26cf48292273639ad3f8e7da941c377c.ppt
- Количество слайдов: 49

Lecture 10 Security of Distributed and Network Systems Ref. Chapter 10 and 13 1

Objectives Clarify the fundamental security problems that arise in distributed systems. n Show distributed system security has changed over the years becoming more ambitious in its goals. n Examine which system layer is best suited for implementing security mechanisms in a distributed system n Get an introduction of the design of network security protocols, using the basic Internet security protocols IPSC and SSL/TLS n Understand the principles of various firewall technologies n 2

Contents Introduction n Authentication n Kerberos n DSSA/SPX n Network Security n TCP/IP Security n SSL/TLS n Firewalls n 3

Introduction How do you authenticate a user? n What is the basis for access control? n User identity n The network address n The distributed services n Where do you authenticate a user? n Where do you make an access control decision? n 4

Delegation: A user may login at a local and then execute a program on a remote node. To obtain access to resources at the remote node, the program will need the relevant access rights. Typically, the program would be endowed with the access rights of the user and then run with these access rights on the remote node. n This mentions controlled invocation. n 5

Authentication requirements The goal is to provide the communication parties with some assurance about other’s true identity n Password sniffers might listen to network traffic and extract packets containing passwords and other security-relevant information. n 6

Kerberos authentication and key distribution service n Secures communication with servers on a local network Developed at MIT in the 1980 s to provide security across a large campus network > 5000 users n based on Needham - Schroeder protocol Standardized and now included in many operating systems n Internet RFC 1510, OSF DCE n BSD UNIX, Linux, Windows 2000, NT, XP, etc. n Available from MIT Kerberos server creates a shared secret key for any required server and sends it (encrypted) to the user's computer User's password is the initial secret shared with Kerberos n n 7 *

Kerberos Terminology Kerberos authentication server (KAS): authenticates principles at login and issues tickets, which is in general are valid for one login session and enable principals to obtain other tickets form ticket-granting servers. Also called KDC n Ticket granting servers (TGSs): issue tickets that give principals access to network services demanding authentication. n 8

Kerberos conventions n n n Ka : the secret cryptographic key of user A, derived from A’s password with a one-way algorithm; KAS has copy of Ka Ktgs : a secret key shared by TGS and KAS Kb : a secret key shared by the server B and TGS Ka, tgs: a session key created by KAS for use between A and TGS Ka, b: a session key created by TGS for use between A and B e. K(X): data packet X encrypted under key K; N 1, N 2 : nonce (random challenges) to prevent replay attacks L 1, L 2 : expiry date (lifetime) of tickets. T 1, T 2, T 3, T 4: creation time of tickets or authenticators Ticketa, tgs: ticket for A to use with TGS, created by KAS Ticketa, b: ticket for A to use with B, created by TGS 9
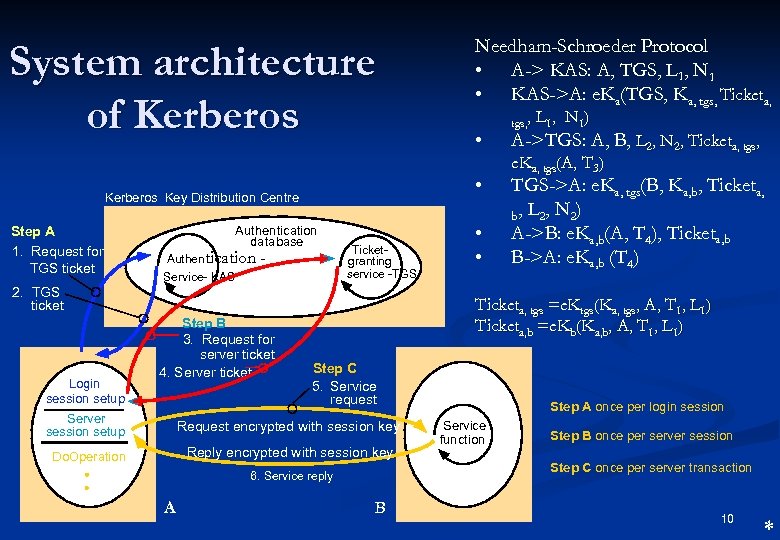
System architecture of Kerberos Authentication database Authentication Service- KAS Ticketgranting service -TGS 2. TGS ticket Login session setup Step B 3. Request for server ticket 4. Server ticket • • tgs, , tgs, L 1 , N 1 ) A->TGS: A, B, L 2, N 2, Ticketa, tgs, e. Ka, tgs(A, T 3) TGS->A: e. Ka, tgs(B, Ka, b, Ticketa, b, L 2, N 2) A->B: e. Ka, b(A, T 4), Ticketa, b B->A: e. Ka, b (T 4) Ticketa, tgs =e. Ktgs(Ka, tgs, A, T 1, L 1) Ticketa, b =e. Kb(Ka, b, A, T 1, L 1) Step C 5. Service request Server session setup Request encrypted with session key Do. Operation Reply encrypted with session key Step A once per login session Service function Step B once per server session Step C once per server transaction 6. Service reply A • • Kerberos Key Distribution Centre Step A 1. Request for TGS ticket Needham-Schroeder Protocol • A-> KAS: A, TGS, L 1, N 1 • KAS->A: e. Ka(TGS, Ka, tgs, Ticketa, B 10 *

Kerberized NFS n n Kerberos protocol is too costly to apply on each NFS operation Kerberos is used in the mount service: n n n For each file request: n n to authenticate the user's identity User's User. ID and Group. ID are stored at the server with the client's IP address User. ID and Group. ID are sent encrypted in the shared session key The User. ID and Group. ID must match those stored at the server IP addresses must also match This approach has some problems n n can't accommodate multiple users sharing the same client computer all remote filestores must be mounted each time a user logs in 11 *

Revocation Update the database so that the access rights are no longer available. n Next session, the principle is revoked. n The current ticket is valid until they expire. n Expire period trade-off: n Long: less security, more convenience for the principle n Short: more security, less convenience for the principle n 12

Realms KAS is the heart n Principals, Keys and access rights must be in the KAS or TGS n It is a centralized security system n A single security policy is enforced n It is relatively easy to check that the system set-up complies with the security policy and to implement changes n 13

Summary of Kerberos n n n n Timeliness of messages is checked by time stamps. Checking of time stamps allows for some clock skew. Servers have to be on-line. Session keys are generated by Kerberos servers. Kerberos does not address the delegation of privileges (tickets) Password guessing and password spoofing attacks are possible. Keys and tickets are held on the clients machine. It is important to distinguish the security of the protocol itself from the security of implementations of Kerberos. 14

DSSA/SPX n n n DSSA (Distributed system security architecture) is developed by DEC SPX (Sequenced Packet Exchange) is a part of DSSA The authentication in SPX n n n Credentials: name Certificates: binding name to public keys Authentication tokens. Certification authority (CA): issues public key certificates Certificate distribution center (CDC): stores the certificates issued by a CA. A certificate can be revoked by maintaining a certificate revocation list. 15

SPX conventions n n n n Sp : the private signature key of principle P Pa, Sa : the long-term public key and long-term private key of A P’a, S’a : the short-term public key and short-term private key of A Ka, b: a session key created by A for use between A and B in a symmetric encryption algorithm e. K(X): data packet X encrypted under key K s. K(X): digital signature of data packet X generated with key K T: a time stamp Lc, Lt : expiry date of a certificate or a ticket 16
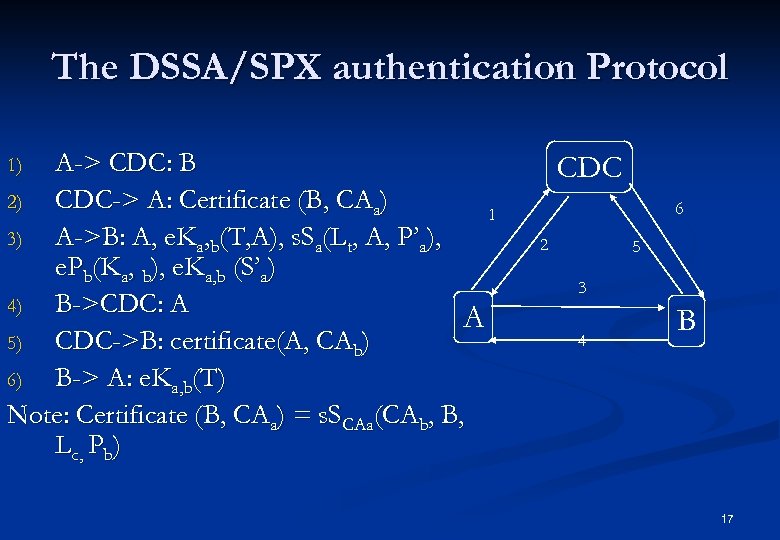
The DSSA/SPX authentication Protocol A-> CDC: B 2) CDC-> A: Certificate (B, CAa) 1 3) A->B: A, e. Ka, b(T, A), s. Sa(Lt, A, P’a), e. Pb(Ka, b), e. Ka, b (S’a) 4) B->CDC: A A 5) CDC->B: certificate(A, CAb) 6) B-> A: e. Ka, b(T) Note: Certificate (B, CAa) = s. SCAa(CAb, B, L c , P b) CDC 1) 6 2 5 3 4 B 17

Security API Security requirements in a DS often exceed mere authentication. n Different components in a DS will not necessarily use the same security mechanisms. n Users and application writers are not necessarily security experts. n 18
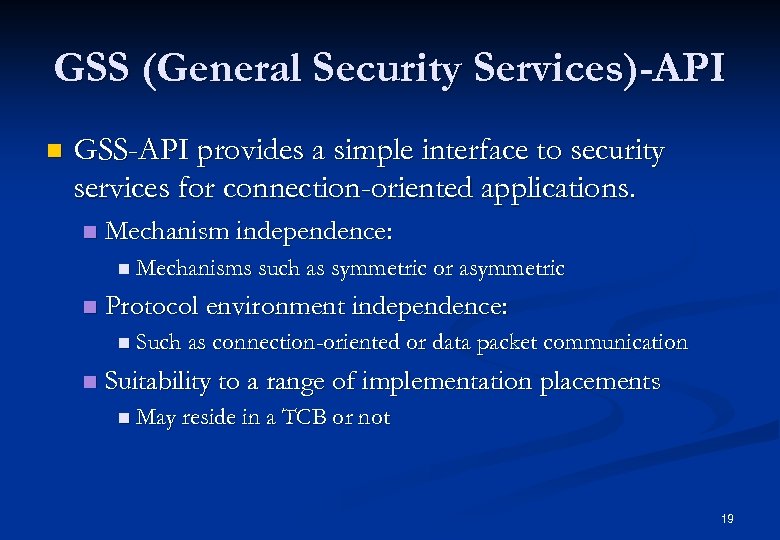
GSS (General Security Services)-API n GSS-API provides a simple interface to security services for connection-oriented applications. n Mechanism independence: n Mechanisms such as symmetric or asymmetric n Protocol environment independence: n Such as connection-oriented or data packet communication n Suitability to a range of implementation placements n May reside in a TCB or not 19
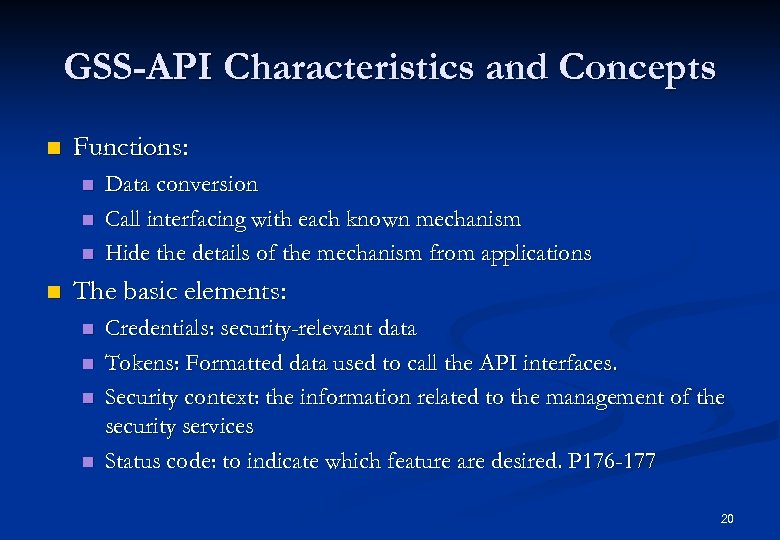
GSS-API Characteristics and Concepts n Functions: n n Data conversion Call interfacing with each known mechanism Hide the details of the mechanism from applications The basic elements: n n Credentials: security-relevant data Tokens: Formatted data used to call the API interfaces. Security context: the information related to the management of the security services Status code: to indicate which feature are desired. P 176 -177 20

GSS-API Interface Descriptions n Credential management calls n n Context-level calls n n To provide cryptographic integrity and confidentiality protection Support calls: n n Initiation, acceptance and deletion of contexts… Per-message calls n n Allow a principal to acquire and release credentials, and inquire about various credential information General housekeeping and support routines, such as freeing memory spaces, name comparison P 177 -178 21

API and security n Security services depend on: Proper implementation of relevant mechanisms n Proper security management n n Key generation n Key storage n Key transport n Key usage n Key management is entirely above the APIs 22
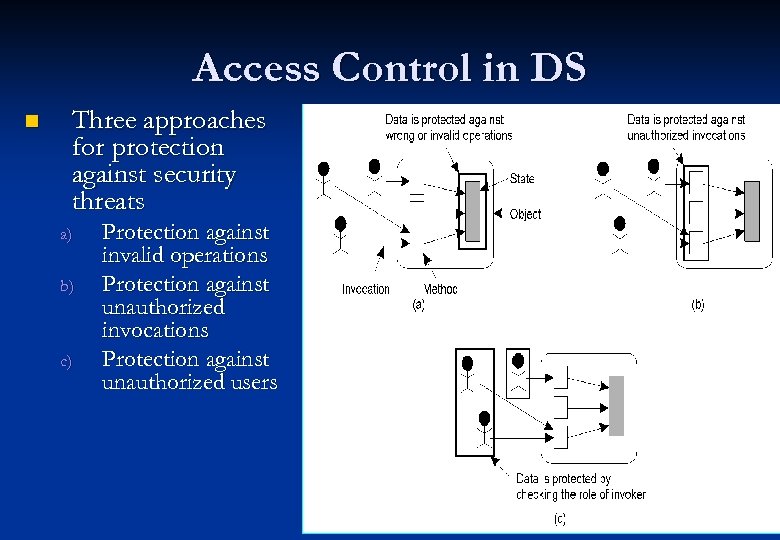
Access Control in DS n Three approaches for protection against security threats a) b) c) Protection against invalid operations Protection against unauthorized invocations Protection against unauthorized users 23

Summary for DS security n n It is essential to protect the resources, communication channels and interfaces of distributed systems and applications against attacks. This is achieved by the use of access control mechanisms and secure channels. Public-key and secret-key cryptography provide the basis for authentication and for secure communication. Kerberos are widely-used system components that support authenticated communication. 24 *

Network security Send and receive n Data Transportation n Sequence of signals n Resemble and present n Route n Loss and corruption of data n 25

Sniffing and spoofing n n A packet sniffer is a wire-tap devices that plugs into computer networks and eavesdrops on the network traffic. Like a telephone wiretap allows the FBI to listen in on other people's conversations, a "sniffing" program lets someone listen in on computer conversations. Web Spoofing is a security attack that allows an adversary to observe and modify all web pages sent to the victim's machine, and observe all information entered into forms by the victim. The attacker can observe and modify all web pages and form submissions, even when the browser's "secure connection" indicator is lit. The user sees no indication that anything is wrong. 26

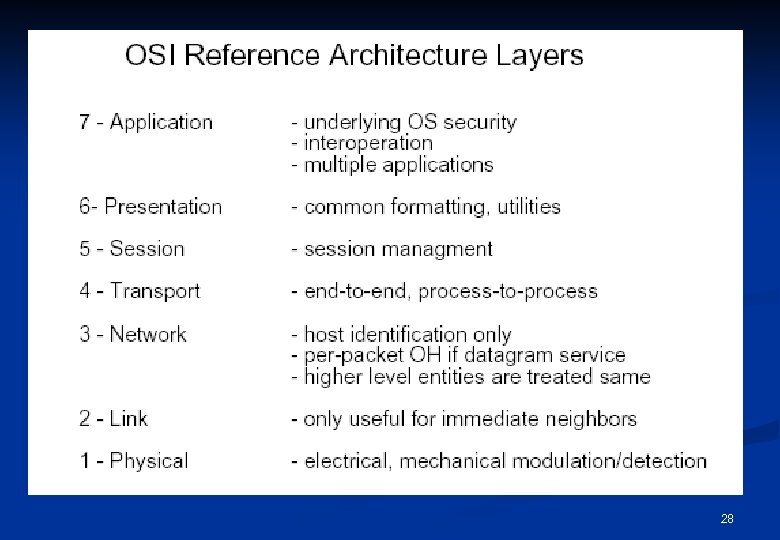
ISO/OSI Security Architecture Data confidentiality: n Data integrity n Data origin authentication: to corroborate the source n Peer-entity authentication: to verify the identity of a peer entity n Non-repudiation: to create evidence that data has been sent or received. (proof of origin and delivery) n 27
28
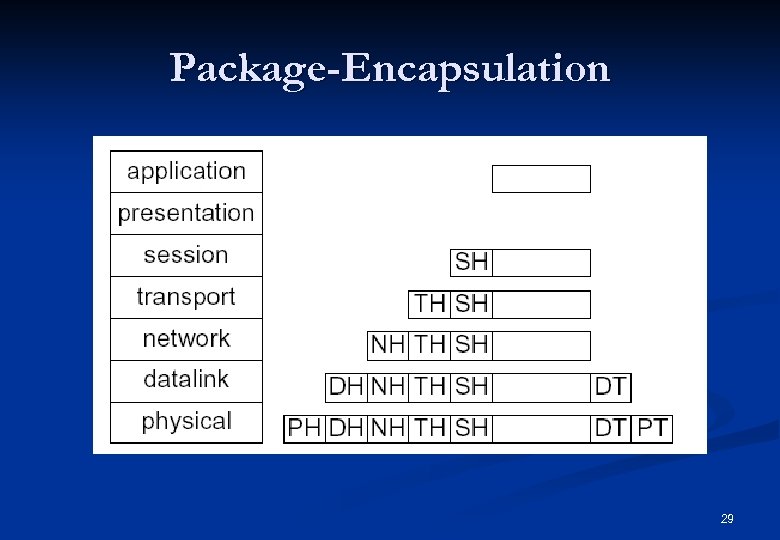
Package-Encapsulation 29

Network Security Issues Sharing n Complexity n Perimeter n Points of attack n Anonymity n Unknown path n 30
The Internet layers n Actual four layers Application layer: Telnet, FTP, HTTP, SMTP or SET n Transport layer: TCP, UDP n Internet layer: IP n Interface layers: the Network Interface Card (Physical) n 31

TCP/IP Security n n n IPSEC (IP Sec rity ) provides security for every one using urity u IP without changing the interface to IP. The IP authentication header (AH), covered in RFC 1826 The IP encapsulating security payload (ESP), covered in RFC 1827 n Transport mode: n n encrypts only the data portion (payload) of each packet, but leaves the header untouched. Tunnel mode: n encrypts both the header and the payload. On the receiving side, an IPSeccompliant device decrypts each packet. 32
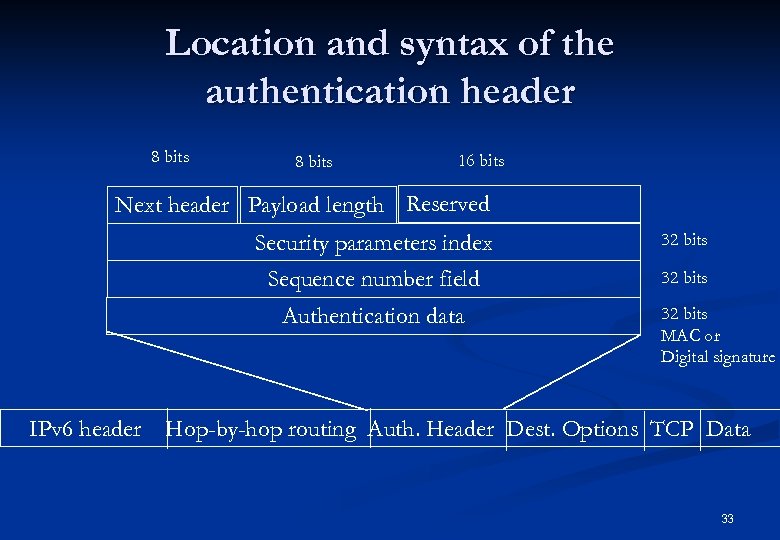
Location and syntax of the authentication header 8 bits 16 bits Next header Payload length Reserved Security parameters index 32 bits Sequence number field 32 bits Authentication data IPv 6 header 32 bits MAC or Digital signature Hop-by-hop routing Auth. Header Dest. Options TCP Data 33
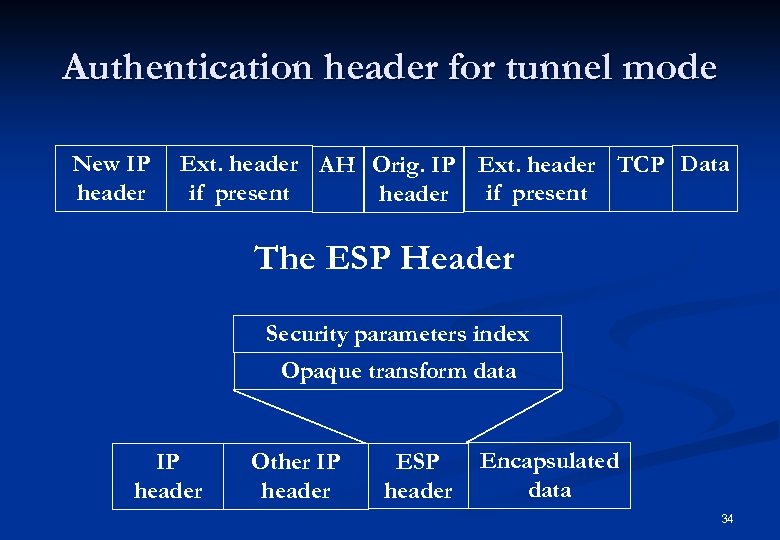
Authentication header for tunnel mode New IP header Ext. header AH Orig. IP Ext. header TCP Data if present header The ESP Header Security parameters index Opaque transform data IP header Other IP header ESP header Encapsulated data 34
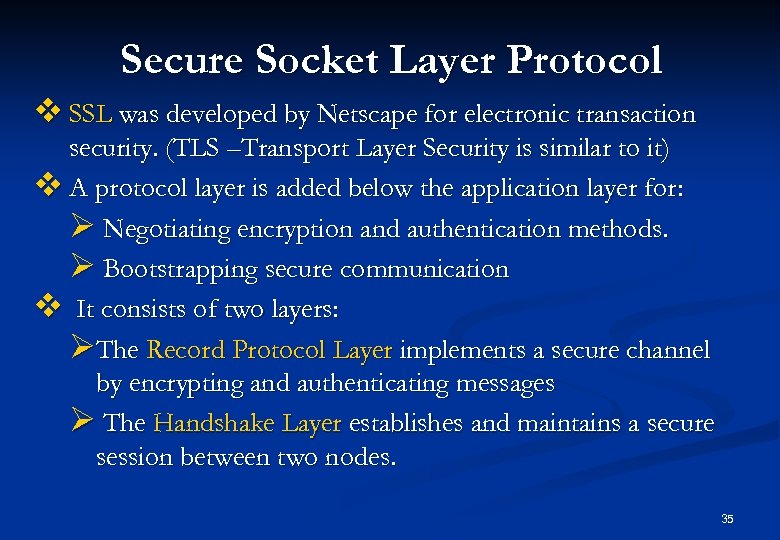
Secure Socket Layer Protocol v SSL was developed by Netscape for electronic transaction security. (TLS –Transport Layer Security is similar to it) v A protocol layer is added below the application layer for: Ø Negotiating encryption and authentication methods. Ø Bootstrapping secure communication v It consists of two layers: ØThe Record Protocol Layer implements a secure channel by encrypting and authenticating messages Ø The Handshake Layer establishes and maintains a secure session between two nodes. 35
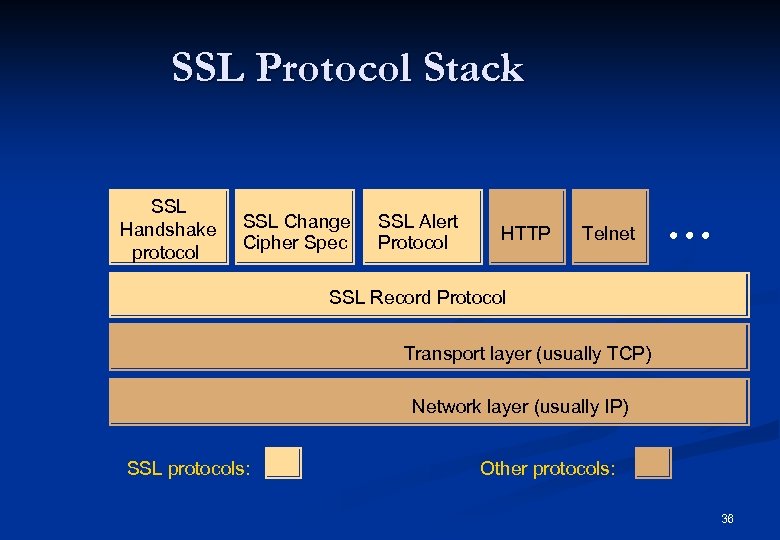
SSL Protocol Stack SSL Handshake protocol SSL Change Cipher Spec SSL Alert Protocol HTTP Telnet SSL Record Protocol Transport layer (usually TCP) Network layer (usually IP) SSL protocols: Other protocols: 36
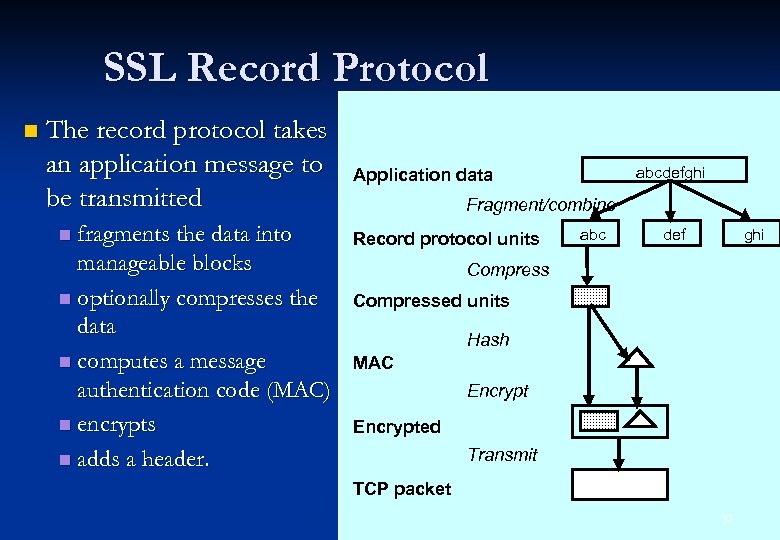
SSL Record Protocol n The record protocol takes an application message to be transmitted n fragments the data into manageable blocks n optionally compresses the data n computes a message authentication code (MAC) n encrypts n adds a header. abcdefghi Application data Fragment/combine Record protocol units abc def ghi Compressed units Hash MAC Encrypted Transmit TCP packet 37
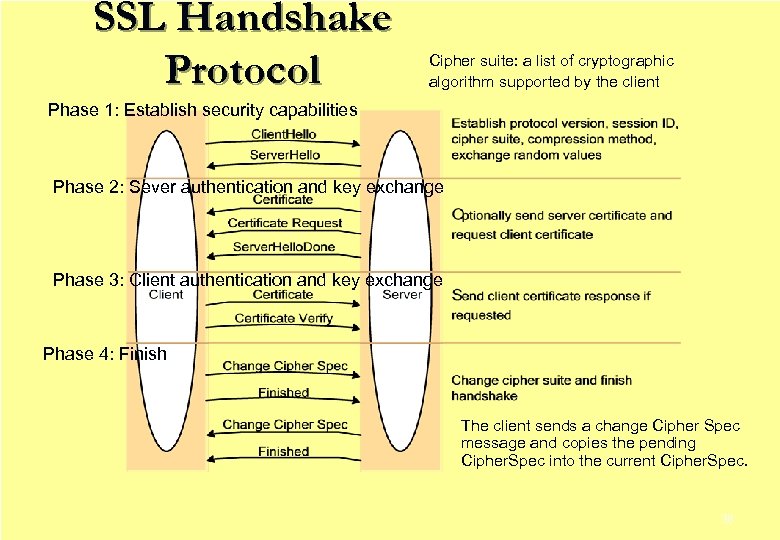
SSL Handshake Protocol Cipher suite: a list of cryptographic algorithm supported by the client Phase 1: Establish security capabilities Phase 2: Sever authentication and key exchange Phase 3: Client authentication and key exchange Phase 4: Finish The client sends a change Cipher Spec message and copies the pending Cipher. Spec into the current Cipher. Spec. 38
![An Example n M 1: n Client. Hello: n n Client. Random[28] Sugessted Cipher An Example n M 1: n Client. Hello: n n Client. Random[28] Sugessted Cipher](https://present5.com/presentation/26cf48292273639ad3f8e7da941c377c/image-39.jpg)
An Example n M 1: n Client. Hello: n n Client. Random[28] Sugessted Cipher Suites: n n n Suggested Compression Algorithm: none Server. Hello: n n Server. Random[28] Use Cipher Suite: n n n n n M 3: n n n A: Client. Key. Exchange: RSA_Encrypt B: Change. Cipher. Spec: NONE C: Finished: MD 5(M 1||M 2||M 3 A) SHA (M 1||M 2||M 3 A) M 4: n n A: Change. Cipher. Spec: NONE B: Finished: MD 5(M 1||M 2||M 3 A||M 3 C) SHA (M 1||M 2||M 3 A||M 3 C) TLS_RSA_WITH_IDEA_CBC_SHA Session ID: 0 x 00372 d 4 XS Certificate: n n TLS_RSA_WITH_IDEA_CBC_SHA TLS_RSA_WITH_DES_CBC_SHA TLS_RSA_EXPORT_WITH_DES 40_CBC_SHA n M 2: n n Subject: Public Key: Issuer: Server Done: None 39

Firewalls n n n Firewall: the general name for any security system protecting the boundary of an internal network. Bastion host: a computer system with strong security as it is exposed to the outside world. Tasks of a firewall: n n n AC based on sender or receiver addresses AC based on the service requested Hiding the internal network (topology, addresses, traffic) Virus checking on incoming messages Authentication based on source of traffic Logging of Internet activities. 40

Packet Filtering v Operates as a router and makes decisions as to whether or not to pass a packet based on its source/destination addresses. v v Destination addresses v Protocol v v Source addresses Connection The gateway on the outside LAN protects against incoming packets. The gateway on the inside LAN protects against outgoing packets. 41

Proxy Servers To implement policies based on user identities and hide information about the internal network n Another example of controlled invocation. n It intercepts the client’s request and decides whether it is permitted according to its security rules. n 42

Firewall Filtering v Firewall filtering can be done at diff. levels v. TCP gateway: checks all TCP connection requests and segment transmissions. TCP segments will be checked for correctness and may be routed to an application-level gateway for content checking. Application-level filtering (proxy gateway): inspects the content of incoming/outgoing messages. v v To prevent applets to be downloaded to the inside LAN, all Web traffic could be directed through a Web proxy gateway. The gateway accepts regular HTTP requests, but may discard certain requests/pages. 43
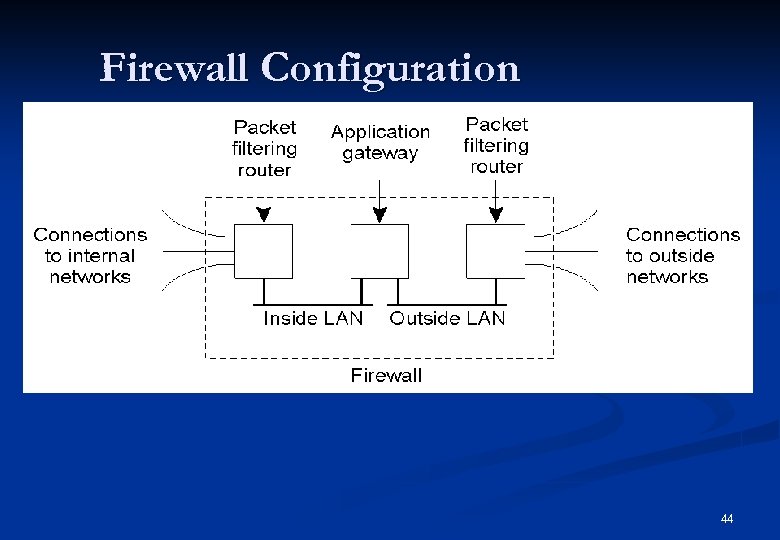
Firewall Configuration n A common implementation of a firewall. 44

Network Security Specialties More Intruders 45

Three Classes of Intruders n n n Masquerader – unauthorized user who penetrates a system exploiting a legitimate user’s account (outside) Misfeasor - legitimate user who makes unauthorized accesses or misuses his privileges (inside) Clandestine user - seizes supervisory control to evade auditing and access controls or suppress audit collection (inside|outside) 46

Intruders Intruder attacks range from benign to serious: n Benign intruders tolerable but consume resources n Difficult to know in advance the type of intruder n Really growing problem n n globalization the move to Client/Server architectures 47
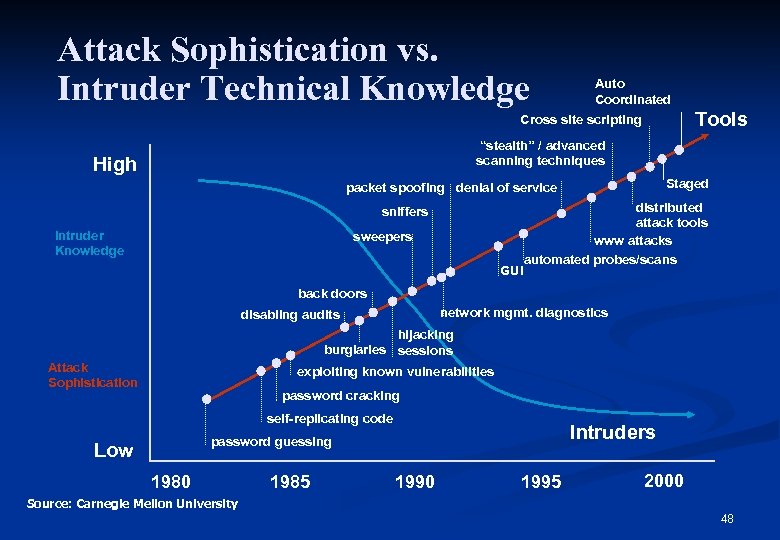
Attack Sophistication vs. Intruder Technical Knowledge Auto Coordinated Tools Cross site scripting “stealth” / advanced scanning techniques High Staged packet spoofing denial of service sniffers Intruder Knowledge sweepers GUI distributed attack tools www attacks automated probes/scans back doors network mgmt. diagnostics disabling audits hijacking burglaries sessions Attack Sophistication exploiting known vulnerabilities password cracking self-replicating code Intruders password guessing Low 1980 1985 1990 1995 2000 Source: Carnegie Mellon University 48

Summary Introduction n Authentication n Kerberos n DSSA/SPX n Network Security n TCP/IP Security n SSL/TLS n Firewalls n 49
26cf48292273639ad3f8e7da941c377c.ppt