ac50994b453aba8a63b20400df1d9bd1.ppt
- Количество слайдов: 52
 Lec 2: Internet Connectivity: Packet Switching ECE 5650 Taxonomy 1 -1
Lec 2: Internet Connectivity: Packet Switching ECE 5650 Taxonomy 1 -1
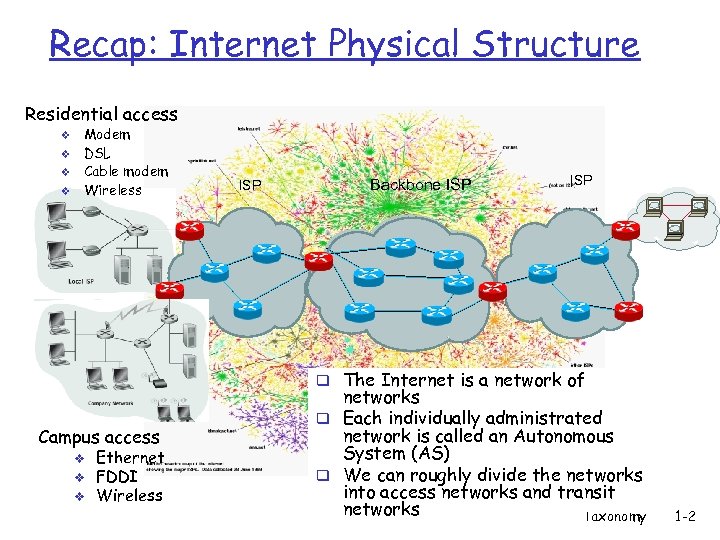 Recap: Internet Physical Structure Residential access v v Modem DSL Cable modem Wireless ISP Backbone ISP q The Internet is a network of Campus access v v v Ethernet FDDI Wireless networks q Each individually administrated network is called an Autonomous System (AS) q We can roughly divide the networks into access networks and transit networks Taxonomy 1 -2
Recap: Internet Physical Structure Residential access v v Modem DSL Cable modem Wireless ISP Backbone ISP q The Internet is a network of Campus access v v v Ethernet FDDI Wireless networks q Each individually administrated network is called an Autonomous System (AS) q We can roughly divide the networks into access networks and transit networks Taxonomy 1 -2
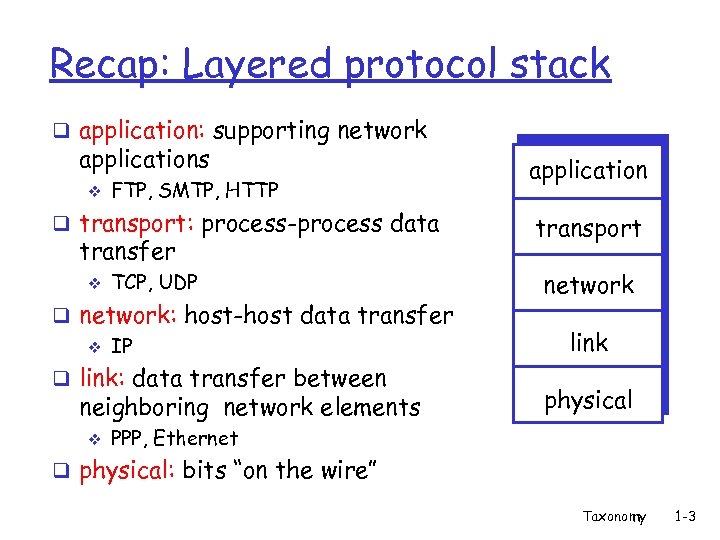 Recap: Layered protocol stack q application: supporting network applications v FTP, SMTP, HTTP q transport: process-process data transfer v TCP, UDP q network: host-host data transfer v IP q link: data transfer between neighboring network elements v application transport network link physical PPP, Ethernet q physical: bits “on the wire” Taxonomy 1 -3
Recap: Layered protocol stack q application: supporting network applications v FTP, SMTP, HTTP q transport: process-process data transfer v TCP, UDP q network: host-host data transfer v IP q link: data transfer between neighboring network elements v application transport network link physical PPP, Ethernet q physical: bits “on the wire” Taxonomy 1 -3
 Recap: Histroy q 60’s: packet switching theory, ARPNET v ARPANET was an attempt to investigate the feasibility of packet switching • ARPANET was built on top of telephone networks q 70’s: internetworking, Ethernet q 80’s: applications: email, ftp, telnet, etc q 90’s: web killer appl and commercialization v totally distributed, autonomous systems roughly hierarchical where ISPs interconnect at Po. P and NAP q Today: As important as utility services v backbone speed: about 10 Gbps v number of hosts: about 400 millions Taxonomy 1 -4
Recap: Histroy q 60’s: packet switching theory, ARPNET v ARPANET was an attempt to investigate the feasibility of packet switching • ARPANET was built on top of telephone networks q 70’s: internetworking, Ethernet q 80’s: applications: email, ftp, telnet, etc q 90’s: web killer appl and commercialization v totally distributed, autonomous systems roughly hierarchical where ISPs interconnect at Po. P and NAP q Today: As important as utility services v backbone speed: about 10 Gbps v number of hosts: about 400 millions Taxonomy 1 -4
 Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Delay, Lose, Throughtput q Security Taxonomy 1 -5
Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Delay, Lose, Throughtput q Security Taxonomy 1 -5
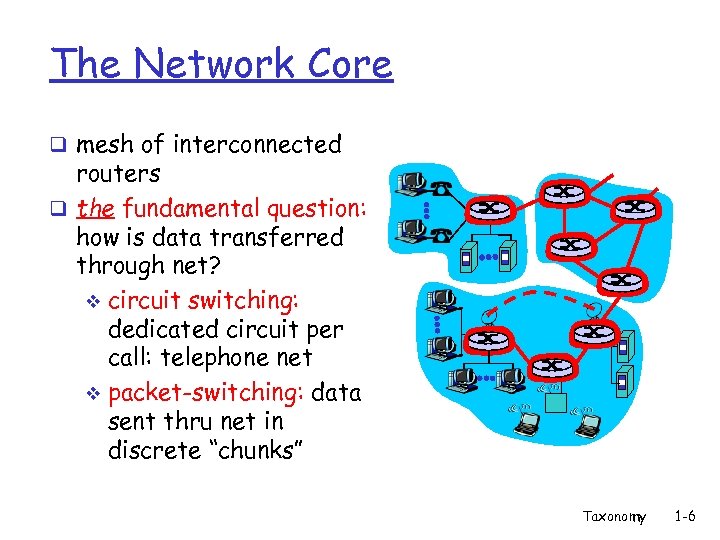 The Network Core q mesh of interconnected routers q the fundamental question: how is data transferred through net? v circuit switching: dedicated circuit per call: telephone net v packet-switching: data sent thru net in discrete “chunks” Taxonomy 1 -6
The Network Core q mesh of interconnected routers q the fundamental question: how is data transferred through net? v circuit switching: dedicated circuit per call: telephone net v packet-switching: data sent thru net in discrete “chunks” Taxonomy 1 -6
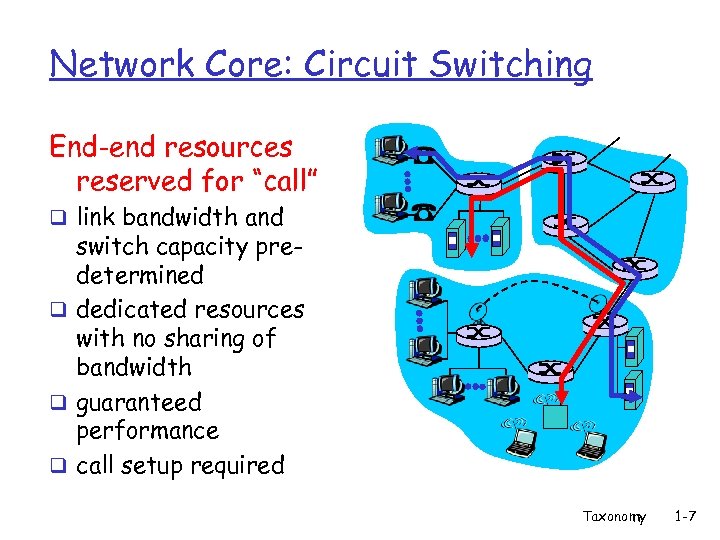 Network Core: Circuit Switching End-end resources reserved for “call” q link bandwidth and switch capacity predetermined q dedicated resources with no sharing of bandwidth q guaranteed performance q call setup required Taxonomy 1 -7
Network Core: Circuit Switching End-end resources reserved for “call” q link bandwidth and switch capacity predetermined q dedicated resources with no sharing of bandwidth q guaranteed performance q call setup required Taxonomy 1 -7
 Network Core: Circuit Switching network resources (e. g. , bandwidth) divided into “pieces” q pieces allocated to calls q dividing link bandwidth into “pieces” v frequency division v time division q resource piece idle if not used by owning call (no sharing) Taxonomy 1 -8
Network Core: Circuit Switching network resources (e. g. , bandwidth) divided into “pieces” q pieces allocated to calls q dividing link bandwidth into “pieces” v frequency division v time division q resource piece idle if not used by owning call (no sharing) Taxonomy 1 -8
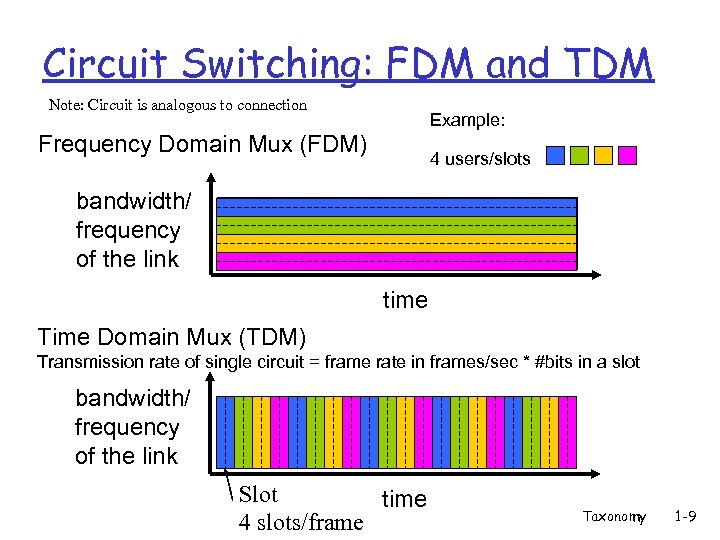 Circuit Switching: FDM and TDM Note: Circuit is analogous to connection Example: Frequency Domain Mux (FDM) 4 users/slots bandwidth/ frequency of the link time Time Domain Mux (TDM) Transmission rate of single circuit = frame rate in frames/sec * #bits in a slot bandwidth/ frequency of the link Slot time 4 slots/frame Taxonomy 1 -9
Circuit Switching: FDM and TDM Note: Circuit is analogous to connection Example: Frequency Domain Mux (FDM) 4 users/slots bandwidth/ frequency of the link time Time Domain Mux (TDM) Transmission rate of single circuit = frame rate in frames/sec * #bits in a slot bandwidth/ frequency of the link Slot time 4 slots/frame Taxonomy 1 -9
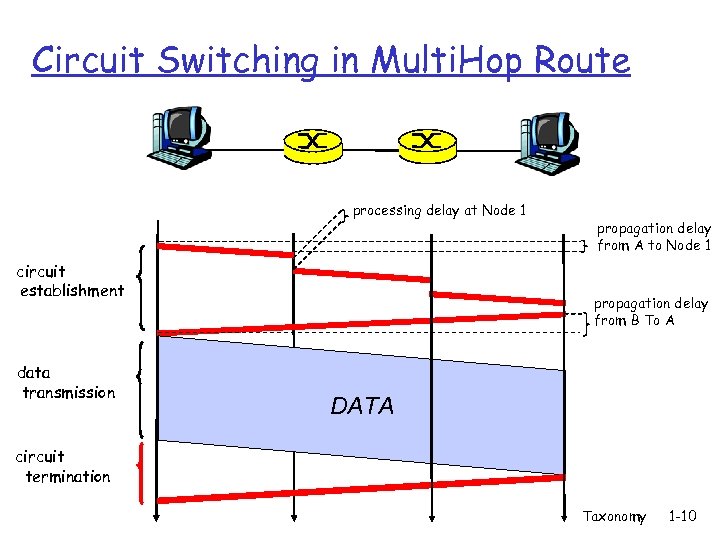 Circuit Switching in Multi. Hop Route processing delay at Node 1 circuit establishment data transmission propagation delay from A to Node 1 propagation delay from B To A DATA circuit termination Taxonomy 1 -10
Circuit Switching in Multi. Hop Route processing delay at Node 1 circuit establishment data transmission propagation delay from A to Node 1 propagation delay from B To A DATA circuit termination Taxonomy 1 -10
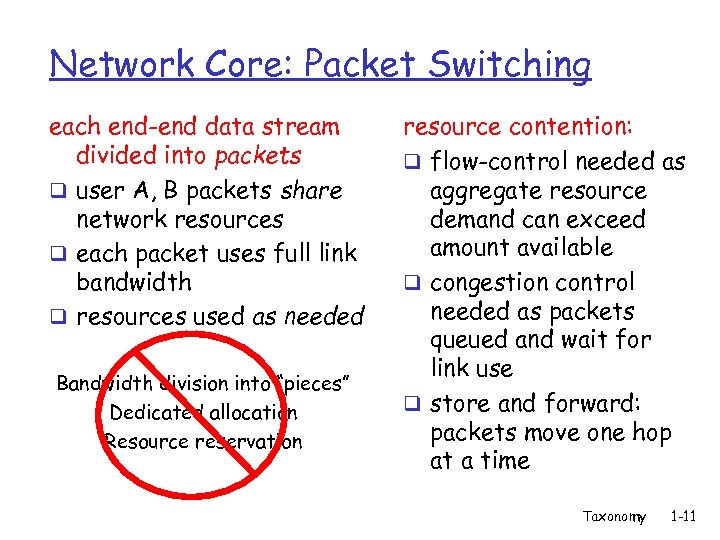 Network Core: Packet Switching each end-end data stream divided into packets q user A, B packets share network resources q each packet uses full link bandwidth q resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation resource contention: q flow-control needed as aggregate resource demand can exceed amount available q congestion control needed as packets queued and wait for link use q store and forward: packets move one hop at a time Taxonomy 1 -11
Network Core: Packet Switching each end-end data stream divided into packets q user A, B packets share network resources q each packet uses full link bandwidth q resources used as needed Bandwidth division into “pieces” Dedicated allocation Resource reservation resource contention: q flow-control needed as aggregate resource demand can exceed amount available q congestion control needed as packets queued and wait for link use q store and forward: packets move one hop at a time Taxonomy 1 -11
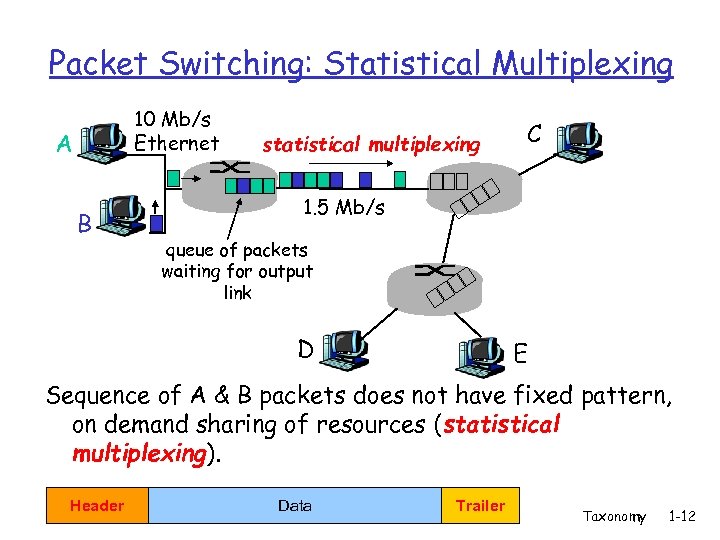 Packet Switching: Statistical Multiplexing 10 Mb/s Ethernet A B statistical multiplexing C 1. 5 Mb/s queue of packets waiting for output link D E Sequence of A & B packets does not have fixed pattern, on demand sharing of resources (statistical multiplexing). Header Data Trailer Taxonomy 1 -12
Packet Switching: Statistical Multiplexing 10 Mb/s Ethernet A B statistical multiplexing C 1. 5 Mb/s queue of packets waiting for output link D E Sequence of A & B packets does not have fixed pattern, on demand sharing of resources (statistical multiplexing). Header Data Trailer Taxonomy 1 -12
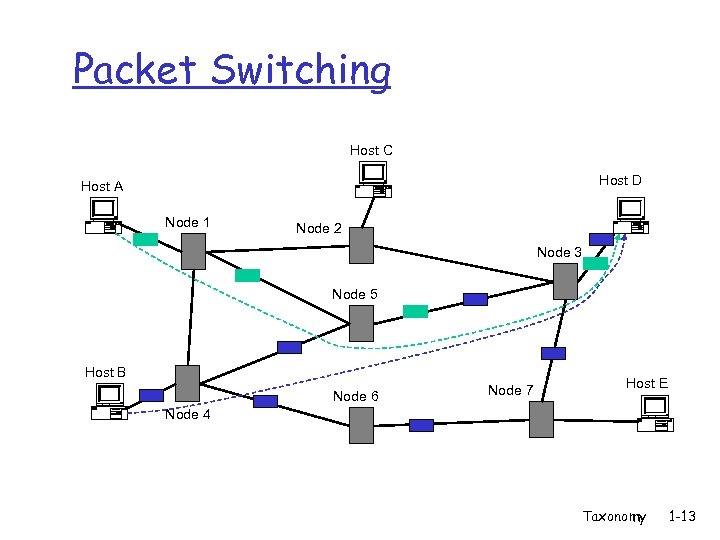 Packet Switching Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 7 Host E Node 4 Taxonomy 1 -13
Packet Switching Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 7 Host E Node 4 Taxonomy 1 -13
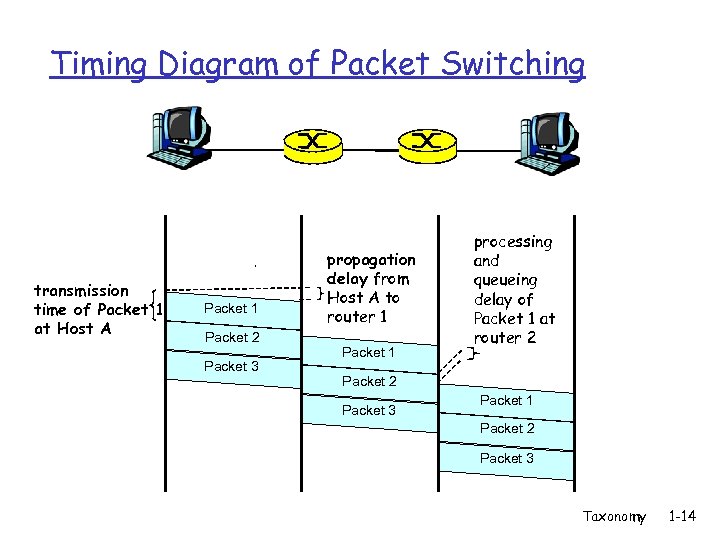 Timing Diagram of Packet Switching transmission time of Packet 1 at Host A Packet 1 Packet 2 Packet 3 propagation delay from Host A to router 1 Packet 1 processing and queueing delay of Packet 1 at router 2 Packet 3 Packet 1 Packet 2 Packet 3 Taxonomy 1 -14
Timing Diagram of Packet Switching transmission time of Packet 1 at Host A Packet 1 Packet 2 Packet 3 propagation delay from Host A to router 1 Packet 1 processing and queueing delay of Packet 1 at router 2 Packet 3 Packet 1 Packet 2 Packet 3 Taxonomy 1 -14
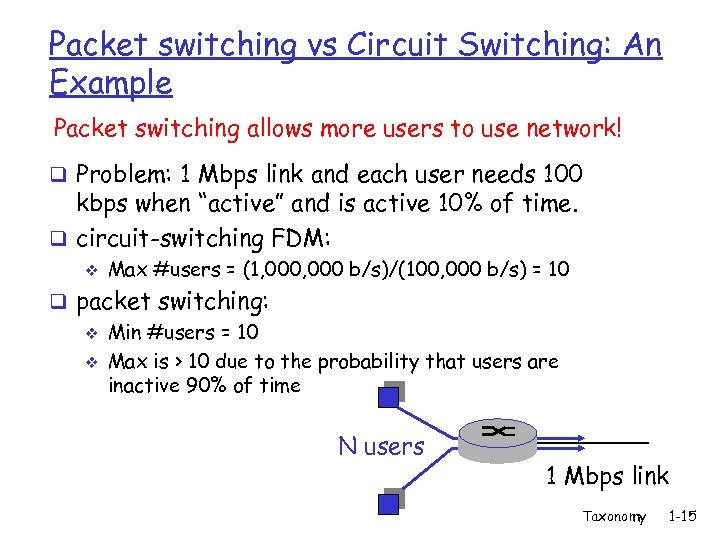 Packet switching vs Circuit Switching: An Example Packet switching allows more users to use network! q Problem: 1 Mbps link and each user needs 100 kbps when “active” and is active 10% of time. q circuit-switching FDM: v Max #users = (1, 000 b/s)/(100, 000 b/s) = 10 q packet switching: v Min #users = 10 v Max is > 10 due to the probability that users are inactive 90% of time N users 1 Mbps link Taxonomy 1 -15
Packet switching vs Circuit Switching: An Example Packet switching allows more users to use network! q Problem: 1 Mbps link and each user needs 100 kbps when “active” and is active 10% of time. q circuit-switching FDM: v Max #users = (1, 000 b/s)/(100, 000 b/s) = 10 q packet switching: v Min #users = 10 v Max is > 10 due to the probability that users are inactive 90% of time N users 1 Mbps link Taxonomy 1 -15
 Packet Switching vs Circuit Switching Is packet switching a “slam dunk winner? ” q Great for bursty data resource sharing v simpler, no call setup q Excessive congestion: packet delay and loss v protocols needed for reliable data transfer, congestion control q Q: How to provide circuit-like behavior? v bandwidth guarantees needed for audio/video apps v still an unsolved problem v Taxonomy 1 -16
Packet Switching vs Circuit Switching Is packet switching a “slam dunk winner? ” q Great for bursty data resource sharing v simpler, no call setup q Excessive congestion: packet delay and loss v protocols needed for reliable data transfer, congestion control q Q: How to provide circuit-like behavior? v bandwidth guarantees needed for audio/video apps v still an unsolved problem v Taxonomy 1 -16
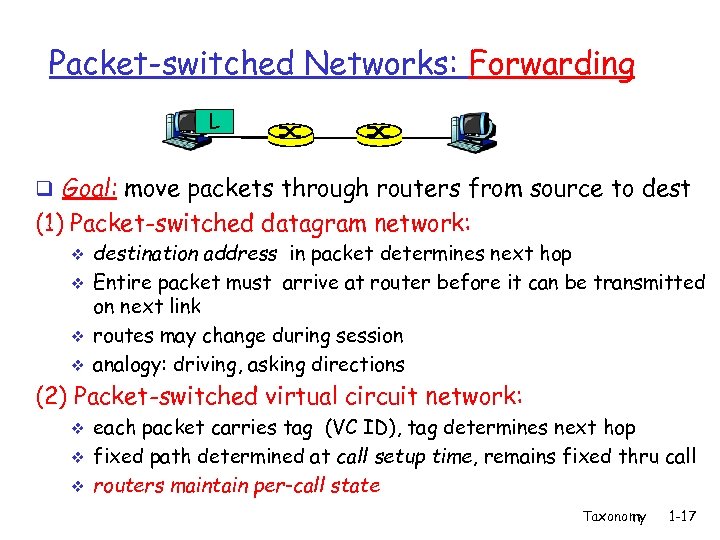 Packet-switched Networks: Forwarding L q Goal: move packets through routers from source to dest (1) Packet-switched datagram network: v v destination address in packet determines next hop Entire packet must arrive at router before it can be transmitted on next link routes may change during session analogy: driving, asking directions (2) Packet-switched virtual circuit network: v v v each packet carries tag (VC ID), tag determines next hop fixed path determined at call setup time, remains fixed thru call routers maintain per-call state Taxonomy 1 -17
Packet-switched Networks: Forwarding L q Goal: move packets through routers from source to dest (1) Packet-switched datagram network: v v destination address in packet determines next hop Entire packet must arrive at router before it can be transmitted on next link routes may change during session analogy: driving, asking directions (2) Packet-switched virtual circuit network: v v v each packet carries tag (VC ID), tag determines next hop fixed path determined at call setup time, remains fixed thru call routers maintain per-call state Taxonomy 1 -17
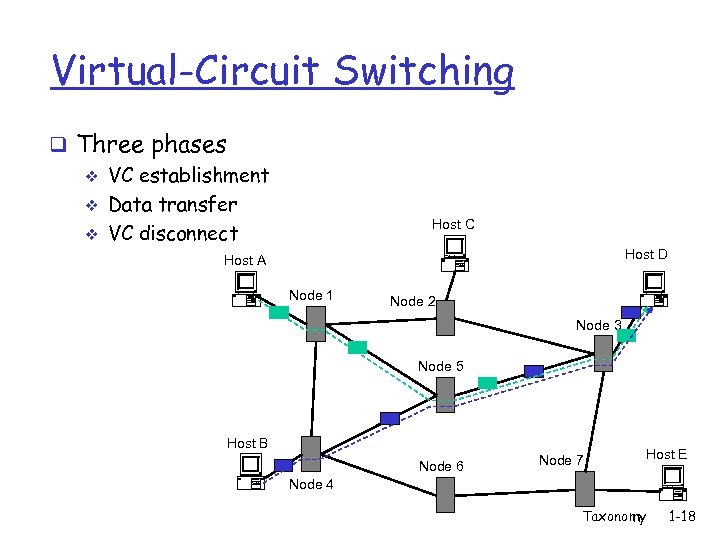 Virtual-Circuit Switching q Three phases v VC establishment v Data transfer v VC disconnect Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 7 Host E Node 4 Taxonomy 1 -18
Virtual-Circuit Switching q Three phases v VC establishment v Data transfer v VC disconnect Host C Host D Host A Node 1 Node 2 Node 3 Node 5 Host B Node 6 Node 7 Host E Node 4 Taxonomy 1 -18
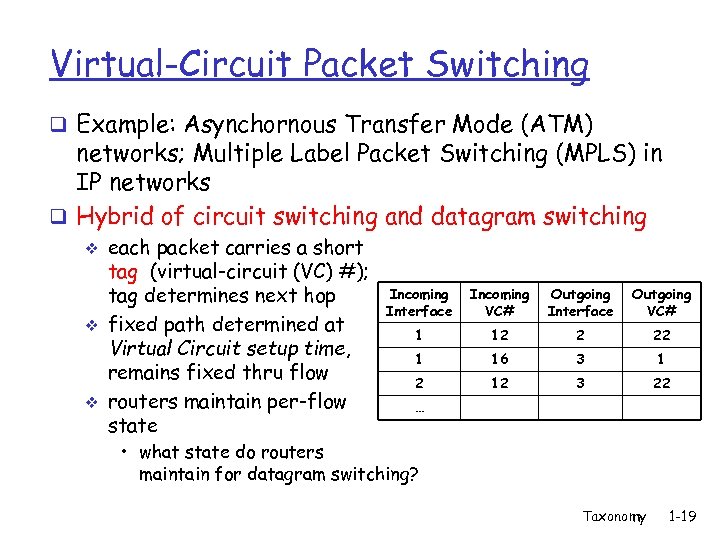 Virtual-Circuit Packet Switching q Example: Asynchornous Transfer Mode (ATM) networks; Multiple Label Packet Switching (MPLS) in IP networks q Hybrid of circuit switching and datagram switching v v v each packet carries a short tag (virtual-circuit (VC) #); tag determines next hop fixed path determined at Virtual Circuit setup time, remains fixed thru flow routers maintain per-flow state Incoming Interface Incoming VC# Outgoing Interface Outgoing VC# 1 12 2 22 1 16 3 1 2 12 3 22 … • what state do routers maintain for datagram switching? Taxonomy 1 -19
Virtual-Circuit Packet Switching q Example: Asynchornous Transfer Mode (ATM) networks; Multiple Label Packet Switching (MPLS) in IP networks q Hybrid of circuit switching and datagram switching v v v each packet carries a short tag (virtual-circuit (VC) #); tag determines next hop fixed path determined at Virtual Circuit setup time, remains fixed thru flow routers maintain per-flow state Incoming Interface Incoming VC# Outgoing Interface Outgoing VC# 1 12 2 22 1 16 3 1 2 12 3 22 … • what state do routers maintain for datagram switching? Taxonomy 1 -19
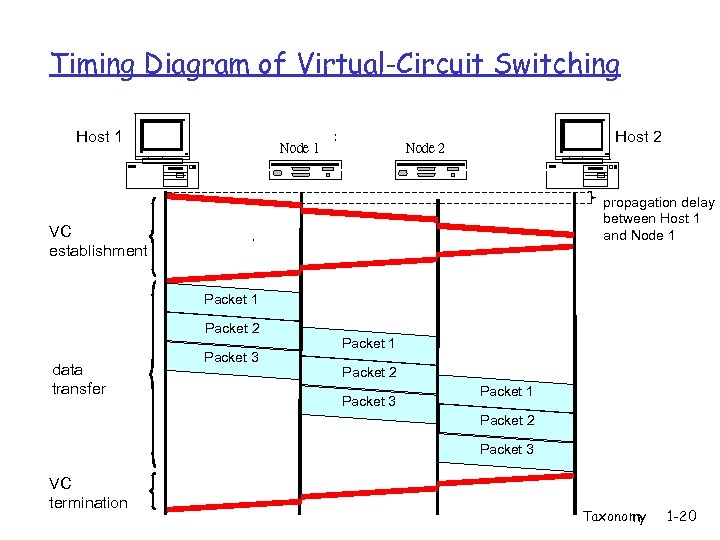 Timing Diagram of Virtual-Circuit Switching Host 1 Node 1 Host 2 Node 2 propagation delay between Host 1 and Node 1 VC establishment Packet 1 Packet 2 data transfer Packet 3 Packet 1 Packet 2 Packet 3 VC termination Taxonomy 1 -20
Timing Diagram of Virtual-Circuit Switching Host 1 Node 1 Host 2 Node 2 propagation delay between Host 1 and Node 1 VC establishment Packet 1 Packet 2 data transfer Packet 3 Packet 1 Packet 2 Packet 3 VC termination Taxonomy 1 -20
 Datagram Switching vs. Virtual Circuit Switching q What are the benefits of datagram switching over virtual circuit switching? q What are the benefits of virtual circuit switching over datagram switching? Taxonomy 1 -21
Datagram Switching vs. Virtual Circuit Switching q What are the benefits of datagram switching over virtual circuit switching? q What are the benefits of virtual circuit switching over datagram switching? Taxonomy 1 -21
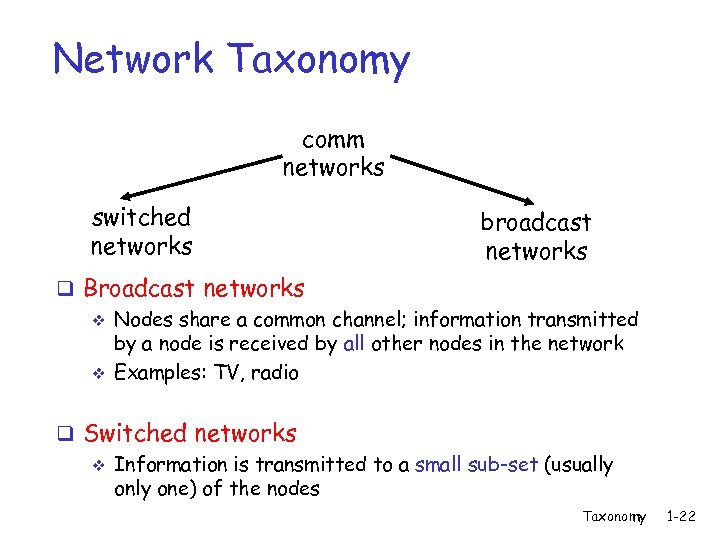 Network Taxonomy comm networks switched networks broadcast networks q Broadcast networks v Nodes share a common channel; information transmitted by a node is received by all other nodes in the network v Examples: TV, radio q Switched networks v Information is transmitted to a small sub-set (usually one) of the nodes Taxonomy 1 -22
Network Taxonomy comm networks switched networks broadcast networks q Broadcast networks v Nodes share a common channel; information transmitted by a node is received by all other nodes in the network v Examples: TV, radio q Switched networks v Information is transmitted to a small sub-set (usually one) of the nodes Taxonomy 1 -22
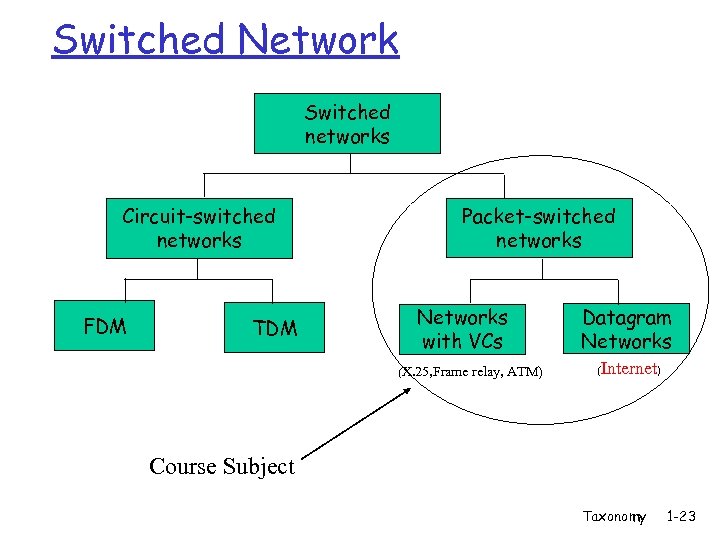 Switched Network Switched networks Circuit-switched networks FDM TDM Packet-switched networks Networks with VCs (X. 25, Frame relay, ATM) Datagram Networks (Internet) Course Subject Taxonomy 1 -23
Switched Network Switched networks Circuit-switched networks FDM TDM Packet-switched networks Networks with VCs (X. 25, Frame relay, ATM) Datagram Networks (Internet) Course Subject Taxonomy 1 -23
 Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Delay: v Loss v Throughput q Security Taxonomy 1 -24
Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Delay: v Loss v Throughput q Security Taxonomy 1 -24
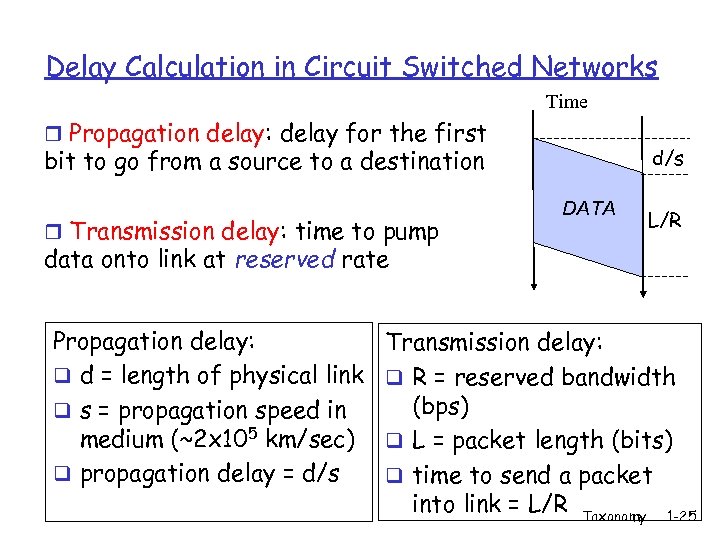 Delay Calculation in Circuit Switched Networks Time r Propagation delay: delay for the first d/s bit to go from a source to a destination r Transmission delay: time to pump DATA L/R data onto link at reserved rate Propagation delay: q d = length of physical link q s = propagation speed in medium (~2 x 105 km/sec) q propagation delay = d/s Transmission delay: q R = reserved bandwidth (bps) q L = packet length (bits) q time to send a packet into link = L/R Taxonomy 1 -25
Delay Calculation in Circuit Switched Networks Time r Propagation delay: delay for the first d/s bit to go from a source to a destination r Transmission delay: time to pump DATA L/R data onto link at reserved rate Propagation delay: q d = length of physical link q s = propagation speed in medium (~2 x 105 km/sec) q propagation delay = d/s Transmission delay: q R = reserved bandwidth (bps) q L = packet length (bits) q time to send a packet into link = L/R Taxonomy 1 -25
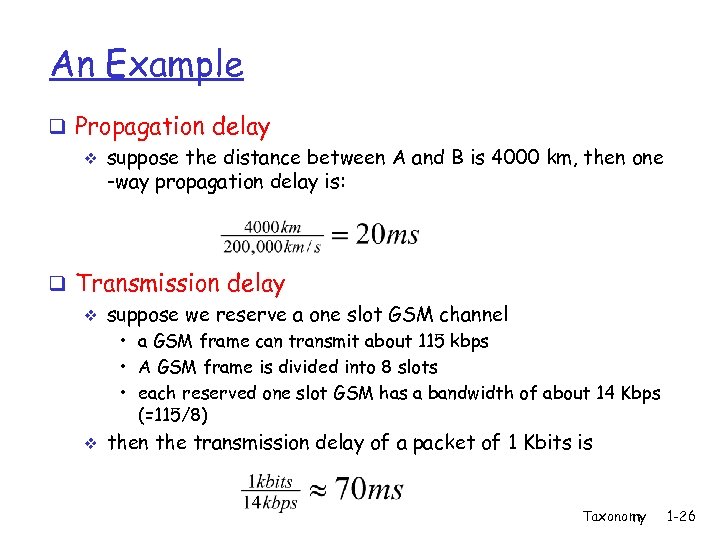 An Example q Propagation delay v suppose the distance between A and B is 4000 km, then one -way propagation delay is: q Transmission delay v suppose we reserve a one slot GSM channel • a GSM frame can transmit about 115 kbps • A GSM frame is divided into 8 slots • each reserved one slot GSM has a bandwidth of about 14 Kbps (=115/8) v then the transmission delay of a packet of 1 Kbits is Taxonomy 1 -26
An Example q Propagation delay v suppose the distance between A and B is 4000 km, then one -way propagation delay is: q Transmission delay v suppose we reserve a one slot GSM channel • a GSM frame can transmit about 115 kbps • A GSM frame is divided into 8 slots • each reserved one slot GSM has a bandwidth of about 14 Kbps (=115/8) v then the transmission delay of a packet of 1 Kbits is Taxonomy 1 -26
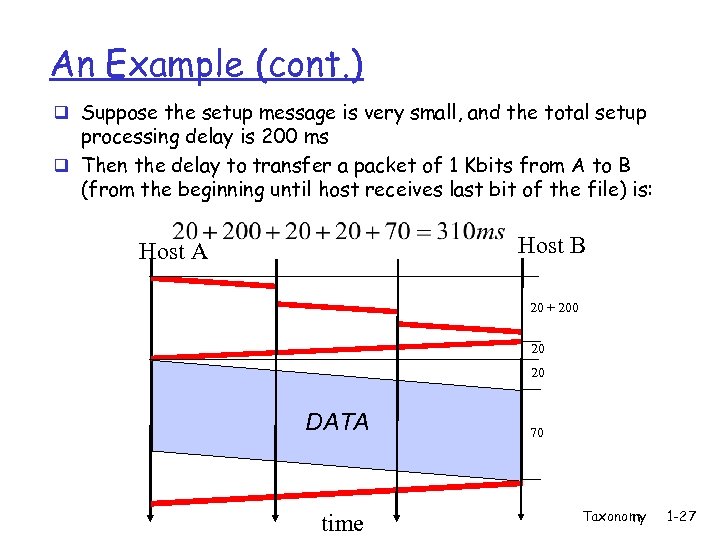 An Example (cont. ) q Suppose the setup message is very small, and the total setup processing delay is 200 ms q Then the delay to transfer a packet of 1 Kbits from A to B (from the beginning until host receives last bit of the file) is: Host B Host A 20 + 200 20 20 DATA time 70 Taxonomy 1 -27
An Example (cont. ) q Suppose the setup message is very small, and the total setup processing delay is 200 ms q Then the delay to transfer a packet of 1 Kbits from A to B (from the beginning until host receives last bit of the file) is: Host B Host A 20 + 200 20 20 DATA time 70 Taxonomy 1 -27
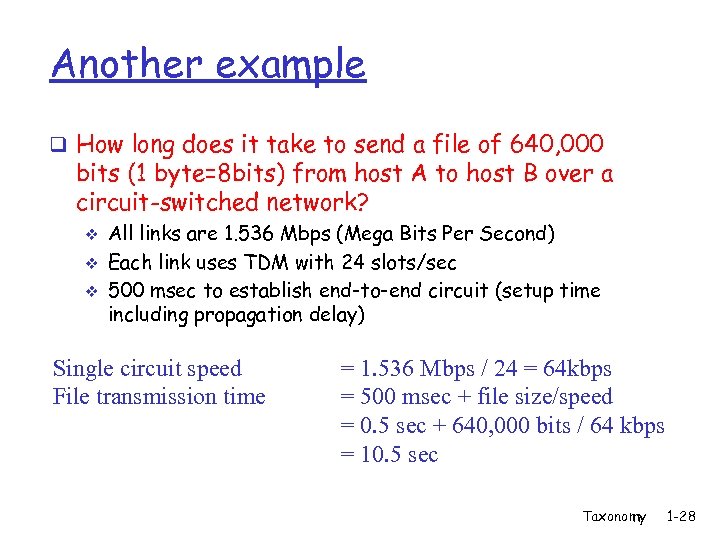 Another example q How long does it take to send a file of 640, 000 bits (1 byte=8 bits) from host A to host B over a circuit-switched network? v v v All links are 1. 536 Mbps (Mega Bits Per Second) Each link uses TDM with 24 slots/sec 500 msec to establish end-to-end circuit (setup time including propagation delay) Single circuit speed File transmission time = 1. 536 Mbps / 24 = 64 kbps = 500 msec + file size/speed = 0. 5 sec + 640, 000 bits / 64 kbps = 10. 5 sec Taxonomy 1 -28
Another example q How long does it take to send a file of 640, 000 bits (1 byte=8 bits) from host A to host B over a circuit-switched network? v v v All links are 1. 536 Mbps (Mega Bits Per Second) Each link uses TDM with 24 slots/sec 500 msec to establish end-to-end circuit (setup time including propagation delay) Single circuit speed File transmission time = 1. 536 Mbps / 24 = 64 kbps = 500 msec + file size/speed = 0. 5 sec + 640, 000 bits / 64 kbps = 10. 5 sec Taxonomy 1 -28
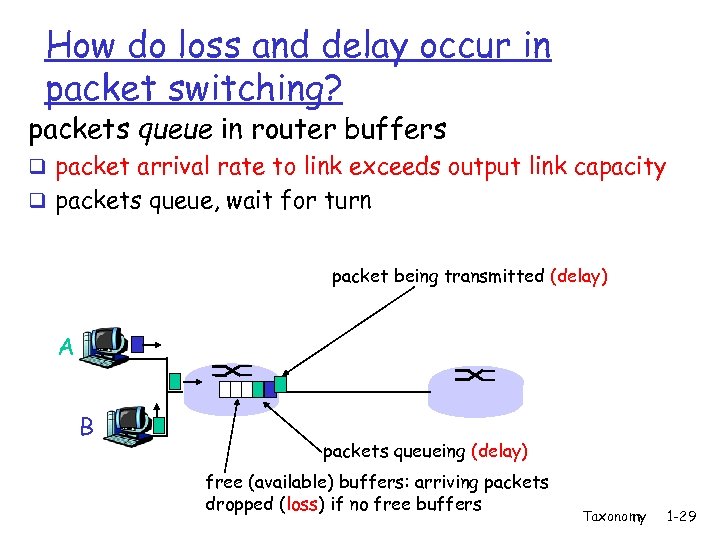 How do loss and delay occur in packet switching? packets queue in router buffers q packet arrival rate to link exceeds output link capacity q packets queue, wait for turn packet being transmitted (delay) A B packets queueing (delay) free (available) buffers: arriving packets dropped (loss) if no free buffers Taxonomy 1 -29
How do loss and delay occur in packet switching? packets queue in router buffers q packet arrival rate to link exceeds output link capacity q packets queue, wait for turn packet being transmitted (delay) A B packets queueing (delay) free (available) buffers: arriving packets dropped (loss) if no free buffers Taxonomy 1 -29
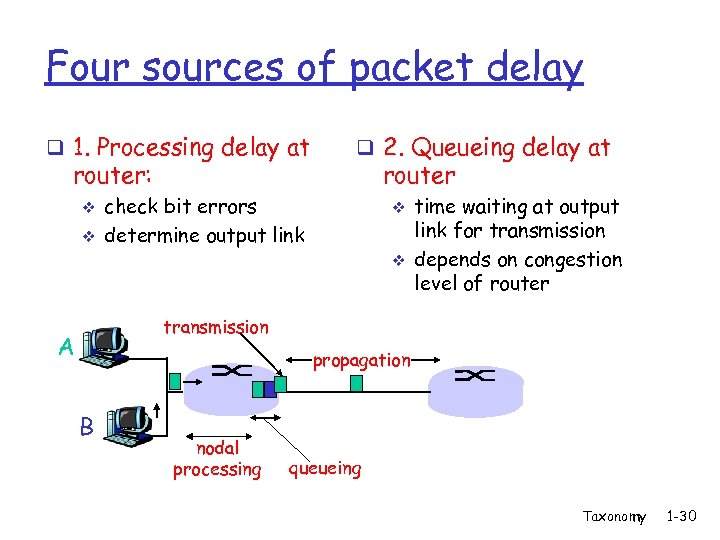 Four sources of packet delay q 1. Processing delay at router: v v q 2. Queueing delay at router check bit errors determine output link v v time waiting at output link for transmission depends on congestion level of router transmission A propagation B nodal processing queueing Taxonomy 1 -30
Four sources of packet delay q 1. Processing delay at router: v v q 2. Queueing delay at router check bit errors determine output link v v time waiting at output link for transmission depends on congestion level of router transmission A propagation B nodal processing queueing Taxonomy 1 -30
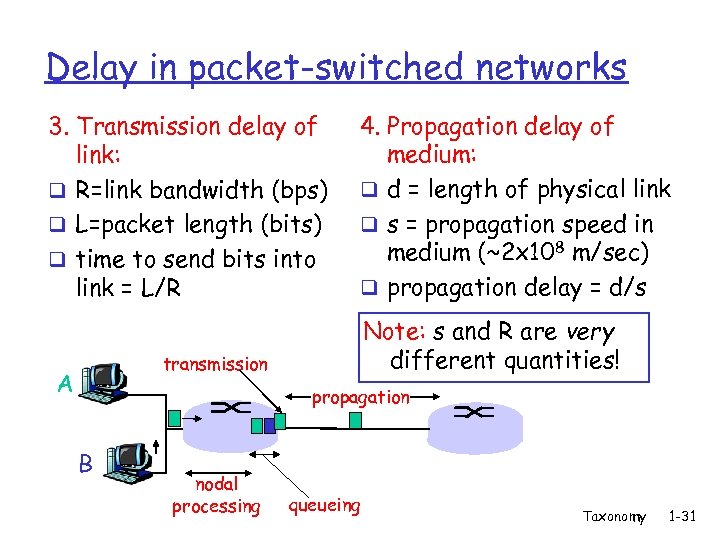 Delay in packet-switched networks 3. Transmission delay of link: q R=link bandwidth (bps) q L=packet length (bits) q time to send bits into link = L/R 4. Propagation delay of medium: q d = length of physical link q s = propagation speed in medium (~2 x 108 m/sec) q propagation delay = d/s Note: s and R are very different quantities! transmission A propagation B nodal processing queueing Taxonomy 1 -31
Delay in packet-switched networks 3. Transmission delay of link: q R=link bandwidth (bps) q L=packet length (bits) q time to send bits into link = L/R 4. Propagation delay of medium: q d = length of physical link q s = propagation speed in medium (~2 x 108 m/sec) q propagation delay = d/s Note: s and R are very different quantities! transmission A propagation B nodal processing queueing Taxonomy 1 -31
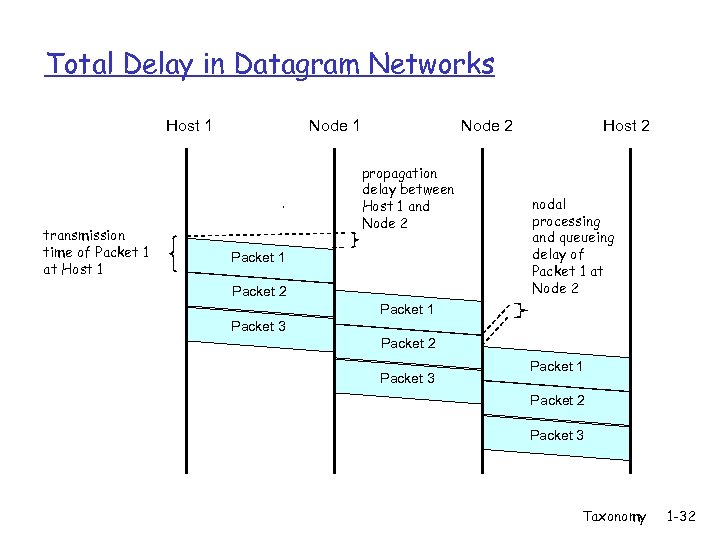 Total Delay in Datagram Networks Host 1 transmission time of Packet 1 at Host 1 Node 2 propagation delay between Host 1 and Node 2 Packet 1 Packet 2 Host 2 nodal processing and queueing delay of Packet 1 at Node 2 Packet 1 Packet 3 Packet 2 Packet 3 Packet 1 Packet 2 Packet 3 Taxonomy 1 -32
Total Delay in Datagram Networks Host 1 transmission time of Packet 1 at Host 1 Node 2 propagation delay between Host 1 and Node 2 Packet 1 Packet 2 Host 2 nodal processing and queueing delay of Packet 1 at Node 2 Packet 1 Packet 3 Packet 2 Packet 3 Packet 1 Packet 2 Packet 3 Taxonomy 1 -32
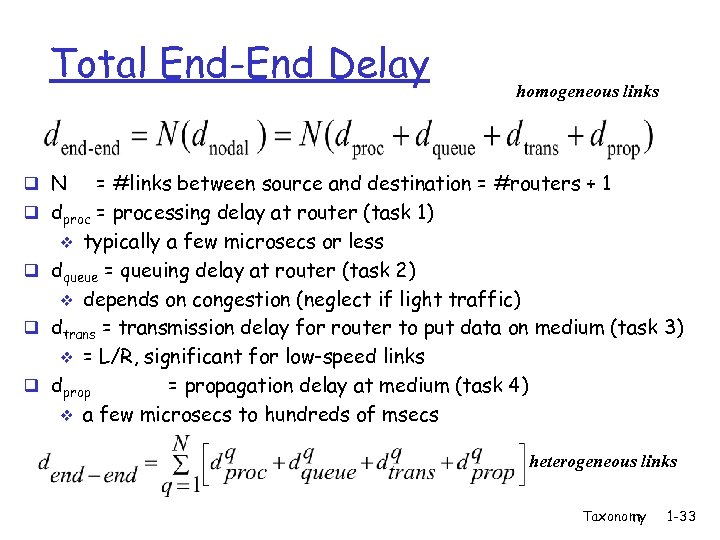 Total End-End Delay homogeneous links q N q q = #links between source and destination = #routers + 1 dproc = processing delay at router (task 1) v typically a few microsecs or less dqueue = queuing delay at router (task 2) v depends on congestion (neglect if light traffic) dtrans = transmission delay for router to put data on medium (task 3) v = L/R, significant for low-speed links dprop = propagation delay at medium (task 4) v a few microsecs to hundreds of msecs heterogeneous links Taxonomy 1 -33
Total End-End Delay homogeneous links q N q q = #links between source and destination = #routers + 1 dproc = processing delay at router (task 1) v typically a few microsecs or less dqueue = queuing delay at router (task 2) v depends on congestion (neglect if light traffic) dtrans = transmission delay for router to put data on medium (task 3) v = L/R, significant for low-speed links dprop = propagation delay at medium (task 4) v a few microsecs to hundreds of msecs heterogeneous links Taxonomy 1 -33
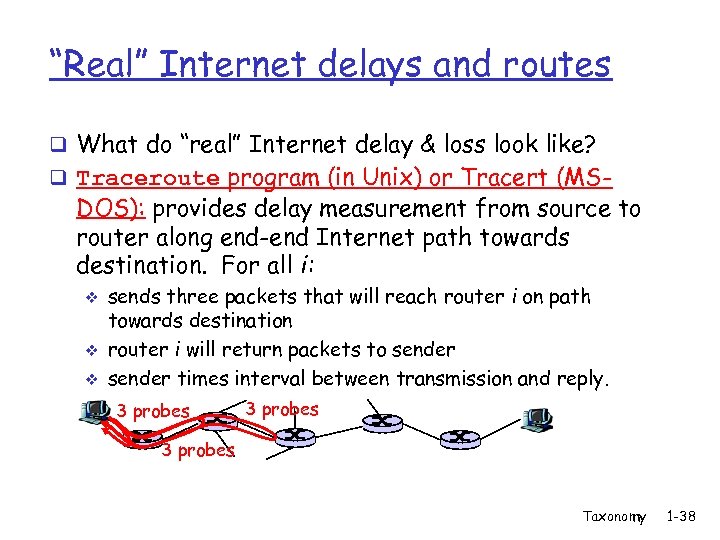 “Real” Internet delays and routes q What do “real” Internet delay & loss look like? q Traceroute program (in Unix) or Tracert (MS- DOS): provides delay measurement from source to router along end-end Internet path towards destination. For all i: v v v sends three packets that will reach router i on path towards destination router i will return packets to sender times interval between transmission and reply. 3 probes Taxonomy 1 -38
“Real” Internet delays and routes q What do “real” Internet delay & loss look like? q Traceroute program (in Unix) or Tracert (MS- DOS): provides delay measurement from source to router along end-end Internet path towards destination. For all i: v v v sends three packets that will reach router i on path towards destination router i will return packets to sender times interval between transmission and reply. 3 probes Taxonomy 1 -38
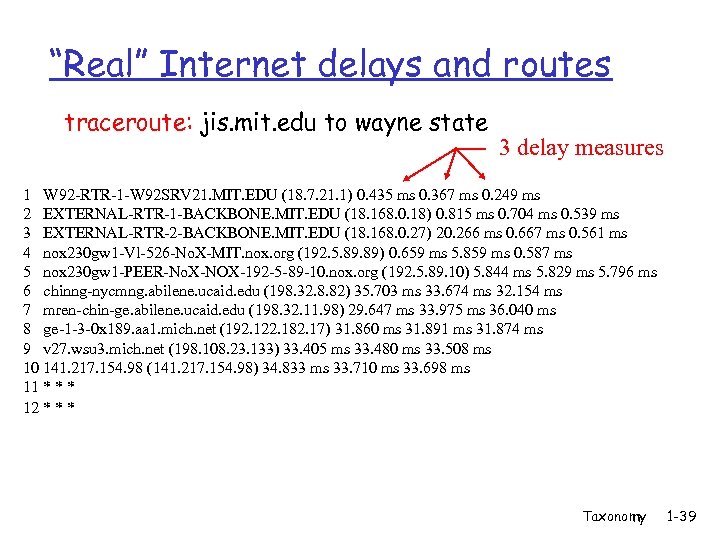 “Real” Internet delays and routes traceroute: jis. mit. edu to wayne state 3 delay measures 1 W 92 -RTR-1 -W 92 SRV 21. MIT. EDU (18. 7. 21. 1) 0. 435 ms 0. 367 ms 0. 249 ms 2 EXTERNAL-RTR-1 -BACKBONE. MIT. EDU (18. 168. 0. 18) 0. 815 ms 0. 704 ms 0. 539 ms 3 EXTERNAL-RTR-2 -BACKBONE. MIT. EDU (18. 168. 0. 27) 20. 266 ms 0. 667 ms 0. 561 ms 4 nox 230 gw 1 -Vl-526 -No. X-MIT. nox. org (192. 5. 89) 0. 659 ms 5. 859 ms 0. 587 ms 5 nox 230 gw 1 -PEER-No. X-NOX-192 -5 -89 -10. nox. org (192. 5. 89. 10) 5. 844 ms 5. 829 ms 5. 796 ms 6 chinng-nycmng. abilene. ucaid. edu (198. 32. 8. 82) 35. 703 ms 33. 674 ms 32. 154 ms 7 mren-chin-ge. abilene. ucaid. edu (198. 32. 11. 98) 29. 647 ms 33. 975 ms 36. 040 ms 8 ge-1 -3 -0 x 189. aa 1. mich. net (192. 122. 182. 17) 31. 860 ms 31. 891 ms 31. 874 ms 9 v 27. wsu 3. mich. net (198. 108. 23. 133) 33. 405 ms 33. 480 ms 33. 508 ms 10 141. 217. 154. 98 (141. 217. 154. 98) 34. 833 ms 33. 710 ms 33. 698 ms 11 * * * 12 * * * Taxonomy 1 -39
“Real” Internet delays and routes traceroute: jis. mit. edu to wayne state 3 delay measures 1 W 92 -RTR-1 -W 92 SRV 21. MIT. EDU (18. 7. 21. 1) 0. 435 ms 0. 367 ms 0. 249 ms 2 EXTERNAL-RTR-1 -BACKBONE. MIT. EDU (18. 168. 0. 18) 0. 815 ms 0. 704 ms 0. 539 ms 3 EXTERNAL-RTR-2 -BACKBONE. MIT. EDU (18. 168. 0. 27) 20. 266 ms 0. 667 ms 0. 561 ms 4 nox 230 gw 1 -Vl-526 -No. X-MIT. nox. org (192. 5. 89) 0. 659 ms 5. 859 ms 0. 587 ms 5 nox 230 gw 1 -PEER-No. X-NOX-192 -5 -89 -10. nox. org (192. 5. 89. 10) 5. 844 ms 5. 829 ms 5. 796 ms 6 chinng-nycmng. abilene. ucaid. edu (198. 32. 8. 82) 35. 703 ms 33. 674 ms 32. 154 ms 7 mren-chin-ge. abilene. ucaid. edu (198. 32. 11. 98) 29. 647 ms 33. 975 ms 36. 040 ms 8 ge-1 -3 -0 x 189. aa 1. mich. net (192. 122. 182. 17) 31. 860 ms 31. 891 ms 31. 874 ms 9 v 27. wsu 3. mich. net (198. 108. 23. 133) 33. 405 ms 33. 480 ms 33. 508 ms 10 141. 217. 154. 98 (141. 217. 154. 98) 34. 833 ms 33. 710 ms 33. 698 ms 11 * * * 12 * * * Taxonomy 1 -39
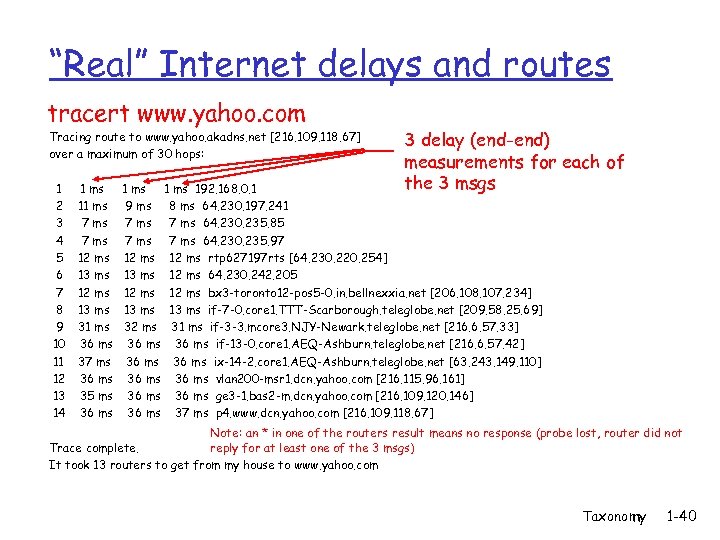 “Real” Internet delays and routes tracert www. yahoo. com Tracing route to www. yahoo. akadns. net [216. 109. 118. 67] over a maximum of 30 hops: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 1 ms 11 ms 7 ms 12 ms 13 ms 31 ms 36 ms 37 ms 36 ms 35 ms 36 ms 3 delay (end-end) measurements for each of the 3 msgs 1 ms 192. 168. 0. 1 9 ms 8 ms 64. 230. 197. 241 7 ms 64. 230. 235. 85 7 ms 64. 230. 235. 97 12 ms rtp 627197 rts [64. 230. 220. 254] 13 ms 12 ms 64. 230. 242. 205 12 ms bx 3 -toronto 12 -pos 5 -0. in. bellnexxia. net [206. 108. 107. 234] 13 ms if-7 -0. core 1. TTT-Scarborough. teleglobe. net [209. 58. 25. 69] 32 ms 31 ms if-3 -3. mcore 3. NJY-Newark. teleglobe. net [216. 6. 57. 33] 36 ms if-13 -0. core 1. AEQ-Ashburn. teleglobe. net [216. 6. 57. 42] 36 ms ix-14 -2. core 1. AEQ-Ashburn. teleglobe. net [63. 243. 149. 110] 36 ms vlan 200 -msr 1. dcn. yahoo. com [216. 115. 96. 161] 36 ms ge 3 -1. bas 2 -m. dcn. yahoo. com [216. 109. 120. 146] 36 ms 37 ms p 4. www. dcn. yahoo. com [216. 109. 118. 67] Note: an * in one of the routers result means no response (probe lost, router did not reply for at least one of the 3 msgs) Trace complete. It took 13 routers to get from my house to www. yahoo. com Taxonomy 1 -40
“Real” Internet delays and routes tracert www. yahoo. com Tracing route to www. yahoo. akadns. net [216. 109. 118. 67] over a maximum of 30 hops: 1 2 3 4 5 6 7 8 9 10 11 12 13 14 1 ms 11 ms 7 ms 12 ms 13 ms 31 ms 36 ms 37 ms 36 ms 35 ms 36 ms 3 delay (end-end) measurements for each of the 3 msgs 1 ms 192. 168. 0. 1 9 ms 8 ms 64. 230. 197. 241 7 ms 64. 230. 235. 85 7 ms 64. 230. 235. 97 12 ms rtp 627197 rts [64. 230. 220. 254] 13 ms 12 ms 64. 230. 242. 205 12 ms bx 3 -toronto 12 -pos 5 -0. in. bellnexxia. net [206. 108. 107. 234] 13 ms if-7 -0. core 1. TTT-Scarborough. teleglobe. net [209. 58. 25. 69] 32 ms 31 ms if-3 -3. mcore 3. NJY-Newark. teleglobe. net [216. 6. 57. 33] 36 ms if-13 -0. core 1. AEQ-Ashburn. teleglobe. net [216. 6. 57. 42] 36 ms ix-14 -2. core 1. AEQ-Ashburn. teleglobe. net [63. 243. 149. 110] 36 ms vlan 200 -msr 1. dcn. yahoo. com [216. 115. 96. 161] 36 ms ge 3 -1. bas 2 -m. dcn. yahoo. com [216. 109. 120. 146] 36 ms 37 ms p 4. www. dcn. yahoo. com [216. 109. 118. 67] Note: an * in one of the routers result means no response (probe lost, router did not reply for at least one of the 3 msgs) Trace complete. It took 13 routers to get from my house to www. yahoo. com Taxonomy 1 -40
 “Real” Internet delays and routes q Ping program: checks if a host is live or not and provides RTT delay measurement from source to destination along end-end Internet path. v v v sends n requests of size 32 bytes and calculates avg RTT sender times interval between transmission and reply. ping -n
“Real” Internet delays and routes q Ping program: checks if a host is live or not and provides RTT delay measurement from source to destination along end-end Internet path. v v v sends n requests of size 32 bytes and calculates avg RTT sender times interval between transmission and reply. ping -n
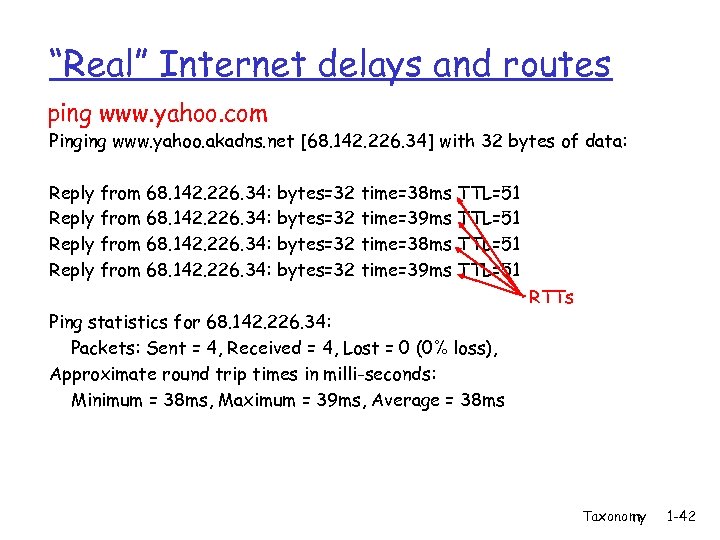 “Real” Internet delays and routes ping www. yahoo. com Pinging www. yahoo. akadns. net [68. 142. 226. 34] with 32 bytes of data: Reply from 68. 142. 226. 34: bytes=32 time=38 ms TTL=51 Reply from 68. 142. 226. 34: bytes=32 time=39 ms TTL=51 Ping statistics for 68. 142. 226. 34: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 38 ms, Maximum = 39 ms, Average = 38 ms RTTs Taxonomy 1 -42
“Real” Internet delays and routes ping www. yahoo. com Pinging www. yahoo. akadns. net [68. 142. 226. 34] with 32 bytes of data: Reply from 68. 142. 226. 34: bytes=32 time=38 ms TTL=51 Reply from 68. 142. 226. 34: bytes=32 time=39 ms TTL=51 Ping statistics for 68. 142. 226. 34: Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 38 ms, Maximum = 39 ms, Average = 38 ms RTTs Taxonomy 1 -42
 Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Performance Metrics: • Delay: • Loss • Throughput q Security Taxonomy 1 -43
Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Performance Metrics: • Delay: • Loss • Throughput q Security Taxonomy 1 -43
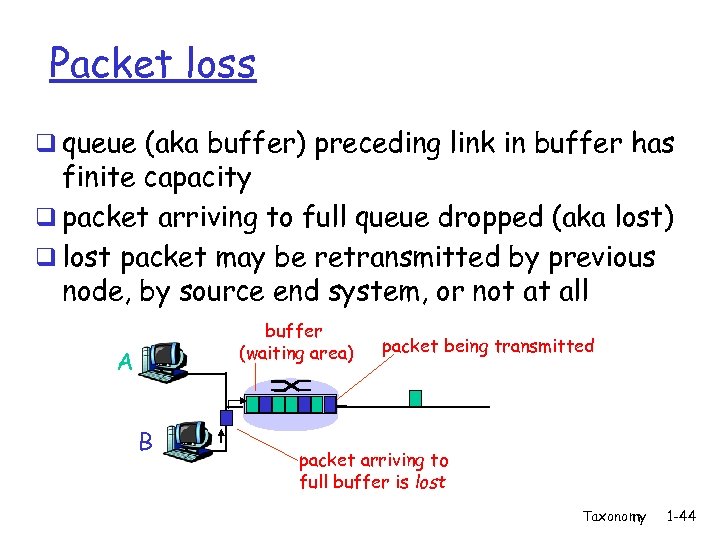 Packet loss q queue (aka buffer) preceding link in buffer has finite capacity q packet arriving to full queue dropped (aka lost) q lost packet may be retransmitted by previous node, by source end system, or not at all buffer (waiting area) A B packet being transmitted packet arriving to full buffer is lost Taxonomy 1 -44
Packet loss q queue (aka buffer) preceding link in buffer has finite capacity q packet arriving to full queue dropped (aka lost) q lost packet may be retransmitted by previous node, by source end system, or not at all buffer (waiting area) A B packet being transmitted packet arriving to full buffer is lost Taxonomy 1 -44
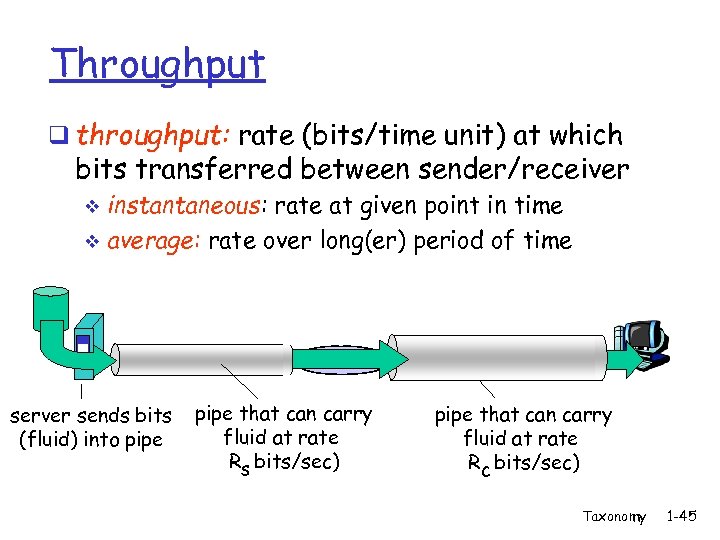 Throughput q throughput: rate (bits/time unit) at which bits transferred between sender/receiver instantaneous: rate at given point in time v average: rate over long(er) period of time v link capacity server, with server sends bits pipe that can carry Rs bits/sec fluid at rate file into pipe (fluid) of F bits Rs bits/sec) to send to client link capacity pipe that can carry Rfluid at rate c bits/sec Rc bits/sec) Taxonomy 1 -45
Throughput q throughput: rate (bits/time unit) at which bits transferred between sender/receiver instantaneous: rate at given point in time v average: rate over long(er) period of time v link capacity server, with server sends bits pipe that can carry Rs bits/sec fluid at rate file into pipe (fluid) of F bits Rs bits/sec) to send to client link capacity pipe that can carry Rfluid at rate c bits/sec Rc bits/sec) Taxonomy 1 -45
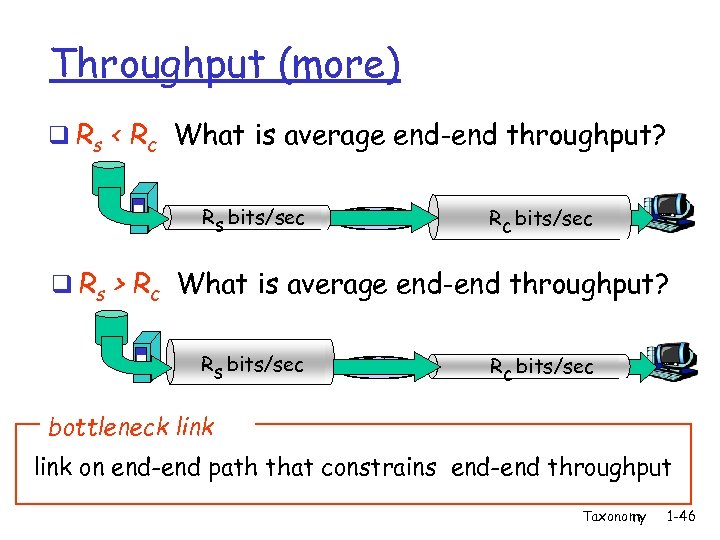 Throughput (more) q Rs < Rc What is average end-end throughput? Rs bits/sec Rc bits/sec q Rs > Rc What is average end-end throughput? Rs bits/sec Rc bits/sec bottleneck link on end-end path that constrains end-end throughput Taxonomy 1 -46
Throughput (more) q Rs < Rc What is average end-end throughput? Rs bits/sec Rc bits/sec q Rs > Rc What is average end-end throughput? Rs bits/sec Rc bits/sec bottleneck link on end-end path that constrains end-end throughput Taxonomy 1 -46
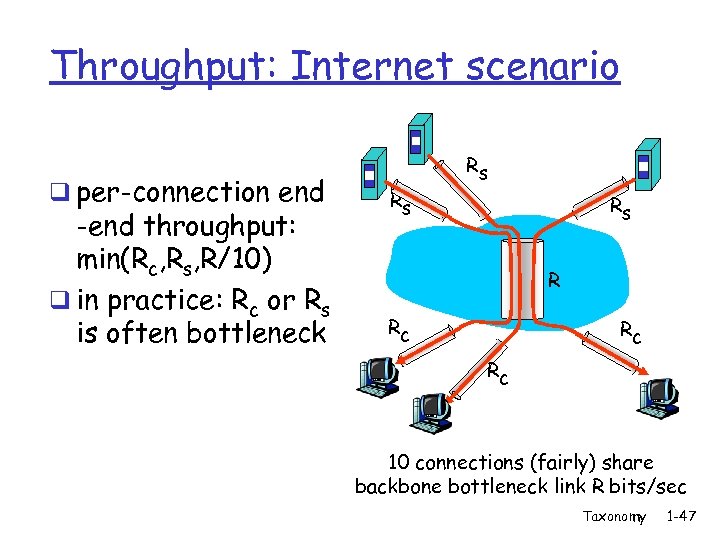 Throughput: Internet scenario q per-connection end -end throughput: min(Rc, Rs, R/10) q in practice: Rc or Rs is often bottleneck Rs Rs Rs R Rc Rc Rc 10 connections (fairly) share backbone bottleneck link R bits/sec Taxonomy 1 -47
Throughput: Internet scenario q per-connection end -end throughput: min(Rc, Rs, R/10) q in practice: Rc or Rs is often bottleneck Rs Rs Rs R Rc Rc Rc 10 connections (fairly) share backbone bottleneck link R bits/sec Taxonomy 1 -47
 Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Performance Metrics: • Delay: • Loss • Throughput q Security Taxonomy 1 -48
Outline q Network Taxonomy v Broadcast vs Switched Networks v Circuit Switched vs packet switched q Switched Network Performance v Performance Metrics: • Delay: • Loss • Throughput q Security Taxonomy 1 -48
 Network Security q attacks on Internet infrastructure: v infecting/attacking hosts: spyware, virus, worms, Trojan Horse, unauthorized access, and malware in geneal • Malware: sw designed to infiltrate or damage a computer system w/o the owner’s informed consent [Wikipedia]; based on intention of its creator, rather than any features • In law, malware is defined as a computer contaminant v denial of service: deny access to resources (servers, link BW) • Vulnerability attack; BW flooding; Connection flooding q Internet not originally designed with security in mind v original vision: “a group of mutually trusting users attached to a transparent network” v Internet protocol designers playing “catch-up” v Security considerations in all layers! Taxonomy 1 -49
Network Security q attacks on Internet infrastructure: v infecting/attacking hosts: spyware, virus, worms, Trojan Horse, unauthorized access, and malware in geneal • Malware: sw designed to infiltrate or damage a computer system w/o the owner’s informed consent [Wikipedia]; based on intention of its creator, rather than any features • In law, malware is defined as a computer contaminant v denial of service: deny access to resources (servers, link BW) • Vulnerability attack; BW flooding; Connection flooding q Internet not originally designed with security in mind v original vision: “a group of mutually trusting users attached to a transparent network” v Internet protocol designers playing “catch-up” v Security considerations in all layers! Taxonomy 1 -49
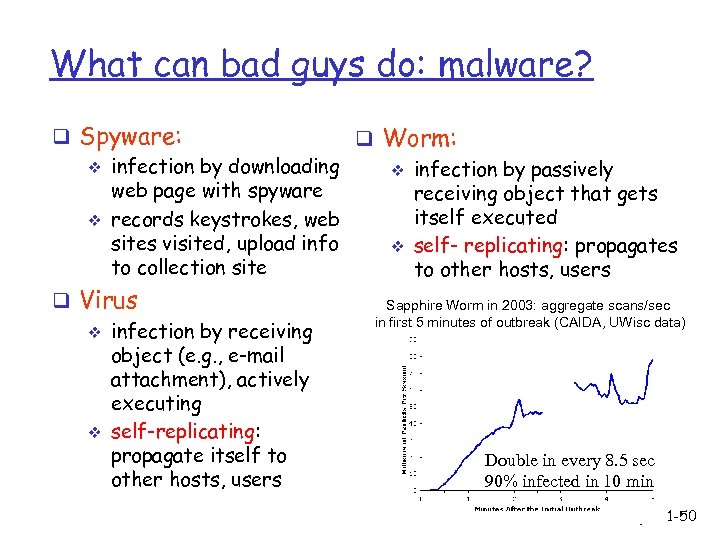 What can bad guys do: malware? q Spyware: q Worm: v infection by downloading v infection by passively web page with spyware receiving object that gets itself executed v records keystrokes, web sites visited, upload info v self- replicating: propagates to collection site to other hosts, users q Virus v infection by receiving object (e. g. , e-mail attachment), actively executing v self-replicating: propagate itself to other hosts, users Sapphire Worm in 2003: aggregate scans/sec in first 5 minutes of outbreak (CAIDA, UWisc data) Double in every 8. 5 sec 90% infected in 10 min Taxonomy 1 -50
What can bad guys do: malware? q Spyware: q Worm: v infection by downloading v infection by passively web page with spyware receiving object that gets itself executed v records keystrokes, web sites visited, upload info v self- replicating: propagates to collection site to other hosts, users q Virus v infection by receiving object (e. g. , e-mail attachment), actively executing v self-replicating: propagate itself to other hosts, users Sapphire Worm in 2003: aggregate scans/sec in first 5 minutes of outbreak (CAIDA, UWisc data) Double in every 8. 5 sec 90% infected in 10 min Taxonomy 1 -50
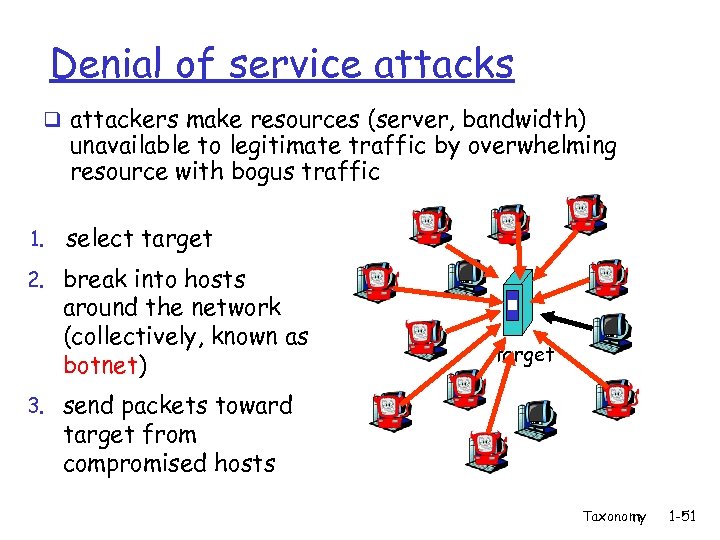 Denial of service attacks q attackers make resources (server, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus traffic 1. select target 2. break into hosts around the network (collectively, known as botnet) target 3. send packets toward target from compromised hosts Taxonomy 1 -51
Denial of service attacks q attackers make resources (server, bandwidth) unavailable to legitimate traffic by overwhelming resource with bogus traffic 1. select target 2. break into hosts around the network (collectively, known as botnet) target 3. send packets toward target from compromised hosts Taxonomy 1 -51
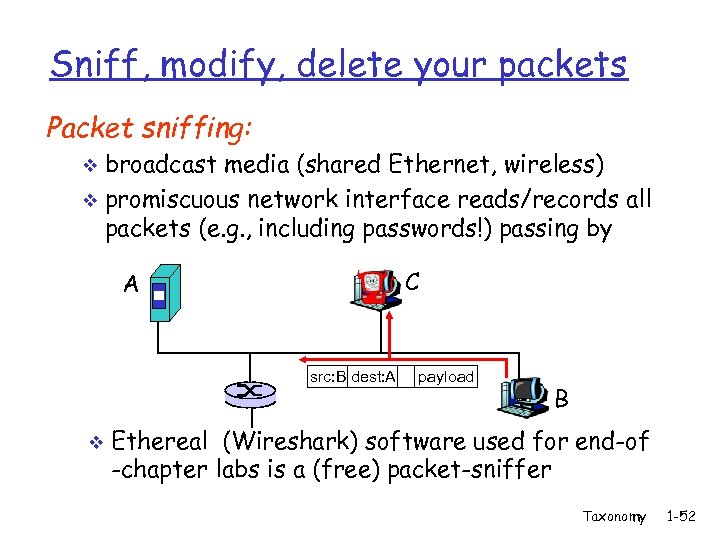 Sniff, modify, delete your packets Packet sniffing: broadcast media (shared Ethernet, wireless) v promiscuous network interface reads/records all packets (e. g. , including passwords!) passing by v C A src: B dest: A v payload B Ethereal (Wireshark) software used for end-of -chapter labs is a (free) packet-sniffer Taxonomy 1 -52
Sniff, modify, delete your packets Packet sniffing: broadcast media (shared Ethernet, wireless) v promiscuous network interface reads/records all packets (e. g. , including passwords!) passing by v C A src: B dest: A v payload B Ethereal (Wireshark) software used for end-of -chapter labs is a (free) packet-sniffer Taxonomy 1 -52
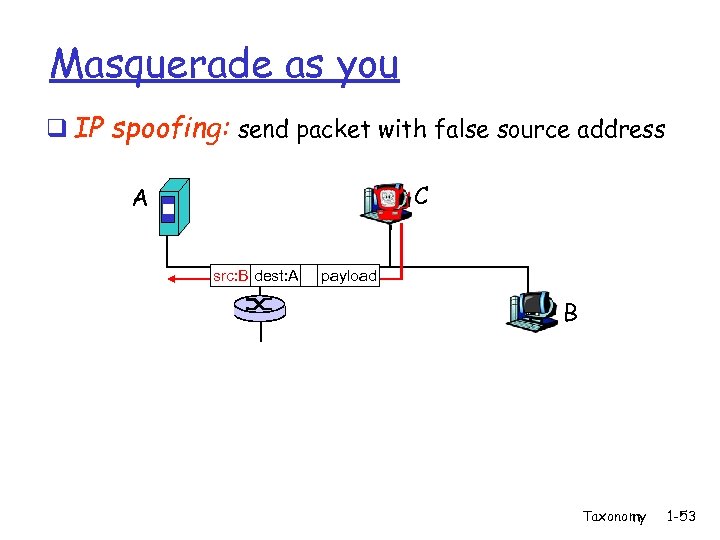 Masquerade as you q IP spoofing: send packet with false source address C A src: B dest: A payload B Taxonomy 1 -53
Masquerade as you q IP spoofing: send packet with false source address C A src: B dest: A payload B Taxonomy 1 -53
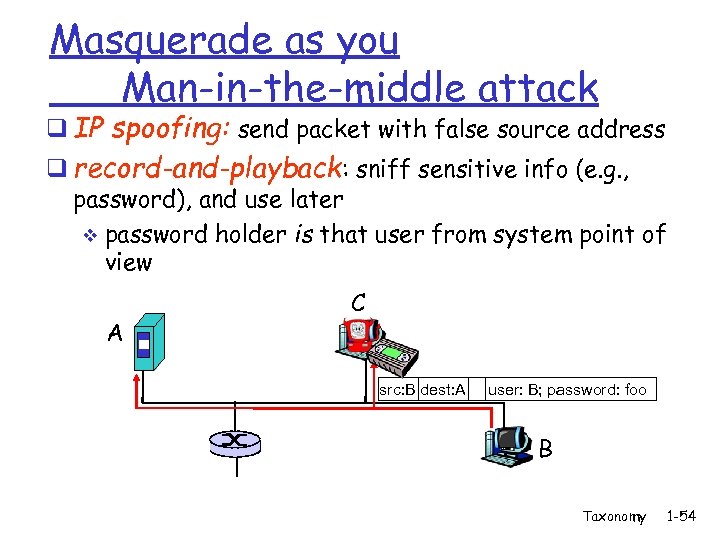 Masquerade as you Man-in-the-middle attack q IP spoofing: send packet with false source address q record-and-playback: sniff sensitive info (e. g. , password), and use later v password holder is that user from system point of view A C src: B dest: A user: B; password: foo B Taxonomy 1 -54
Masquerade as you Man-in-the-middle attack q IP spoofing: send packet with false source address q record-and-playback: sniff sensitive info (e. g. , password), and use later v password holder is that user from system point of view A C src: B dest: A user: B; password: foo B Taxonomy 1 -54
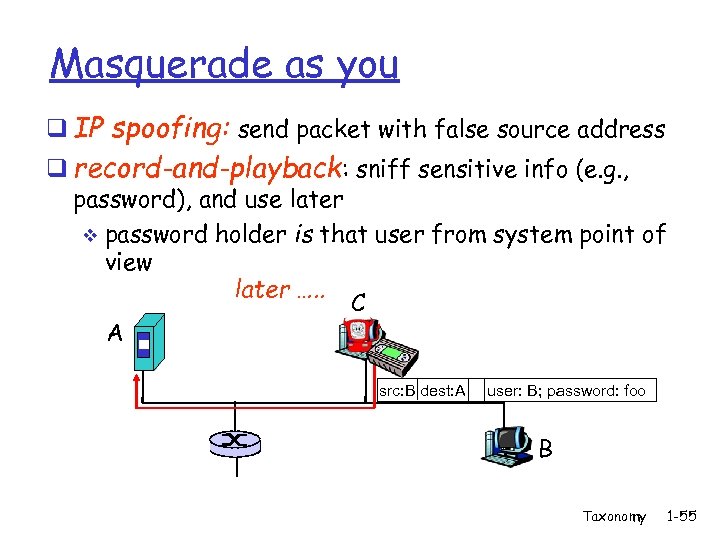 Masquerade as you q IP spoofing: send packet with false source address q record-and-playback: sniff sensitive info (e. g. , password), and use later v password holder is that user from system point of view later …. . C A src: B dest: A user: B; password: foo B Taxonomy 1 -55
Masquerade as you q IP spoofing: send packet with false source address q record-and-playback: sniff sensitive info (e. g. , password), and use later v password holder is that user from system point of view later …. . C A src: B dest: A user: B; password: foo B Taxonomy 1 -55
 Summary q Network Taxonomy v Broadcast v Circuit Switch v Packet switch v Virtual circuit switch q Switched Network Performance v Delay, packet loss, throughput q Security Taxonomy 1 -56
Summary q Network Taxonomy v Broadcast v Circuit Switch v Packet switch v Virtual circuit switch q Switched Network Performance v Delay, packet loss, throughput q Security Taxonomy 1 -56


