a270cbcebff0fc1c02a4db878ddd991b.ppt
- Количество слайдов: 25
 Lecture 19 Message Integrity CPE 401/601 Computer Network Systems All material copyright 1996 -2009 J. F Kurose and K. W. Ross, All Rights Reserved slides are modified from Jim Kurose & Keith Ross
Lecture 19 Message Integrity CPE 401/601 Computer Network Systems All material copyright 1996 -2009 J. F Kurose and K. W. Ross, All Rights Reserved slides are modified from Jim Kurose & Keith Ross
 Message Integrity r Allows communicating parties to verify that received messages are authentic. m Content of message has not been altered m Source of message is who/what you think it is m Message has not been replayed m Sequence of messages is maintained 2
Message Integrity r Allows communicating parties to verify that received messages are authentic. m Content of message has not been altered m Source of message is who/what you think it is m Message has not been replayed m Sequence of messages is maintained 2
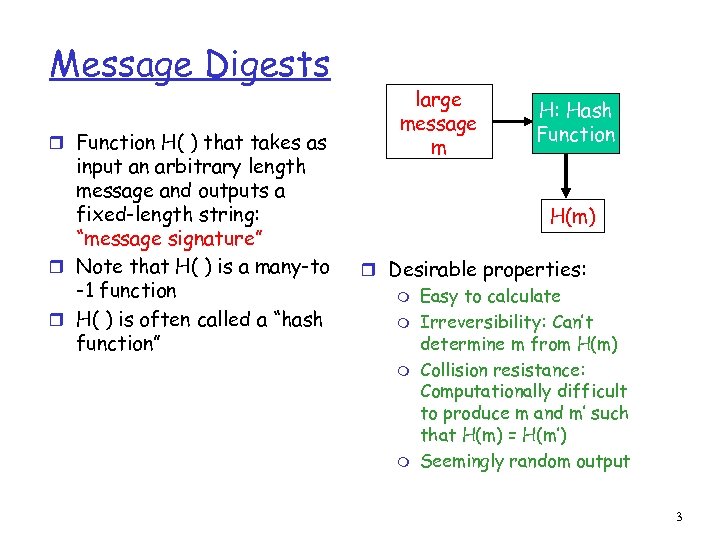 Message Digests r Function H( ) that takes as input an arbitrary length message and outputs a fixed-length string: “message signature” r Note that H( ) is a many-to -1 function r H( ) is often called a “hash function” large message m H: Hash Function H(m) r Desirable properties: m m Easy to calculate Irreversibility: Can’t determine m from H(m) Collision resistance: Computationally difficult to produce m and m’ such that H(m) = H(m’) Seemingly random output 3
Message Digests r Function H( ) that takes as input an arbitrary length message and outputs a fixed-length string: “message signature” r Note that H( ) is a many-to -1 function r H( ) is often called a “hash function” large message m H: Hash Function H(m) r Desirable properties: m m Easy to calculate Irreversibility: Can’t determine m from H(m) Collision resistance: Computationally difficult to produce m and m’ such that H(m) = H(m’) Seemingly random output 3
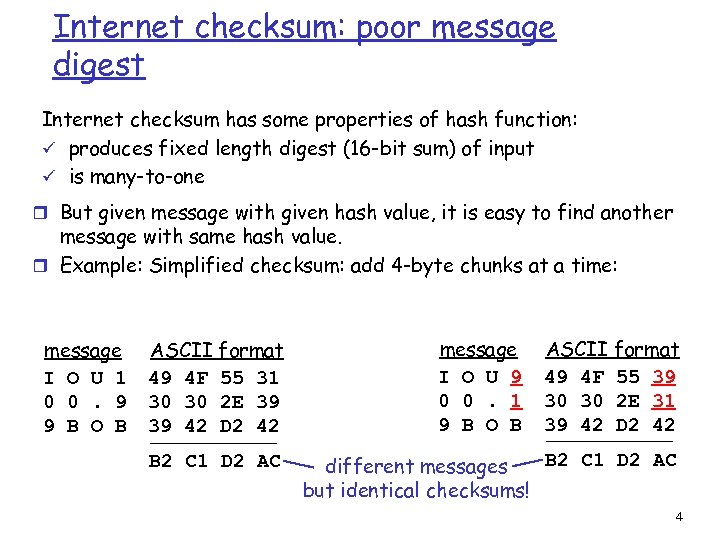 Internet checksum: poor message digest Internet checksum has some properties of hash function: ü produces fixed length digest (16 -bit sum) of input ü is many-to-one r But given message with given hash value, it is easy to find another message with same hash value. r Example: Simplified checksum: add 4 -byte chunks at a time: message I O U 1 0 0. 9 9 B O B ASCII format 49 4 F 55 31 30 30 2 E 39 39 42 D 2 42 B 2 C 1 D 2 AC message I O U 9 0 0. 1 9 B O B ASCII format 49 4 F 55 39 30 30 2 E 31 39 42 D 2 42 B 2 C 1 D 2 AC different messages but identical checksums! 4
Internet checksum: poor message digest Internet checksum has some properties of hash function: ü produces fixed length digest (16 -bit sum) of input ü is many-to-one r But given message with given hash value, it is easy to find another message with same hash value. r Example: Simplified checksum: add 4 -byte chunks at a time: message I O U 1 0 0. 9 9 B O B ASCII format 49 4 F 55 31 30 30 2 E 39 39 42 D 2 42 B 2 C 1 D 2 AC message I O U 9 0 0. 1 9 B O B ASCII format 49 4 F 55 39 30 30 2 E 31 39 42 D 2 42 B 2 C 1 D 2 AC different messages but identical checksums! 4
 Hash Function Algorithms r MD 5 hash function widely used (RFC 1321) m computes process. 128 -bit message digest in 4 -step r SHA-1 is also used. m US standard [NIST, FIPS PUB 180 -1] m 160 -bit message digest 5
Hash Function Algorithms r MD 5 hash function widely used (RFC 1321) m computes process. 128 -bit message digest in 4 -step r SHA-1 is also used. m US standard [NIST, FIPS PUB 180 -1] m 160 -bit message digest 5
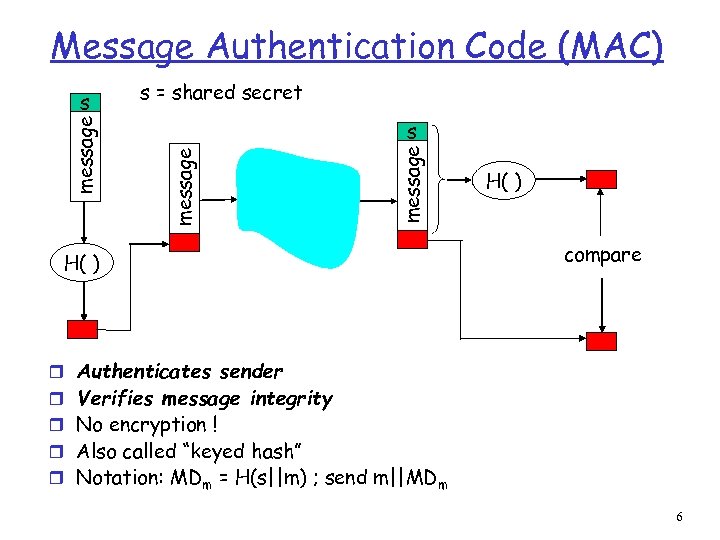 Message Authentication Code (MAC) s = shared secret message s H( ) compare r Authenticates sender r Verifies message integrity r No encryption ! r Also called “keyed hash” r Notation: MDm = H(s||m) ; send m||MDm 6
Message Authentication Code (MAC) s = shared secret message s H( ) compare r Authenticates sender r Verifies message integrity r No encryption ! r Also called “keyed hash” r Notation: MDm = H(s||m) ; send m||MDm 6
 HMAC r Popular MAC standard r Addresses some subtle security flaws Concatenates secret to front of message. 2. Hashes concatenated message 3. Concatenates the secret to front of digest 4. Hashes the combination again. 1. 7
HMAC r Popular MAC standard r Addresses some subtle security flaws Concatenates secret to front of message. 2. Hashes concatenated message 3. Concatenates the secret to front of digest 4. Hashes the combination again. 1. 7
 Example: OSPF r Recall that OSPF is an intra-AS routing protocol r Each router creates map of entire AS (or area) and runs shortest path algorithm over map. r Router receives linkstate advertisements (LSAs) from all other routers in AS. Attacks: r Message insertion r Message deletion r Message modification r How do we know if an OSPF message is authentic? 8
Example: OSPF r Recall that OSPF is an intra-AS routing protocol r Each router creates map of entire AS (or area) and runs shortest path algorithm over map. r Router receives linkstate advertisements (LSAs) from all other routers in AS. Attacks: r Message insertion r Message deletion r Message modification r How do we know if an OSPF message is authentic? 8
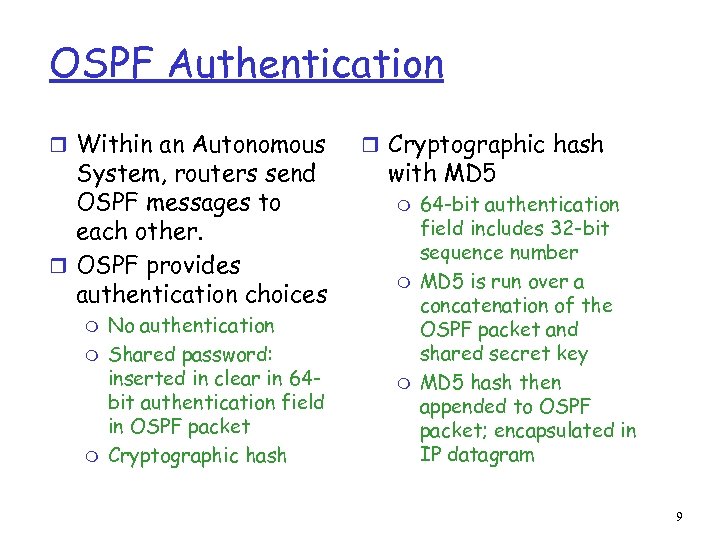 OSPF Authentication r Within an Autonomous System, routers send OSPF messages to each other. r OSPF provides authentication choices m m m No authentication Shared password: inserted in clear in 64 bit authentication field in OSPF packet Cryptographic hash r Cryptographic hash with MD 5 m m m 64 -bit authentication field includes 32 -bit sequence number MD 5 is run over a concatenation of the OSPF packet and shared secret key MD 5 hash then appended to OSPF packet; encapsulated in IP datagram 9
OSPF Authentication r Within an Autonomous System, routers send OSPF messages to each other. r OSPF provides authentication choices m m m No authentication Shared password: inserted in clear in 64 bit authentication field in OSPF packet Cryptographic hash r Cryptographic hash with MD 5 m m m 64 -bit authentication field includes 32 -bit sequence number MD 5 is run over a concatenation of the OSPF packet and shared secret key MD 5 hash then appended to OSPF packet; encapsulated in IP datagram 9
 End-point authentication r Want to be sure of the originator of the message m end-point authentication r Assuming Alice and Bob have a shared secret, will MAC provide end-point authentication. m We do know that Alice created the message. m But did she send it? 10
End-point authentication r Want to be sure of the originator of the message m end-point authentication r Assuming Alice and Bob have a shared secret, will MAC provide end-point authentication. m We do know that Alice created the message. m But did she send it? 10
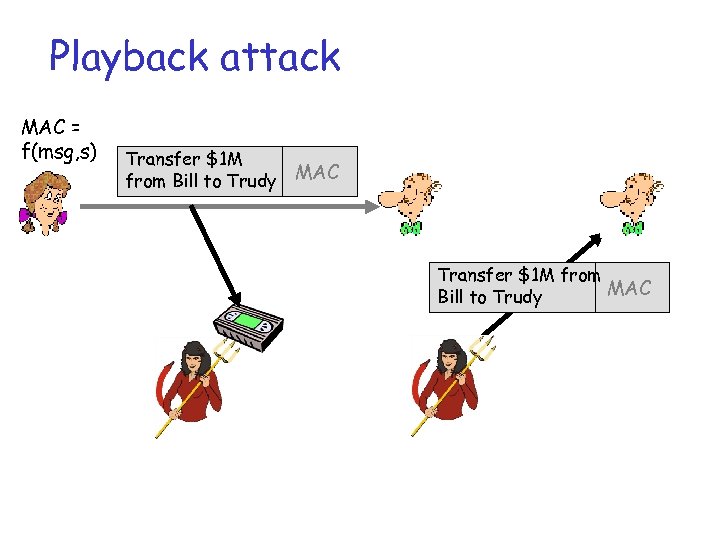 Playback attack MAC = f(msg, s) Transfer $1 M from Bill to Trudy MAC Transfer $1 M from MAC Bill to Trudy
Playback attack MAC = f(msg, s) Transfer $1 M from Bill to Trudy MAC Transfer $1 M from MAC Bill to Trudy
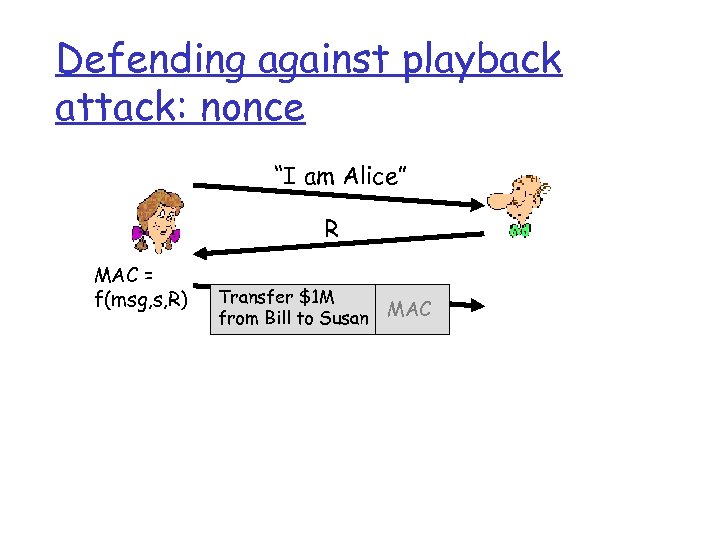 Defending against playback attack: nonce “I am Alice” R MAC = f(msg, s, R) Transfer $1 M from Bill to Susan MAC
Defending against playback attack: nonce “I am Alice” R MAC = f(msg, s, R) Transfer $1 M from Bill to Susan MAC
 Digital Signatures Cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r Goal is similar to that of a MAC, except now use public-key cryptography r verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 13
Digital Signatures Cryptographic technique analogous to handwritten signatures. r sender (Bob) digitally signs document, establishing he is document owner/creator. r Goal is similar to that of a MAC, except now use public-key cryptography r verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 13
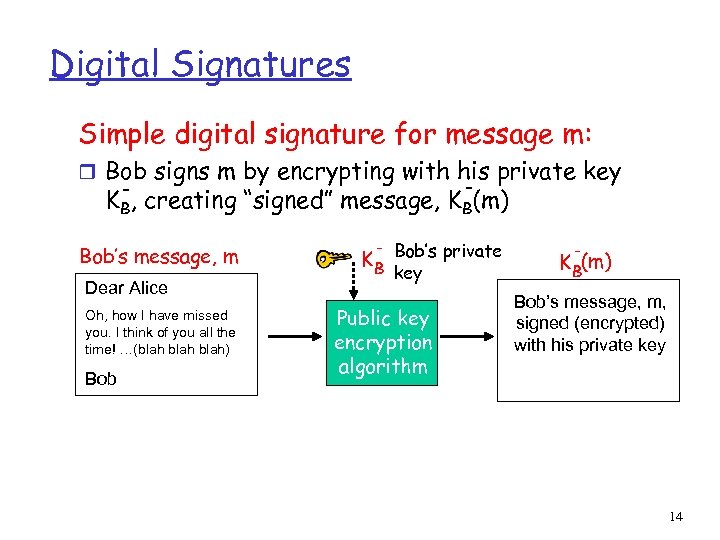 Digital Signatures Simple digital signature for message m: r Bob signs m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key Public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 14
Digital Signatures Simple digital signature for message m: r Bob signs m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. I think of you all the time! …(blah) Bob K B Bob’s private key Public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 14
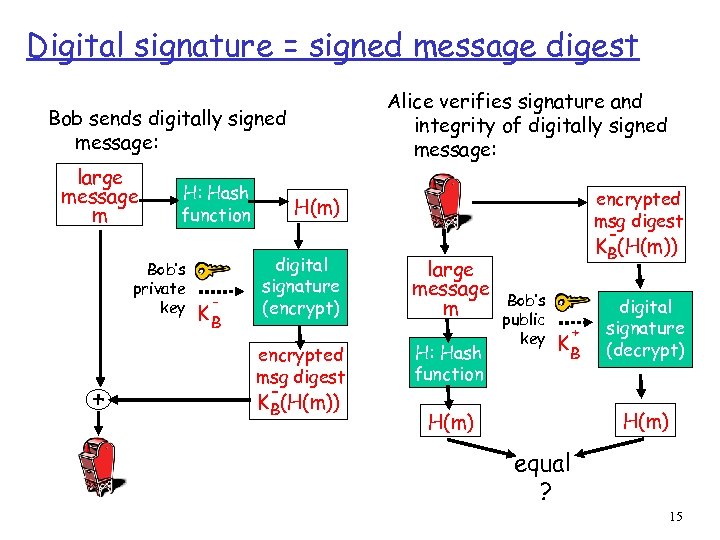 Digital signature = signed message digest Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 15
Digital signature = signed message digest Alice verifies signature and integrity of digitally signed message: Bob sends digitally signed message: large message m H: Hash function Bob’s private key + - KB encrypted msg digest H(m) digital signature (encrypt) encrypted msg digest KB(H(m)) large message m H: Hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 15
 Digital Signatures (more) - r Suppose Alice receives msg m, digital signature K B(m) r Alice verifies m signed by Bob by applying Bob’s + - public key KB to KB(m) then checks KB(KB(m) ) = m. + - r If KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 16
Digital Signatures (more) - r Suppose Alice receives msg m, digital signature K B(m) r Alice verifies m signed by Bob by applying Bob’s + - public key KB to KB(m) then checks KB(KB(m) ) = m. + - r If KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Alice thus verifies that: ü Bob signed m. ü No one else signed m. ü Bob signed m and not m’. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 16
 Public-key certification r Motivation: Trudy plays pizza prank on Bob m Trudy creates e-mail order: Dear Pizza Store, Please deliver to me four pepperoni pizzas. Thank you, Bob m Trudy signs order with her private key m Trudy sends order to Pizza Store m Trudy sends to Pizza Store her public key, but says it’s Bob’s public key. m Pizza Store verifies signature; then delivers four pizzas to Bob. m Bob doesn’t even like Pepperoni 17
Public-key certification r Motivation: Trudy plays pizza prank on Bob m Trudy creates e-mail order: Dear Pizza Store, Please deliver to me four pepperoni pizzas. Thank you, Bob m Trudy signs order with her private key m Trudy sends order to Pizza Store m Trudy sends to Pizza Store her public key, but says it’s Bob’s public key. m Pizza Store verifies signature; then delivers four pizzas to Bob. m Bob doesn’t even like Pepperoni 17
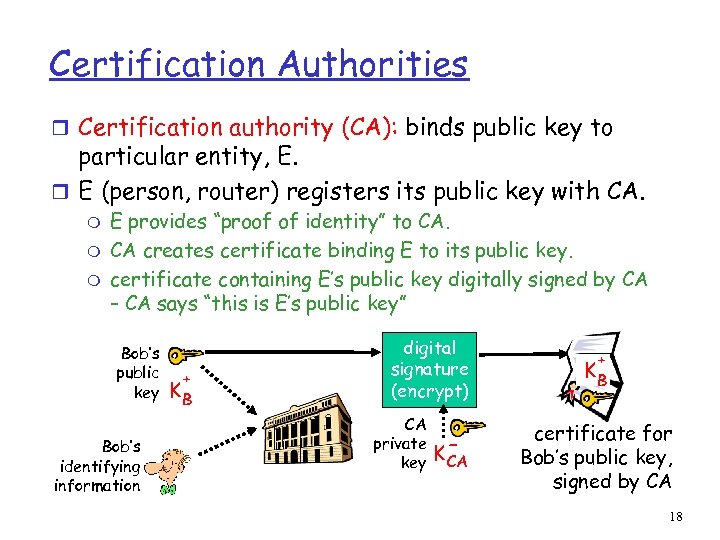 Certification Authorities r Certification authority (CA): binds public key to particular entity, E. r E (person, router) registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA 18
Certification Authorities r Certification authority (CA): binds public key to particular entity, E. r E (person, router) registers its public key with CA. m m m E provides “proof of identity” to CA. CA creates certificate binding E to its public key. certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” Bob’s public key Bob’s identifying information + KB digital signature (encrypt) CA private key K- CA + KB certificate for Bob’s public key, signed by CA 18
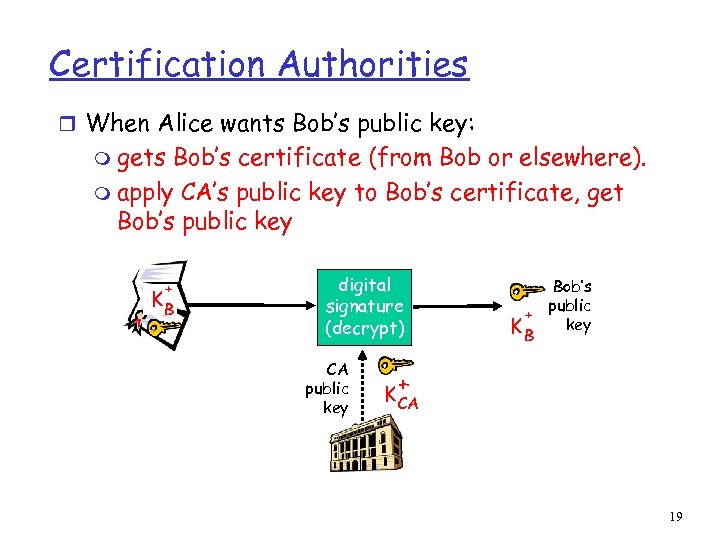 Certification Authorities r When Alice wants Bob’s public key: m gets Bob’s certificate (from Bob or elsewhere). m apply CA’s public key to Bob’s certificate, get Bob’s public key + KB digital signature (decrypt) CA public key Bob’s public + key KB + K CA 19
Certification Authorities r When Alice wants Bob’s public key: m gets Bob’s certificate (from Bob or elsewhere). m apply CA’s public key to Bob’s certificate, get Bob’s public key + KB digital signature (decrypt) CA public key Bob’s public + key KB + K CA 19
 Certificates: summary r Primary standard X. 509 (RFC 2459) r Certificate contains: m Issuer name m Entity name, address, domain name, etc. m Entity’s public key m Digital signature (signed with issuer’s private key) r Public-Key Infrastructure (PKI) m Certificates and certification authorities m Often considered “heavy” 20
Certificates: summary r Primary standard X. 509 (RFC 2459) r Certificate contains: m Issuer name m Entity name, address, domain name, etc. m Entity’s public key m Digital signature (signed with issuer’s private key) r Public-Key Infrastructure (PKI) m Certificates and certification authorities m Often considered “heavy” 20
 Chapter 8 roadmap 8. 1 What is network security? 8. 2 Principles of cryptography 8. 3 Message integrity 8. 4 Securing e-mail 8. 5 Securing TCP connections: SSL 8. 6 Network layer security: IPsec 8. 7 Securing wireless LANs 8. 8 Operational security: firewalls and IDS
Chapter 8 roadmap 8. 1 What is network security? 8. 2 Principles of cryptography 8. 3 Message integrity 8. 4 Securing e-mail 8. 5 Securing TCP connections: SSL 8. 6 Network layer security: IPsec 8. 7 Securing wireless LANs 8. 8 Operational security: firewalls and IDS
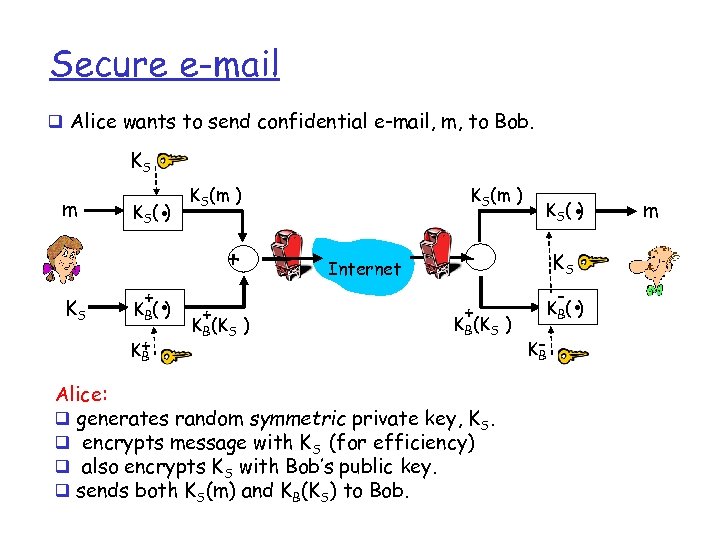 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . KB ( ) K+ B KS(m ) + + KB(KS ) Internet . KS( ) - KS + KB ( ) KB(KS ) Alice: q generates random symmetric private key, KS. q encrypts message with KS (for efficiency) q also encrypts KS with Bob’s public key. q sends both KS(m) and KB(KS) to Bob. - KB . m
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . KB ( ) K+ B KS(m ) + + KB(KS ) Internet . KS( ) - KS + KB ( ) KB(KS ) Alice: q generates random symmetric private key, KS. q encrypts message with KS (for efficiency) q also encrypts KS with Bob’s public key. q sends both KS(m) and KB(KS) to Bob. - KB . m
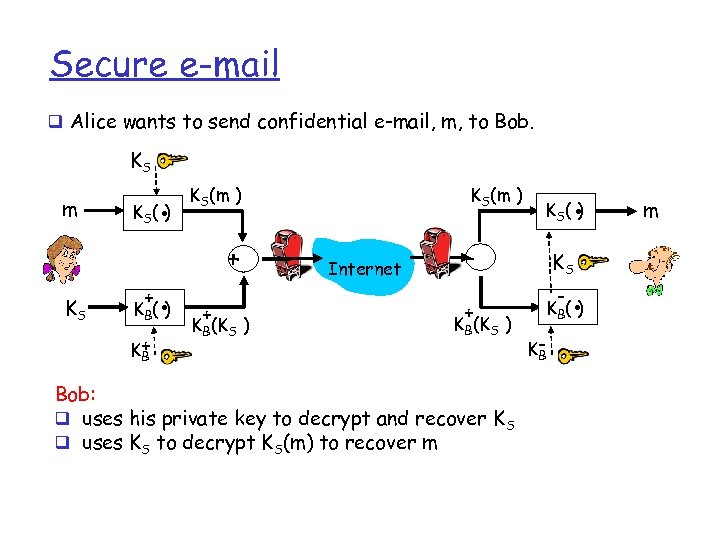 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . KB ( ) K+ B KS(m ) + + KB(KS ) Internet . KS( ) - KS + KB ( ) KB(KS ) Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m - KB . m
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + . KB ( ) K+ B KS(m ) + + KB(KS ) Internet . KS( ) - KS + KB ( ) KB(KS ) Bob: q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m - KB . m
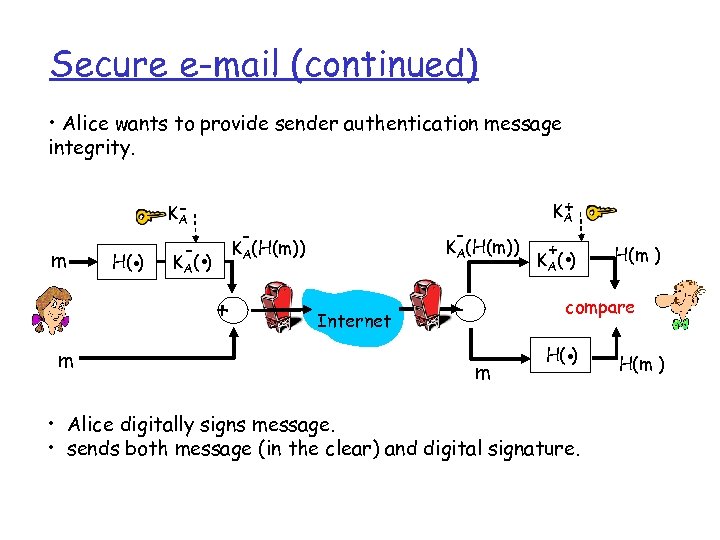 Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . + m - - KA(H(m)) KA( ) + KA Internet - + . KA( ) H(m ) compare m . H( ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. H(m )
Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . + m - - KA(H(m)) KA( ) + KA Internet - + . KA( ) H(m ) compare m . H( ) • Alice digitally signs message. • sends both message (in the clear) and digital signature. H(m )
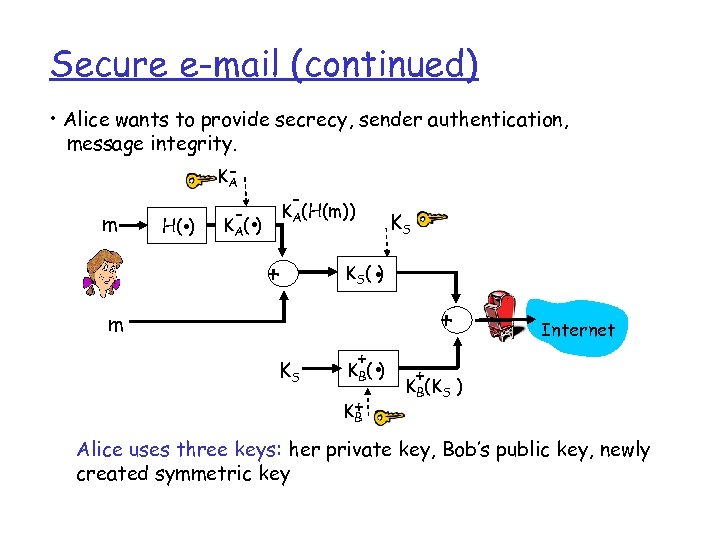 Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. KA KA(H(m)) KS m KA( ) H( ) . . + . KS( ) m KS + . KB ( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key
Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. KA KA(H(m)) KS m KA( ) H( ) . . + . KS( ) m KS + . KB ( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key


