28081ff73c508949fb9f0caa8e823840.ppt
- Количество слайдов: 24

LCG/EGEE Security Update HEPi. X, Fall 2004 BNL, 18 October 2004 David Kelsey CCLRC/RAL, UK d. p. kelsey@rl. ac. uk 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 1

Outline Update since October 2003 (Vancouver HEPi. X) • Introduction • Policy • Procedures & Operations • Technology • Future work 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 2

Introduction LCG & EGEE 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 3
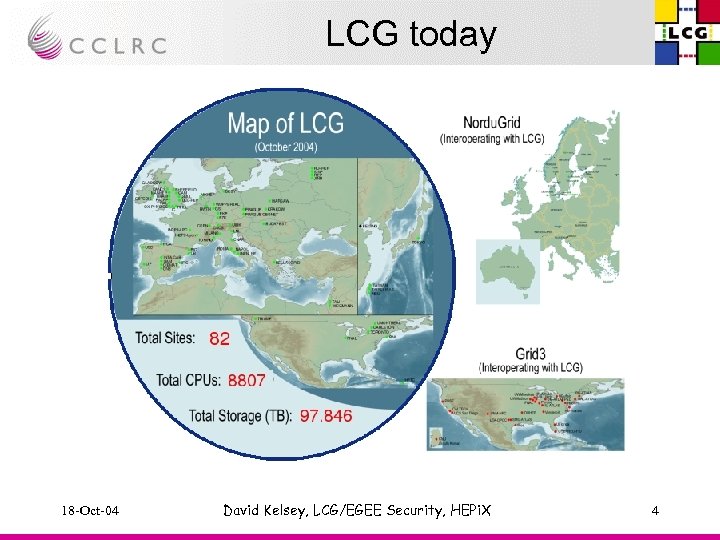
LCG today 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 4
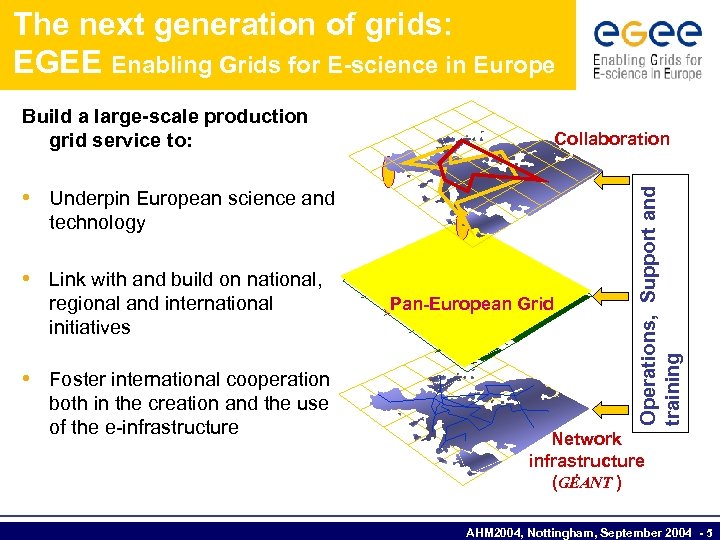
The next generation of grids: EGEE Enabling Grids for E-science in Europe Build a large-scale production grid service to: • Underpin European science and technology • Link with and build on national, regional and international initiatives • Foster international cooperation both in the creation and the use of the e-infrastructure Pan-European Grid Operations, Support and training Collaboration Network infrastructure (GÉANT ) AHM 2004, Nottingham, September 2004 - 5
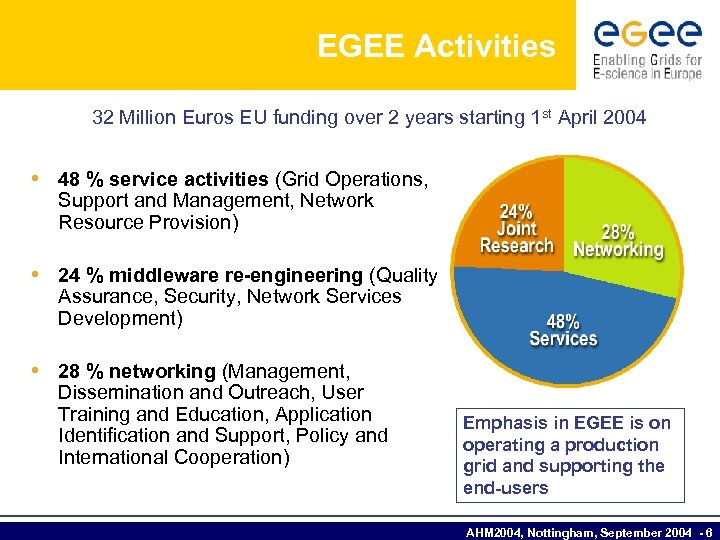
EGEE Activities 32 Million Euros EU funding over 2 years starting 1 st April 2004 • 48 % service activities (Grid Operations, Support and Management, Network Resource Provision) • 24 % middleware re-engineering (Quality Assurance, Security, Network Services Development) • 28 % networking (Management, Dissemination and Outreach, User Training and Education, Application Identification and Support, Policy and International Cooperation) Emphasis in EGEE is on operating a production grid and supporting the end-users AHM 2004, Nottingham, September 2004 - 6
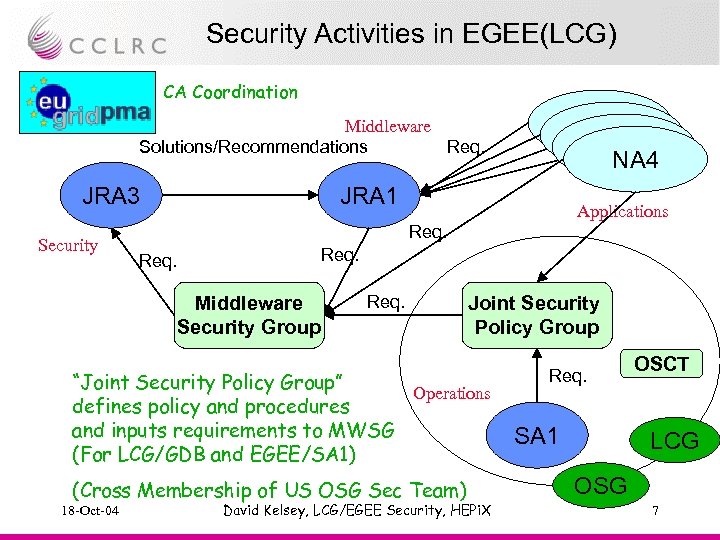
Security Activities in EGEE(LCG) CA Coordination NA 4 Middleware Solutions/Recommendations Req. JRA 3 Security JRA 1 Applications Req. Middleware Security Group Req. Joint Security Policy Group “Joint Security Policy Group” Operations defines policy and procedures and inputs requirements to MWSG (For LCG/GDB and EGEE/SA 1) (Cross Membership of US OSG Sec Team) 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X Req. SA 1 OSCT LCG OSG 7

Security Policy 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 8

LCG Security Policy • During 2003/04, the LCG project agreed a first version of its Security Policy – Written by the Joint Security Policy Group – Approved by the Grid Deployment Board/PEB • A single common policy for the whole project – But does not override local policies • An important step forward for a production Grid • The policy – Defines Attitude of the project towards security and availability – Gives Authority for defined actions – Puts Responsibilities on individuals and bodies • Now being used by EGEE and (some) national Grids 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 9
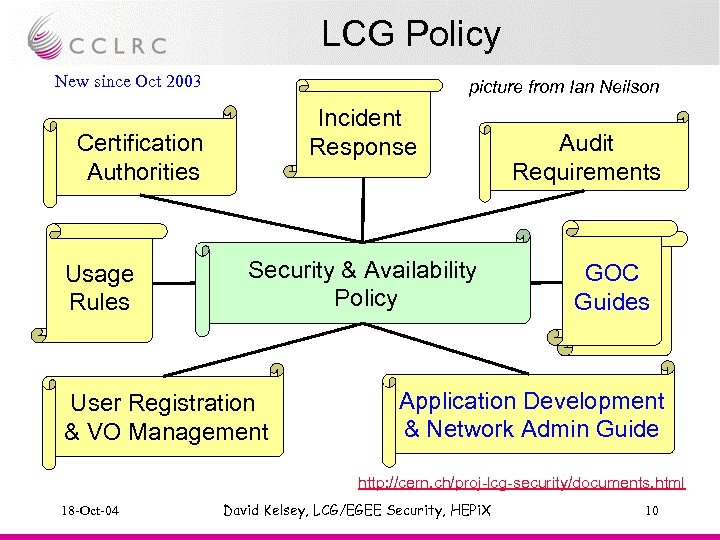
LCG Policy New since Oct 2003 picture from Ian Neilson Incident Response Certification Authorities Usage Rules Security & Availability Policy User Registration & VO Management Audit Requirements GOC Guides Application Development & Network Admin Guide http: //cern. ch/proj-lcg-security/documents. html 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 10

Security Procedures & Operations 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 11

Security Procedures • Incident Response – Open Science Grid leading this area – See talks in Friday morning’s Operations session • LCG/EGEE Operational Security – Operational Security Coordination Team (OSCT) – Again: see Friday’s talk • User Registration & VO Management – Requirements for 4 LHC Experiments • Presented at May 2004 (Edinburgh) HEPi. X (M. Dimou) 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 12
User Registration and VO Membership Management • Requirements document (V 2. 7) – https: //edms. cern. ch/document/428034 – approved by GDB in May 2004 • Task force created to propose the solution • Many discussions with CERN HR, User Office, Experiment Secretariats, VO managers, … • Recent Meeting at CERN – 15 -17 September, 2004 http: //cern. ch/dimou/lcg/registrar/TF/meetings/ 2004 -09 -15/ – Technical solution now agreed 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 13
User Registration (1) • Every user (4 LHC expts) must register in CERN HR db first – Already true for the majority • Advantages of using existing procedures • No duplication of effort or personal data – External users (e. g. people never coming to CERN) and short-term users (e. g. external summer students) • Need a simple, speedy and robust procedure – Non-VO people • e. g. testers/experiment independent people • must register in CERN HR (e. g. via LCG/IT) • Eventual aim is to use the experiment participation end-date in CERN HR to trigger immediate suspension from the VO 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 14
User Registration (2) • VO registration expiry date – Not exceeding 1 year from date of VO registration – Less if institute-contract/CERN HR registration expires before then • Personal User Data will only reside in CERN HR • There is no automatic membership of VO – User has to complete a form and the VO manager has to approve • Authorized personnel at resource centres will have read access to the VO registration info 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 15

User Registration (3) • When VO expiry date is reached, the VO membership is immediately suspended – Advance warning will be sent to the user • There will be other possible reasons for suspension – E. g. following security problems 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 16

Technical Solution agreed • 15 -17 Sep meeting decisions: • The VO registration database – Will be VOMRS component from US CMS VOX – VOMRS needs development to meet new requirements (FNAL working on this) – VOMRS manages the groups and roles -> VOMS • CERN is working on VOMRS interconnection to the CERN HR DB (Oracle) • The dynamic Authorization will be VOMS – Groups and roles • Non-LHC VO’s may use the VOMS-admin component (an alternative admin UI) • Time to implement not yet agreed – Aiming for early in 2005 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 17

Security Technology 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 18
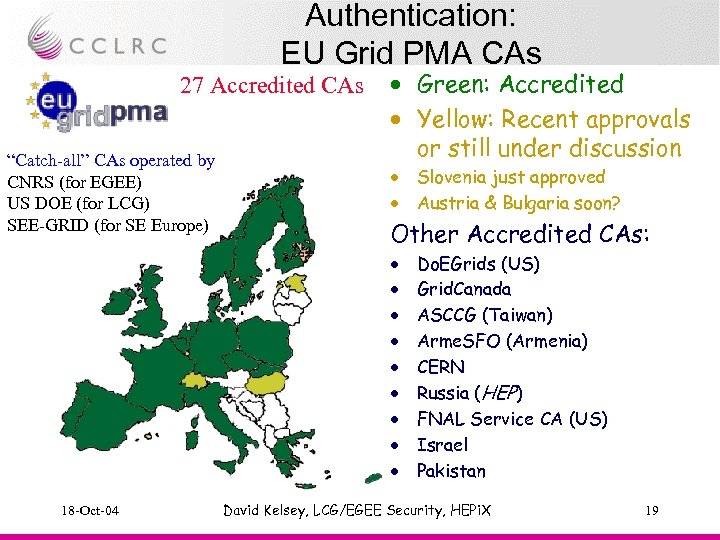
Authentication: EU Grid PMA CAs 27 Accredited CAs “Catch-all” CAs operated by CNRS (for EGEE) US DOE (for LCG) SEE-GRID (for SE Europe) · Green: Accredited · Yellow: Recent approvals or still under discussion · · Other Accredited CAs: · · · · · 18 -Oct-04 Slovenia just approved Austria & Bulgaria soon? Do. EGrids (US) Grid. Canada ASCCG (Taiwan) Arme. SFO (Armenia) CERN Russia (HEP) FNAL Service CA (US) Israel Pakistan David Kelsey, LCG/EGEE Security, HEPi. X 19
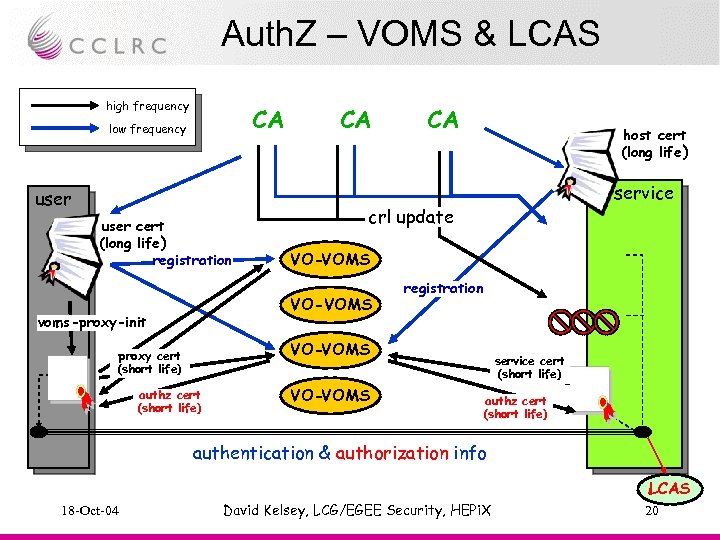
Auth. Z – VOMS & LCAS high frequency CA low frequency user cert (long life ) registration CA host cert (long life ) service crl update VO-VOMS voms-proxy-init CA registration VO-VOMS proxy cert (short life) authz cert (short life) VO-VOMS service cert (short life) authz cert (short life) authentication & authorization info LCAS 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 20
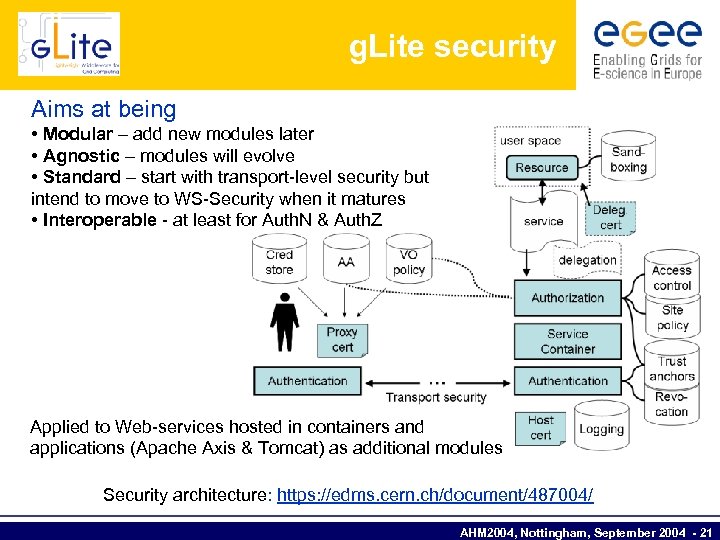
g. Lite security Aims at being • Modular – add new modules later • Agnostic – modules will evolve • Standard – start with transport-level security but intend to move to WS-Security when it matures • Interoperable - at least for Auth. N & Auth. Z Applied to Web-services hosted in containers and applications (Apache Axis & Tomcat) as additional modules Security architecture: https: //edms. cern. ch/document/487004/ AHM 2004, Nottingham, September 2004 - 21
EGEE Auth. Z Policy comes from many stakeholders Graphics from Globus Alliance & GGF OGSA-WG 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 22

Future Work • Policy – Working on more general policy (with OSG) • No longer LCG-specific – EU e. Infrastructure Reflection Group (18 Nov 04) • • • Acceptable Use Policy and Authorization for EU e. Science Procedures – Operational Security, including Incident Response – User Registration Technology – Authentication • Asia/Pacific & Americas PMAs being created • Credential Repositories – Authorization – dynamic role-based access control • • VOMRS & VOMS • Local control and policy, e. g. via LCAS/LCMAPS Security requirements, Operational Constraints – Very important to get Site input to operations and middleware development (all feedback is very welcome!) 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 23
References • LCG/EGEE Joint Security Policy Group http: //proj-lcg-security. web. cern. ch/ • EGEE JRA 3 (Security) http: //egee-jra 3. web. cern. ch/ • Open Science Grid Security • http: //www. opensciencegrid. org/techgroups/security/ EU Data. Grid Security http: //hep-project-grid-scg. web. cern. ch/ • LCG Guide to Application, Middleware and Network Security https: //edms. cern. ch/document/452128 • EU e. Infrastructure Reflection Group http: //www. e-irg. org/ • EU Grid PMA (CA coordination) http: //www. eugridpma. org/ • TERENA Tacar (CA repository) http: //www. terena. nl/tech/task-forces/tf-aace/tacar/ 18 -Oct-04 David Kelsey, LCG/EGEE Security, HEPi. X 24
28081ff73c508949fb9f0caa8e823840.ppt