Mod 2 - MVA Defense-in-Depth Windows Security.pptx
- Количество слайдов: 19
 Key Principles of Security
Key Principles of Security
 Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
Module 1: Today’s Threat Landscape Module 2: Key Principles of Security Module 3: Understanding your enemy! Module 4: Phases of Hackers Lunch Break Module 5: What motivates hackers? Module 6: Pass the Hash Module 7: Windows Security Capabilities and Tools
 Module Insights Explore the key concepts of IT Security with strong focus on ISO 2700 x.
Module Insights Explore the key concepts of IT Security with strong focus on ISO 2700 x.
 Not hard to guess but… Not every network administrator is a security expert But, all network administrators must understand the basics Follow the Key Principals to secure your network(s)
Not hard to guess but… Not every network administrator is a security expert But, all network administrators must understand the basics Follow the Key Principals to secure your network(s)
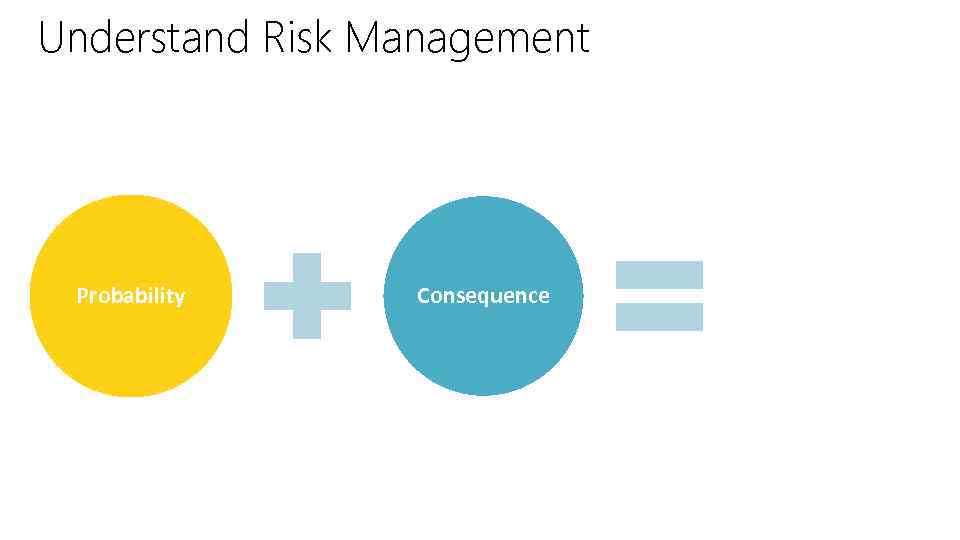 Understand Risk Management Probability Consequence Risk
Understand Risk Management Probability Consequence Risk
 Golden Rules • First key principle of security is that no network is completely secure • Information security is really about risk management • The more important the asset is and the more it is exposed to security threats, the more resources you should put into securing it
Golden Rules • First key principle of security is that no network is completely secure • Information security is really about risk management • The more important the asset is and the more it is exposed to security threats, the more resources you should put into securing it
![Asset Define elements of value [ISO 27001: 2005, Clause 3. 1] Asset Define elements of value [ISO 27001: 2005, Clause 3. 1]](https://present5.com/presentation/168361774_312968392/image-7.jpg) Asset Define elements of value [ISO 27001: 2005, Clause 3. 1]
Asset Define elements of value [ISO 27001: 2005, Clause 3. 1]
![Identification of Assets A possible classification [ISO 27001: 2005, Clause 3. 1] Identification of Assets A possible classification [ISO 27001: 2005, Clause 3. 1]](https://present5.com/presentation/168361774_312968392/image-8.jpg) Identification of Assets A possible classification [ISO 27001: 2005, Clause 3. 1]
Identification of Assets A possible classification [ISO 27001: 2005, Clause 3. 1]
 Threat, Vulnerabilities and Information Security Threat Potential cause of an unwanted incident, which may result in harm to a system or organization Vulnerability Weakness of an asset or group of assets that can be exploited by one or more threats Information Security Protection of information from a wide range of threats, in order to ensure business continuity, minimize business risk, and maximize return on investment and business opportunities. [ISO 27001: 2005]
Threat, Vulnerabilities and Information Security Threat Potential cause of an unwanted incident, which may result in harm to a system or organization Vulnerability Weakness of an asset or group of assets that can be exploited by one or more threats Information Security Protection of information from a wide range of threats, in order to ensure business continuity, minimize business risk, and maximize return on investment and business opportunities. [ISO 27001: 2005]
 Confidentiality, Integrity and Availability Confidentiality The property that information is not made available or disclosed to unauthorized individuals, entities, or processes Integrity The property of safeguarding the accuracy and completeness of assets Availability The property of being accessible and usable upon demand by an authorized entity [ISO 27001: 2005]
Confidentiality, Integrity and Availability Confidentiality The property that information is not made available or disclosed to unauthorized individuals, entities, or processes Integrity The property of safeguarding the accuracy and completeness of assets Availability The property of being accessible and usable upon demand by an authorized entity [ISO 27001: 2005]
 Identification of assets Identification of threats Identification of existing controls Identification of vulnerabilities Identification of consequences [ISO 27005– 8. 2. 1]
Identification of assets Identification of threats Identification of existing controls Identification of vulnerabilities Identification of consequences [ISO 27005– 8. 2. 1]
 Monitor the assets Once the actions defined in the risk management plan have been implemented, you will need to monitor the assets for realization of the security risks
Monitor the assets Once the actions defined in the risk management plan have been implemented, you will need to monitor the assets for realization of the security risks
 Track changes to risks As time progresses, changes to your organization’s hardware, software, personnel, and business processes will add and obsolete security risks. Similarly, threats to assets and vulnerabilities will evolve and increase in sophistication.
Track changes to risks As time progresses, changes to your organization’s hardware, software, personnel, and business processes will add and obsolete security risks. Similarly, threats to assets and vulnerabilities will evolve and increase in sophistication.
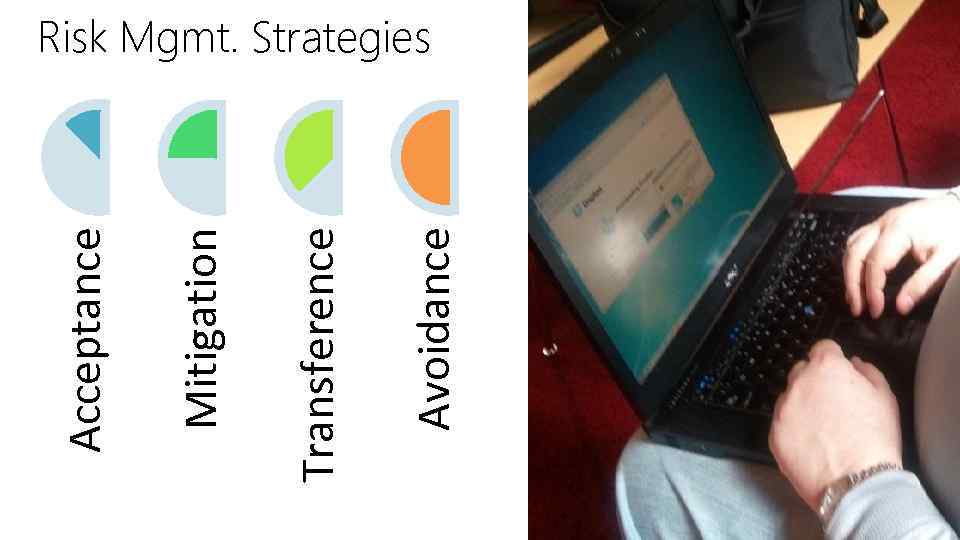 Avoidance Transference Mitigation Acceptance Risk Mgmt. Strategies
Avoidance Transference Mitigation Acceptance Risk Mgmt. Strategies
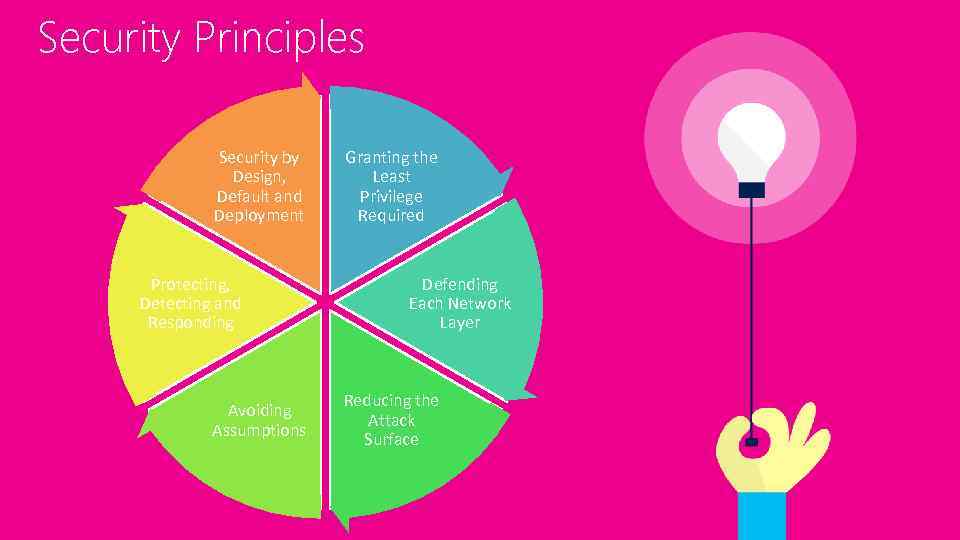 Security Principles Security by Design, Default and Deployment Protecting, Detecting and Responding Avoiding Assumptions Granting the Least Privilege Required Defending Each Network Layer Reducing the Attack Surface
Security Principles Security by Design, Default and Deployment Protecting, Detecting and Responding Avoiding Assumptions Granting the Least Privilege Required Defending Each Network Layer Reducing the Attack Surface
 Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
Connect with the speakers! @Erdal. Ozkaya @Milad. PFE http: //erdalozkaya. com/ https: //www. facebook. com/milad. aslaner
 Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
Tech. Net Virtual Labs Deep technical content and free product evaluations Hands-on deep technical labs Free, online, technical courses Download Microsoftware trials today. Find Hand On Labs. Take a free online course. Technet. microsoft. com/evalcenter Technet. microsoft. com/virtuallabs microsoftvirtualacademy. com
 © 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
© 2013 Microsoft Corporation. All rights reserved. Microsoft, Windows, Office, Azure, System Center, Dynamics and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.


