fcabb36076103fa71dc3bd4defe76309.ppt
- Количество слайдов: 24
 “Limiting electronic fraud through an Information Security Management System (ISMS): An Introduction to ISO 27001" Presented to the ICGFM Annual Conference May 2006 James St. Clair Senior Manager Grant Thornton LLP Global Public Sector
“Limiting electronic fraud through an Information Security Management System (ISMS): An Introduction to ISO 27001" Presented to the ICGFM Annual Conference May 2006 James St. Clair Senior Manager Grant Thornton LLP Global Public Sector
 Disclaimer The views expressed do not necessarily reflect the views of Grant Thornton LLP
Disclaimer The views expressed do not necessarily reflect the views of Grant Thornton LLP
 Areas of Discussion • • • Global trends in Electronic Finance (E-Finance) Risks to E-Finance Establishing a policy framework Overview of Information Security Management Questions?
Areas of Discussion • • • Global trends in Electronic Finance (E-Finance) Risks to E-Finance Establishing a policy framework Overview of Information Security Management Questions?
 Presentation Objectives • Familiarize the audience with the pervasiveness of E-Finance • Discuss how E-Finance is vulnerable • Outline steps to implement a framework to limit risk • Discuss the specifics of an Information Security Management System
Presentation Objectives • Familiarize the audience with the pervasiveness of E-Finance • Discuss how E-Finance is vulnerable • Outline steps to implement a framework to limit risk • Discuss the specifics of an Information Security Management System
 The Growth of Electronic Finance
The Growth of Electronic Finance
 Electronic Finance is now the world standard • E-Finance consists of four primary categories: – – Electronic Funds Transfer (EFT) Electronic Benefits Transfers (EBT) Electronic Data Interchange (EDI) Electronic Trade Confirmations (ETC) • Additionally, the communications channels used for E-Finance have grown – Home PCs – E-Banking – Phones and PDAs
Electronic Finance is now the world standard • E-Finance consists of four primary categories: – – Electronic Funds Transfer (EFT) Electronic Benefits Transfers (EBT) Electronic Data Interchange (EDI) Electronic Trade Confirmations (ETC) • Additionally, the communications channels used for E-Finance have grown – Home PCs – E-Banking – Phones and PDAs
 Growth of E-Finance has been tremendous • E-Finance accounts for over $2 trillion a day • Percentage of banking online has risen from 5% to 50% in 5 years • Number of connect countries and individuals has exploded globally – Internet availability in developing countries – 90% penetration of mobile phone markets – Wireless applications for daily business • Proliferation of e-credit mechanisms
Growth of E-Finance has been tremendous • E-Finance accounts for over $2 trillion a day • Percentage of banking online has risen from 5% to 50% in 5 years • Number of connect countries and individuals has exploded globally – Internet availability in developing countries – 90% penetration of mobile phone markets – Wireless applications for daily business • Proliferation of e-credit mechanisms
 The Risks to Electronic Finance
The Risks to Electronic Finance
 Risks to E-Finance have also grown explosively • Sheer number of global internet users have created a "wild west" for conducting business – "Open" nature of the Internet now its biggest flaw • Tremendous growth in the technology to create financial havoc – Data and records theft that used to take days can be reduced to minutes • Lack of appreciation in how accessible data can really be – What is your risk?
Risks to E-Finance have also grown explosively • Sheer number of global internet users have created a "wild west" for conducting business – "Open" nature of the Internet now its biggest flaw • Tremendous growth in the technology to create financial havoc – Data and records theft that used to take days can be reduced to minutes • Lack of appreciation in how accessible data can really be – What is your risk?
 Primary types of threats • Electronic Fraud – Identity theft – Access manipulation • Security Breaches – Hacking – Viruses and "spy-ware"
Primary types of threats • Electronic Fraud – Identity theft – Access manipulation • Security Breaches – Hacking – Viruses and "spy-ware"
 Legal and Policy framework for Information Security
Legal and Policy framework for Information Security
 Policy and Law are the first step to limiting risk • Legal framework – Countries and organizations have been active in developing the legal framework needed to prosecute electronic crime • OECD • UN • OAS – Most importantly, efforts are made to enforce the laws once created
Policy and Law are the first step to limiting risk • Legal framework – Countries and organizations have been active in developing the legal framework needed to prosecute electronic crime • OECD • UN • OAS – Most importantly, efforts are made to enforce the laws once created
 Policy and Law are the first step to limiting risk (cont'd) • Policy requirements – Oorganizations must have an adequate policy framework to enforce good security – Policies are clearly understood and enforced and based on applicable law • What should an information security policy framework look like?
Policy and Law are the first step to limiting risk (cont'd) • Policy requirements – Oorganizations must have an adequate policy framework to enforce good security – Policies are clearly understood and enforced and based on applicable law • What should an information security policy framework look like?
 ISO 27001: The framework for an Information Security Management System (ISMS)
ISO 27001: The framework for an Information Security Management System (ISMS)
 ISO/IEC 27001: 2005 - Specification • Specifies requirements for establishing, implementing, and documenting Information Security Management Systems (ISMS) • Specifies requirements for security controls to be implemented according to the needs of individual organizations • Consists of 11 control sections, 39 control objectives, and 133 controls • Is aligned with ISO/IEC 17799: 2005 Source: BSI America
ISO/IEC 27001: 2005 - Specification • Specifies requirements for establishing, implementing, and documenting Information Security Management Systems (ISMS) • Specifies requirements for security controls to be implemented according to the needs of individual organizations • Consists of 11 control sections, 39 control objectives, and 133 controls • Is aligned with ISO/IEC 17799: 2005 Source: BSI America
 Development of ISO/IEC 270001 "family" of standards ISO/IEC Standard Description 27000 Vocabulary and definitions 27001 Specification (BS 7799 -2) Issued October 2005 27002 Code of Practice (ISO 17799: 2005) 27003 Implementation Guidance 27004 Metrics and Measurement 27005 Risk Management (BS 7799 -3) Source: BSI America
Development of ISO/IEC 270001 "family" of standards ISO/IEC Standard Description 27000 Vocabulary and definitions 27001 Specification (BS 7799 -2) Issued October 2005 27002 Code of Practice (ISO 17799: 2005) 27003 Implementation Guidance 27004 Metrics and Measurement 27005 Risk Management (BS 7799 -3) Source: BSI America
 Key considerations for ISO/IEC 27001: 2005 • Integrates IT security policy and procedures with existing organization practices • Implements a means for continuous compliance and improvement • Reinforces IT security as part of good corporate governance • Built on internationally accepted standards – Implementation of OECD principles for privacy and security
Key considerations for ISO/IEC 27001: 2005 • Integrates IT security policy and procedures with existing organization practices • Implements a means for continuous compliance and improvement • Reinforces IT security as part of good corporate governance • Built on internationally accepted standards – Implementation of OECD principles for privacy and security
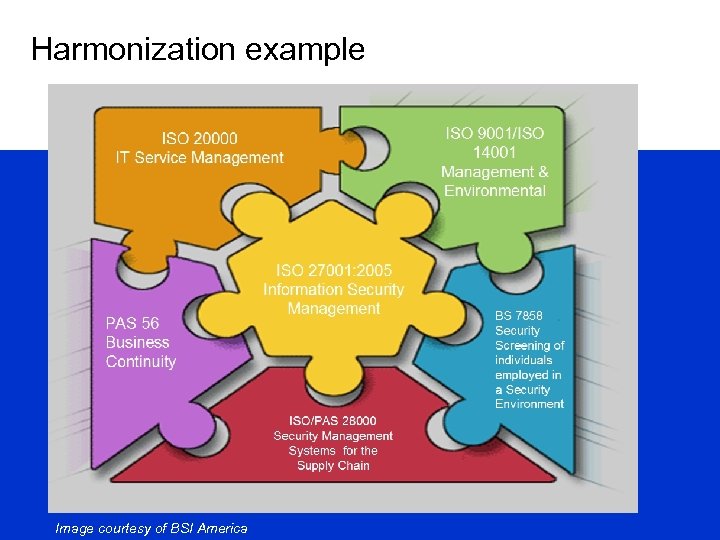 Harmonization example Image courtesy of BSI America
Harmonization example Image courtesy of BSI America
 Growing Acceptance Source: http: //www. xisec. com/
Growing Acceptance Source: http: //www. xisec. com/
 Registration of ISMS Organizations are registered (or certificated) by a Registration Body in accordance with the requirements of a scheme such as exists for ISO 9001, ISO 14001, or ISO/IEC 27001 Registration Bodies (and in some instances auditors) are accredited by a recognized body (e. g. , UKAS, IRCA, ANAB) to conduct assessment and certification to a recognized scheme
Registration of ISMS Organizations are registered (or certificated) by a Registration Body in accordance with the requirements of a scheme such as exists for ISO 9001, ISO 14001, or ISO/IEC 27001 Registration Bodies (and in some instances auditors) are accredited by a recognized body (e. g. , UKAS, IRCA, ANAB) to conduct assessment and certification to a recognized scheme
 Government Benefits of an ISMS • • Helps build a positive image for government agencies, as well as a reinforce a country's political and financial status in the world market Provides satisfaction and confidence that citizens’ information security requirements are being met and privacy is being protected Reduces liability and risk due to implemented or enforced policies and procedures (due diligence) Gain improvement of process efficiency and the management of security costs
Government Benefits of an ISMS • • Helps build a positive image for government agencies, as well as a reinforce a country's political and financial status in the world market Provides satisfaction and confidence that citizens’ information security requirements are being met and privacy is being protected Reduces liability and risk due to implemented or enforced policies and procedures (due diligence) Gain improvement of process efficiency and the management of security costs
 What steps are necessary to implement an ISMS? • An organizational investment – Requires "buy-in" from all members of the organization • Must be implemented with existing Risk management efforts • Make sure you understand legal issues as well as technical
What steps are necessary to implement an ISMS? • An organizational investment – Requires "buy-in" from all members of the organization • Must be implemented with existing Risk management efforts • Make sure you understand legal issues as well as technical
 Questions to ask of your ISMS 1. Has your scope been defined? 2. Who should be involved in developing and maintaining our ISMS? a) Cannot be assigned like another IT project 3. Do IT Security plans exist for all agencies, and are they tested in any format? 4. Has proper resources been allocated?
Questions to ask of your ISMS 1. Has your scope been defined? 2. Who should be involved in developing and maintaining our ISMS? a) Cannot be assigned like another IT project 3. Do IT Security plans exist for all agencies, and are they tested in any format? 4. Has proper resources been allocated?
 Questions? Thank You! James A. St. Clair, CISM Senior Manager Global Public Sector Grant Thornton LLP T 703. 637. 3078 F 703. 837. 4455 C 703. 727. 6332 E Jim. St. Clair@gt. com
Questions? Thank You! James A. St. Clair, CISM Senior Manager Global Public Sector Grant Thornton LLP T 703. 637. 3078 F 703. 837. 4455 C 703. 727. 6332 E Jim. St. Clair@gt. com


