fd79643cab9105b822b5714b573c2b94.ppt
- Количество слайдов: 39
 Low Cost Security for Internet-0? Frontiers and Limits Jean-Jacques Quisquater jjq@dice. ucl. ac. be (visiting scientist at MIT) (research director CNRS, France) Université catholique de Louvain-la-Neuve, Belgium UCL Crypto Group http: //uclcrypto. org © UCL Crypto group – October 2004 – I 0
Low Cost Security for Internet-0? Frontiers and Limits Jean-Jacques Quisquater jjq@dice. ucl. ac. be (visiting scientist at MIT) (research director CNRS, France) Université catholique de Louvain-la-Neuve, Belgium UCL Crypto Group http: //uclcrypto. org © UCL Crypto group – October 2004 – I 0
 b questions • security? • existence of secure objects? • low cost security? • state-of-the art? © UCL Crypto group October 2004 - I 0 2
b questions • security? • existence of secure objects? • low cost security? • state-of-the art? © UCL Crypto group October 2004 - I 0 2
 Goal of security for I-0 • • Accidental access by neighbors Malicious access by others Cloning? Security from internet-1? : many solutions: ssh, tls, https, ipsec, … • Many crypto algorithms are not designed for low power or for small implementations (compression? ) • Similar situation: smart card (contact or contactless) versus card reader © UCL Crypto group October 2004 - I 0 3
Goal of security for I-0 • • Accidental access by neighbors Malicious access by others Cloning? Security from internet-1? : many solutions: ssh, tls, https, ipsec, … • Many crypto algorithms are not designed for low power or for small implementations (compression? ) • Similar situation: smart card (contact or contactless) versus card reader © UCL Crypto group October 2004 - I 0 3
 Cost of security? • • Implementation (not the losses) Comms Silicon area Programs (protocols) Detectors (intrusion) and firewalls Physical security (tamperresistance) Update: the third version syndrome © UCL Crypto group October 2004 - I 0 4
Cost of security? • • Implementation (not the losses) Comms Silicon area Programs (protocols) Detectors (intrusion) and firewalls Physical security (tamperresistance) Update: the third version syndrome © UCL Crypto group October 2004 - I 0 4
 Internet-0 • • Low cost object Slow and close communication « serial » communication … © UCL Crypto group October 2004 - I 0 5
Internet-0 • • Low cost object Slow and close communication « serial » communication … © UCL Crypto group October 2004 - I 0 5
 Cost of security? Smart cards • • Implementation (not the risk) Comms 9600 b-100 kb-…Silicon area 3 mm 2 -O. 1… Programs (protocols) 2 k. Bytes. Detectors (intrusion) and firewalls % Physical security (tamperresistance) !!!? ? ? Update: Java applets © UCL Crypto group October 2004 - I 0 6
Cost of security? Smart cards • • Implementation (not the risk) Comms 9600 b-100 kb-…Silicon area 3 mm 2 -O. 1… Programs (protocols) 2 k. Bytes. Detectors (intrusion) and firewalls % Physical security (tamperresistance) !!!? ? ? Update: Java applets © UCL Crypto group October 2004 - I 0 6
 Security is a dynamic process • Best at the beginning of the system life, if static • Initialisation (keys, names, …): here we need some physical security (context) • Uses: new applications and contexts • Update, new attacks (algo, hardware, …) • End of life © UCL Crypto group October 2004 - I 0 7
Security is a dynamic process • Best at the beginning of the system life, if static • Initialisation (keys, names, …): here we need some physical security (context) • Uses: new applications and contexts • Update, new attacks (algo, hardware, …) • End of life © UCL Crypto group October 2004 - I 0 7
 Short Story of Smart Cards • René Barjavel (1966) « La nuit des temps » (Gondas) • several inventors in USA (IBM - 1968), Japan, Germany, France • Roland Moreno (F) pushed the right version (1974) • Michel Ugon and Louis Guillou were the technical inventors (~ 1977) • SPOM: single chip (security): 1981: first crypto algo and protocol (secret key): tests in France • first DES: 1985 (TRASEC, Belgium, TB 100 -> Proton) • first RSA: CORSAIR(Philips): 1989 (coprocessor) • first RISC 32 bits: 1997 (CASCADE-> Gem. Expresso) • first JAVA smart card: 1997 (Schlumberger-software) • . . . © UCL Crypto group – October 2004 – I 0
Short Story of Smart Cards • René Barjavel (1966) « La nuit des temps » (Gondas) • several inventors in USA (IBM - 1968), Japan, Germany, France • Roland Moreno (F) pushed the right version (1974) • Michel Ugon and Louis Guillou were the technical inventors (~ 1977) • SPOM: single chip (security): 1981: first crypto algo and protocol (secret key): tests in France • first DES: 1985 (TRASEC, Belgium, TB 100 -> Proton) • first RSA: CORSAIR(Philips): 1989 (coprocessor) • first RISC 32 bits: 1997 (CASCADE-> Gem. Expresso) • first JAVA smart card: 1997 (Schlumberger-software) • . . . © UCL Crypto group – October 2004 – I 0
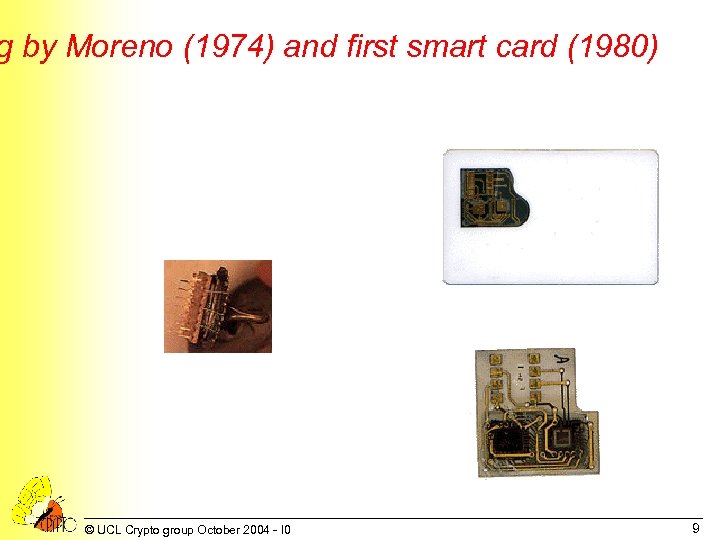 g by Moreno (1974) and first smart card (1980) © UCL Crypto group October 2004 - I 0 9
g by Moreno (1974) and first smart card (1980) © UCL Crypto group October 2004 - I 0 9
 The chip (a complete computer) • • • CPU security logic and sensors ROM: OS - including self-test procedures RAM (mainly static) (E)EPROM and/or flash memory – cryptographic keys – PIN – biometric profiles – applications • serial I/O • internal bus(ses) • accelerators for cryptoalgorithms DES, RSA. . . (coprocessors) © UCL Crypto group October 2004 - I 0 10
The chip (a complete computer) • • • CPU security logic and sensors ROM: OS - including self-test procedures RAM (mainly static) (E)EPROM and/or flash memory – cryptographic keys – PIN – biometric profiles – applications • serial I/O • internal bus(ses) • accelerators for cryptoalgorithms DES, RSA. . . (coprocessors) © UCL Crypto group October 2004 - I 0 10
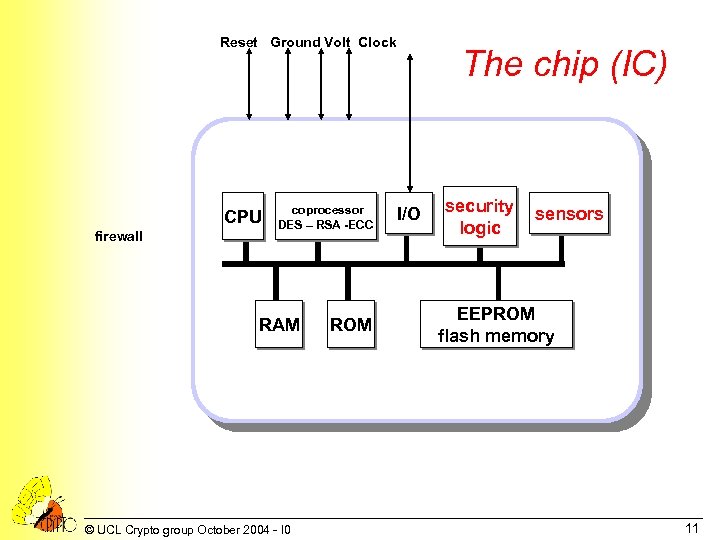 Reset Ground Volt Clock CPU firewall coprocessor DES – RSA -ECC RAM © UCL Crypto group October 2004 - I 0 ROM The chip (IC) I/O security logic sensors EEPROM flash memory 11
Reset Ground Volt Clock CPU firewall coprocessor DES – RSA -ECC RAM © UCL Crypto group October 2004 - I 0 ROM The chip (IC) I/O security logic sensors EEPROM flash memory 11
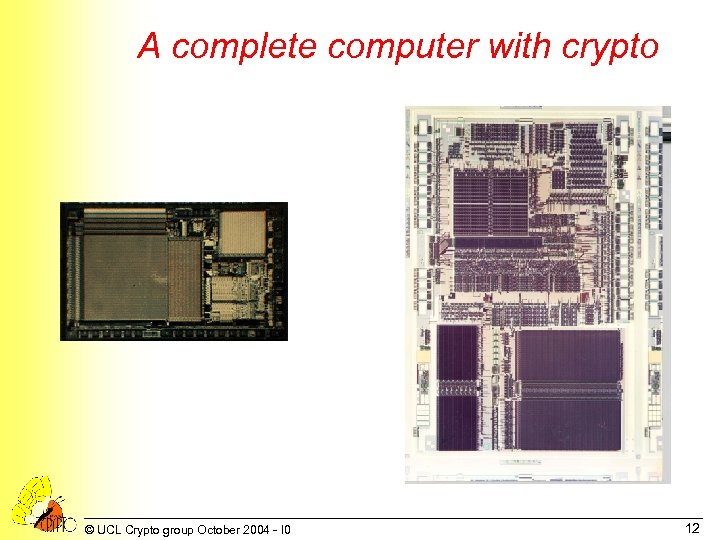 A complete computer with crypto © UCL Crypto group October 2004 - I 0 12
A complete computer with crypto © UCL Crypto group October 2004 - I 0 12
 Standards for (secure) chips • • • © UCL Crypto group October 2004 - I 0 ISO-7816 GSM 11. * EMV FIPS 140 -1, -2 … Do you need it? 13
Standards for (secure) chips • • • © UCL Crypto group October 2004 - I 0 ISO-7816 GSM 11. * EMV FIPS 140 -1, -2 … Do you need it? 13
 Lesson learned from smart cards • Design for: – access for pay. TV, – phone coins, – banking cards, – common property: easy to trace or small loss. • Security is « easy » : avoiding intrusion • But used for many applications with high targets (SWIFT, …) • Problems of side-channels (1996) © UCL Crypto group October 2004 - I 0 14
Lesson learned from smart cards • Design for: – access for pay. TV, – phone coins, – banking cards, – common property: easy to trace or small loss. • Security is « easy » : avoiding intrusion • But used for many applications with high targets (SWIFT, …) • Problems of side-channels (1996) © UCL Crypto group October 2004 - I 0 14
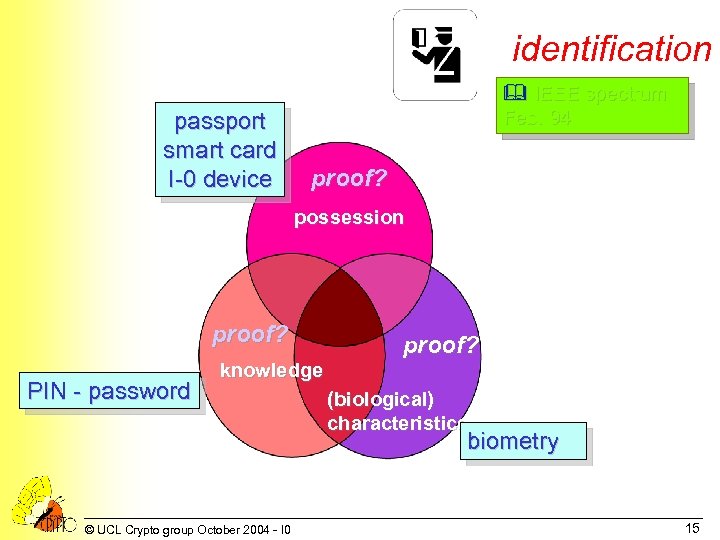 identification passport smart card I-0 device & IEEE spectrum Feb. 94 proof? possession proof? PIN - password knowledge proof? (biological) characteristics biometry © UCL Crypto group October 2004 - I 0 15
identification passport smart card I-0 device & IEEE spectrum Feb. 94 proof? possession proof? PIN - password knowledge proof? (biological) characteristics biometry © UCL Crypto group October 2004 - I 0 15
 (Physical) naming process • By an authority (TTP) • Self-nomination (using some random process) • Distributed // election of a leader in a group © UCL Crypto group October 2004 - I 0 16
(Physical) naming process • By an authority (TTP) • Self-nomination (using some random process) • Distributed // election of a leader in a group © UCL Crypto group October 2004 - I 0 16
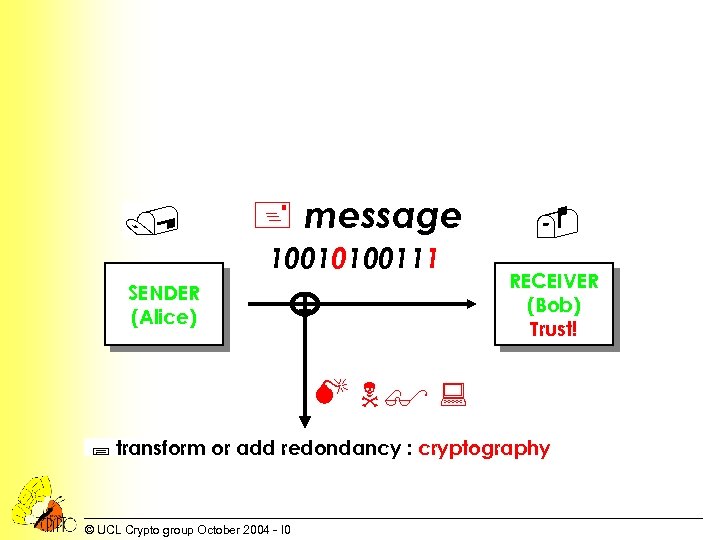 / + message 10010100111 SENDER (Alice) RECEIVER (Bob) Trust! M N$ : ; transform or add redondancy : cryptography © UCL Crypto group October 2004 - I 0
/ + message 10010100111 SENDER (Alice) RECEIVER (Bob) Trust! M N$ : ; transform or add redondancy : cryptography © UCL Crypto group October 2004 - I 0
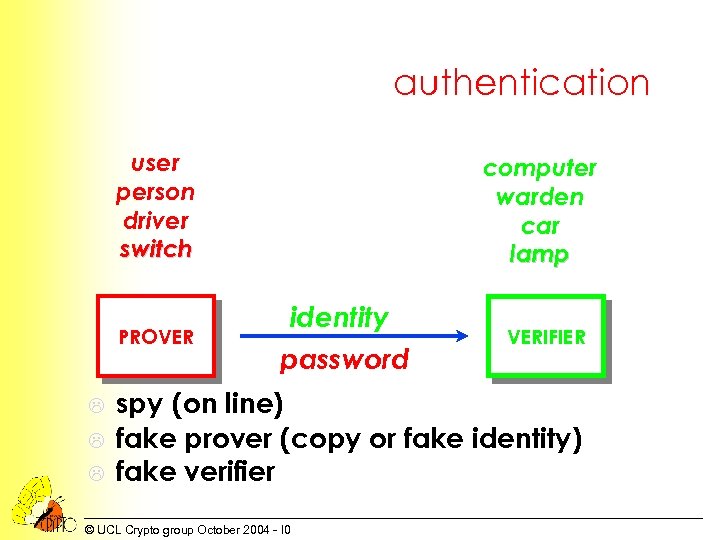 authentication user person driver switch PROVER L L L computer warden car lamp identity password VERIFIER spy (on line) fake prover (copy or fake identity) fake verifier © UCL Crypto group October 2004 - I 0
authentication user person driver switch PROVER L L L computer warden car lamp identity password VERIFIER spy (on line) fake prover (copy or fake identity) fake verifier © UCL Crypto group October 2004 - I 0
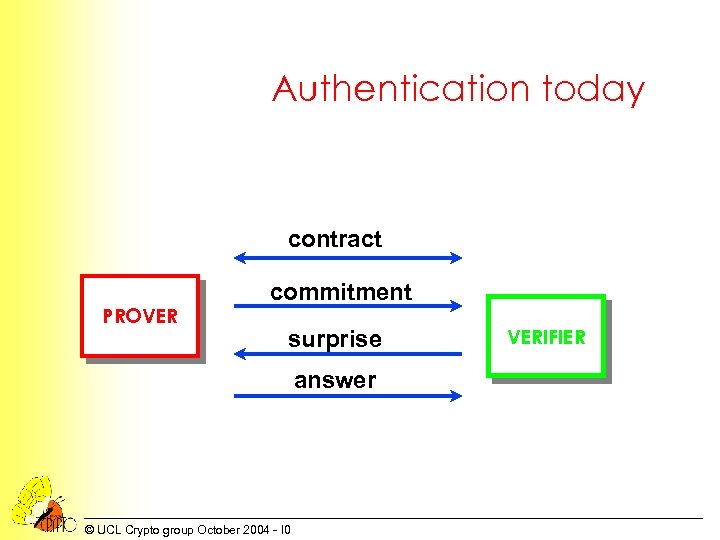 Authentication today contract PROVER commitment surprise answer © UCL Crypto group October 2004 - I 0 VERIFIER
Authentication today contract PROVER commitment surprise answer © UCL Crypto group October 2004 - I 0 VERIFIER
 Solutions Œ proof: – specific protocol: theory invented in 1984, called “zero-knowledge” new proof (fresh): – verifier must be convinced it is not a replay Ž tamper-resistant object: – “smart card” – secure and powerful microprocessor – important subject of research © UCL Crypto group October 2004 - I 0
Solutions Œ proof: – specific protocol: theory invented in 1984, called “zero-knowledge” new proof (fresh): – verifier must be convinced it is not a replay Ž tamper-resistant object: – “smart card” – secure and powerful microprocessor – important subject of research © UCL Crypto group October 2004 - I 0
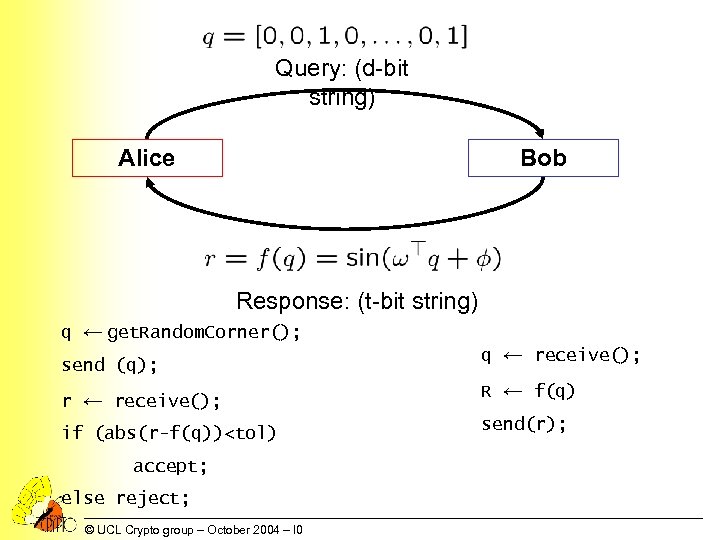 Query: (d-bit string) Alice Bob Response: (t-bit string) q ← get. Random. Corner(); send (q); r ← receive(); if (abs(r-f(q))
Query: (d-bit string) Alice Bob Response: (t-bit string) q ← get. Random. Corner(); send (q); r ← receive(); if (abs(r-f(q))
 © UCL Crypto group October 2004 - I 0 22
© UCL Crypto group October 2004 - I 0 22
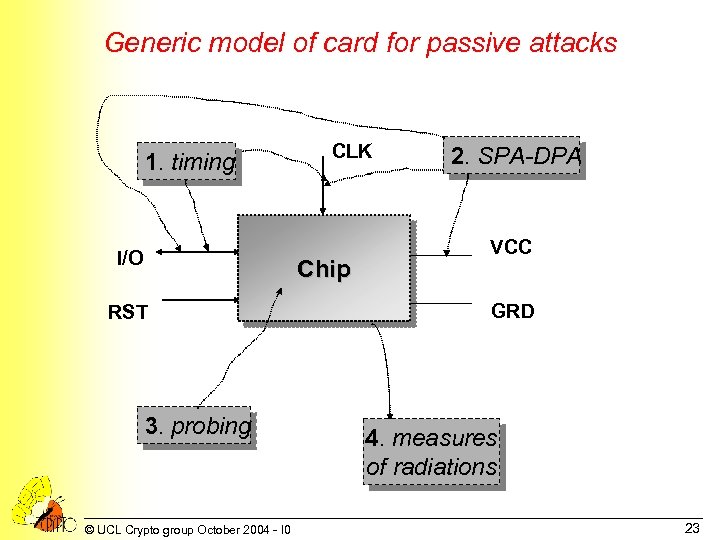 Generic model of card for passive attacks 1. timing I/O CLK Chip RST 3. probing © UCL Crypto group October 2004 - I 0 2. SPA-DPA VCC GRD 4. measures of radiations 23
Generic model of card for passive attacks 1. timing I/O CLK Chip RST 3. probing © UCL Crypto group October 2004 - I 0 2. SPA-DPA VCC GRD 4. measures of radiations 23
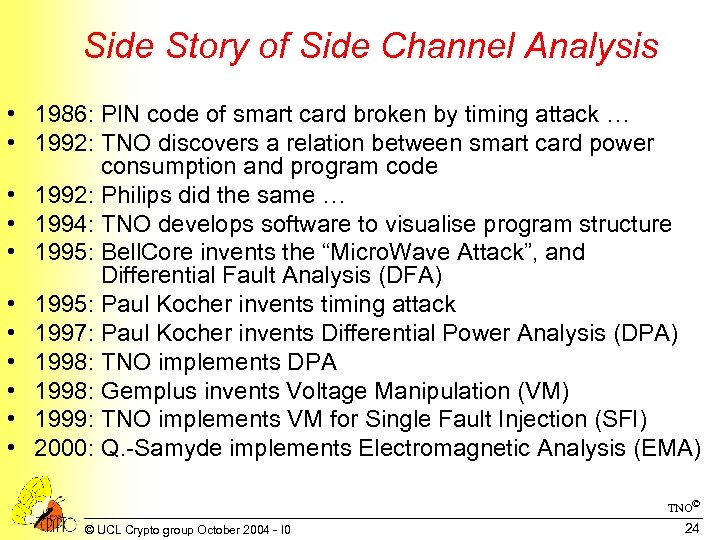 Side Story of Side Channel Analysis • 1986: PIN code of smart card broken by timing attack … • 1992: TNO discovers a relation between smart card power consumption and program code • 1992: Philips did the same … • 1994: TNO develops software to visualise program structure • 1995: Bell. Core invents the “Micro. Wave Attack”, and Differential Fault Analysis (DFA) • 1995: Paul Kocher invents timing attack • 1997: Paul Kocher invents Differential Power Analysis (DPA) • 1998: TNO implements DPA • 1998: Gemplus invents Voltage Manipulation (VM) • 1999: TNO implements VM for Single Fault Injection (SFI) • 2000: Q. -Samyde implements Electromagnetic Analysis (EMA) TNO© © UCL Crypto group October 2004 - I 0 24
Side Story of Side Channel Analysis • 1986: PIN code of smart card broken by timing attack … • 1992: TNO discovers a relation between smart card power consumption and program code • 1992: Philips did the same … • 1994: TNO develops software to visualise program structure • 1995: Bell. Core invents the “Micro. Wave Attack”, and Differential Fault Analysis (DFA) • 1995: Paul Kocher invents timing attack • 1997: Paul Kocher invents Differential Power Analysis (DPA) • 1998: TNO implements DPA • 1998: Gemplus invents Voltage Manipulation (VM) • 1999: TNO implements VM for Single Fault Injection (SFI) • 2000: Q. -Samyde implements Electromagnetic Analysis (EMA) TNO© © UCL Crypto group October 2004 - I 0 24
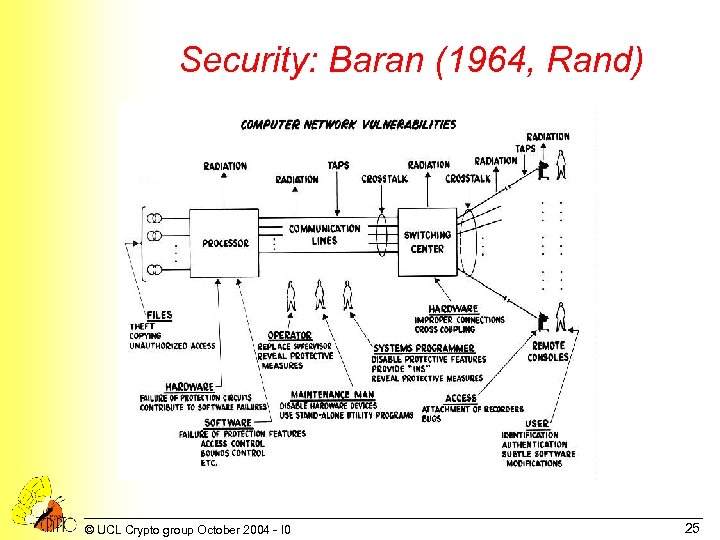 Security: Baran (1964, Rand) © UCL Crypto group October 2004 - I 0 25
Security: Baran (1964, Rand) © UCL Crypto group October 2004 - I 0 25
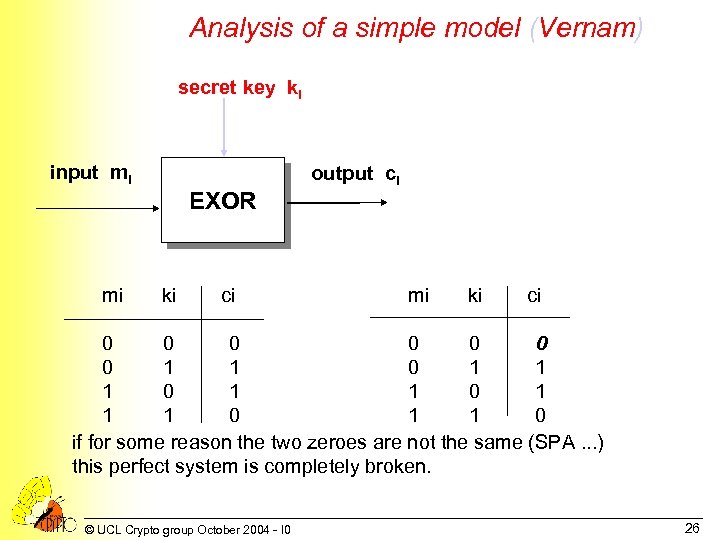 Analysis of a simple model (Vernam) secret key ki input mi EXOR mi ki ci output ci mi ki ci 0 0 0 0 1 1 1 0 1 1 1 0 if for some reason the two zeroes are not the same (SPA. . . ) this perfect system is completely broken. © UCL Crypto group October 2004 - I 0 26
Analysis of a simple model (Vernam) secret key ki input mi EXOR mi ki ci output ci mi ki ci 0 0 0 0 1 1 1 0 1 1 1 0 if for some reason the two zeroes are not the same (SPA. . . ) this perfect system is completely broken. © UCL Crypto group October 2004 - I 0 26
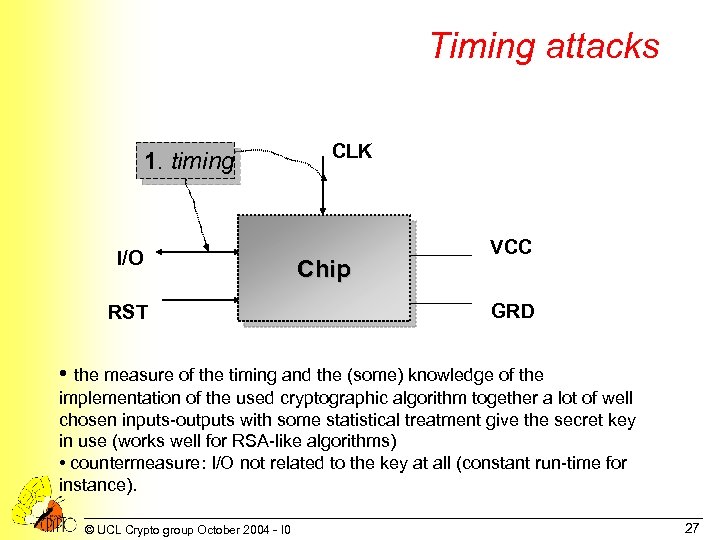 Timing attacks 1. timing I/O RST CLK Chip VCC GRD • the measure of the timing and the (some) knowledge of the implementation of the used cryptographic algorithm together a lot of well chosen inputs-outputs with some statistical treatment give the secret key in use (works well for RSA-like algorithms) • countermeasure: I/O not related to the key at all (constant run-time for instance). © UCL Crypto group October 2004 - I 0 27
Timing attacks 1. timing I/O RST CLK Chip VCC GRD • the measure of the timing and the (some) knowledge of the implementation of the used cryptographic algorithm together a lot of well chosen inputs-outputs with some statistical treatment give the secret key in use (works well for RSA-like algorithms) • countermeasure: I/O not related to the key at all (constant run-time for instance). © UCL Crypto group October 2004 - I 0 27
 Fault attacks (Bellcore) Key=1010110. . . © UCL Crypto group October 2004 - I 0 28
Fault attacks (Bellcore) Key=1010110. . . © UCL Crypto group October 2004 - I 0 28
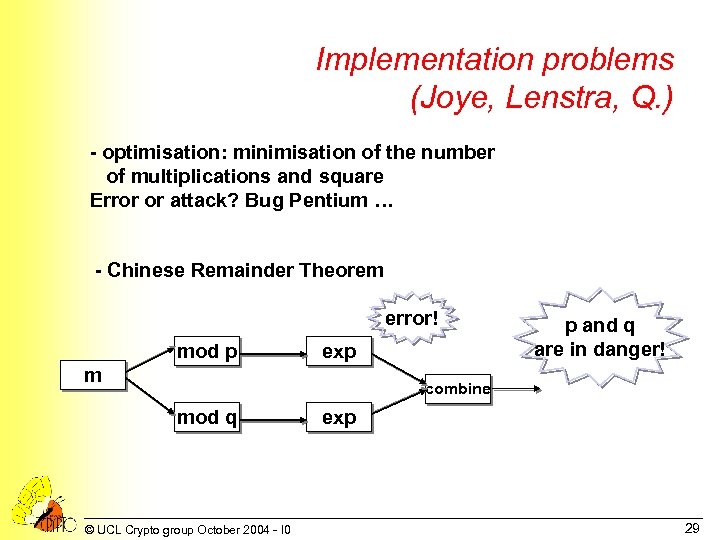 Implementation problems (Joye, Lenstra, Q. ) - optimisation: minimisation of the number of multiplications and square Error or attack? Bug Pentium … - Chinese Remainder Theorem error! mod p exp m p and q are in danger! combine mod q © UCL Crypto group October 2004 - I 0 exp 29
Implementation problems (Joye, Lenstra, Q. ) - optimisation: minimisation of the number of multiplications and square Error or attack? Bug Pentium … - Chinese Remainder Theorem error! mod p exp m p and q are in danger! combine mod q © UCL Crypto group October 2004 - I 0 exp 29
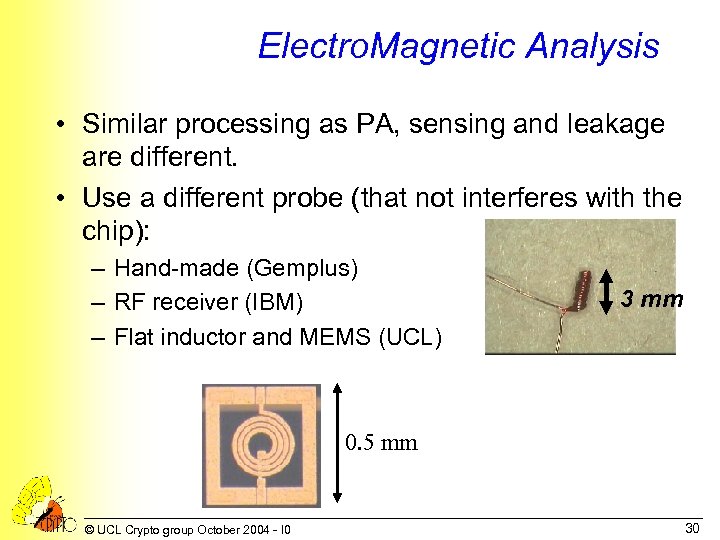 Electro. Magnetic Analysis • Similar processing as PA, sensing and leakage are different. • Use a different probe (that not interferes with the chip): – Hand-made (Gemplus) – RF receiver (IBM) – Flat inductor and MEMS (UCL) 3 mm 0. 5 mm © UCL Crypto group October 2004 - I 0 30
Electro. Magnetic Analysis • Similar processing as PA, sensing and leakage are different. • Use a different probe (that not interferes with the chip): – Hand-made (Gemplus) – RF receiver (IBM) – Flat inductor and MEMS (UCL) 3 mm 0. 5 mm © UCL Crypto group October 2004 - I 0 30
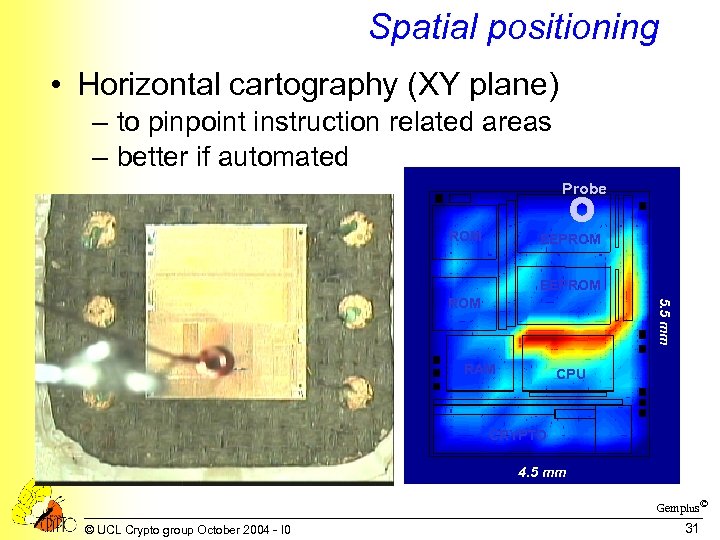 Spatial positioning • Horizontal cartography (XY plane) – to pinpoint instruction related areas – better if automated Probe ROM EEPROM 5. 5 mm ROM RAM CPU CRYPTO 4. 5 mm Gemplus© © UCL Crypto group October 2004 - I 0 31
Spatial positioning • Horizontal cartography (XY plane) – to pinpoint instruction related areas – better if automated Probe ROM EEPROM 5. 5 mm ROM RAM CPU CRYPTO 4. 5 mm Gemplus© © UCL Crypto group October 2004 - I 0 31
 Side Channel Conclusion • Direct and serious threat to the security of crypto systems • Applicable to all algorithms • (mostly) a non-destructive class of attacks • Can be developed in order of weeks, repeated in order of hours • Can be prevented or discouraged by (combinations of) countermeasures © UCL Crypto group October 2004 - I 0 32
Side Channel Conclusion • Direct and serious threat to the security of crypto systems • Applicable to all algorithms • (mostly) a non-destructive class of attacks • Can be developed in order of weeks, repeated in order of hours • Can be prevented or discouraged by (combinations of) countermeasures © UCL Crypto group October 2004 - I 0 32
 Faults insertion • Aim: Cryptanalysis of an algorithm using fault(s) - Glitch attack clock - Local ionisation (Rads 2003) - UV light applied to a certain location - X-rays - Local heating - Optical attack (Ches 2002) - Eddy Currents (ESmart 2002) © UCL Crypto group October 2004 - I 0 33
Faults insertion • Aim: Cryptanalysis of an algorithm using fault(s) - Glitch attack clock - Local ionisation (Rads 2003) - UV light applied to a certain location - X-rays - Local heating - Optical attack (Ches 2002) - Eddy Currents (ESmart 2002) © UCL Crypto group October 2004 - I 0 33
 Security? Free slot at a cyclotron © UCL Crypto group October 2004 - I 0 34
Security? Free slot at a cyclotron © UCL Crypto group October 2004 - I 0 34
 Countermeasures • Scramble the memory structure • CRC • Dedicated sensors • Opaque passivation layer or top-layer shielding • Self-timed circuit & Dual-rail logic • Software countermeasures © UCL Crypto group October 2004 - I 0 35
Countermeasures • Scramble the memory structure • CRC • Dedicated sensors • Opaque passivation layer or top-layer shielding • Self-timed circuit & Dual-rail logic • Software countermeasures © UCL Crypto group October 2004 - I 0 35
 • Software Countermeasures – Check each bit before to set/reset it – Test integrity of all ( Data, Crypto, … ) • Hardware : – Scramble the memory structure – Implement CRC (Well chosen) – Build new architecture for error detection/corrections – Asynchronous processors (www. g 3 card. org) – Dedicated sensors and avoid static sensors If there is a CRC check, there’s a transistor to give a right or wrong value… It could then be possible to lock the value (FPGA, …). © UCL Crypto group October 2004 - I 0 UCL© 36
• Software Countermeasures – Check each bit before to set/reset it – Test integrity of all ( Data, Crypto, … ) • Hardware : – Scramble the memory structure – Implement CRC (Well chosen) – Build new architecture for error detection/corrections – Asynchronous processors (www. g 3 card. org) – Dedicated sensors and avoid static sensors If there is a CRC check, there’s a transistor to give a right or wrong value… It could then be possible to lock the value (FPGA, …). © UCL Crypto group October 2004 - I 0 UCL© 36
 Countermeasures • A lot: New hardware design, new technology, … • Randomize carefully! • No difference between square and multiply (add and doubling): subtle solutions, • Verify the result before outputs, • … • Very mathematical, very cryptographic, • Another story (see recent thesis of Mathieu Ciet – UCL, June 2003 about ECC, aso). © UCL Crypto group October 2004 - I 0 37
Countermeasures • A lot: New hardware design, new technology, … • Randomize carefully! • No difference between square and multiply (add and doubling): subtle solutions, • Verify the result before outputs, • … • Very mathematical, very cryptographic, • Another story (see recent thesis of Mathieu Ciet – UCL, June 2003 about ECC, aso). © UCL Crypto group October 2004 - I 0 37
 © UCL Crypto group October 2004 - I 0 38
© UCL Crypto group October 2004 - I 0 38
 Other directions • Quantum cryptography: nanocrypto • More physics less cryptography: new research • Identify the object (variations, added or not) • Use the object in protocols? © UCL Crypto group October 2004 - I 0 39
Other directions • Quantum cryptography: nanocrypto • More physics less cryptography: new research • Identify the object (variations, added or not) • Use the object in protocols? © UCL Crypto group October 2004 - I 0 39


