307623db21da97ea0a78a34d373208f2.ppt
- Количество слайдов: 13

Key Distribution CS 470 Introduction to Applied Cryptography Instructor: Ali Aydin Selcuk CS 470, A. Selcuk Key Distribution 1
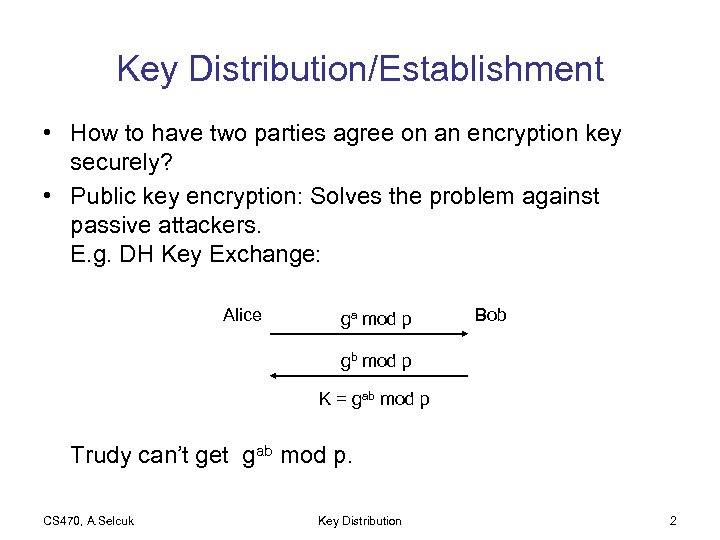
Key Distribution/Establishment • How to have two parties agree on an encryption key securely? • Public key encryption: Solves the problem against passive attackers. E. g. DH Key Exchange: Alice ga mod p Bob gb mod p K = gab mod p Trudy can’t get gab mod p. CS 470, A. Selcuk Key Distribution 2
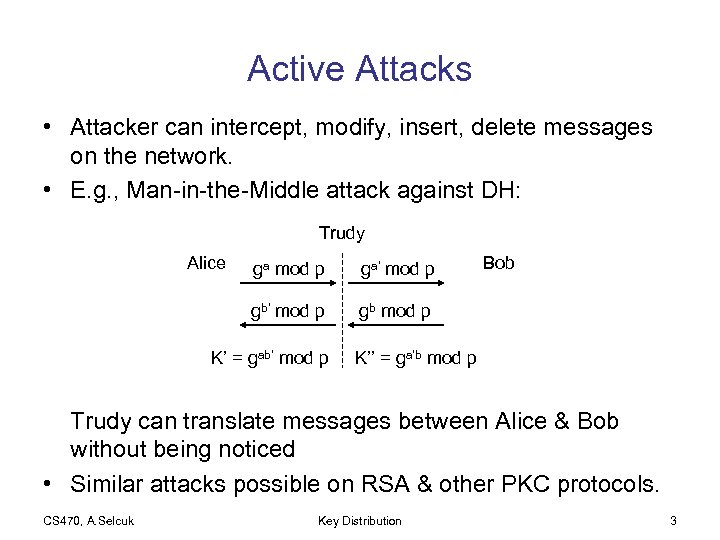
Active Attacks • Attacker can intercept, modify, insert, delete messages on the network. • E. g. , Man-in-the-Middle attack against DH: Trudy Alice ga mod p ga’ mod p gb’ mod p Bob gb mod p K’ = gab’ mod p K’’ = ga’b mod p Trudy can translate messages between Alice & Bob without being noticed • Similar attacks possible on RSA & other PKC protocols. CS 470, A. Selcuk Key Distribution 3

Trusted Third Parties • Solution against active attackers: “Trusted Third Parties” (TTPs) • Symmetric key solution: KDC – Everyone registers with the KDC, shares a secret key. – When A & B want to communicate, they contact the KDC & obtain a session key. • Public key solution: CA – Everyone registers with the CA, obtains a “certificate” for his/her public key. – Certificate: A document signed by the CA, including the ID and the public key of the subject. – People obtain each other’s certificates thru a repository, a webpage, or at the beginning of the protocol, – and use the certified public keys in the protocols. CS 470, A. Selcuk Key Distribution 4
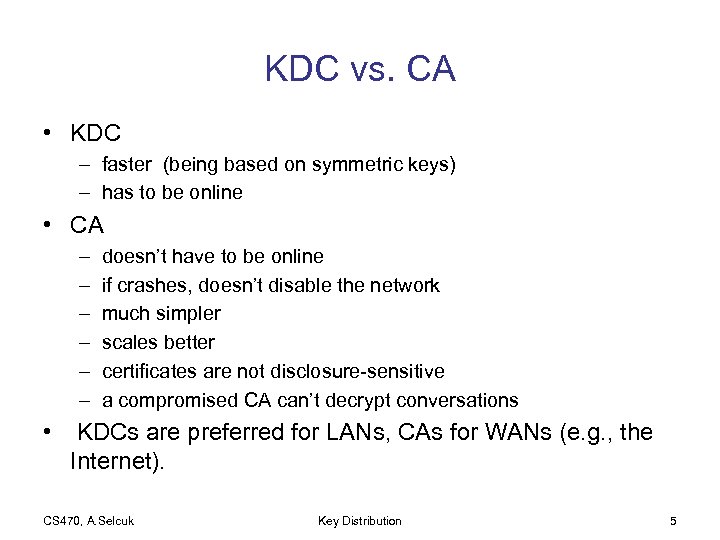
KDC vs. CA • KDC – faster (being based on symmetric keys) – has to be online • CA – – – • doesn’t have to be online if crashes, doesn’t disable the network much simpler scales better certificates are not disclosure-sensitive a compromised CA can’t decrypt conversations KDCs are preferred for LANs, CAs for WANs (e. g. , the Internet). CS 470, A. Selcuk Key Distribution 5
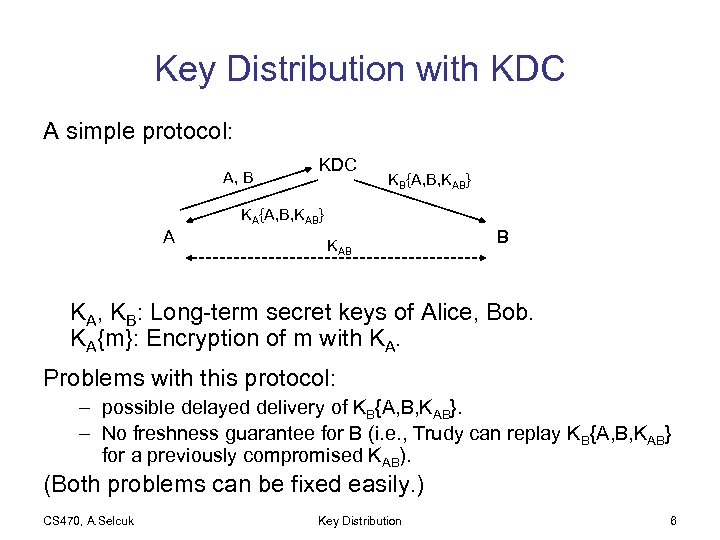
Key Distribution with KDC A simple protocol: A, B KDC KB{A, B, KAB} KA{A, B, KAB} A KAB B KA, KB: Long-term secret keys of Alice, Bob. KA{m}: Encryption of m with KA. Problems with this protocol: – possible delayed delivery of KB{A, B, KAB}. – No freshness guarantee for B (i. e. , Trudy can replay KB{A, B, KAB} for a previously compromised KAB). (Both problems can be fixed easily. ) CS 470, A. Selcuk Key Distribution 6
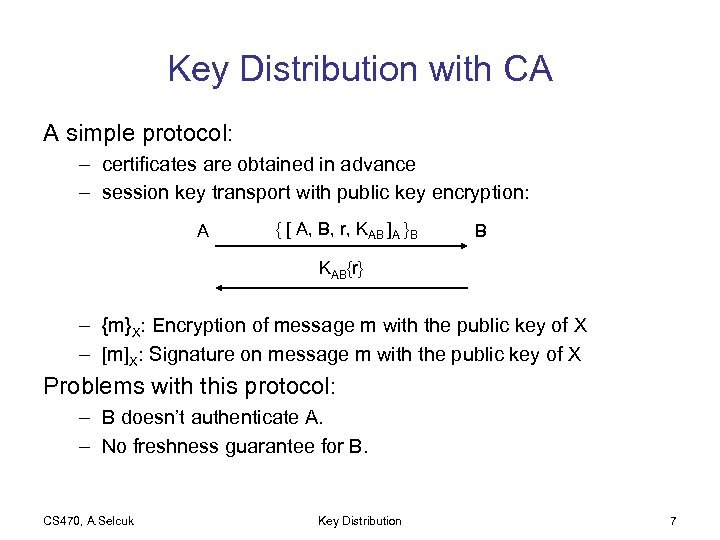
Key Distribution with CA A simple protocol: – certificates are obtained in advance – session key transport with public key encryption: A { [ A, B, r, KAB ]A }B B KAB{r} – {m}X: Encryption of message m with the public key of X – [m]X: Signature on message m with the public key of X Problems with this protocol: – B doesn’t authenticate A. – No freshness guarantee for B. CS 470, A. Selcuk Key Distribution 7
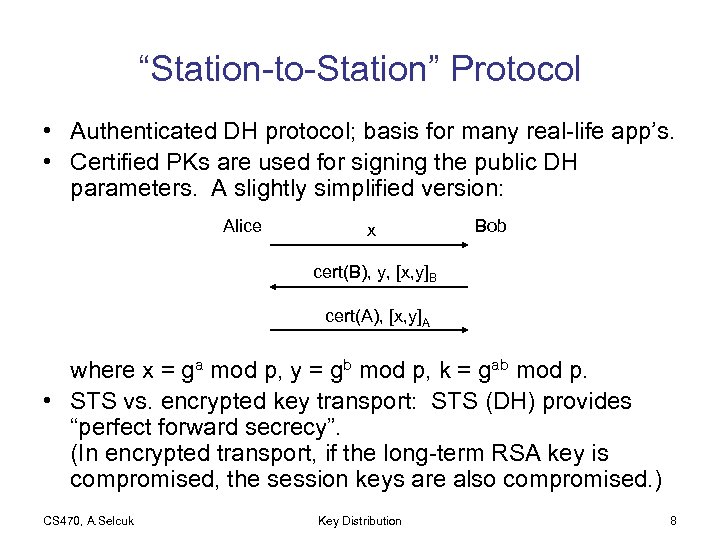
“Station-to-Station” Protocol • Authenticated DH protocol; basis for many real-life app’s. • Certified PKs are used for signing the public DH parameters. A slightly simplified version: Alice x Bob cert(B), y, [x, y]B cert(A), [x, y]A where x = ga mod p, y = gb mod p, k = gab mod p. • STS vs. encrypted key transport: STS (DH) provides “perfect forward secrecy”. (In encrypted transport, if the long-term RSA key is compromised, the session keys are also compromised. ) CS 470, A. Selcuk Key Distribution 8
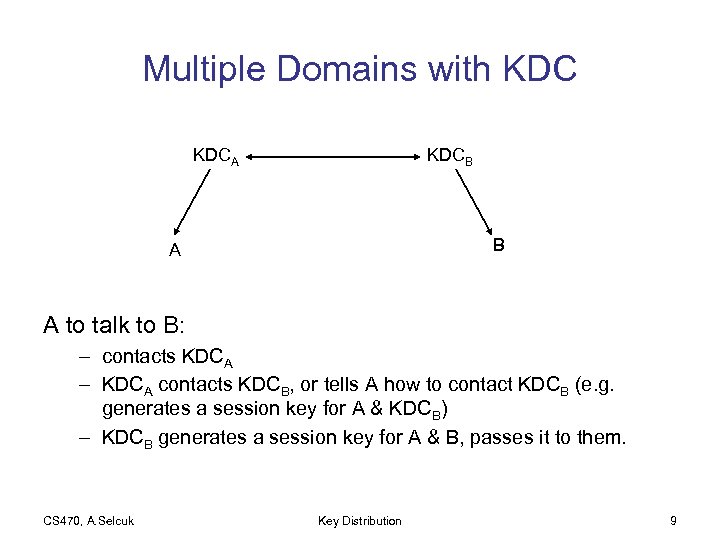
Multiple Domains with KDCA KDCB B A A to talk to B: – contacts KDCA – KDCA contacts KDCB, or tells A how to contact KDCB (e. g. generates a session key for A & KDCB) – KDCB generates a session key for A & B, passes it to them. CS 470, A. Selcuk Key Distribution 9
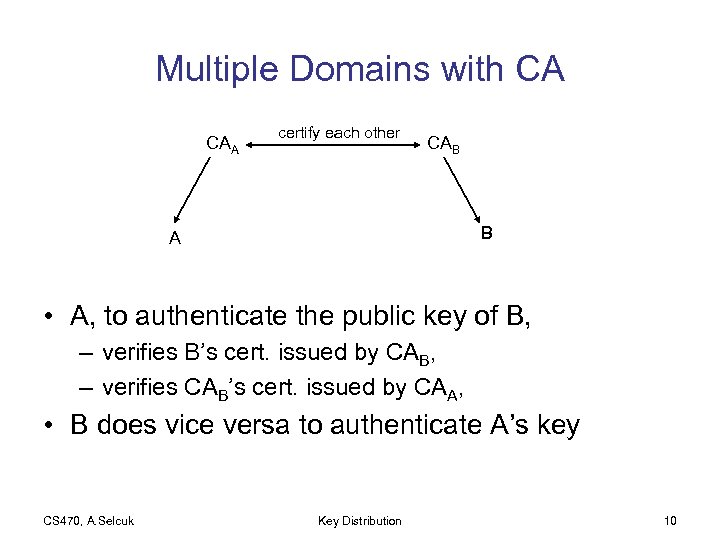
Multiple Domains with CA CAA certify each other CAB B A • A, to authenticate the public key of B, – verifies B’s cert. issued by CAB, – verifies CAB’s cert. issued by CAA, • B does vice versa to authenticate A’s key CS 470, A. Selcuk Key Distribution 10

ID-Based Crypto • Idea: Is a scheme possible where Alice’s public key is her ID? • Would solve the problem of authenticating a public key received. • Q: But if anyone can derive the public key from the ID, can’t they derive the private key as well? • Support from a trusted “private key generator”. – Private keys are generated from a unique secret S known by PKG. – Users know a one-way function of S, sufficient for public key generation. • Practical schemes exist for signature (Shamir) and encryption (Boneh-Franklin). CS 470, A. Selcuk Key Distribution 11

ID-Based Crypto • Advantages: – There is no need for Alice to retrieve Bob’s certificate to send him an encrypted message. – Alice can send Bob an encrypted message even before he gets his decryption key. • Disadvantages: – Key revocation is (almost) impossible. – It is not so significant in interactive protocols. • “Feature”: – Inherent key escrow. CS 470, A. Selcuk Key Distribution 12
Crypto-Based ID • Similar to ID-based crypto, ID and PK are inherently related. • But instead of generating PK from ID, do the opposite: IDA = h(PKA). • Useful in pseudonym systems where (part of) the ID can be given a random value. – P 2 P systems – IPv 6 “cryptographically generated address” • No “big brother” is necessary. CS 470, A. Selcuk Key Distribution 13
307623db21da97ea0a78a34d373208f2.ppt