bcb525a53db2fa949fb256e0b9fec957.ppt
- Количество слайдов: 32
 KÜRT COMPUTER RT. COMPUTER AND AUTOMATION RESEARCH INSTITUTE (MTA SZTAKI) UNIVERSITY OF VESZPRÉM MATHEMATICS AND COMPUTING DEPARTMENT Information Technology Security Technology and Data Insurance KÜRT Computer National Research and Development Program Project leader Sándor KÜRTI dr. KÜRT Computer Rt. Veszprémi Egyetem MTA SZTAKI
KÜRT COMPUTER RT. COMPUTER AND AUTOMATION RESEARCH INSTITUTE (MTA SZTAKI) UNIVERSITY OF VESZPRÉM MATHEMATICS AND COMPUTING DEPARTMENT Information Technology Security Technology and Data Insurance KÜRT Computer National Research and Development Program Project leader Sándor KÜRTI dr. KÜRT Computer Rt. Veszprémi Egyetem MTA SZTAKI
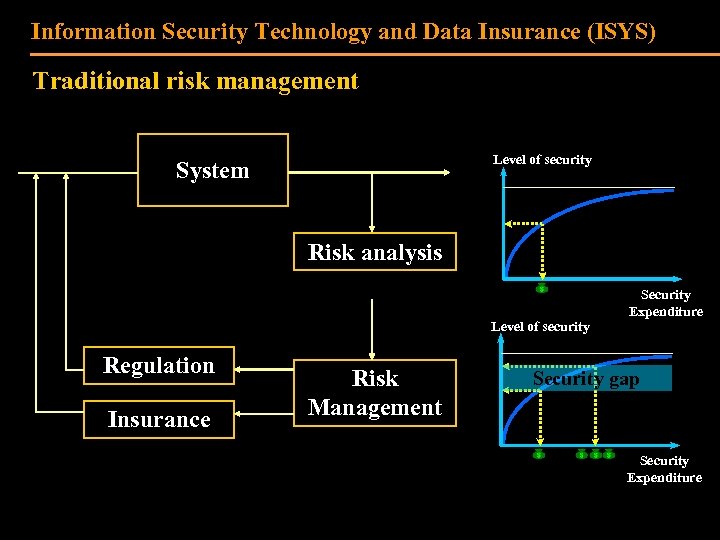 Information Security Technology and Data Insurance (ISYS) Traditional risk management Level of security System Risk analysis Level of security Regulation Insurance Risk Management Security Expenditure Security gap Security Expenditure
Information Security Technology and Data Insurance (ISYS) Traditional risk management Level of security System Risk analysis Level of security Regulation Insurance Risk Management Security Expenditure Security gap Security Expenditure
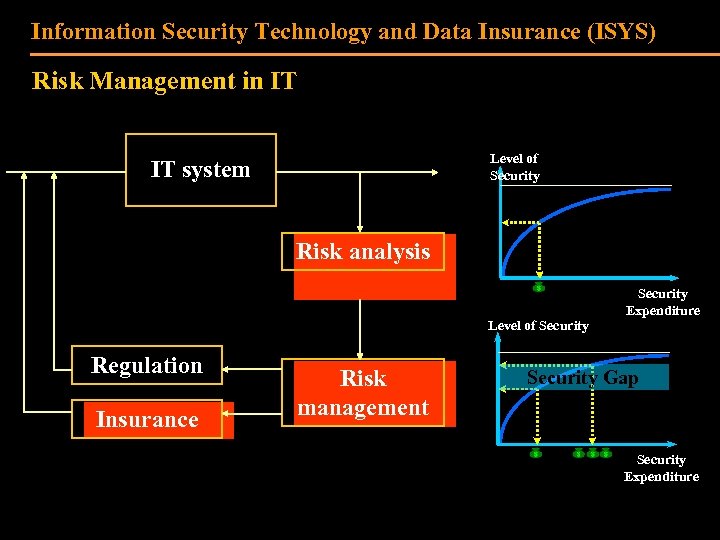 Information Security Technology and Data Insurance (ISYS) Risk Management in IT Level of Security IT system Risk analysis Level of Security Regulation Insurance Risk management Security Expenditure Security Gap Security Expenditure
Information Security Technology and Data Insurance (ISYS) Risk Management in IT Level of Security IT system Risk analysis Level of Security Regulation Insurance Risk management Security Expenditure Security Gap Security Expenditure
 Information Security Technology and Data Insurance (ISYS) Research Targets • Determination of value of information • Development of an up-to-date IT security technology • Development of a comprehensive e-Risk management program – Network security applications – Computer-based e-Insurance methodology
Information Security Technology and Data Insurance (ISYS) Research Targets • Determination of value of information • Development of an up-to-date IT security technology • Development of a comprehensive e-Risk management program – Network security applications – Computer-based e-Insurance methodology
 Information Security Technology and Data Insurance (ISYS) Strengths of the project 1. Technological backgrounds. 2. High level project management practice. 3. Database of information technology catastrophes and the reasons of data loss. 4. High level mathematical background.
Information Security Technology and Data Insurance (ISYS) Strengths of the project 1. Technological backgrounds. 2. High level project management practice. 3. Database of information technology catastrophes and the reasons of data loss. 4. High level mathematical background.
 Information Security Technology and Data Insurance (ISYS) 2. Mathematical researches in the Risk analysis area • Processing of multi-valued statistical data • Examination of internal relationships, determination of background variables • Determination of quantitative dependencies • Visualization of connections with introduction of new variables • Determination of the value of the risk
Information Security Technology and Data Insurance (ISYS) 2. Mathematical researches in the Risk analysis area • Processing of multi-valued statistical data • Examination of internal relationships, determination of background variables • Determination of quantitative dependencies • Visualization of connections with introduction of new variables • Determination of the value of the risk
 Information Security Technology and Data Insurance (ISYS) First Phase: Information Collection (data security issues) • Scientific processing of data recovery data set • Planning of the database structure • Analysis of the causes of data losses and data crimes • Starting of the statistical analysis
Information Security Technology and Data Insurance (ISYS) First Phase: Information Collection (data security issues) • Scientific processing of data recovery data set • Planning of the database structure • Analysis of the causes of data losses and data crimes • Starting of the statistical analysis
 Information Security Technology and Data Insurance (ISYS) Scientific processing of data recovery database • Analysis of possible damages of data storing media • Analysis of the possible data backup and recovery methodologies • Collecting of paper-based and electronic data recovery information
Information Security Technology and Data Insurance (ISYS) Scientific processing of data recovery database • Analysis of possible damages of data storing media • Analysis of the possible data backup and recovery methodologies • Collecting of paper-based and electronic data recovery information
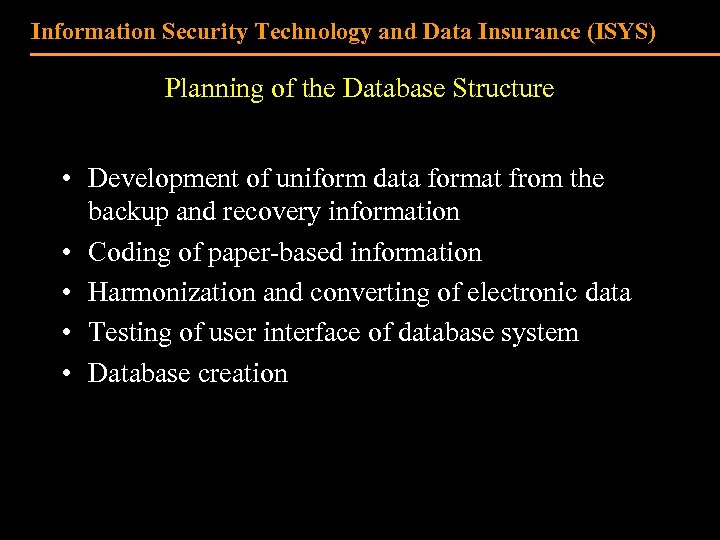 Information Security Technology and Data Insurance (ISYS) Planning of the Database Structure • Development of uniform data format from the backup and recovery information • Coding of paper-based information • Harmonization and converting of electronic data • Testing of user interface of database system • Database creation
Information Security Technology and Data Insurance (ISYS) Planning of the Database Structure • Development of uniform data format from the backup and recovery information • Coding of paper-based information • Harmonization and converting of electronic data • Testing of user interface of database system • Database creation
 Information Security Technology and Data Insurance (ISYS) Analysis of the causes of data losses and data crimes • • Analysis of international trends Analysis of the Hungarian trends Data loss hardware causes (appr. 70%) Data crimes internal workers (appr. 77%)
Information Security Technology and Data Insurance (ISYS) Analysis of the causes of data losses and data crimes • • Analysis of international trends Analysis of the Hungarian trends Data loss hardware causes (appr. 70%) Data crimes internal workers (appr. 77%)
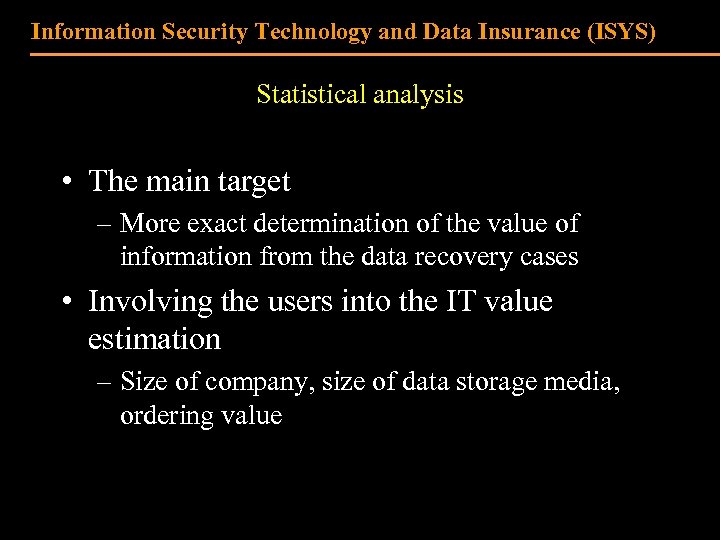 Information Security Technology and Data Insurance (ISYS) Statistical analysis • The main target – More exact determination of the value of information from the data recovery cases • Involving the users into the IT value estimation – Size of company, size of data storage media, ordering value
Information Security Technology and Data Insurance (ISYS) Statistical analysis • The main target – More exact determination of the value of information from the data recovery cases • Involving the users into the IT value estimation – Size of company, size of data storage media, ordering value
 Information Security Technology and Data Insurance (ISYS) Assessment of the first phase • • Project tasks were done The data recovery database is operable Scientifically valuable results (publications) Initialization of statistical analyses for assisting the definition of value of information and risks
Information Security Technology and Data Insurance (ISYS) Assessment of the first phase • • Project tasks were done The data recovery database is operable Scientifically valuable results (publications) Initialization of statistical analyses for assisting the definition of value of information and risks
 Information Security Technology and Data Insurance (ISYS) Phase 2: Production of knowledge base • Converting recovery database into the initial knowledge base • Cryptographic protocol errors, case studies • Assessment of market needs and possibilities • Continuation of statistical analysis
Information Security Technology and Data Insurance (ISYS) Phase 2: Production of knowledge base • Converting recovery database into the initial knowledge base • Cryptographic protocol errors, case studies • Assessment of market needs and possibilities • Continuation of statistical analysis
 Information Security Technology and Data Insurance (ISYS) Converting recovery database into the initial knowledge base • Observation matrix – Knowledge base format • • Identifiers Company data (industrial sector, size) Operating system information Causes of data losses Recoverable/Non-recoverable Ordered/ Not-ordered Price of data recovery action
Information Security Technology and Data Insurance (ISYS) Converting recovery database into the initial knowledge base • Observation matrix – Knowledge base format • • Identifiers Company data (industrial sector, size) Operating system information Causes of data losses Recoverable/Non-recoverable Ordered/ Not-ordered Price of data recovery action
 Information Security Technology and Data Insurance (ISYS) Cryptographic protocol errors, case studies • Contingencies of cryptographic systems – Assessment for the risk management • Case studies • Assessments, statistical analysis • Legal issues – Hungarian and international (EU) regulations • Assessment of data insurance possibilities
Information Security Technology and Data Insurance (ISYS) Cryptographic protocol errors, case studies • Contingencies of cryptographic systems – Assessment for the risk management • Case studies • Assessments, statistical analysis • Legal issues – Hungarian and international (EU) regulations • Assessment of data insurance possibilities
 Information Security Technology and Data Insurance (ISYS) Assessment of market needs and possibilities • Data insurance possibilities (Hungary, international) – – Needs Concurrent products Client preferences User groups • Market possibilities – Methodology for the insurance companies – Methodology for IT companies (risk analysis)
Information Security Technology and Data Insurance (ISYS) Assessment of market needs and possibilities • Data insurance possibilities (Hungary, international) – – Needs Concurrent products Client preferences User groups • Market possibilities – Methodology for the insurance companies – Methodology for IT companies (risk analysis)
 Information Security Technology and Data Insurance (ISYS) Continuation of statistical analysis • Development a statistical model • Simulation on the data recovery data set – The observatory matrix gives a solid base for the statistical analysis • The simulation tool proofs the goodness of the statistical analysis
Information Security Technology and Data Insurance (ISYS) Continuation of statistical analysis • Development a statistical model • Simulation on the data recovery data set – The observatory matrix gives a solid base for the statistical analysis • The simulation tool proofs the goodness of the statistical analysis
 Information Security Technology and Data Insurance (ISYS) Results of the 2 nd phase • Project tasks were done • Scientifically valuable results (publications) • High level analysis of the weak points of the cryptographic systems • Market analysis — good base for product development and analysis • The next step in ISYS development is the development of Business Continuity Plan and Disaster Recovery Plan and an insurance module
Information Security Technology and Data Insurance (ISYS) Results of the 2 nd phase • Project tasks were done • Scientifically valuable results (publications) • High level analysis of the weak points of the cryptographic systems • Market analysis — good base for product development and analysis • The next step in ISYS development is the development of Business Continuity Plan and Disaster Recovery Plan and an insurance module
 Information Security Technology and Data Insurance (ISYS) 3 rd Project Phase: Statistical Analysis, Summary of Methodologies • Collection and examination of multi-valued statistical methods • Assessments • Development of algorithms
Information Security Technology and Data Insurance (ISYS) 3 rd Project Phase: Statistical Analysis, Summary of Methodologies • Collection and examination of multi-valued statistical methods • Assessments • Development of algorithms
 Information Security Technology and Data Insurance (ISYS) Collection and examination of multi-valued statistical methods • Method selection – Single-valued – Multivalued • Strategy for assessments – Statistical analysis on the stored data recovery data (10, 000 cases)
Information Security Technology and Data Insurance (ISYS) Collection and examination of multi-valued statistical methods • Method selection – Single-valued – Multivalued • Strategy for assessments – Statistical analysis on the stored data recovery data (10, 000 cases)
 Information Security Technology and Data Insurance (ISYS) Assessments • Time functions of data losses • Recoverable/ordered recovery cases • Analysis of data recovery cases – Business strategy analysis – Analysis of data insurance possibilities
Information Security Technology and Data Insurance (ISYS) Assessments • Time functions of data losses • Recoverable/ordered recovery cases • Analysis of data recovery cases – Business strategy analysis – Analysis of data insurance possibilities
 Information Security Technology and Data Insurance (ISYS) Development of algorithms • Extension of examination methods based on censored sample • Examination of the goodness of the other analysis and solutions • Single- and multi-valued analysis
Information Security Technology and Data Insurance (ISYS) Development of algorithms • Extension of examination methods based on censored sample • Examination of the goodness of the other analysis and solutions • Single- and multi-valued analysis
 Information Security Technology and Data Insurance (ISYS) Evaluation of the 3 rd phase • Scientifically relevant results (publications) • Business decisions were made based on the statistical results (in the project and in KÜRT) • Solid base for the further developments in value estimations and insurance strategies
Information Security Technology and Data Insurance (ISYS) Evaluation of the 3 rd phase • Scientifically relevant results (publications) • Business decisions were made based on the statistical results (in the project and in KÜRT) • Solid base for the further developments in value estimations and insurance strategies
 Information Security Technology and Data Insurance (ISYS) 4 th Phase: Quality Management • IT quality management – IT system parts – IT business processes – Cryptographic processes and solutions • New developments in quality management, further improvements in our system
Information Security Technology and Data Insurance (ISYS) 4 th Phase: Quality Management • IT quality management – IT system parts – IT business processes – Cryptographic processes and solutions • New developments in quality management, further improvements in our system
 Information Security Technology and Data Insurance (ISYS) IT Quality Management • IT system parts, technological processes and organizational processes • Uniform – – – Processes Utilities Measurement tools Feedbacks Reporting system • ISO 9001: 2000 based quality management system in KÜRT and in MTA SZTAKI (TÜV Rheinland)
Information Security Technology and Data Insurance (ISYS) IT Quality Management • IT system parts, technological processes and organizational processes • Uniform – – – Processes Utilities Measurement tools Feedbacks Reporting system • ISO 9001: 2000 based quality management system in KÜRT and in MTA SZTAKI (TÜV Rheinland)
 Information Security Technology and Data Insurance (ISYS) New developments in quality management, further improvements in our system • Quality management trends – Software Process Improvement (SPI) – ESSI Scope measurement tools – Target: Capability Maturity Model • IT Security trends – ISACA COBIT – BS 7799 -ISO 17799
Information Security Technology and Data Insurance (ISYS) New developments in quality management, further improvements in our system • Quality management trends – Software Process Improvement (SPI) – ESSI Scope measurement tools – Target: Capability Maturity Model • IT Security trends – ISACA COBIT – BS 7799 -ISO 17799
 Information Security Technology and Data Insurance (ISYS) Evaluation of 4 th phase results • ISO 9001: 2000 systems in KÜRT and MTA SZTAKI • Possible trends in improvement of quality systems (international trends) — EU trends
Information Security Technology and Data Insurance (ISYS) Evaluation of 4 th phase results • ISO 9001: 2000 systems in KÜRT and MTA SZTAKI • Possible trends in improvement of quality systems (international trends) — EU trends
 Information Security Technology and Data Insurance (ISYS) Next Project Phases • Tasks of 5 th Phase – Disaster Recovery Module for IBi. T (DRP module, in progress) • • Methodology for IBi. T Determination of value of damages Risk analysis methodology Business Continuity Processes • Tasks of 6 th Phase – Data insurance system (service pack, in progress) • • Probability of damage cases Damage value models Business value determinations Insurance value determinations
Information Security Technology and Data Insurance (ISYS) Next Project Phases • Tasks of 5 th Phase – Disaster Recovery Module for IBi. T (DRP module, in progress) • • Methodology for IBi. T Determination of value of damages Risk analysis methodology Business Continuity Processes • Tasks of 6 th Phase – Data insurance system (service pack, in progress) • • Probability of damage cases Damage value models Business value determinations Insurance value determinations
 Information Security Technology and Data Insurance (ISYS) Cooperation in the consortium • Task areas — as planned • Workflow system — project management (Prince) (electronic tools) • Acceptance of ready material • Stable project staff
Information Security Technology and Data Insurance (ISYS) Cooperation in the consortium • Task areas — as planned • Workflow system — project management (Prince) (electronic tools) • Acceptance of ready material • Stable project staff
 Information Security Technology and Data Insurance (ISYS) Dissemination of Results • Lectures: – Ministry of Education (2002) – Hungarian IT-Business Conference (2002) – Centennial Conference of the John von Neumann Computer Society (invited lecture 2003) • Scientific seminar (MTA SZTAKI) http: //csillag. ilab. sztaki. hu/dms/eszigno/szeminarium. htm • Educational courses – University of Budapest, Informatics Ph. D. programme (2002 -) – University of Debrecen, Informatics Ph. D. programme (2002 -) – University of Veszprém, Informatics Ph. D. programme (2001 -)
Information Security Technology and Data Insurance (ISYS) Dissemination of Results • Lectures: – Ministry of Education (2002) – Hungarian IT-Business Conference (2002) – Centennial Conference of the John von Neumann Computer Society (invited lecture 2003) • Scientific seminar (MTA SZTAKI) http: //csillag. ilab. sztaki. hu/dms/eszigno/szeminarium. htm • Educational courses – University of Budapest, Informatics Ph. D. programme (2002 -) – University of Debrecen, Informatics Ph. D. programme (2002 -) – University of Veszprém, Informatics Ph. D. programme (2001 -)
 Information Security Technology and Data Insurance (ISYS) Dissemination of Results (2) • 2 Ph. D. candidates in the project area • TV programs : – CNN (2001) – Hungarian TV 1 DELTA (2002) – Duna TV (2002) • Awards – Innovation Award (Ministry of Informatics) (2003)
Information Security Technology and Data Insurance (ISYS) Dissemination of Results (2) • 2 Ph. D. candidates in the project area • TV programs : – CNN (2001) – Hungarian TV 1 DELTA (2002) – Duna TV (2002) • Awards – Innovation Award (Ministry of Informatics) (2003)
 Information Security Technology and Data Insurance (ISYS) Thank you for your attention! KÜRT Computer Veszprémi Egyetem MTA SZTAKI
Information Security Technology and Data Insurance (ISYS) Thank you for your attention! KÜRT Computer Veszprémi Egyetem MTA SZTAKI


