fd74d541add0f948533e47a99320e6c7.ppt
- Количество слайдов: 91

LAW ENFORCEMENT TRAINING & CAPACITY BUILDING CYBERCRIME &SECURITY, DIGITAL FORENSIC, SOCIAL MEDIA ANALYSIS, CELL TOWER ANALYSIS AND E-INVESTIGATIONS BY : CHRIS I. ANICHEBE CEH, CHFI, ECSA, LPT CERTIFIED SECURITY ANALYST & FORENSIC INVESTIGATOR

Motivation For Training q q Law enforcement needs to be developed in combating electronic, high tech crime(Cybercrimes) Designed for ABUAD

Objectives Of Training At the end of the presentation, participants will be able to n Conduct internet investigation, n Cyber Policing in cyber space n Become efficient cyber investigators, n Managing effectively digital forensic laboratory. n Cybercrime: From Crime to Courtroom

Training Contents Cybersecurity & Cybercrime • Introduction. • What is cybercrime • History of cybercrime • Categories of cybercrime. • Types of cybercrime • Cybercriminals • Prevention. • Definition of Cybersecurity • Nigeria Cybercrime Law • Conclusion Digital Forensics • Mobile Phone Interrogation • Computer Interrogation • Email tracking and tracing • IP tracing to geolocation • Website Investigation Social Media Analysis & Investigations • Media & Platforms • Tools for Investigations Cell Tower Analysis & Investigations • Call Data Records{CDR}analysis • Triangulation with coordinates • IMEI investigation • Mobile Phone Tracking • Phone Number Tracking

Cyber crime Cybercrime is nothing but where the computer used as an object or subject of crime. .

Content For Cybercrime & Security n n n n n Introduction What is Cyber Crime History of cyber crime Categories of cyber crime Types of cyber crime Cyber criminals Prevention Defining cyber Security Nigeria Cybercrime Law Conclusion

Introduction To Cybercrime n n The internet in Nigeria and the world in general is growing rapidly. It has given rise to new opportunities in every field we can think of ? be it entertainment, business, sports or education. There are two sides to a coin. Internet also has its own disadvantages. One of the major disadvantages is Cyber crime ? illegal activity committed on the internet.

What is Cybercrime n n Cybercrime is any illegal act committed using a computer network (especially the Internet). Cybercrime is a subset of computer crime.

History n n The first recorded cyber crime took place in the year 1820! In 1820, Joseph-Marie Jacquard, a textile manufacturer in France, produced the loom. This device allowed the repetition of a series of steps in the weaving of special fabrics. This resulted in a fear amongst Jacquard‘s employees that their traditional employment and livelihood were being threatened. They committed acts of sabotage to discourage Jacquard from further use of the new technology. This is the first recorded cyber crime!

Types of Cyber Crime n n n Hacking Denial OF Service Attack Virus Dissemination Ransomware Attack Computer Forgery Credit Card Fraud Phishing Spoofing Cyber Stalking Threatening Salami attack

Modification of a conventional crime by using computers. n n n n n Financial crimes Cyber pornography Sale of illegal articles Online gambling Intellectual Property crime Email spoofing Forgery Cyber Defamation Cyber stalking Cyber-kidnapping

Categories Cyber crimes n Cyber crimes can be basically divided into 3 major categories: n n n Cyber crimes against persons. Cyber crimes against property. Cyber crimes against government. Take a look at the cybercrime guide lines.

First Category n Cyber harassment is a distinct Cybercrime. Various kinds of harassment can and do occur in cyberspace, or through the use of cyberspace. Harassment can be sexual, racial, religious, or other.

Second Category n n These crimes include computer vandalism(destruction of others' property), transmission of harmful programs, unauthorized trespassing through cyber space, unauthorized possession of computer information. Ransomware is a computer virus that installs discreetly on a victim’s device, holding his data hostage until ransom, which is usually in cryptocurrency is paid. The payee is called Ransomee. This is cyber-kidnapping. n example : Wannacry

Third Category n n Cyber terrorism is one distinct kind of crime in this category. The growth of internet has shown that the medium of Cyberspace is being used by individuals and groups to threaten the international governments as also to terrorize the citizens of a country.

Cyber Criminals n Kids (age group 9 -16 etc. ) n Organized hacktivists n Disgruntled employees n Professional hackers (corporate espionage)

PREVENTION OF CYBER CRIME n Avoid disclosing your identity to any strangers. n Always use latest antivirus software to guard against virus attacks. n Never send your credit card number to any site which is not secured. n Use of firewall. n Change passwords frequently. n Uninstall unnecessary software.
CYBER SECURITY n n Internet security is a branch of computer security specifically related to the Internet. It's objective is to establish rules and measure to use against attacks over the Internet.

DEFINING CYBERSECURITY n n n Cybersecurity strives to ensure the attainment and maintenance of the security properties of the organization and user’s assets against relevant security risks in the cyber environment. n The collection of tools, n policies, security concepts, n security safeguards, guidelines, n risk management approaches, actions, training, best practices, assurance and technologies that can be used to protect the cyber environment and organization and user’s assets. Organization and user’s assets include n connected computing devices, personnel, infrastructure, applications, services, telecommunications systems, and the totality of transmitted and/or stored information in the cyber environment. The general security objectives comprise the following: – Confidentiality, Integrity, Availability{CIA}

NIGERIA CYBER CRIME LAW CYBERCRIMES (PROHIBITION, PREVENTION, ETC) ACT, 2015 n Provides an effective, unified and comprehensive legal, regulatory and institutional framework for the prohibition, prevention, detection, prosecution and punishment of cybercrimes in Nigeria. This act also ensures the protection of critical national information infrastructure, and promotes cybersecurity and the protection of computer systems and networks, electronic communications, data and computer programs, intellectual property and privacy rights. n Contains 43 sections, and is a very important piece of legislation to foster the development of the nascent ICT sector in Nigeria. – Cyber. Crime (Prohibition, Prevention, etc) Act 2015

Cybercrime Crime case study

Cybercrime Crime case study

Cybercrime Crime case study

Cybercrime Crime case study
Cybercrime Crime case study
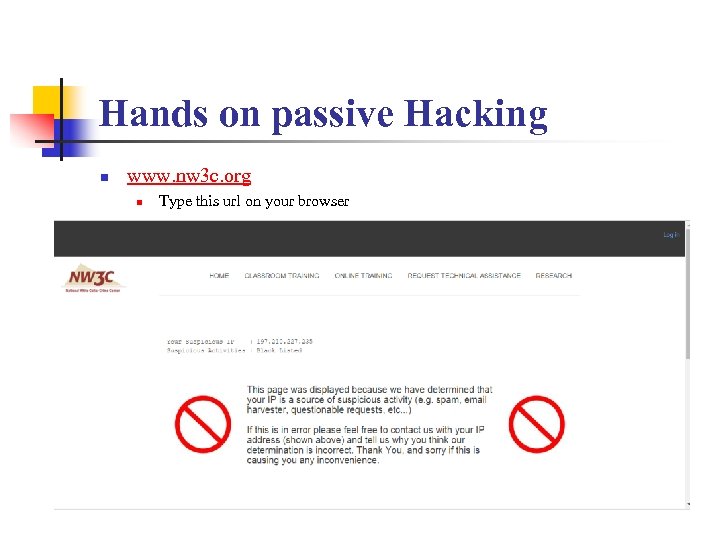
Hands on passive Hacking n www. nw 3 c. org n Type this url on your browser

Conclusion n Officers of the law enforcement agencies, must be developed and trained to address the various categories of computer crime. n As such, investigators will know what and which materials to search and seize, the electronic evidence to recover, and the chain of custody to maintain.

Training Contents Cybersecurity & Cybercrime • Introduction. • What is cybercrime • History of cybercrime • Categories of cybercrime. • Types of cybercrime • Cybercriminals • Prevention. • Definition of Cybersecurity • Nigeria Cybercrime Law • Conclusion Digital Forensics • Mobile Phone Interrogation • Computer Interrogation • Email tracking and tracing • IP tracing to geolocation • Website investigation Social Media Analysis & Investigations • Media & Platforms • Tools for Investigations Cell Tower Analysis & Investigations • Call Data Records{CDR}analysis • Triangulation with coordinates • IMEI investigation • Mobile phone tracking • Phone number tracking

Digital Forensic • Whatever people do on computers and other digital devices, they leave traces behind.

Digital Devices Acquire, analyze, and share digital evidence from computers, smartphones, and tablets Digital Forensic

Mobile Phone Interrogation n What is Mobile Device Forensics? Mobile device forensics is directly connected to digital forensics and can be defined as being the recovery of digital information or data which is often used for criminal evidence. n Mobile Device Forensics by definition applies only to mobile devices, e. g. tablets, cell phones etc, but it the term also includes any portable digital device that has both internal memory and communication abilities such as PDA devices and also GPS devices. n Recovering deleted data has always been a problem when it comes to mobile phones but after the class LEA can investigate mobile devices at ease.

Mobile Phone Interrogation n n Mobile phones keep an activity trail that can be uncovered with specialist tools. Law enforcement can interrogate handset including i. Phones, Blackberry and Androids. Other mobile devices such as i. Pads, i. Pods and can also be investigated. n Texts, photos and file exchanges via popular apps such as Whats. App, . Messenger and Skype can be stored on modern mobile phones along with web browsing, social media activity, contact lists, videos and emails. Even the most basic phones keep call logs and SMS traffic.

Digital Mobile Forensic Investigation Tools for law enforcement officers n The list is a mix of open source and commercial digital forensics tools used in forensics tools are typically platform-specific and are configured to address Smartphone analysis n Bit. Pim n Mobile Internal Acquisition Tool (MIAT) n TULP 2 G n Katana Forensics’ Lantern Lite Imager n Dr. Fone n Bulk Extractor n Oxygen n Android Data Recovery. Go here for Free forensic tools

Mobile Android Investigation Steps To Recover Deleted Text Messages On Android using Android Data Recovery. n Step 1. First of all in your windows PC download and install the tool n n Step 2. Now you have to enable USB debugging in your android for that you have to go to Settings -> About Phone -> Build Number and tap on it 7 -10 times. Now you will see developer option in your settings and tap on it and scroll down and enable USB Debugging. . Step 3. Now launch the tool that you installed in your PC and from there select your android version and proceed by connecting your android to your PC via USB cable. Now select the messages at the recovery section and then simply click on next. Step 4. Now the Android Data Recovery software will ask you to Allow/Grant/ Authorize the access in order to get the privilege to scan SMS data. simply allow it. Step 5. Now after the scan gets completed you will see all the deleted text messages from the android device, click on the items you want to restore and then click on “Recover” button.
Computer Forensics n n n The general definition of computer forensics is the processes and investigative methods used to find digital evidence and prepare it for legal proceedings. The more in-depth definition includes the preservation of media and data, identification of computer-related evidence, extraction of the data and interpretation. Whatever people do on computers and other digital devices, they leave tell-tale traces behind. Digital Forensics can track that activity and present you with a clear report of what happened and when.
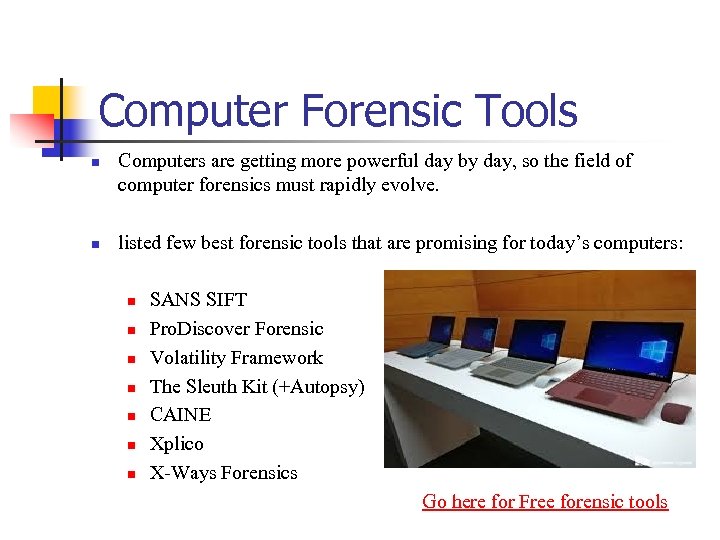
Computer Forensic Tools n n Computers are getting more powerful day by day, so the field of computer forensics must rapidly evolve. listed few best forensic tools that are promising for today’s computers: SANS SIFT n Pro. Discover Forensic n Volatility Framework n The Sleuth Kit (+Autopsy) n CAINE n Xplico n X-Ways Forensics Go here for Free forensic tools n
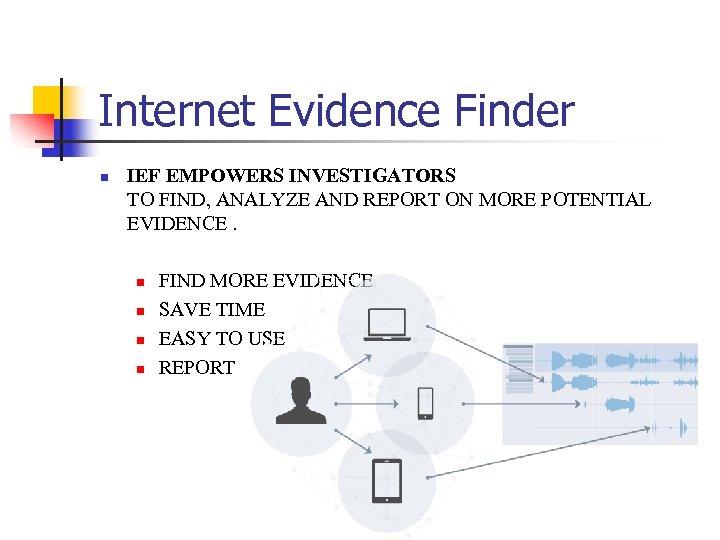
Internet Evidence Finder n IEF EMPOWERS INVESTIGATORS TO FIND, ANALYZE AND REPORT ON MORE POTENTIAL EVIDENCE. n n FIND MORE EVIDENCE SAVE TIME EASY TO USE REPORT

Email tracking and tracing n n n . Emails have become one of the most helpful means to communicate and share information. But along with its positive sides, emails are also very frequently used by the digital criminals in committing digital crimes. An email consists of three vital components: the envelope, the header(s), and the body of the message. n The envelope is something that an email user will never see since it is part of the internal process by which an email is routed. n The body is the part that we always see as it is the actual content of the message contained in the email. n The header(s), the third component of an email, is perhaps a little more difficult to explain, though it is arguably the most interesting part of an email. (A header is the unseen part of every sent and received email
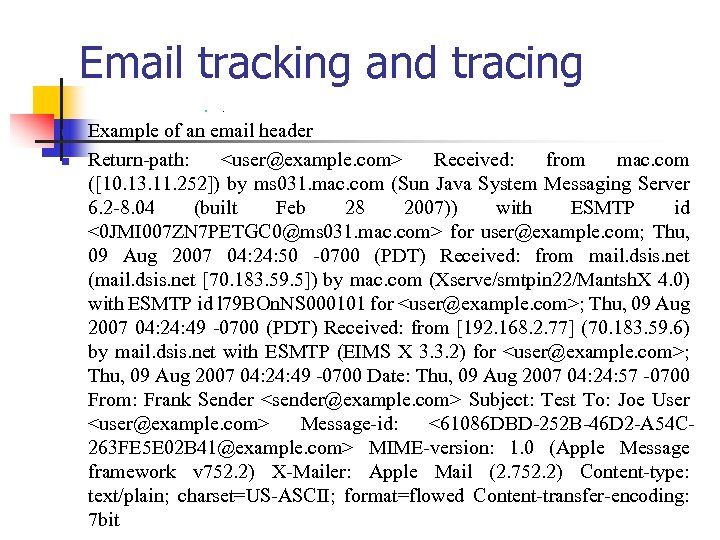
Email tracking and tracing n n n . Example of an email header Return-path: <user@example. com> Received: from mac. com ([10. 13. 11. 252]) by ms 031. mac. com (Sun Java System Messaging Server 6. 2 -8. 04 (built Feb 28 2007)) with ESMTP id <0 JMI 007 ZN 7 PETGC 0@ms 031. mac. com> for user@example. com; Thu, 09 Aug 2007 04: 24: 50 -0700 (PDT) Received: from mail. dsis. net (mail. dsis. net [70. 183. 59. 5]) by mac. com (Xserve/smtpin 22/Mantsh. X 4. 0) with ESMTP id l 79 BOn. NS 000101 for <user@example. com>; Thu, 09 Aug 2007 04: 24: 49 -0700 (PDT) Received: from [192. 168. 2. 77] (70. 183. 59. 6) by mail. dsis. net with ESMTP (EIMS X 3. 3. 2) for <user@example. com>; Thu, 09 Aug 2007 04: 24: 49 -0700 Date: Thu, 09 Aug 2007 04: 24: 57 -0700 From: Frank Sender <sender@example. com> Subject: Test To: Joe User <user@example. com> Message-id: <61086 DBD-252 B-46 D 2 -A 54 C 263 FE 5 E 02 B 41@example. com> MIME-version: 1. 0 (Apple Message framework v 752. 2) X-Mailer: Apple Mail (2. 752. 2) Content-type: text/plain; charset=US-ASCII; format=flowed Content-transfer-encoding: 7 bit

Email trace to location n In the following steps n you'll learn how to find and copy an email header and paste it into the Trace Email Analyzer to get the sender's IP address and track the source. n We track down (or trace) where an email that you send or received came from

Email trace to location n To find the IP address of a received email you're curious about, open the email and look for the header details. How you find that email's header depends on the email program you use. Do you use Gmail or Yahoo? Hotmail or Outlook? For example, if you're a Gmail user, here are the steps you'd take:

Email trace to location n For example, if you're a Gmail user, here are the steps. n n n Open the message you want to view Click the down arrow next to the "Reply" link Select "Show Original" to open a new window with the full headers Paste on the analyzer here 1 Paste on the analyzer here 2
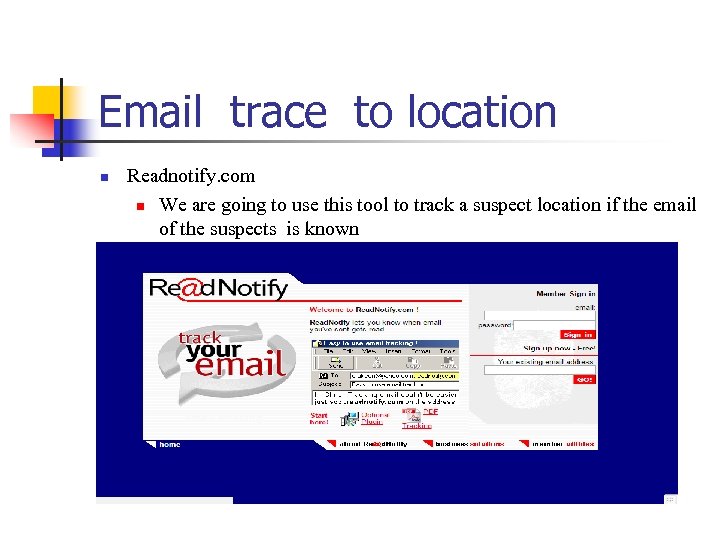
Email trace to location n Readnotify. com n We are going to use this tool to track a suspect location if the email of the suspects is known

IP tracing to location n How to trace hackers and suspect n to know about the people who have sent malicious messages or making any threatening post, suspected criminal We use this tool to trace any known IP.
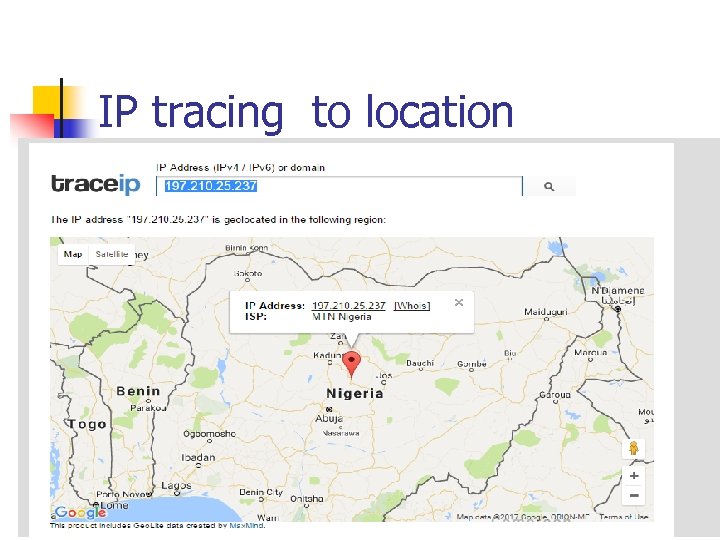
IP tracing to location

WEBSITE INVESTIGATION INTRO n n Investigation of almost all crimes benefits from evidence collected from the Web or electronic devices used for sto ring, sending, or transferring data, information, communication, and imagery. Some information may be directly related to the crime, or act as supplemental or circumstantial evidence. The following list of crimes are those where evidence is most likely to be found from Web sources and the information contained within. .

WHOIS What is WHOIS data used for, by law enforcement agencies? n To establish or look into an identity in cyberspace, and as part of an incident response following an Internet or computer attack. (Security professionals and law enforcement agents use WHOIS to identify points of contact for a domain name. ) n To gather investigative leads (i. e. , to identify parties from whom additional information might be obtained). Law enforcement agents use WHOIS to find email addresses and attempt to identify the location of an alleged perpetrator of a crime involving fraud. n To investigate spam, law enforcement agents look to the WHOIS database to collect information on the website advertised in the spam.

WEBSITE INVESTIGATION n Law enforcement can find out who was really behind a website or owner of a fraudulent website? n Whatever the reason, the internet has a system that will show you who owns a domain and with contacts address. This system is called WHOIS (pronounced as two words 'who-is'). n Practical application n Example 1 case study n Example 2 case study








Training Contents Cybersecurity & Cybercrime • Introduction. • What is cybercrime • History of cybercrime • Categories of cybercrime. • Types of cybercrime • Cybercriminals • Prevention. • Definition of Cybersecurity • Nigeria Cybercrime Law • Conclusion Digital Forensics • Mobile Phone Interrogation • Computer Interrogation • Email tracking and tracing • IP tracing to geolocation • Website investigation Social Media Analysis & Investigations • Media & Platforms • Tools for Investigations Cell Tower Analysis & Investigations • Call Data Records{CDR}analysis • Triangulation with coordinates • IMEI investigation • Mobile phone tracking • Phone number tracking


Social Media Analysis (SMA) Investigations and Intelligence Gathering



ATTENTION & CAUTION! Police Questioning a Robber: n *Police: * How did you come to know that there was no one in the house. n *Robber: * The update of the entire family with 15 photos was available on Facebook. *"Enjoying Holidays away from home for one week". * n n Think about this seriously. Be careful what you put on facebook. Discuss this with your children & wards. *Stop sharing personal information on the social media. !!*

Practical applications n n Law enforcement agencies uses SMA to identify Suspects, criminal and terrorist networks from traces of communication that they collect; and then identify key players in these networks. Social Network Sites like Facebook use basic elements of SNA to identify and recommend potential friends based on friends-of-friends

Social Media Platform üFacebook üInstagram üTwitter üLinked. In üYou. Tube üTumblr üBlogs üWeb pages & websites üGoogle+ üPintrest üNewsgroups
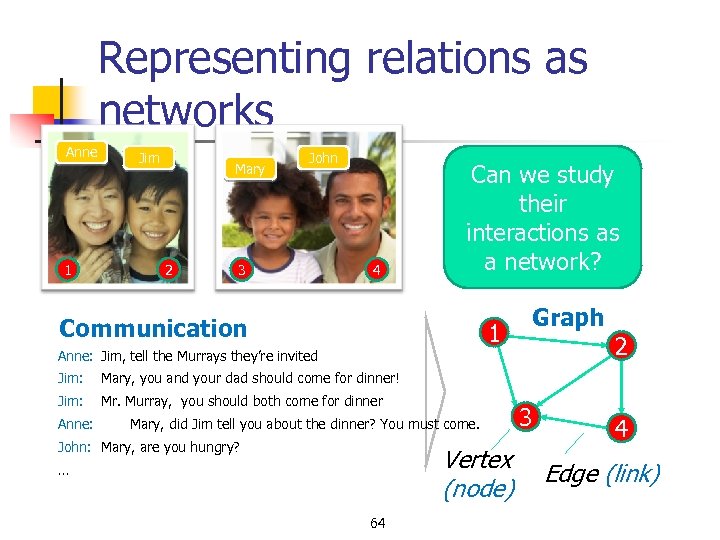
Representing relations as networks Anne 1 Jim Mary 2 John 3 4 Can we study their interactions as a network? Communication 1 Graph 2 Anne: Jim, tell the Murrays they’re invited Jim: Mary, you and your dad should come for dinner! Jim: Mr. Murray, you should both come for dinner Anne: Mary, did Jim tell you about the dinner? You must come. John: Mary, are you hungry? Vertex (node) … 64 3 4 Edge (link)

Tools and Recommendations for Social Media Investigations n n n Harnessing the social web has become an integral part of work for any investigator. So much information is being shared with smartphones and social media that it’s absolutely impossible to ignore. And the amount of data is growing every day. While there is no “magic bullet” or “secret sauce” to conducting these social media investigations, there are some tools that can help with the process. Tools n Law Enforcement Online Requests n Reverse Image Search n Facebook Graph Search n Spokeo n Knowem n Instagram Search n Sweat

Law Enforcement Online Requests n Lawenforcement agent who is authorized to gather evidence in connection with an official investigation, can use the tool to get information about a suspect from facebook Online Requests

Reverse Image Search n n n With Google’s reverse image search, you can scour the Internet for any instances in which a particular photo has been published. It will find the exact matching photo or any similar photo that has been posted on Facebook, Instagram, blogs or anywhere else on the Internet, for that matter. It’s not perfect, but it’s an incredibly powerful tool if you are trying to find social profiles of individuals or websites in the deep dark web. How can this help you? Most people don’t bother changing the profile picture for the various social networks they use, often using the same exact photo and posting the exact same pictures. Over the course of the past several years, I have found people on pornography websites, people using pseudonyms and even a collection of completely fake profiles to try to scam people out of money. [Tineye is also another reverse image search, but I have found it to be much less successful at finding photographs than Google’s reverse image search. ]

Facebook Graph Search n n n n Facebook announced Facebook Graph Search, which is effectively a search engine within Facebook to help find information more easily. So, for example, if you need to find someone with the name Lucinda who lived near Canton, Ohio, you would type “People named ‘Lucinda’ who live near Canton, Ohio” in the Facebook search bar. Simple as that. To find someone, you can use a variety of search terms, such as: Friends of people named “first. name last. name” Photos of people named “first. name last. name” People who have visited “place name” It’s an incredibly powerful tool, [SMI Aware has a great primer on how to utilize Facebook Graph Search more effectively. ] Bonus tip: Even if the person you are looking for has blocked himself or herself from public view, you may be able to find him or her through family members.

Spokeo n n Spokeo has been around the block for a few years. Its main benefit is that it can search 60 of the top social media sites to determine whether a particular email address or person is linked to a social media profile utilizing an email address. This is especially helpful when the person may be using some type of pseudonym. Spokeo doesn’t always work. In fact, it rarely does. But when it works, it can be an absolute gold mine.

Knowem n n This may come as a surprise to you, but not everyone uses his or her real name on the Internet. People use an alter ego, so to speak. While the person you are searching for may go by Tom Jones in real life, he may go by Mr. Lions 100 on the Internet. It certainly makes it more difficult to track down these people, but one thing we have going for us is that people are creatures of habit. Once they’ve got a username, they usually stick with it. So if a person is known as Mr. Lions 100 on Instagram, there is a good chance that he is known as Mr. Lions 100 on many other sites as well. That’s where Knowem comes in. With Knowem, you can search over 500 popular social networks to see whether that particular name has been taken. If you get a hit with Knowem, you’ve now got a whole new rabbit hole to go down
Instagram Search n n If a picture is worth a thousand words, then Instagram, with more than 20 billion photos, is worth 20 trillion words. With more than 200 million active users, Instagram is a phenomenal (and growing) source for investigators. The trouble is that Instagram was built as a mobile platform, and unlike Facebook, it doesn’t have a very good “desktop” version to search and review with. That’s where a tool such as Instagram for Chrome can harness the power of searching Instagram on your desktop. We recently conducted an investigation to try to find individuals who were connected to a particular individual and a particular address. Utilizing Instagram for Chrome, we were able search hashtags, GPS tags and user tags in order to develop a full picture of close confidants and groups of individuals who were a regular part of this individual’s entourage.

Sweat n n n Everyone loves the magic bullet or the secret sauce. But you know what? It’s not always that easy. Sometimes you just need some good old-fashioned time and sweat. The social web is not structured in a way that lets you click a few buttons and have everything at your fingertips. If you really want to know what someone has been saying in his or her 42, 301 tweets, you are going to have to read them. All of them.

Join the Social Media Party n The only way you are going to become a good social media investigator is to n n n join the party. Know how people interact, get attention, post, like/heart/retweet, friend, etc. If you don’t know how the individual social media sites work, it’s really hard to know what their capabilities are.

In Closing …conclusion n There are hundreds of social media sites, each with its own intricacies. And they are changing every day. There really is no magic bullet, but in order to have a better understanding of social media investigations, you really need to know how each of them works.

Training Contents Cybersecurity & Cybercrime • Introduction. • What is cybercrime • History of cybercrime • Categories of cybercrime. • Types of cybercrime • Cybercriminals • Prevention. • Definition of Cybersecurity • Nigeria Cybercrime Law • Conclusion Digital Forensics • Mobile Phone Interrogation • Computer Interrogation • Email tracking and tracing • IP tracing to geolocation • Website investigation Social Media Analysis & Investigations • Media & Platforms • Tools for Investigations Cell Tower Analysis & Investigations • Call Data Records{CDR}analysis • Triangulation with coordinates • IMEI investigation • Mobile phone tracking • Phone number tracking

Cell Tower Analysis Cell tower analysis & Investigation will help Police Dept, Law Enforcement Agencies, Security Agencies.

Cell Tower Analysis n Cell Site analysis places the geographical location of mobile phones with remarkable accuracy. n Whenever calls are made, n texts are sent or web browsing occurs, n records are kept by service providers. q Call Details Records These can be used to plot the movements of a mobile phone at given dates and times. Together with on-site signal coverage measurements, cell site location data can pin point whether a phone was at or near a given location during use, information which can be invaluable for prosecutors and investigators seeking to question or verify location of suspected criminal on a skip. . CDR Analysis & Investigation will help Police Dept, Law Enforcement Agencies, Security Agencies.
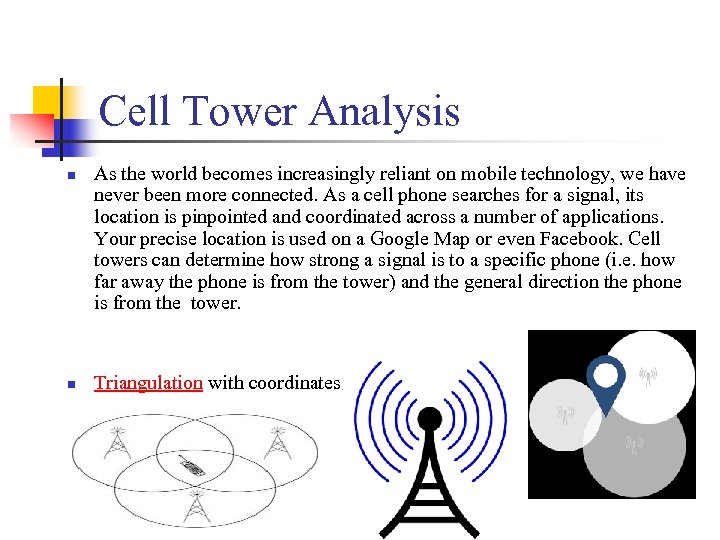
Cell Tower Analysis n n As the world becomes increasingly reliant on mobile technology, we have never been more connected. As a cell phone searches for a signal, its location is pinpointed and coordinated across a number of applications. Your precise location is used on a Google Map or even Facebook. Cell towers can determine how strong a signal is to a specific phone (i. e. how far away the phone is from the tower) and the general direction the phone is from the tower. Triangulation with coordinates

Call Data Records CDR Analysis & Investigation Types of CDR n Personal – CDR of Accused, Suspect or Victim etc n Site – CDR of a particular Tower / BTS n IMEI – CDR of a particular Mobile Handset n IP – Internet Protocol CDR or IPDR Sample CDR Suspect, Victim. Sample CDR Site Tower

IMEI Investigations What Is An IMEI n The International Mobile station Equipment Identity number (IMEI) is a number used to identify a device that uses terrestrial cellular networks. “And what is a terrestrial cellular network? ” you may ask. This is the network you use when you place a call on your cell phone or access an internet connection provided by your cellular carrier through your data plan. It’s called “terrestrial” because it uses planet-side antennas, not satellites, to connect.

IMEI Investigations What Is The Purpose of an IMEI Number? n IMEI numbers have one principal purpose: to identify mobile devices. Their secondary purpose, or intention, is to prevent theft. If a mobile device can be universally identified, a thief cannot change the SIM card on a phone and expect to keep the phone. IMEI numbers are hardcoded into device hardware, making it nearly impossible to change them without somehow damaging the device. n When a carrier knows that a device has been stolen, it can blacklist the IMEI code and lock it out of the network. Later on, it tells other cellular networks to do the same.

IMEI Investigations n Law enforcement can Use IMEI Number to Track suspects

IMEI Investigations n How To Find Your IMEI n The majority of mobile devices will display their IMEI by entering *#06# on the keypad. This is generally enough to reveal the code on older devices and most newer ones too, though you can also use other techniques if you’ve got a phone manufactured by one of the following:
![International Mobile Equipment Identity [IMEI] n n n The IMEI is used for equipment International Mobile Equipment Identity [IMEI] n n n The IMEI is used for equipment](https://present5.com/presentation/fd74d541add0f948533e47a99320e6c7/image-84.jpg)
International Mobile Equipment Identity [IMEI] n n n The IMEI is used for equipment identification. An IMEI uniquely identifies a mobile station as a piece or assembly of equipment. IMEI = TAC + FAC + SNR + sp n n TAC= Type Approval Code (6 digits), determined by GSM body FAC= Final Assembly Code (2 digits), identifies the manufacturer SNR= Serial Number (6 digits), uniquely identifying all equipment within each TAC and FAC sp = Spare for future use (1 digit) 85
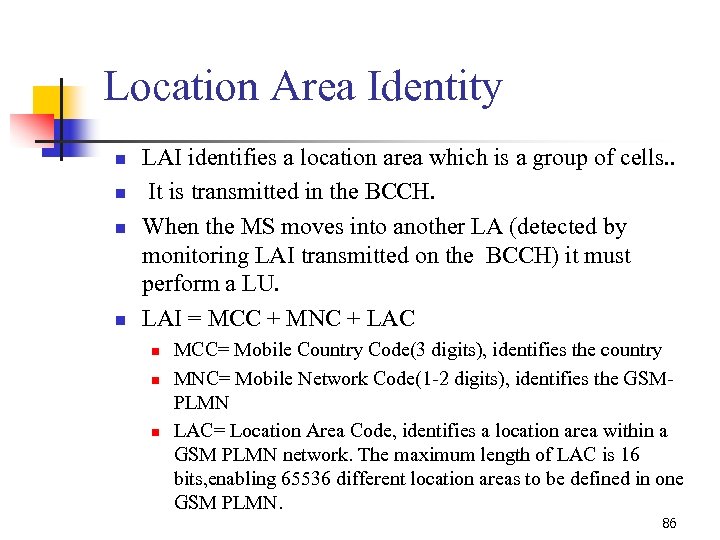
Location Area Identity n n LAI identifies a location area which is a group of cells. . It is transmitted in the BCCH. When the MS moves into another LA (detected by monitoring LAI transmitted on the BCCH) it must perform a LU. LAI = MCC + MNC + LAC n n n MCC= Mobile Country Code(3 digits), identifies the country MNC= Mobile Network Code(1 -2 digits), identifies the GSMPLMN LAC= Location Area Code, identifies a location area within a GSM PLMN network. The maximum length of LAC is 16 bits, enabling 65536 different location areas to be defined in one GSM PLMN. 86

Mobile Phone Tracking n n Track a Cell Phone That’s Not Yours To track Suspect phone under custody , you can simply use a cell phone tracking app such as Spy. Stealth Premium. This is a very small yet powerful app that can be installed in just a few simple steps. The whole installation process takes only 2 -3 minutes to complete. Once installed the app stays hidden on the phone but keeps track of its GPS location. Furthermore it also records call, text messages, social media activity and much more.

Mobile Phone Tracking n n n How Tracking Works? First of all, download and install the tracking app onto the target phone that you wish to track. Have the target phone in your hand for a few minutes until the installation is complete. Finally after installation is done, the tracking process will begin immediately. Recorded logs are silently uploaded to your online account as shown in the demo below. You can login to this online account any time to view the logs containing GPS location and all other activities.

Phone Number Tracking With Triangulation Coordinates n n n Cell Phone Tower Triangulation is use for mobile phone number tracking. It is possible to track down the location of a suspect base on the results of the CDR provided by the phone network provider. Cell tower triangulation is similar to GPS tracking in many ways. Multiple towers are used to track the phone’s location by measuring with time calls was made with from the phone. This is calculated into distance and gives a fairly accurate location of the phone or suspect location Cell tower triangulation provides the ability to track the historic location of the cell phone’s presence. It will then identify where the cell phone was when receiving/making calls, texting, emailing, etc The cell tower triangulation data can be used forensically in many ways to achieve many objectives, i. e. intelligence, criminal location verifications, alibi confirmation, etc.

Phone Number Tracking n Cell Tower Triangulation – How it Works n single-tower location n second cell tower location n third tower is brought into play n Some of the newest cell phones can actually report a GPS location, and this is quite accurate, and doesn’t rely on the cell towers at all.
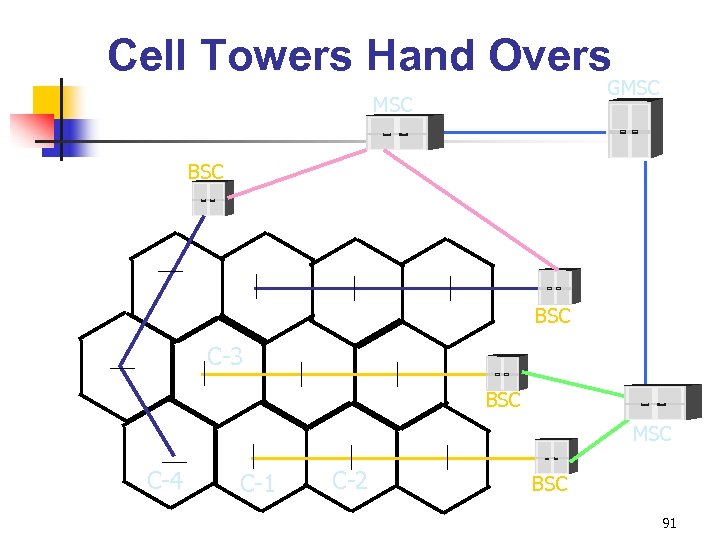
Cell Towers Hand Overs GMSC BSC C-3 BSC MSC C-4 C-1 C-2 BSC 91

Any QUERIES?
fd74d541add0f948533e47a99320e6c7.ppt