f9b96f87b7eed4194660fda8e75cb919.ppt
- Количество слайдов: 160
 Legal Aspects of Investigating & Prosecuting Computer Crimes 6 th Annual MSIA Graduate Security Conference Norwich University Workshop: June 10, 2009 M. E. Kabay, Ph. D, CISSP-ISSMP 1 mailto: mekabay@gmail. com V: 802. 479. 7937 Assoc Prof Information Assurance, School of Business & Management Norwich University, Vermont http: //www. mekabay. com SLIDES AVAILABLE ONLINE AT http: //tinyurl. com/l 5 vusf Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Legal Aspects of Investigating & Prosecuting Computer Crimes 6 th Annual MSIA Graduate Security Conference Norwich University Workshop: June 10, 2009 M. E. Kabay, Ph. D, CISSP-ISSMP 1 mailto: mekabay@gmail. com V: 802. 479. 7937 Assoc Prof Information Assurance, School of Business & Management Norwich University, Vermont http: //www. mekabay. com SLIDES AVAILABLE ONLINE AT http: //tinyurl. com/l 5 vusf Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Topics: Fire Hose Time Ø Introduction (slides 1: 24) Hour 1 Ø Search Warrants (25: 49=25) 49 slides Ø Warrantless Seizure of Evidence (50: 73=24) Hour 2 Hour 3 53 Ø Electronic Crime Scene Investigation (74: 102=29) Ø Analysis of Digital Evidence (103: 143=41) 58 Ø Using Seized Materials & Results in Evidence (144: 160=17) 2 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Topics: Fire Hose Time Ø Introduction (slides 1: 24) Hour 1 Ø Search Warrants (25: 49=25) 49 slides Ø Warrantless Seizure of Evidence (50: 73=24) Hour 2 Hour 3 53 Ø Electronic Crime Scene Investigation (74: 102=29) Ø Analysis of Digital Evidence (103: 143=41) 58 Ø Using Seized Materials & Results in Evidence (144: 160=17) 2 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Disclaimers ØInstructor is not a lawyer. ØThis is not legal advice. ØFor legal advice, consult an attorney specializing in this practice area. ØThis overview is NOT an in-depth discussion of the entire field of IP law: it is an overview to remind students of key issues. We won’t be discussing all the slides in detail. ØYou may download the PPT file from http: //www. mekabay. com/courses/academic/norwich/msia/ipcc. ppt or http: //tinyurl. com/l 5 vusf 3 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Disclaimers ØInstructor is not a lawyer. ØThis is not legal advice. ØFor legal advice, consult an attorney specializing in this practice area. ØThis overview is NOT an in-depth discussion of the entire field of IP law: it is an overview to remind students of key issues. We won’t be discussing all the slides in detail. ØYou may download the PPT file from http: //www. mekabay. com/courses/academic/norwich/msia/ipcc. ppt or http: //tinyurl. com/l 5 vusf 3 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Introduction Ø Goals Ø Recommended Texts Ø Recent Internet Usage Statistics Ø Tracing a Suspect on the Internet Ø Proactive vs Reactive strategies Ø Online Stings: Entrapment? 4 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Introduction Ø Goals Ø Recommended Texts Ø Recent Internet Usage Statistics Ø Tracing a Suspect on the Internet Ø Proactive vs Reactive strategies Ø Online Stings: Entrapment? 4 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Goals Ø Review (or introduce) basic concepts Ø Manage evidence q. Gather q. Preserve q. Present Ø Law and procedures useful to q. Law enforcement officials q. Information security professionals Ø Interest participants in further / deeper study 5 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Goals Ø Review (or introduce) basic concepts Ø Manage evidence q. Gather q. Preserve q. Present Ø Law and procedures useful to q. Law enforcement officials q. Information security professionals Ø Interest participants in further / deeper study 5 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Recommended Texts Ø Burgunder, L. (2007). Legal Aspects of Managing Technology, Fourth Edition. Thomson West Legal Studies in Business (ISBN 0 -324 -39973 -1). xv + 683. Index. Ø Moore, R. (2005). Cybercrime: Investigating High. Technology Computer Crime. Matthew Bender & Co. (ISBN 1 -59345 -303 -5). xii + 258. Index. Ø Clifford, R. D. (2006). Cybercrime: Investigation, Prosecution and Defense of a Computer-Related Crime, Second Edition. Carolina Academic Press (ISBN 1 -59460 -150 -X). xii + 282. Index. These texts are used in the CJ 341 Cyberlaw & Cybercrime course at Norwich University. 6 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Recommended Texts Ø Burgunder, L. (2007). Legal Aspects of Managing Technology, Fourth Edition. Thomson West Legal Studies in Business (ISBN 0 -324 -39973 -1). xv + 683. Index. Ø Moore, R. (2005). Cybercrime: Investigating High. Technology Computer Crime. Matthew Bender & Co. (ISBN 1 -59345 -303 -5). xii + 258. Index. Ø Clifford, R. D. (2006). Cybercrime: Investigation, Prosecution and Defense of a Computer-Related Crime, Second Edition. Carolina Academic Press (ISBN 1 -59460 -150 -X). xii + 282. Index. These texts are used in the CJ 341 Cyberlaw & Cybercrime course at Norwich University. 6 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
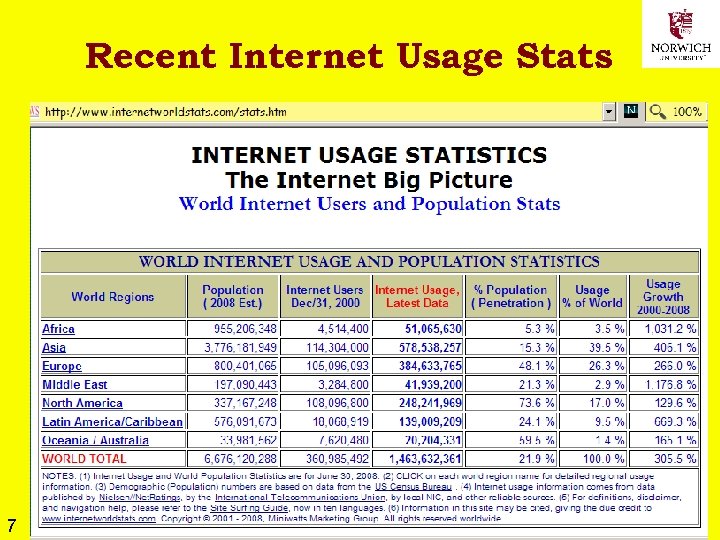 Recent Internet Usage Stats 7 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Recent Internet Usage Stats 7 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
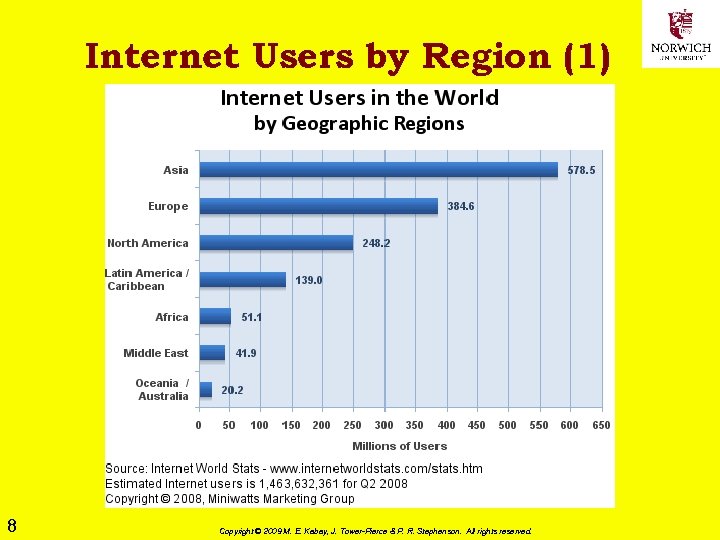 Internet Users by Region (1) 8 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Users by Region (1) 8 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
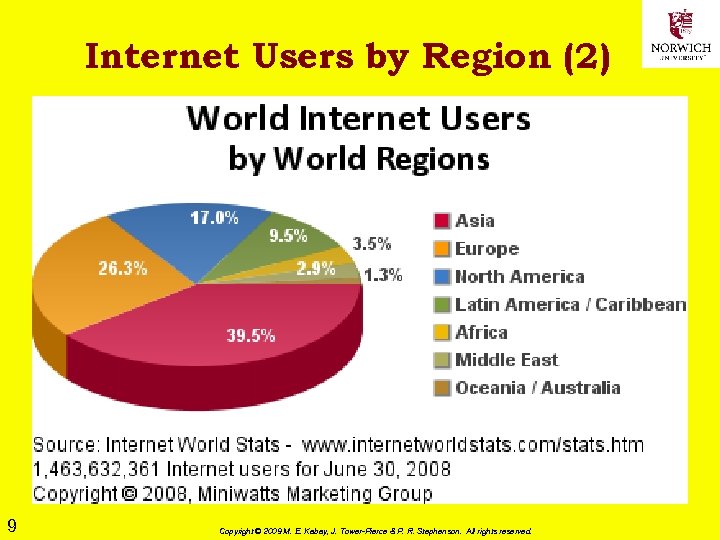 Internet Users by Region (2) 9 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Users by Region (2) 9 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
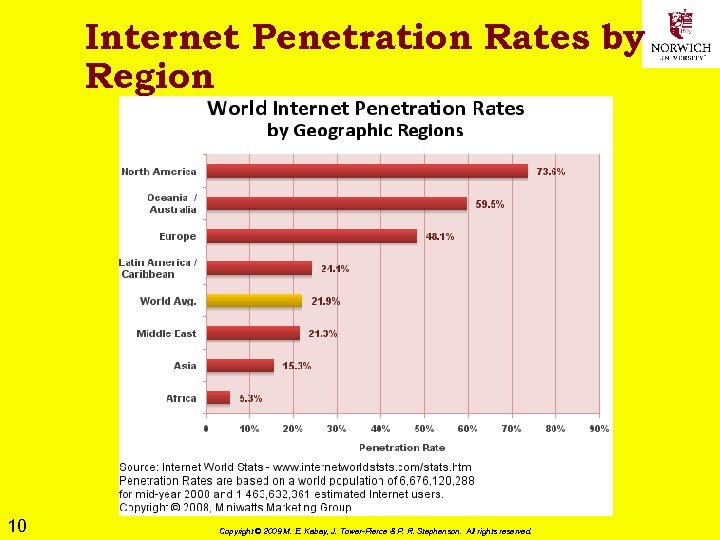 Internet Penetration Rates by Region 10 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Penetration Rates by Region 10 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Tracing a Suspect on the Internet Ø The Dynamic IP Address Ø Locating the Host Ø DNS Lookup Ø whois. net Ø Sam. Spade Program Ø Locating Information from E-Mails Ø E-Mail Headers 11 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Tracing a Suspect on the Internet Ø The Dynamic IP Address Ø Locating the Host Ø DNS Lookup Ø whois. net Ø Sam. Spade Program Ø Locating Information from E-Mails Ø E-Mail Headers 11 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 The Dynamic IP Address Ø Suspect may have own connection to ‘Net q Has permanent IP address q E. g. , gmail. com has IP address 64. 233. 171. 83 q Norwich. edu is 192. 149. 109. 197 Ø Or suspect connects to Internet via ISP q DHCP (Dynamic Host Configuration Protocol) q User is assigned temporary “dynamic” address q Re-used and not unique q Logged by ISP for some time (days to forever) q Must absolutely get cooperation of ISP and obtain records (if they still exist) under subpoena What would q The records will show match of dynamic address to an unsecured user’s modem’s MAC (media access control) WAP do to address and from there to the assigned modem this linkage? location, authorized user, address and so on 12 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Dynamic IP Address Ø Suspect may have own connection to ‘Net q Has permanent IP address q E. g. , gmail. com has IP address 64. 233. 171. 83 q Norwich. edu is 192. 149. 109. 197 Ø Or suspect connects to Internet via ISP q DHCP (Dynamic Host Configuration Protocol) q User is assigned temporary “dynamic” address q Re-used and not unique q Logged by ISP for some time (days to forever) q Must absolutely get cooperation of ISP and obtain records (if they still exist) under subpoena What would q The records will show match of dynamic address to an unsecured user’s modem’s MAC (media access control) WAP do to address and from there to the assigned modem this linkage? location, authorized user, address and so on 12 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Locating the Host Ø ICANN (Internet Corporation for Assigned Names and Numbers) http: //www. icann. org/ q. Global coordination of IP address assignments q. Defines rules for domain names Ø Inter. NIC < http: //www. icann. org/ > points to registrars around world q. See lists e. g. , http: //www. internic. net/origin. html q. Australia has 13 registrars q. Canada has 152 q. US has 562 13 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Locating the Host Ø ICANN (Internet Corporation for Assigned Names and Numbers) http: //www. icann. org/ q. Global coordination of IP address assignments q. Defines rules for domain names Ø Inter. NIC < http: //www. icann. org/ > points to registrars around world q. See lists e. g. , http: //www. internic. net/origin. html q. Australia has 13 registrars q. Canada has 152 q. US has 562 13 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 DNS Lookup Ø WHOIS functions available online from each registrar q. But http: //www. whois. net/ works with all registrars (see next page) Ø Many other tools available online for DNS lookup Ø Sam. Spade tool and service from http: //www. samspade. org can find many records as well as providing additional functions (see page after next) Ø Info in registry may be false or out of date q. Often see dummy phone numbers in DNS 14 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
DNS Lookup Ø WHOIS functions available online from each registrar q. But http: //www. whois. net/ works with all registrars (see next page) Ø Many other tools available online for DNS lookup Ø Sam. Spade tool and service from http: //www. samspade. org can find many records as well as providing additional functions (see page after next) Ø Info in registry may be false or out of date q. Often see dummy phone numbers in DNS 14 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
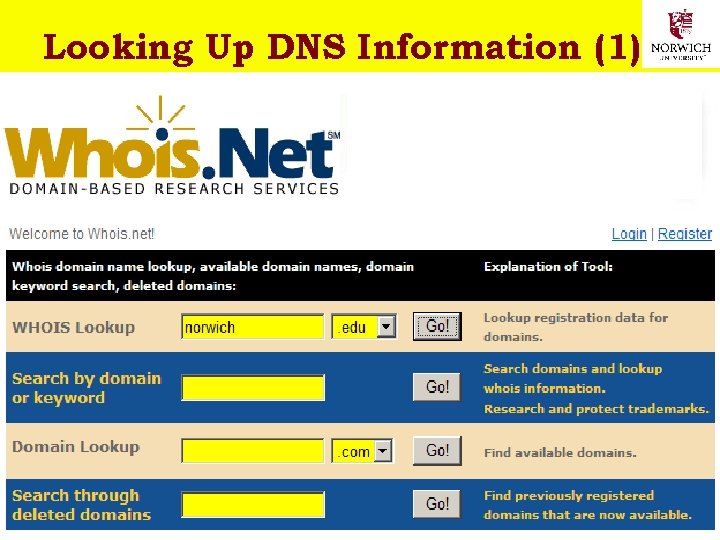 Looking Up DNS Information (1) 15 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Looking Up DNS Information (1) 15 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Looking Up DNS Information (2) Domain Name: NORWICH. EDU Registrant: Norwich University 158 Harmon Drive Juckett Hall / Computer Service Northfield, VT 05663 UNITED STATES Administrative Contact: NORWICH DNS ADMINISTRATOR … Technical Contact: … Name Servers: NS. NORWICH. EDU 192. 149. 109. 19 A. DNS. TDS. NET … 16 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Looking Up DNS Information (2) Domain Name: NORWICH. EDU Registrant: Norwich University 158 Harmon Drive Juckett Hall / Computer Service Northfield, VT 05663 UNITED STATES Administrative Contact: NORWICH DNS ADMINISTRATOR … Technical Contact: … Name Servers: NS. NORWICH. EDU 192. 149. 109. 19 A. DNS. TDS. NET … 16 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
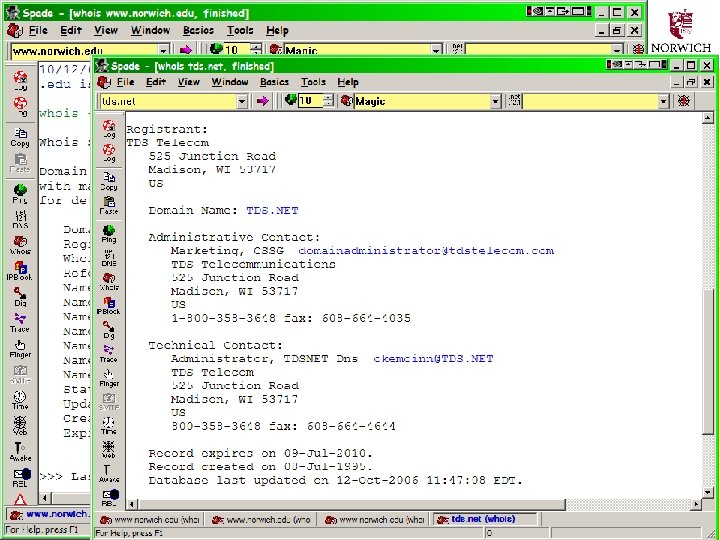 Sam. Spade Program 17 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Sam. Spade Program 17 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
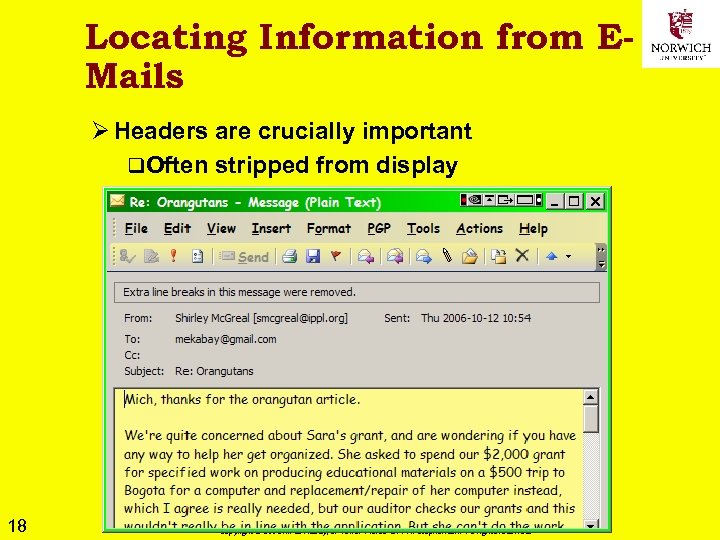 Locating Information from EMails Ø Headers are crucially important q. Often stripped from display 18 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Locating Information from EMails Ø Headers are crucially important q. Often stripped from display 18 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
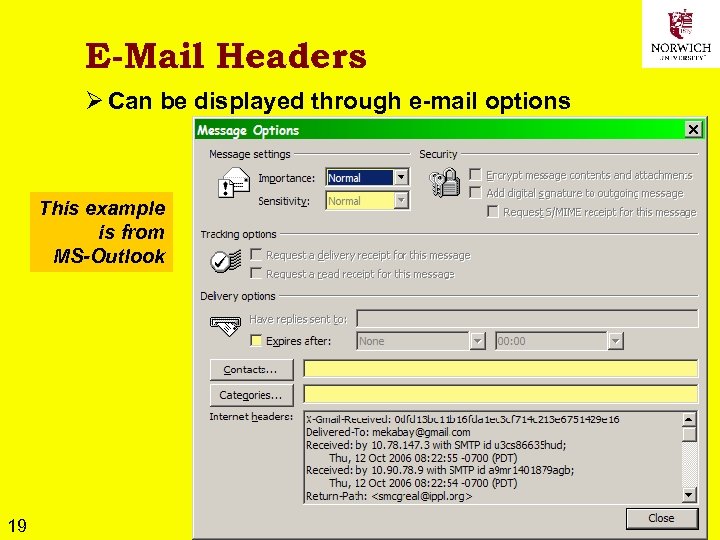 E-Mail Headers Ø Can be displayed through e-mail options This example is from MS-Outlook 19 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
E-Mail Headers Ø Can be displayed through e-mail options This example is from MS-Outlook 19 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
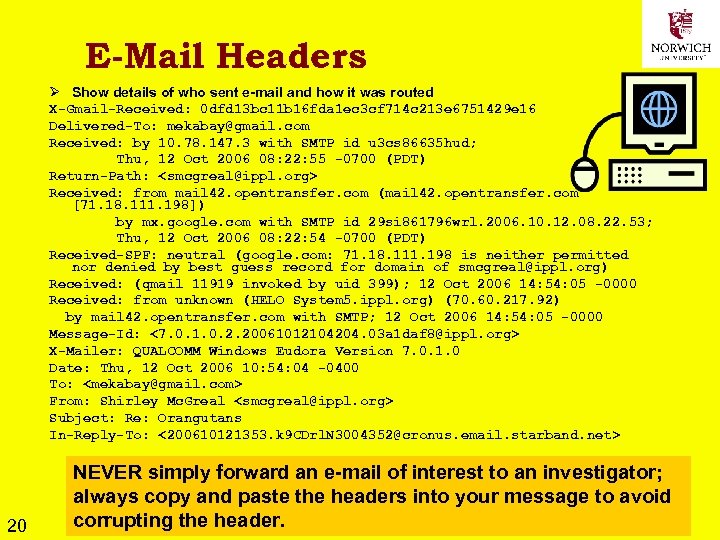 E-Mail Headers Ø Show details of who sent e-mail and how it was routed X-Gmail-Received: 0 dfd 13 bc 11 b 16 fda 1 ec 3 cf 714 c 213 e 6751429 e 16 Delivered-To: mekabay@gmail. com Received: by 10. 78. 147. 3 with SMTP id u 3 cs 86635 hud; Thu, 12 Oct 2006 08: 22: 55 -0700 (PDT) Return-Path:
E-Mail Headers Ø Show details of who sent e-mail and how it was routed X-Gmail-Received: 0 dfd 13 bc 11 b 16 fda 1 ec 3 cf 714 c 213 e 6751429 e 16 Delivered-To: mekabay@gmail. com Received: by 10. 78. 147. 3 with SMTP id u 3 cs 86635 hud; Thu, 12 Oct 2006 08: 22: 55 -0700 (PDT) Return-Path:
 Proactive vs Reactive Strategies Ø Some crimes are difficult to locate before they happen – need victim complaint to find out q. Identity theft q. Cyberstalking Ø Others benefit from dragnets q. Child pornography q. Child abuse Ø Officers need familiarity with argot (slang), culture 21 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Proactive vs Reactive Strategies Ø Some crimes are difficult to locate before they happen – need victim complaint to find out q. Identity theft q. Cyberstalking Ø Others benefit from dragnets q. Child pornography q. Child abuse Ø Officers need familiarity with argot (slang), culture 21 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Online Stings: Entrapment? Ø Must not give any basis for claim that officer initiated, suggested, prompted, or encouraged q. Illegal activity or q. Investigative actions that violate privacy or q. Convert a civilian into an agent of law enforcement to violate legal restrictions Ø ENTRAPMENT can destroy case q. Why? 4 th Amendment safeguards Ø Sorrells v. United States (1932) q. SCOTUS ruled that entrapment defense must show proof that LEO encouraged crime q. Defendant would not have been predisposed to commit crime 22 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Online Stings: Entrapment? Ø Must not give any basis for claim that officer initiated, suggested, prompted, or encouraged q. Illegal activity or q. Investigative actions that violate privacy or q. Convert a civilian into an agent of law enforcement to violate legal restrictions Ø ENTRAPMENT can destroy case q. Why? 4 th Amendment safeguards Ø Sorrells v. United States (1932) q. SCOTUS ruled that entrapment defense must show proof that LEO encouraged crime q. Defendant would not have been predisposed to commit crime 22 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 United States v. Poehlman (2000) 23 Ø Poehlman alleged to have met undercover LEO to have sex with minor Ø But defendant said he started online discussions with LEO to form adult relationship Ø LEO wrote she was looking for someone “to train her daughters in the ways of the world” Ø Poehlman explicitly said he wasn’t interested and LEO responded that she would terminate relationship Ø Poehlman offered to “train” daughters as way of continuing relation but claimed he had no intention of having sex with them – was ploy Ø SCOTUS ruled in favor of defendant: evidence that pedophilia was not his original intent & LEO was significantly responsible for his actions Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
United States v. Poehlman (2000) 23 Ø Poehlman alleged to have met undercover LEO to have sex with minor Ø But defendant said he started online discussions with LEO to form adult relationship Ø LEO wrote she was looking for someone “to train her daughters in the ways of the world” Ø Poehlman explicitly said he wasn’t interested and LEO responded that she would terminate relationship Ø Poehlman offered to “train” daughters as way of continuing relation but claimed he had no intention of having sex with them – was ploy Ø SCOTUS ruled in favor of defendant: evidence that pedophilia was not his original intent & LEO was significantly responsible for his actions Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 BREAK 5’ 12” 24 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
BREAK 5’ 12” 24 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Search Warrants & Seizure of Electronic Evidence Ø Identifying Physical Location of Electronic Evidence q. ECPA Effects on Data Acquisition q. Collaboration from Third-Party Record-Holders Ø Which Computers? Ø Legal Limits on Searches q. Federal Constitutional Limits q. State Constitutional Limits References: q. Statutes 25 Clifford pp 111 -137 Moore pp 141 -153; 148 -155 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Search Warrants & Seizure of Electronic Evidence Ø Identifying Physical Location of Electronic Evidence q. ECPA Effects on Data Acquisition q. Collaboration from Third-Party Record-Holders Ø Which Computers? Ø Legal Limits on Searches q. Federal Constitutional Limits q. State Constitutional Limits References: q. Statutes 25 Clifford pp 111 -137 Moore pp 141 -153; 148 -155 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Identifying Physical Location of Electronic Evidence Ø General Principles Ø ECPA Effects on Data Acquisition q Coverage q Disclosure to Government Agents q Contents of Electronic Communications q Violations of the ECPA Ø Collaboration from Third-Party Record-Holders q Finding the Records q Evaluating Utility of Records q Authenticating Records q Obtaining Records q Contacting ISP & Serving Papers 26 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Identifying Physical Location of Electronic Evidence Ø General Principles Ø ECPA Effects on Data Acquisition q Coverage q Disclosure to Government Agents q Contents of Electronic Communications q Violations of the ECPA Ø Collaboration from Third-Party Record-Holders q Finding the Records q Evaluating Utility of Records q Authenticating Records q Obtaining Records q Contacting ISP & Serving Papers 26 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 General Principles Ø Katz v US (1967): SCOTUS held that publicly disclosed information is not constitutionally protected q. Includes voluntarily transferred info in hands of third parties q. Thus third-party repositories limited by statute, not 4 th amendment Ø Restrictions include laws protecting q. Bank records q. Cable TV & video rentals q. E-mail & other electronic communications 27 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
General Principles Ø Katz v US (1967): SCOTUS held that publicly disclosed information is not constitutionally protected q. Includes voluntarily transferred info in hands of third parties q. Thus third-party repositories limited by statute, not 4 th amendment Ø Restrictions include laws protecting q. Bank records q. Cable TV & video rentals q. E-mail & other electronic communications 27 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 ECPA Coverage Ø 2000: Updated Wiretap law (18 USC § 2510 -22) Ø 2004: Added Stored Electronic Communications Privacy Act (SECA, 18 USC § 270111) Ø Protects contents of ecommunications in storage by service Ø Prohibits provision of communications to government agencies without strict controls 28 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
ECPA Coverage Ø 2000: Updated Wiretap law (18 USC § 2510 -22) Ø 2004: Added Stored Electronic Communications Privacy Act (SECA, 18 USC § 270111) Ø Protects contents of ecommunications in storage by service Ø Prohibits provision of communications to government agencies without strict controls 28 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Disclosure to Government Agents Ø All records may be obtained through warrant Ø Subscriber/customer records (identity, services) may also be obtained by subpoena Ø Transaction history available through subpoena since U. S. A. P. A. T. R. I. O. T. Act passed Ø E-mail may be retrieved by subpoena provided user given notice (up to 90 -180 days delay) Ø May use “§ 2703(d) court order” to access everything except unopened e-mail stored < 180 days 29 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Disclosure to Government Agents Ø All records may be obtained through warrant Ø Subscriber/customer records (identity, services) may also be obtained by subpoena Ø Transaction history available through subpoena since U. S. A. P. A. T. R. I. O. T. Act passed Ø E-mail may be retrieved by subpoena provided user given notice (up to 90 -180 days delay) Ø May use “§ 2703(d) court order” to access everything except unopened e-mail stored < 180 days 29 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Contents of Electronic Communications Ø Agreement of one party in electronic communication suffices for legal disclosure Ø Take that fact into account when you are writing e-mail q. In general, when writing with employee user. ID, all e-mail must be considered equivalent to using company letterhead q. All official e-mail may become evidence in a court of law Ø When writing informally using your own address, remember that everything on Internet is POTENTIALLY PERMANENT and may affect your future employment prospects 30 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Contents of Electronic Communications Ø Agreement of one party in electronic communication suffices for legal disclosure Ø Take that fact into account when you are writing e-mail q. In general, when writing with employee user. ID, all e-mail must be considered equivalent to using company letterhead q. All official e-mail may become evidence in a court of law Ø When writing informally using your own address, remember that everything on Internet is POTENTIALLY PERMANENT and may affect your future employment prospects 30 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Violations of the ECPA Ø Criminal liability q. Up to 2 years in federal prison Ø Civil liability q. Damages & attorneys’ fees q. Government agent may be personally liable Ø Suppression: NOT a remedy Ø Good faith defense: q. Government agent may q. Rely on good faith application of warrant or subpoena q. As absolute defense against civil or criminal charges stemming from actions 31 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Violations of the ECPA Ø Criminal liability q. Up to 2 years in federal prison Ø Civil liability q. Damages & attorneys’ fees q. Government agent may be personally liable Ø Suppression: NOT a remedy Ø Good faith defense: q. Government agent may q. Rely on good faith application of warrant or subpoena q. As absolute defense against civil or criminal charges stemming from actions 31 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Evaluating Utility of Records But look for Ø Records may not be available video camera q. Typically 30 -60 day retention of log tapes records q. Dynamic IP addresses may make identification difficult for older evidence Ø Some records may originate in public computers that are effectively anonymous q. Business services (e. g. , Kinko’s) q. Libraries, Internet cafés q. Wireless services q. Hijacked services q. Anonymizers 32 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Evaluating Utility of Records But look for Ø Records may not be available video camera q. Typically 30 -60 day retention of log tapes records q. Dynamic IP addresses may make identification difficult for older evidence Ø Some records may originate in public computers that are effectively anonymous q. Business services (e. g. , Kinko’s) q. Libraries, Internet cafés q. Wireless services q. Hijacked services q. Anonymizers 32 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Authenticating Records Ø Spoofing may disguise origin q. Naïve users alter originating address q. But headers show real IP addresses Ø More sophisticated criminals add faked header lines q. Must always analyze entire header q. Sam. Spade does this (discussed in lecture 16) Ø Open spam relay a danger q. Logon to unprotected SMTP server q. Send mail from someone else’s system 33 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Authenticating Records Ø Spoofing may disguise origin q. Naïve users alter originating address q. But headers show real IP addresses Ø More sophisticated criminals add faked header lines q. Must always analyze entire header q. Sam. Spade does this (discussed in lecture 16) Ø Open spam relay a danger q. Logon to unprotected SMTP server q. Send mail from someone else’s system 33 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Obtaining Records Ø Typically obtain search warrant q. Better than subpoena q. Can obtain any records at all q. Avoids problem of more restrictive state laws that require warrant Ø So why not use a warrant? q. Might not have probable cause q. Difficulty getting warrant across state lines 34 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Obtaining Records Ø Typically obtain search warrant q. Better than subpoena q. Can obtain any records at all q. Avoids problem of more restrictive state laws that require warrant Ø So why not use a warrant? q. Might not have probable cause q. Difficulty getting warrant across state lines 34 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Contacting ISP & Serving Papers Ø Call ISP to be sure they have records you need q. Discuss IP addresses with technical staff q. Identify possible errors of analysis q. Find out if there have been mergers or acquisitions q. Identify possible IP sub-blocks owned/used by other entities Ø Ask if ISP will accept warrant by fax Ø Explain exactly what you need 35 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Contacting ISP & Serving Papers Ø Call ISP to be sure they have records you need q. Discuss IP addresses with technical staff q. Identify possible errors of analysis q. Find out if there have been mergers or acquisitions q. Identify possible IP sub-blocks owned/used by other entities Ø Ask if ISP will accept warrant by fax Ø Explain exactly what you need 35 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Search Warrants Ø Which Computers? Ø Legal Limits on Searches q. Federal Constitutional Limits q. State Constitutional Limits q. Statutes 36 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Search Warrants Ø Which Computers? Ø Legal Limits on Searches q. Federal Constitutional Limits q. State Constitutional Limits q. Statutes 36 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Which Computers? Ø Goal of tracing electronic communications: q. Locate computer at origin of evidence of crime q. Link to specific person Ø Computers that may be involved q. Victims’ computers may be searched without warrant with permission q. Publishers’ computers not restricted if publisher is the victim q. ECPA does not apply to suspects’ computers 37 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Which Computers? Ø Goal of tracing electronic communications: q. Locate computer at origin of evidence of crime q. Link to specific person Ø Computers that may be involved q. Victims’ computers may be searched without warrant with permission q. Publishers’ computers not restricted if publisher is the victim q. ECPA does not apply to suspects’ computers 37 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Federal Constitutional Limits Ø Fourth Amendment q. Reasonable expectation of privacy q. Government action Ø Legal Warrant q. Probable cause q. Neutral/detached magistrate q. Reasonably precise Ø Rules for Executing Warrant http: //tinyurl. com/4 jmcaz 38 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Federal Constitutional Limits Ø Fourth Amendment q. Reasonable expectation of privacy q. Government action Ø Legal Warrant q. Probable cause q. Neutral/detached magistrate q. Reasonably precise Ø Rules for Executing Warrant http: //tinyurl. com/4 jmcaz 38 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 The Fourth Amendment Text 39 Bold emphasis added Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Fourth Amendment Text 39 Bold emphasis added Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 4 th Amendment Issues (1) Reasonable expectation of privacy (EOP) Ø Subjective expectation q. Computer in home has higher EOP q. Shared computer has lower EOP q. Employer’s computer: depends – üPolicy? üAwareness? üEnforcement? Ø Social acceptance or expectation of search 40 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
4 th Amendment Issues (1) Reasonable expectation of privacy (EOP) Ø Subjective expectation q. Computer in home has higher EOP q. Shared computer has lower EOP q. Employer’s computer: depends – üPolicy? üAwareness? üEnforcement? Ø Social acceptance or expectation of search 40 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 4 th Amendment Issues (2) Ø Government action q. Searches by state law enforcement may transfer results to federal agencies üBut federal authorities must not have been involved in a way that would require suppression of evidence Ø Private citizens q. Constitution does not affect search by private citizen not acting as an agent of law enforcement q. Thus evidence usually admissible in court 41 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
4 th Amendment Issues (2) Ø Government action q. Searches by state law enforcement may transfer results to federal agencies üBut federal authorities must not have been involved in a way that would require suppression of evidence Ø Private citizens q. Constitution does not affect search by private citizen not acting as an agent of law enforcement q. Thus evidence usually admissible in court 41 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Legal Warrant 42 Ø Probable cause q Evidence of a crime q Likelihood that evidence will be found in location to be searched üHow do you know suspect used computer in home? Could have been elsewhere üMay need circumstantial evidence such as time stamps, stakeout Ø Neutral/detached magistrate q Who has authority for warrant location q Watch out for cross-state jurisdiction Ø Reasonably precise q General description may lead to suppression q Best to mention computers & media explicitly Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Legal Warrant 42 Ø Probable cause q Evidence of a crime q Likelihood that evidence will be found in location to be searched üHow do you know suspect used computer in home? Could have been elsewhere üMay need circumstantial evidence such as time stamps, stakeout Ø Neutral/detached magistrate q Who has authority for warrant location q Watch out for cross-state jurisdiction Ø Reasonably precise q General description may lead to suppression q Best to mention computers & media explicitly Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Rules for Executing Warrant (1) Ø Knock and announce: identify as LEOs & explain purpose in entering premises Ø Take items in plain view q. But contraband tools for crime may also be seized if they are visible and obviously incriminating 43 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Rules for Executing Warrant (1) Ø Knock and announce: identify as LEOs & explain purpose in entering premises Ø Take items in plain view q. But contraband tools for crime may also be seized if they are visible and obviously incriminating 43 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Rules for Executing Warrant (2) Ø Good faith q Evidence seized under faulty warrant may be suppressed q But generally LEOs not prosecuted if acting under good faith in legality of (later overturned) warrant Ø Remove computers for analysis off -site Ø Prompt execution q Don’t let evidence evaporate q Cannot hold warrant in abeyance indefinitely 44 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Rules for Executing Warrant (2) Ø Good faith q Evidence seized under faulty warrant may be suppressed q But generally LEOs not prosecuted if acting under good faith in legality of (later overturned) warrant Ø Remove computers for analysis off -site Ø Prompt execution q Don’t let evidence evaporate q Cannot hold warrant in abeyance indefinitely 44 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 State Constitutional Limits Ø Some states more restrictive than federal rules Ø Some do not allow good-faith exception to requirement for valid warrant Ø Some may protect vehicles (and by implication portable computers) more than federal courts 45 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
State Constitutional Limits Ø Some states more restrictive than federal rules Ø Some do not allow good-faith exception to requirement for valid warrant Ø Some may protect vehicles (and by implication portable computers) more than federal courts 45 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Statutes Ø ECPA (as discussed above) Ø Zurcher v. Stanford Daily q. LEOs had warrant to search student newspaper’s computer for pictures of political demonstration q. SCOTUS ruled that 1 st Amendment issues did not further limit warranted searches This is not a statute. 46 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Statutes Ø ECPA (as discussed above) Ø Zurcher v. Stanford Daily q. LEOs had warrant to search student newspaper’s computer for pictures of political demonstration q. SCOTUS ruled that 1 st Amendment issues did not further limit warranted searches This is not a statute. 46 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Statutes: PPA Ø PPA passed to further restrict warrants q. Privacy Protection Act (42 USC § 2000 aa) q. Passed in 2000 q. Any material intended for publication or broadcasting requires a subpoena q. Exceptions üContraband, fruits or tools for crime üPreventing imminent death or injury üMaterial held by target of investigation üChild pornography 47 And neither is this. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Statutes: PPA Ø PPA passed to further restrict warrants q. Privacy Protection Act (42 USC § 2000 aa) q. Passed in 2000 q. Any material intended for publication or broadcasting requires a subpoena q. Exceptions üContraband, fruits or tools for crime üPreventing imminent death or injury üMaterial held by target of investigation üChild pornography 47 And neither is this. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 PPA & Steve Jackson Games Ø March 1990: Secret Service raided Steve Jackson Games q Looking for info about Bell. South’s emergency service q Had been posted on BBS q Seized entire computer for BBS q Held for months q Severely damaged company Ø SJG sued under PPA & ECPA q Won trial q Awarded damages $51 K q Attorneys’ fees $250 K Ø Irony: Bell. South info was actually public & available for sale from company 48 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
PPA & Steve Jackson Games Ø March 1990: Secret Service raided Steve Jackson Games q Looking for info about Bell. South’s emergency service q Had been posted on BBS q Seized entire computer for BBS q Held for months q Severely damaged company Ø SJG sued under PPA & ECPA q Won trial q Awarded damages $51 K q Attorneys’ fees $250 K Ø Irony: Bell. South info was actually public & available for sale from company 48 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 BREAK 10’ 27” 49 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
BREAK 10’ 27” 49 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Warrantless Seizure of Evidence Ø Exceptions to the Requirement for Warrant Ø Consent Ø Search Incident to Arrest Ø Exigent Circumstances Ø Inventory Ø Stop and Frisk Clifford pp 137 -155 Ø Mobility Moore pp 153 -165 Ø Plain View 50 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Warrantless Seizure of Evidence Ø Exceptions to the Requirement for Warrant Ø Consent Ø Search Incident to Arrest Ø Exigent Circumstances Ø Inventory Ø Stop and Frisk Clifford pp 137 -155 Ø Mobility Moore pp 153 -165 Ø Plain View 50 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Exceptions to Requirement for Warrant Ø Long-standing view in jurisprudence: q. Warrant not necessary IF q. Owner of property agrees to search Ø Issues q. Does consenter have legitimate right to consent to search? q. Expectation of privacy q. Degree of ownership of property 51 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Exceptions to Requirement for Warrant Ø Long-standing view in jurisprudence: q. Warrant not necessary IF q. Owner of property agrees to search Ø Issues q. Does consenter have legitimate right to consent to search? q. Expectation of privacy q. Degree of ownership of property 51 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Consent Ø Who May Consent? q. Employer q. Parent q. Spouse q. Co-User q. Third-Party Holder Ø Notification of Right to Withhold Consent Ø Limitations and Withdrawal of Consent 52 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Consent Ø Who May Consent? q. Employer q. Parent q. Spouse q. Co-User q. Third-Party Holder Ø Notification of Right to Withhold Consent Ø Limitations and Withdrawal of Consent 52 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Who May Consent? Ø Matlock 1974: Common authority or sufficient relationship to the premises or effects Ø Rith 1999: Mutual use q Joint access q Control of property for most purposes Ø Crucial test: expectation of privacy q Reduced in shared accommodations q But evidence of rent & of security strengthens expectation of privacy (see later slides) 53 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Who May Consent? Ø Matlock 1974: Common authority or sufficient relationship to the premises or effects Ø Rith 1999: Mutual use q Joint access q Control of property for most purposes Ø Crucial test: expectation of privacy q Reduced in shared accommodations q But evidence of rent & of security strengthens expectation of privacy (see later slides) 53 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Private Employers Ø Employer not acting as agent of LEO is free to search own property without suppression of evidence Ø General acceptance of right of search q. For area not exclusively reserved for a particular employee q. Expect same rule for computers Ø Explicit policy reducing expectation of privacy strengthens admissibility of evidence 54 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Private Employers Ø Employer not acting as agent of LEO is free to search own property without suppression of evidence Ø General acceptance of right of search q. For area not exclusively reserved for a particular employee q. Expect same rule for computers Ø Explicit policy reducing expectation of privacy strengthens admissibility of evidence 54 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Public Employers Ø SCOTUS: O’Connor v. Ortega (1987) established expectation of privacy for government employees q But open office could reduce expectation q Also affected by specific policy Ø Policy effectiveness depends on q Clear enunciation of limits to privacy (e. g. , logon banner) q Evidence that employees are aware of policy Used with permission of artist. http: //tinyurl. com Copyright © 1998 Steve Greenberg. All rights re Ø Problems q Allowing private use of government computers q Allowing unauthorized encryption 55 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Public Employers Ø SCOTUS: O’Connor v. Ortega (1987) established expectation of privacy for government employees q But open office could reduce expectation q Also affected by specific policy Ø Policy effectiveness depends on q Clear enunciation of limits to privacy (e. g. , logon banner) q Evidence that employees are aware of policy Used with permission of artist. http: //tinyurl. com Copyright © 1998 Steve Greenberg. All rights re Ø Problems q Allowing private use of government computers q Allowing unauthorized encryption 55 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Parent 56 Ø Closer relationship supports consent Ø Parents’ consent generally accepted by court q. But child must be “essentially dependent” on parent q. Payment of rent reduces authority to grant consent Ø US v. Durham (1998): Mother could not grant consent for search of son’s computer q. Even though she owned some of equipment q. Because son applied security to system Pietà, marble sculpture by q. And he paid small amount of Michelangelo, 1499; in St. Peter's rent Basilica, Rome Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Parent 56 Ø Closer relationship supports consent Ø Parents’ consent generally accepted by court q. But child must be “essentially dependent” on parent q. Payment of rent reduces authority to grant consent Ø US v. Durham (1998): Mother could not grant consent for search of son’s computer q. Even though she owned some of equipment q. Because son applied security to system Pietà, marble sculpture by q. And he paid small amount of Michelangelo, 1499; in St. Peter's rent Basilica, Rome Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Spouse Ø Generally viewed as having “joint control and equal right to occupancy of premises and access to computers on the premises” [Orton p 141] Ø BUT consent is invalid if q. Computer is used exclusively by nonconsenting partner q. Kept in separate room (esp. if locked) 57 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Spouse Ø Generally viewed as having “joint control and equal right to occupancy of premises and access to computers on the premises” [Orton p 141] Ø BUT consent is invalid if q. Computer is used exclusively by nonconsenting partner q. Kept in separate room (esp. if locked) 57 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Co-User Ø Shared use reduces expectation of privacy Ø But still case law to develop on effects of q. Access controls q. Encryption Ø For time being, assume co-user cannot grant consent to prima facie private areas of computer 58 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Co-User Ø Shared use reduces expectation of privacy Ø But still case law to develop on effects of q. Access controls q. Encryption Ø For time being, assume co-user cannot grant consent to prima facie private areas of computer 58 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Third-Party Holder 59 Ø If equipment or media left in possession of someone else, does that person have right to consent to search without warrant? Ø Problematic case law: contradictions Ø US v. James (2003): q Court ruled search of data CDs invalid because q Owner did not intend to give 3 rd party authority to grant consent for search q But note that CDs were in sealed envelope Ø US v. Falcon (1985): q Cassette tape labeled “confidential/do not play” q Court ruled tape admissible without warrant q Argued holder could have played tape any time Ø CONCLUSION: best to proceed with warrant to avoid risk of suppression Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Third-Party Holder 59 Ø If equipment or media left in possession of someone else, does that person have right to consent to search without warrant? Ø Problematic case law: contradictions Ø US v. James (2003): q Court ruled search of data CDs invalid because q Owner did not intend to give 3 rd party authority to grant consent for search q But note that CDs were in sealed envelope Ø US v. Falcon (1985): q Cassette tape labeled “confidential/do not play” q Court ruled tape admissible without warrant q Argued holder could have played tape any time Ø CONCLUSION: best to proceed with warrant to avoid risk of suppression Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Notification of Right to Withhold Consent Ø Is the consent to the search voluntary? Ø Federal system imposes burden of proof on government using preponderance of evidence Ø Other jurisdictions may be more exigent q E. g. , requiring “clear and convincing evidence” 60 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Notification of Right to Withhold Consent Ø Is the consent to the search voluntary? Ø Federal system imposes burden of proof on government using preponderance of evidence Ø Other jurisdictions may be more exigent q E. g. , requiring “clear and convincing evidence” 60 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Factors affecting judgement of voluntary consent: Ø Age/intelligence of suspect Ø Being advised of constitutional rights (Miranda warning) Ø Custody or detention (and length) Ø Physical punishment or deprivation (sleep, food) Ø Generally, advising person that warrant will be sought if consent not granted is acceptable 61 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Factors affecting judgement of voluntary consent: Ø Age/intelligence of suspect Ø Being advised of constitutional rights (Miranda warning) Ø Custody or detention (and length) Ø Physical punishment or deprivation (sleep, food) Ø Generally, advising person that warrant will be sought if consent not granted is acceptable 61 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Limitations and Withdrawal of Consent Ø Consent for search may be withdrawn at any time Ø Area of search may be limited Ø Continuing to search after withdrawal or in unauthorized areas leads to suppression of evidence Ø Does breaking access protection or encryption violate restrictions on unwarranted search? q. In physical world, breaking locks or sealed containers has led to suppression q. But no damage when breaking security so evidence may be accepted by court 62 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Limitations and Withdrawal of Consent Ø Consent for search may be withdrawn at any time Ø Area of search may be limited Ø Continuing to search after withdrawal or in unauthorized areas leads to suppression of evidence Ø Does breaking access protection or encryption violate restrictions on unwarranted search? q. In physical world, breaking locks or sealed containers has led to suppression q. But no damage when breaking security so evidence may be accepted by court 62 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Search Incident to Arrest Ø General principle allows search and seizure of evidence at time of arrest q. Purpose: prevent destruction of evidence q. Therefore expect same rule for digital evidence Ø Particularly useful for seizing cell phones and PDAs q. May contain useful data q. E. g. , phone lists, calendars, call logs 63 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Search Incident to Arrest Ø General principle allows search and seizure of evidence at time of arrest q. Purpose: prevent destruction of evidence q. Therefore expect same rule for digital evidence Ø Particularly useful for seizing cell phones and PDAs q. May contain useful data q. E. g. , phone lists, calendars, call logs 63 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Exigent Circumstances (1) Ø Probable cause Ø Exigent circumstances defined essentially by q. Imminent destruction of evidence Ø BUT q. Allows for seizure of computer q. But NOT for search üNeed separate warrant for search 64 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Exigent Circumstances (1) Ø Probable cause Ø Exigent circumstances defined essentially by q. Imminent destruction of evidence Ø BUT q. Allows for seizure of computer q. But NOT for search üNeed separate warrant for search 64 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Exigent Circumstances (2) Ø US v. Reed (1991) established requirements for admitting evidence obtained under warrantless search with claim of exigency q. Must demonstrate degree of urgency q. Amount of time required for getting warrant would seriously interfere with process of ensuring justice q. Evidence in danger of destruction or removal q. Danger to officers or evidence at crime scene q. Suspect’s awareness of anticipated seizure of evidence q. Ease of destruction of evidence by suspect 65 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Exigent Circumstances (2) Ø US v. Reed (1991) established requirements for admitting evidence obtained under warrantless search with claim of exigency q. Must demonstrate degree of urgency q. Amount of time required for getting warrant would seriously interfere with process of ensuring justice q. Evidence in danger of destruction or removal q. Danger to officers or evidence at crime scene q. Suspect’s awareness of anticipated seizure of evidence q. Ease of destruction of evidence by suspect 65 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Exigent Circumstances (3) Ø US v. David (1991) q LEO observed suspect deleting data from PDA q Seized device and scanned names q Court admitted evidence q But exigency ended as soon as PDA was seized Ø US v. Ortiz (1996): court ruled that search of pager was warranted because of risk of data loss as batteries failed Ø US v. Romero-Garcia (1997): search of laptop computer was not warranted by fear of battery failure (would not normally destroy data) Ø Best practice: if device seized under exigent circumstances, obtain a warrant using probable cause to justify search that will ensure evidence is accepted in court unless data are evanescent 66 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Exigent Circumstances (3) Ø US v. David (1991) q LEO observed suspect deleting data from PDA q Seized device and scanned names q Court admitted evidence q But exigency ended as soon as PDA was seized Ø US v. Ortiz (1996): court ruled that search of pager was warranted because of risk of data loss as batteries failed Ø US v. Romero-Garcia (1997): search of laptop computer was not warranted by fear of battery failure (would not normally destroy data) Ø Best practice: if device seized under exigent circumstances, obtain a warrant using probable cause to justify search that will ensure evidence is accepted in court unless data are evanescent 66 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Inventory Ø Normally associated with searching vehicles to list all evidence present Ø Booking search catalogs possessions of suspect at time of arrest Ø Might permit LEO to search computer or electronic device to determine identity of suspect Ø But should not use as basis for extensive forensic analysis: get a warrant 67 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Inventory Ø Normally associated with searching vehicles to list all evidence present Ø Booking search catalogs possessions of suspect at time of arrest Ø Might permit LEO to search computer or electronic device to determine identity of suspect Ø But should not use as basis for extensive forensic analysis: get a warrant 67 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Stop and Frisk Ø LEO may search suspect for weapons Ø May seize computing device during search Ø BUT should not search computer without warrant 68 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Stop and Frisk Ø LEO may search suspect for weapons Ø May seize computing device during search Ø BUT should not search computer without warrant 68 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Mobility Ø Vehicle’s mobility serves as exigent circumstance justifying immediate search without warrant Ø Could therefore reasonably seize a computer found in such a search Ø But Orton argues that this view could not justify search of computing devices Ø And there is no current case law supporting such a procedure 69 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Mobility Ø Vehicle’s mobility serves as exigent circumstance justifying immediate search without warrant Ø Could therefore reasonably seize a computer found in such a search Ø But Orton argues that this view could not justify search of computing devices Ø And there is no current case law supporting such a procedure 69 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Plain View (1) Ø Doctrine: If contraband is q. Left in plain view of LEO q. Who is in lawful place q. Then there is no expectation of privacy Ø Limits q. Incriminating nature must be obvious q. LEO must be legally allowed to be in position where item is in view q. LEO must not alter search process as result of plain-view discovery 70 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Plain View (1) Ø Doctrine: If contraband is q. Left in plain view of LEO q. Who is in lawful place q. Then there is no expectation of privacy Ø Limits q. Incriminating nature must be obvious q. LEO must be legally allowed to be in position where item is in view q. LEO must not alter search process as result of plain-view discovery 70 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Plain View (2) Ø So cannot exceed limits of warrant when searching computer even if plain-view item such as file-name suggests crime Ø If protocol in warrant specifies searching all files, may log child porn as long as search continues through all files Ø If protocol in warrant specifies searching all files but only for business fraud data, may NOT open file suspected to contain child porn Ø So if new evidence of a different crime is discovered in plain view, get a warrant to change search protocol. 71 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Plain View (2) Ø So cannot exceed limits of warrant when searching computer even if plain-view item such as file-name suggests crime Ø If protocol in warrant specifies searching all files, may log child porn as long as search continues through all files Ø If protocol in warrant specifies searching all files but only for business fraud data, may NOT open file suspected to contain child porn Ø So if new evidence of a different crime is discovered in plain view, get a warrant to change search protocol. 71 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Plain View (3) Ø US v. Carey (1999) q Narcotics investigation of computer disk q Officer’s discovery of 1 st child porn image accepted in court q But subsequent discoveries suppressed – unlawful search beyond terms of warrant Ø US v. Gray (1999) q LEO conducting file-by-file search q Discovered child porn q Immediately applied for warrant to search of child porn q Court ruled that not only was officer correct but also that had other child porn been discovered in systematic examination of all files, those images would have been admissible also 72 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Plain View (3) Ø US v. Carey (1999) q Narcotics investigation of computer disk q Officer’s discovery of 1 st child porn image accepted in court q But subsequent discoveries suppressed – unlawful search beyond terms of warrant Ø US v. Gray (1999) q LEO conducting file-by-file search q Discovered child porn q Immediately applied for warrant to search of child porn q Court ruled that not only was officer correct but also that had other child porn been discovered in systematic examination of all files, those images would have been admissible also 72 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 BREAK 4’ 58” 73 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
BREAK 4’ 58” 73 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Electronic Crime Scene Investigation Ø Introduction Moore Ch 9 Clifford Ch 3 pp 155 -160 Ø Nature of Electronic Evidence Ø Handling Electronic Evidence at the Crime Scene Ø Electronic Devices Ø Securing and Evaluating the Scene ECSIGFR = Electronic Crime Ø Documenting the Scene Investigation: A Guide for First Responders (NIJ) Another useful reference: Volonino, L. , R. Anzaldua, J. Godwin (2007). Computer Forensics: Principles and Practices. Pearson Prentice Hall (ISBN 0 -13 -154727 -5). xviii + 534. Index. 74 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Electronic Crime Scene Investigation Ø Introduction Moore Ch 9 Clifford Ch 3 pp 155 -160 Ø Nature of Electronic Evidence Ø Handling Electronic Evidence at the Crime Scene Ø Electronic Devices Ø Securing and Evaluating the Scene ECSIGFR = Electronic Crime Ø Documenting the Scene Investigation: A Guide for First Responders (NIJ) Another useful reference: Volonino, L. , R. Anzaldua, J. Godwin (2007). Computer Forensics: Principles and Practices. Pearson Prentice Hall (ISBN 0 -13 -154727 -5). xviii + 534. Index. 74 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Introduction Ø Law Enforcement Response to Electronic Evidence Ø Latent Nature of Electronic Evidence Ø RULE 1 OF DIGITAL FORENSICS Ø Forensic Process 75 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Introduction Ø Law Enforcement Response to Electronic Evidence Ø Latent Nature of Electronic Evidence Ø RULE 1 OF DIGITAL FORENSICS Ø Forensic Process 75 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Law Enforcement Response to Electronic Evidence Ø Computers involved in crime may be q Tools q Repositories of evidence q Targets Ø Personnel of many types may be involved in responding to crime involving computers q LEOs q Investigators (private, corporate) q Forensic examiners q Managers (case, corporate, political) Ø First responder can be anyone in LE q Must safeguard EE against loss or tampering 76 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Law Enforcement Response to Electronic Evidence Ø Computers involved in crime may be q Tools q Repositories of evidence q Targets Ø Personnel of many types may be involved in responding to crime involving computers q LEOs q Investigators (private, corporate) q Forensic examiners q Managers (case, corporate, political) Ø First responder can be anyone in LE q Must safeguard EE against loss or tampering 76 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
![Latent Nature of Electronic Evidence [EE] Ø “Electronic evidence is information and data of Latent Nature of Electronic Evidence [EE] Ø “Electronic evidence is information and data of](https://present5.com/presentation/f9b96f87b7eed4194660fda8e75cb919/image-77.jpg) Latent Nature of Electronic Evidence [EE] Ø “Electronic evidence is information and data of investigative value that is stored on or transmitted by an electronic device. ” [ECSIGFR p. 17] Ø EE thus latent (like fingerprints, DNA evidence) because not immediately visible q Requires technical equipment & expertise q May need expert testimony in court to explain analysis Ø EE fragile q Easily destroyed or altered q Chain of custody & technical safeguards essential for successful prosecution 77 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Latent Nature of Electronic Evidence [EE] Ø “Electronic evidence is information and data of investigative value that is stored on or transmitted by an electronic device. ” [ECSIGFR p. 17] Ø EE thus latent (like fingerprints, DNA evidence) because not immediately visible q Requires technical equipment & expertise q May need expert testimony in court to explain analysis Ø EE fragile q Easily destroyed or altered q Chain of custody & technical safeguards essential for successful prosecution 77 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 RULE 1 OF DIGITAL FORENSICS HARM NOTHING! (E. G. , DON’T LET AMATEURS COLLECT DIGITAL EVIDENCE) 78 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
RULE 1 OF DIGITAL FORENSICS HARM NOTHING! (E. G. , DON’T LET AMATEURS COLLECT DIGITAL EVIDENCE) 78 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Forensic Process Key phases: Ø Collection: search / recognition / collection / documentation of evidence Ø Examination (technical perspective) q Document content / state of evidence q Reveal hidden data q Identify relevant data Ø Analysis (legal perspective) Ø Reporting q Process notes for expert testimony q Results q Reliability 79 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Forensic Process Key phases: Ø Collection: search / recognition / collection / documentation of evidence Ø Examination (technical perspective) q Document content / state of evidence q Reveal hidden data q Identify relevant data Ø Analysis (legal perspective) Ø Reporting q Process notes for expert testimony q Results q Reliability 79 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Nature of Electronic Evidence Quoting directly from ECSIGFR p. 20 Ø Is often latent in the same sense as fingerprints or DNA evidence. Ø Can transcend borders with ease and speed. Ø Is fragile and can be easily altered, damaged, or destroyed. Ø Is sometimes time-sensitive Ø Therefore only those with expertise should handle digital evidence q. E. g. , rebooting alters or destroys data that could be useful in investigation q. Forensic data-capture tools often require training 80 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Nature of Electronic Evidence Quoting directly from ECSIGFR p. 20 Ø Is often latent in the same sense as fingerprints or DNA evidence. Ø Can transcend borders with ease and speed. Ø Is fragile and can be easily altered, damaged, or destroyed. Ø Is sometimes time-sensitive Ø Therefore only those with expertise should handle digital evidence q. E. g. , rebooting alters or destroys data that could be useful in investigation q. Forensic data-capture tools often require training 80 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Handling Electronic Evidence at the Crime Scene Ø Preparations q. Secure and document crime scene (photographs, sketches, notes) q. Use protective equipment to avoid contaminating crime scene (e. g. , gloves) Ø Recognize and identify evidence Ø Document electronic equipment at crime scene Ø Collect and preserve EE Ø Package and transport EE Ø Maintain chain of custody 81 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Handling Electronic Evidence at the Crime Scene Ø Preparations q. Secure and document crime scene (photographs, sketches, notes) q. Use protective equipment to avoid contaminating crime scene (e. g. , gloves) Ø Recognize and identify evidence Ø Document electronic equipment at crime scene Ø Collect and preserve EE Ø Package and transport EE Ø Maintain chain of custody 81 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 The Digital Forensics Tool Kit (1) Volonino et al. p 126 ff ECSIGFR p 23 ff Ø Cellular phone Ø Basic hardware toolkit: screwdrivers, pliers, duct tape etc. Ø Watertight & static-resistant plastic evidence bags Ø Labels and indelible markers Ø Bootable media: DOS startup, bootable CDs, bootable USB drives w/ forensic software Ø Cables: USB, Fire. Wire, CAT 5 crossover & straight -through, power cables Ø Laptop computer for tools and notes Ø PDA with integrated camera & link to PC 82 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Digital Forensics Tool Kit (1) Volonino et al. p 126 ff ECSIGFR p 23 ff Ø Cellular phone Ø Basic hardware toolkit: screwdrivers, pliers, duct tape etc. Ø Watertight & static-resistant plastic evidence bags Ø Labels and indelible markers Ø Bootable media: DOS startup, bootable CDs, bootable USB drives w/ forensic software Ø Cables: USB, Fire. Wire, CAT 5 crossover & straight -through, power cables Ø Laptop computer for tools and notes Ø PDA with integrated camera & link to PC 82 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 The Digital Forensics Tool Kit (2) Ø High-resolution camera(s) w/ date-time stamps Ø Hardware-write blocker (e. g. , Fast. Bloc, Drive. Lock) to prevent damage to removed drive Ø Luggage cart Ø Flashlight Ø Power strip Ø Log book Ø Gloves Ø External USB hard drive Ø Forensic examiner platform (e. g. , specialized tools) for data acquisition 83 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Digital Forensics Tool Kit (2) Ø High-resolution camera(s) w/ date-time stamps Ø Hardware-write blocker (e. g. , Fast. Bloc, Drive. Lock) to prevent damage to removed drive Ø Luggage cart Ø Flashlight Ø Power strip Ø Log book Ø Gloves Ø External USB hard drive Ø Forensic examiner platform (e. g. , specialized tools) for data acquisition 83 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Specialized Forensics Tools Ø E. g. , Logicube® < http: //www. logicube. com/ > Ø Popular hard-drive cloning systems Ø Used by q. Law enforcement q. Military q. Internal IT departments Ø Products support various drive interfaces and connectors q. IDE q. SATA q. SAS q. SCSI q. USB 84 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Specialized Forensics Tools Ø E. g. , Logicube® < http: //www. logicube. com/ > Ø Popular hard-drive cloning systems Ø Used by q. Law enforcement q. Military q. Internal IT departments Ø Products support various drive interfaces and connectors q. IDE q. SATA q. SAS q. SCSI q. USB 84 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Establish Your Search Parameters Volonino et al. p 129 Ø What types of evidence are you looking for? q Photographs? Document? DBs? E-mail? Ø What is the user’s/suspect’s skill level? Ø What kind of hardware is involved? q Computers (Mac? Windows? Linux? ) q PDAs? Cell phones? Watches? Ø What kind of software is involved? Ø Do I need to preserve other types of evidence? q Fingerprints? DNA? Ø What is the computer environment? q Network? (Protocols, topology…) ISP? q Security? User. IDs? Passwords? Encryption? q Real bombs inside the cases [thanks to Chris Tanguay] 85 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Establish Your Search Parameters Volonino et al. p 129 Ø What types of evidence are you looking for? q Photographs? Document? DBs? E-mail? Ø What is the user’s/suspect’s skill level? Ø What kind of hardware is involved? q Computers (Mac? Windows? Linux? ) q PDAs? Cell phones? Watches? Ø What kind of software is involved? Ø Do I need to preserve other types of evidence? q Fingerprints? DNA? Ø What is the computer environment? q Network? (Protocols, topology…) ISP? q Security? User. IDs? Passwords? Encryption? q Real bombs inside the cases [thanks to Chris Tanguay] 85 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Managing the Onsite Volonino et al. p 130 ff Investigation Ø Maintain integrity of data collection process Ø Estimate time required for onsite examination Ø Limit costs to target organization q Legal liability for interruptions of business q May outweigh importance of crime q May stop investigation Ø Evaluate necessary equipment for onsite work Ø Evaluate personnel costs q Who should be onsite? q Would their involvement impede other critical investigations? 86 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Managing the Onsite Volonino et al. p 130 ff Investigation Ø Maintain integrity of data collection process Ø Estimate time required for onsite examination Ø Limit costs to target organization q Legal liability for interruptions of business q May outweigh importance of crime q May stop investigation Ø Evaluate necessary equipment for onsite work Ø Evaluate personnel costs q Who should be onsite? q Would their involvement impede other critical investigations? 86 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Remove Suspect from Computer Moore Ch 9 Ø Potential for instant data deletion by suspect q. Can prepare programs to delete key evidence q. Activate at touch of keyboard (macros, “hot keys”) q. Or through voice-command interface üE. g. , Dragon Dictation, Windows voice-recognition Ø No-knock search warrants still problematic Ø Therefore instantly move suspect away from computer q. Shake hands with LEO & prevent return q. Physical force only if necessary q. Allow no return to computer BOOM 87 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Remove Suspect from Computer Moore Ch 9 Ø Potential for instant data deletion by suspect q. Can prepare programs to delete key evidence q. Activate at touch of keyboard (macros, “hot keys”) q. Or through voice-command interface üE. g. , Dragon Dictation, Windows voice-recognition Ø No-knock search warrants still problematic Ø Therefore instantly move suspect away from computer q. Shake hands with LEO & prevent return q. Physical force only if necessary q. Allow no return to computer BOOM 87 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Secure the Scene Ø Photograph scene q Agencies are currently using digital cameras q But recall discussion of falsifiability of digital images q Use video camera to document process q May see cases hinging on credibility of such evidence üDefense sometimes challenges timestamps üBut claims of fraud / error must include likelihood (proffer of proof) Ø Photograph computer screen(s) q Especially evidence of system time Ø Photograph everything that may be evidence q Cost is not a factor w/ digital cameras 88 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Secure the Scene Ø Photograph scene q Agencies are currently using digital cameras q But recall discussion of falsifiability of digital images q Use video camera to document process q May see cases hinging on credibility of such evidence üDefense sometimes challenges timestamps üBut claims of fraud / error must include likelihood (proffer of proof) Ø Photograph computer screen(s) q Especially evidence of system time Ø Photograph everything that may be evidence q Cost is not a factor w/ digital cameras 88 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Disconnect Outside Control Ø Remove network connectivity q. Phone line / DSL q. Cable / satellite modem q. Suspect may be storing evidence on remote systems Ø Wireless connectivity may be more difficult to handle* q. Wireless I/F may be integrated within computer case – not obvious outside q. Especially true in laptop computers Ø Look for evidence of home network q. May have data storage in other locations 89 *For more details see “The Need for a Technical Approach to Digital Forensic Evidence Collection for Wireless Technologies” by B. Turnbull & J. Slay (2006) < http: //www. itoc. usma. edu/Workshop/2006/ Program/Presentations/IAW 2006 -07 -1. pdf > Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Disconnect Outside Control Ø Remove network connectivity q. Phone line / DSL q. Cable / satellite modem q. Suspect may be storing evidence on remote systems Ø Wireless connectivity may be more difficult to handle* q. Wireless I/F may be integrated within computer case – not obvious outside q. Especially true in laptop computers Ø Look for evidence of home network q. May have data storage in other locations 89 *For more details see “The Need for a Technical Approach to Digital Forensic Evidence Collection for Wireless Technologies” by B. Turnbull & J. Slay (2006) < http: //www. itoc. usma. edu/Workshop/2006/ Program/Presentations/IAW 2006 -07 -1. pdf > Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Handling Downloads Ø What if system shows signs that user was downloading file(s)? q. Could be evidence Ø Photograph download window q. Reduces chance that suspect can successfully deny involvement in download q. May allow download to complete Ø Videotape entire process 90 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Handling Downloads Ø What if system shows signs that user was downloading file(s)? q. Could be evidence Ø Photograph download window q. Reduces chance that suspect can successfully deny involvement in download q. May allow download to complete Ø Videotape entire process 90 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Powering Down Computer Want to avoid damaging data Moore p 172 ff ECSIGFR p 30 ff Ø Determine Operating System Ø Save Data from Running Programs? Ø Save Data in RAM? Ø Handling Specific OSs Ø Laptop Computers 91 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Powering Down Computer Want to avoid damaging data Moore p 172 ff ECSIGFR p 30 ff Ø Determine Operating System Ø Save Data from Running Programs? Ø Save Data in RAM? Ø Handling Specific OSs Ø Laptop Computers 91 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Determine Operating System Ø GOAL: make bit-images of RAM and of DISK before going any further Ø OS does not influence which tools to use for bit-image capture onsite q. Mac versions q. Windows versions q. Unix flavors q. Hardware-specific OSs (cell phones, PDAs) Ø Must have right tools and procedures q. Avoid imprecise copy Ø Subject of more advanced courses 92 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Determine Operating System Ø GOAL: make bit-images of RAM and of DISK before going any further Ø OS does not influence which tools to use for bit-image capture onsite q. Mac versions q. Windows versions q. Unix flavors q. Hardware-specific OSs (cell phones, PDAs) Ø Must have right tools and procedures q. Avoid imprecise copy Ø Subject of more advanced courses 92 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Save Data from Running Programs? Ø May be able to see that programs are running (e. g. , on program bar) Ø Disagreement among experts q. Pull the plug: data in temporary regions on disk anyway; or q. Save the temporary data explicitly in case they have not yet been written to disk Ø Technical knowledge essential q. E. g. , many OS use extensive write-behind buffering q. Encrypted volumes may be corrupted by instant power-down 93 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Save Data from Running Programs? Ø May be able to see that programs are running (e. g. , on program bar) Ø Disagreement among experts q. Pull the plug: data in temporary regions on disk anyway; or q. Save the temporary data explicitly in case they have not yet been written to disk Ø Technical knowledge essential q. E. g. , many OS use extensive write-behind buffering q. Encrypted volumes may be corrupted by instant power-down 93 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Save Data in RAM? Ø Most OSs use Virtual Memory (VM) q. Reserve space on hard disk for extension of main memory (RAM) q. Swap data back and forth between VM and RAM q. Thus VM swap file a treasure-trove of potentially valuable data about what was in RAM q. However, some users disable VM because of large RAM (e. g. , 2 GB) Ø Specialized utilities for saving data directly from RAM depending on OS & hardware Ø Particularly important for cell phones and PDAs which may depend on battery power for maintenance of volatile memory 94 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Save Data in RAM? Ø Most OSs use Virtual Memory (VM) q. Reserve space on hard disk for extension of main memory (RAM) q. Swap data back and forth between VM and RAM q. Thus VM swap file a treasure-trove of potentially valuable data about what was in RAM q. However, some users disable VM because of large RAM (e. g. , 2 GB) Ø Specialized utilities for saving data directly from RAM depending on OS & hardware Ø Particularly important for cell phones and PDAs which may depend on battery power for maintenance of volatile memory 94 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Handling Specific OSs at the Scene Ø Not suitable topic for this course Ø For brief overview of instructions involved, see Moore p 175 ff q. Microsoft OSs üWindows 3. 11 through XP q. Macintosh q. Unix/Linux Ø Special tools for PDAs (e. g. , Palm, Windows CE) 95 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Handling Specific OSs at the Scene Ø Not suitable topic for this course Ø For brief overview of instructions involved, see Moore p 175 ff q. Microsoft OSs üWindows 3. 11 through XP q. Macintosh q. Unix/Linux Ø Special tools for PDAs (e. g. , Palm, Windows CE) 95 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Laptop Computers Ø Problem: unplugging laptop instantly switches to battery power Ø Need to remove battery from laptop q. Usually easy q. Simple latch or an easy screw or two Ø Keep battery with laptop for bagging & shipment * TRS Model 100 from 1983 Computer Desktop Encyclopedia Used with permission. Prof Kabay’s very first portable! 96 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. *
Laptop Computers Ø Problem: unplugging laptop instantly switches to battery power Ø Need to remove battery from laptop q. Usually easy q. Simple latch or an easy screw or two Ø Keep battery with laptop for bagging & shipment * TRS Model 100 from 1983 Computer Desktop Encyclopedia Used with permission. Prof Kabay’s very first portable! 96 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. *
 Disassembling Computer Ø Critically important that each computer can be reassembled exactly as it was Ø Identify each computer with unique identifier Ø Label absolutely every component with its computer’s identifier q. Particularly the ports q. Mask and mark ports not in use q. Masking tape or colored labels are fine q. Colors can be assigned to specific computers Ø Show directions of connectors (which end to which computer and port) 97 Moore p 179 ff Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Disassembling Computer Ø Critically important that each computer can be reassembled exactly as it was Ø Identify each computer with unique identifier Ø Label absolutely every component with its computer’s identifier q. Particularly the ports q. Mask and mark ports not in use q. Masking tape or colored labels are fine q. Colors can be assigned to specific computers Ø Show directions of connectors (which end to which computer and port) 97 Moore p 179 ff Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Securing Additional Evidence (1) Ø How much peripheral equipment should you seize? q. Terms of warrant q. Peculiarities of system (e. g. , old) Ø Peripherals may have evidence q. Cameras, games (XBox, PSPs) q. Scanners (check the scanner bed) q. Sound recorders, i. Pods (can even carry computer data or operating environments)* q. Calculators (large memory) *Thanks to Ryan Davis Ø Other evidence & Stanley François q. Paper notes and documents q. Digital storage media (magnetic & optical disks – but remember old tape systems) q. Label evidence bags in detail (where, who…) 98 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Securing Additional Evidence (1) Ø How much peripheral equipment should you seize? q. Terms of warrant q. Peculiarities of system (e. g. , old) Ø Peripherals may have evidence q. Cameras, games (XBox, PSPs) q. Scanners (check the scanner bed) q. Sound recorders, i. Pods (can even carry computer data or operating environments)* q. Calculators (large memory) *Thanks to Ryan Davis Ø Other evidence & Stanley François q. Paper notes and documents q. Digital storage media (magnetic & optical disks – but remember old tape systems) q. Label evidence bags in detail (where, who…) 98 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Securing Additional Evidence (2) USB Port Ø Already mentioned obvious devices q. PDAs, cell phones, data-watches Ø USB flash drives may not be obvious q. Small q. May look like pens q. May look like … wait for it … sushi! 99 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Securing Additional Evidence (2) USB Port Ø Already mentioned obvious devices q. PDAs, cell phones, data-watches Ø USB flash drives may not be obvious q. Small q. May look like pens q. May look like … wait for it … sushi! 99 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Preparing for Transport Ø Complete asset-seizure log q Provide copy to suspect q Get suspect to sign log sheet q Note refusal & have OIC sign sheet Ø Bags or boxes depending on agency q Do not use Styrofoam – static electricity q Disk drives that take mobile media (floppies, CDs) should have blanks inserted to prevent damage in transit Ø DO NOT PUT IN TRUNK OF CAR q Heat & electronic gear can harm evidence q Place on floor or on storage surface 100 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Preparing for Transport Ø Complete asset-seizure log q Provide copy to suspect q Get suspect to sign log sheet q Note refusal & have OIC sign sheet Ø Bags or boxes depending on agency q Do not use Styrofoam – static electricity q Disk drives that take mobile media (floppies, CDs) should have blanks inserted to prevent damage in transit Ø DO NOT PUT IN TRUNK OF CAR q Heat & electronic gear can harm evidence q Place on floor or on storage surface 100 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Chain of Custody Ø Standard concerns about maintaining credible protection of evidence in custody Ø NEVER allow evidence to be unsecured at any time Ø Digital evidence can be altered at any time Ø Unique identification to ensure credibility in court Ø Detailed records of who accessed the evidence at what time and for how long Ø Provide detailed records of why individuals needed access to evidence Ø Ideally, original data must never be released – keep for comparison with digital bitwise copies if anyone challenges authenticity 101 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Chain of Custody Ø Standard concerns about maintaining credible protection of evidence in custody Ø NEVER allow evidence to be unsecured at any time Ø Digital evidence can be altered at any time Ø Unique identification to ensure credibility in court Ø Detailed records of who accessed the evidence at what time and for how long Ø Provide detailed records of why individuals needed access to evidence Ø Ideally, original data must never be released – keep for comparison with digital bitwise copies if anyone challenges authenticity 101 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 BREAK 11’ 3” 102 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
BREAK 11’ 3” 102 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Analysis of Evidence Ø Introduction to Computer Forensics q How Computers Store Data q Internet Activity Stored on Disk Ø Computer Forensics Process q Verifying Files and File Signatures q Forensic Analysis q Forensics Report Ø Concealing Evidence Ø Computer Forensics Software Packages q En. Case q Forensic Tool Kit q Non GUI Software Utilities 103 Moore Ch 10 Clifford pp 160 -174 ECSIGFR pp 37 -46 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Analysis of Evidence Ø Introduction to Computer Forensics q How Computers Store Data q Internet Activity Stored on Disk Ø Computer Forensics Process q Verifying Files and File Signatures q Forensic Analysis q Forensics Report Ø Concealing Evidence Ø Computer Forensics Software Packages q En. Case q Forensic Tool Kit q Non GUI Software Utilities 103 Moore Ch 10 Clifford pp 160 -174 ECSIGFR pp 37 -46 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Introduction to Computer Forensics Ø Forensic science q. Latin forensis = “of legal proceedings from forum where discussions take place” q. Application of scientific techniques to criminal investigation q. Presentation of evidence at trial Ø Growing value to computer forensics q. Increasing role of computers throughout human activity, including crime q. Persistence of digital trail useful as evidence q. Opportunities for employment in LE and in private industry Moore Ch 19 104 Clifford Ch 3 pp 160 -174 NIJ Guide Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. for First Responders pp
Introduction to Computer Forensics Ø Forensic science q. Latin forensis = “of legal proceedings from forum where discussions take place” q. Application of scientific techniques to criminal investigation q. Presentation of evidence at trial Ø Growing value to computer forensics q. Increasing role of computers throughout human activity, including crime q. Persistence of digital trail useful as evidence q. Opportunities for employment in LE and in private industry Moore Ch 19 104 Clifford Ch 3 pp 160 -174 NIJ Guide Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. for First Responders pp
 How Computers Store Data A - Platter/s B - Read/Write Head/s (and slider) C - Actuator Arm/s D - Actuator E - Spindle 105 http: //www. helpwithpcs. com/courses/hard-drive-mechanics. htm Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
How Computers Store Data A - Platter/s B - Read/Write Head/s (and slider) C - Actuator Arm/s D - Actuator E - Spindle 105 http: //www. helpwithpcs. com/courses/hard-drive-mechanics. htm Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
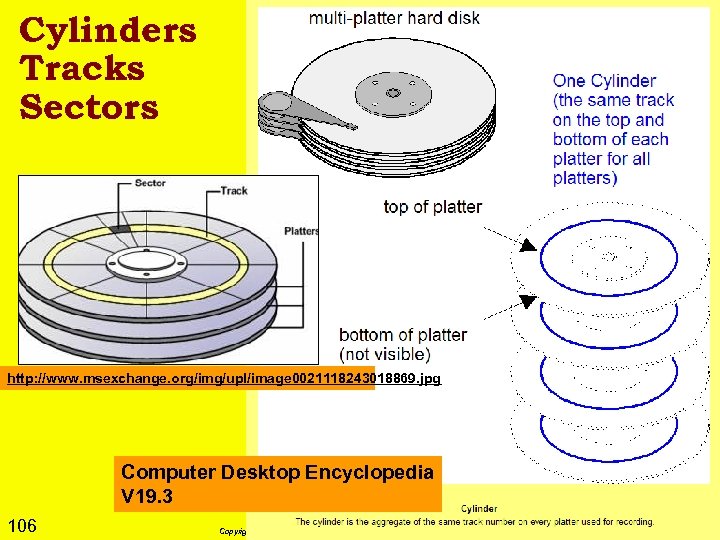 Cylinders Tracks Sectors http: //www. msexchange. org/img/upl/image 0021118243018869. jpg Computer Desktop Encyclopedia V 19. 3 106 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Cylinders Tracks Sectors http: //www. msexchange. org/img/upl/image 0021118243018869. jpg Computer Desktop Encyclopedia V 19. 3 106 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
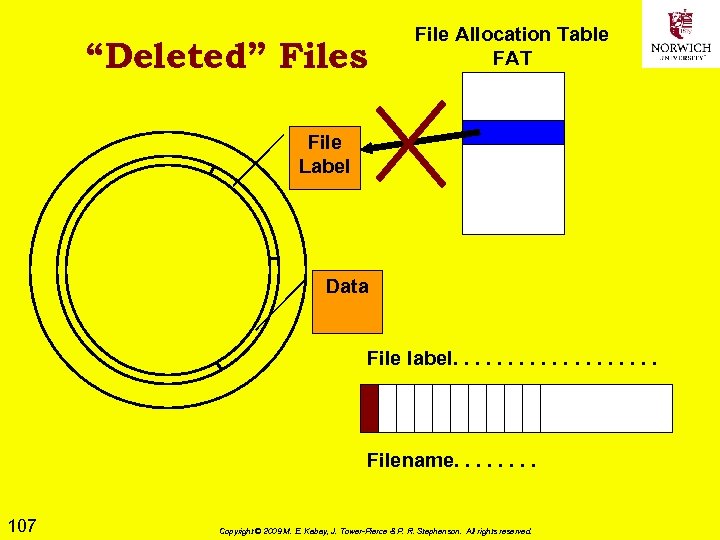 “Deleted” Files File Allocation Table FAT File Label Data File label. . . . . Filename. . . . 107 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
“Deleted” Files File Allocation Table FAT File Label Data File label. . . . . Filename. . . . 107 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
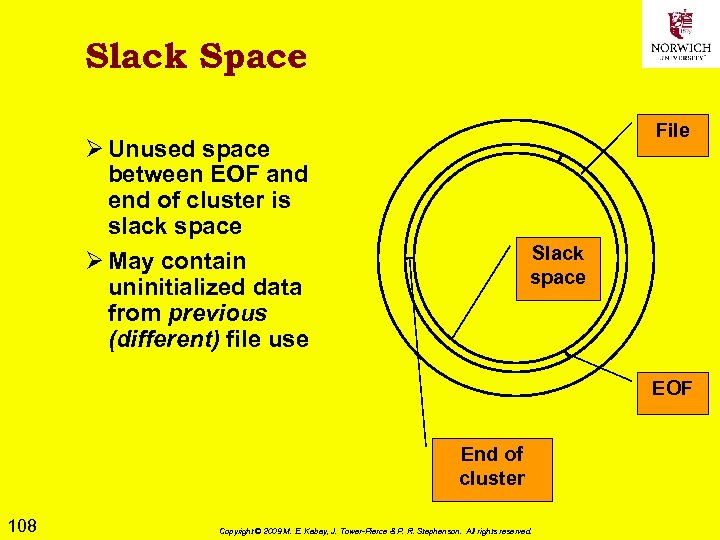 Slack Space File Ø Unused space between EOF and end of cluster is slack space Ø May contain uninitialized data from previous (different) file use Slack space EOF End of cluster 108 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Slack Space File Ø Unused space between EOF and end of cluster is slack space Ø May contain uninitialized data from previous (different) file use Slack space EOF End of cluster 108 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
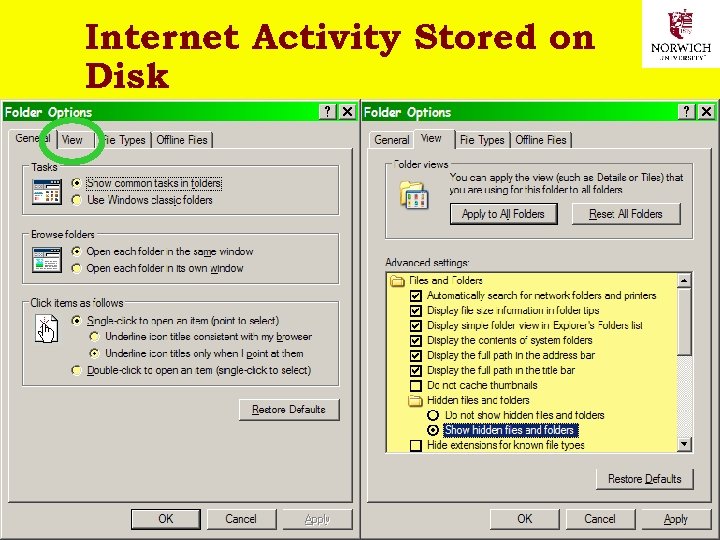 Internet Activity Stored on Disk 109 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Activity Stored on Disk 109 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
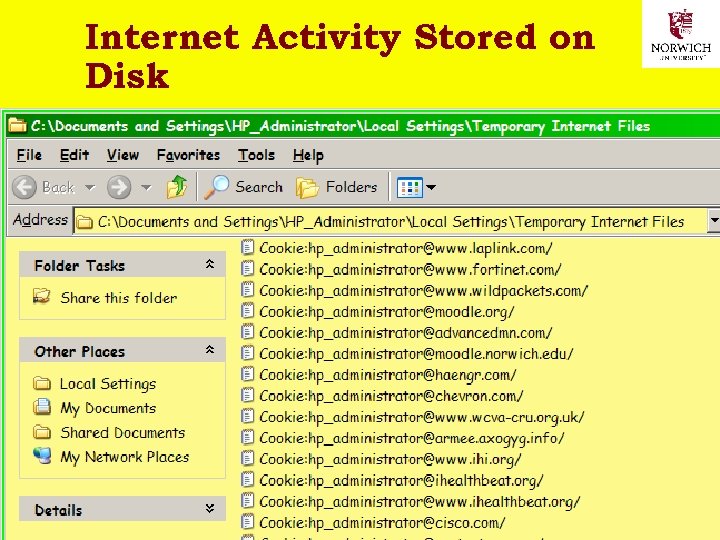 Internet Activity Stored on Disk 110 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Activity Stored on Disk 110 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
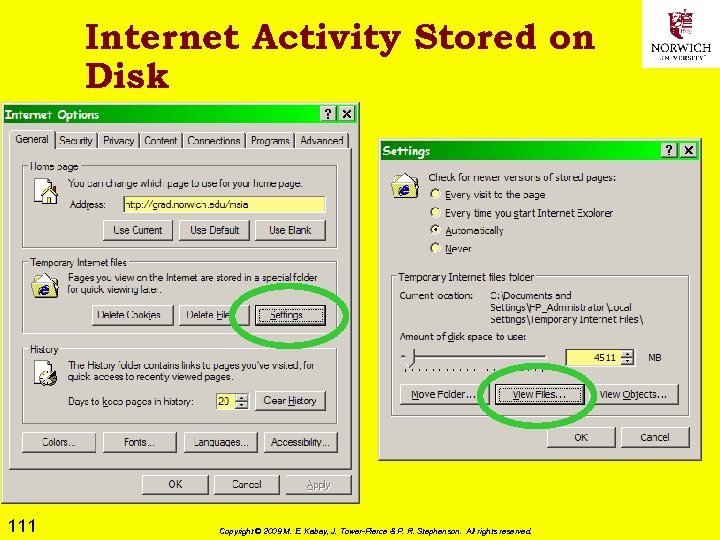 Internet Activity Stored on Disk 111 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Activity Stored on Disk 111 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
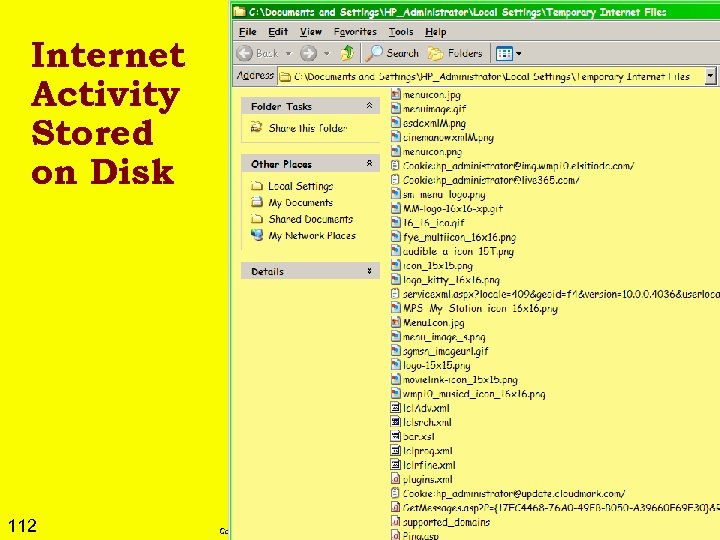 Internet Activity Stored on Disk 112 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Internet Activity Stored on Disk 112 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Computer Forensics Process Ø Copy entire hard disk(s) q. Disks typically now 100 GB and up q. CD-ROM now too small (700 MB) q. Even DVDs too small (4 or 8 GB) q. Separate medium – new hard disk best ü 250 GB Western Digital USB for $100 ü 1 TB Maxtor external drive for $200 Ø Make bit-for-bit copy (bit-image) q. Ordinary copy reads file, creates new file üLose all data in deleted files üLose all data in slack space q. Bit-image copies everything 113 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Computer Forensics Process Ø Copy entire hard disk(s) q. Disks typically now 100 GB and up q. CD-ROM now too small (700 MB) q. Even DVDs too small (4 or 8 GB) q. Separate medium – new hard disk best ü 250 GB Western Digital USB for $100 ü 1 TB Maxtor external drive for $200 Ø Make bit-for-bit copy (bit-image) q. Ordinary copy reads file, creates new file üLose all data in deleted files üLose all data in slack space q. Bit-image copies everything 113 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Digitally Securing Evidence Ø How can one mark digital data so that any change, even to just one bit, flags the copy as bad? Ø Three approaches q. Hash q. Encryption q. Digital signatures 114 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Digitally Securing Evidence Ø How can one mark digital data so that any change, even to just one bit, flags the copy as bad? Ø Three approaches q. Hash q. Encryption q. Digital signatures 114 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
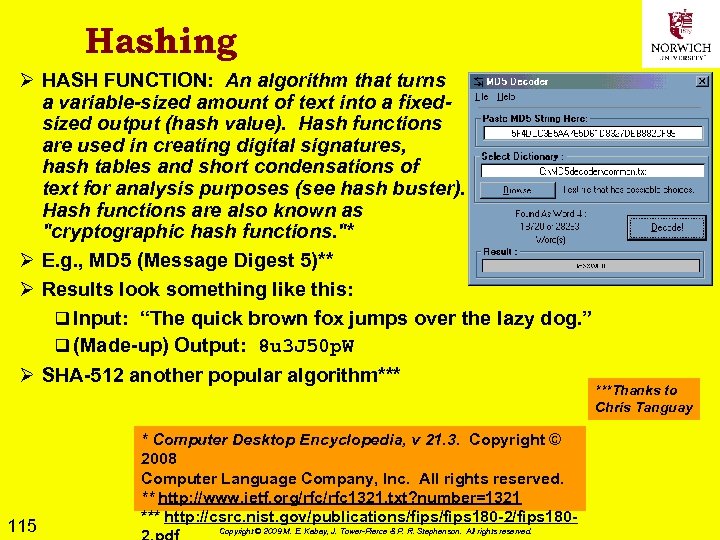 Hashing Ø HASH FUNCTION: An algorithm that turns a variable-sized amount of text into a fixedsized output (hash value). Hash functions are used in creating digital signatures, hash tables and short condensations of text for analysis purposes (see hash buster). Hash functions are also known as "cryptographic hash functions. "* Ø E. g. , MD 5 (Message Digest 5)** Ø Results look something like this: q Input: “The quick brown fox jumps over the lazy dog. ” q (Made-up) Output: 8 u 3 J 50 p. W Ø SHA-512 another popular algorithm*** 115 * Computer Desktop Encyclopedia, v 21. 3. Copyright © 2008 Computer Language Company, Inc. All rights reserved. ** http: //www. ietf. org/rfc 1321. txt? number=1321 *** http: //csrc. nist. gov/publications/fips 180 -2/fips 180 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. ***Thanks to Chris Tanguay
Hashing Ø HASH FUNCTION: An algorithm that turns a variable-sized amount of text into a fixedsized output (hash value). Hash functions are used in creating digital signatures, hash tables and short condensations of text for analysis purposes (see hash buster). Hash functions are also known as "cryptographic hash functions. "* Ø E. g. , MD 5 (Message Digest 5)** Ø Results look something like this: q Input: “The quick brown fox jumps over the lazy dog. ” q (Made-up) Output: 8 u 3 J 50 p. W Ø SHA-512 another popular algorithm*** 115 * Computer Desktop Encyclopedia, v 21. 3. Copyright © 2008 Computer Language Company, Inc. All rights reserved. ** http: //www. ietf. org/rfc 1321. txt? number=1321 *** http: //csrc. nist. gov/publications/fips 180 -2/fips 180 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. ***Thanks to Chris Tanguay
 Hashing (cont’d) Ø Hashing functions are designed so that any change to the input produces a different output Ø E. g. (made-up, not real): q“The quick brown fox jumped over the lazy dog. ” could hash to “ 8 u 3 J 50 p. W” q“The quick brown fox jumped over the lazy dog!” could hash to “Y 35_e)t 7 k” Ø Thus by keeping a copy of all data with hash function output, one can identify changed data. 116 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Hashing (cont’d) Ø Hashing functions are designed so that any change to the input produces a different output Ø E. g. (made-up, not real): q“The quick brown fox jumped over the lazy dog. ” could hash to “ 8 u 3 J 50 p. W” q“The quick brown fox jumped over the lazy dog!” could hash to “Y 35_e)t 7 k” Ø Thus by keeping a copy of all data with hash function output, one can identify changed data. 116 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Using Hash Function for File Inventory Ø File. List utility q. Every single file on disk q. Directory tree format Ø Most important: MD 5 hash q. Applied to copy of original disk q. Every file marked with hash q. Nearly impossible to alter file without altering hash q. Unchanged MD 5 hash value is very strong evidence that files have not been altered since the hash was originally calculated 117 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Using Hash Function for File Inventory Ø File. List utility q. Every single file on disk q. Directory tree format Ø Most important: MD 5 hash q. Applied to copy of original disk q. Every file marked with hash q. Nearly impossible to alter file without altering hash q. Unchanged MD 5 hash value is very strong evidence that files have not been altered since the hash was originally calculated 117 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Digital Signatures Ø Digital signatures encrypt a hash Ø Quicker than encrypting entire source Ø Many different tools available for such signature Ø Legally recognized as evidence of data integrity Ø Can also indicate exactly who signed document Ø Contributes to chain of evidence by tying specific analyst to digital copy 118 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Digital Signatures Ø Digital signatures encrypt a hash Ø Quicker than encrypting entire source Ø Many different tools available for such signature Ø Legally recognized as evidence of data integrity Ø Can also indicate exactly who signed document Ø Contributes to chain of evidence by tying specific analyst to digital copy 118 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
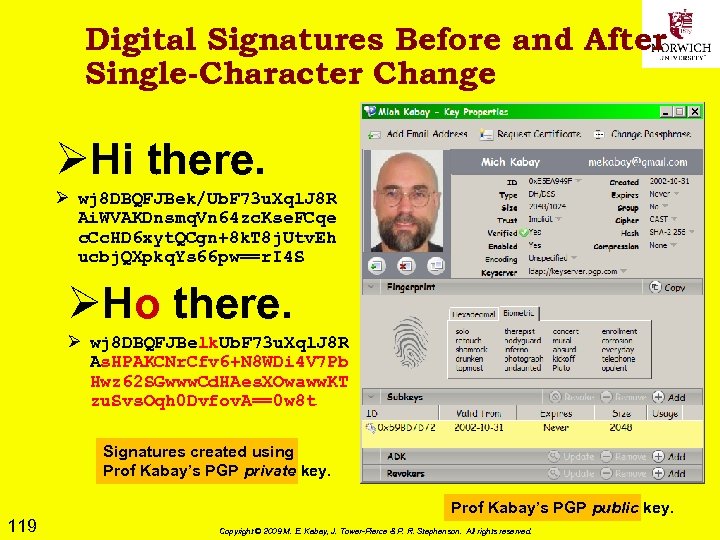 Digital Signatures Before and After Single-Character Change ØHi there. Ø wj 8 DBQFJBek/Ub. F 73 u. Xql. J 8 R Ai. WVAKDnsmq. Vn 64 zc. Kse. FCqe c. Cc. HD 6 xyt. QCgn+8 k. T 8 j. Utv. Eh ucbj. QXpkq. Ys 66 pw==r. I 4 S ØHo there. Ø wj 8 DBQFJBelk. Ub. F 73 u. Xql. J 8 R As. HPAKCNr. Cfv 6+N 8 WDi 4 V 7 Pb Hwz 62 SGwww. Cd. HAes. XOwaww. KT zu. Svs. Oqh 0 Dvfov. A==0 w 8 t Signatures created using Prof Kabay’s PGP private key. 119 Prof Kabay’s PGP public key. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Digital Signatures Before and After Single-Character Change ØHi there. Ø wj 8 DBQFJBek/Ub. F 73 u. Xql. J 8 R Ai. WVAKDnsmq. Vn 64 zc. Kse. FCqe c. Cc. HD 6 xyt. QCgn+8 k. T 8 j. Utv. Eh ucbj. QXpkq. Ys 66 pw==r. I 4 S ØHo there. Ø wj 8 DBQFJBelk. Ub. F 73 u. Xql. J 8 R As. HPAKCNr. Cfv 6+N 8 WDi 4 V 7 Pb Hwz 62 SGwww. Cd. HAes. XOwaww. KT zu. Svs. Oqh 0 Dvfov. A==0 w 8 t Signatures created using Prof Kabay’s PGP private key. 119 Prof Kabay’s PGP public key. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Verifying Files and File Signatures Ø Create digital signature for disk contents q Typically use MD 5 hash q Effectively impossible to modify contents of original disk without changing hash Ø Analyze files to detect altered file types q Can crudely hide data by pretending that images are documents (etc) q Forensic packages can detect such subterfuges Ø Error on p. 196 of Moore (Chapter 10): author meant “algorithm” where “logarithm” is written in paragraph beginning “The MD 5 logarithm…. ” 120 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Verifying Files and File Signatures Ø Create digital signature for disk contents q Typically use MD 5 hash q Effectively impossible to modify contents of original disk without changing hash Ø Analyze files to detect altered file types q Can crudely hide data by pretending that images are documents (etc) q Forensic packages can detect such subterfuges Ø Error on p. 196 of Moore (Chapter 10): author meant “algorithm” where “logarithm” is written in paragraph beginning “The MD 5 logarithm…. ” 120 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Concealing Evidence Ø Stop people from finding or capturing information q. Prevent penetration of system perimeters Ø Stop people from using information q. Encryption Ø Stop people from knowing there’s any information q. Misleading directory and file names q. Misleading file types q. Information hiding: steganography 121 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Concealing Evidence Ø Stop people from finding or capturing information q. Prevent penetration of system perimeters Ø Stop people from using information q. Encryption Ø Stop people from knowing there’s any information q. Misleading directory and file names q. Misleading file types q. Information hiding: steganography 121 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Hard to Find Ø Secret compartments (furniture, clothing, luggage) Ø Messages placed inside books, in book covers. . . Ø Palimpsests: overwriting or overpainting 122 The Archimedes Palimpsest discovered 1899 in Istanbul. Original Greek (3 rd century BCE) was overwritten at 90° in 12 th century CE by Greek Orthodox monks rights reserved. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. Allin Constantinople.
Hard to Find Ø Secret compartments (furniture, clothing, luggage) Ø Messages placed inside books, in book covers. . . Ø Palimpsests: overwriting or overpainting 122 The Archimedes Palimpsest discovered 1899 in Istanbul. Original Greek (3 rd century BCE) was overwritten at 90° in 12 th century CE by Greek Orthodox monks rights reserved. Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. Allin Constantinople.
 Hard to See Ø Invisible ink q. Substances change from colorless to colored upon treatment (heat, UV light…) q. Milk, lemon juice, cobalt chloride solution Ø Microdots q. Invented by Germans during WWII q. Images at high resolution q. Shrunken to tiny size – usually that of period (. ), dots on i, j or umlauts (ö) in text q. Read with microscope if you knew where to look 123 * Mark IV microdot camera < http: //en. wikipedia. org/wiki/Microdot > Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. *
Hard to See Ø Invisible ink q. Substances change from colorless to colored upon treatment (heat, UV light…) q. Milk, lemon juice, cobalt chloride solution Ø Microdots q. Invented by Germans during WWII q. Images at high resolution q. Shrunken to tiny size – usually that of period (. ), dots on i, j or umlauts (ö) in text q. Read with microscope if you knew where to look 123 * Mark IV microdot camera < http: //en. wikipedia. org/wiki/Microdot > Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved. *
 Hard to Notice 124 Ø Coded language q Writing, speech, symbols in pictorial art q Shared code-book + start-point permits decoding (not decryption) of meaning q E. g. , “The ship sails at midnight” Cipher for Telegraphic Corresponde = “Meet Bob on Thursday” — a code book used by Union Gene Joseph Hooker’s code clerk Ø Chaffing and winnowing (From Answers. com q Ron Rivest (1998) http: //tinyurl. com/6 gguav ) q Output large volume of info, hide small amounts of significant data q See < http: //theory. lcs. mit. edu/~rivest/chaffing. txt > Ø Steganography q Embedded information in music, pictures, numbers and data communications Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Hard to Notice 124 Ø Coded language q Writing, speech, symbols in pictorial art q Shared code-book + start-point permits decoding (not decryption) of meaning q E. g. , “The ship sails at midnight” Cipher for Telegraphic Corresponde = “Meet Bob on Thursday” — a code book used by Union Gene Joseph Hooker’s code clerk Ø Chaffing and winnowing (From Answers. com q Ron Rivest (1998) http: //tinyurl. com/6 gguav ) q Output large volume of info, hide small amounts of significant data q See < http: //theory. lcs. mit. edu/~rivest/chaffing. txt > Ø Steganography q Embedded information in music, pictures, numbers and data communications Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Searching for Hidden Information Ø Intelligent filters q Filter_I used only on copy of original data ü http: //www. forensics-intl. com/filter_i. html ü Removes binary data from output ü Eliminates useless ASCII strings ü Use in multiple passes, step by step Ø Slack space & free space q Getslack (http: //www. forensics-intl. com/getslack. html ) & Getfree (http: //www. forensics-intl. com/getfree. html ) q Convert these types of disk data into files q Can also create files from swap and cache Ø Steganography and steganalysis q Hiding data in low-order bits of a file q E. g. , putting text inside a picture file q See following slides 125 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Searching for Hidden Information Ø Intelligent filters q Filter_I used only on copy of original data ü http: //www. forensics-intl. com/filter_i. html ü Removes binary data from output ü Eliminates useless ASCII strings ü Use in multiple passes, step by step Ø Slack space & free space q Getslack (http: //www. forensics-intl. com/getslack. html ) & Getfree (http: //www. forensics-intl. com/getfree. html ) q Convert these types of disk data into files q Can also create files from swap and cache Ø Steganography and steganalysis q Hiding data in low-order bits of a file q E. g. , putting text inside a picture file q See following slides 125 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Steganography 126 Ø Steganography = information hiding q Greek: secret writing q Hiding existence of message or other data q Different from cryptography, which hides the meaning but not message itself Ø Sometimes referred to as using covert channels Illustration from article by Rachel Thomas (20 “Safety in numbers” in +plus magazine (21), q E. g. , could conceal text in Sept 2002. < http: //tinyurl. com/6 yalbs > Used with permission. low-order bits of cells of a spreadsheet q Currently most popular using images and music as channels for message Ø Press reports claim terrorists are using steganography – but see later slides Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Steganography 126 Ø Steganography = information hiding q Greek: secret writing q Hiding existence of message or other data q Different from cryptography, which hides the meaning but not message itself Ø Sometimes referred to as using covert channels Illustration from article by Rachel Thomas (20 “Safety in numbers” in +plus magazine (21), q E. g. , could conceal text in Sept 2002. < http: //tinyurl. com/6 yalbs > Used with permission. low-order bits of cells of a spreadsheet q Currently most popular using images and music as channels for message Ø Press reports claim terrorists are using steganography – but see later slides Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
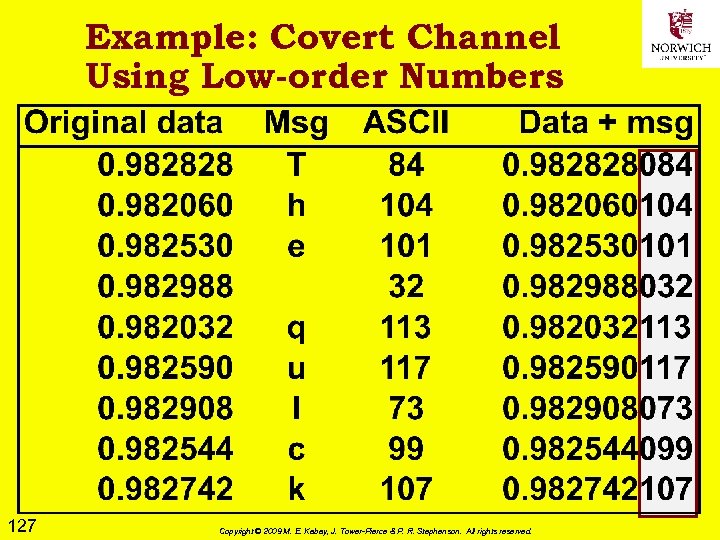 Example: Covert Channel Using Low-order Numbers 127 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Example: Covert Channel Using Low-order Numbers 127 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Example: Steganography Using a JPG Image Ø “The top image of Voyager contains no stego and is not featured in the search engine's output. However, the second image contains a 10 K text file encoded with JSteg…. ” Copyright © 2008 F. C. Gonzalez. All rights reserved. Used with permission. http: //mscmese. tripod. com/steg/ 128 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Example: Steganography Using a JPG Image Ø “The top image of Voyager contains no stego and is not featured in the search engine's output. However, the second image contains a 10 K text file encoded with JSteg…. ” Copyright © 2008 F. C. Gonzalez. All rights reserved. Used with permission. http: //mscmese. tripod. com/steg/ 128 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Steganography using JPG (cont’d) Ø Niels Provos & Peter Honeyman q. University of Michigan Center for Information Technology Integration q. Scanning Web for steganography Ø Located sovereigntime. jpg q. Shown on ABC TV program q. Retrieved concealed image embedded in JPG – B 52 s Ø ONLY case found in 2, 000 images checked http: //www. citi. umich. edu/projects/steganography/faq. html 129 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Steganography using JPG (cont’d) Ø Niels Provos & Peter Honeyman q. University of Michigan Center for Information Technology Integration q. Scanning Web for steganography Ø Located sovereigntime. jpg q. Shown on ABC TV program q. Retrieved concealed image embedded in JPG – B 52 s Ø ONLY case found in 2, 000 images checked http: //www. citi. umich. edu/projects/steganography/faq. html 129 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Why Use Steganography? Ø To avoid notice q. Some governments ban unauthorized use of encryption q. Obvious encryption may draw unwanted attention to its users q. Encrypted traffic may be susceptible to data-flow analysis (e. g. , identifying areas of greater operational importance) Ø To embed secret information in documents or other files to help protect copyright q. Allow copies to be identified or traced q. Called Digital Watermarking 130 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Why Use Steganography? Ø To avoid notice q. Some governments ban unauthorized use of encryption q. Obvious encryption may draw unwanted attention to its users q. Encrypted traffic may be susceptible to data-flow analysis (e. g. , identifying areas of greater operational importance) Ø To embed secret information in documents or other files to help protect copyright q. Allow copies to be identified or traced q. Called Digital Watermarking 130 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Steganography Tools Ø Medium + message + stegokey = stego-medium Ø Freeware, shareware, commercial programs available q. List of over 80 programs at 131 http: //www. stegoarchive. com/ Ø Many use JPG picture files as carrier Ø Scramdisk creates virtual encrypted drives by using a WAV audio file as output Ø MP 3 Stego program hides data in MPE audio files Ø Sam’s Big Play Maker hides data in a postmodern play (mostly gibberish) qhttp: //www. scramdisk. clara. net/playmake r. html Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Steganography Tools Ø Medium + message + stegokey = stego-medium Ø Freeware, shareware, commercial programs available q. List of over 80 programs at 131 http: //www. stegoarchive. com/ Ø Many use JPG picture files as carrier Ø Scramdisk creates virtual encrypted drives by using a WAV audio file as output Ø MP 3 Stego program hides data in MPE audio files Ø Sam’s Big Play Maker hides data in a postmodern play (mostly gibberish) qhttp: //www. scramdisk. clara. net/playmake r. html Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Sam’s Big Play Maker 132 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Sam’s Big Play Maker 132 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Steganalysis Ø Tools available to identify and reconstitute hidden messages Ø Carrier-information degradation problem q. Any modification of data in original file degrades quality üImage üSound 133 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Steganalysis Ø Tools available to identify and reconstitute hidden messages Ø Carrier-information degradation problem q. Any modification of data in original file degrades quality üImage üSound 133 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Steganalysis (cont’d) Ø Some stego tools generate signatures q. Statistical techniques use many modified images to identify signatures q. Can identify repetitive patterns q. Spot abnormal palette colors in images 134 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Steganalysis (cont’d) Ø Some stego tools generate signatures q. Statistical techniques use many modified images to identify signatures q. Can identify repetitive patterns q. Spot abnormal palette colors in images 134 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Forensic Analysis Ø Examine only bit-image copies of original disks Ø Can analyze every file Ø Locate files of specified types Ø List all file and real types Ø Search contents of files for strings Ø Search deleted files Ø Search unallocated space Ø Can take days of work 135 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Forensic Analysis Ø Examine only bit-image copies of original disks Ø Can analyze every file Ø Locate files of specified types Ø List all file and real types Ø Search contents of files for strings Ø Search deleted files Ø Search unallocated space Ø Can take days of work 135 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Forensics Report Ø Written report q. Can be partly software-generated q. Explain exactly how searches were performed q. Detail exact locations of evidence Ø Useful in many ways q. Help prosecutor decide whether to charge suspect q. Help persuade perpetrator to plea-bargain q. Support testimony in trial 136 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Forensics Report Ø Written report q. Can be partly software-generated q. Explain exactly how searches were performed q. Detail exact locations of evidence Ø Useful in many ways q. Help prosecutor decide whether to charge suspect q. Help persuade perpetrator to plea-bargain q. Support testimony in trial 136 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Computer Forensics Software Packages Ø GUI-based packages q. Helpful for LEOs with less experience üEn. Case from Guidance Software üForensic Tool Kit from Access. Data Ø Command-line interfaces q. Require expert to know command language 137 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Computer Forensics Software Packages Ø GUI-based packages q. Helpful for LEOs with less experience üEn. Case from Guidance Software üForensic Tool Kit from Access. Data Ø Command-line interfaces q. Require expert to know command language 137 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 En. Case Ø Preview allows selection of which disks to image (can save time) Ø Extensive training available Ø Ability to image disk without removal from case Ø Extensive automated search capabilities Ø http: //www. guidancesoftware. com/ 138 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
En. Case Ø Preview allows selection of which disks to image (can save time) Ø Extensive training available Ø Ability to image disk without removal from case Ø Extensive automated search capabilities Ø http: //www. guidancesoftware. com/ 138 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 En. Case 139 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
En. Case 139 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Forensic Tool Kit (FTK) Ø Similar to En. Case + improvements Ø E-mail search Ø Import image files in wide variety of formats Ø Password-cracker (Password Recovery Tool Kit, PRTK) Ø Distributed Network Attack (DNA) for parallel processing of decryption tasks Ø http: //www. accessdata. com/ 140 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Forensic Tool Kit (FTK) Ø Similar to En. Case + improvements Ø E-mail search Ø Import image files in wide variety of formats Ø Password-cracker (Password Recovery Tool Kit, PRTK) Ø Distributed Network Attack (DNA) for parallel processing of decryption tasks Ø http: //www. accessdata. com/ 140 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 FTK 141 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
FTK 141 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
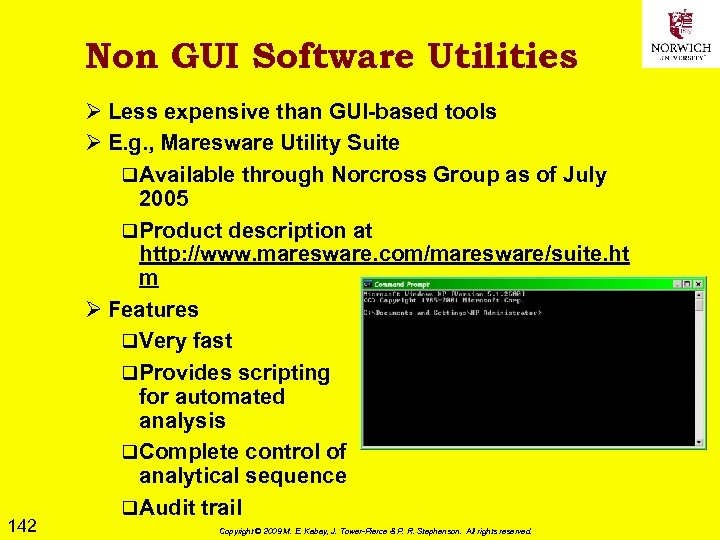 Non GUI Software Utilities 142 Ø Less expensive than GUI-based tools Ø E. g. , Maresware Utility Suite q Available through Norcross Group as of July 2005 q Product description at http: //www. maresware. com/maresware/suite. ht m Ø Features q Very fast q Provides scripting for automated analysis q Complete control of analytical sequence q Audit trail Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Non GUI Software Utilities 142 Ø Less expensive than GUI-based tools Ø E. g. , Maresware Utility Suite q Available through Norcross Group as of July 2005 q Product description at http: //www. maresware. com/maresware/suite. ht m Ø Features q Very fast q Provides scripting for automated analysis q Complete control of analytical sequence q Audit trail Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 BREAK 5’ 19” 143 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
BREAK 5’ 19” 143 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Use of Seized Materials & Results in Evidence Ø Admissibility of Digital Evidence Ø The Courts & Digital Evidence Ø Admission of Digital Evidence at Trial Moore Chapter 11 Clifford Chapter 3 pp 174 -186 SSCOEECI §V (PDF pp 119 -128). 144 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Use of Seized Materials & Results in Evidence Ø Admissibility of Digital Evidence Ø The Courts & Digital Evidence Ø Admission of Digital Evidence at Trial Moore Chapter 11 Clifford Chapter 3 pp 174 -186 SSCOEECI §V (PDF pp 119 -128). 144 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Admissibility of Digital Evidence Ø US v. Liebert (1975) q. Could computer records for alleged federal tax-evader be admitted as evidence? q. Yes, provided üProsecution could prove digital data were accurate and authentic üDefense was given opportunity to check Ø Resistance to admitting digital evidence continued q. Based on Federal Rules of Evidence qhttp: //www. law. cornell. edu/rules/fre/ q. Includes hearsay, authentication, nature of writings & copies 145 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Admissibility of Digital Evidence Ø US v. Liebert (1975) q. Could computer records for alleged federal tax-evader be admitted as evidence? q. Yes, provided üProsecution could prove digital data were accurate and authentic üDefense was given opportunity to check Ø Resistance to admitting digital evidence continued q. Based on Federal Rules of Evidence qhttp: //www. law. cornell. edu/rules/fre/ q. Includes hearsay, authentication, nature of writings & copies 145 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Hearsay Ø Rule 801: “…statement, other than one made by the declarant…. ” Ø Rule 801(d)(1) permits digital evidence such as e-mail or Web postings if q. Statement contradicts sworn testimony q. Statement rebuts accusation of lying q. Statement helps identify person 146 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Hearsay Ø Rule 801: “…statement, other than one made by the declarant…. ” Ø Rule 801(d)(1) permits digital evidence such as e-mail or Web postings if q. Statement contradicts sworn testimony q. Statement rebuts accusation of lying q. Statement helps identify person 146 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Authentication (1) Ø Authentication validates evidence Ø Rule 901(a) requires authentication q. One method uses selfauthentication mostly involving public records and certification (rarely works for digital evidence) q. Other approach involves authentication by a qualified professional Ø Prof Moore argues that only 2 of the Rule 901 subclauses apply to digital evidence: both involve testimony of expert witnesses 147 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Authentication (1) Ø Authentication validates evidence Ø Rule 901(a) requires authentication q. One method uses selfauthentication mostly involving public records and certification (rarely works for digital evidence) q. Other approach involves authentication by a qualified professional Ø Prof Moore argues that only 2 of the Rule 901 subclauses apply to digital evidence: both involve testimony of expert witnesses 147 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Nature of Writings Ø Rule 1002: specifies that original “writing, recording or photograph” must be available to authenticate copies presented in evidence Ø Rule 1001(1) stipulates that writings and recordings include “letters, words, or numbers, or their equivalent, set down by…magnetic impulse, mechanical or electronic recording, or other form of data compilation. ” Ø Rule 1004: allows for admission of bit-images of forensic data 148 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Nature of Writings Ø Rule 1002: specifies that original “writing, recording or photograph” must be available to authenticate copies presented in evidence Ø Rule 1001(1) stipulates that writings and recordings include “letters, words, or numbers, or their equivalent, set down by…magnetic impulse, mechanical or electronic recording, or other form of data compilation. ” Ø Rule 1004: allows for admission of bit-images of forensic data 148 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Copies Rule 1004 allows submission of copies when Ø Originals are lost or destroyed q. But verifiable copies make it easy to present in court given hash functions, proper bit-image Ø Original is not obtainable q. Usually have to return equipment to suspect q. But data may be destroyed by suspect Ø Original is in possession of opponent q. Suspect may refuse to grant access to original data 149 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Copies Rule 1004 allows submission of copies when Ø Originals are lost or destroyed q. But verifiable copies make it easy to present in court given hash functions, proper bit-image Ø Original is not obtainable q. Usually have to return equipment to suspect q. But data may be destroyed by suspect Ø Original is in possession of opponent q. Suspect may refuse to grant access to original data 149 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 The Courts & Digital Evidence Ø Frye v. US (1923) Ø Daubert v. Merrell Dow Pharmaceuticals (1993) Ø State v. Hayden (1998) Ø People v. Lugashi (1988) Ø US v. Scott-Emuakpor (2000) Ø Williford v. State (2004) 150 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Courts & Digital Evidence Ø Frye v. US (1923) Ø Daubert v. Merrell Dow Pharmaceuticals (1993) Ø State v. Hayden (1998) Ø People v. Lugashi (1988) Ø US v. Scott-Emuakpor (2000) Ø Williford v. State (2004) 150 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
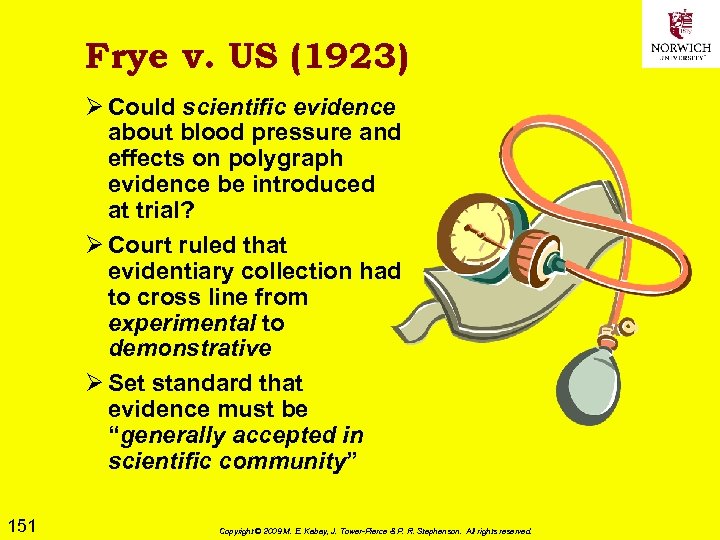 Frye v. US (1923) Ø Could scientific evidence about blood pressure and effects on polygraph evidence be introduced at trial? Ø Court ruled that evidentiary collection had to cross line from experimental to demonstrative Ø Set standard that evidence must be “generally accepted in scientific community” 151 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Frye v. US (1923) Ø Could scientific evidence about blood pressure and effects on polygraph evidence be introduced at trial? Ø Court ruled that evidentiary collection had to cross line from experimental to demonstrative Ø Set standard that evidence must be “generally accepted in scientific community” 151 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
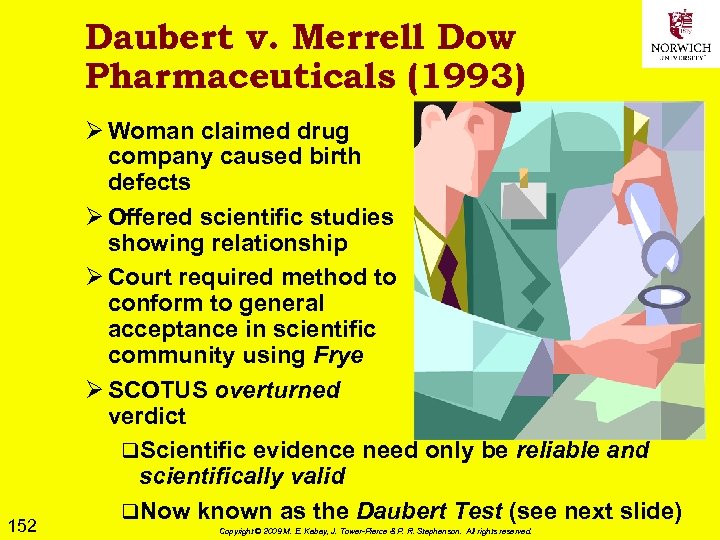 Daubert v. Merrell Dow Pharmaceuticals (1993) 152 Ø Woman claimed drug company caused birth defects Ø Offered scientific studies showing relationship Ø Court required method to conform to general acceptance in scientific community using Frye Ø SCOTUS overturned verdict q. Scientific evidence need only be reliable and scientifically valid q. Now known as the Daubert Test (see next slide) Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Daubert v. Merrell Dow Pharmaceuticals (1993) 152 Ø Woman claimed drug company caused birth defects Ø Offered scientific studies showing relationship Ø Court required method to conform to general acceptance in scientific community using Frye Ø SCOTUS overturned verdict q. Scientific evidence need only be reliable and scientifically valid q. Now known as the Daubert Test (see next slide) Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
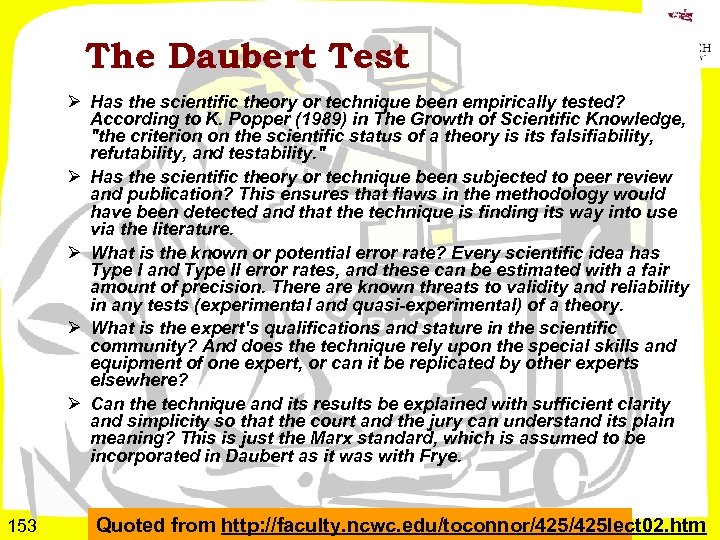 The Daubert Test Ø Has the scientific theory or technique been empirically tested? According to K. Popper (1989) in The Growth of Scientific Knowledge, "the criterion on the scientific status of a theory is its falsifiability, refutability, and testability. " Ø Has the scientific theory or technique been subjected to peer review and publication? This ensures that flaws in the methodology would have been detected and that the technique is finding its way into use via the literature. Ø What is the known or potential error rate? Every scientific idea has Type I and Type II error rates, and these can be estimated with a fair amount of precision. There are known threats to validity and reliability in any tests (experimental and quasi-experimental) of a theory. Ø What is the expert's qualifications and stature in the scientific community? And does the technique rely upon the special skills and equipment of one expert, or can it be replicated by other experts elsewhere? Ø Can the technique and its results be explained with sufficient clarity and simplicity so that the court and the jury can understand its plain meaning? This is just the Marx standard, which is assumed to be incorporated in Daubert as it was with Frye. 153 Quoted from http: //faculty. ncwc. edu/toconnor/425 lect 02. htm Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
The Daubert Test Ø Has the scientific theory or technique been empirically tested? According to K. Popper (1989) in The Growth of Scientific Knowledge, "the criterion on the scientific status of a theory is its falsifiability, refutability, and testability. " Ø Has the scientific theory or technique been subjected to peer review and publication? This ensures that flaws in the methodology would have been detected and that the technique is finding its way into use via the literature. Ø What is the known or potential error rate? Every scientific idea has Type I and Type II error rates, and these can be estimated with a fair amount of precision. There are known threats to validity and reliability in any tests (experimental and quasi-experimental) of a theory. Ø What is the expert's qualifications and stature in the scientific community? And does the technique rely upon the special skills and equipment of one expert, or can it be replicated by other experts elsewhere? Ø Can the technique and its results be explained with sufficient clarity and simplicity so that the court and the jury can understand its plain meaning? This is just the Marx standard, which is assumed to be incorporated in Daubert as it was with Frye. 153 Quoted from http: //faculty. ncwc. edu/toconnor/425 lect 02. htm Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
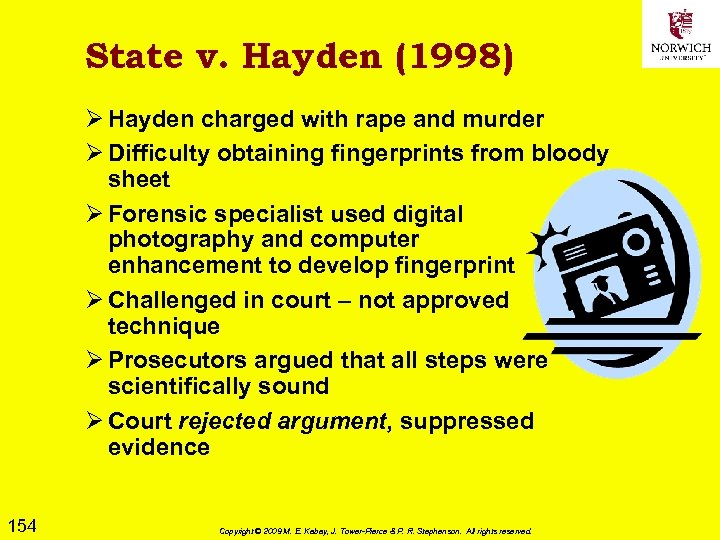 State v. Hayden (1998) Ø Hayden charged with rape and murder Ø Difficulty obtaining fingerprints from bloody sheet Ø Forensic specialist used digital photography and computer enhancement to develop fingerprint Ø Challenged in court – not approved technique Ø Prosecutors argued that all steps were scientifically sound Ø Court rejected argument, suppressed evidence 154 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
State v. Hayden (1998) Ø Hayden charged with rape and murder Ø Difficulty obtaining fingerprints from bloody sheet Ø Forensic specialist used digital photography and computer enhancement to develop fingerprint Ø Challenged in court – not approved technique Ø Prosecutors argued that all steps were scientifically sound Ø Court rejected argument, suppressed evidence 154 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 People v. Lugashi (1988) Ø Case involved theft of creditcard data from backup tapes Ø Forensic investigator could not explain details of how forensic software worked Ø Defense argued for suppression of evidence Ø Court ruled that expert had sufficient experience with software to warrant confidence q. Relying solely on experts who understood all details of all hardware & software would limit testimony & impede justice 155 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
People v. Lugashi (1988) Ø Case involved theft of creditcard data from backup tapes Ø Forensic investigator could not explain details of how forensic software worked Ø Defense argued for suppression of evidence Ø Court ruled that expert had sufficient experience with software to warrant confidence q. Relying solely on experts who understood all details of all hardware & software would limit testimony & impede justice 155 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 US v. Scott-Emuakpor (2000) Ø Nigerian advance-fee fraud Ø Secret Service investigators searched defendant’s computer q. Found evidence of crime Ø Defense argued that SS officials were not computer experts and evidence should be suppressed Ø Court ruled that SS agents were sufficiently expert in use of forensic tools to qualify as witnesses 156 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
US v. Scott-Emuakpor (2000) Ø Nigerian advance-fee fraud Ø Secret Service investigators searched defendant’s computer q. Found evidence of crime Ø Defense argued that SS officials were not computer experts and evidence should be suppressed Ø Court ruled that SS agents were sufficiently expert in use of forensic tools to qualify as witnesses 156 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Williford v. State (2004) Ø Computer repair tech found child porn on computer Ø Police investigator made bit-image of suspect’s HD using En. Case Ø Investigator challenged at trial over lack of computer-science education Ø Prosecution argued that extensive training in use of En. Case + reliability of software itself warranted admission of evidence Ø Court ruled in favor of prosecution (2003) q Officer did qualify as expert for purposes of presenting digital forensic evidence q En. Case satisfied requirements for admission as scientific evidence Ø Appeals Court of Texas supported decision (2004) 157 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Williford v. State (2004) Ø Computer repair tech found child porn on computer Ø Police investigator made bit-image of suspect’s HD using En. Case Ø Investigator challenged at trial over lack of computer-science education Ø Prosecution argued that extensive training in use of En. Case + reliability of software itself warranted admission of evidence Ø Court ruled in favor of prosecution (2003) q Officer did qualify as expert for purposes of presenting digital forensic evidence q En. Case satisfied requirements for admission as scientific evidence Ø Appeals Court of Texas supported decision (2004) 157 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Admission of Digital Evidence at Trial Ø Additional criteria for admissibility q. Authentication q. Chain of custody Ø Authentication based largely on digital signatures or hashes Ø Chain of custody requires minute attention to detail q. Every person in contact w/ evidence is opportunity for challenge q. Must have valid reason for access q. Detailed records of involvement 158 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Admission of Digital Evidence at Trial Ø Additional criteria for admissibility q. Authentication q. Chain of custody Ø Authentication based largely on digital signatures or hashes Ø Chain of custody requires minute attention to detail q. Every person in contact w/ evidence is opportunity for challenge q. Must have valid reason for access q. Detailed records of involvement 158 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Supporting the Chain of Custody Chain-of-custody log should include Moore p 213 critical elements Also “Chain of Custody” Ø Evidence inventory number By R. L. Trench of the Ø Date and Time Intl Assoc Property & Evidence Ø Who Removed the Evidence http: //tinyurl. com/6 febwf Ø Location Removed and Taken To Ø Reason Evidence Being Removed Ø Date of return 159 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Supporting the Chain of Custody Chain-of-custody log should include Moore p 213 critical elements Also “Chain of Custody” Ø Evidence inventory number By R. L. Trench of the Ø Date and Time Intl Assoc Property & Evidence Ø Who Removed the Evidence http: //tinyurl. com/6 febwf Ø Location Removed and Taken To Ø Reason Evidence Being Removed Ø Date of return 159 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
 Now go and study* ______________ *A Roman prankster once sneeringly asked the famous Jewish sage Hillel the Elder (110 B “Can you teach me the whole of the Torah while I stand on one foot? ” Hillel answered, “The whole of the Torah is this: what is hateful to you, do not do to others All the rest is commentary. Now go and study. ” 160 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.
Now go and study* ______________ *A Roman prankster once sneeringly asked the famous Jewish sage Hillel the Elder (110 B “Can you teach me the whole of the Torah while I stand on one foot? ” Hillel answered, “The whole of the Torah is this: what is hateful to you, do not do to others All the rest is commentary. Now go and study. ” 160 Copyright © 2009 M. E. Kabay, J. Tower-Pierce & P. R. Stephenson. All rights reserved.


