42dad49ab2ab4759400f4a83eb039710.ppt
- Количество слайдов: 44
 Lecture 19: Authentication John Daugman, http: //www. cl. cam. ac. uk/users/jgd 1000/iriscollage. jpg CS 588: Cryptography David Evans University of Virginia 19 April 2005 University of Virginia CS 588 http: //www. cs. virginia. edu/evans Computer Science
Lecture 19: Authentication John Daugman, http: //www. cl. cam. ac. uk/users/jgd 1000/iriscollage. jpg CS 588: Cryptography David Evans University of Virginia 19 April 2005 University of Virginia CS 588 http: //www. cs. virginia. edu/evans Computer Science
 How do you authenticate? • Something you know – Password • Something you have – Secure. ID, physical key • Something you are – Biometrics (voiceprint, fingerprint, etc. ) • Decent authentication requires combination of at least 2 of these 19 April 2005 University of Virginia CS 588 2
How do you authenticate? • Something you know – Password • Something you have – Secure. ID, physical key • Something you are – Biometrics (voiceprint, fingerprint, etc. ) • Decent authentication requires combination of at least 2 of these 19 April 2005 University of Virginia CS 588 2
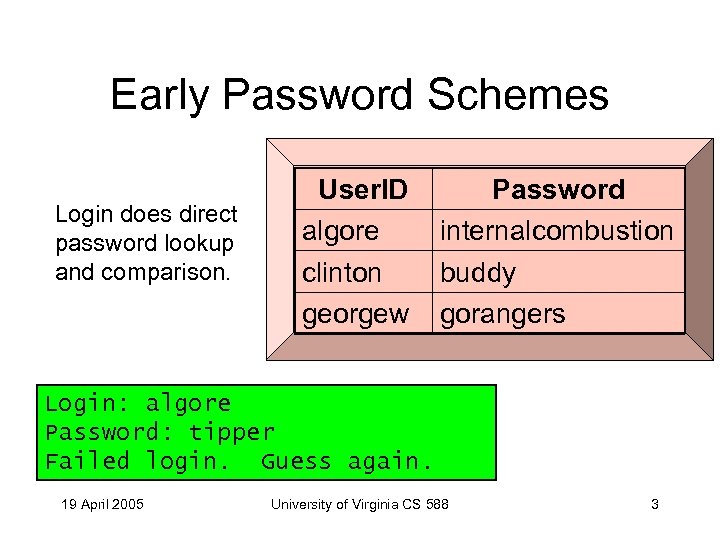 Early Password Schemes Login does direct password lookup and comparison. User. ID algore clinton georgew Password internalcombustion buddy gorangers Login: algore Password: tipper Failed login. Guess again. 19 April 2005 University of Virginia CS 588 3
Early Password Schemes Login does direct password lookup and comparison. User. ID algore clinton georgew Password internalcombustion buddy gorangers Login: algore Password: tipper Failed login. Guess again. 19 April 2005 University of Virginia CS 588 3
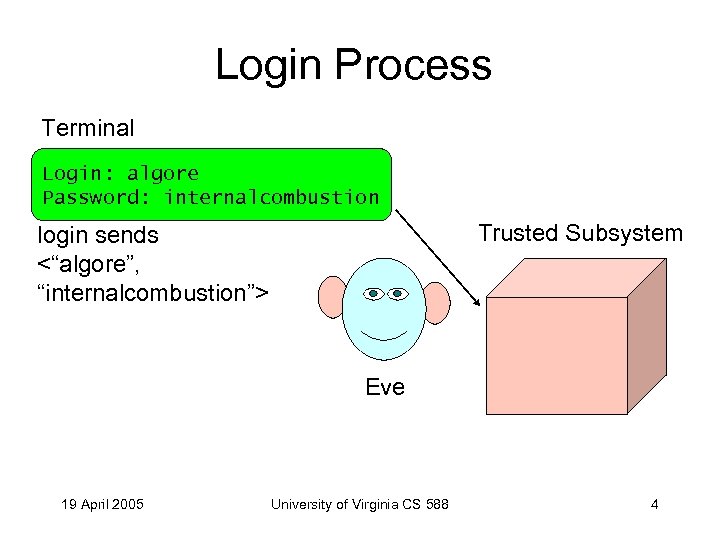 Login Process Terminal Login: algore Password: internalcombustion Trusted Subsystem login sends <“algore”, “internalcombustion”> Eve 19 April 2005 University of Virginia CS 588 4
Login Process Terminal Login: algore Password: internalcombustion Trusted Subsystem login sends <“algore”, “internalcombustion”> Eve 19 April 2005 University of Virginia CS 588 4
 Authentication Problems • Need to store the passwords somewhere – dangerous to rely on this being secure – Encrypt them? But then, need to hide key • Need to transmit password from user to host – Use a secure line (i. e. , no remote logins) – Encrypt the transmission (what key? ) 19 April 2005 University of Virginia CS 588 5
Authentication Problems • Need to store the passwords somewhere – dangerous to rely on this being secure – Encrypt them? But then, need to hide key • Need to transmit password from user to host – Use a secure line (i. e. , no remote logins) – Encrypt the transmission (what key? ) 19 April 2005 University of Virginia CS 588 5
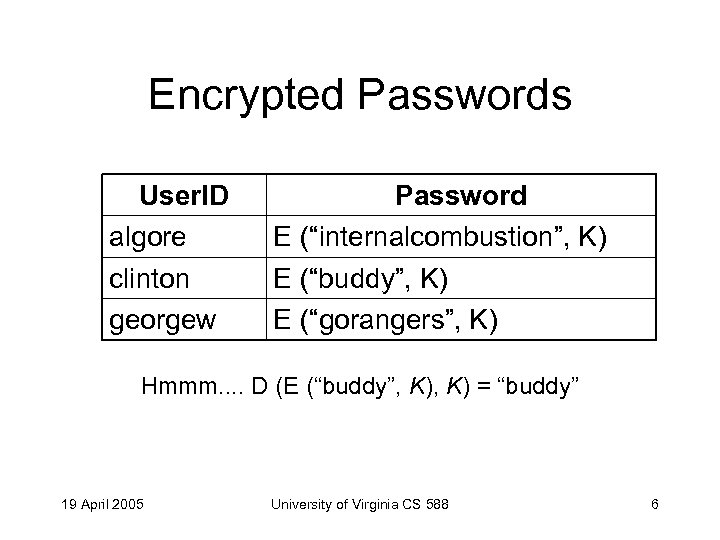 Encrypted Passwords User. ID algore clinton georgew Password E (“internalcombustion”, K) E (“buddy”, K) E (“gorangers”, K) Hmmm. . D (E (“buddy”, K) = “buddy” 19 April 2005 University of Virginia CS 588 6
Encrypted Passwords User. ID algore clinton georgew Password E (“internalcombustion”, K) E (“buddy”, K) E (“gorangers”, K) Hmmm. . D (E (“buddy”, K) = “buddy” 19 April 2005 University of Virginia CS 588 6
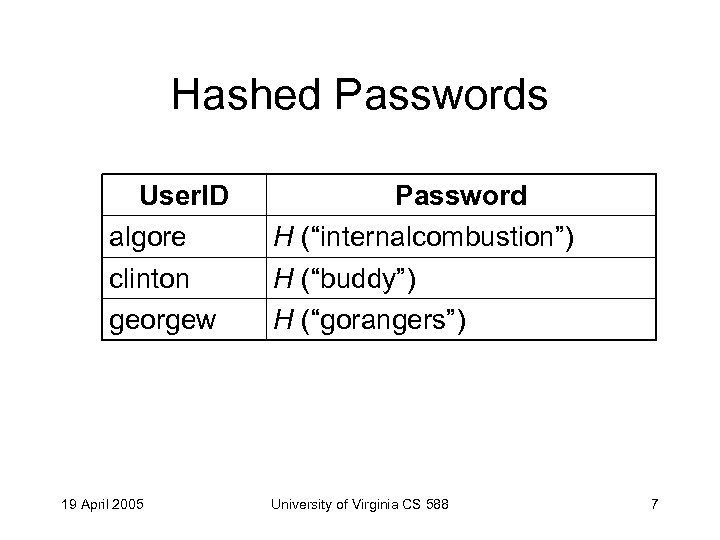 Hashed Passwords User. ID algore clinton georgew 19 April 2005 Password H (“internalcombustion”) H (“buddy”) H (“gorangers”) University of Virginia CS 588 7
Hashed Passwords User. ID algore clinton georgew 19 April 2005 Password H (“internalcombustion”) H (“buddy”) H (“gorangers”) University of Virginia CS 588 7
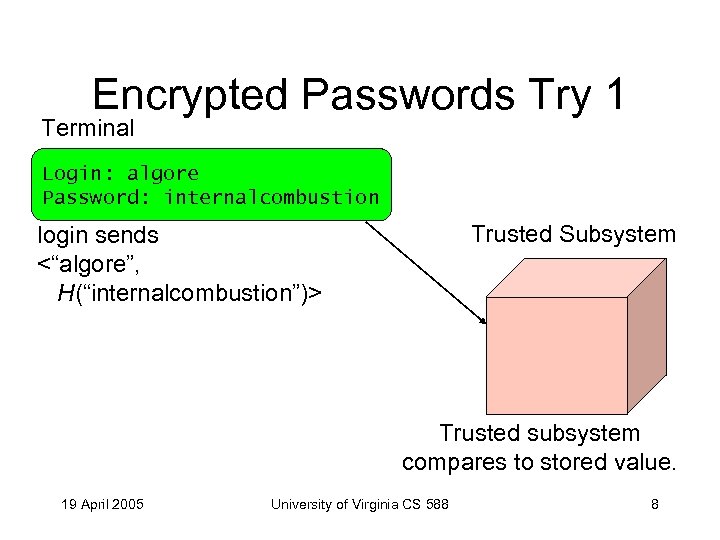 Encrypted Passwords Try 1 Terminal Login: algore Password: internalcombustion Trusted Subsystem login sends <“algore”, H(“internalcombustion”)> Trusted subsystem compares to stored value. 19 April 2005 University of Virginia CS 588 8
Encrypted Passwords Try 1 Terminal Login: algore Password: internalcombustion Trusted Subsystem login sends <“algore”, H(“internalcombustion”)> Trusted subsystem compares to stored value. 19 April 2005 University of Virginia CS 588 8
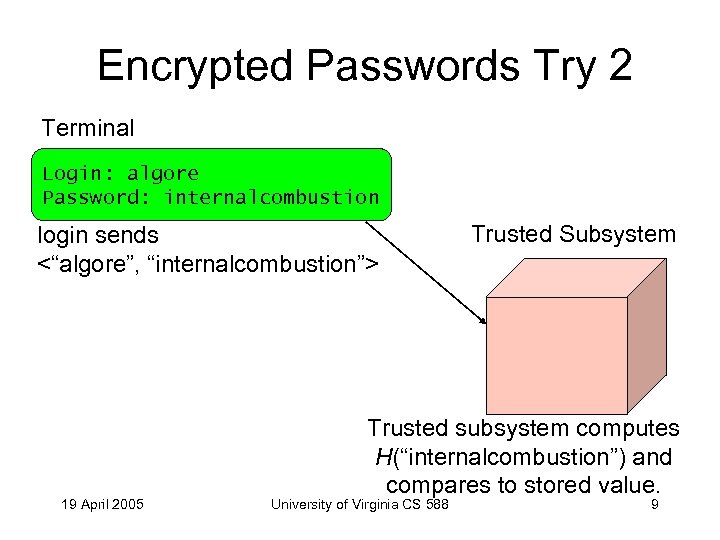 Encrypted Passwords Try 2 Terminal Login: algore Password: internalcombustion login sends <“algore”, “internalcombustion”> 19 April 2005 Trusted Subsystem Trusted subsystem computes H(“internalcombustion”) and compares to stored value. University of Virginia CS 588 9
Encrypted Passwords Try 2 Terminal Login: algore Password: internalcombustion login sends <“algore”, “internalcombustion”> 19 April 2005 Trusted Subsystem Trusted subsystem computes H(“internalcombustion”) and compares to stored value. University of Virginia CS 588 9
![First UNIX Password Scheme • [Wilkes 68] (recall DES was 1976) • Encryption based First UNIX Password Scheme • [Wilkes 68] (recall DES was 1976) • Encryption based](https://present5.com/presentation/42dad49ab2ab4759400f4a83eb039710/image-10.jpg) First UNIX Password Scheme • [Wilkes 68] (recall DES was 1976) • Encryption based on M-209 cipher machine (US Army WWII) • Easy to invert unknown plaintext and known key, used password as key: – Instead of EK (password) used hash function EPassword (0) • PDP-11 could check all 5 or less letter lower-case passwords in 4 hours! 19 April 2005 University of Virginia CS 588 10
First UNIX Password Scheme • [Wilkes 68] (recall DES was 1976) • Encryption based on M-209 cipher machine (US Army WWII) • Easy to invert unknown plaintext and known key, used password as key: – Instead of EK (password) used hash function EPassword (0) • PDP-11 could check all 5 or less letter lower-case passwords in 4 hours! 19 April 2005 University of Virginia CS 588 10
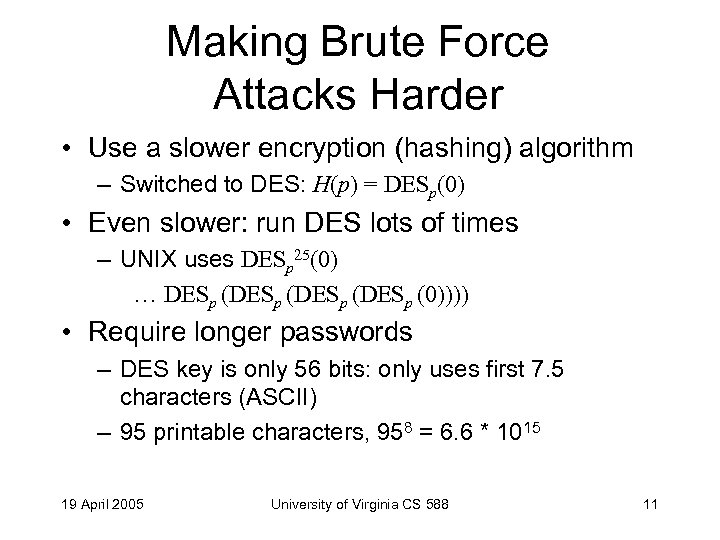 Making Brute Force Attacks Harder • Use a slower encryption (hashing) algorithm – Switched to DES: H(p) = DESp(0) • Even slower: run DES lots of times – UNIX uses DESp 25(0) … DESp (DESp (0)))) • Require longer passwords – DES key is only 56 bits: only uses first 7. 5 characters (ASCII) – 95 printable characters, 958 = 6. 6 * 1015 19 April 2005 University of Virginia CS 588 11
Making Brute Force Attacks Harder • Use a slower encryption (hashing) algorithm – Switched to DES: H(p) = DESp(0) • Even slower: run DES lots of times – UNIX uses DESp 25(0) … DESp (DESp (0)))) • Require longer passwords – DES key is only 56 bits: only uses first 7. 5 characters (ASCII) – 95 printable characters, 958 = 6. 6 * 1015 19 April 2005 University of Virginia CS 588 11
 Dictionary Attacks • Try a list of common passwords – All 1 -4 letter words – List of common (dog) names – Words from dictionary – Phone numbers, license plates – All of the above in reverse • Simple dictionary attacks retrieve most user-selected passwords • Precompute H(x) for all dictionary entries 19 April 2005 University of Virginia CS 588 12
Dictionary Attacks • Try a list of common passwords – All 1 -4 letter words – List of common (dog) names – Words from dictionary – Phone numbers, license plates – All of the above in reverse • Simple dictionary attacks retrieve most user-selected passwords • Precompute H(x) for all dictionary entries 19 April 2005 University of Virginia CS 588 12
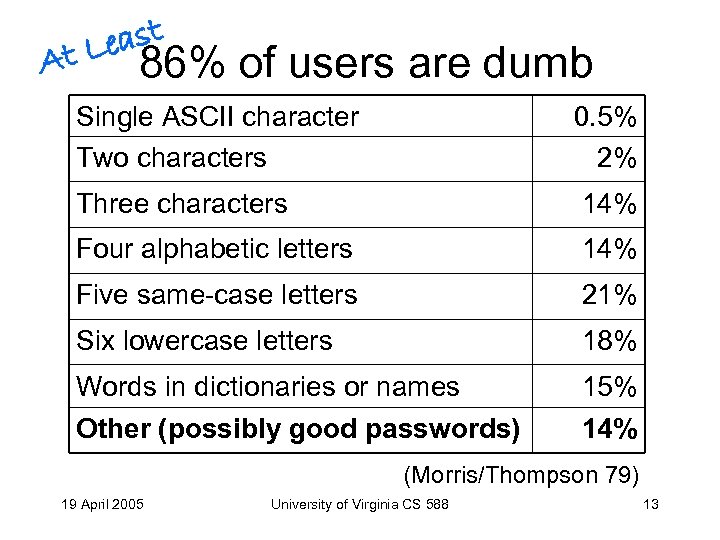 east t. L A 86% of users are dumb Single ASCII character Two characters 0. 5% 2% Three characters 14% Four alphabetic letters 14% Five same-case letters 21% Six lowercase letters 18% Words in dictionaries or names 15% Other (possibly good passwords) 14% (Morris/Thompson 79) 19 April 2005 University of Virginia CS 588 13
east t. L A 86% of users are dumb Single ASCII character Two characters 0. 5% 2% Three characters 14% Four alphabetic letters 14% Five same-case letters 21% Six lowercase letters 18% Words in dictionaries or names 15% Other (possibly good passwords) 14% (Morris/Thompson 79) 19 April 2005 University of Virginia CS 588 13
 Making Dictionary Attacks Harder • Force/convince users to pick better passwords – Test selected passwords against a known dictionary – Enforce rules on non-alphabet characters, length, etc. • Don’t let attacker see the password file 19 April 2005 University of Virginia CS 588 14
Making Dictionary Attacks Harder • Force/convince users to pick better passwords – Test selected passwords against a known dictionary – Enforce rules on non-alphabet characters, length, etc. • Don’t let attacker see the password file 19 April 2005 University of Virginia CS 588 14
 Problems with User Rules • Users get annoyed • If you require hard to remember passwords, users write them down • Attackers know the password selection rules too – reduces search space! 19 April 2005 University of Virginia CS 588 15
Problems with User Rules • Users get annoyed • If you require hard to remember passwords, users write them down • Attackers know the password selection rules too – reduces search space! 19 April 2005 University of Virginia CS 588 15
 True Anecdote • One installation: machines generated random 8 -letter passwords • Used PDP-11 pseudo-random number generator with 215 possible values • Time to try all possible passwords on PDP-11: One minute! • Good news: at least people don’t have to remember the 8 random letters 19 April 2005 University of Virginia CS 588 16
True Anecdote • One installation: machines generated random 8 -letter passwords • Used PDP-11 pseudo-random number generator with 215 possible values • Time to try all possible passwords on PDP-11: One minute! • Good news: at least people don’t have to remember the 8 random letters 19 April 2005 University of Virginia CS 588 16
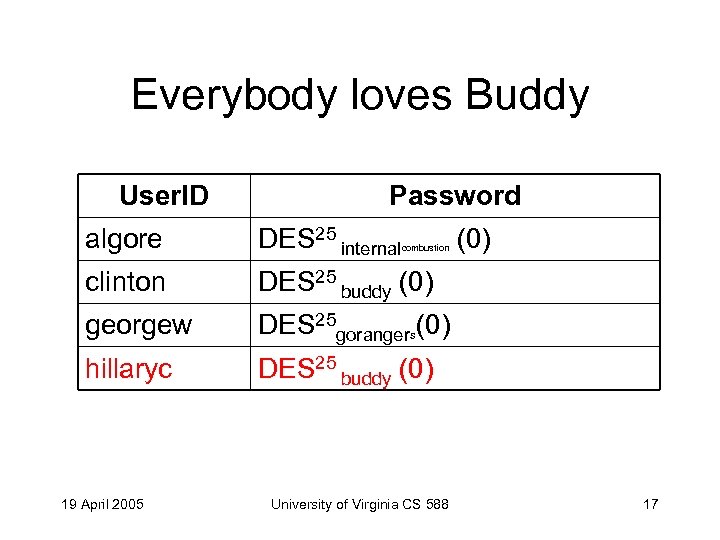 Everybody loves Buddy User. ID Password algore DES 25 internal clinton DES 25 buddy (0) georgew DES 25 gorangers(0) hillaryc DES 25 buddy (0) 19 April 2005 combustion University of Virginia CS 588 (0) 17
Everybody loves Buddy User. ID Password algore DES 25 internal clinton DES 25 buddy (0) georgew DES 25 gorangers(0) hillaryc DES 25 buddy (0) 19 April 2005 combustion University of Virginia CS 588 (0) 17
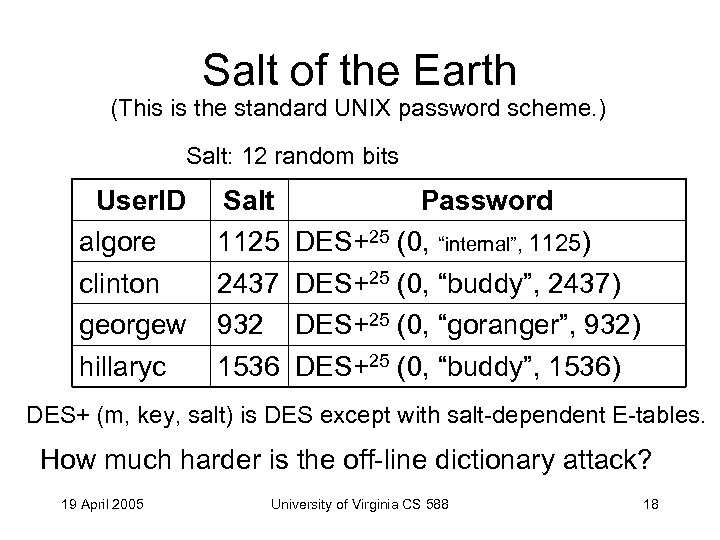 Salt of the Earth (This is the standard UNIX password scheme. ) Salt: 12 random bits User. ID algore clinton georgew hillaryc Salt 1125 2437 932 1536 Password DES+25 (0, “internal”, 1125) DES+25 (0, “buddy”, 2437) DES+25 (0, “goranger”, 932) DES+25 (0, “buddy”, 1536) DES+ (m, key, salt) is DES except with salt-dependent E-tables. How much harder is the off-line dictionary attack? 19 April 2005 University of Virginia CS 588 18
Salt of the Earth (This is the standard UNIX password scheme. ) Salt: 12 random bits User. ID algore clinton georgew hillaryc Salt 1125 2437 932 1536 Password DES+25 (0, “internal”, 1125) DES+25 (0, “buddy”, 2437) DES+25 (0, “goranger”, 932) DES+25 (0, “buddy”, 1536) DES+ (m, key, salt) is DES except with salt-dependent E-tables. How much harder is the off-line dictionary attack? 19 April 2005 University of Virginia CS 588 18
 Security of UNIX Passwords • Paper by Robert Morris (Sr. ) and Ken Thompson, 1979 (link on manifest) • Demonstration of guessability of Unix passwords by Robert Morris, Jr. (Internet Worm, 1988) • L 0 ftcrack breaks ALL alphanumeric passwords in under 24 hours on Pentium II/450 (Windows NT) 19 April 2005 University of Virginia CS 588 19
Security of UNIX Passwords • Paper by Robert Morris (Sr. ) and Ken Thompson, 1979 (link on manifest) • Demonstration of guessability of Unix passwords by Robert Morris, Jr. (Internet Worm, 1988) • L 0 ftcrack breaks ALL alphanumeric passwords in under 24 hours on Pentium II/450 (Windows NT) 19 April 2005 University of Virginia CS 588 19
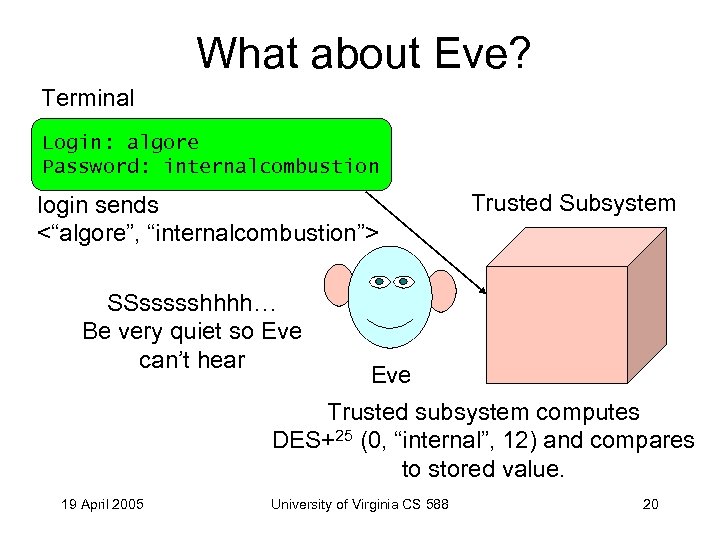 What about Eve? Terminal Login: algore Password: internalcombustion login sends <“algore”, “internalcombustion”> SSssssshhhh… Be very quiet so Eve can’t hear Trusted Subsystem Eve Trusted subsystem computes DES+25 (0, “internal”, 12) and compares to stored value. 19 April 2005 University of Virginia CS 588 20
What about Eve? Terminal Login: algore Password: internalcombustion login sends <“algore”, “internalcombustion”> SSssssshhhh… Be very quiet so Eve can’t hear Trusted Subsystem Eve Trusted subsystem computes DES+25 (0, “internal”, 12) and compares to stored value. 19 April 2005 University of Virginia CS 588 20
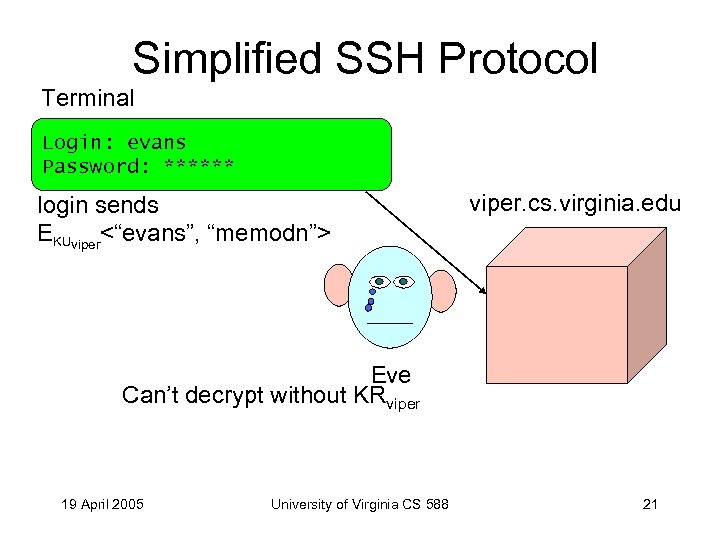 Simplified SSH Protocol Terminal Login: evans Password: ****** login sends EKUviper<“evans”, “memodn”> viper. cs. virginia. edu Eve Can’t decrypt without KRviper 19 April 2005 University of Virginia CS 588 21
Simplified SSH Protocol Terminal Login: evans Password: ****** login sends EKUviper<“evans”, “memodn”> viper. cs. virginia. edu Eve Can’t decrypt without KRviper 19 April 2005 University of Virginia CS 588 21
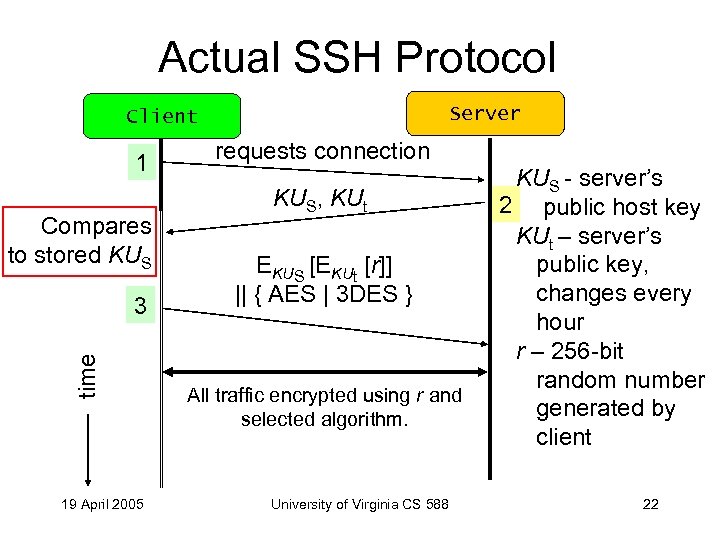 Actual SSH Protocol Server Client 1 Compares to stored KUS time 3 19 April 2005 requests connection KUS, KUt EKUS [EKUt [r]] || { AES | 3 DES } All traffic encrypted using r and selected algorithm. University of Virginia CS 588 KUS - server’s 2 public host key KUt – server’s public key, changes every hour r – 256 -bit random number generated by client 22
Actual SSH Protocol Server Client 1 Compares to stored KUS time 3 19 April 2005 requests connection KUS, KUt EKUS [EKUt [r]] || { AES | 3 DES } All traffic encrypted using r and selected algorithm. University of Virginia CS 588 KUS - server’s 2 public host key KUt – server’s public key, changes every hour r – 256 -bit random number generated by client 22
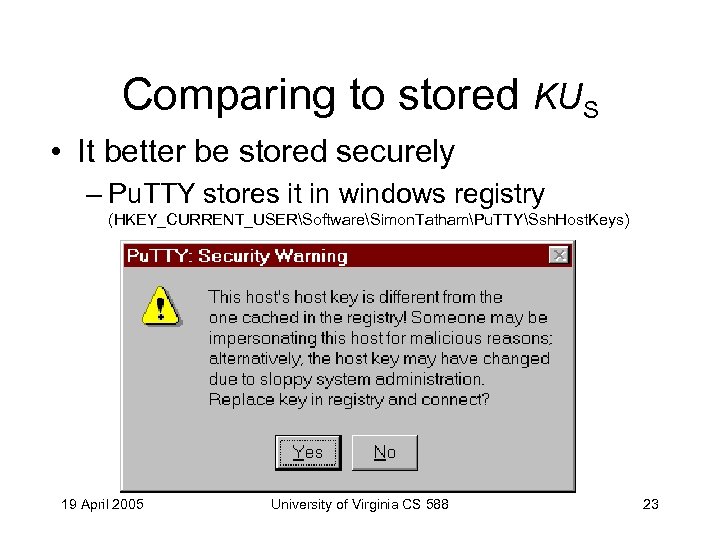 Comparing to stored KUS • It better be stored securely – Pu. TTY stores it in windows registry (HKEY_CURRENT_USERSoftwareSimon. TathamPu. TTYSsh. Host. Keys) 19 April 2005 University of Virginia CS 588 23
Comparing to stored KUS • It better be stored securely – Pu. TTY stores it in windows registry (HKEY_CURRENT_USERSoftwareSimon. TathamPu. TTYSsh. Host. Keys) 19 April 2005 University of Virginia CS 588 23
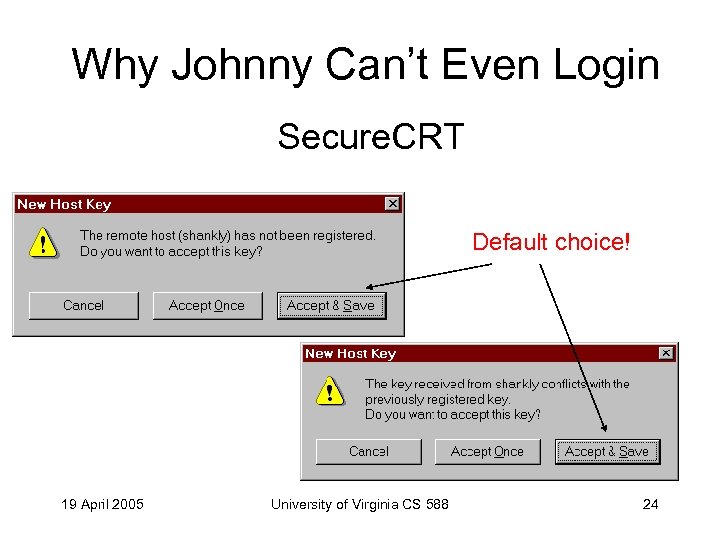 Why Johnny Can’t Even Login Secure. CRT Default choice! 19 April 2005 University of Virginia CS 588 24
Why Johnny Can’t Even Login Secure. CRT Default choice! 19 April 2005 University of Virginia CS 588 24
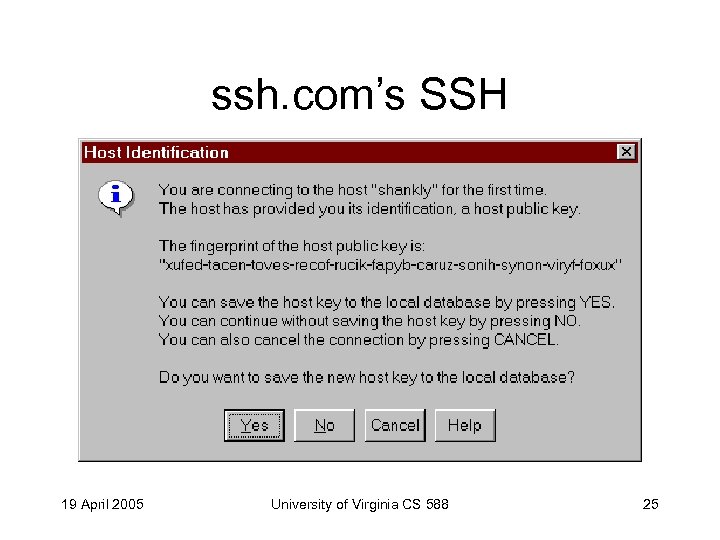 ssh. com’s SSH 19 April 2005 University of Virginia CS 588 25
ssh. com’s SSH 19 April 2005 University of Virginia CS 588 25
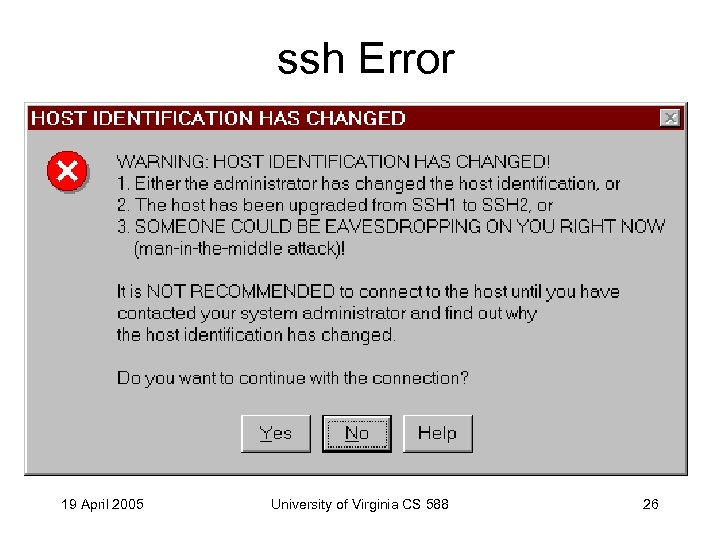 ssh Error 19 April 2005 University of Virginia CS 588 26
ssh Error 19 April 2005 University of Virginia CS 588 26
 Jennifer Kahng’s 4 th Year Thesis Project • People are stupid 31% clicked Continue • Getting people to pay attention is difficult unless you really want to make them angry. (Security vs. convenience) • Only two people (of > 700) emailed webmaster about potential security vulnerability 2% typed in “yes” 19 April 2005 University of Virginia CS 588 27
Jennifer Kahng’s 4 th Year Thesis Project • People are stupid 31% clicked Continue • Getting people to pay attention is difficult unless you really want to make them angry. (Security vs. convenience) • Only two people (of > 700) emailed webmaster about potential security vulnerability 2% typed in “yes” 19 April 2005 University of Virginia CS 588 27
 Why Johnny (von Neumann) Can’t Even Login • A smart attacker just replaces the stored key in registry – An Active. X control can do this trivially – No warning from SSH when you now connect to the host controlled by the attacker (have to spoof DNS or intercept connection, but this is easy) 19 April 2005 University of Virginia CS 588 28
Why Johnny (von Neumann) Can’t Even Login • A smart attacker just replaces the stored key in registry – An Active. X control can do this trivially – No warning from SSH when you now connect to the host controlled by the attacker (have to spoof DNS or intercept connection, but this is easy) 19 April 2005 University of Virginia CS 588 28
 Recap – Authentication Problems • Need to store the passwords somewhere – dangerous to rely on this being secure • Need to transmit password from user to host • Remaining problems: • User’s pick bad passwords • Even if everything is secure, can still watch victim type! • Only have to mess up once 19 April 2005 University of Virginia CS 588 29
Recap – Authentication Problems • Need to store the passwords somewhere – dangerous to rely on this being secure • Need to transmit password from user to host • Remaining problems: • User’s pick bad passwords • Even if everything is secure, can still watch victim type! • Only have to mess up once 19 April 2005 University of Virginia CS 588 29
 19 April 2005 University of Virginia CS 588 30
19 April 2005 University of Virginia CS 588 30
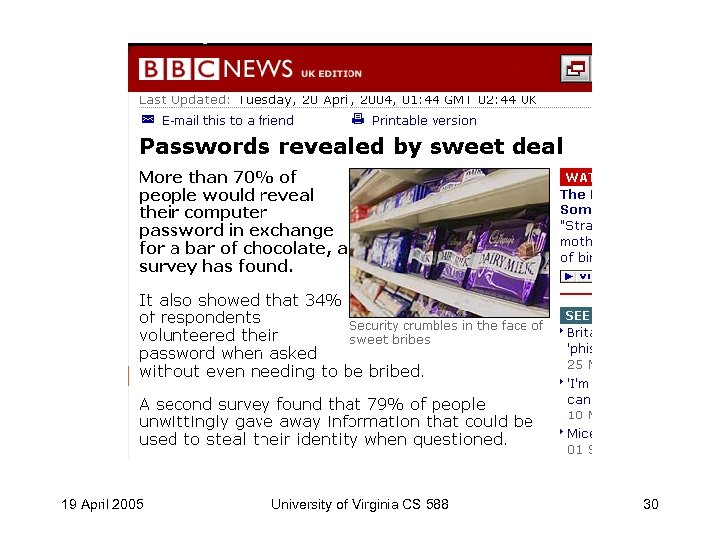
 GAO IRS Study The auditors called 100 IRS employees and managers, portraying themselves as personnel from the information technology help desk trying to correct a network problem. They asked the employees to provide their network logon name and temporarily change their password to one they suggested. "We were able to convince 35 managers and employees to provide us their username and change their password, " the report said. That was a 50 percent improvement when compared with a similar test in 2001, when 71 employees cooperated and changed their passwords. http: //www. sfgate. com/cgi-bin/article. cgi? file=/news/archive/2005/03/16/national/w 162055 S 07. DTL 19 April 2005 University of Virginia CS 588 31
GAO IRS Study The auditors called 100 IRS employees and managers, portraying themselves as personnel from the information technology help desk trying to correct a network problem. They asked the employees to provide their network logon name and temporarily change their password to one they suggested. "We were able to convince 35 managers and employees to provide us their username and change their password, " the report said. That was a 50 percent improvement when compared with a similar test in 2001, when 71 employees cooperated and changed their passwords. http: //www. sfgate. com/cgi-bin/article. cgi? file=/news/archive/2005/03/16/national/w 162055 S 07. DTL 19 April 2005 University of Virginia CS 588 31
 Solution – Don’t Reuse Passwords • One-time passwords • New users have to memorize a list of secure passwords and use one in turn for each login • Host generates the list using cryptographic random numbers and stores it securely • Users spend hours memorizing passwords. . . and better not forget one! 19 April 2005 University of Virginia CS 588 32
Solution – Don’t Reuse Passwords • One-time passwords • New users have to memorize a list of secure passwords and use one in turn for each login • Host generates the list using cryptographic random numbers and stores it securely • Users spend hours memorizing passwords. . . and better not forget one! 19 April 2005 University of Virginia CS 588 32
 One-Time Use Passwords • Can we create a sequence of passwords the host can check without storing anything useful to an attacker on the host? Recall: Unix repeated use passwords Host stores: H(p) User provides: x Password is valid if H(x) = H(p) 19 April 2005 University of Virginia CS 588 33
One-Time Use Passwords • Can we create a sequence of passwords the host can check without storing anything useful to an attacker on the host? Recall: Unix repeated use passwords Host stores: H(p) User provides: x Password is valid if H(x) = H(p) 19 April 2005 University of Virginia CS 588 33
 S-Key • Alice picks random number R • S-Key program generates H(R), H(H(R)), . . . , H 99(R). • Alice prints out these numbers and stores somewhere secure • Host stores H 100(R). 19 April 2005 University of Virginia CS 588 34
S-Key • Alice picks random number R • S-Key program generates H(R), H(H(R)), . . . , H 99(R). • Alice prints out these numbers and stores somewhere secure • Host stores H 100(R). 19 April 2005 University of Virginia CS 588 34
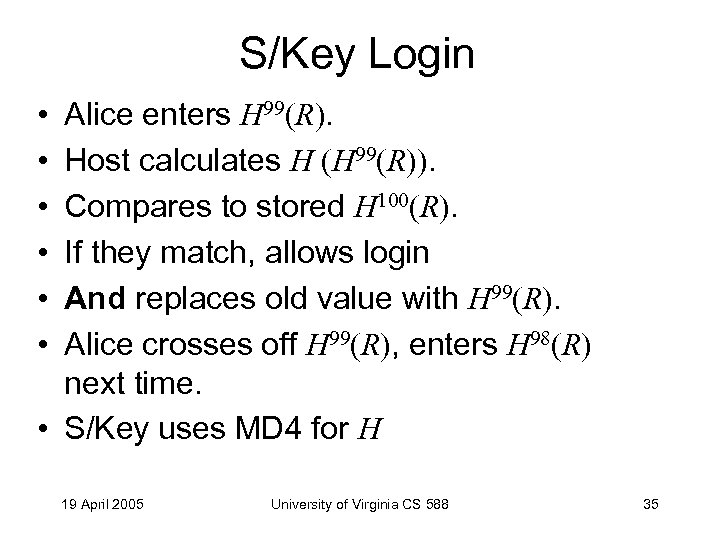 S/Key Login • • • Alice enters H 99(R). Host calculates H (H 99(R)). Compares to stored H 100(R). If they match, allows login And replaces old value with H 99(R). Alice crosses off H 99(R), enters H 98(R) next time. • S/Key uses MD 4 for H 19 April 2005 University of Virginia CS 588 35
S/Key Login • • • Alice enters H 99(R). Host calculates H (H 99(R)). Compares to stored H 100(R). If they match, allows login And replaces old value with H 99(R). Alice crosses off H 99(R), enters H 98(R) next time. • S/Key uses MD 4 for H 19 April 2005 University of Virginia CS 588 35
 S/Key > keyinit Adding evans: Reminder - Only use this method if you are directly connected. If you are using telnet or rlogin exit with no password and use keyinit -s. Enter secret password: test Again secret password: test ID evans s/key is 99 sh 69506 H 100(test) = sh 69506 What do I need to enter to log in? 19 April 2005 University of Virginia CS 588 36
S/Key > keyinit Adding evans: Reminder - Only use this method if you are directly connected. If you are using telnet or rlogin exit with no password and use keyinit -s. Enter secret password: test Again secret password: test ID evans s/key is 99 sh 69506 H 100(test) = sh 69506 What do I need to enter to log in? 19 April 2005 University of Virginia CS 588 36
 S/Key > key -n 100 99 sh 69506 Reminder - Do not use this program while logged in via telnet or rlogin. Enter secret password: test 0: KEEL FLED SUDS BOHR DUD SUP 1: TOW JOBS HOFF GIVE CHUB LAUD … 98: JEAN THEN WEAK ELAN SLOB GAS 99: MUG KNOB ACT ALOE REST TOO 19 April 2005 University of Virginia CS 588 37
S/Key > key -n 100 99 sh 69506 Reminder - Do not use this program while logged in via telnet or rlogin. Enter secret password: test 0: KEEL FLED SUDS BOHR DUD SUP 1: TOW JOBS HOFF GIVE CHUB LAUD … 98: JEAN THEN WEAK ELAN SLOB GAS 99: MUG KNOB ACT ALOE REST TOO 19 April 2005 University of Virginia CS 588 37
![Terminal Challenge-Response Login: evans EKUmamba[“evans”] Challenge x Challenge: 2357938523 Response: f(x) 19 April 2005 Terminal Challenge-Response Login: evans EKUmamba[“evans”] Challenge x Challenge: 2357938523 Response: f(x) 19 April 2005](https://present5.com/presentation/42dad49ab2ab4759400f4a83eb039710/image-38.jpg) Terminal Challenge-Response Login: evans EKUmamba[“evans”] Challenge x Challenge: 2357938523 Response: f(x) 19 April 2005 University of Virginia CS 588 38
Terminal Challenge-Response Login: evans EKUmamba[“evans”] Challenge x Challenge: 2357938523 Response: f(x) 19 April 2005 University of Virginia CS 588 38
 Challenge-Response Systems • Ask a question, see if the answer is right • Hard to make up questions only host and user can answer • Question: x? Answer: f(x). • What’s a good choice for f? – E (x, key known to both) – Still have to problem of storing the key • Secure. ID systems work like this – Challenge is current time (nothing to send) 19 April 2005 University of Virginia CS 588 39
Challenge-Response Systems • Ask a question, see if the answer is right • Hard to make up questions only host and user can answer • Question: x? Answer: f(x). • What’s a good choice for f? – E (x, key known to both) – Still have to problem of storing the key • Secure. ID systems work like this – Challenge is current time (nothing to send) 19 April 2005 University of Virginia CS 588 39
 Biometrics: “Something you are” • Unique(ish) properties of most humans: • Fingerprint – FBI’s Integrated Automated Fingerprint ID system has 48 Million • • Iris Hand shape Voice Gait, etc. 19 April 2005 University of Virginia CS 588 40
Biometrics: “Something you are” • Unique(ish) properties of most humans: • Fingerprint – FBI’s Integrated Automated Fingerprint ID system has 48 Million • • Iris Hand shape Voice Gait, etc. 19 April 2005 University of Virginia CS 588 40
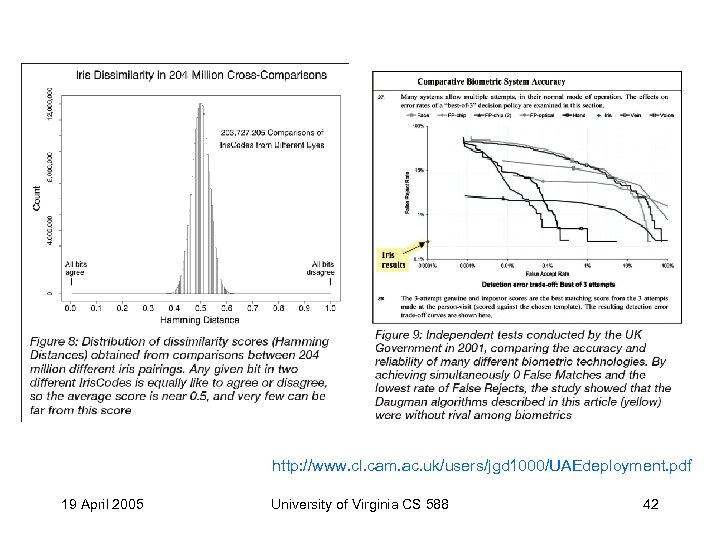
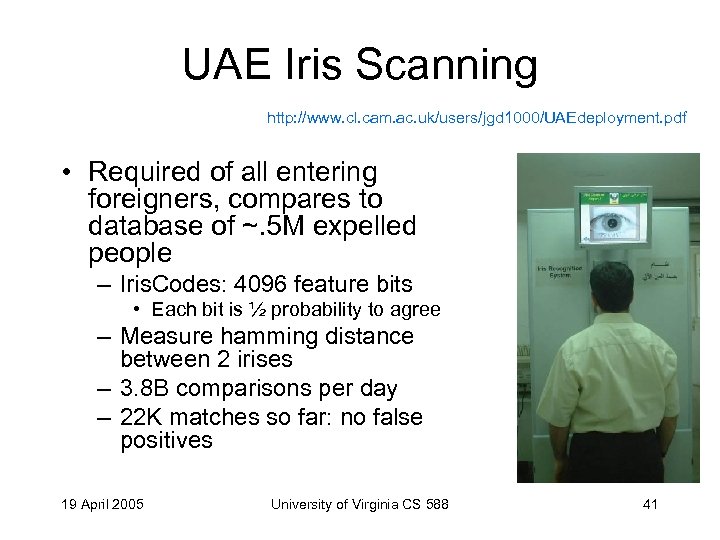 UAE Iris Scanning http: //www. cl. cam. ac. uk/users/jgd 1000/UAEdeployment. pdf • Required of all entering foreigners, compares to database of ~. 5 M expelled people – Iris. Codes: 4096 feature bits • Each bit is ½ probability to agree – Measure hamming distance between 2 irises – 3. 8 B comparisons per day – 22 K matches so far: no false positives 19 April 2005 University of Virginia CS 588 41
UAE Iris Scanning http: //www. cl. cam. ac. uk/users/jgd 1000/UAEdeployment. pdf • Required of all entering foreigners, compares to database of ~. 5 M expelled people – Iris. Codes: 4096 feature bits • Each bit is ½ probability to agree – Measure hamming distance between 2 irises – 3. 8 B comparisons per day – 22 K matches so far: no false positives 19 April 2005 University of Virginia CS 588 41
 http: //www. cl. cam. ac. uk/users/jgd 1000/UAEdeployment. pdf 19 April 2005 University of Virginia CS 588 42
http: //www. cl. cam. ac. uk/users/jgd 1000/UAEdeployment. pdf 19 April 2005 University of Virginia CS 588 42
 Problems with Biometrics • Fuzzy measures: need to set thresholds to have some false positives and negatives • Easily stolen: expert could obtain all of your fingerprints from this room after you leave – Non-expert can cut off your finger – Voiceprints can be stolen too (Sneakers) • Hard/impossible to change • Transmission link is still vulnerable 19 April 2005 University of Virginia CS 588 43
Problems with Biometrics • Fuzzy measures: need to set thresholds to have some false positives and negatives • Easily stolen: expert could obtain all of your fingerprints from this room after you leave – Non-expert can cut off your finger – Voiceprints can be stolen too (Sneakers) • Hard/impossible to change • Transmission link is still vulnerable 19 April 2005 University of Virginia CS 588 43
 Charge • Identify and authentication are hard problems • Passwords don’t work • Windows Longhorn may use two-factor authentication I believe that the time of password-only authentication is gone. We need to go to two-factor authentication. This is the only way to bring the level of trust business needs. Detlef Eckert, Microsoft’s Trustworthy Computing initiative 19 April 2005 University of Virginia CS 588 44
Charge • Identify and authentication are hard problems • Passwords don’t work • Windows Longhorn may use two-factor authentication I believe that the time of password-only authentication is gone. We need to go to two-factor authentication. This is the only way to bring the level of trust business needs. Detlef Eckert, Microsoft’s Trustworthy Computing initiative 19 April 2005 University of Virginia CS 588 44


