1c4c9a75dda747cf89c511c9f4dec649.ppt
- Количество слайдов: 51
 Lessons from a Sufficiently Rich Model of (Id)entity, Authentication and Authorisation Roger Clarke Xamax Consultancy, Canberra Visiting Professor – Cyberspace Law & Policy Centre @ UNSW and in Computer Science @ ANU http: //www. rogerclarke. com/ID/Id. Model-UT-091026 {. html, . ppt} http: //www. rogerclarke. com/ID/Id. Model. Gloss. html Identity, Privacy and Security Institute (IPSI), Uni Toronto 26 October 2009 Copyright 1987 -2009 1
Lessons from a Sufficiently Rich Model of (Id)entity, Authentication and Authorisation Roger Clarke Xamax Consultancy, Canberra Visiting Professor – Cyberspace Law & Policy Centre @ UNSW and in Computer Science @ ANU http: //www. rogerclarke. com/ID/Id. Model-UT-091026 {. html, . ppt} http: //www. rogerclarke. com/ID/Id. Model. Gloss. html Identity, Privacy and Security Institute (IPSI), Uni Toronto 26 October 2009 Copyright 1987 -2009 1
 We Need a Specialist English-Language Dialect for Discourse on (Id)entity and Authentication AGENDA • • Preliminaries The Model • The Basic Model • • • Identity, Identifier Entity, Entifier Nym (Id)entification Processes • Authentication, but of what? • Authorisation Processes Applications of the Model • • Copyright 1987 -2009 2
We Need a Specialist English-Language Dialect for Discourse on (Id)entity and Authentication AGENDA • • Preliminaries The Model • The Basic Model • • • Identity, Identifier Entity, Entifier Nym (Id)entification Processes • Authentication, but of what? • Authorisation Processes Applications of the Model • • Copyright 1987 -2009 2
 Preliminaries • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them Copyright 1987 -2009 3
Preliminaries • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them Copyright 1987 -2009 3
 Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms Copyright 1987 -2009 4
Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms Copyright 1987 -2009 4
 Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms But existing terms carry a lot of baggage So each term: • requires explicit definition • must be related to other terms in the model Copyright 1987 -2009 5
Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms But existing terms carry a lot of baggage So each term: • requires explicit definition • must be related to other terms in the model Copyright 1987 -2009 5
 Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms But existing terms carry a lot of baggage So each term: • requires explicit definition • must be related to other terms in the model The meaning of each term in the new dialect may conflict with its (many? !) existing usages Copyright 1987 -2009 6
Preliminaries • • • Deep discourse in a domain needs a specialist dialect For this domain, sufficient richness involves c. 50 concepts, and relationships among them 50 neologisms is too much, so let's use existing terms But existing terms carry a lot of baggage So each term: • requires explicit definition • must be related to other terms in the model The meaning of each term in the new dialect may conflict with its (many? !) existing usages Copyright 1987 -2009 6
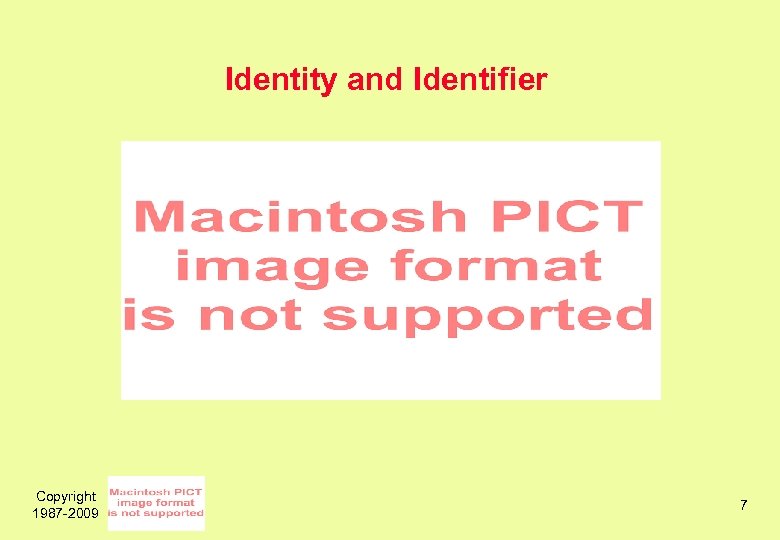 Identity and Identifier Names Codes Roles Copyright 1987 -2009 7
Identity and Identifier Names Codes Roles Copyright 1987 -2009 7
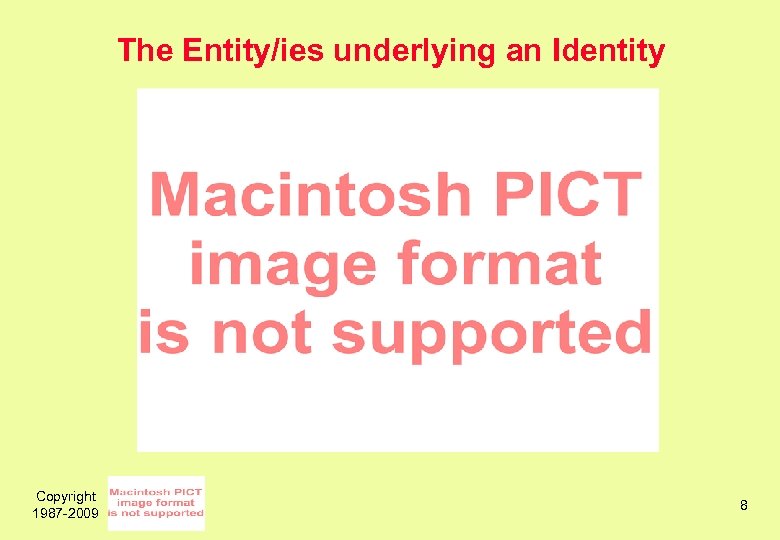 The Entity/ies underlying an Identity Copyright 1987 -2009 8
The Entity/ies underlying an Identity Copyright 1987 -2009 8
 Entity and Entifier Copyright 1987 -2009 9
Entity and Entifier Copyright 1987 -2009 9
 Nymity Copyright 1987 -2009 10
Nymity Copyright 1987 -2009 10
 Nym One or more attributes of an Identity (represented in transactions and records as one or more data-items) sufficient to distinguish that Identity from other instances of its class but not sufficient to enable association with a specific Entity Copyright 1987 -2009 11
Nym One or more attributes of an Identity (represented in transactions and records as one or more data-items) sufficient to distinguish that Identity from other instances of its class but not sufficient to enable association with a specific Entity Copyright 1987 -2009 11
 Nym One or more attributes of an Identity (represented in transactions and records as one or more data-items) sufficient to distinguish that Identity from other instances of its class but not sufficient to enable association with a specific Entity Pseudonym – association is not made, but possible Anonym – association is not possible Copyright 1987 -2009 12
Nym One or more attributes of an Identity (represented in transactions and records as one or more data-items) sufficient to distinguish that Identity from other instances of its class but not sufficient to enable association with a specific Entity Pseudonym – association is not made, but possible Anonym – association is not possible Copyright 1987 -2009 12
 Nymality is Normality aka ('also-known-as'), alias, avatar, character, nickname, nom de guerre, nom de plume, manifestation, moniker, personality, profile, pseudonym, pseudo-identifier, sobriquet, stage-name Cyberpace has adopted those and spawned more: account, avatar, handle, nick, persona, . . . Copyright 1987 -2009 13
Nymality is Normality aka ('also-known-as'), alias, avatar, character, nickname, nom de guerre, nom de plume, manifestation, moniker, personality, profile, pseudonym, pseudo-identifier, sobriquet, stage-name Cyberpace has adopted those and spawned more: account, avatar, handle, nick, persona, . . . Copyright 1987 -2009 13
 Common Nymous Transactions • • • Barter transactions Visits to Enquiry Counters in government agencies Telephone Enquiries Inspection of publications on library premises Access to Public Documents by electronic means, at a kiosk or over the Internet Copyright 1987 -2009 • • • Cash Transactions, incl. the myriad daily payments for inexpensive goods and services, gambling, road-tolls Voting in secret ballots Treatment at discreet clinics, e. g. for sexually transmitted diseases 14
Common Nymous Transactions • • • Barter transactions Visits to Enquiry Counters in government agencies Telephone Enquiries Inspection of publications on library premises Access to Public Documents by electronic means, at a kiosk or over the Internet Copyright 1987 -2009 • • • Cash Transactions, incl. the myriad daily payments for inexpensive goods and services, gambling, road-tolls Voting in secret ballots Treatment at discreet clinics, e. g. for sexually transmitted diseases 14
 Applications of Pseudonymity • • Epidemiological Research (HIV/AIDS) Financial Exchanges, including dealing in commodities, stocks, shares, derivatives, and foreign currencies Nominee Trading and Ownership Banking Secrecy, incl. ‘Swiss’ / Austrian bank accounts Copyright 1987 -2009 • • Political Speech Artistic Speech Call Centres Counselling Phone-calls with CLI Internet Transactions 'Anonymous' re-mailers Chaumian e. Cash™ 15
Applications of Pseudonymity • • Epidemiological Research (HIV/AIDS) Financial Exchanges, including dealing in commodities, stocks, shares, derivatives, and foreign currencies Nominee Trading and Ownership Banking Secrecy, incl. ‘Swiss’ / Austrian bank accounts Copyright 1987 -2009 • • Political Speech Artistic Speech Call Centres Counselling Phone-calls with CLI Internet Transactions 'Anonymous' re-mailers Chaumian e. Cash™ 15
 “. . . the thing that says the government says I'm over 18. . . You can prove who you are to a third party and then, in actual usage, they don't know who you are. “A lot of the previous designs had the idea that if you authenticated, then you gave up privacy. There are lots of cases where you want to be authentic but not give up your privacy”. Financial Times, 19 Feb 2006 Interview with Bill Gates re MS Identity Metasystem Architecture and Info. Card Copyright 1987 -2009 16
“. . . the thing that says the government says I'm over 18. . . You can prove who you are to a third party and then, in actual usage, they don't know who you are. “A lot of the previous designs had the idea that if you authenticated, then you gave up privacy. There are lots of cases where you want to be authentic but not give up your privacy”. Financial Times, 19 Feb 2006 Interview with Bill Gates re MS Identity Metasystem Architecture and Info. Card Copyright 1987 -2009 16
 Copyright 1987 -2009 17
Copyright 1987 -2009 17
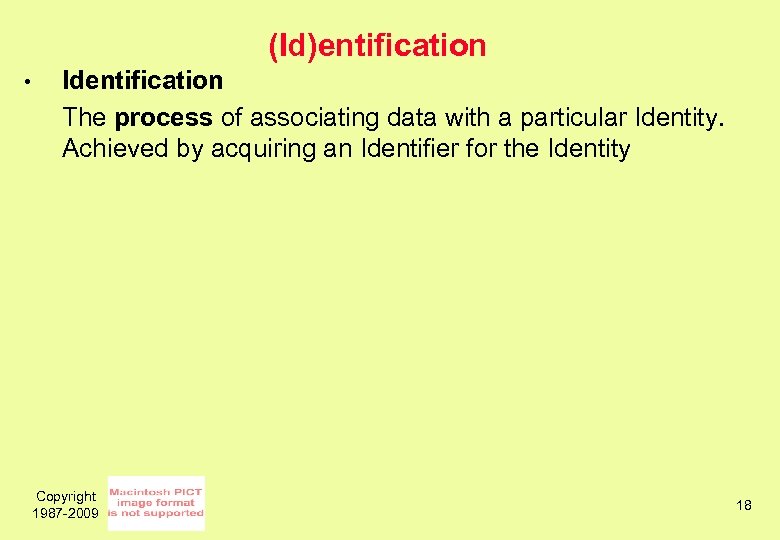 (Id)entification • Identification The process of associating data with a particular Identity. Achieved by acquiring an Identifier for the Identity Copyright 1987 -2009 18
(Id)entification • Identification The process of associating data with a particular Identity. Achieved by acquiring an Identifier for the Identity Copyright 1987 -2009 18
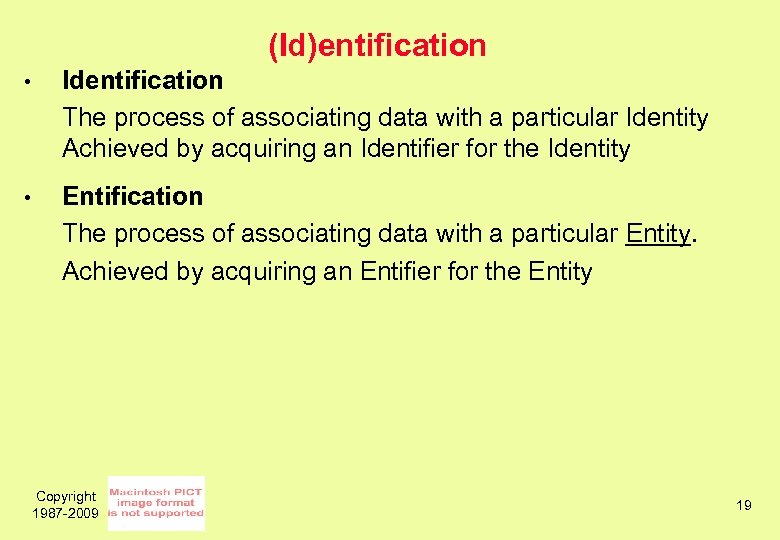 (Id)entification • Identification The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Entification The process of associating data with a particular Entity. Achieved by acquiring an Entifier for the Entity Copyright 1987 -2009 19
(Id)entification • Identification The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Entification The process of associating data with a particular Entity. Achieved by acquiring an Entifier for the Entity Copyright 1987 -2009 19
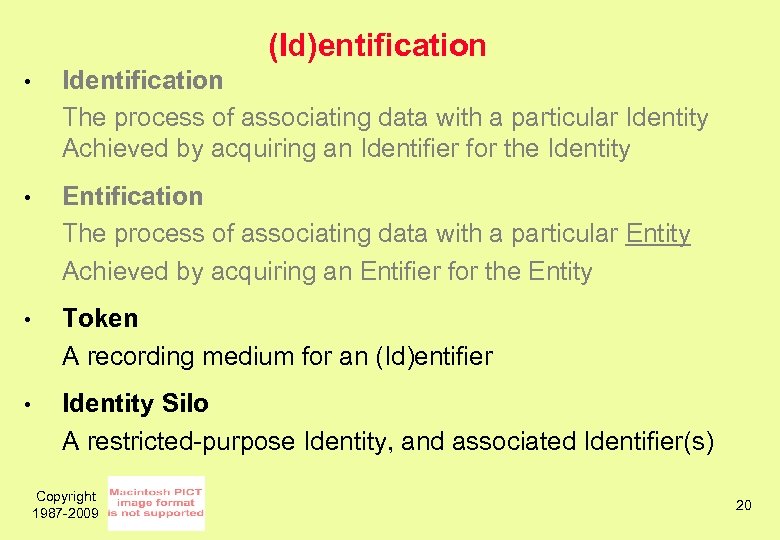 (Id)entification • Identification The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Entification The process of associating data with a particular Entity Achieved by acquiring an Entifier for the Entity • Token A recording medium for an (Id)entifier • Identity Silo A restricted-purpose Identity, and associated Identifier(s) Copyright 1987 -2009 20
(Id)entification • Identification The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Entification The process of associating data with a particular Entity Achieved by acquiring an Entifier for the Entity • Token A recording medium for an (Id)entifier • Identity Silo A restricted-purpose Identity, and associated Identifier(s) Copyright 1987 -2009 20
 Authentication of Assertions • • Authentication: A process that establishes a level of confidence in an Assertion: a proposition. . . of some kind. . . made by some party Copyright 1987 -2009 21
Authentication of Assertions • • Authentication: A process that establishes a level of confidence in an Assertion: a proposition. . . of some kind. . . made by some party Copyright 1987 -2009 21
 Authentication of Assertions • • Authentication: A process that establishes a level of confidence in an Assertion: a proposition. . . of some kind. . . made by some party • Authenticator: • Credential: • EOI: Copyright 1987 -2009 evidence relating to an Assertion a physical or digital Authenticator an Authenticator for Identity Assertions 22
Authentication of Assertions • • Authentication: A process that establishes a level of confidence in an Assertion: a proposition. . . of some kind. . . made by some party • Authenticator: • Credential: • EOI: Copyright 1987 -2009 evidence relating to an Assertion a physical or digital Authenticator an Authenticator for Identity Assertions 22
 Categories of Assertions Relevant to e. Business • • • Copyright 1987 -2009 About Real-World Facts About Data Quality (accuracy, timeliness, . . . ) About Value About Location About Documents • • About Attributes About Principal-Agent Relationships About Identities About Entities 23
Categories of Assertions Relevant to e. Business • • • Copyright 1987 -2009 About Real-World Facts About Data Quality (accuracy, timeliness, . . . ) About Value About Location About Documents • • About Attributes About Principal-Agent Relationships About Identities About Entities 23
 Value Assertion Value is transferred to/from an (Id)entity or Nym ‘This bone‘s been aged in loam for three months’ Copyright 1987 -2009 24
Value Assertion Value is transferred to/from an (Id)entity or Nym ‘This bone‘s been aged in loam for three months’ Copyright 1987 -2009 24
 A Defining Aphorism of Cyberspace The New Yorker 5 July 1993 Copyright 1987 -2009 25
A Defining Aphorism of Cyberspace The New Yorker 5 July 1993 Copyright 1987 -2009 25
 Value Assertion Value is transferred to/from an (Id)entity or Nym ‘This bone‘s been aged in loam for three months’ Authentication of Value Assertions For Goods For Cash • Inspect them Release the Goods only: • Get them put into • For Cash On Delivery Escrow, for release by • After Clearing the Cheque the Agent only when all • Against a Credit-Card conditions have been Authorisation fulfilled • After a Debit-Card Transaction Copyright 1987 -2009 26
Value Assertion Value is transferred to/from an (Id)entity or Nym ‘This bone‘s been aged in loam for three months’ Authentication of Value Assertions For Goods For Cash • Inspect them Release the Goods only: • Get them put into • For Cash On Delivery Escrow, for release by • After Clearing the Cheque the Agent only when all • Against a Credit-Card conditions have been Authorisation fulfilled • After a Debit-Card Transaction Copyright 1987 -2009 26
 Attribute Assertion • An Identity or Nym has a particular Attribute: • Age / Do. B before or after some Threshhold • Disability, Health Condition, War Service • Professional, Trade (or Dog) Qualification Authentication of Attribute Assertions • • • Copyright 1987 -2009 ID-Card and Do. B (may or may not record ID) Bearer Credential (ticket, disabled-driver sticker) Attribute Certificates (with or without ID) 27
Attribute Assertion • An Identity or Nym has a particular Attribute: • Age / Do. B before or after some Threshhold • Disability, Health Condition, War Service • Professional, Trade (or Dog) Qualification Authentication of Attribute Assertions • • • Copyright 1987 -2009 ID-Card and Do. B (may or may not record ID) Bearer Credential (ticket, disabled-driver sticker) Attribute Certificates (with or without ID) 27
 Which Assertions Matter? • Copyright 1987 -2009 Utilise Risk Assessment techniques to determine: • Which Assertions? • What level/strength of Authentication? 28
Which Assertions Matter? • Copyright 1987 -2009 Utilise Risk Assessment techniques to determine: • Which Assertions? • What level/strength of Authentication? 28
 Australian Government e-Authentication Framework (AGAF) http: //www. finance. gov. au/e-government/security-and-authentication/authentication-framework. html • • • Copyright 1987 -2009 Decide what statements need to be authenticated Use risk assessment techniques in order to decide on the level of assurance needed From among the alternative e-authentication mechanisms, select an appropriate approach Assess the impact on public policy concerns such as privacy and social equity Implement Evaluate 29
Australian Government e-Authentication Framework (AGAF) http: //www. finance. gov. au/e-government/security-and-authentication/authentication-framework. html • • • Copyright 1987 -2009 Decide what statements need to be authenticated Use risk assessment techniques in order to decide on the level of assurance needed From among the alternative e-authentication mechanisms, select an appropriate approach Assess the impact on public policy concerns such as privacy and social equity Implement Evaluate 29
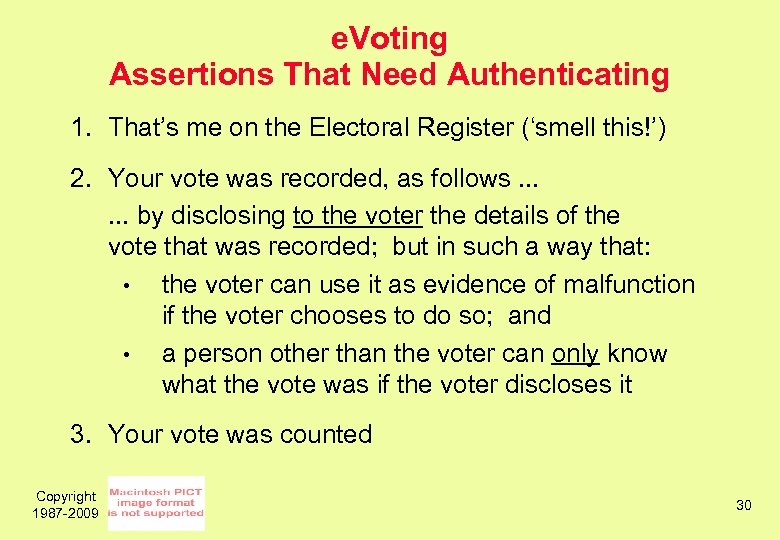 e. Voting Assertions That Need Authenticating 1. That’s me on the Electoral Register (‘smell this!’) 2. Your vote was recorded, as follows. . . by disclosing to the voter the details of the vote that was recorded; but in such a way that: • the voter can use it as evidence of malfunction if the voter chooses to do so; and • a person other than the voter can only know what the vote was if the voter discloses it 3. Your vote was counted Copyright 1987 -2009 30
e. Voting Assertions That Need Authenticating 1. That’s me on the Electoral Register (‘smell this!’) 2. Your vote was recorded, as follows. . . by disclosing to the voter the details of the vote that was recorded; but in such a way that: • the voter can use it as evidence of malfunction if the voter chooses to do so; and • a person other than the voter can only know what the vote was if the voter discloses it 3. Your vote was counted Copyright 1987 -2009 30
 Copyright 1987 -2009 Authorisation 31
Copyright 1987 -2009 Authorisation 31
 Copyright 1987 -2009 Authorisation 32
Copyright 1987 -2009 Authorisation 32
 Authorisation: Access Control Copyright 1987 -2009 33
Authorisation: Access Control Copyright 1987 -2009 33
 Applications of the Model • • Copyright 1987 -2009 Goods Packaging Animals Vehicles Devices Software Organisations Humans 34
Applications of the Model • • Copyright 1987 -2009 Goods Packaging Animals Vehicles Devices Software Organisations Humans 34
 Applications to Humans and Proxies for Humans • • Copyright 1987 -2009 Goods Packaging Animals Vehicles Devices Software Organisations Humans • Personal Goods • Pets Personal Vehicles Personal Devices Reg-Codes, IP-Addresses Organisational Roles Biometrics, Embedded Chips • • • 35
Applications to Humans and Proxies for Humans • • Copyright 1987 -2009 Goods Packaging Animals Vehicles Devices Software Organisations Humans • Personal Goods • Pets Personal Vehicles Personal Devices Reg-Codes, IP-Addresses Organisational Roles Biometrics, Embedded Chips • • • 35
 A Sample Personal Device – The Mobile Phone • Entifier for the Product – model-name, model-number Copyright 1987 -2009 36
A Sample Personal Device – The Mobile Phone • Entifier for the Product – model-name, model-number Copyright 1987 -2009 36
 A Sample Personal Device – The Mobile Phone • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Copyright 1987 -2009 37
A Sample Personal Device – The Mobile Phone • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Copyright 1987 -2009 37
 A Sample Personal Device – The Mobile Phone • • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Identifier for the Persona – Serial-Number of a chip, the International Mobile Subscriber Identity (IMSI) • Subscriber Identity Module (SIM) – GSM / UMTS • Removable User Identity Module (R-UIM) or CDMA Subscriber Identity Module (CSIM) – CDMA • Universal Subscriber Identity Module (USIM) – 3 G Copyright 1987 -2009 38
A Sample Personal Device – The Mobile Phone • • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Identifier for the Persona – Serial-Number of a chip, the International Mobile Subscriber Identity (IMSI) • Subscriber Identity Module (SIM) – GSM / UMTS • Removable User Identity Module (R-UIM) or CDMA Subscriber Identity Module (CSIM) – CDMA • Universal Subscriber Identity Module (USIM) – 3 G Copyright 1987 -2009 38
 A Sample Personal Device – The Mobile Phone • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Identifier for the Persona – Serial-Number of a chip, the International Mobile Subscriber Identity (IMSI) • Subscriber Identity Module (SIM) – GSM / UMTS • Removable User Identity Module (R-UIM) or CDMA Subscriber Identity Module (CSIM) – CDMA • Universal Subscriber Identity Module (USIM) – 3 G Proxy-(Id)entifier – MAC Address / NICId, or IP-Address Copyright 1987 -2009 39
A Sample Personal Device – The Mobile Phone • • Entifier for the Product – model-name, model-number Entifier for the Handset – Serial-Number of the device • Mobile Equipment Identity (IMEI) – GSM / UMTS • Electronic Serial Number (ESN) or Mobile Equipment Identifier (MEID) – CDMA Identifier for the Persona – Serial-Number of a chip, the International Mobile Subscriber Identity (IMSI) • Subscriber Identity Module (SIM) – GSM / UMTS • Removable User Identity Module (R-UIM) or CDMA Subscriber Identity Module (CSIM) – CDMA • Universal Subscriber Identity Module (USIM) – 3 G Proxy-(Id)entifier – MAC Address / NICId, or IP-Address Copyright 1987 -2009 39
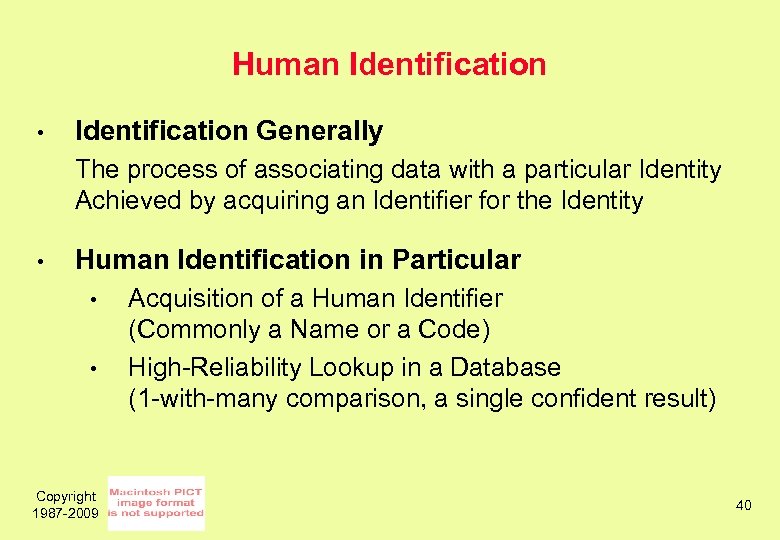 Human Identification • Identification Generally The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Human Identification in Particular • • Copyright 1987 -2009 Acquisition of a Human Identifier (Commonly a Name or a Code) High-Reliability Lookup in a Database (1 -with-many comparison, a single confident result) 40
Human Identification • Identification Generally The process of associating data with a particular Identity Achieved by acquiring an Identifier for the Identity • Human Identification in Particular • • Copyright 1987 -2009 Acquisition of a Human Identifier (Commonly a Name or a Code) High-Reliability Lookup in a Database (1 -with-many comparison, a single confident result) 40
 Human Identity Authentication • What the Person Knows e. g. mother’s maiden name, Password, PIN • What the Person Has (‘Credentials’) e. g. a Token, such as an ‘ID-Card’, a Ticket e. g. a Digital Token such as “a Digital Signature consistent with the Public Key attested to by a Digital Certificate” Copyright 1987 -2009 41
Human Identity Authentication • What the Person Knows e. g. mother’s maiden name, Password, PIN • What the Person Has (‘Credentials’) e. g. a Token, such as an ‘ID-Card’, a Ticket e. g. a Digital Token such as “a Digital Signature consistent with the Public Key attested to by a Digital Certificate” Copyright 1987 -2009 41
 Human Identity Authentication • What the Person Knows e. g. mother’s maiden name, Password, PIN • What the Person Has (‘Credentials’) e. g. a Token, such as an ‘ID-Card’, a Ticket e. g. a Digital Token such as “a Digital Signature consistent with the Public Key attested to by a Digital Certificate” Human Entity Authentication • • • Copyright 1987 -2009 What the Person Does (Dynamic Biometrics) What the Person Is (Static Biometrics) What the Person Is Now (Imposed Biometrics) 42
Human Identity Authentication • What the Person Knows e. g. mother’s maiden name, Password, PIN • What the Person Has (‘Credentials’) e. g. a Token, such as an ‘ID-Card’, a Ticket e. g. a Digital Token such as “a Digital Signature consistent with the Public Key attested to by a Digital Certificate” Human Entity Authentication • • • Copyright 1987 -2009 What the Person Does (Dynamic Biometrics) What the Person Is (Static Biometrics) What the Person Is Now (Imposed Biometrics) 42
 The Biometric Process Copyright 1987 -2009 43
The Biometric Process Copyright 1987 -2009 43
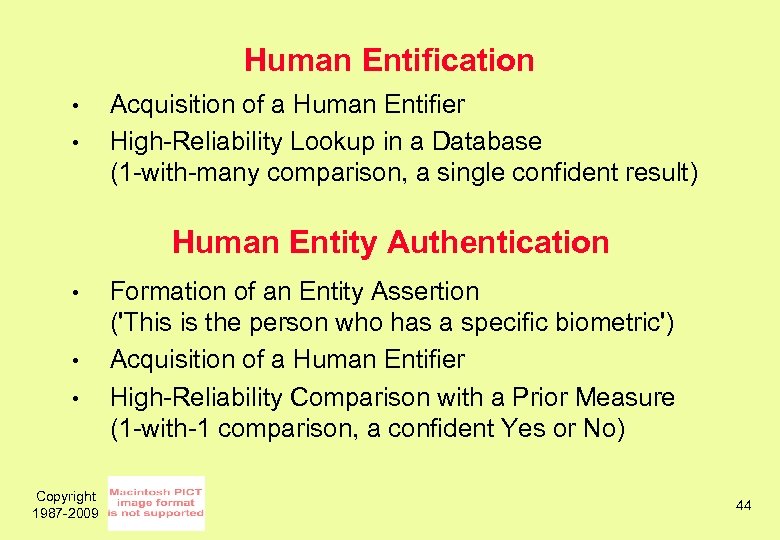 Human Entification • • Acquisition of a Human Entifier High-Reliability Lookup in a Database (1 -with-many comparison, a single confident result) Human Entity Authentication • • • Copyright 1987 -2009 Formation of an Entity Assertion ('This is the person who has a specific biometric') Acquisition of a Human Entifier High-Reliability Comparison with a Prior Measure (1 -with-1 comparison, a confident Yes or No) 44
Human Entification • • Acquisition of a Human Entifier High-Reliability Lookup in a Database (1 -with-many comparison, a single confident result) Human Entity Authentication • • • Copyright 1987 -2009 Formation of an Entity Assertion ('This is the person who has a specific biometric') Acquisition of a Human Entifier High-Reliability Comparison with a Prior Measure (1 -with-1 comparison, a confident Yes or No) 44
 Some Mythologies of the 'Identity Management' Industry • • • That the assertions that need to be authenticated are assertions of identity (cf. fact, value, attribute, agency and location) That biometric identification: • works • is inevitable • doesn’t threaten freedoms That individuals only have • will help much one identity • will help at all in That identity and entity are counter-terrorism the same thing Copyright 1987 -2009 45
Some Mythologies of the 'Identity Management' Industry • • • That the assertions that need to be authenticated are assertions of identity (cf. fact, value, attribute, agency and location) That biometric identification: • works • is inevitable • doesn’t threaten freedoms That individuals only have • will help much one identity • will help at all in That identity and entity are counter-terrorism the same thing Copyright 1987 -2009 45
 C 2 K Policy Imperatives • • • Maximise the use of anonymous transactions (tx) Where anonymity is not an effective option, maximise the use of pseudonymous tx Resist, and reverse, conversion of nymous to identified tx Preclude identified transactions except where functionally necessary, or meaningful, informed consent exists Enable multiple identities for multiple roles Enable the authentication of pseudonyms Provide legal, organisational and technical protections for the link between a pseudonym and the person behind it Resist, and reverse, multiple usage of identifiers Resist, and reverse, the correlation of identifiers Copyright 1987 -2009 46
C 2 K Policy Imperatives • • • Maximise the use of anonymous transactions (tx) Where anonymity is not an effective option, maximise the use of pseudonymous tx Resist, and reverse, conversion of nymous to identified tx Preclude identified transactions except where functionally necessary, or meaningful, informed consent exists Enable multiple identities for multiple roles Enable the authentication of pseudonyms Provide legal, organisational and technical protections for the link between a pseudonym and the person behind it Resist, and reverse, multiple usage of identifiers Resist, and reverse, the correlation of identifiers Copyright 1987 -2009 46
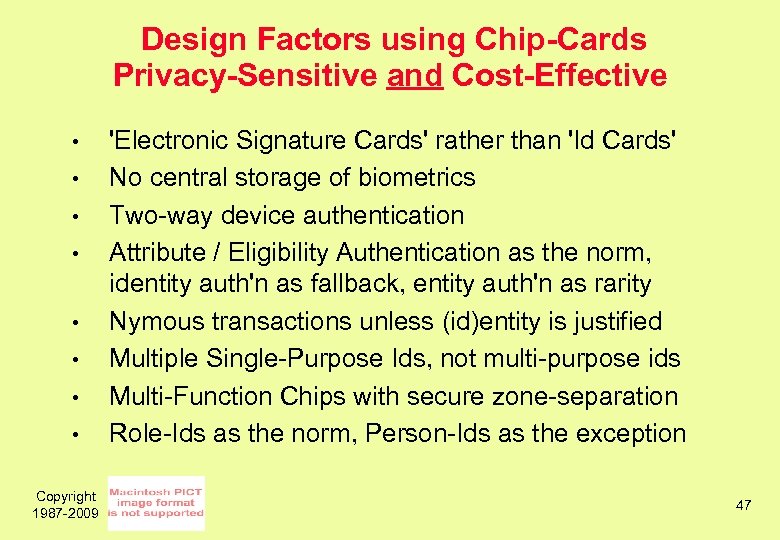 Design Factors using Chip-Cards Privacy-Sensitive and Cost-Effective • • Copyright 1987 -2009 'Electronic Signature Cards' rather than 'Id Cards' No central storage of biometrics Two-way device authentication Attribute / Eligibility Authentication as the norm, identity auth'n as fallback, entity auth'n as rarity Nymous transactions unless (id)entity is justified Multiple Single-Purpose Ids, not multi-purpose ids Multi-Function Chips with secure zone-separation Role-Ids as the norm, Person-Ids as the exception 47
Design Factors using Chip-Cards Privacy-Sensitive and Cost-Effective • • Copyright 1987 -2009 'Electronic Signature Cards' rather than 'Id Cards' No central storage of biometrics Two-way device authentication Attribute / Eligibility Authentication as the norm, identity auth'n as fallback, entity auth'n as rarity Nymous transactions unless (id)entity is justified Multiple Single-Purpose Ids, not multi-purpose ids Multi-Function Chips with secure zone-separation Role-Ids as the norm, Person-Ids as the exception 47
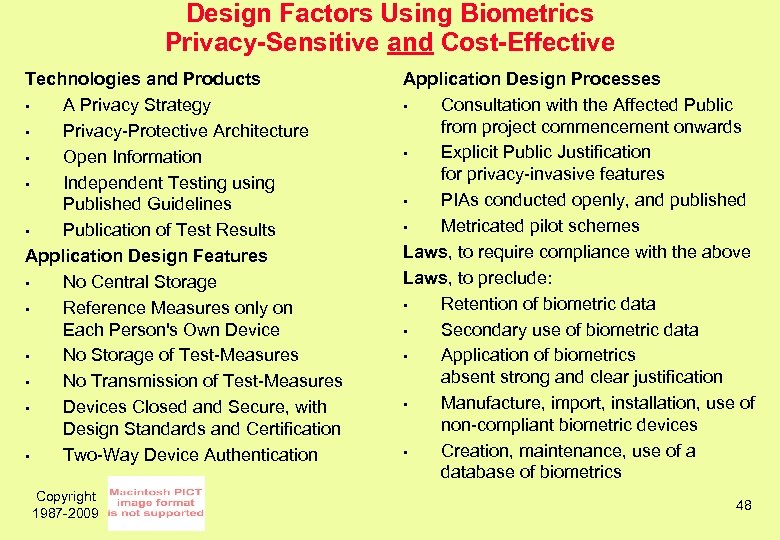 Design Factors Using Biometrics Privacy-Sensitive and Cost-Effective Technologies and Products • A Privacy Strategy • Privacy-Protective Architecture • Open Information • Independent Testing using Published Guidelines • Publication of Test Results Application Design Features • No Central Storage • Reference Measures only on Each Person's Own Device • No Storage of Test-Measures • No Transmission of Test-Measures • Devices Closed and Secure, with Design Standards and Certification • Two-Way Device Authentication Copyright 1987 -2009 Application Design Processes • Consultation with the Affected Public from project commencement onwards • Explicit Public Justification for privacy-invasive features • PIAs conducted openly, and published • Metricated pilot schemes Laws, to require compliance with the above Laws, to preclude: • Retention of biometric data • Secondary use of biometric data • Application of biometrics absent strong and clear justification • Manufacture, import, installation, use of non-compliant biometric devices • Creation, maintenance, use of a database of biometrics 48
Design Factors Using Biometrics Privacy-Sensitive and Cost-Effective Technologies and Products • A Privacy Strategy • Privacy-Protective Architecture • Open Information • Independent Testing using Published Guidelines • Publication of Test Results Application Design Features • No Central Storage • Reference Measures only on Each Person's Own Device • No Storage of Test-Measures • No Transmission of Test-Measures • Devices Closed and Secure, with Design Standards and Certification • Two-Way Device Authentication Copyright 1987 -2009 Application Design Processes • Consultation with the Affected Public from project commencement onwards • Explicit Public Justification for privacy-invasive features • PIAs conducted openly, and published • Metricated pilot schemes Laws, to require compliance with the above Laws, to preclude: • Retention of biometric data • Secondary use of biometric data • Application of biometrics absent strong and clear justification • Manufacture, import, installation, use of non-compliant biometric devices • Creation, maintenance, use of a database of biometrics 48
 We Need a Specialist English-Language Dialect for Discourse on (Id)entity and Authentication AGENDA • • Preliminaries The Model • The Basic Model • • • Identity, Identifier Entity, Entifier Nym (Id)entification Processes • Authentication, but of what? • Authorisation Processes Applications of the Model • • Copyright 1987 -2009 49
We Need a Specialist English-Language Dialect for Discourse on (Id)entity and Authentication AGENDA • • Preliminaries The Model • The Basic Model • • • Identity, Identifier Entity, Entifier Nym (Id)entification Processes • Authentication, but of what? • Authorisation Processes Applications of the Model • • Copyright 1987 -2009 49
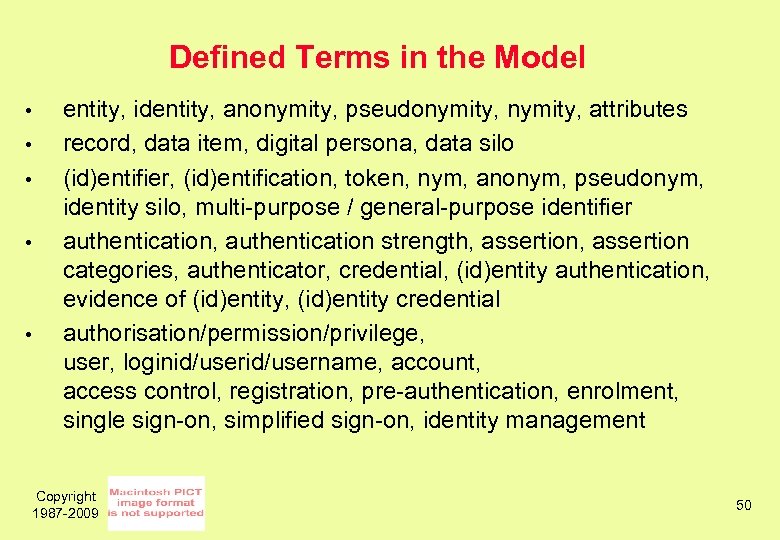 Defined Terms in the Model • • • entity, identity, anonymity, pseudonymity, attributes record, data item, digital persona, data silo (id)entifier, (id)entification, token, nym, anonym, pseudonym, identity silo, multi-purpose / general-purpose identifier authentication, authentication strength, assertion categories, authenticator, credential, (id)entity authentication, evidence of (id)entity, (id)entity credential authorisation/permission/privilege, user, loginid/username, account, access control, registration, pre-authentication, enrolment, single sign-on, simplified sign-on, identity management Copyright 1987 -2009 50
Defined Terms in the Model • • • entity, identity, anonymity, pseudonymity, attributes record, data item, digital persona, data silo (id)entifier, (id)entification, token, nym, anonym, pseudonym, identity silo, multi-purpose / general-purpose identifier authentication, authentication strength, assertion categories, authenticator, credential, (id)entity authentication, evidence of (id)entity, (id)entity credential authorisation/permission/privilege, user, loginid/username, account, access control, registration, pre-authentication, enrolment, single sign-on, simplified sign-on, identity management Copyright 1987 -2009 50
 Lessons from a Sufficiently Rich Model of (Id)entity, Authentication and Authorisation Roger Clarke Xamax Consultancy, Canberra Visiting Professor – Cyberspace Law & Policy Centre @ UNSW and in Computer Science @ ANU http: //www. rogerclarke. com/ID/Id. Model-UT-091026 {. html, . ppt} http: //www. rogerclarke. com/ID/Id. Model. Gloss. html Identity, Privacy and Security Institute (IPSI), Uni Toronto 26 October 2009 Copyright 1987 -2009 51
Lessons from a Sufficiently Rich Model of (Id)entity, Authentication and Authorisation Roger Clarke Xamax Consultancy, Canberra Visiting Professor – Cyberspace Law & Policy Centre @ UNSW and in Computer Science @ ANU http: //www. rogerclarke. com/ID/Id. Model-UT-091026 {. html, . ppt} http: //www. rogerclarke. com/ID/Id. Model. Gloss. html Identity, Privacy and Security Institute (IPSI), Uni Toronto 26 October 2009 Copyright 1987 -2009 51


