31fa99e0ae44780772564a6f5f017de4.ppt
- Количество слайдов: 16
 Key Management with the Voltage Data Protection Server Luther Martin IEEE P 1619. 3 May 7, 2007
Key Management with the Voltage Data Protection Server Luther Martin IEEE P 1619. 3 May 7, 2007
 Overview } } Key management with the Voltage Data Protection Server is motivated by the typical customer uses An administrator defines policies at a central management console that pushes configuration and policy data to individual key servers Management of symmetric keys is integrated with management of asymmetric keys (identity-based encryption) Not really an API § 2 Data is either Base 64 -encoded PKCS#7 or XML and is transported over HTTPS
Overview } } Key management with the Voltage Data Protection Server is motivated by the typical customer uses An administrator defines policies at a central management console that pushes configuration and policy data to individual key servers Management of symmetric keys is integrated with management of asymmetric keys (identity-based encryption) Not really an API § 2 Data is either Base 64 -encoded PKCS#7 or XML and is transported over HTTPS
 Typical use of the Voltage Data Protection System - 1 } Used to encrypt sensitive information in a database § } 3 Typically for PCI DSS compliance In this case, encryption and decryption are both automated
Typical use of the Voltage Data Protection System - 1 } Used to encrypt sensitive information in a database § } 3 Typically for PCI DSS compliance In this case, encryption and decryption are both automated
 Typical use of the Voltage Data Protection System - 2 } Encrypting unstructured data in storage according to a security policy Documents § Spreadsheets § Etc. § } In this case, encryption may be automated but a human user may decrypt the data May even be in a different security domain § “Federation” § 4
Typical use of the Voltage Data Protection System - 2 } Encrypting unstructured data in storage according to a security policy Documents § Spreadsheets § Etc. § } In this case, encryption may be automated but a human user may decrypt the data May even be in a different security domain § “Federation” § 4
 Design goals } } Must support multiple cryptographic algorithms Must support multiple authentication methods for each algorithm Must work across multiple security domains May require user interaction § 5 Could be an application
Design goals } } Must support multiple cryptographic algorithms Must support multiple authentication methods for each algorithm Must work across multiple security domains May require user interaction § 5 Could be an application
 Components } Management console § § } Key servers § § § } Create and grant keys Enforce policy Log events Users § § § 6 Creates policies and pushes to key servers Creates configuration data and pushes to key servers Logs events and allows an authorized admin to review logs Pulls logs from key servers Request keys Request policy Authenticate as needed
Components } Management console § § } Key servers § § § } Create and grant keys Enforce policy Log events Users § § § 6 Creates policies and pushes to key servers Creates configuration data and pushes to key servers Logs events and allows an authorized admin to review logs Pulls logs from key servers Request keys Request policy Authenticate as needed
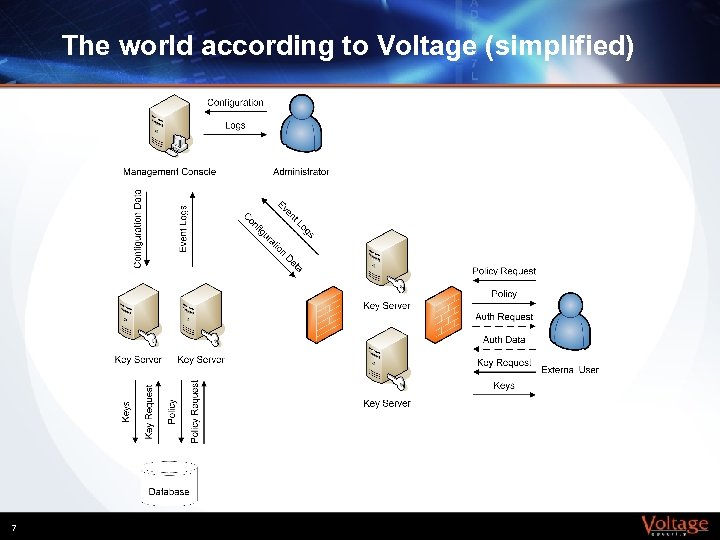 The world according to Voltage (simplified) 7
The world according to Voltage (simplified) 7
 Downloading policy } Clients download policy from key server over HTTPS § A policy URL Policy defines what keys a key server can create § Stored in a Base 64 -encoded PKCS#7 on the key server § Gives URL of where to request keys § Other administrative information § Validity period of the policy • How often clients should check for new policy • Etc. • § 8 Knowing the policy URL is all that a client needs to start encrypting
Downloading policy } Clients download policy from key server over HTTPS § A policy URL Policy defines what keys a key server can create § Stored in a Base 64 -encoded PKCS#7 on the key server § Gives URL of where to request keys § Other administrative information § Validity period of the policy • How often clients should check for new policy • Etc. • § 8 Knowing the policy URL is all that a client needs to start encrypting
 Example policy – not very enlightening } } 9 -----BEGIN PKCS 7 ----MIIKKg. YJKo. ZIhvc. NAQc. Co. IIKGz. CCChc. CAQEx. Cz. AJBg. Ur. Dg. MCGg. UAMIIGfg. YJKo. ZI a. Cwka. TUA 8 e 6 G 3 Rtynz 2 GFi. Hrrr. LTu 6 h 9 IKea. M 1 Zhu. Sh. K+CTMdi. Vr. Ej. CCAT 8 CAQEw w. Biei. N 8 Dvim. Mxmo. Et. Ns 4 Ff. ZRAxb. Hx 7 VVIcw. Ko. PMwg. ZEGC 2 CGSAGG/R 4 BAQEBBEAA AAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAA my. POGhn. Hop. YNvm. Rja. Xs 13 efx. L 08 k 79 Kf. SX/IEgco. Rsnvbh. Rkf. QDW 30 x 85 Om 701 UG 4 RZI 3 e 9 o. C 3 X/iu. Sx 5 i 1 Nnb. TW 2 Kq 4 y. Q+j. W 9 h 7 Xt. TGTf. Z 4 r. Mlytg. Ssl 1 Vpa. WUXT 7 m 4 gg. Rm. MBIGC 2 CGSAGG/R 4 BAw. IKBAMCAQMw. IAYLYIZIAYb 9 Hg. EDAg. EBAf 8 EDh. MMMDQw hkg. Bhv 0 e. AQMCBg. EB/w. Qa. DBh 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy. MTE 2 MTYw. Lw. YLYIZI SAGG/R 4 BAw. IHAQH/BB 0 MG 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl. Lm. Nvb. TBVBgtg Lm. Nvb. S 9 mb 3 Jtc. G 9 zd. GRpci 9 z. YWZl. Zm 9 yb. XBvc 3 Qu. YXNwe. DBVBgtghkg. Bhv 0 e. AQMC c. G 9 zd. GRpci 9 z. YWZl. Zm 9 yb. XBvc 3 Qu. YXNwe. DCCAsw. GC 2 CGSAGG/R 4 BAw. IEAQH/BIIC d. GFn. ZS 5 jb 20 w. Hhc. NMDQw. NDIy. MTgw. Nj. A 1 Whc. NMjkw. NDE 2 MTgw. Nj. A 1 Wj. Al. MSMw. IQYD MIIBHg. KBg. QD 2 N 0 O 2 t 9 OUCRm+APvg. YO 1 t. EAPD 1+hey. LVFp 5 Tg. VABry. Chuhht. Wdq. Xv s. AXKJNRntnb. A 4 Srkkl 4 Tfi. GMWEid. E+67 k 2 a. FLe. Tgg. TDn 90 h. Eq. HHit. QIVAO 6 MTSFm C 8 axk. SSEjgfx. I 0 QPhnjgf. Ai. Pgns. Wm. Joox. Hv. B 62/k. ARCX 6 z. Ft 5 jjcr 2 g. M 7 Enl. Ycw. A 3 d. QDg. YQAAo. GAG 8 t. Lodfq. JNcqu. Jfjpv. Xu 7 X/3 hf 7 cnz+x. NHEd. Eq. Mq. TJOO 5 PVk 9 Ere 8 B 1 Rjr 3 q. YGDdd 8 Pkk. Opxr. Js. Nw. Arl. KQid. ZZ 2 p. Rs+54 y. Sw. XRF 9 o. Vz. KNUej. Qj. BAMA 8 G 2 a 4128+cz. LGa. Csi 3 a. DAJBgcqhkj. OOAQDAy 8 AMCw. CFDJB 6 Vsqx 1 Hx. T 6 Cz. XWx. CPMJA Byq. GSM 44 BAMw. Fj. EUMBIGA 1 UEAx. MLdm 9 sd. GFn. ZS 5 jb 20 w. Hhc. NMDQw. NDIy. MTgw. Nj. A 3 MTE 2 MTY 6 UDCCAbcwgg. Es. Bgcqhkj. OOAQBMIIBHw. KBg. QCcm. UTb 9 u 179 pw 8 RQn 27 e. Ei ej. Y+xpys 0 RK 4 i. Ff. J 7 NLZz 7 e. AMQwbkidz. BGBib. WNQsxdmsvv. SJLc+26 g 54 pa 8 Crj 8 Nip. TQ 0 TX+1 Dx 9+m. Wd. Hhj. MLf. Tess. Ld. C 47 k. Fmw. Yepx. Bz/ZKu 4 ZG 9+wtpqu 5 Rod 0340 o. Ny 1 KML+n 8 k. TAJp 1 elp. T/0 Cy. Seph 7 KVjgut. HA 4 GEAAKBg. Bv. VSd 19 w. Qh. Gw. XGr 7 zvb K+Ro. TFURqe 82/1 bf. E 1 tn. Nn. VE 1 j. UEc. FJod. Ep. N 1 z. QRQ 6 i 1 TOMV+0 n. Vp. Jlb 9 yl. Op 9 E 1 /w. QEAw. IBBj. Ad. Bg. NVHQ 4 EFg. QU 160 Me 2 kzzl 3 w 1 cv. Jhf 81 RERMGVgw. CQYHKo. ZIzjg. E 8 ipx. MYHIMIHFAg. EBMBsw. Fj. EUMBIGA 1 UEAx. MLdm 9 sd. GFn. ZS 5 jb 20 CAQEw. CQYFKw 4 D DTA 2 MTIw. ODAy. MTYz. M 1 ow. Iw. YJKo. ZIhvc. NAQk. EMRYEFBtovu 1 emw. W 496 e. Aic. S 53 o+Z YG 2 aj. Zg. KJ/AGFe. Yk. G 7 s= -----END PKCS 7 ----- hvc. NAQc. Bo. IIGbw. SCBmswgg. Zn. Ag. EBBEECjrk 1 v. Le. Ey. C 1 gb. ZBi. II 8 Gp. SNU 7 h. VZe. GEA TAYHKo. ZIzj 0 BAQJBAJ 8 H 1 g. R 9 xl. CYucz 2 u. Tz. Layu. TJi 7 AILge. Rz 4 Lp 6 r. Epy 0 j 9 e. GO AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBEECAmm 7 c 2 j. Aous. Qfw. T 1 W 8 v. Gjw. IVAP///////v//////MVIw. UAYLYIZIAYb 9 Hg. EDAQIEQQKX Yhd 7 Eg. Qt. BP 4 Sv. ELey 3 U 4 MB 4 XDTA 0 MDQy. Mj. E 4 MDYw. N 1 o. XDTI 5 MDQx. Nj. E 4 MDYw. N 1 ox Mj. Az. Mj. Ex. Nj. E 2 MCAGC 2 CGSAGG/R 4 BAw. IFAQH/BA 4 w. DAYKYIZIAYb 9 Hg. IBATAs. Bgtg AYb 9 Hg. EDAg. IBAf 8 EHRMbdm 9 sd. GFn. ZS 1 wcy 0 w. MDAw. Ln. Zvb. HRh. Z 2 Uu. Y 29 t. MC 8 GC 2 CG hkg. Bhv 0 e. AQMCAw. EB/w. RDE 0 Fod. HRwczov. L 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl CAEB/w. RDDEFod. HRwczov. L 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl. Lm. Nvb. S 9 mb 3 Jt u. DCCAr. Qwgg. Kw. MIICc. KADAg. ECAg. EBMAk. GByq. GSM 44 BAMw. Fj. EUMBIGA 1 UEAx. MLdm 9 s VQQDFBp 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy. MTE 2 MTY 6 Uz. CCAb. Ywgg. Er. Bgcqhkj. OOAQB c. UCT 6 u. A 7+8 pth 2 KWB 6 zv. MR 1 Fs. BHHFb 0 Du 2 S 3 Hvga. Bqqh. NRr+t 1 Gvv. P 1/hf. Xyqhd. L MJ 777 vg 9 h. R 76 QUu. HPqcj. Ao. GAf+DTTEL/i. LZw. PHg 2 d. AW 7 NQm. Ho. Eua. JZg. VCt. XVzr. I 6 Bw+PH 8 d. Wr. Qu. GMQohwv. UML 2 k/h. Ezh. U+78 p 6 J 9 h 1 hd. Wso. IR 7 yewuxi. BWD+Np. Pn 9 UU 2 nu 0 Aj 50 l 84 z+r. Ji. GQvo. XXtde. RVTxgq. Agzl. GXs/7 Flu. F 8 c. K 2 lpw. Bj 5 m 1 v. Q 3 c. AHz. DA A 1 Ud. Ew. EB/w. QFMAMBAf 8 w. Dg. YDVR 0 PAQH/BAQDAg. EGMB 0 GA 1 Ud. Dg. QWBBRDGs 9 z. RYnj SEfh. Ah. Q 3 BIm 2 DH 2 m 8 Mr. Gi. Nl 4 JMl. B 66 hw. NKCCAr. Ywgg. Ky. MIICca. ADAg. ECAg. EBMAk. G Whc. NMjkw. NDE 2 MTgw. Nj. A 3 Wj. Al. MSMw. IQYDVQQDFBp 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy 4 Mc 1 RY 2 JWl/w. Rw. YE+F 3 ru. Am. Bmo 4 m 6 g. Mm. I 5 pvj 4 Mt. Gf. U+3 ip. Pbug. OAOB 3 DLu 5 w 9 R 5 g. NO 6 H 4 Lkgt. HE 4 rp. UO 63 Z 5 w. IVAITw. Iv. Ryibe. CMu. BHjds. L 6 C 7 g 9 Jy/Ao. GBAJn. U/8 K+ Q 3 Jd 4 Ycmt. TKt. MTi. Lp/Pm 6 QQn 6 b. Kchx. Jqj. S 27 w. Ve 7 Ig 4 G 3 Z 4 z. Xc 0 Yie 18 v. TPDp. D 1 l j. Li 8 w. KRFvveo 8 PPlf. Sf. HJgz. NZr. Mv. BK 4 Hlc. K/Ks. Tx/6 Bx. Sl. Lf 8 E 2 Uaax 8 JGArh. Pu. W 3 k. VY 5+hu. CZM 4 Mqb. QQv. Dd/Ex. Io 0 Iw. QDAPBg. NVHRMBAf 8 EBTADAQH/MA 4 GA 1 Ud. Dw. EB Aw. Mw. ADAt. Ah. UAgf. WYot 9 R 24 alb 8 wu. PD/2 o. Wp. A 6 og. CFEv 9 xddpd. K 78 OLy. Oj. Hd. Mt. FBl Aho. FAKBd. MBg. GCSq. GSIb 3 DQEJAz. ELBgkqhki. G 9 w 0 BBw. Ew. HAYJKo. ZIhvc. NAQk. FMQ 8 X d. FXb. MAk. GByq. GSM 44 BAEELj. As. Ah. Qo. LURHi. Nst/mw. Fz 7 Fm+q 31 GDop. Dg. IUXOGILtq. M
Example policy – not very enlightening } } 9 -----BEGIN PKCS 7 ----MIIKKg. YJKo. ZIhvc. NAQc. Co. IIKGz. CCChc. CAQEx. Cz. AJBg. Ur. Dg. MCGg. UAMIIGfg. YJKo. ZI a. Cwka. TUA 8 e 6 G 3 Rtynz 2 GFi. Hrrr. LTu 6 h 9 IKea. M 1 Zhu. Sh. K+CTMdi. Vr. Ej. CCAT 8 CAQEw w. Biei. N 8 Dvim. Mxmo. Et. Ns 4 Ff. ZRAxb. Hx 7 VVIcw. Ko. PMwg. ZEGC 2 CGSAGG/R 4 BAQEBBEAA AAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAA my. POGhn. Hop. YNvm. Rja. Xs 13 efx. L 08 k 79 Kf. SX/IEgco. Rsnvbh. Rkf. QDW 30 x 85 Om 701 UG 4 RZI 3 e 9 o. C 3 X/iu. Sx 5 i 1 Nnb. TW 2 Kq 4 y. Q+j. W 9 h 7 Xt. TGTf. Z 4 r. Mlytg. Ssl 1 Vpa. WUXT 7 m 4 gg. Rm. MBIGC 2 CGSAGG/R 4 BAw. IKBAMCAQMw. IAYLYIZIAYb 9 Hg. EDAg. EBAf 8 EDh. MMMDQw hkg. Bhv 0 e. AQMCBg. EB/w. Qa. DBh 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy. MTE 2 MTYw. Lw. YLYIZI SAGG/R 4 BAw. IHAQH/BB 0 MG 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl. Lm. Nvb. TBVBgtg Lm. Nvb. S 9 mb 3 Jtc. G 9 zd. GRpci 9 z. YWZl. Zm 9 yb. XBvc 3 Qu. YXNwe. DBVBgtghkg. Bhv 0 e. AQMC c. G 9 zd. GRpci 9 z. YWZl. Zm 9 yb. XBvc 3 Qu. YXNwe. DCCAsw. GC 2 CGSAGG/R 4 BAw. IEAQH/BIIC d. GFn. ZS 5 jb 20 w. Hhc. NMDQw. NDIy. MTgw. Nj. A 1 Whc. NMjkw. NDE 2 MTgw. Nj. A 1 Wj. Al. MSMw. IQYD MIIBHg. KBg. QD 2 N 0 O 2 t 9 OUCRm+APvg. YO 1 t. EAPD 1+hey. LVFp 5 Tg. VABry. Chuhht. Wdq. Xv s. AXKJNRntnb. A 4 Srkkl 4 Tfi. GMWEid. E+67 k 2 a. FLe. Tgg. TDn 90 h. Eq. HHit. QIVAO 6 MTSFm C 8 axk. SSEjgfx. I 0 QPhnjgf. Ai. Pgns. Wm. Joox. Hv. B 62/k. ARCX 6 z. Ft 5 jjcr 2 g. M 7 Enl. Ycw. A 3 d. QDg. YQAAo. GAG 8 t. Lodfq. JNcqu. Jfjpv. Xu 7 X/3 hf 7 cnz+x. NHEd. Eq. Mq. TJOO 5 PVk 9 Ere 8 B 1 Rjr 3 q. YGDdd 8 Pkk. Opxr. Js. Nw. Arl. KQid. ZZ 2 p. Rs+54 y. Sw. XRF 9 o. Vz. KNUej. Qj. BAMA 8 G 2 a 4128+cz. LGa. Csi 3 a. DAJBgcqhkj. OOAQDAy 8 AMCw. CFDJB 6 Vsqx 1 Hx. T 6 Cz. XWx. CPMJA Byq. GSM 44 BAMw. Fj. EUMBIGA 1 UEAx. MLdm 9 sd. GFn. ZS 5 jb 20 w. Hhc. NMDQw. NDIy. MTgw. Nj. A 3 MTE 2 MTY 6 UDCCAbcwgg. Es. Bgcqhkj. OOAQBMIIBHw. KBg. QCcm. UTb 9 u 179 pw 8 RQn 27 e. Ei ej. Y+xpys 0 RK 4 i. Ff. J 7 NLZz 7 e. AMQwbkidz. BGBib. WNQsxdmsvv. SJLc+26 g 54 pa 8 Crj 8 Nip. TQ 0 TX+1 Dx 9+m. Wd. Hhj. MLf. Tess. Ld. C 47 k. Fmw. Yepx. Bz/ZKu 4 ZG 9+wtpqu 5 Rod 0340 o. Ny 1 KML+n 8 k. TAJp 1 elp. T/0 Cy. Seph 7 KVjgut. HA 4 GEAAKBg. Bv. VSd 19 w. Qh. Gw. XGr 7 zvb K+Ro. TFURqe 82/1 bf. E 1 tn. Nn. VE 1 j. UEc. FJod. Ep. N 1 z. QRQ 6 i 1 TOMV+0 n. Vp. Jlb 9 yl. Op 9 E 1 /w. QEAw. IBBj. Ad. Bg. NVHQ 4 EFg. QU 160 Me 2 kzzl 3 w 1 cv. Jhf 81 RERMGVgw. CQYHKo. ZIzjg. E 8 ipx. MYHIMIHFAg. EBMBsw. Fj. EUMBIGA 1 UEAx. MLdm 9 sd. GFn. ZS 5 jb 20 CAQEw. CQYFKw 4 D DTA 2 MTIw. ODAy. MTYz. M 1 ow. Iw. YJKo. ZIhvc. NAQk. EMRYEFBtovu 1 emw. W 496 e. Aic. S 53 o+Z YG 2 aj. Zg. KJ/AGFe. Yk. G 7 s= -----END PKCS 7 ----- hvc. NAQc. Bo. IIGbw. SCBmswgg. Zn. Ag. EBBEECjrk 1 v. Le. Ey. C 1 gb. ZBi. II 8 Gp. SNU 7 h. VZe. GEA TAYHKo. ZIzj 0 BAQJBAJ 8 H 1 g. R 9 xl. CYucz 2 u. Tz. Layu. TJi 7 AILge. Rz 4 Lp 6 r. Epy 0 j 9 e. GO AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBEECAmm 7 c 2 j. Aous. Qfw. T 1 W 8 v. Gjw. IVAP///////v//////MVIw. UAYLYIZIAYb 9 Hg. EDAQIEQQKX Yhd 7 Eg. Qt. BP 4 Sv. ELey 3 U 4 MB 4 XDTA 0 MDQy. Mj. E 4 MDYw. N 1 o. XDTI 5 MDQx. Nj. E 4 MDYw. N 1 ox Mj. Az. Mj. Ex. Nj. E 2 MCAGC 2 CGSAGG/R 4 BAw. IFAQH/BA 4 w. DAYKYIZIAYb 9 Hg. IBATAs. Bgtg AYb 9 Hg. EDAg. IBAf 8 EHRMbdm 9 sd. GFn. ZS 1 wcy 0 w. MDAw. Ln. Zvb. HRh. Z 2 Uu. Y 29 t. MC 8 GC 2 CG hkg. Bhv 0 e. AQMCAw. EB/w. RDE 0 Fod. HRwczov. L 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl CAEB/w. RDDEFod. HRwczov. L 3 Zvb. HRh. Z 2 Utc. HMt. MDAw. MC 52 b 2 x 0 YWdl. Lm. Nvb. S 9 mb 3 Jt u. DCCAr. Qwgg. Kw. MIICc. KADAg. ECAg. EBMAk. GByq. GSM 44 BAMw. Fj. EUMBIGA 1 UEAx. MLdm 9 s VQQDFBp 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy. MTE 2 MTY 6 Uz. CCAb. Ywgg. Er. Bgcqhkj. OOAQB c. UCT 6 u. A 7+8 pth 2 KWB 6 zv. MR 1 Fs. BHHFb 0 Du 2 S 3 Hvga. Bqqh. NRr+t 1 Gvv. P 1/hf. Xyqhd. L MJ 777 vg 9 h. R 76 QUu. HPqcj. Ao. GAf+DTTEL/i. LZw. PHg 2 d. AW 7 NQm. Ho. Eua. JZg. VCt. XVzr. I 6 Bw+PH 8 d. Wr. Qu. GMQohwv. UML 2 k/h. Ezh. U+78 p 6 J 9 h 1 hd. Wso. IR 7 yewuxi. BWD+Np. Pn 9 UU 2 nu 0 Aj 50 l 84 z+r. Ji. GQvo. XXtde. RVTxgq. Agzl. GXs/7 Flu. F 8 c. K 2 lpw. Bj 5 m 1 v. Q 3 c. AHz. DA A 1 Ud. Ew. EB/w. QFMAMBAf 8 w. Dg. YDVR 0 PAQH/BAQDAg. EGMB 0 GA 1 Ud. Dg. QWBBRDGs 9 z. RYnj SEfh. Ah. Q 3 BIm 2 DH 2 m 8 Mr. Gi. Nl 4 JMl. B 66 hw. NKCCAr. Ywgg. Ky. MIICca. ADAg. ECAg. EBMAk. G Whc. NMjkw. NDE 2 MTgw. Nj. A 3 Wj. Al. MSMw. IQYDVQQDFBp 2 b 2 x 0 YWdl. Lm. Nvb. SMw. NDAy. MDMy 4 Mc 1 RY 2 JWl/w. Rw. YE+F 3 ru. Am. Bmo 4 m 6 g. Mm. I 5 pvj 4 Mt. Gf. U+3 ip. Pbug. OAOB 3 DLu 5 w 9 R 5 g. NO 6 H 4 Lkgt. HE 4 rp. UO 63 Z 5 w. IVAITw. Iv. Ryibe. CMu. BHjds. L 6 C 7 g 9 Jy/Ao. GBAJn. U/8 K+ Q 3 Jd 4 Ycmt. TKt. MTi. Lp/Pm 6 QQn 6 b. Kchx. Jqj. S 27 w. Ve 7 Ig 4 G 3 Z 4 z. Xc 0 Yie 18 v. TPDp. D 1 l j. Li 8 w. KRFvveo 8 PPlf. Sf. HJgz. NZr. Mv. BK 4 Hlc. K/Ks. Tx/6 Bx. Sl. Lf 8 E 2 Uaax 8 JGArh. Pu. W 3 k. VY 5+hu. CZM 4 Mqb. QQv. Dd/Ex. Io 0 Iw. QDAPBg. NVHRMBAf 8 EBTADAQH/MA 4 GA 1 Ud. Dw. EB Aw. Mw. ADAt. Ah. UAgf. WYot 9 R 24 alb 8 wu. PD/2 o. Wp. A 6 og. CFEv 9 xddpd. K 78 OLy. Oj. Hd. Mt. FBl Aho. FAKBd. MBg. GCSq. GSIb 3 DQEJAz. ELBgkqhki. G 9 w 0 BBw. Ew. HAYJKo. ZIhvc. NAQk. FMQ 8 X d. FXb. MAk. GByq. GSM 44 BAEELj. As. Ah. Qo. LURHi. Nst/mw. Fz 7 Fm+q 31 GDop. Dg. IUXOGILtq. M
 Getting keys } } 10 Clients request keys from key server and use to encrypt/decrypt data Key identifier can be stored as an Attribute in a PKCS#7 encrypted-data content type § As defined in RFC 3852/CMS Identifier includes information about key § OID of algorithm § Key length § URL of policy § Application (can’t enforce, but useful for licensing) § Recipient identifier (device, user, etc. ) Identifier is a Base 64 -encoded DER-encoded block that can be used for multiple purposes
Getting keys } } 10 Clients request keys from key server and use to encrypt/decrypt data Key identifier can be stored as an Attribute in a PKCS#7 encrypted-data content type § As defined in RFC 3852/CMS Identifier includes information about key § OID of algorithm § Key length § URL of policy § Application (can’t enforce, but useful for licensing) § Recipient identifier (device, user, etc. ) Identifier is a Base 64 -encoded DER-encoded block that can be used for multiple purposes
 Authentication } Authentication data can be passed with a key request § } If a valid auth token is not present in a key request, the key server performs whatever auth is required by the security policy § § 11 Optional May query user May also query other data sources Returns auth token to user upon success User then requests the key using the valid auth token
Authentication } Authentication data can be passed with a key request § } If a valid auth token is not present in a key request, the key server performs whatever auth is required by the security policy § § 11 Optional May query user May also query other data sources Returns auth token to user upon success User then requests the key using the valid auth token
 Server response } } 13 Response from server includes the key plus an identifier for the key Identifier includes information about key § OID of algorithm § Key length § URL of policy § Application (can’t enforce, but useful for licensing) § Recipient identifier (device, user, etc. )
Server response } } 13 Response from server includes the key plus an identifier for the key Identifier includes information about key § OID of algorithm § Key length § URL of policy § Application (can’t enforce, but useful for licensing) § Recipient identifier (device, user, etc. )
 Key server response
Key server response
 User authentication } } } User identifier and key identifier are in the key request Key server requires authentication per its security policy before granting keys Configurable per user/device or group of users/devices § § § § 15 Shared secret Active Directory E-mail answerback Q&A X. 509 client certificates Secure. ID Others
User authentication } } } User identifier and key identifier are in the key request Key server requires authentication per its security policy before granting keys Configurable per user/device or group of users/devices § § § § 15 Shared secret Active Directory E-mail answerback Q&A X. 509 client certificates Secure. ID Others
 Summary } The key management capabilities of the Voltage Data Protection Server includes features that make it useful in a wide range of applications Encryption and decryption may be automated but it is also easy for a human user to perform the same operations § Users/devices may even be in a different security domain § Wide range of authentication options § Same framework applies to asymmetric key management § 16
Summary } The key management capabilities of the Voltage Data Protection Server includes features that make it useful in a wide range of applications Encryption and decryption may be automated but it is also easy for a human user to perform the same operations § Users/devices may even be in a different security domain § Wide range of authentication options § Same framework applies to asymmetric key management § 16


