice, Sub. Seven Maintaining Access 11
Remote-Control Backdoor q Thousands of such backdoors o See www. megasecurity. org q Some months, 50 or more released o Eventually, detectable by antivirus q Popular remote-control tools o VNC, Dameware, Back Orifice, Sub. Seven Maintaining Access 11
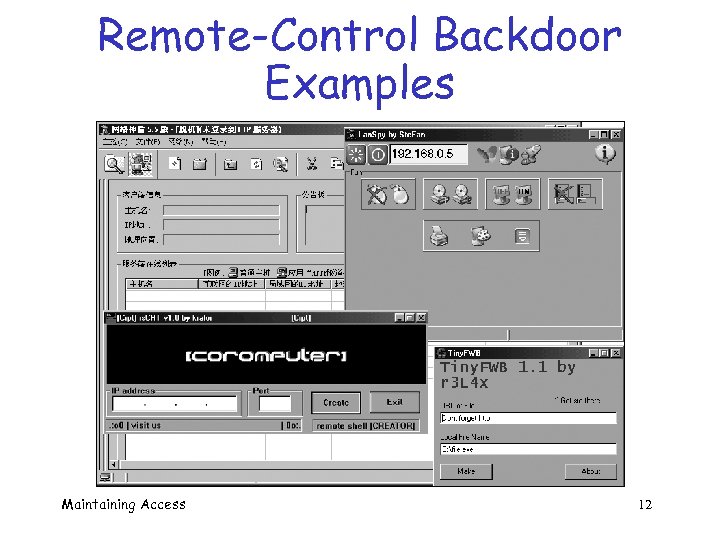 Remote-Control Backdoor Examples Maintaining Access 12
Remote-Control Backdoor Examples Maintaining Access 12
 Remote-Control Backdoor q Functionality o o o o Pop-up dialog box on victim’s machine Log keystrokes List system info Collect passwords Manipulate files (view, copy, …) Modify registry settings or processes Remotely accessible command shell GUI “control”, video, audio, sniffers Maintaining Access 13
Remote-Control Backdoor q Functionality o o o o Pop-up dialog box on victim’s machine Log keystrokes List system info Collect passwords Manipulate files (view, copy, …) Modify registry settings or processes Remotely accessible command shell GUI “control”, video, audio, sniffers Maintaining Access 13
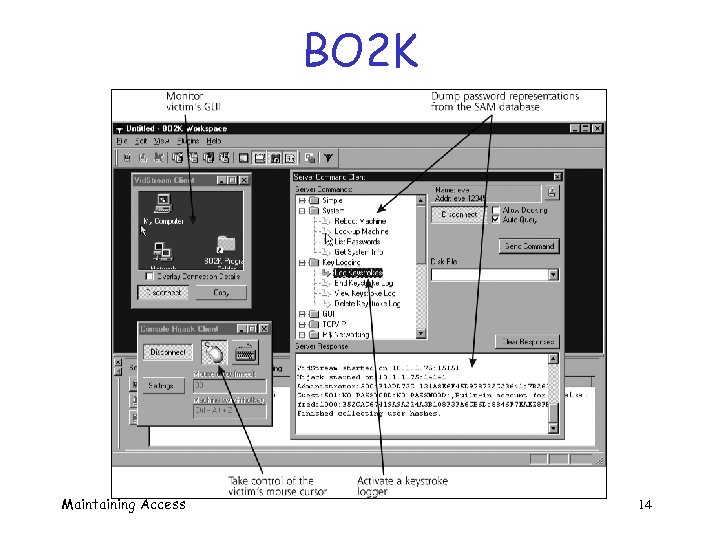 BO 2 K Maintaining Access 14
BO 2 K Maintaining Access 14
 Remote-Control Backdoors q Like a hammer… q In the right hands, useful tool o Administrator, white hat, … q In the wrong hands, can cause damage o Hacker, black hat, … Maintaining Access 15
Remote-Control Backdoors q Like a hammer… q In the right hands, useful tool o Administrator, white hat, … q In the wrong hands, can cause damage o Hacker, black hat, … Maintaining Access 15
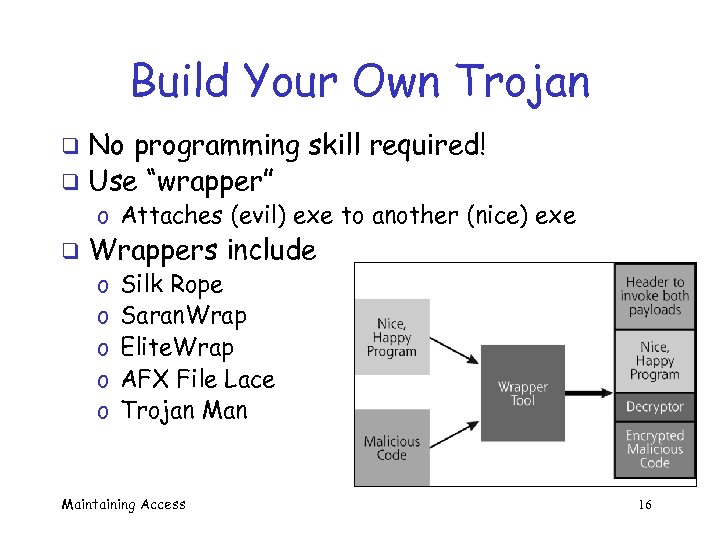 Build Your Own Trojan No programming skill required! q Use “wrapper” q o Attaches (evil) exe to another (nice) exe q Wrappers include o o o Silk Rope Saran. Wrap Elite. Wrap AFX File Lace Trojan Maintaining Access 16
Build Your Own Trojan No programming skill required! q Use “wrapper” q o Attaches (evil) exe to another (nice) exe q Wrappers include o o o Silk Rope Saran. Wrap Elite. Wrap AFX File Lace Trojan Maintaining Access 16
 Build Your Own Trojan Use a wrapper q Give program a nice name q o Free. Game. exe, not Evil. Virus. exe Email it to lots of people q Spoof source of email, etc. q Problem: where are the victims? q o Solution: “notification” functionality o Via email? Maintaining Access 17
Build Your Own Trojan Use a wrapper q Give program a nice name q o Free. Game. exe, not Evil. Virus. exe Email it to lots of people q Spoof source of email, etc. q Problem: where are the victims? q o Solution: “notification” functionality o Via email? Maintaining Access 17
 Related Attacks q Phishing o Email-based o Can be fairly sophisticated/targeted q URL obfuscation o Evil site disguised as legitimate website Maintaining Access 18
Related Attacks q Phishing o Email-based o Can be fairly sophisticated/targeted q URL obfuscation o Evil site disguised as legitimate website Maintaining Access 18
 Bots Designed for “economies of scale” q Control many machines, not one at a time q o A botnet, controlled by a bot master o Usually via IRC (but that is changing) q Bots of 100, 000 or more machines o Bot code freely available o Phatbot (500+ variations), sdbot, m. IRC bot o Some high-quality code (phatbot) Maintaining Access 19
Bots Designed for “economies of scale” q Control many machines, not one at a time q o A botnet, controlled by a bot master o Usually via IRC (but that is changing) q Bots of 100, 000 or more machines o Bot code freely available o Phatbot (500+ variations), sdbot, m. IRC bot o Some high-quality code (phatbot) Maintaining Access 19
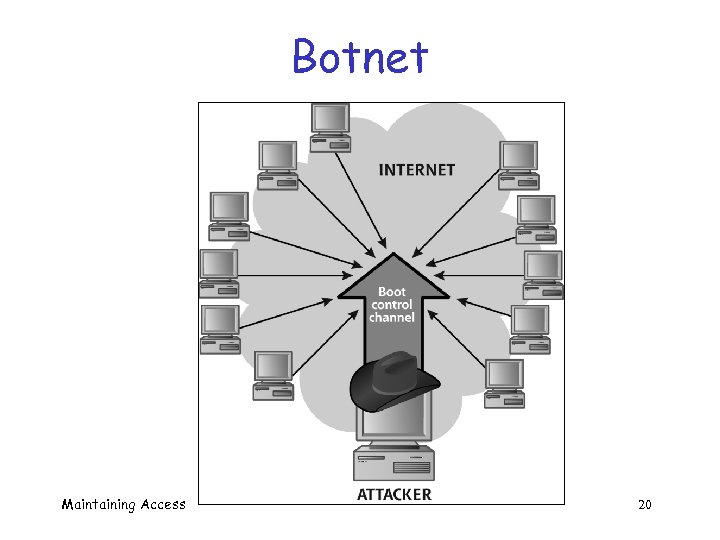 Botnet Maintaining Access 20
Botnet Maintaining Access 20
 Botnets q Botnet o o o functionality includes Do. S Vulnerability scanning Metamorphism Anonymizing HTTP proxy Email address collection/spamming Other? Maintaining Access 21
Botnets q Botnet o o o functionality includes Do. S Vulnerability scanning Metamorphism Anonymizing HTTP proxy Email address collection/spamming Other? Maintaining Access 21
 Virtual Machine Detection q Virtual machines used to analyze bots o And other malware q Some bots try to detect virtual machine o What if virtual machine is detected? q Red Pill o o Execute SIDT, look at IDTR location If non-virtual then IDTR is at low address If virtual machine then IDTR at high address What could be simpler than that? Maintaining Access 22
Virtual Machine Detection q Virtual machines used to analyze bots o And other malware q Some bots try to detect virtual machine o What if virtual machine is detected? q Red Pill o o Execute SIDT, look at IDTR location If non-virtual then IDTR is at low address If virtual machine then IDTR at high address What could be simpler than that? Maintaining Access 22
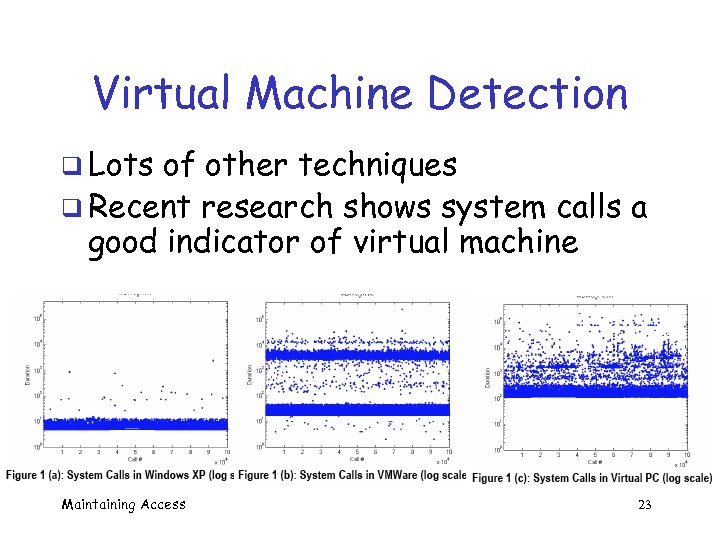 Virtual Machine Detection q Lots of other techniques q Recent research shows system calls a good indicator of virtual machine Maintaining Access 23
Virtual Machine Detection q Lots of other techniques q Recent research shows system calls a good indicator of virtual machine Maintaining Access 23
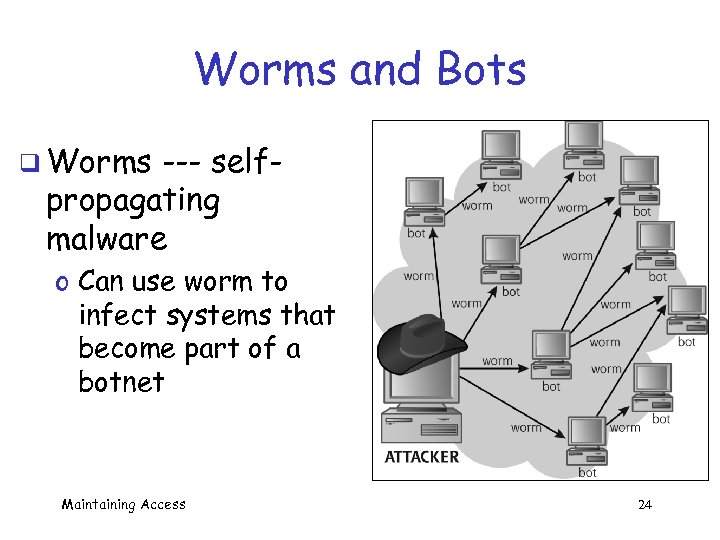 Worms and Bots q Worms --- selfpropagating malware o Can use worm to infect systems that become part of a botnet Maintaining Access 24
Worms and Bots q Worms --- selfpropagating malware o Can use worm to infect systems that become part of a botnet Maintaining Access 24
 Spyware q Software the spies on you q Typically focused on one objective q Usually simple propagation method o User installs it o May be disguised as anti-spyware o May also use browser flaws Maintaining Access 25
Spyware q Software the spies on you q Typically focused on one objective q Usually simple propagation method o User installs it o May be disguised as anti-spyware o May also use browser flaws Maintaining Access 25
 Spyware q Capabilities o o o of spyware Web surfing statistics Personal identifiable information (PII) Customized advertising Customized filtering of searches Pop-up ads Keystroke logging Maintaining Access 26
Spyware q Capabilities o o o of spyware Web surfing statistics Personal identifiable information (PII) Customized advertising Customized filtering of searches Pop-up ads Keystroke logging Maintaining Access 26
 Defenses against application level trojans/backdoors, bots, spyware q Antivirus, user education q Look for unusual TCP/UDP ports q Know your software q o Easier said than done! o Check hashes/fingerprints o Better yet, use digital signatures Maintaining Access 27
Defenses against application level trojans/backdoors, bots, spyware q Antivirus, user education q Look for unusual TCP/UDP ports q Know your software q o Easier said than done! o Check hashes/fingerprints o Better yet, use digital signatures Maintaining Access 27
 Defenses q MD 5 hash q NOT a “signature” o Regardless of the “signatures” line Maintaining Access 28
Defenses q MD 5 hash q NOT a “signature” o Regardless of the “signatures” line Maintaining Access 28
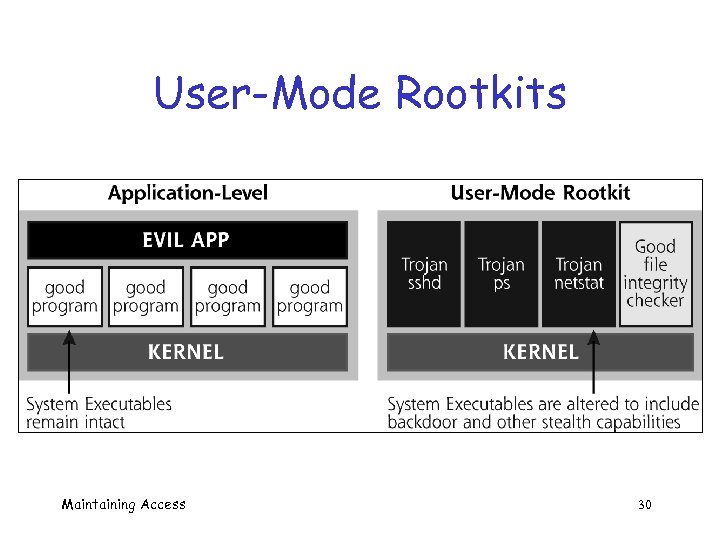
 User-Mode Rootkits q Application level backdoors o Separate applications o Relatively easy to detect q User-mode rootkits o More insidious o Modify OS software/libraries Maintaining Access 29
User-Mode Rootkits q Application level backdoors o Separate applications o Relatively easy to detect q User-mode rootkits o More insidious o Modify OS software/libraries Maintaining Access 29
 User-Mode Rootkits Maintaining Access 30
User-Mode Rootkits Maintaining Access 30
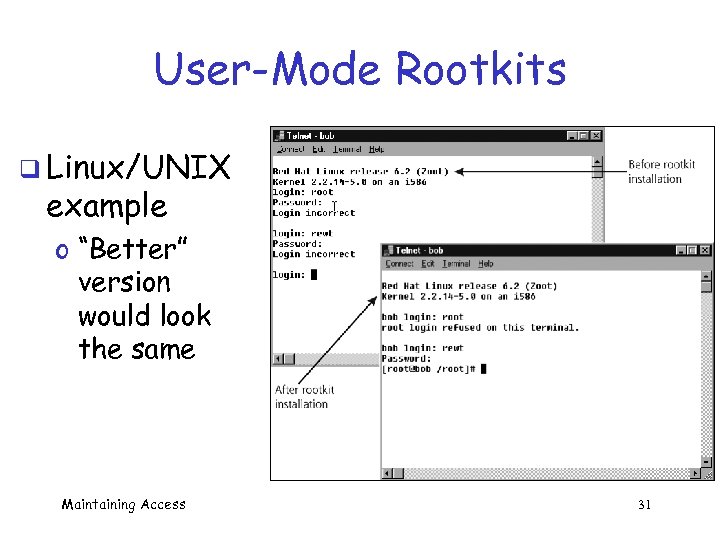 User-Mode Rootkits q Linux/UNIX example o “Better” version would look the same Maintaining Access 31
User-Mode Rootkits q Linux/UNIX example o “Better” version would look the same Maintaining Access 31
 User-Mode Rootkits q Linux/UNIX o o o rootkits might replace… du --- to lie about disk usage find --- hide attacker’s files ls --- hide rootkit files netstat --- lie about ports in use ps --- hide processes syslogd --- don’t log attacker’s actions Maintaining Access 32
User-Mode Rootkits q Linux/UNIX o o o rootkits might replace… du --- to lie about disk usage find --- hide attacker’s files ls --- hide rootkit files netstat --- lie about ports in use ps --- hide processes syslogd --- don’t log attacker’s actions Maintaining Access 32
 User-Mode Rootkits q Windows rootkits are different q Often alter memory of running processes associated with OS o E. g. , make OS “think” port not in use… q Why this approach? o Difficult to change critical system files o Easy for one process to access another Maintaining Access 33
User-Mode Rootkits q Windows rootkits are different q Often alter memory of running processes associated with OS o E. g. , make OS “think” port not in use… q Why this approach? o Difficult to change critical system files o Easy for one process to access another Maintaining Access 33
 User-Mode Rootkits q In Windows, rootkit “hooks” API calls o Rootkit overwrites API call to point to attacker’s code o Attack code calls real function, returns altered results to hooked function q Rootkit likely also includes command shell backdoor Maintaining Access 34
User-Mode Rootkits q In Windows, rootkit “hooks” API calls o Rootkit overwrites API call to point to attacker’s code o Attack code calls real function, returns altered results to hooked function q Rootkit likely also includes command shell backdoor Maintaining Access 34
 User-Mode Rootkits q Windows rootkits might hook… o Nt. Query. System. Information --- Hide running processes o Nt. Query. Directory. File --- Hide files o Nt. Enumerate. Key --- hide registry keys o Nt. Read. Virtual. Memory --- hide hooked API calls Maintaining Access 35
User-Mode Rootkits q Windows rootkits might hook… o Nt. Query. System. Information --- Hide running processes o Nt. Query. Directory. File --- Hide files o Nt. Enumerate. Key --- hide registry keys o Nt. Read. Virtual. Memory --- hide hooked API calls Maintaining Access 35
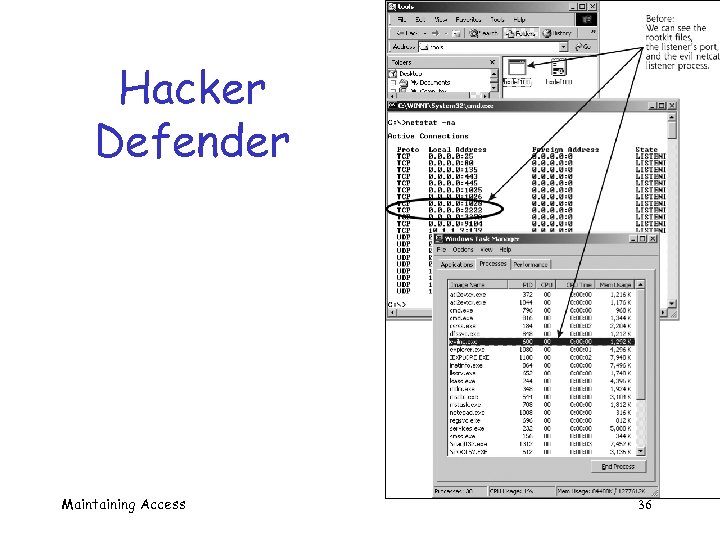 Hacker Defender Maintaining Access 36
Hacker Defender Maintaining Access 36
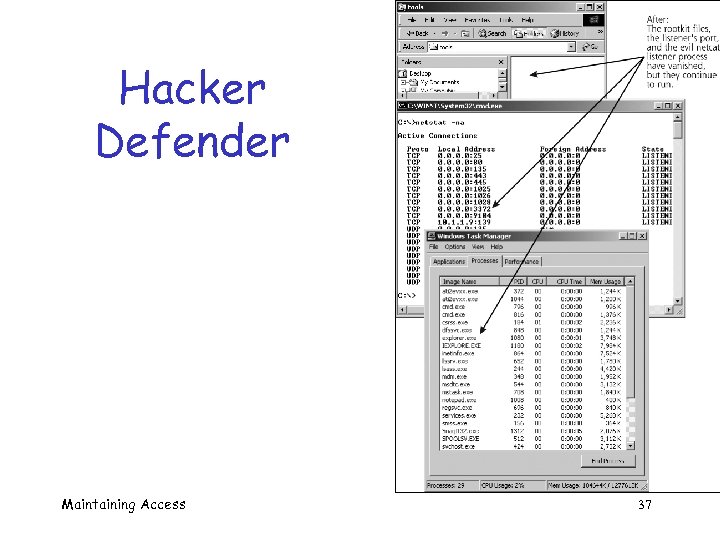 Hacker Defender Maintaining Access 37
Hacker Defender Maintaining Access 37
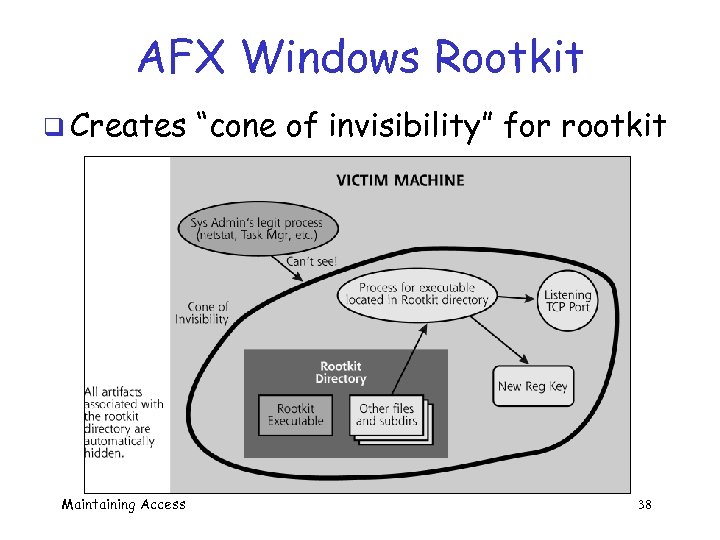 AFX Windows Rootkit q Creates Maintaining Access “cone of invisibility” for rootkit 38
AFX Windows Rootkit q Creates Maintaining Access “cone of invisibility” for rootkit 38
 Cone of Silence Maintaining Access 39
Cone of Silence Maintaining Access 39
 Defenses q Defenses against user-mode rootkits q Don’t let attacker get root access o Good pwds, close ports, etc. q Employ file integrity/hash checking o Tripwire q Antivirus Maintaining Access 40
Defenses q Defenses against user-mode rootkits q Don’t let attacker get root access o Good pwds, close ports, etc. q Employ file integrity/hash checking o Tripwire q Antivirus Maintaining Access 40
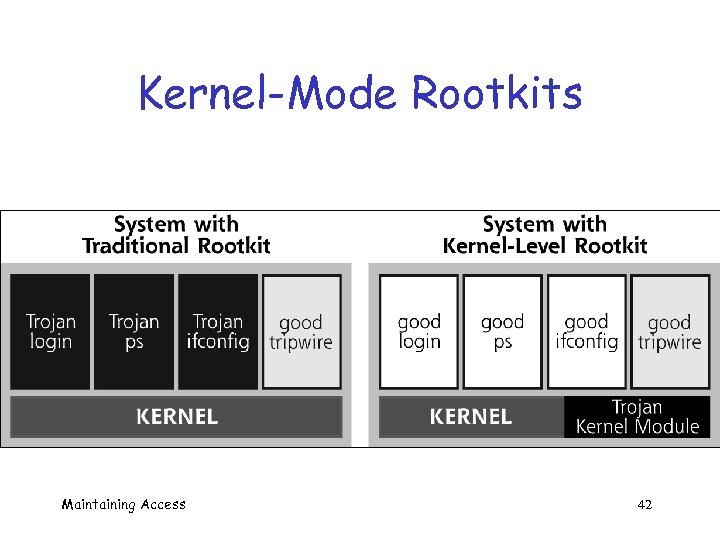
 Kernel-Mode Rootkits q Kernel is heart of OS q User-mode rootkit o Alters administrator’s eyes and ears q Kernel-mode rootkit o Alters part of administrator’s brain q “If the kernel cannot be trusted, you can trust nothing on the system” Maintaining Access 41
Kernel-Mode Rootkits q Kernel is heart of OS q User-mode rootkit o Alters administrator’s eyes and ears q Kernel-mode rootkit o Alters part of administrator’s brain q “If the kernel cannot be trusted, you can trust nothing on the system” Maintaining Access 41
 Kernel-Mode Rootkits Maintaining Access 42
Kernel-Mode Rootkits Maintaining Access 42
 Kernel-Mode Rootkit q Execution redirection o Calls to certain app mapped elsewhere o For example, map sshd to backdoor_sshd q File hiding o You see only what attacker wants you to q Process Maintaining Access hiding, network hiding, etc. 43
Kernel-Mode Rootkit q Execution redirection o Calls to certain app mapped elsewhere o For example, map sshd to backdoor_sshd q File hiding o You see only what attacker wants you to q Process Maintaining Access hiding, network hiding, etc. 43
 Kernel-Mode Rootkits q Adore-ng: Linux Kernel-Mode Rootkit o Promiscuous mode hiding: smart enough to check if promiscuous mode is by admin o Process hiding: can cloak any process o Kernel module hiding: Adore-ng hides itself Maintaining Access 44
Kernel-Mode Rootkits q Adore-ng: Linux Kernel-Mode Rootkit o Promiscuous mode hiding: smart enough to check if promiscuous mode is by admin o Process hiding: can cloak any process o Kernel module hiding: Adore-ng hides itself Maintaining Access 44
 Kernel-Mode Rootkits q Windows FU Kernel-Mode Rootkit Pronounced “F” “U”, not “foo” So it is OK to say “Windows FU” Created by “Fuzen” Consists of special device driver: msdirectx. sys o Hide processes, alter privilege, hides events, etc. o o Maintaining Access 45
Kernel-Mode Rootkits q Windows FU Kernel-Mode Rootkit Pronounced “F” “U”, not “foo” So it is OK to say “Windows FU” Created by “Fuzen” Consists of special device driver: msdirectx. sys o Hide processes, alter privilege, hides events, etc. o o Maintaining Access 45
 Defenses q Install kernel-mode rootkit on your own system? Good idea or bad idea? q Bad idea… o Attacker might understand rootkit better than you do… o Postmortem analysis more difficult o Multiple rootkits could be installed, in principle Maintaining Access 46
Defenses q Install kernel-mode rootkit on your own system? Good idea or bad idea? q Bad idea… o Attacker might understand rootkit better than you do… o Postmortem analysis more difficult o Multiple rootkits could be installed, in principle Maintaining Access 46
 Defenses Don’t let attacker get root q Control access to kernel q o Systrace (by Niels Provos), CSA, Entercept Use IDS q Automated rootkit checkers q o Chkrootkit: signature scan, hidden processes, file structure inconsistencies, … o Rootkit Hunter, Rootkit Revealer: look for discrepancies between user mode/kernel mode Maintaining Access 47
Defenses Don’t let attacker get root q Control access to kernel q o Systrace (by Niels Provos), CSA, Entercept Use IDS q Automated rootkit checkers q o Chkrootkit: signature scan, hidden processes, file structure inconsistencies, … o Rootkit Hunter, Rootkit Revealer: look for discrepancies between user mode/kernel mode Maintaining Access 47
 Defenses q File integrity check q Antivirus o Note: some antivirus will flag rootkit checkers q Boot from CD for analysis Maintaining Access 48
Defenses q File integrity check q Antivirus o Note: some antivirus will flag rootkit checkers q Boot from CD for analysis Maintaining Access 48
 Conclusions Maintaining Access 49
Conclusions Maintaining Access 49
 Summary Maintaining Access 50
Summary Maintaining Access 50


