160af2d1908a4f323f867f64b3a06c95.ppt
- Количество слайдов: 38
 Large Scale Malicious Code: A Research Agenda N. Weaver, V. Paxson, S. Staniford, R. Cunningham 1
Large Scale Malicious Code: A Research Agenda N. Weaver, V. Paxson, S. Staniford, R. Cunningham 1
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 2
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 2
 Motivation and Goal ● Networking infrastructure is essential to many activities – Address the “worm threat” ● Establish taxonomy for worms ● Motivate Cyber “CDC” ● Establish a road map for research efforts 3
Motivation and Goal ● Networking infrastructure is essential to many activities – Address the “worm threat” ● Establish taxonomy for worms ● Motivate Cyber “CDC” ● Establish a road map for research efforts 3
 Challenges ● Prevention – ● Avoidance – ● i. e. Filter ports Detection – ● i. e. Non-executable stacks i. e. Network telescopes Recovery – i. e. Fix vulnerability 4
Challenges ● Prevention – ● Avoidance – ● i. e. Filter ports Detection – ● i. e. Non-executable stacks i. e. Network telescopes Recovery – i. e. Fix vulnerability 4
 Challenges ● ● Spread speed is faster than human reaction time Further generations of worms address previous counter measurements – Smart guys behind the scene ● Monocultures in today Internet ● People are not sensitive to security 5
Challenges ● ● Spread speed is faster than human reaction time Further generations of worms address previous counter measurements – Smart guys behind the scene ● Monocultures in today Internet ● People are not sensitive to security 5
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 6
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 6
 Taxonomy ● Activation techniques – – Scheduled process – ● Human Self Propagation strategies – – Pre-generated Target Lists – Externally Generated Target Lists – Internal Target Lists – ● Scanning Passive Propagation carriers – Self, Embedded 7
Taxonomy ● Activation techniques – – Scheduled process – ● Human Self Propagation strategies – – Pre-generated Target Lists – Externally Generated Target Lists – Internal Target Lists – ● Scanning Passive Propagation carriers – Self, Embedded 7
 Taxonomy • Motivation and Attackers – – – – Pride and Power Commercial Advantage Extortion, Random Protest Political Protest Terrorism Cyber Warfare • Payloads – – – – – None Opening Backdoors Remote DOS Receive Updates Espionage Data Harvesting Data Damage Hardware Damage Coercion 8
Taxonomy • Motivation and Attackers – – – – Pride and Power Commercial Advantage Extortion, Random Protest Political Protest Terrorism Cyber Warfare • Payloads – – – – – None Opening Backdoors Remote DOS Receive Updates Espionage Data Harvesting Data Damage Hardware Damage Coercion 8
 Ecology of Worms ● Application Design ● Buffer Overflows ● Privileges – Mail worms ● Application Deployment ● Economic Factors ● Monocultures 9
Ecology of Worms ● Application Design ● Buffer Overflows ● Privileges – Mail worms ● Application Deployment ● Economic Factors ● Monocultures 9
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 10
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 10
 Cooperative Information Technology Org. ● CERT/CC – ● IIAP – ● Human analysis and aggregation Human-time analysis ISAC – Practices and background ● FIRST ● Public Mailing Lists 11
Cooperative Information Technology Org. ● CERT/CC – ● IIAP – ● Human analysis and aggregation Human-time analysis ISAC – Practices and background ● FIRST ● Public Mailing Lists 11
 Commercial Entities ● Anti-virus Companies – Computer Anti-Virus Researchers Organization (CARO) ● Network based IDS Vendors ● Centralized Security Monitoring ● Training Organizations ● Limited Scope of Commercial Response – Worm has yet to cause significant damage – No clear way to generate additional revenue 12
Commercial Entities ● Anti-virus Companies – Computer Anti-Virus Researchers Organization (CARO) ● Network based IDS Vendors ● Centralized Security Monitoring ● Training Organizations ● Limited Scope of Commercial Response – Worm has yet to cause significant damage – No clear way to generate additional revenue 12
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 13
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 13
 Cyber CDC ● Identify outbreaks – – ● Develop mechanism for gathering information Sponsor research in automated detection Rapidly analyzing pathogens – – ● Develop analysis tools Understand the harm and spread of pathogens Fighting Infections – Deploy agent that detect, terminate or isolate worms 14
Cyber CDC ● Identify outbreaks – – ● Develop mechanism for gathering information Sponsor research in automated detection Rapidly analyzing pathogens – – ● Develop analysis tools Understand the harm and spread of pathogens Fighting Infections – Deploy agent that detect, terminate or isolate worms 14
 Cyber CDC ● Anticipating new vectors – ● Proactively devising detectors for new vectors – ● Develop analysis modules for IDS Resisting future threats – ● Analyze threat potential of new applications Foster research into resilient application design paradigms How open? 15
Cyber CDC ● Anticipating new vectors – ● Proactively devising detectors for new vectors – ● Develop analysis modules for IDS Resisting future threats – ● Analyze threat potential of new applications Foster research into resilient application design paradigms How open? 15
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 16
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 16
 Vulnerability Prevention Defenses ● Grading potentials – A: high potential, lower cost – B: medium potential or significant cost – C: low potential but high risk 17
Vulnerability Prevention Defenses ● Grading potentials – A: high potential, lower cost – B: medium potential or significant cost – C: low potential but high risk 17
 Vulnerability Prevention Defenses ● Programming Languages and Compilers – Safe C Dialects (C, active area) ● ● Ccured / Cyclone ● – Enforcing type and memory safety [future] extending to C++ Software Fault Isolation (C, active area) ● ● – Memory safe sandboxes Lack of availability of SFI-based systems Stack. Guard (C, active area) ● Compiler calling-convention ● Works well against conventional stack attacks 18
Vulnerability Prevention Defenses ● Programming Languages and Compilers – Safe C Dialects (C, active area) ● ● Ccured / Cyclone ● – Enforcing type and memory safety [future] extending to C++ Software Fault Isolation (C, active area) ● ● – Memory safe sandboxes Lack of availability of SFI-based systems Stack. Guard (C, active area) ● Compiler calling-convention ● Works well against conventional stack attacks 18
 Vulnerability ● Programming Languages and Compilers – Nonexecutable Stacks and Heaps w/ Randomized Layouts (B, mostly engineering) ● ● ● – Randomizing layout Guard pages, exception when accessed No attempt to build such a complete system Monitoring for Policy- and Semantics-Enforcement (B, opportunities for worm specific monitoring) ● ● ● System call patterns (“mimicry” attack) Static analysis [future] increase performance and precision 19
Vulnerability ● Programming Languages and Compilers – Nonexecutable Stacks and Heaps w/ Randomized Layouts (B, mostly engineering) ● ● ● – Randomizing layout Guard pages, exception when accessed No attempt to build such a complete system Monitoring for Policy- and Semantics-Enforcement (B, opportunities for worm specific monitoring) ● ● ● System call patterns (“mimicry” attack) Static analysis [future] increase performance and precision 19
 Vulnerability ● Automatic vulnerability analysis (B, highly difficult, active area) – Discover buffer overflow in C – Sanitized integers from untrusted source – User-supplied pointers for kernel – [future] assemply level – [future] specific patterns of system calls 20
Vulnerability ● Automatic vulnerability analysis (B, highly difficult, active area) – Discover buffer overflow in C – Sanitized integers from untrusted source – User-supplied pointers for kernel – [future] assemply level – [future] specific patterns of system calls 20
 Vulnerability Prevention Defenses ● Privilege Issues – Fine-grained Access Control (C, active area) ● – Code Signing (C, active area) ● – [future] integrating into commodity OS Publi-key authentication Privilege Isolation (C, some active research, difficult) ● Mach kernel 21
Vulnerability Prevention Defenses ● Privilege Issues – Fine-grained Access Control (C, active area) ● – Code Signing (C, active area) ● – [future] integrating into commodity OS Publi-key authentication Privilege Isolation (C, some active research, difficult) ● Mach kernel 21
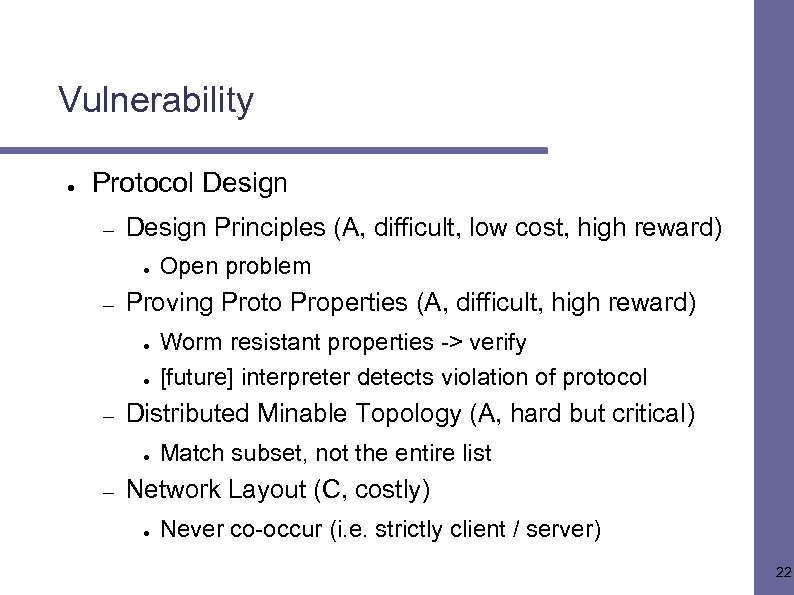 Vulnerability ● Protocol Design – Design Principles (A, difficult, low cost, high reward) ● – Proving Proto Properties (A, difficult, high reward) ● ● – Worm resistant properties -> verify [future] interpreter detects violation of protocol Distributed Minable Topology (A, hard but critical) ● – Open problem Match subset, not the entire list Network Layout (C, costly) ● Never co-occur (i. e. strictly client / server) 22
Vulnerability ● Protocol Design – Design Principles (A, difficult, low cost, high reward) ● – Proving Proto Properties (A, difficult, high reward) ● ● – Worm resistant properties -> verify [future] interpreter detects violation of protocol Distributed Minable Topology (A, hard but critical) ● – Open problem Match subset, not the entire list Network Layout (C, costly) ● Never co-occur (i. e. strictly client / server) 22
 Vulnerability ● Network Provider Practices – Machine Removal (C, already under development) ● ● No standard protocol Implementation Diversity – Monoculture is a dangerous phenomena 23
Vulnerability ● Network Provider Practices – Machine Removal (C, already under development) ● ● No standard protocol Implementation Diversity – Monoculture is a dangerous phenomena 23
 Vulnerability ● Synthetic Polycultures – Synthetic polycultures (C, difficult, may add unpredictability) ● ● ● [future] techniques to develop synthetic polycultures [future] Code obfuscation Economic and Social – Why is Security Hard (B, active area of research) ● [future] understanding of why practices remain so poor 24
Vulnerability ● Synthetic Polycultures – Synthetic polycultures (C, difficult, may add unpredictability) ● ● ● [future] techniques to develop synthetic polycultures [future] Code obfuscation Economic and Social – Why is Security Hard (B, active area of research) ● [future] understanding of why practices remain so poor 24
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 25
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 25
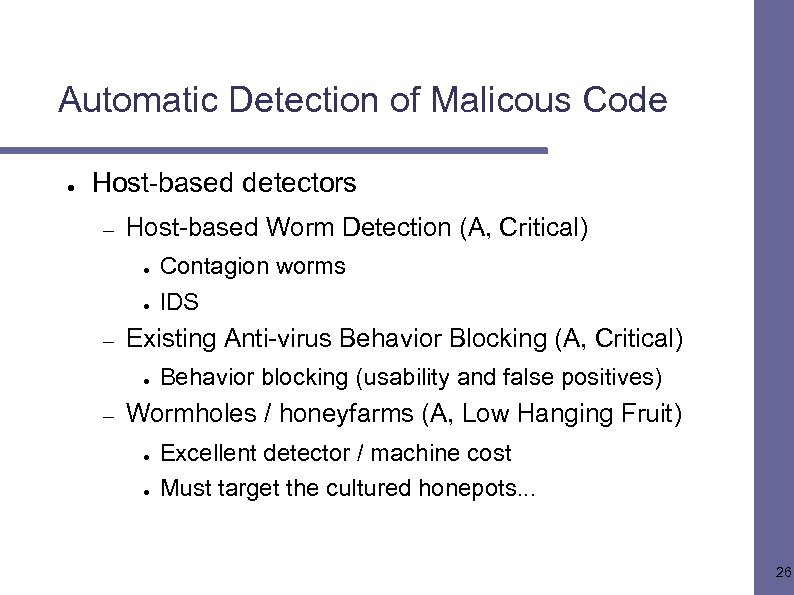 Automatic Detection of Malicous Code ● Host-based detectors – Host-based Worm Detection (A, Critical) ● ● – Existing Anti-virus Behavior Blocking (A, Critical) ● – Contagion worms IDS Behavior blocking (usability and false positives) Wormholes / honeyfarms (A, Low Hanging Fruit) ● ● Excellent detector / machine cost Must target the cultured honepots. . . 26
Automatic Detection of Malicous Code ● Host-based detectors – Host-based Worm Detection (A, Critical) ● ● – Existing Anti-virus Behavior Blocking (A, Critical) ● – Contagion worms IDS Behavior blocking (usability and false positives) Wormholes / honeyfarms (A, Low Hanging Fruit) ● ● Excellent detector / machine cost Must target the cultured honepots. . . 26
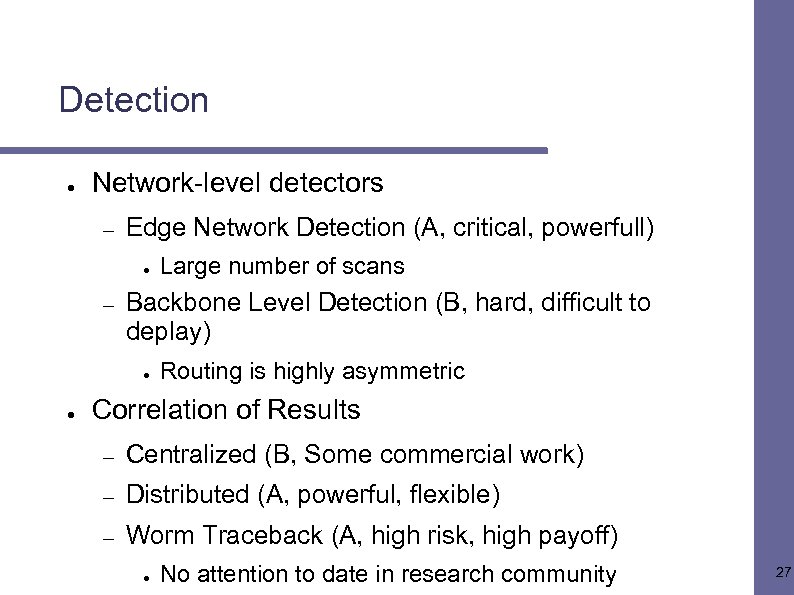 Detection ● Network-level detectors – Edge Network Detection (A, critical, powerfull) ● – Backbone Level Detection (B, hard, difficult to deplay) ● ● Large number of scans Routing is highly asymmetric Correlation of Results – Centralized (B, Some commercial work) – Distributed (A, powerful, flexible) – Worm Traceback (A, high risk, high payoff) ● No attention to date in research community 27
Detection ● Network-level detectors – Edge Network Detection (A, critical, powerfull) ● – Backbone Level Detection (B, hard, difficult to deplay) ● ● Large number of scans Routing is highly asymmetric Correlation of Results – Centralized (B, Some commercial work) – Distributed (A, powerful, flexible) – Worm Traceback (A, high risk, high payoff) ● No attention to date in research community 27
 Automated Response to Malicious Code ● Host-Based (B, overlaps with personal firewall) – ● Edge Network (A, poweful, flexible) – ● ● [future] Filter traffic (side effects. . . ) Backbone/ISP Level (B, difficult, deployment issues) – ● Open question [future] Limitation of outbound scanning National Boundaries (C, too coarse grained) Graceful Degradation and Containment (B, mostly engineering) – [future] Quarantine sections 28
Automated Response to Malicious Code ● Host-Based (B, overlaps with personal firewall) – ● Edge Network (A, poweful, flexible) – ● ● [future] Filter traffic (side effects. . . ) Backbone/ISP Level (B, difficult, deployment issues) – ● Open question [future] Limitation of outbound scanning National Boundaries (C, too coarse grained) Graceful Degradation and Containment (B, mostly engineering) – [future] Quarantine sections 28
 Aids to Manual Analysis of Malicious Code ● ● Collaborative Code Analysis Tool (A, scaling is important, some ongoing research) Higher Level Analysis (B, important, Halting problem imposes limitations Hybrid Static-Dynamic Analysis (A, hard but valuable) Visualization (B, mostly educational value) – [future] Real-time analysis – [future] what information might be gathered 29
Aids to Manual Analysis of Malicious Code ● ● Collaborative Code Analysis Tool (A, scaling is important, some ongoing research) Higher Level Analysis (B, important, Halting problem imposes limitations Hybrid Static-Dynamic Analysis (A, hard but valuable) Visualization (B, mostly educational value) – [future] Real-time analysis – [future] what information might be gathered 29
 Aids to Recovery ● ● ● Anti-worms (C, impractical, illegal) Patch distribution in a hostile environment (C, already evolving commercially) Updating in a hostile environment (C, hard engineering, already evolving) – Metamorphic code to insert a small bootstrap program 30
Aids to Recovery ● ● ● Anti-worms (C, impractical, illegal) Patch distribution in a hostile environment (C, already evolving commercially) Updating in a hostile environment (C, hard engineering, already evolving) – Metamorphic code to insert a small bootstrap program 30
 Policy considerations ● Privacy and Data Analysis ● Obscurity ● Internet Sanitation – ● Scan limiters The “Closed” Alternative – Apply topological restrictions 31
Policy considerations ● Privacy and Data Analysis ● Obscurity ● Internet Sanitation – ● Scan limiters The “Closed” Alternative – Apply topological restrictions 31
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 32
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 32
 Challenging Problems ● Common evaluation framework – – Finding proper level of abstraction for analysis – ● DARPA IDS evaluation Limit resource available to attacker Milestones for detection – Sensitivity to presence – False positive – Distortion resistant 33
Challenging Problems ● Common evaluation framework – – Finding proper level of abstraction for analysis – ● DARPA IDS evaluation Limit resource available to attacker Milestones for detection – Sensitivity to presence – False positive – Distortion resistant 33
 Challenging Problems ● Milestones for analysis – Strategize vs. Understanding – State of practice: Identifying vs. Reverse engineering – Metrics: accuracy, completeness, speed, usability – Milestone: progressively bigger variety of worms ● Detecting targeted worms ● Tools for validating defenses – Worm Simulation Environment – Internet Wide Worm Testbed (A, essential) – Testing in the Wild (A, essential) 34
Challenging Problems ● Milestones for analysis – Strategize vs. Understanding – State of practice: Identifying vs. Reverse engineering – Metrics: accuracy, completeness, speed, usability – Milestone: progressively bigger variety of worms ● Detecting targeted worms ● Tools for validating defenses – Worm Simulation Environment – Internet Wide Worm Testbed (A, essential) – Testing in the Wild (A, essential) 34
 Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 35
Contents ● ● ● Overview Worms: Type, Attackers, Enabling Factors Existing Practices and Models Cyber CDC Vulnerability Prevention Defenses Automatic Detection of Malicious Code Automated Response to Malicious Code Aid to Manual Analysis of Malicious Code Aid to Recovery Policy Considerations Validation and Challenging Problems Conclusion 35
 Conclusions ● Worms are a significant thread ● Limited number of strategies ● Inadequate defensive infrastructure ● Cyber CDC – ● Prevention role Huge potential damage 36
Conclusions ● Worms are a significant thread ● Limited number of strategies ● Inadequate defensive infrastructure ● Cyber CDC – ● Prevention role Huge potential damage 36
 Problems ● Build tomorrows security system based on todays worm technologies – – ● Will always be one step behind Reactive Need to address root cause instead of patching things – Prevention 37
Problems ● Build tomorrows security system based on todays worm technologies – – ● Will always be one step behind Reactive Need to address root cause instead of patching things – Prevention 37
 ? 38
? 38


