da10e3b08bafece172b928b5cd234fae.ppt
- Количество слайдов: 36

Lecture 6 Copyright © 2015 Stuart Jacobs 1
Network Architectures • An architecture serves as the conceptual framework of the system to be developed or purchased. • In the late 1960 s most computer manufacturers developed proprietary architectures( e. g. , IBM’s SNA, DEC’s DECnet, Burrough’s BNA, etc. ) • X. 25 packet networking came into existence in the early 1970 s • In 1975 AT&T Bell Labs developed the Signaling System 7 (SS 7) protocol stack for PSTN signaling between telephone switches. • European Common Channel Signaling System 7 (CCSS 7) in 1980 and internationalized by the ITU when it was called the CCITT. • First standardized work on abstract computing and communications concepts was performed by the International Standards Organization (ISO) in the 1982; more on this soon. • ARPA work on what is know as the Internet stack started in the late 1960 s with IPv 4 ( and TCPv 4 & UDPv 4) finalized in 1980 -1981; more on this soon. Copyright © 2015 Stuart Jacobs 2
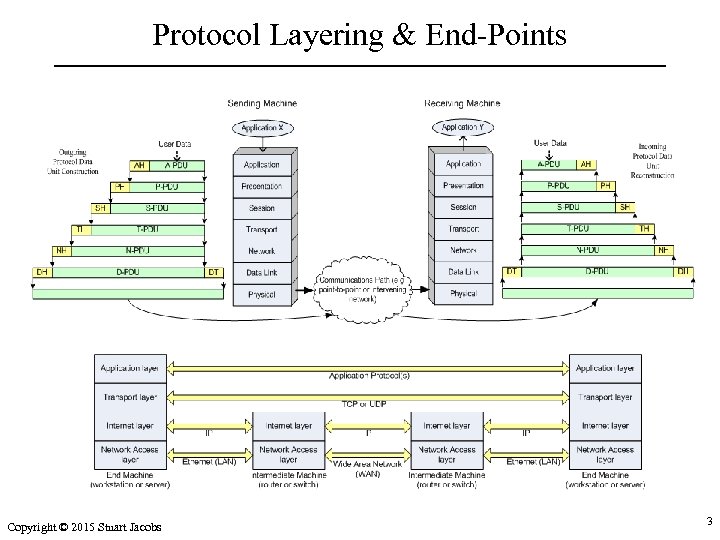
Protocol Layering & End-Points Copyright © 2015 Stuart Jacobs 3
Layer 1 (L 1) - Physical • Broadcast Free Air Radio Frequency Media – Many frequencies and signal encoding schemes (Wi. Fi, Bluetooth, Military, Commercial) • Point–to-Point Free Air Radio Frequency Media – Microwave, Wage Guide, Fixed Wireless (802. 16) • Broadcast Constrained Radio Frequency Media – Coax (i. e. , 10 base 5, 10 base 2, QAM) • Point–to-Point Constrained Radio Frequency Media – T 1/T 3, Coax • Broadcast Free Air Optical Media – IR • Point–to-Point Free Air Optical Media – Laser with many forms of signal encoding schemes • Broadcast Constrained Optical Media – none • Point–to-Point Constrained Optical Media – Single Mode Fiber w/wo DWDM Copyright © 2015 Stuart Jacobs 4
Data Link Layer Complexity • First conceived as just one or two alternative protocols – Ethernet (IEEE 802. 3) over coax or twisted pair (TP), IEEE 802. 5 over coax, Fiber Distributed Data Interface (FDDI) over coax, proprietary protocols over Serial lines • Evolved into multiple protocols layered upon each other – IP over Point-to-Point Protocol (PPP) over Serial – IP over PPP over Ethernet (PPPo. E) – IP over Ethernet over Frame Relay or ATM over Serial – IP over Ethernet over ATM over SONET over Fiber – IP over 1(10)-Gig. E over Generalized Framing Protocol (GFP) over (WDM) Fiber – IP over Multi Protocol Label Switching (MPLS) over 10/100 base. T (TP) – IP over MPLS over 1(10)-Gig. E over (WDM) Fiber – SONET over GFP over (WDM) Fiber – IP over 10/100/1, 000/10, 000 Ethernet over Generalized Multi Protocol Label Switching (G-MPLS) over GFP over (WDM) Fiber Copyright © 2015 Stuart Jacobs 5
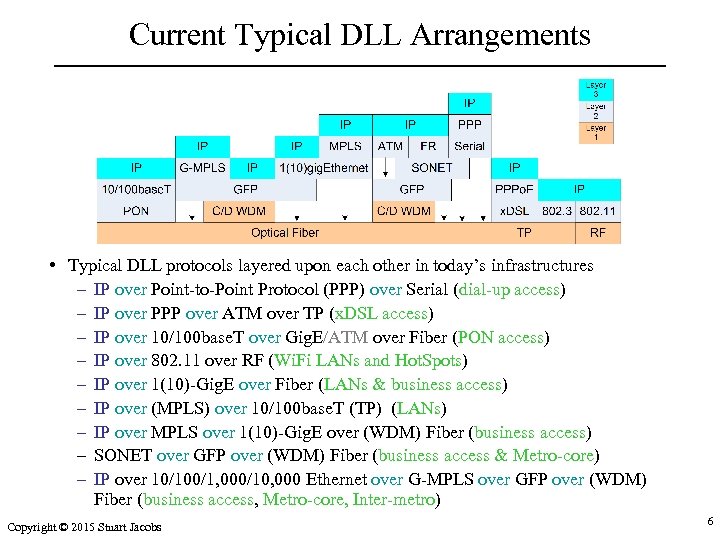
Current Typical DLL Arrangements • Typical DLL protocols layered upon each other in today’s infrastructures – IP over Point-to-Point Protocol (PPP) over Serial (dial-up access) – IP over PPP over ATM over TP (x. DSL access) – IP over 10/100 base. T over Gig. E/ATM over Fiber (PON access) – IP over 802. 11 over RF (Wi. Fi LANs and Hot. Spots) – IP over 1(10)-Gig. E over Fiber (LANs & business access) – IP over (MPLS) over 10/100 base. T (TP) (LANs) – IP over MPLS over 1(10)-Gig. E over (WDM) Fiber (business access) – SONET over GFP over (WDM) Fiber (business access & Metro-core) – IP over 10/100/1, 000/10, 000 Ethernet over G-MPLS over GFP over (WDM) Fiber (business access, Metro-core, Inter-metro) Copyright © 2015 Stuart Jacobs 6

Local Area Networks • Most wired LANs historically were broadcast type networks, which means that they distribute data to all the users of the network via shared physical media. • This approach of interconnecting multiple computers is also referred to as multi-drop. • In the last five to seven years this broadcast approach has been replaced with point-to-point switched technology. • This approach the same layer 2 protocol IEEE 802. 3 (CSMA-CD) even though collision detection not necessary. • Can now be logically divided into multiple virtual LANs on the same physical media using the IEEE 802. 1 q protocol. • Monitoring, or eves-dropping/sniffing: – simple when hubs used – Requires access to a “spanning port” when switches used. Copyright © 2015 Stuart Jacobs 7

Wireless LANs & Personal LANs • Did not exist until FCC opened the ISM bands – 902– 928 MHz (center frequency 915 MHz) – 2. 400– 2. 500 GHz (center frequency 2. 450 GHz) – 5. 725– 5. 875 GHz (center frequency 5. 800 GHz) • • • in the mid 1990 s for data communications purposes. Initial products were proprietary (i. e. , ATT’s Wave. LAN). IEEE 802. 11 link layer protocol published in 1997 with two versions 802. 11 a (54 Mbps), 802. 11 b (11 Mbps); 802. 11 g (54 Mbps) added. Wireless signals are broadcasted everywhere within the range of an access point (up to 100 M) with attenuation from walls/windows, etc. Wireless eves-dropping/sniffing equipment for available, done without service disruption, and without detection. Strong encryption necessary for: – confidentiality – control LAN access (authorization). • Security issues and mechanisms discussed later in course. Copyright © 2015 Stuart Jacobs 8
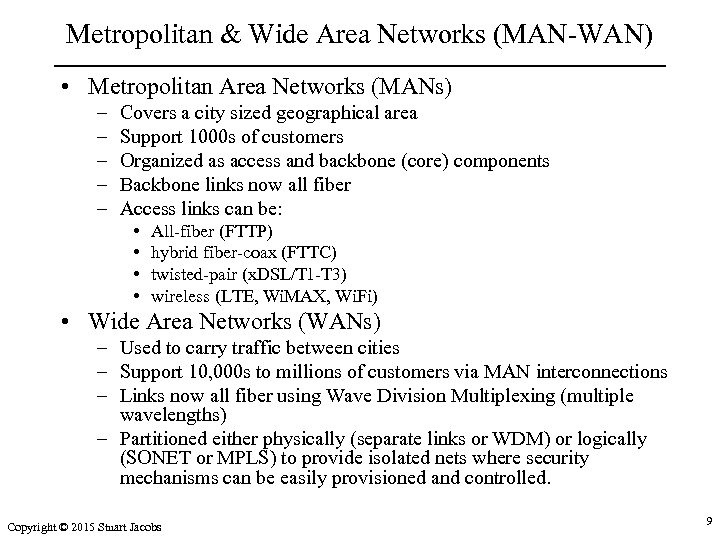
Metropolitan & Wide Area Networks (MAN-WAN) • Metropolitan Area Networks (MANs) – – – Covers a city sized geographical area Support 1000 s of customers Organized as access and backbone (core) components Backbone links now all fiber Access links can be: • • All-fiber (FTTP) hybrid fiber-coax (FTTC) twisted-pair (x. DSL/T 1 -T 3) wireless (LTE, Wi. MAX, Wi. Fi) • Wide Area Networks (WANs) – Used to carry traffic between cities – Support 10, 000 s to millions of customers via MAN interconnections – Links now all fiber using Wave Division Multiplexing (multiple wavelengths) – Partitioned either physically (separate links or WDM) or logically (SONET or MPLS) to provide isolated nets where security mechanisms can be easily provisioned and controlled. Copyright © 2015 Stuart Jacobs 9
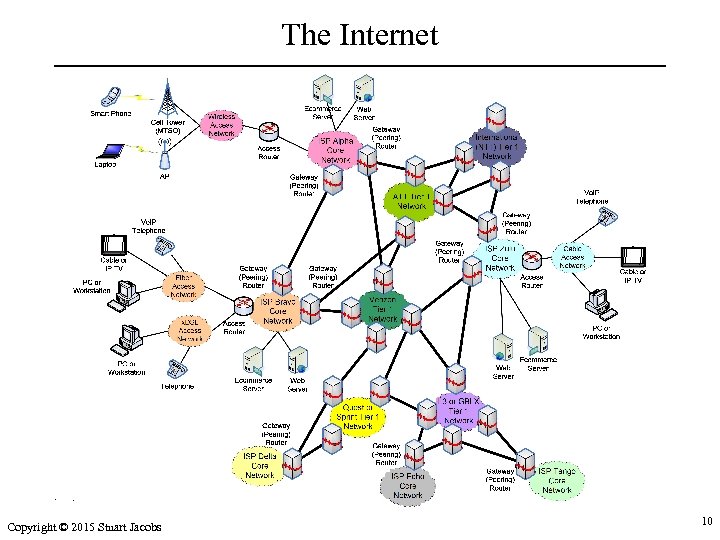
The Internet Copyright © 2015 Stuart Jacobs 10
Address Resolution Protocol (ARP) • Method for finding a system's hardware address when only its IPv 4 address is known • Defined in RFC 826 • Not an IP or Ethernet only protocol; primarily used to translate IP addresses to Ethernet MAC addresses • Also used for IP over Token Ring, FDDI, or IEEE 802. 11, and IP over ATM. • For IPv 6 ARP replaced by Neighbor Discovery Protocol (NDP). • Inverse ARP (In. ARP) used for obtaining IP addresses of other systems from Layer 2 addresses – Primarily used in Frame Relay and ATM networks – Actually implemented as an extension to ARP, only the operation code and the filled fields differ. • Reverse ARP (RARP), like In. ARP, also translates Layer 2 addresses to IP – Used to obtain the Layer 3 address of the requesting station itself – Has since been abandoned in favor of DHCP. Copyright © 2015 Stuart Jacobs 11
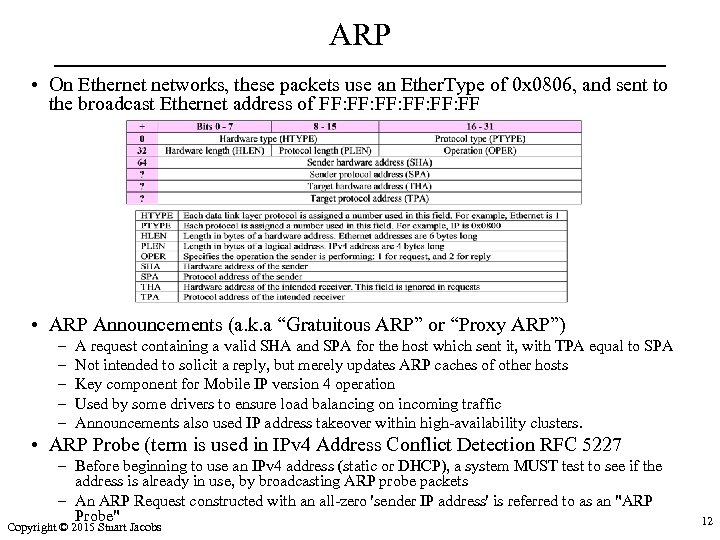
ARP • On Ethernet networks, these packets use an Ether. Type of 0 x 0806, and sent to the broadcast Ethernet address of FF: FF: FF: FF • ARP Announcements (a. k. a “Gratuitous ARP” or “Proxy ARP”) – – – A request containing a valid SHA and SPA for the host which sent it, with TPA equal to SPA Not intended to solicit a reply, but merely updates ARP caches of other hosts Key component for Mobile IP version 4 operation Used by some drivers to ensure load balancing on incoming traffic Announcements also used IP address takeover within high-availability clusters. • ARP Probe (term is used in IPv 4 Address Conflict Detection RFC 5227 – Before beginning to use an IPv 4 address (static or DHCP), a system MUST test to see if the address is already in use, by broadcasting ARP probe packets – An ARP Request constructed with an all-zero 'sender IP address' is referred to as an "ARP Probe" Copyright © 2015 Stuart Jacobs 12
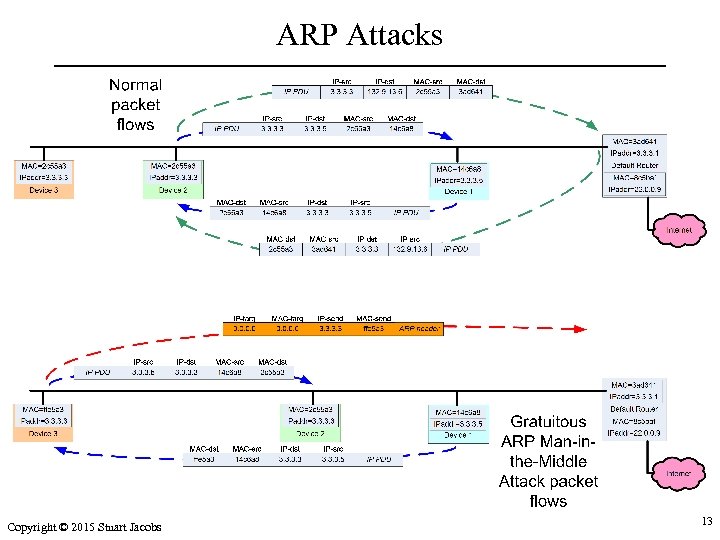
ARP Attacks Copyright © 2015 Stuart Jacobs 13
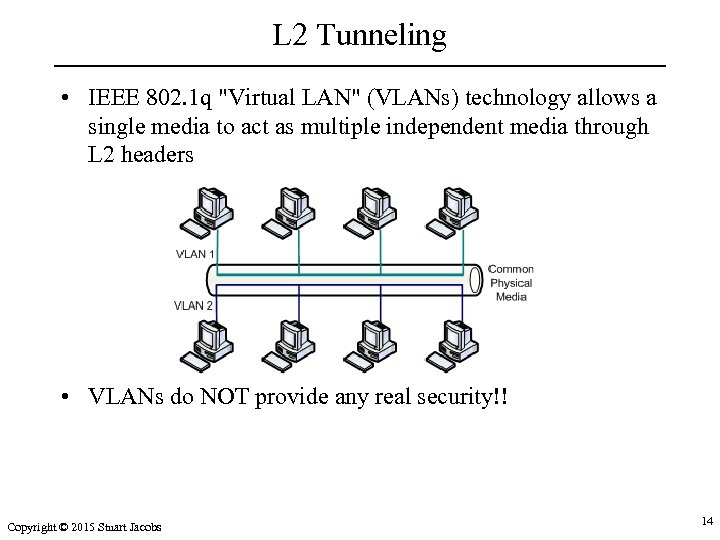
L 2 Tunneling • IEEE 802. 1 q "Virtual LAN" (VLANs) technology allows a single media to act as multiple independent media through L 2 headers • VLANs do NOT provide any real security!! Copyright © 2015 Stuart Jacobs 14
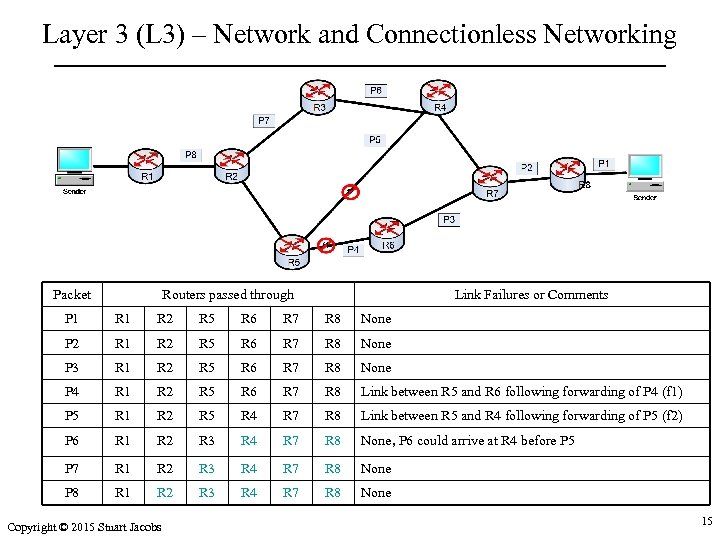
Layer 3 (L 3) – Network and Connectionless Networking Packet Routers passed through Link Failures or Comments P 1 R 2 R 5 R 6 R 7 R 8 None P 2 R 1 R 2 R 5 R 6 R 7 R 8 None P 3 R 1 R 2 R 5 R 6 R 7 R 8 None P 4 R 1 R 2 R 5 R 6 R 7 R 8 Link between R 5 and R 6 following forwarding of P 4 (f 1) P 5 R 1 R 2 R 5 R 4 R 7 R 8 Link between R 5 and R 4 following forwarding of P 5 (f 2) P 6 R 1 R 2 R 3 R 4 R 7 R 8 None, P 6 could arrive at R 4 before P 5 P 7 R 1 R 2 R 3 R 4 R 7 R 8 None P 8 R 1 R 2 R 3 R 4 R 7 R 8 None Copyright © 2015 Stuart Jacobs 15
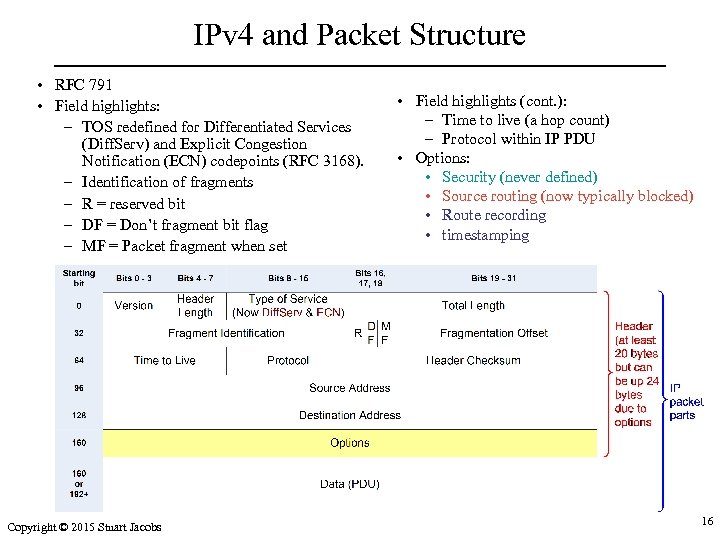
IPv 4 and Packet Structure • RFC 791 • Field highlights: – TOS redefined for Differentiated Services (Diff. Serv) and Explicit Congestion Notification (ECN) codepoints (RFC 3168). – Identification of fragments – R = reserved bit – DF = Don’t fragment bit flag – MF = Packet fragment when set Copyright © 2015 Stuart Jacobs • Field highlights (cont. ): – Time to live (a hop count) – Protocol within IP PDU • Options: • Security (never defined) • Source routing (now typically blocked) • Route recording • timestamping 16
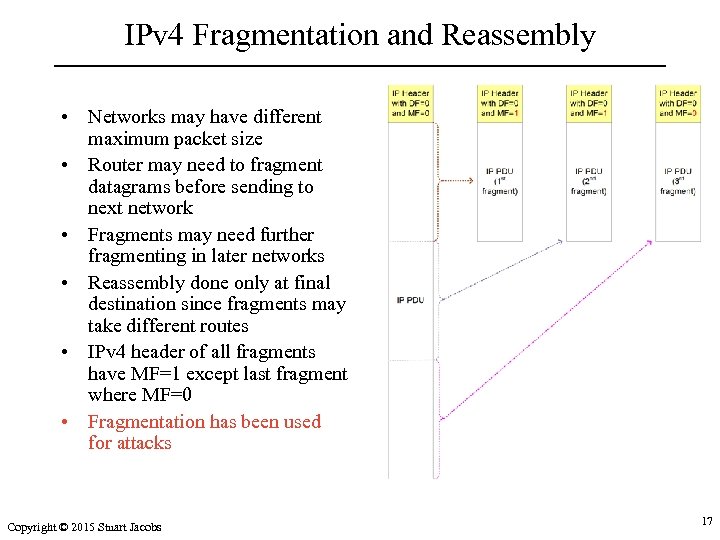
IPv 4 Fragmentation and Reassembly • Networks may have different maximum packet size • Router may need to fragment datagrams before sending to next network • Fragments may need further fragmenting in later networks • Reassembly done only at final destination since fragments may take different routes • IPv 4 header of all fragments have MF=1 except last fragment where MF=0 • Fragmentation has been used for attacks Copyright © 2015 Stuart Jacobs 17
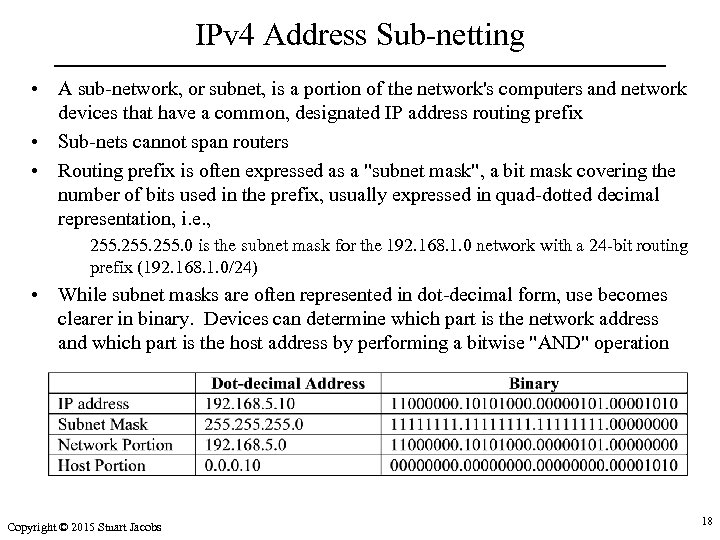
IPv 4 Address Sub-netting • A sub-network, or subnet, is a portion of the network's computers and network devices that have a common, designated IP address routing prefix • Sub-nets cannot span routers • Routing prefix is often expressed as a "subnet mask", a bit mask covering the number of bits used in the prefix, usually expressed in quad-dotted decimal representation, i. e. , 255. 0 is the subnet mask for the 192. 168. 1. 0 network with a 24 -bit routing prefix (192. 168. 1. 0/24) • While subnet masks are often represented in dot-decimal form, use becomes clearer in binary. Devices can determine which part is the network address and which part is the host address by performing a bitwise "AND" operation Copyright © 2015 Stuart Jacobs 18
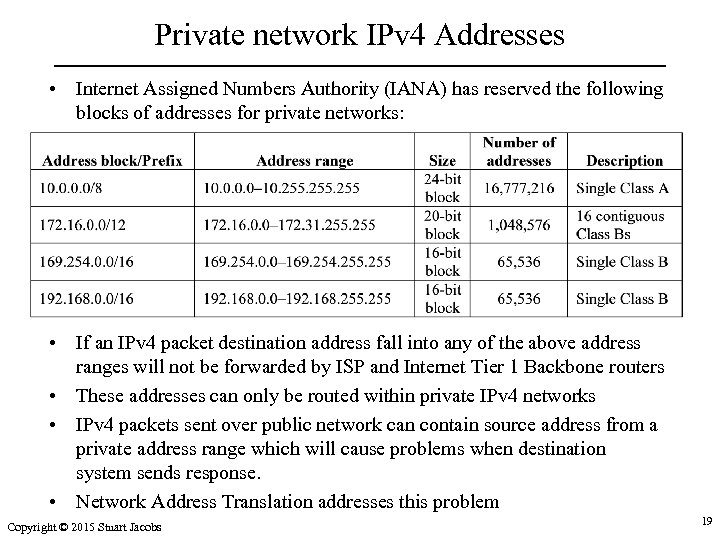
Private network IPv 4 Addresses • Internet Assigned Numbers Authority (IANA) has reserved the following blocks of addresses for private networks: • If an IPv 4 packet destination address fall into any of the above address ranges will not be forwarded by ISP and Internet Tier 1 Backbone routers • These addresses can only be routed within private IPv 4 networks • IPv 4 packets sent over public network can contain source address from a private address range which will cause problems when destination system sends response. • Network Address Translation addresses this problem Copyright © 2015 Stuart Jacobs 19
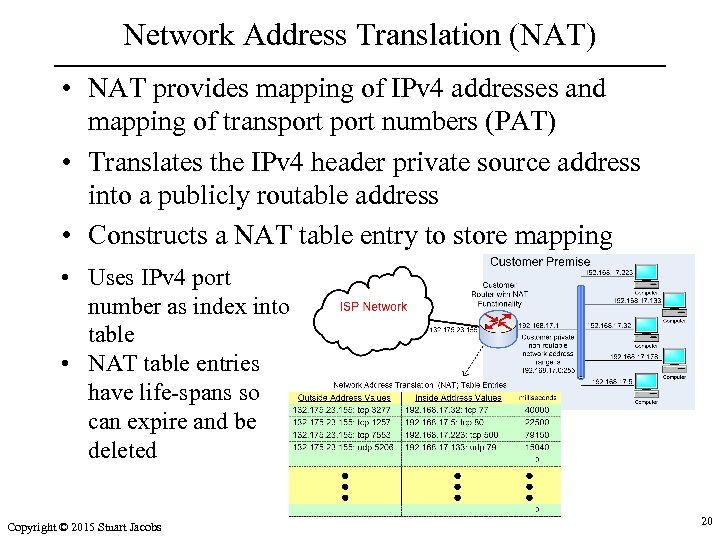
Network Address Translation (NAT) • NAT provides mapping of IPv 4 addresses and mapping of transport numbers (PAT) • Translates the IPv 4 header private source address into a publicly routable address • Constructs a NAT table entry to store mapping • Uses IPv 4 port number as index into table • NAT table entries have life-spans so can expire and be deleted Copyright © 2015 Stuart Jacobs 20
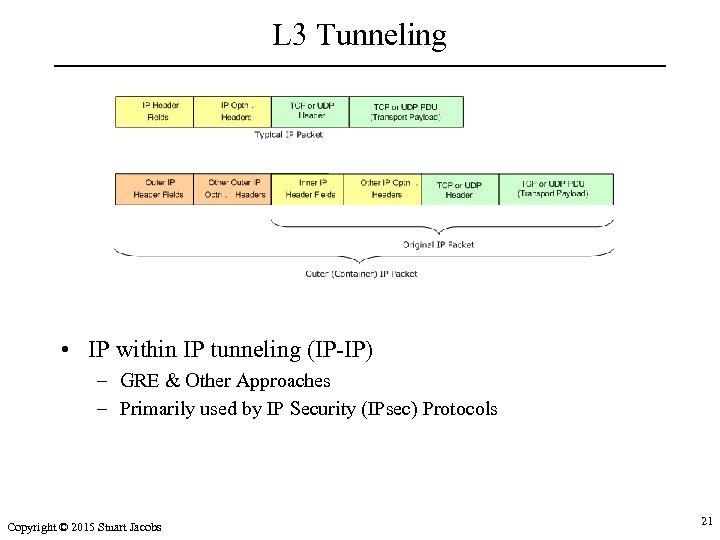
L 3 Tunneling • IP within IP tunneling (IP-IP) – GRE & Other Approaches – Primarily used by IP Security (IPsec) Protocols Copyright © 2015 Stuart Jacobs 21

Internet Control Message Protocol (ICMP) • Used by systems to send error messages (i. e. , a service is not available or a host or router could not be reached and is an integral part of IP and is unreliable • Not used to send and receive data between end systems, exceptions being ping and traceroute • ICMP messages are typically generated in response to errors in IP packets or for diagnostic or routing purposes • Versions are ICMPv 4, RFC 791 (1981), and ICMPv 6, RFC 4443 (2006) • Messages constructed at the IP layer, IP places ICMP message in new IP packet and sends to original sending host • I. e. , every system (e. g. , routers) forwarding an IP packet decrements the IP header TTL field by one; if TTL reaches 0, an ICMP Time to live exceeded in transit message is sent to the source of the packet. • Traceroute implemented using UDP datagrams – With specially set TTL header field – Looking for ICMP Time to live exceeded in transit and "Destination unreachable" messages generated in response • Ping utility uses ICMP "Echo request" and "Echo reply" messages Copyright © 2015 Stuart Jacobs 22
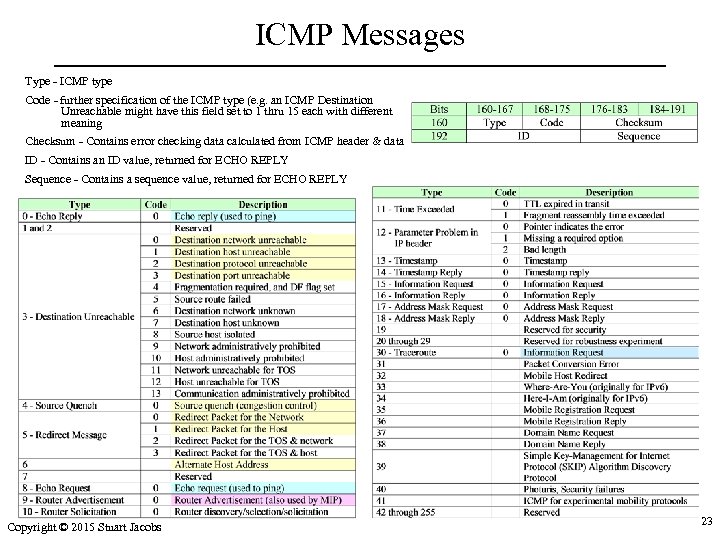
ICMP Messages Type - ICMP type Code - further specification of the ICMP type (e. g. an ICMP Destination Unreachable might have this field set to 1 thru 15 each with different meaning Checksum - Contains error checking data calculated from ICMP header & data ID - Contains an ID value, returned for ECHO REPLY Sequence - Contains a sequence value, returned for ECHO REPLY Copyright © 2015 Stuart Jacobs 23
IPv 6 • Increases IP address from 32 bits to 128 (RFC 4291) • Fixed size 40 -octet header, followed by optional extension headers • IPv 4 address space contains roughly 4 billion addresses, IPv 6 supports up to 3. 4× 1038 unique addresses • IPv 6 addresses typically composed of two logical parts: – a 64 -bit (sub-)network prefix, and – a 64 -bit host part, which is either automatically generated from the interface's MAC address • IPv 6 addresses are normally written as eight groups of four hexadecimal digits, where each group is separated by a colon (: ), i. e. , 2011: 0 ab 9: 85 a 3: 0000: 1 c 6 e: 0370: 3461 – Any leading zeros in a group may be omitted; thus, the example becomes 2011: ab 9: 85 a 3: 0: 0: 1 c 6 e: 370: 3461 – One or any number of consecutive groups of 0 value may be replaced with two colons (: : ): 2011: ab 9: 85 a 3: : 1 c 6 e: 370: 3461 • Longer header but fewer fields (8 vs 12), so routers should have less processing Copyright © 2015 Stuart Jacobs 24
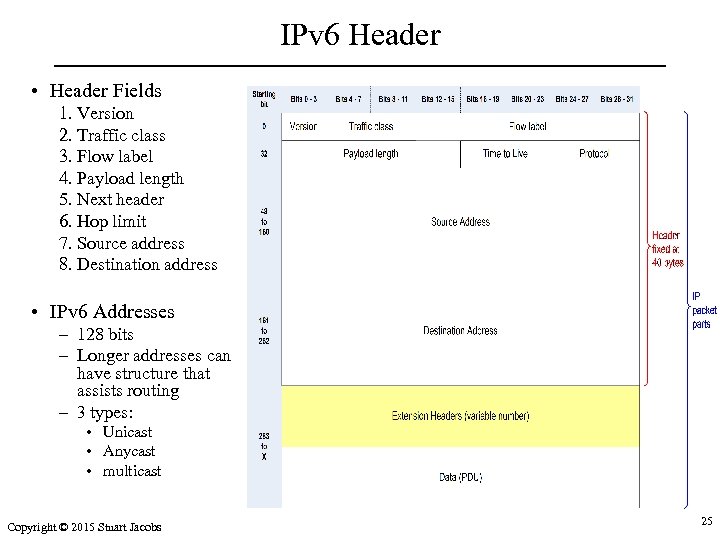
IPv 6 Header • Header Fields 1. Version 2. Traffic class 3. Flow label 4. Payload length 5. Next header 6. Hop limit 7. Source address 8. Destination address • IPv 6 Addresses – 128 bits – Longer addresses can have structure that assists routing – 3 types: • Unicast • Anycast • multicast Copyright © 2015 Stuart Jacobs 25
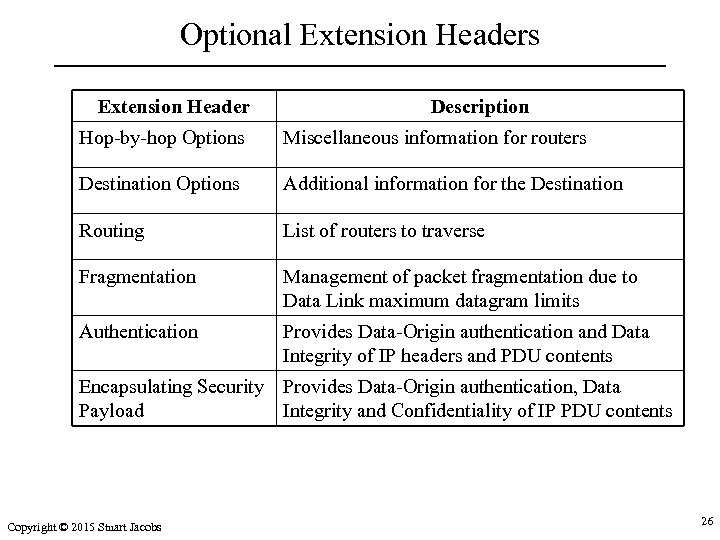
Optional Extension Headers Extension Header Description Hop-by-hop Options Miscellaneous information for routers Destination Options Additional information for the Destination Routing List of routers to traverse Fragmentation Management of packet fragmentation due to Data Link maximum datagram limits Authentication Provides Data-Origin authentication and Data Integrity of IP headers and PDU contents Encapsulating Security Provides Data-Origin authentication, Data Payload Integrity and Confidentiality of IP PDU contents Copyright © 2015 Stuart Jacobs 26
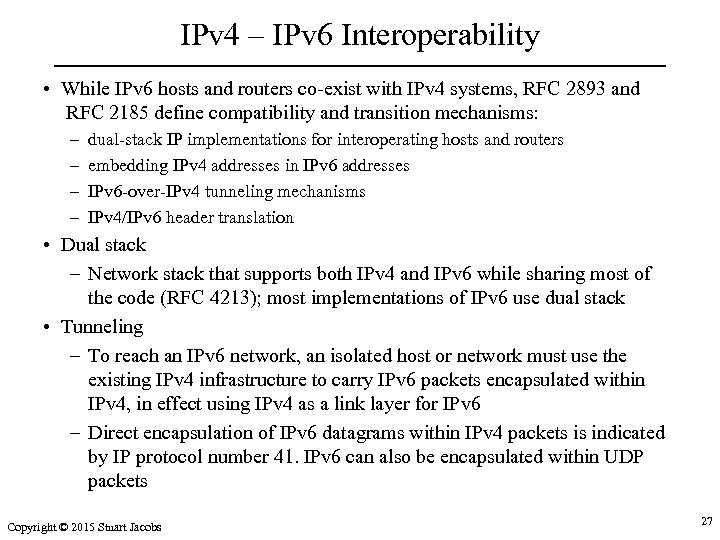
IPv 4 – IPv 6 Interoperability • While IPv 6 hosts and routers co-exist with IPv 4 systems, RFC 2893 and RFC 2185 define compatibility and transition mechanisms: – – dual-stack IP implementations for interoperating hosts and routers embedding IPv 4 addresses in IPv 6 addresses IPv 6 -over-IPv 4 tunneling mechanisms IPv 4/IPv 6 header translation • Dual stack – Network stack that supports both IPv 4 and IPv 6 while sharing most of the code (RFC 4213); most implementations of IPv 6 use dual stack • Tunneling – To reach an IPv 6 network, an isolated host or network must use the existing IPv 4 infrastructure to carry IPv 6 packets encapsulated within IPv 4, in effect using IPv 4 as a link layer for IPv 6 – Direct encapsulation of IPv 6 datagrams within IPv 4 packets is indicated by IP protocol number 41. IPv 6 can also be encapsulated within UDP packets Copyright © 2015 Stuart Jacobs 27
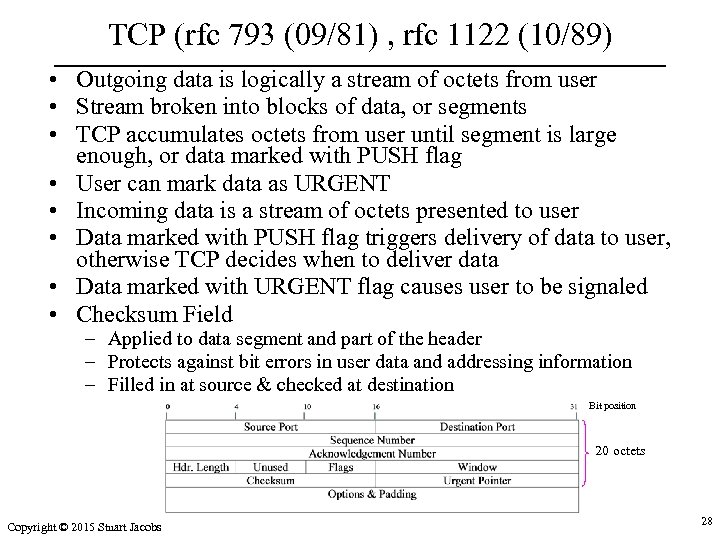
TCP (rfc 793 (09/81) , rfc 1122 (10/89) • Outgoing data is logically a stream of octets from user • Stream broken into blocks of data, or segments • TCP accumulates octets from user until segment is large enough, or data marked with PUSH flag • User can mark data as URGENT • Incoming data is a stream of octets presented to user • Data marked with PUSH flag triggers delivery of data to user, otherwise TCP decides when to deliver data • Data marked with URGENT flag causes user to be signaled • Checksum Field – Applied to data segment and part of the header – Protects against bit errors in user data and addressing information – Filled in at source & checked at destination Bit position 20 octets Copyright © 2015 Stuart Jacobs 28
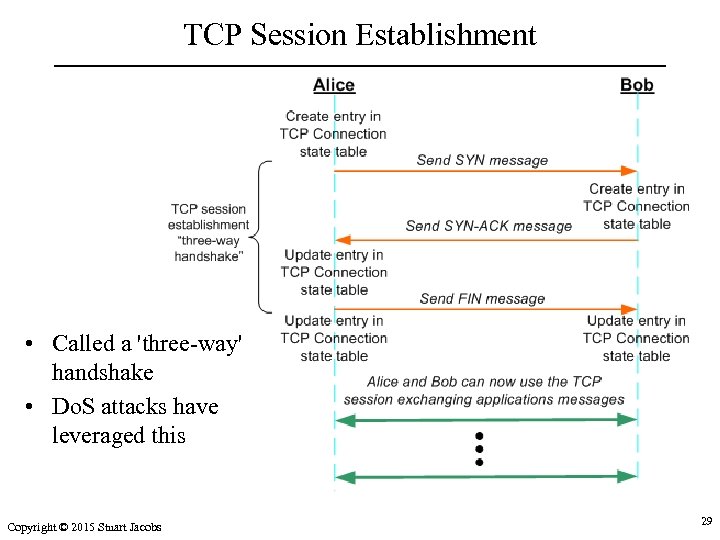
TCP Session Establishment • Called a 'three-way' handshake • Do. S attacks have leveraged this Copyright © 2015 Stuart Jacobs 29
UDP (rfc 768) • • • Connectionless, unreliable Less overhead Simply adds port addressing to IP Checksum is optional Appropriate Uses of UDP – – Inward data collection Outward data dissemination Request-response Real-time applications Bit position 8 octets • UDP includes and echo request/reply capability that has been used for attacks Copyright © 2015 Stuart Jacobs 30
SCTP (rfc 2960) • Designed to transport PSTN signaling messages over IP networks, but is capable of broader applications • Offers the following services – acknowledged error-free non-duplicated transfer of user data, – data fragmentation to conform to discovered path MTU size, – sequenced delivery of user messages within multiple streams, with an option for order-of-arrival delivery of individual user messages, – optional bundling of multiple user messages into a single SCTP packet, and – network-level fault tolerance through supporting of multi-homing at either or both ends of an association. • Includes appropriate congestion avoidance behavior and resistance to flooding and masquerade attacks • Mandates use of IP Security (IPsec) Copyright © 2015 Stuart Jacobs 31
Initial Internet User Application Protocols • User application protocols developed in the early 1980 s were not designed with any meaningful security capabilities – – File Transfer Protocol (FTP) Trivial File Transfer Protocol (TFTP) Telnet protocol Remote Procedure Protocol (RCP) • All rely on passwords passed over networks as clear-text subject to eavesdropping and identity spoofing • Should not be used without additional security mechanisms such as TLS, SSH or IPsec. Copyright © 2015 Stuart Jacobs 32
Other Application Layer Protocols • X Window System (commonly X or X 11) – Designed to be used over networks – Does not include any security mechanisms beyond reliance on clear-text exchanged passwords • Resource Reservation Protocol (RSVP) – Informational RFC – Number of mechanisms based on shared secret keys and digest algorithms • Border Gateway Protocol version 4 (BGPv 4) – Relies on optional keyed MD 5 security option added to TCP – Does not address how shared secret keys are managed • Network Time Protocol (NTP) and Simple Network Time Protocol (SNTP) – Relies on optional keyed MD 5 security option • Domain Name System (DNS) • Not designed with security in mind, and issues arise: including: – DNS cache poisoning Targeting DNS servers – DNS server compromise by some malware (a virus or worm) or a disgruntled employee – Domain Name spoofing by registering domain names that are similar looking to other domain names. One example could be, "paypa 1. com“ (using the digit ” 1”) and "paypal. com" (using the letter ”l”) Copyright © 2015 Stuart Jacobs 33
Hyper. Text Transfer Protocol (HTTP) • Two approaches for authenticating HTTP requests have been developed: – HTTP Basic Authentication – HTTP Digest Access Authentication. • HTTP Basic Authentication uses a Base 64 algorithm that maps three octets into four octets, i. e. , given the user name Moses and the password exodus, the string Moses: exdus is Base 64 encoded, resulting in TW 92 ZXM 6 ZXhkd. XM that is easily decoded – Uses a shared secret (the user password) – Assumes connection between the client and server is secure (not a valid assumption) – Provides no protection for information passed between the server and the UA • HTTP Digest Authentication replaces Basic Authentication – – Uses the MD 5 digest algorithm with nonce values to prevent cryptanalysis Client nonce defends against chosen plaintext attacks, Server nonce may contain timestamps to prevent replay attacks Uses a shared secret (the user password) without addressing how this secret is shared – Vvulnerable to a Man-in-the-middle attack as the attacker could tell UAs to use Basic instead of Digest access authentication. – Provides no protection for information between the server and the UA. Copyright © 2015 Stuart Jacobs 34

Simple Network Management Protocol • Security issues include: – Versions 1 and 2 c use the clear-text ‘community string’ for authentication and are subject to packet sniffing – Versions 2 and 3 are subject to brute force and dictionary attacks and neither address how shared secret key management should occur – SNMP's configuration SET capabilities can be misconfigured and used to cause severe damage – SNMPv 1 is number 1 on the list of the SANS Institute's Common Default Configuration Issues due to default SNMP community strings set to ‘public’ and ‘private’ • RMON is simply SNMP Copyright © 2015 Stuart Jacobs 35

Questions? ? ? Copyright © 2015 Stuart Jacobs 36
da10e3b08bafece172b928b5cd234fae.ppt