5f1e9a7436a6d7410f4a31e79af70533.ppt
- Количество слайдов: 38
 Local & Metropolitan Area Networks ACOE 322 Lecture 7 Upper OSI layers Dr. L. Christofi 1
Local & Metropolitan Area Networks ACOE 322 Lecture 7 Upper OSI layers Dr. L. Christofi 1
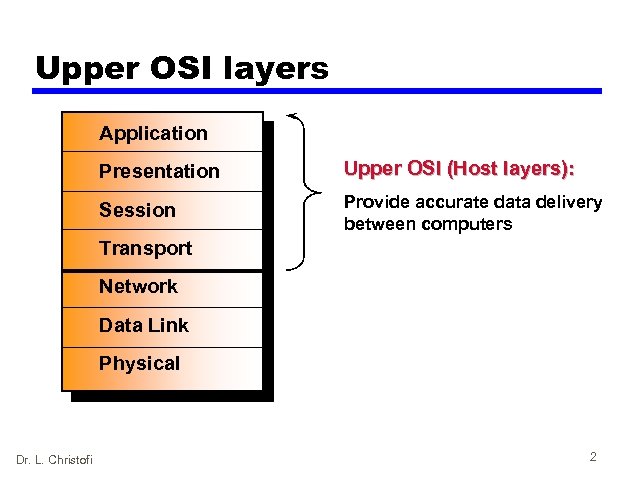 Upper OSI layers 7 Application 6 Presentation Upper OSI (Host layers): 5 Session Provide accurate data delivery between computers 4 Transport 3 Network 2 Data Link 1 Physical Dr. L. Christofi 2
Upper OSI layers 7 Application 6 Presentation Upper OSI (Host layers): 5 Session Provide accurate data delivery between computers 4 Transport 3 Network 2 Data Link 1 Physical Dr. L. Christofi 2
 Transport Layer • It is responsible for source-to-destination (end-toend) delivery of the entire message. — Whereas the network layer oversees end-to-end delivery of individual packets, it does not recognize any relationship between those packets. • Ensures that the whole message arrives intact and in order, overseeing both error control and flow control at the source-to-destination level. Dr. L. Christofi 3
Transport Layer • It is responsible for source-to-destination (end-toend) delivery of the entire message. — Whereas the network layer oversees end-to-end delivery of individual packets, it does not recognize any relationship between those packets. • Ensures that the whole message arrives intact and in order, overseeing both error control and flow control at the source-to-destination level. Dr. L. Christofi 3
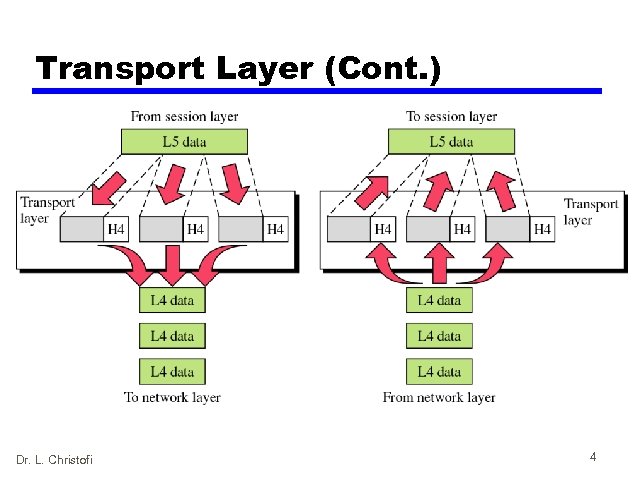 Transport Layer (Cont. ) Dr. L. Christofi 4
Transport Layer (Cont. ) Dr. L. Christofi 4
 The responsibilities of Transport Layer • Service-point addressing — Source-to-destination delivery means delivery not only from one computer to the next but also from a specific process(running program) on one computer to a specific process(running program) on the other. — The transport layer header must include a type of address called a service-point address (or port address). — The network layer gets each packet to the correct computer; the transport layer gets the entire message to the correct process on that computer. Dr. L. Christofi 5
The responsibilities of Transport Layer • Service-point addressing — Source-to-destination delivery means delivery not only from one computer to the next but also from a specific process(running program) on one computer to a specific process(running program) on the other. — The transport layer header must include a type of address called a service-point address (or port address). — The network layer gets each packet to the correct computer; the transport layer gets the entire message to the correct process on that computer. Dr. L. Christofi 5
 The responsibilities of Transport Layer (cont. ) • Segmentation and reassembly — A message is divided into transmittable segments, each segment containing a sequence number. — These numbers enable the transport layer to reassemble the message correctly upon arriving at the destination and to identify and replace packets that were lost in the transmission. • Flow control — The transport layer is responsible for flow control. — It is performed end-to-end rather than across a single link. Dr. L. Christofi 6
The responsibilities of Transport Layer (cont. ) • Segmentation and reassembly — A message is divided into transmittable segments, each segment containing a sequence number. — These numbers enable the transport layer to reassemble the message correctly upon arriving at the destination and to identify and replace packets that were lost in the transmission. • Flow control — The transport layer is responsible for flow control. — It is performed end-to-end rather than across a single link. Dr. L. Christofi 6
 The responsibilities of Transport Layer (cont. ) • Connection control — Can be either connectionless or connection-oriented. — A connectionless transport layer treats each segment as an independent packet and delivers it to the transport layer at the destination machine. — A connection-oriented transport layer makes a connection with the transport layer at the destination machine first before delivering the packets. — After all the data is transferred, the connection is terminated. • Error control — It is performed end-to-end rather than across a single link. Dr. L. Christofi 7
The responsibilities of Transport Layer (cont. ) • Connection control — Can be either connectionless or connection-oriented. — A connectionless transport layer treats each segment as an independent packet and delivers it to the transport layer at the destination machine. — A connection-oriented transport layer makes a connection with the transport layer at the destination machine first before delivering the packets. — After all the data is transferred, the connection is terminated. • Error control — It is performed end-to-end rather than across a single link. Dr. L. Christofi 7
 User Layers • The session, presentation and application layers are known as user layers • Mainly implemented by software • In most protocols like TCP/IP and Novell, these layers are implemented by a single layer called application layer Dr. L. Christofi 8
User Layers • The session, presentation and application layers are known as user layers • Mainly implemented by software • In most protocols like TCP/IP and Novell, these layers are implemented by a single layer called application layer Dr. L. Christofi 8
 Session Layer • It is responsible for establishing, maintaining, and synchronising dialogs between communication upper layers • Also helps to handle upper level problems such as inadequate disk space or out of paper for the printer • Although it is considered as user layer, but it is often implemented within the operating system Dr. L. Christofi 9
Session Layer • It is responsible for establishing, maintaining, and synchronising dialogs between communication upper layers • Also helps to handle upper level problems such as inadequate disk space or out of paper for the printer • Although it is considered as user layer, but it is often implemented within the operating system Dr. L. Christofi 9
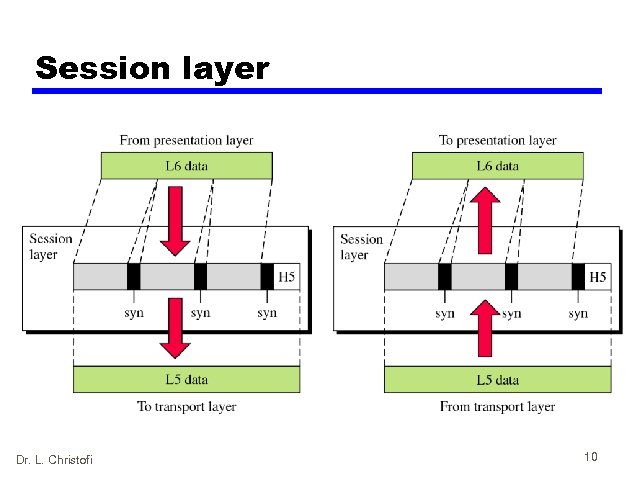 Session layer Dr. L. Christofi 10
Session layer Dr. L. Christofi 10
 Services of the Session Layer • Coordinate connection and disconnection of dialogs between application • Provide synchronisation points for data exchange • Coordinate who sends first and when • Ensure that the data exchange is complete before the session closes Dr. L. Christofi 11
Services of the Session Layer • Coordinate connection and disconnection of dialogs between application • Provide synchronisation points for data exchange • Coordinate who sends first and when • Ensure that the data exchange is complete before the session closes Dr. L. Christofi 11
 Session and Transport Interaction • The transport layer can make an abrupt disconnection while session layer has an obligation to the user and cannot disconnect until the session can be brought to a conclusion • The communication with the transport layer can be of 3 types: — One-to-one: there is one session layer connection for each transport layer connection — Many-to-one: multiple session layer connections share the services of one transport layer connection — One-to-many: one session layer connection needs many transport layer connections to handle the task Dr. L. Christofi 12
Session and Transport Interaction • The transport layer can make an abrupt disconnection while session layer has an obligation to the user and cannot disconnect until the session can be brought to a conclusion • The communication with the transport layer can be of 3 types: — One-to-one: there is one session layer connection for each transport layer connection — Many-to-one: multiple session layer connections share the services of one transport layer connection — One-to-many: one session layer connection needs many transport layer connections to handle the task Dr. L. Christofi 12
 Synchronization points • Mechanism for recovering data that have been delivered but mishandled • Reference points are introduced into the data to control flow of information and allow recovery from software or operator errors • These reference points may call for user acknowledgment or just may provide a go-back facility for data recovery Dr. L. Christofi 13
Synchronization points • Mechanism for recovering data that have been delivered but mishandled • Reference points are introduced into the data to control flow of information and allow recovery from software or operator errors • These reference points may call for user acknowledgment or just may provide a go-back facility for data recovery Dr. L. Christofi 13
 Two types of synchronization points • Major synchronization points: — Divide an exchange into a series of dialogs — Each point must be acknowledged before the session can continue — If an error occurs, data can be recovered only up to the last major point — A session layer activity can be a single dialog or several dialogs separated by major synchronization points Dr. L. Christofi 14
Two types of synchronization points • Major synchronization points: — Divide an exchange into a series of dialogs — Each point must be acknowledged before the session can continue — If an error occurs, data can be recovered only up to the last major point — A session layer activity can be a single dialog or several dialogs separated by major synchronization points Dr. L. Christofi 14
 Two types of synchronization points • Minor synchronization points: —Are inserted into the middle of dialogs and may or may not require confirmation —If an error occurs, the control can go back one or more minor synchronization points within a dialog to recover the data Dr. L. Christofi 15
Two types of synchronization points • Minor synchronization points: —Are inserted into the middle of dialogs and may or may not require confirmation —If an error occurs, the control can go back one or more minor synchronization points within a dialog to recover the data Dr. L. Christofi 15
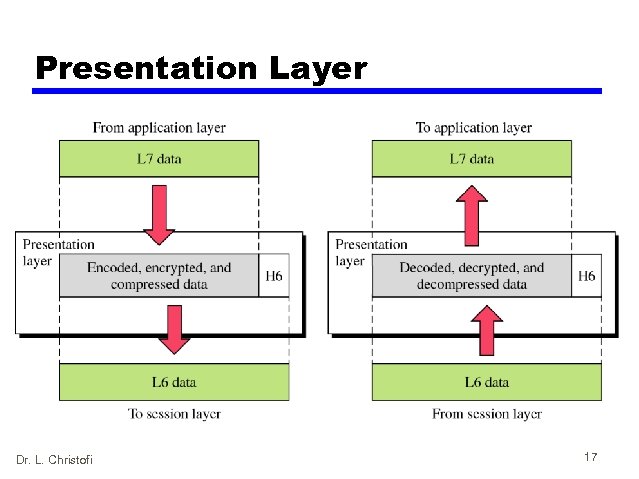
 Presentation Layer • Functions performed includes: —Translation —Encryption/decryption —Authentication —Compression Dr. L. Christofi 16
Presentation Layer • Functions performed includes: —Translation —Encryption/decryption —Authentication —Compression Dr. L. Christofi 16
 Presentation Layer Dr. L. Christofi 17
Presentation Layer Dr. L. Christofi 17
 Translation • The internal representation of a piece of information might vary enormously from one machine to the other (e. g. one may be using ASCII and the other using EBCDIC) • Therefore translation is require so that the two machines can communicate • Two methods: direct or indirect Dr. L. Christofi 18
Translation • The internal representation of a piece of information might vary enormously from one machine to the other (e. g. one may be using ASCII and the other using EBCDIC) • Therefore translation is require so that the two machines can communicate • Two methods: direct or indirect Dr. L. Christofi 18
 Direct and Indirect Translation • Direct translation performs the translation at the receiver • Indirect translation performs the translation at the sender and at the receiver • The direct method is not acceptable in most cases, because if a computer is communicating with several other computers, it may need several conversion tables • The indirect is recommended by OSI and the recommended model is called abstract syntax notation 1 (ASN. 1) • ASN. 1 not only takes care of translation but also handles other formatting problems such as the diverse nature of data (text, program) and the diversity in data storage (store data in different format) Dr. L. Christofi 19
Direct and Indirect Translation • Direct translation performs the translation at the receiver • Indirect translation performs the translation at the sender and at the receiver • The direct method is not acceptable in most cases, because if a computer is communicating with several other computers, it may need several conversion tables • The indirect is recommended by OSI and the recommended model is called abstract syntax notation 1 (ASN. 1) • ASN. 1 not only takes care of translation but also handles other formatting problems such as the diverse nature of data (text, program) and the diversity in data storage (store data in different format) Dr. L. Christofi 19
 Encryption/Decryption • To assure privacy for transmitting sensitive information • Microwave, satellite and other wireless media cannot be protected from unauthorised reception of the transmission, cable transmission cannot totally avoid that either. • To alter the information before transmitting so that only an authorised receiver can understand it • Encryption means that the sender transforms the original information to another form and sends the resulting message out over the network • Decryption reverses the encryption process in order to transform the message back to its original form Dr. L. Christofi 20
Encryption/Decryption • To assure privacy for transmitting sensitive information • Microwave, satellite and other wireless media cannot be protected from unauthorised reception of the transmission, cable transmission cannot totally avoid that either. • To alter the information before transmitting so that only an authorised receiver can understand it • Encryption means that the sender transforms the original information to another form and sends the resulting message out over the network • Decryption reverses the encryption process in order to transform the message back to its original form Dr. L. Christofi 20
 Encryption/Decryption Methods • Conventional Methods: the encryption key (Ke) and the decryption key (Kd) are the same and secret • Public Key Methods: every user has the same encryption algorithm and key, however, the decryption algorithm and key are kept secret Dr. L. Christofi 21
Encryption/Decryption Methods • Conventional Methods: the encryption key (Ke) and the decryption key (Kd) are the same and secret • Public Key Methods: every user has the same encryption algorithm and key, however, the decryption algorithm and key are kept secret Dr. L. Christofi 21
 Conventional Method • Can be divided into two categories: — Character-level encryption — Bit-level encryption • There are two methods in character-level encryption: — Substitutional — Transpositional Dr. L. Christofi 22
Conventional Method • Can be divided into two categories: — Character-level encryption — Bit-level encryption • There are two methods in character-level encryption: — Substitutional — Transpositional Dr. L. Christofi 22
 Substitutional Character-level Encryption • The simplest form of ciphering • In mono-alphabetic substitution, also known as Caesar Cipher, each character is replaced by another character in the set • The mono-alphabetic encryption algorithm simply adds a number to the ASCII code of the character; and the decryption algorithm simply subtracts the same number • Mono-alphabetic substitution is very simple and can be broken easily Dr. L. Christofi 23
Substitutional Character-level Encryption • The simplest form of ciphering • In mono-alphabetic substitution, also known as Caesar Cipher, each character is replaced by another character in the set • The mono-alphabetic encryption algorithm simply adds a number to the ASCII code of the character; and the decryption algorithm simply subtracts the same number • Mono-alphabetic substitution is very simple and can be broken easily Dr. L. Christofi 23
 Substitutional Character-level Encryption • In poly-alphabetic substitution, each occurrence of a character can have different substitute • One poly-alphabetic encryption technique is to find the position of the character in the text and use that value as the key • It is not very secure as well, even though the words replaced by different characters but their position is still the same; the code can easily be broken by someone with more experience Dr. L. Christofi 24
Substitutional Character-level Encryption • In poly-alphabetic substitution, each occurrence of a character can have different substitute • One poly-alphabetic encryption technique is to find the position of the character in the text and use that value as the key • It is not very secure as well, even though the words replaced by different characters but their position is still the same; the code can easily be broken by someone with more experience Dr. L. Christofi 24
 Transpositional Character-level Encryption • Transpositional encryption is a more secure method in which the characters retain their plaintext form but change their positions to create the ciphertext • The text is organised into a 2 -dimensional table and the columns are interchanged according to a key • The key defines which columns should be swapped • Again this encryption is not very secure either, one can still break it through trial and error Dr. L. Christofi 25
Transpositional Character-level Encryption • Transpositional encryption is a more secure method in which the characters retain their plaintext form but change their positions to create the ciphertext • The text is organised into a 2 -dimensional table and the columns are interchanged according to a key • The key defines which columns should be swapped • Again this encryption is not very secure either, one can still break it through trial and error Dr. L. Christofi 25
 Bit-level Encryption • Data as text, graphics, audio, or video are first divided into blocks of bits, then altered by — encoding/decoding — permutation — exclusive OR — rotation — others Dr. L. Christofi 26
Bit-level Encryption • Data as text, graphics, audio, or video are first divided into blocks of bits, then altered by — encoding/decoding — permutation — exclusive OR — rotation — others Dr. L. Christofi 26
 Public Key Encryption • In conventional method, the decryption algorithm is always the inverse of the encryption algorithm and uses the same key • Anyone who knows the encryption algorithm and key can deduce the decryption algorithm • Security can only be assured only if the entire process is kept secret • In public key, anyone can encrypt information but only an authorised receiver can decrypt it • The decryption algorithm is designed in such a way that it is not the inverse of the encryption algorithm • Figure 23. 21 shows the idea; every customer can use them but the decryption algorithm and key are kept secret and used only by the bank Dr. L. Christofi 27
Public Key Encryption • In conventional method, the decryption algorithm is always the inverse of the encryption algorithm and uses the same key • Anyone who knows the encryption algorithm and key can deduce the decryption algorithm • Security can only be assured only if the entire process is kept secret • In public key, anyone can encrypt information but only an authorised receiver can decrypt it • The decryption algorithm is designed in such a way that it is not the inverse of the encryption algorithm • Figure 23. 21 shows the idea; every customer can use them but the decryption algorithm and key are kept secret and used only by the bank Dr. L. Christofi 27
 Authentication • Means verifying the identity of a sender • There are many methods, only digital signature will be discuss here • Digital signature is based on public key encryption/decryption • See Figure 23. 25 to get an idea of how digital signature works. • If the customer claims never have made such a transaction, the bank can take C 1 out of its file and apply Kp-2 (public key) to it to show that it creates P. This decryption is not possible unless the customer had originally applied Ks-1 (secret key) to P to create C 1 Dr. L. Christofi 28
Authentication • Means verifying the identity of a sender • There are many methods, only digital signature will be discuss here • Digital signature is based on public key encryption/decryption • See Figure 23. 25 to get an idea of how digital signature works. • If the customer claims never have made such a transaction, the bank can take C 1 out of its file and apply Kp-2 (public key) to it to show that it creates P. This decryption is not possible unless the customer had originally applied Ks-1 (secret key) to P to create C 1 Dr. L. Christofi 28
 Compression • Reduces the number of bits sent • Becomes important when data that are not pure text such as audio and video are send • Can be divided into two broad categories: — lossless — lossy Dr. L. Christofi 29
Compression • Reduces the number of bits sent • Becomes important when data that are not pure text such as audio and video are send • Can be divided into two broad categories: — lossless — lossy Dr. L. Christofi 29
 Lossless Compression • The compressing and decompressing algorithms are usually the inverse of each other • After decompressing, we will get the exact data as they were before compressing • Some of the techniques used in lossless compression: — Run-length encoding: when data contain strings of repeated symbols, the strings can be replaced by a special marker, followed by the repeated symbol, followed by the number of occurrences (see Figure 23. 27) Dr. L. Christofi 30
Lossless Compression • The compressing and decompressing algorithms are usually the inverse of each other • After decompressing, we will get the exact data as they were before compressing • Some of the techniques used in lossless compression: — Run-length encoding: when data contain strings of repeated symbols, the strings can be replaced by a special marker, followed by the repeated symbol, followed by the number of occurrences (see Figure 23. 27) Dr. L. Christofi 30
 Lossless Compression — Statistical compression: uses short codes for frequent symbols and long codes for infrequent symbols — Relative compression: when there is little difference between consecutive frames, only the difference between the consecutive frames are send instead of the entire frame Dr. L. Christofi 31
Lossless Compression — Statistical compression: uses short codes for frequent symbols and long codes for infrequent symbols — Relative compression: when there is little difference between consecutive frames, only the difference between the consecutive frames are send instead of the entire frame Dr. L. Christofi 31
 Lossy Compression • The decompressed information does not produce exactly the same information as the original but something very close • In video transmission, if an image does not have sharp discontinuities, after transformation to a mathematical expression, most of the information is contained in the first few terms • Using the terms sent, it is possible to reproduce the original frame with enough accuracy • Some methods are: — Joint photographic experts group (JPEG): for pictures and graphics — Motion picture experts group (MPEG): for video Dr. L. Christofi 32
Lossy Compression • The decompressed information does not produce exactly the same information as the original but something very close • In video transmission, if an image does not have sharp discontinuities, after transformation to a mathematical expression, most of the information is contained in the first few terms • Using the terms sent, it is possible to reproduce the original frame with enough accuracy • Some methods are: — Joint photographic experts group (JPEG): for pictures and graphics — Motion picture experts group (MPEG): for video Dr. L. Christofi 32
 Application Layer • Contains whatever functions are required by the user • No standardisation in general is possible • However, ITU-T has recognised some common applications for which standardisation is possible. Two of them are: — Message Handling System (MHS) — File Transfer, Access, and Management (FTAM) Dr. L. Christofi 33
Application Layer • Contains whatever functions are required by the user • No standardisation in general is possible • However, ITU-T has recognised some common applications for which standardisation is possible. Two of them are: — Message Handling System (MHS) — File Transfer, Access, and Management (FTAM) Dr. L. Christofi 33
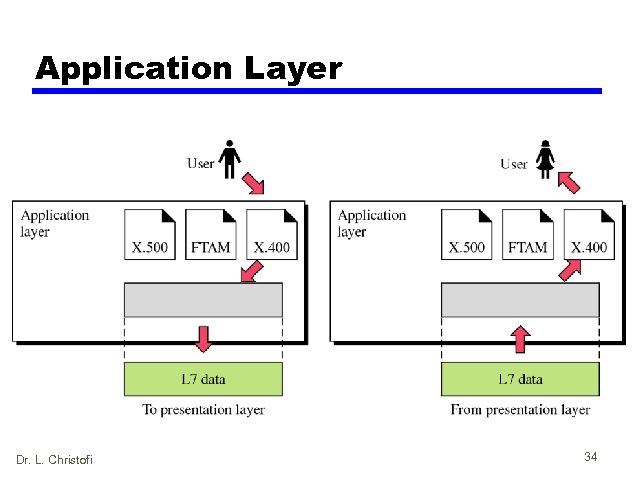 Application Layer Dr. L. Christofi 34
Application Layer Dr. L. Christofi 34
 Message Handling System (MHS) • Is the OSI protocol that underlies electronic mail and store-and-forward handling • Is the system used to send any message that can be delivered in a store-and-forward manner • Store-and-forward: instead of opening an active channel between the sender and receiver, the protocol provides a delivery service that forwards the message when a link becomes available Dr. L. Christofi 35
Message Handling System (MHS) • Is the OSI protocol that underlies electronic mail and store-and-forward handling • Is the system used to send any message that can be delivered in a store-and-forward manner • Store-and-forward: instead of opening an active channel between the sender and receiver, the protocol provides a delivery service that forwards the message when a link becomes available Dr. L. Christofi 35
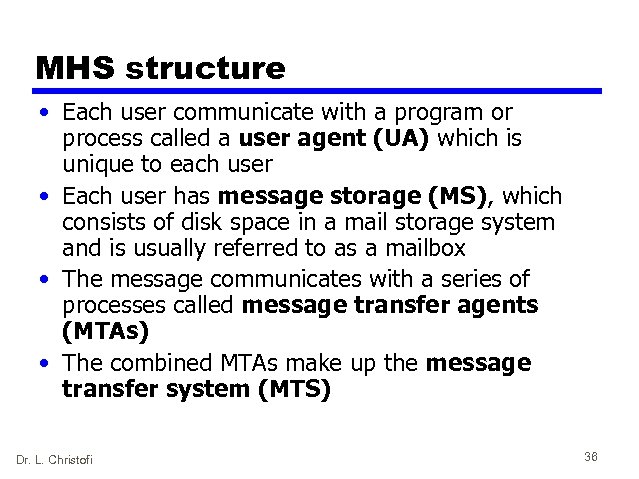 MHS structure • Each user communicate with a program or process called a user agent (UA) which is unique to each user • Each user has message storage (MS), which consists of disk space in a mail storage system and is usually referred to as a mailbox • The message communicates with a series of processes called message transfer agents (MTAs) • The combined MTAs make up the message transfer system (MTS) Dr. L. Christofi 36
MHS structure • Each user communicate with a program or process called a user agent (UA) which is unique to each user • Each user has message storage (MS), which consists of disk space in a mail storage system and is usually referred to as a mailbox • The message communicates with a series of processes called message transfer agents (MTAs) • The combined MTAs make up the message transfer system (MTS) Dr. L. Christofi 36
 File Transfer, Access, and Management (FTAM) • It is used to — transfer (copy) — access (read, write, or modify) — manage (control) files • To allow the interaction of different file systems, it uses the concept of virtual files and virtual filestores • A virtual filestore is a non implementation-specific model for files and databases that can be used as an intermediary for file transfer, access, and management • Each transaction requires an initiator and responder Dr. L. Christofi 37
File Transfer, Access, and Management (FTAM) • It is used to — transfer (copy) — access (read, write, or modify) — manage (control) files • To allow the interaction of different file systems, it uses the concept of virtual files and virtual filestores • A virtual filestore is a non implementation-specific model for files and databases that can be used as an intermediary for file transfer, access, and management • Each transaction requires an initiator and responder Dr. L. Christofi 37
 References • W. Stalling, Local and Metropolitan Area Networks, 6 th edition, Prentice Hall, 2000 • B. A. Forouzan, Data Communications and Networking, 3 rd edition, Mc. Graw-Hill, 2004 • W. Stallings, Data and Computer Communications, 7 th edition, Prentice Hall, 2004 • F. Halsall, Data Communications, Computer Networks and Open Systems, 4 th edition, Addison Wesley, 1995 Dr. L. Christofi 38
References • W. Stalling, Local and Metropolitan Area Networks, 6 th edition, Prentice Hall, 2000 • B. A. Forouzan, Data Communications and Networking, 3 rd edition, Mc. Graw-Hill, 2004 • W. Stallings, Data and Computer Communications, 7 th edition, Prentice Hall, 2004 • F. Halsall, Data Communications, Computer Networks and Open Systems, 4 th edition, Addison Wesley, 1995 Dr. L. Christofi 38


