eaaf889260e01c0262b4410fe029d54f.ppt
- Количество слайдов: 14

Key Substitution Attacks on Some Provably Secure Signature Schemes Author: Chik-How Tan (Singapore) Source: IEICE Trans. Fundamentals, Vol. E 87 -A, No. 1 Jan. 2004 Speaker: Su Sheng-Yao Date: 2004/12/22
Outline • Introduction • Two Provably Secure Signature Scheme – Fischlin Signature Scheme – Camenisch-Lysyanskaya Signature Scheme • Cryptoanalysis • Conclusion

Introduction • Provable Security – Security could be proved under standard and well-believed complexity theoretic assumptions • Definition, Protocol, Proof • Provably Secure Signature Schemes • Key Substitution Attack – Given U’s public key and signature s on m – adversary A tries to produce a new public key s. t. s is also a valid A’s signature on m

May Occur • e-lottery – the gambler uses his/her secret key to sign on the e-lottery to ensure that he owns the e-lottery

History • (1998) Goldwasser, Micali and Rivest introduced the security notion of existential unforgeability against adaptive chosen-message attacks • (1999) Blake-Wilson and Menezes introduced a duplicatesignature key selection attacks • (2004) Menezes and Smart analyzed the security of some signature schemes against this attack, named as key substitution attacks (also proved to secure in the standard model against adaptive chosen-message attacks, but subject to key substitution attacks)

• Two Provably Secure Signature Schemes – Fischlin Signature Scheme – Camenisch-Lysyanskaya Signature Scheme Subject to KS attacks
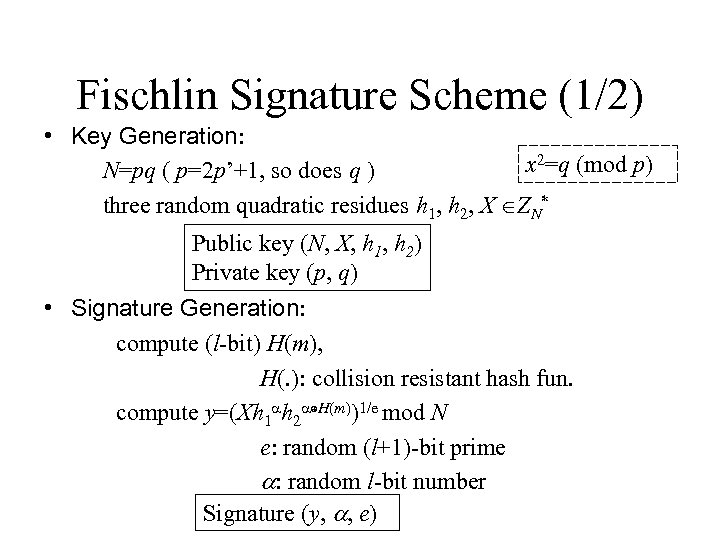
Fischlin Signature Scheme (1/2) • Key Generation: x 2=q (mod p) N=pq ( p=2 p’+1, so does q ) three random quadratic residues h 1, h 2, X ZN* Public key (N, X, h 1, h 2) Private key (p, q) • Signature Generation: compute (l-bit) H(m), H(. ): collision resistant hash fun. compute y=(Xh 1 ah 2 a⊕H(m))1/e mod N e: random (l+1)-bit prime a: random l-bit number Signature (y, a, e)
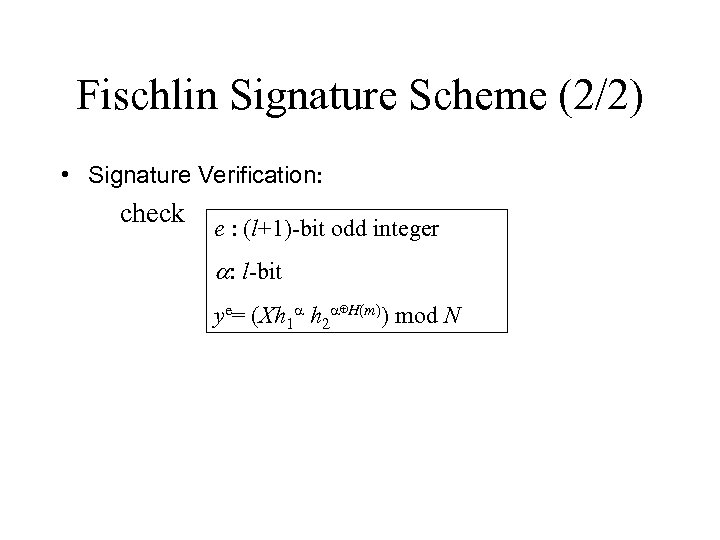
Fischlin Signature Scheme (2/2) • Signature Verification: check e : (l+1)-bit odd integer a: l-bit ye= (Xh 1 a h 2 a⊕H(m)) mod N
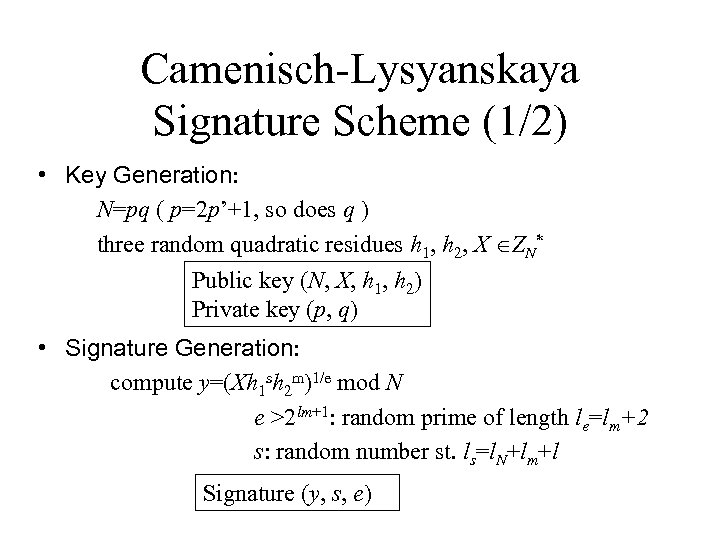
Camenisch-Lysyanskaya Signature Scheme (1/2) • Key Generation: N=pq ( p=2 p’+1, so does q ) three random quadratic residues h 1, h 2, X ZN* Public key (N, X, h 1, h 2) Private key (p, q) • Signature Generation: compute y=(Xh 1 sh 2 m)1/e mod N e >2 lm+1: random prime of length le=lm+2 s: random number st. ls=l. N+lm+l Signature (y, s, e)
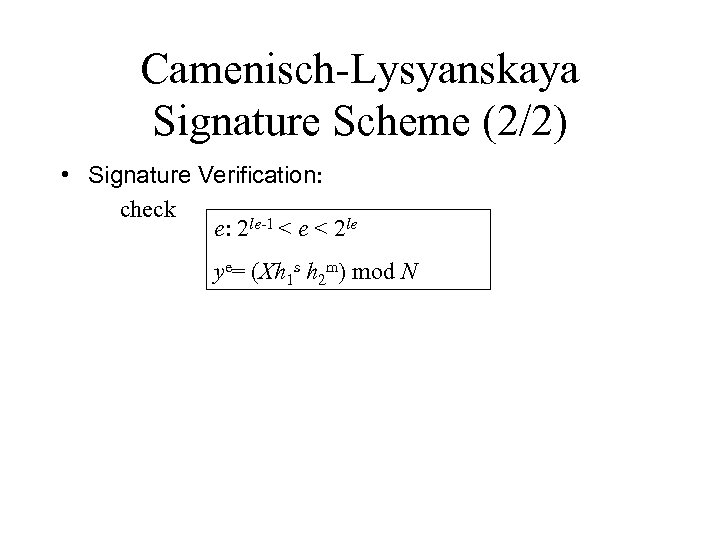
Camenisch-Lysyanskaya Signature Scheme (2/2) • Signature Verification: check e: 2 le-1 < e < 2 le ye= (Xh 1 s h 2 m) mod N
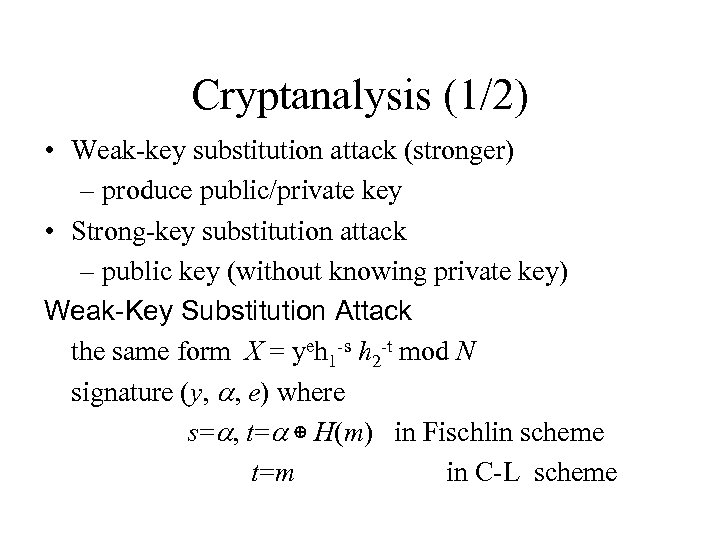
Cryptanalysis (1/2) • Weak-key substitution attack (stronger) – produce public/private key • Strong-key substitution attack – public key (without knowing private key) Weak-Key Substitution Attack the same form X = yeh 1 -s h 2 -t mod N signature (y, a, e) where s=a, t=a ⊕ H(m) in Fischlin scheme t=m in C-L scheme
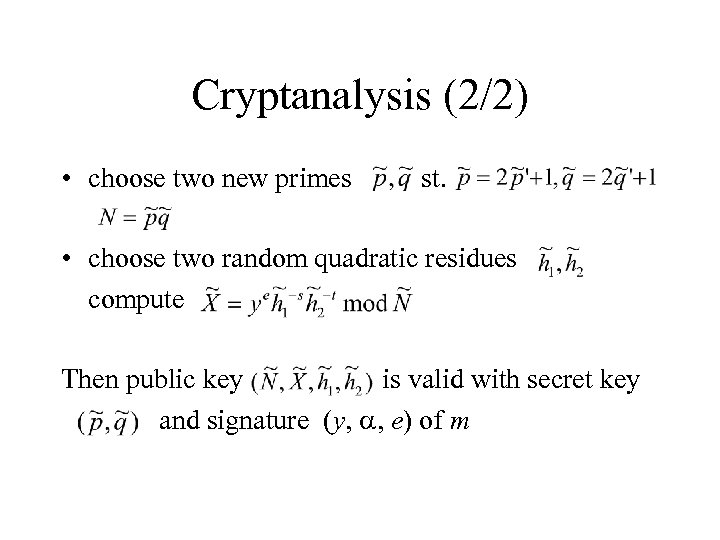
Cryptanalysis (2/2) • choose two new primes st. • choose two random quadratic residues compute Then public key is valid with secret key and signature (y, a, e) of m

Conclusion • Attack the two schemes by weak-key substitution attack • A signature scheme secure against existential forgery under adaptive chosen-message attack is inadequate • A scheme should be against key substitution attacks or rather under multi-user setting
Thanks for comments. . Merry Christmas !
eaaf889260e01c0262b4410fe029d54f.ppt