3827150733d6784388c836d5221253c1.ppt
- Количество слайдов: 62
 Lecture 4. Ethics and the Value of Data David R. Merrell 90 -786 Intermediate Empirical Methods for Public Policy and Management
Lecture 4. Ethics and the Value of Data David R. Merrell 90 -786 Intermediate Empirical Methods for Public Policy and Management
 Lecture 4. Agenda n n n Review of Lecture 3 Social Value of Data Privacy Issues Confidentiality Applications in Health Care
Lecture 4. Agenda n n n Review of Lecture 3 Social Value of Data Privacy Issues Confidentiality Applications in Health Care
 Review of Lecture 3 n n Cross-Classification Scatterplot
Review of Lecture 3 n n Cross-Classification Scatterplot
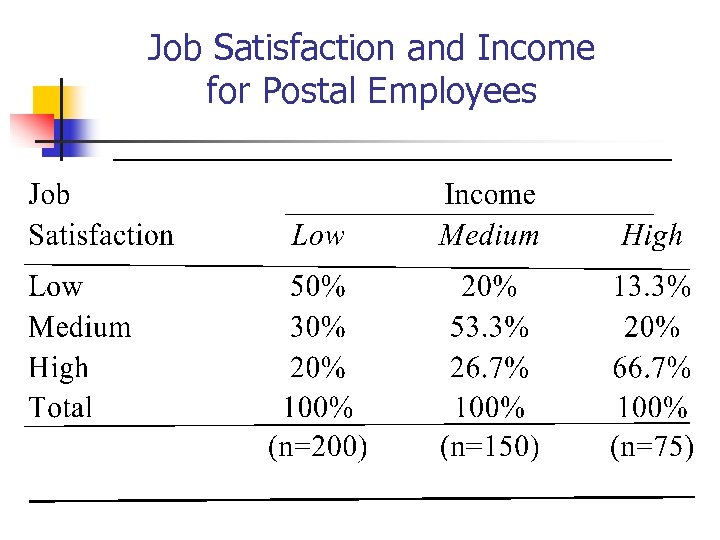 Job Satisfaction and Income for Postal Employees
Job Satisfaction and Income for Postal Employees
 Stock Mutual Funds--Chatterjee et al In Excel, OPEN funds. dat in r: /academic/90 -786/chatterjee
Stock Mutual Funds--Chatterjee et al In Excel, OPEN funds. dat in r: /academic/90 -786/chatterjee
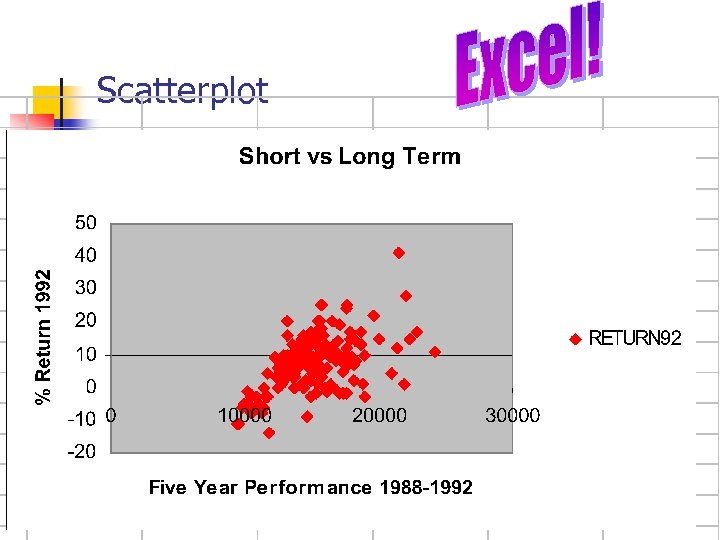 Scatterplot
Scatterplot
 Scatterplot
Scatterplot
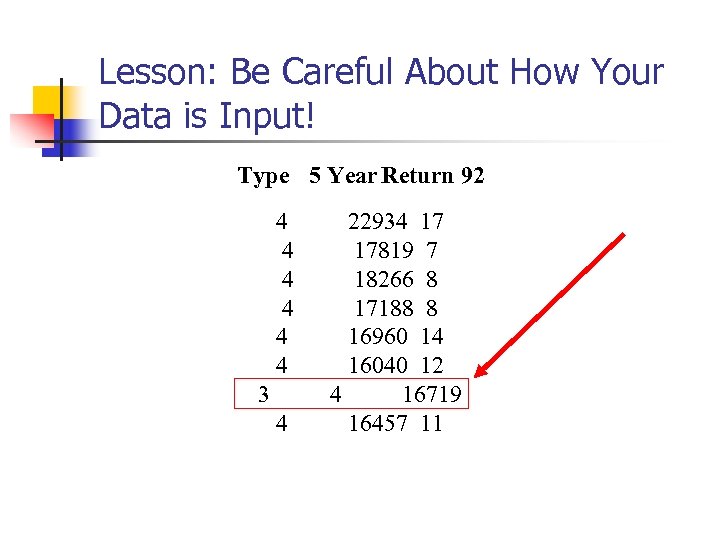 Lesson: Be Careful About How Your Data is Input! Type 5 Year Return 92 4 4 4 3 4 22934 17 17819 7 18266 8 17188 8 16960 14 16040 12 4 16719 16457 11
Lesson: Be Careful About How Your Data is Input! Type 5 Year Return 92 4 4 4 3 4 22934 17 17819 7 18266 8 17188 8 16960 14 16040 12 4 16719 16457 11
 Lecture 4: Ethics and the Value of Data n n Social Value of Data Privacy Issues Confidentiality Applications in Health Care
Lecture 4: Ethics and the Value of Data n n Social Value of Data Privacy Issues Confidentiality Applications in Health Care
 "Every sort of shouting is a transitory thing after which the grim silence of facts remains. " --Joseph Conrad
"Every sort of shouting is a transitory thing after which the grim silence of facts remains. " --Joseph Conrad

 Social Value of Data: Why Do We Need Access to Data? n n Human Rights Statistics Making Defense Decisions Individuals with Disabilities Medical Experimentation
Social Value of Data: Why Do We Need Access to Data? n n Human Rights Statistics Making Defense Decisions Individuals with Disabilities Medical Experimentation
 Human Rights Statistics n n n Lynchings in the United States “No-name” burials in Argentina “I see one-third of a nation …” Persons with no health insurance Childhood immunizations Monitoring international human rights treaties
Human Rights Statistics n n n Lynchings in the United States “No-name” burials in Argentina “I see one-third of a nation …” Persons with no health insurance Childhood immunizations Monitoring international human rights treaties
 More. . . n n n Housing market and employment audits Landmines Rape in Bosnia and Herzegovina
More. . . n n n Housing market and employment audits Landmines Rape in Bosnia and Herzegovina
 Uses of Human Rights Statistics n n Advocacy purposes Monitoring and enforcement
Uses of Human Rights Statistics n n Advocacy purposes Monitoring and enforcement
 Types and Sources of Human Rights Statistics n n Statistical indicators disaggregated by gender, race, religion, age, etc. Amnesty International
Types and Sources of Human Rights Statistics n n Statistical indicators disaggregated by gender, race, religion, age, etc. Amnesty International
 Background on Human Rights Statistics n Human Rights in the World Community: Issues and Action, edited by Claude and Weston, 1989 n Human Rights and Statistics: Getting the Record Straight, by Jabine and Claude, 1992 n Data Analysis for Monitoring Human Rights, by Spirer and Spirer, 1994
Background on Human Rights Statistics n Human Rights in the World Community: Issues and Action, edited by Claude and Weston, 1989 n Human Rights and Statistics: Getting the Record Straight, by Jabine and Claude, 1992 n Data Analysis for Monitoring Human Rights, by Spirer and Spirer, 1994
 Making Defense Decisions n n n World War II, Operations Research-Estimating German war production All-volunteer army--What should the compensation level be? 1978 debacle Military intelligence Resource allocation Cost estimation
Making Defense Decisions n n n World War II, Operations Research-Estimating German war production All-volunteer army--What should the compensation level be? 1978 debacle Military intelligence Resource allocation Cost estimation
 Individuals with Disabilities n n n 1990 Americans with Disabilities Act 1970 Decennial Census 1990 Survey of Income and Program Participation National Health Interview Survey Canadian National Database on Disability
Individuals with Disabilities n n n 1990 Americans with Disabilities Act 1970 Decennial Census 1990 Survey of Income and Program Participation National Health Interview Survey Canadian National Database on Disability
 Experimentation n n n Renewing driver’s licenses IRS collection of delinquent accounts Licensing new drugs Salk polio vaccine trial Scandinavian highway experiments Minneapolis domestic violence experiment
Experimentation n n n Renewing driver’s licenses IRS collection of delinquent accounts Licensing new drugs Salk polio vaccine trial Scandinavian highway experiments Minneapolis domestic violence experiment
 The Flip Side. . . n n Privacy Confidentiality
The Flip Side. . . n n Privacy Confidentiality
 Privacy Intrusive surveillance l Cryptography l Firewalls l
Privacy Intrusive surveillance l Cryptography l Firewalls l
 Intrusive Surveillance n n “Surveys” Electronic Data Capture
Intrusive Surveillance n n “Surveys” Electronic Data Capture
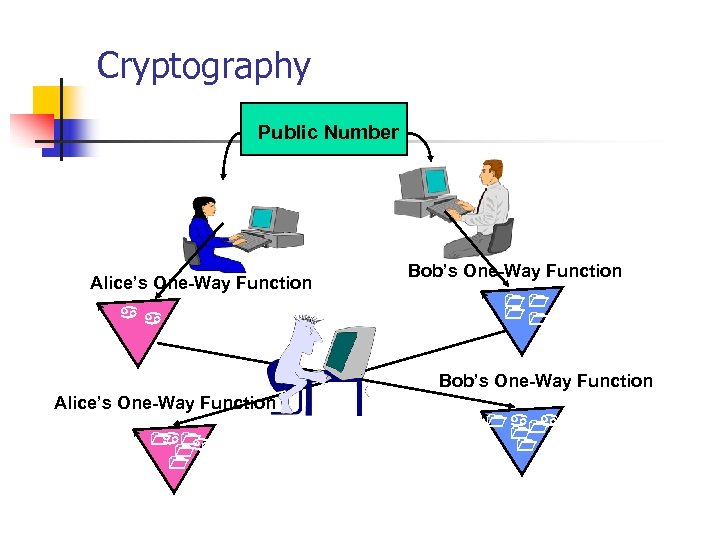 Cryptography Public Number Alice’s One-Way Function Bob’s One-Way Function Alice’s One-Way Function
Cryptography Public Number Alice’s One-Way Function Bob’s One-Way Function Alice’s One-Way Function
 A Firewall Authentication Server Router Application level gateway Local Network Internet Fire Wall ftp e-mail telnet Wall Packet Filter
A Firewall Authentication Server Router Application level gateway Local Network Internet Fire Wall ftp e-mail telnet Wall Packet Filter
 Emerging Privacy & Confidentiality Issues Substantive Fields l Public Sensitivity l Technology l
Emerging Privacy & Confidentiality Issues Substantive Fields l Public Sensitivity l Technology l
 Emerging Fields Global Information Infrastructure n. Health care information systems n. Immigration control n
Emerging Fields Global Information Infrastructure n. Health care information systems n. Immigration control n
 Emerging Sensitivity Surveys show privacy concerns; also lack of “community spirit”? n. More participants in information exchange n“Reduction to a number” in a surveillance society n
Emerging Sensitivity Surveys show privacy concerns; also lack of “community spirit”? n. More participants in information exchange n“Reduction to a number” in a surveillance society n
 Trends in Concerns About Privacy Harris surveys asked, n “How concerned are you about threats to your personal privacy in America today? ” Percentage “very concerned”: n 1978 --31% n 1994 --58% n
Trends in Concerns About Privacy Harris surveys asked, n “How concerned are you about threats to your personal privacy in America today? ” Percentage “very concerned”: n 1978 --31% n 1994 --58% n
 Emerging Technologies Data warehousing n. Computer networks n. Electronic data capture n
Emerging Technologies Data warehousing n. Computer networks n. Electronic data capture n
 PERSPECTIVE Restricted Data Restricted Access
PERSPECTIVE Restricted Data Restricted Access
 RESTRICTED DATA Confidentiality motivates release of transformed data n. Apply a statistical disclosurelimitation technique n
RESTRICTED DATA Confidentiality motivates release of transformed data n. Apply a statistical disclosurelimitation technique n
 Anonymized Data Arnold Edelman Male Physics Randall Ferguson Male Chemistry $81, 250 Robert Widom Male Biology $48, 500 Sarah Majestic Female Physics $51, 000 Curtis Miller Male Math $54, 300 Ling-Fong Lu Male Physics $38, 000 $76, 300
Anonymized Data Arnold Edelman Male Physics Randall Ferguson Male Chemistry $81, 250 Robert Widom Male Biology $48, 500 Sarah Majestic Female Physics $51, 000 Curtis Miller Male Math $54, 300 Ling-Fong Lu Male Physics $38, 000 $76, 300
 Data Snooping n Q. Physicists. How many? Average salary? n n Q. Male physicists. How many? Average salary? n n A. 3 and $55, 100 A. 2 and $57, 150 Inference: Salary of Sarah Majestic is 3*55, 100 - 2*57, 150 = $51, 000
Data Snooping n Q. Physicists. How many? Average salary? n n Q. Male physicists. How many? Average salary? n n A. 3 and $55, 100 A. 2 and $57, 150 Inference: Salary of Sarah Majestic is 3*55, 100 - 2*57, 150 = $51, 000
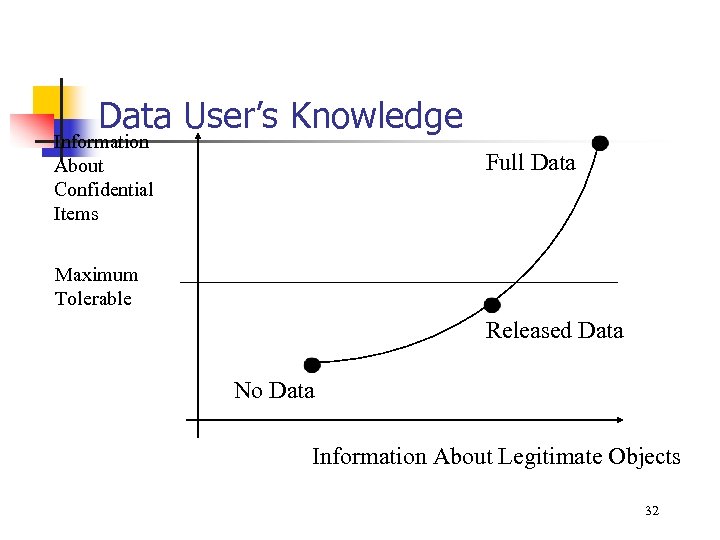 Data User’s Knowledge Information About Confidential Items Full Data Maximum Tolerable Released Data No Data Information About Legitimate Objects 32
Data User’s Knowledge Information About Confidential Items Full Data Maximum Tolerable Released Data No Data Information About Legitimate Objects 32
 How to Measure Information About Confidential Objects? n n n Disclosure Risk Record Linkage Possibilities Simulating the Data Snooper 33
How to Measure Information About Confidential Objects? n n n Disclosure Risk Record Linkage Possibilities Simulating the Data Snooper 33
 What is a Tolerable Level? n n n Balance Confidentiality and Data Access? No What Factors Should Determine? Who Decides? 34
What is a Tolerable Level? n n n Balance Confidentiality and Data Access? No What Factors Should Determine? Who Decides? 34
 What is the Disclosure-Limitation Frontier? n Given a level of disclosure risk, what is the best that can be achieved in data utility? 35
What is the Disclosure-Limitation Frontier? n Given a level of disclosure risk, what is the best that can be achieved in data utility? 35
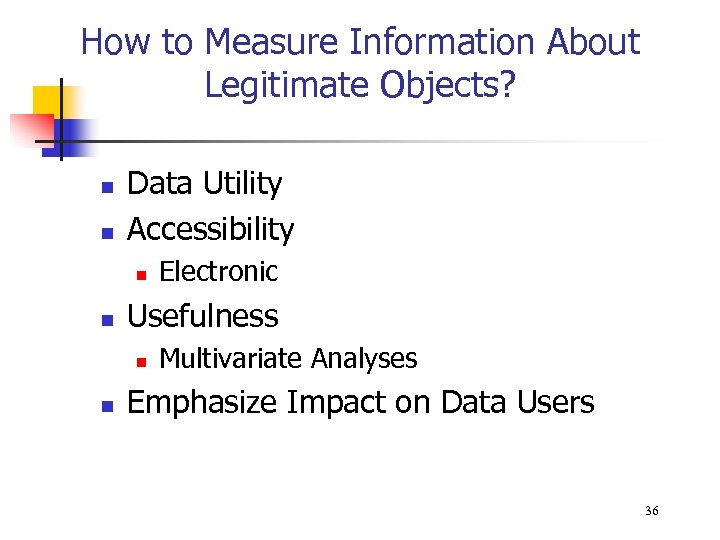 How to Measure Information About Legitimate Objects? n n Data Utility Accessibility n n Usefulness n n Electronic Multivariate Analyses Emphasize Impact on Data Users 36
How to Measure Information About Legitimate Objects? n n Data Utility Accessibility n n Usefulness n n Electronic Multivariate Analyses Emphasize Impact on Data Users 36
 RESTRICTED ACCESS Registered data users n. Monitored use n. Heinz-Census Data Center n
RESTRICTED ACCESS Registered data users n. Monitored use n. Heinz-Census Data Center n
 Applications in Health Care n n Data Access Empowers Privacy and Confidentiality Protection Shields
Applications in Health Care n n Data Access Empowers Privacy and Confidentiality Protection Shields
 Empowerment Through Information Resources Scientific Data and Images n. Improved Health Care Delivery n
Empowerment Through Information Resources Scientific Data and Images n. Improved Health Care Delivery n
 Scientific Data and Images NIH Visible Human Project nhttp: //www. nlm. nih. gov/research/visible_human. html n n Transmitting Biomedical Images n Biomedical digital image libraries that use the Internet as a high speed distribution channel
Scientific Data and Images NIH Visible Human Project nhttp: //www. nlm. nih. gov/research/visible_human. html n n Transmitting Biomedical Images n Biomedical digital image libraries that use the Internet as a high speed distribution channel
 More technology. . . Virtual reality to simulate surgery n. Collaboration tools so health care providers in remote locations can provide real-time treatment to patients n. Databases to give health care providers access to medical information n
More technology. . . Virtual reality to simulate surgery n. Collaboration tools so health care providers in remote locations can provide real-time treatment to patients n. Databases to give health care providers access to medical information n
 An Experiment Randomized Controlled Trial n. Physicians Wrote Inpatient Orders on Workstations with Screen Information that Encouraged Cost-Effective Ordering n Charges per admission reduced $887 n Hospital stays reduced. 89 days n Physician time per patient increased 5. 5 minutes per patient n
An Experiment Randomized Controlled Trial n. Physicians Wrote Inpatient Orders on Workstations with Screen Information that Encouraged Cost-Effective Ordering n Charges per admission reduced $887 n Hospital stays reduced. 89 days n Physician time per patient increased 5. 5 minutes per patient n
 Agency for Health Care Policy Research (AHCPR) Computer-Based Patient Record Systems n. Clinical Computer Decision Support Systems n. Analysis of Confidentiality and Privacy Issues Concerning Researcher Access to Patient Care Data n
Agency for Health Care Policy Research (AHCPR) Computer-Based Patient Record Systems n. Clinical Computer Decision Support Systems n. Analysis of Confidentiality and Privacy Issues Concerning Researcher Access to Patient Care Data n
 Health Care Financing Administration (HCFA) Medicare and Medicaid Database n. Large computer network, linking enrollment and benefits information to contractor claims payment sites and providers n. Process over 500 million claims annually n
Health Care Financing Administration (HCFA) Medicare and Medicaid Database n. Large computer network, linking enrollment and benefits information to contractor claims payment sites and providers n. Process over 500 million claims annually n
 Department of Veterans Affairs VA maintains Patient Data Exchange (PDX) n. Share clinical data across network n. Integrated imaging project to store medical images as part of the electronic patient record n
Department of Veterans Affairs VA maintains Patient Data Exchange (PDX) n. Share clinical data across network n. Integrated imaging project to store medical images as part of the electronic patient record n
 Regenstrief Medical Record System (RMRS) Three Hospitals of Indiana University Medical Center and Thirty off-Campus Sites Around Indianapolis n. Contains n Coded diagnostic impressions n Encounter information n Medication records n Physician orders n Vital signs n
Regenstrief Medical Record System (RMRS) Three Hospitals of Indiana University Medical Center and Thirty off-Campus Sites Around Indianapolis n. Contains n Coded diagnostic impressions n Encounter information n Medication records n Physician orders n Vital signs n
 RMRS Data Access Anywhere Within IU Medical System n. By 1995, Carried 80 Million Observations for 800 Thousand Different Patients n. Immediate Access for Patient Care, Management, or Clinical Research Purposes n
RMRS Data Access Anywhere Within IU Medical System n. By 1995, Carried 80 Million Observations for 800 Thousand Different Patients n. Immediate Access for Patient Care, Management, or Clinical Research Purposes n
 What Information Contained? Clinical Information n. Family History n. Insurance Information n
What Information Contained? Clinical Information n. Family History n. Insurance Information n
 Positive Effects of IT on Medical Records Mobility in Health Care System n. Competition Among Health Care Providers n. Speed Treatment n. Reduce Administrative Costs n Eliminate duplication of paperwork n Promote standard data definitions n Speed claims processing n
Positive Effects of IT on Medical Records Mobility in Health Care System n. Competition Among Health Care Providers n. Speed Treatment n. Reduce Administrative Costs n Eliminate duplication of paperwork n Promote standard data definitions n Speed claims processing n
 More Positive Effects. . . Audits of Health Care Providers and Insurers n. Legal Accountability of Provider to Patient n. Scientific studies of medically-effective and cost-effective patient care n. Link patient outcome to medical treatment n
More Positive Effects. . . Audits of Health Care Providers and Insurers n. Legal Accountability of Provider to Patient n. Scientific studies of medically-effective and cost-effective patient care n. Link patient outcome to medical treatment n
 Technology Needed n Data Input Oral n Direct feed from monitoring instruments n n Data Storage Graphics n Video, Audio n n Data Dissemination High-speed networks n Sophisticated database query languages n
Technology Needed n Data Input Oral n Direct feed from monitoring instruments n n Data Storage Graphics n Video, Audio n n Data Dissemination High-speed networks n Sophisticated database query languages n
 But … Why Privacy and Confidentiality Matter A Basic Value Related to Solitude, Autonomy, and Individuality n. Without Confidentiality Assurance, Patient May Not Provide Accurate Data n. Even More Critically, They May Not Present or Cooperate In Treatment n
But … Why Privacy and Confidentiality Matter A Basic Value Related to Solitude, Autonomy, and Individuality n. Without Confidentiality Assurance, Patient May Not Provide Accurate Data n. Even More Critically, They May Not Present or Cooperate In Treatment n
 Breach of Confidentiality New York State Health Department Disclosed the Names of 28 Abortion Patients in a Publicly Available Report n
Breach of Confidentiality New York State Health Department Disclosed the Names of 28 Abortion Patients in a Publicly Available Report n
 Sensitivity of Health Care Data Diagnostic and Testing Information n. Family History n. Genetic Testing n. History of Diseases and Treatments n. History of Drug Use n. Sexual Orientation and Practices n. Demeanor, Character, and Mental State n. Financial Information n
Sensitivity of Health Care Data Diagnostic and Testing Information n. Family History n. Genetic Testing n. History of Diseases and Treatments n. History of Drug Use n. Sexual Orientation and Practices n. Demeanor, Character, and Mental State n. Financial Information n
 Information Demands Hospital Administration n. Physician n. Insurance Company n. Government n. Employer n. Health Care Researcher n. Journalist n. Family Member n
Information Demands Hospital Administration n. Physician n. Insurance Company n. Government n. Employer n. Health Care Researcher n. Journalist n. Family Member n
 Source of Threats Unauthorized Access n. Computer Viruses n. Negligent Handling n. Insider Misuse n
Source of Threats Unauthorized Access n. Computer Viruses n. Negligent Handling n. Insider Misuse n
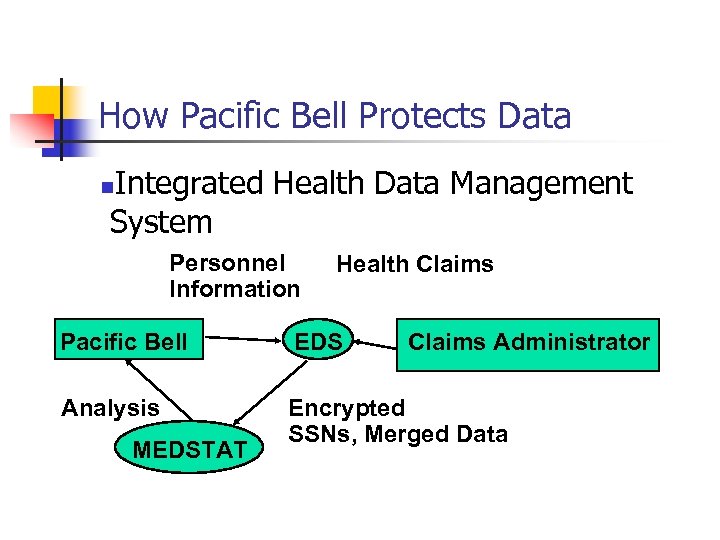 How Pacific Bell Protects Data Integrated Health Data Management System n Personnel Information Health Claims Pacific Bell EDS Analysis Encrypted SSNs, Merged Data MEDSTAT Claims Administrator
How Pacific Bell Protects Data Integrated Health Data Management System n Personnel Information Health Claims Pacific Bell EDS Analysis Encrypted SSNs, Merged Data MEDSTAT Claims Administrator
 Shore the Foundations Data Access Confidentiality Protection
Shore the Foundations Data Access Confidentiality Protection
 Next Time. . . Basic Probability n n Interpretations Odds Rules Contingency Tables
Next Time. . . Basic Probability n n Interpretations Odds Rules Contingency Tables


