fd9ebad04310900cfd578702266dd228.ppt
- Количество слайдов: 23
 Juniper Security Products and Solutions Overview Stephen Philip Senior Director - Product Marketing Security Products Group Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1 1
Juniper Security Products and Solutions Overview Stephen Philip Senior Director - Product Marketing Security Products Group Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 1 1
 Agenda § Juniper leadership in Security § Juniper Product Portfolio § Juniper Solutions by Location • • • Campus WAN GW Data Center Distributed Organization Extended Organization Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 2 2
Agenda § Juniper leadership in Security § Juniper Product Portfolio § Juniper Solutions by Location • • • Campus WAN GW Data Center Distributed Organization Extended Organization Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 2 2
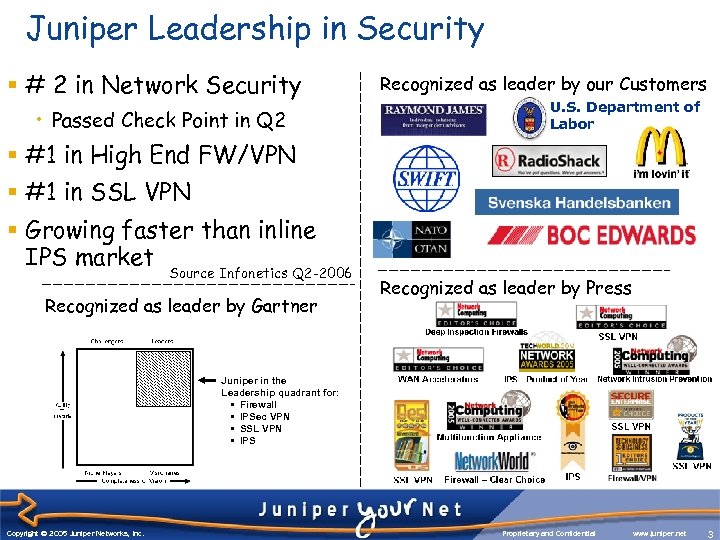 Juniper Leadership in Security § # 2 in Network Security • Passed Check Point in Q 2 Recognized as leader by our Customers U. S. Department of Labor § #1 in High End FW/VPN § #1 in SSL VPN § Growing faster than inline IPS market Source Infonetics Q 2 -2006 Recognized as leader by Gartner Recognized as leader by Press Juniper in the Leadership quadrant for: • Firewall • IPSec VPN • SSL VPN • IPS Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 3 3
Juniper Leadership in Security § # 2 in Network Security • Passed Check Point in Q 2 Recognized as leader by our Customers U. S. Department of Labor § #1 in High End FW/VPN § #1 in SSL VPN § Growing faster than inline IPS market Source Infonetics Q 2 -2006 Recognized as leader by Gartner Recognized as leader by Press Juniper in the Leadership quadrant for: • Firewall • IPSec VPN • SSL VPN • IPS Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 3 3
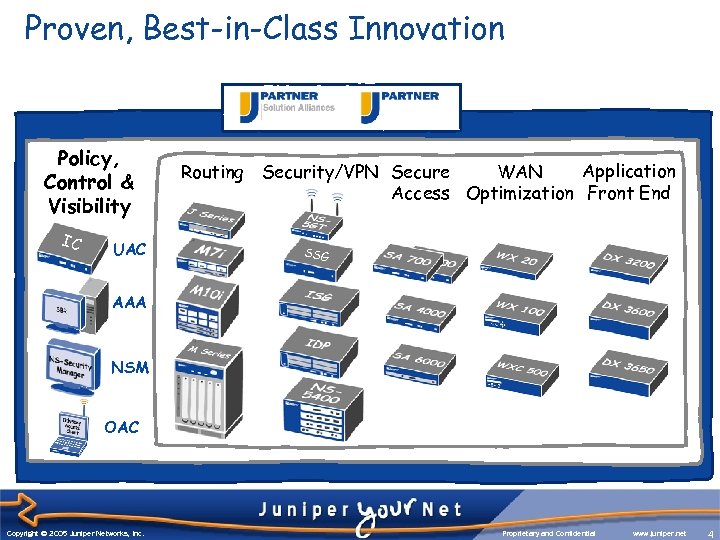 Proven, Best-in-Class Innovation Policy, Control & Visibility IC UAC Routing Application Security/VPN Secure WAN Access Optimization Front End SSG AAA NSM OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 4 4
Proven, Best-in-Class Innovation Policy, Control & Visibility IC UAC Routing Application Security/VPN Secure WAN Access Optimization Front End SSG AAA NSM OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 4 4
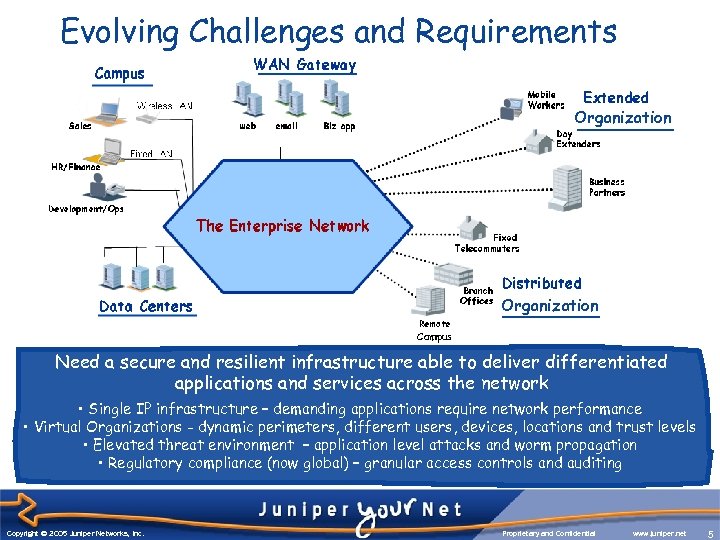 Evolving Challenges and Requirements Organization Campus Need a secure and resilient infrastructure able to deliver differentiated applications and services across the network • Single IP infrastructure – demanding applications require network performance • Virtual Organizations - dynamic perimeters, different users, devices, locations and trust levels • Elevated threat environment – application level attacks and worm propagation • Regulatory compliance (now global) – granular access controls and auditing Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 5 5
Evolving Challenges and Requirements Organization Campus Need a secure and resilient infrastructure able to deliver differentiated applications and services across the network • Single IP infrastructure – demanding applications require network performance • Virtual Organizations - dynamic perimeters, different users, devices, locations and trust levels • Elevated threat environment – application level attacks and worm propagation • Regulatory compliance (now global) – granular access controls and auditing Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 5 5
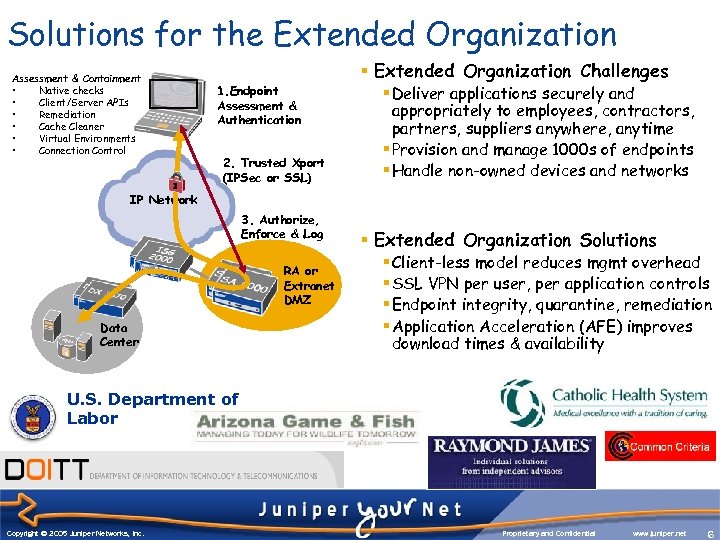 Solutions for the Extended Organization Assessment & Containment • Native checks • Client/Server APIs • Remediation • Cache Cleaner • Virtual Environments • Connection Control 1. Endpoint Assessment & Authentication 2. Trusted Xport (IPSec or SSL) § Extended Organization Challenges § Deliver applications securely and appropriately to employees, contractors, partners, suppliers anywhere, anytime § Provision and manage 1000 s of endpoints § Handle non-owned devices and networks IP Network 3. Authorize, Enforce & Log RA or Extranet DMZ Data Center § Extended Organization Solutions § Client-less model reduces mgmt overhead § SSL VPN per user, per application controls § Endpoint integrity, quarantine, remediation § Application Acceleration (AFE) improves download times & availability U. S. Department of Labor Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 6 6
Solutions for the Extended Organization Assessment & Containment • Native checks • Client/Server APIs • Remediation • Cache Cleaner • Virtual Environments • Connection Control 1. Endpoint Assessment & Authentication 2. Trusted Xport (IPSec or SSL) § Extended Organization Challenges § Deliver applications securely and appropriately to employees, contractors, partners, suppliers anywhere, anytime § Provision and manage 1000 s of endpoints § Handle non-owned devices and networks IP Network 3. Authorize, Enforce & Log RA or Extranet DMZ Data Center § Extended Organization Solutions § Client-less model reduces mgmt overhead § SSL VPN per user, per application controls § Endpoint integrity, quarantine, remediation § Application Acceleration (AFE) improves download times & availability U. S. Department of Labor Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 6 6
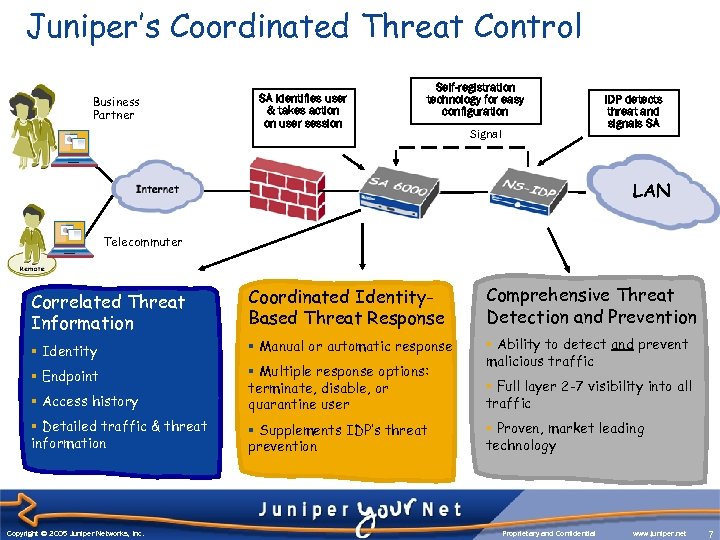 Juniper’s Coordinated Threat Control Business Partner SA identifies user & takes action on user session Self-registration technology for easy configuration Signal IDP detects threat and signals SA LAN Telecommuter Correlated Threat Information Coordinated Identity. Based Threat Response Comprehensive Threat Detection and Prevention § Identity § Manual or automatic response § Endpoint § Access history § Multiple response options: terminate, disable, or quarantine user § Ability to detect and prevent malicious traffic § Detailed traffic & threat information § Supplements IDP’s threat prevention Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. § Full layer 2 -7 visibility into all traffic § Proven, market leading technology Proprietary and Confidential www. juniper. net 7 7
Juniper’s Coordinated Threat Control Business Partner SA identifies user & takes action on user session Self-registration technology for easy configuration Signal IDP detects threat and signals SA LAN Telecommuter Correlated Threat Information Coordinated Identity. Based Threat Response Comprehensive Threat Detection and Prevention § Identity § Manual or automatic response § Endpoint § Access history § Multiple response options: terminate, disable, or quarantine user § Ability to detect and prevent malicious traffic § Detailed traffic & threat information § Supplements IDP’s threat prevention Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. § Full layer 2 -7 visibility into all traffic § Proven, market leading technology Proprietary and Confidential www. juniper. net 7 7
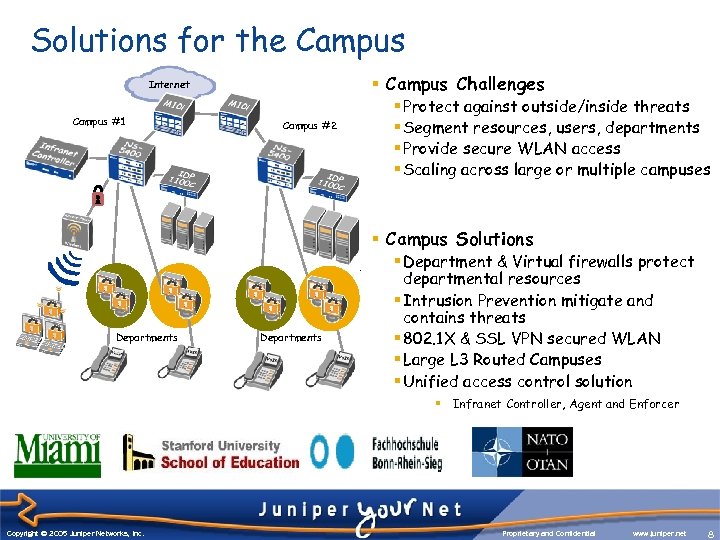 Solutions for the Campus § Campus Challenges Internet Campus #1 Campus #2 § Protect against outside/inside threats § Segment resources, users, departments § Provide secure WLAN access § Scaling across large or multiple campuses § Campus Solutions Departments § Department & Virtual firewalls protect departmental resources § Intrusion Prevention mitigate and contains threats § 802. 1 X & SSL VPN secured WLAN § Large L 3 Routed Campuses § Unified access control solution § Infranet Controller, Agent and Enforcer Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 8 8
Solutions for the Campus § Campus Challenges Internet Campus #1 Campus #2 § Protect against outside/inside threats § Segment resources, users, departments § Provide secure WLAN access § Scaling across large or multiple campuses § Campus Solutions Departments § Department & Virtual firewalls protect departmental resources § Intrusion Prevention mitigate and contains threats § 802. 1 X & SSL VPN secured WLAN § Large L 3 Routed Campuses § Unified access control solution § Infranet Controller, Agent and Enforcer Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 8 8
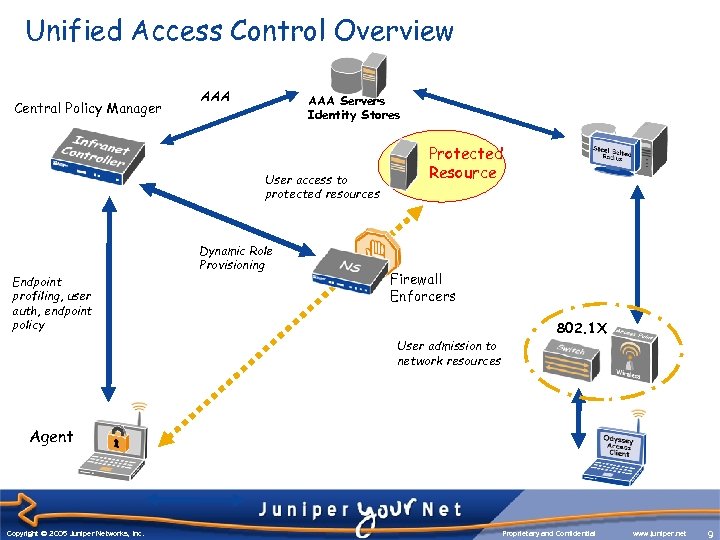 Unified Access Control Overview Central Policy Manager AAA Servers Identity Stores User access to protected resources Endpoint profiling, user auth, endpoint policy Dynamic Role Provisioning Protected Resource Firewall Enforcers 802. 1 X User admission to network resources Agent Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 9 9
Unified Access Control Overview Central Policy Manager AAA Servers Identity Stores User access to protected resources Endpoint profiling, user auth, endpoint policy Dynamic Role Provisioning Protected Resource Firewall Enforcers 802. 1 X User admission to network resources Agent Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 9 9
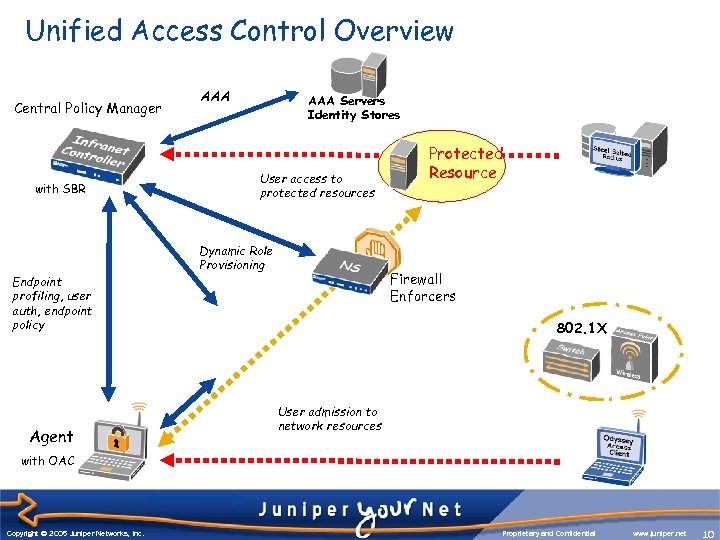 Unified Access Control Overview Central Policy Manager with SBR Endpoint profiling, user auth, endpoint policy Agent AAA Servers Identity Stores User access to protected resources Dynamic Role Provisioning Protected Resource Firewall Enforcers 802. 1 X User admission to network resources with OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10 10
Unified Access Control Overview Central Policy Manager with SBR Endpoint profiling, user auth, endpoint policy Agent AAA Servers Identity Stores User access to protected resources Dynamic Role Provisioning Protected Resource Firewall Enforcers 802. 1 X User admission to network resources with OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 10 10
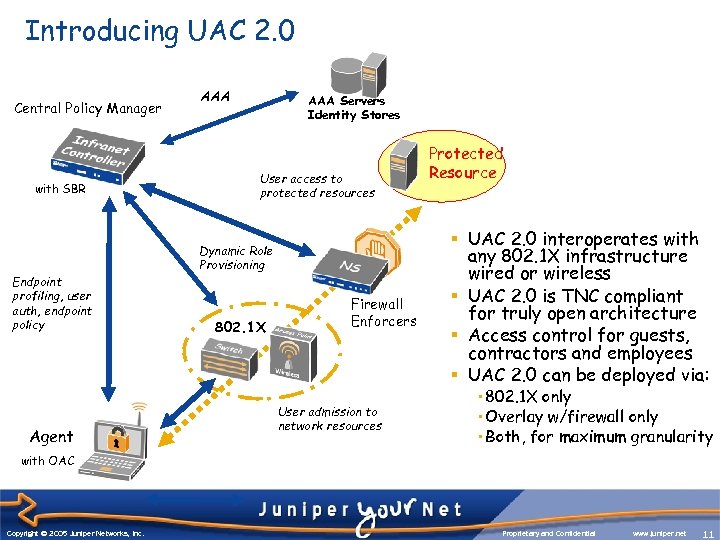 Introducing UAC 2. 0 Central Policy Manager with SBR Endpoint profiling, user auth, endpoint policy Agent AAA Servers Identity Stores User access to protected resources Dynamic Role Provisioning 802. 1 X Firewall Enforcers User admission to network resources Protected Resource § UAC 2. 0 interoperates with any 802. 1 X infrastructure wired or wireless § UAC 2. 0 is TNC compliant for truly open architecture § Access control for guests, contractors and employees § UAC 2. 0 can be deployed via: • 802. 1 X only • Overlay w/firewall only • Both, for maximum granularity with OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 11 11
Introducing UAC 2. 0 Central Policy Manager with SBR Endpoint profiling, user auth, endpoint policy Agent AAA Servers Identity Stores User access to protected resources Dynamic Role Provisioning 802. 1 X Firewall Enforcers User admission to network resources Protected Resource § UAC 2. 0 interoperates with any 802. 1 X infrastructure wired or wireless § UAC 2. 0 is TNC compliant for truly open architecture § Access control for guests, contractors and employees § UAC 2. 0 can be deployed via: • 802. 1 X only • Overlay w/firewall only • Both, for maximum granularity with OAC Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 11 11
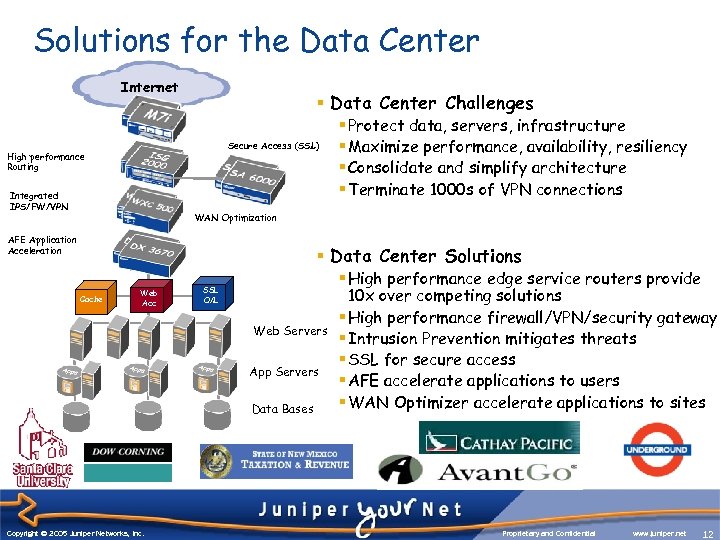 Solutions for the Data Center Internet § Data Center Challenges Secure Access (SSL) High performance Routing Integrated IPS/FW/VPN § Protect data, servers, infrastructure § Maximize performance, availability, resiliency § Consolidate and simplify architecture § Terminate 1000 s of VPN connections WAN Optimization AFE Application Acceleration § Data Center Solutions SLB Cache Web Acc SSL O/L Web Servers App Servers Data Bases Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. § High performance edge service routers provide 10 x over competing solutions § High performance firewall/VPN/security gateway § Intrusion Prevention mitigates threats § SSL for secure access § AFE accelerate applications to users § WAN Optimizer accelerate applications to sites Proprietary and Confidential www. juniper. net 12 12
Solutions for the Data Center Internet § Data Center Challenges Secure Access (SSL) High performance Routing Integrated IPS/FW/VPN § Protect data, servers, infrastructure § Maximize performance, availability, resiliency § Consolidate and simplify architecture § Terminate 1000 s of VPN connections WAN Optimization AFE Application Acceleration § Data Center Solutions SLB Cache Web Acc SSL O/L Web Servers App Servers Data Bases Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. § High performance edge service routers provide 10 x over competing solutions § High performance firewall/VPN/security gateway § Intrusion Prevention mitigates threats § SSL for secure access § AFE accelerate applications to users § WAN Optimizer accelerate applications to sites Proprietary and Confidential www. juniper. net 12 12
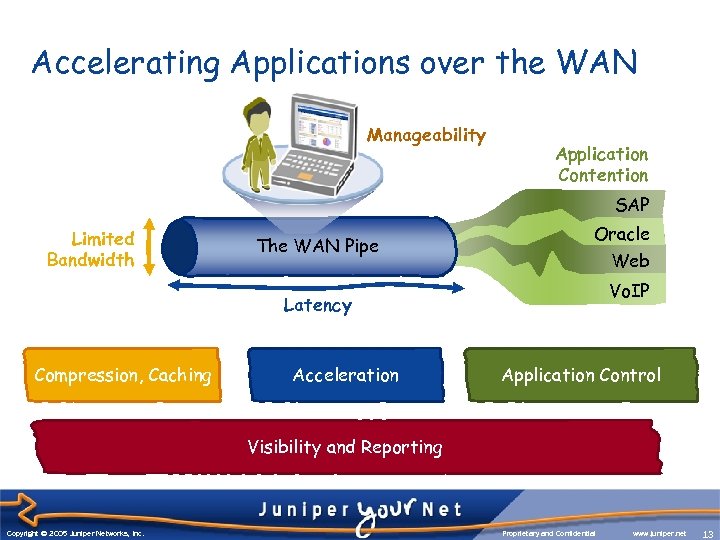 How the WAN slows applications Accelerating Applications over the WAN Manageability Application Contention SAP Limited Bandwidth Oracle Web The WAN Pipe Vo. IP Latency Compression, Caching More rich content Protocol chattiness Acceleration Lower-priority apps Application Control slow down critical ones Visibility and Reporting Inability to understand application and WAN performance Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 13 13
How the WAN slows applications Accelerating Applications over the WAN Manageability Application Contention SAP Limited Bandwidth Oracle Web The WAN Pipe Vo. IP Latency Compression, Caching More rich content Protocol chattiness Acceleration Lower-priority apps Application Control slow down critical ones Visibility and Reporting Inability to understand application and WAN performance Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 13 13
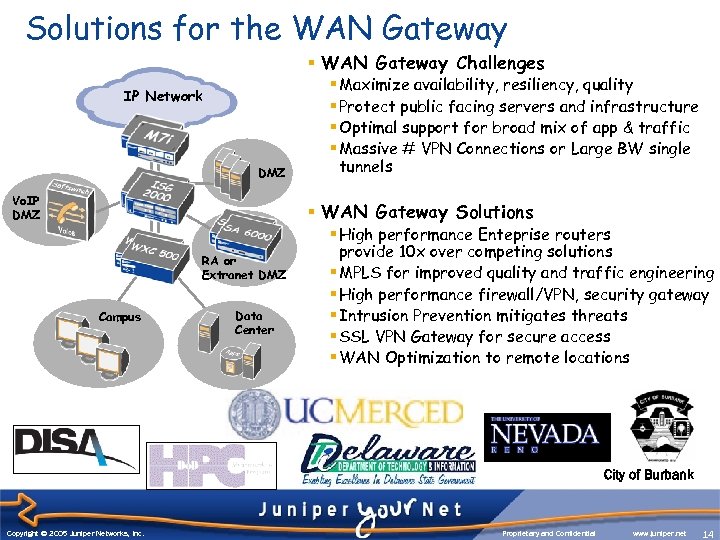 Solutions for the WAN Gateway § WAN Gateway Challenges IP Network DMZ Vo. IP DMZ § Maximize availability, resiliency, quality § Protect public facing servers and infrastructure § Optimal support for broad mix of app & traffic § Massive # VPN Connections or Large BW single tunnels § WAN Gateway Solutions RA or Extranet DMZ Campus Data Center § High performance Enteprise routers provide 10 x over competing solutions § MPLS for improved quality and traffic engineering § High performance firewall/VPN, security gateway § Intrusion Prevention mitigates threats § SSL VPN Gateway for secure access § WAN Optimization to remote locations City of Burbank Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 14 14
Solutions for the WAN Gateway § WAN Gateway Challenges IP Network DMZ Vo. IP DMZ § Maximize availability, resiliency, quality § Protect public facing servers and infrastructure § Optimal support for broad mix of app & traffic § Massive # VPN Connections or Large BW single tunnels § WAN Gateway Solutions RA or Extranet DMZ Campus Data Center § High performance Enteprise routers provide 10 x over competing solutions § MPLS for improved quality and traffic engineering § High performance firewall/VPN, security gateway § Intrusion Prevention mitigates threats § SSL VPN Gateway for secure access § WAN Optimization to remote locations City of Burbank Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 14 14
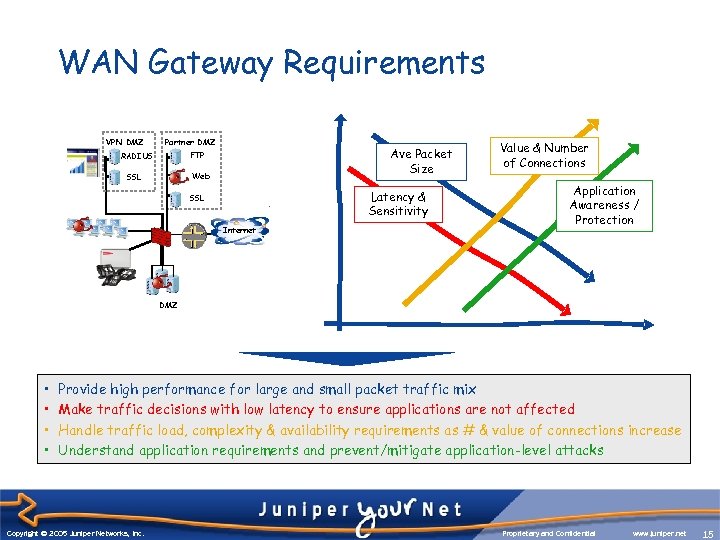 WAN Gateway Requirements VPN DMZ Partner DMZ Ave Packet Size FTP RADIUS Web SSL Latency & Sensitivity SSL Internet Value & Number of Connections Application Awareness / Protection DMZ • • Provide high performance for large and small packet traffic mix Make traffic decisions with low latency to ensure applications are not affected Handle traffic load, complexity & availability requirements as # & value of connections increase Understand application requirements and prevent/mitigate application-level attacks Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 15 15
WAN Gateway Requirements VPN DMZ Partner DMZ Ave Packet Size FTP RADIUS Web SSL Latency & Sensitivity SSL Internet Value & Number of Connections Application Awareness / Protection DMZ • • Provide high performance for large and small packet traffic mix Make traffic decisions with low latency to ensure applications are not affected Handle traffic load, complexity & availability requirements as # & value of connections increase Understand application requirements and prevent/mitigate application-level attacks Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 15 15
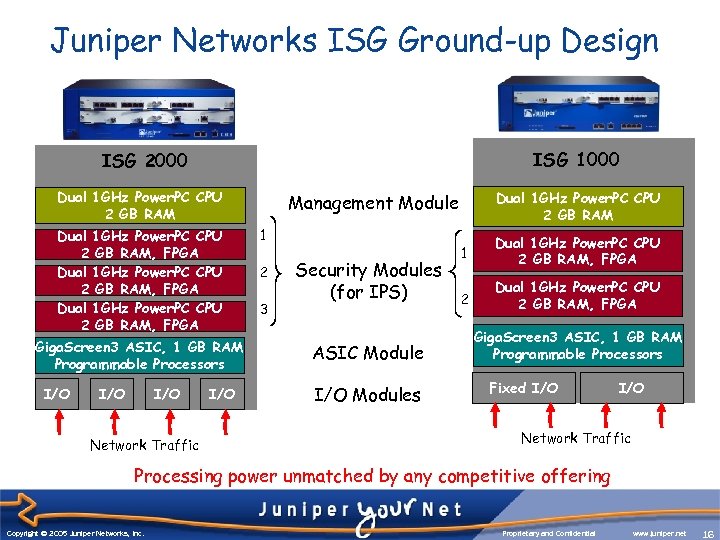 Juniper Networks ISG Ground-up Design ISG 1000 ISG 2000 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA Giga. Screen 3 ASIC, 1 GB RAM Programmable Processors I/O I/O Network Traffic I/O Dual 1 GHz Power. PC CPU 2 GB RAM Management Module 1 2 3 Security Modules (for IPS) ASIC Module I/O Modules 1 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA 2 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA Giga. Screen 3 ASIC, 1 GB RAM Programmable Processors Fixed I/O Network Traffic Processing power unmatched by any competitive offering Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 16 16
Juniper Networks ISG Ground-up Design ISG 1000 ISG 2000 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA Giga. Screen 3 ASIC, 1 GB RAM Programmable Processors I/O I/O Network Traffic I/O Dual 1 GHz Power. PC CPU 2 GB RAM Management Module 1 2 3 Security Modules (for IPS) ASIC Module I/O Modules 1 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA 2 Dual 1 GHz Power. PC CPU 2 GB RAM, FPGA Giga. Screen 3 ASIC, 1 GB RAM Programmable Processors Fixed I/O Network Traffic Processing power unmatched by any competitive offering Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 16 16
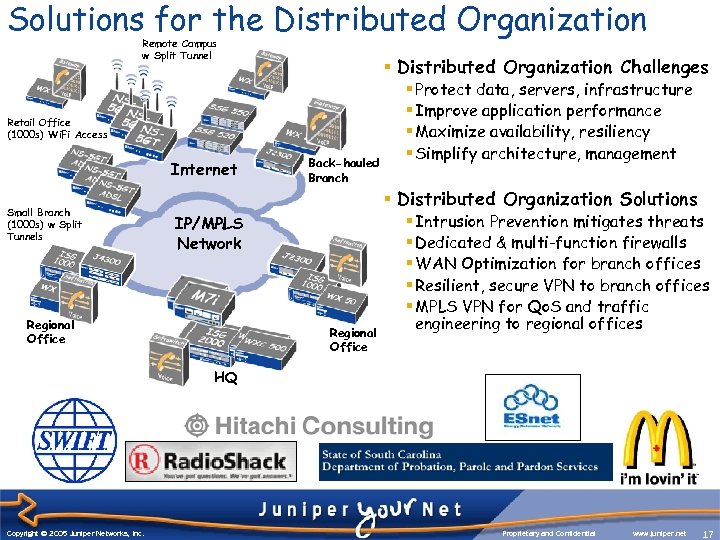 Solutions for the Distributed Organization Remote Campus w Split Tunnel § Distributed Organization Challenges Retail Office (1000 s) Wi. Fi Access Internet Small Branch (1000 s) w Split Tunnels Back-hauled Branch IP/MPLS Network Regional Office § Protect data, servers, infrastructure § Improve application performance § Maximize availability, resiliency § Simplify architecture, management § Distributed Organization Solutions § Intrusion Prevention mitigates threats § Dedicated & multi-function firewalls § WAN Optimization for branch offices § Resilient, secure VPN to branch offices § MPLS VPN for Qo. S and traffic engineering to regional offices HQ Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 17 17
Solutions for the Distributed Organization Remote Campus w Split Tunnel § Distributed Organization Challenges Retail Office (1000 s) Wi. Fi Access Internet Small Branch (1000 s) w Split Tunnels Back-hauled Branch IP/MPLS Network Regional Office § Protect data, servers, infrastructure § Improve application performance § Maximize availability, resiliency § Simplify architecture, management § Distributed Organization Solutions § Intrusion Prevention mitigates threats § Dedicated & multi-function firewalls § WAN Optimization for branch offices § Resilient, secure VPN to branch offices § MPLS VPN for Qo. S and traffic engineering to regional offices HQ Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 17 17
 Best in Class Security – Secure Services Gateway New Secure Services Gateway Models § Advanced Security - Integrated Branch Routing and WAN interfaces • FW, VPN , AV (including - phishing, - spyware) & Anti SPAM • ADSL 2+, T 1, E 1, ISDN BRI S/T, V. 92, Gig E § SSG 5 - Six fixed form factor models • • § • ISDN BRI S/T, V. 92, Serial Dual radio 802. 11 a + 802. 11 b/g variants of each 160 Mbps FW / 40 Mbps VPN 5 Fast Ethernet + 2 Mini I/O slots • • Mini PIM options include ADSL 2+, T 1, E 1, ISDN BRI S/T, V. 92 at FCS Dual radio 802. 11 a + 802. 11 b/g variant 160 Mbps FW / 40 Mbps VPN SSG 140 • • • § • • SSG 20 – 2 modular models • § 7 Fast Ethernet + 1 WAN interface 8 FE and 2 GE Interfaces 4 WAN PIM slots • • Standard J Series WAN interfaces ISDN, Dual E 1 and Dual T 1 350 Mbps FW / 100 Mbps VPN SSG 550/520 • • 6 WAN/LAN I/O expansion slots • Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. 4 on-board 10/1000 ports Up to 1 Gbps FW/NAT / 500 Mbps IPSec / 500 Mbps IPS (DI) Proprietary and Confidential www. juniper. net 18 18
Best in Class Security – Secure Services Gateway New Secure Services Gateway Models § Advanced Security - Integrated Branch Routing and WAN interfaces • FW, VPN , AV (including - phishing, - spyware) & Anti SPAM • ADSL 2+, T 1, E 1, ISDN BRI S/T, V. 92, Gig E § SSG 5 - Six fixed form factor models • • § • ISDN BRI S/T, V. 92, Serial Dual radio 802. 11 a + 802. 11 b/g variants of each 160 Mbps FW / 40 Mbps VPN 5 Fast Ethernet + 2 Mini I/O slots • • Mini PIM options include ADSL 2+, T 1, E 1, ISDN BRI S/T, V. 92 at FCS Dual radio 802. 11 a + 802. 11 b/g variant 160 Mbps FW / 40 Mbps VPN SSG 140 • • • § • • SSG 20 – 2 modular models • § 7 Fast Ethernet + 1 WAN interface 8 FE and 2 GE Interfaces 4 WAN PIM slots • • Standard J Series WAN interfaces ISDN, Dual E 1 and Dual T 1 350 Mbps FW / 100 Mbps VPN SSG 550/520 • • 6 WAN/LAN I/O expansion slots • Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. 4 on-board 10/1000 ports Up to 1 Gbps FW/NAT / 500 Mbps IPSec / 500 Mbps IPS (DI) Proprietary and Confidential www. juniper. net 18 18
 Deploy Once – Add Services later § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 19 19
Deploy Once – Add Services later § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 19 19
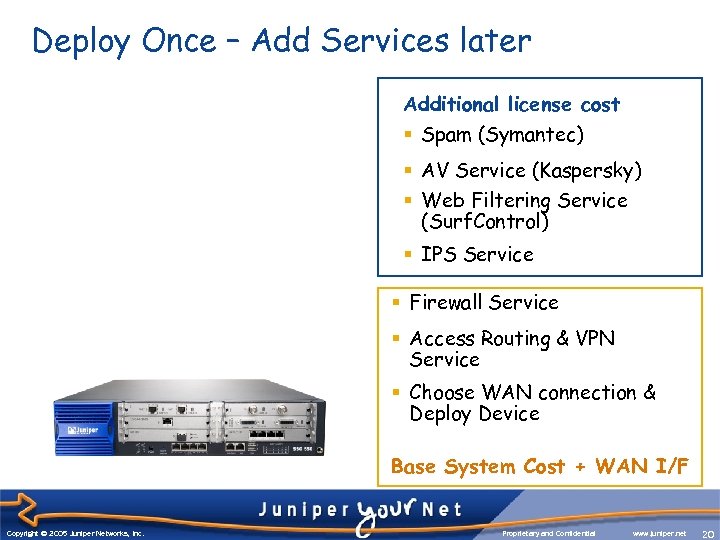 Deploy Once – Add Services later Additional license cost § Spam (Symantec) § AV Service (Kaspersky) § Web Filtering Service (Surf. Control) § IPS Service § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 20 20
Deploy Once – Add Services later Additional license cost § Spam (Symantec) § AV Service (Kaspersky) § Web Filtering Service (Surf. Control) § IPS Service § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 20 20
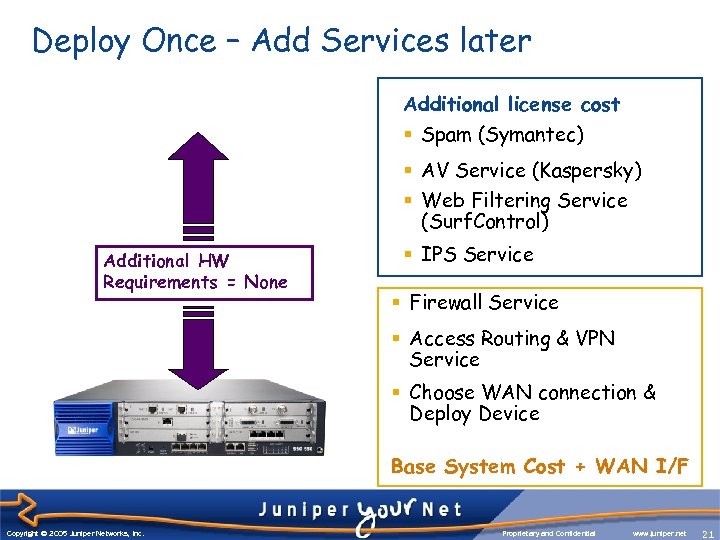 Deploy Once – Add Services later Additional license cost § Spam (Symantec) § AV Service (Kaspersky) § Web Filtering Service (Surf. Control) Additional HW Requirements = None § IPS Service § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 21 21
Deploy Once – Add Services later Additional license cost § Spam (Symantec) § AV Service (Kaspersky) § Web Filtering Service (Surf. Control) Additional HW Requirements = None § IPS Service § Firewall Service § Access Routing & VPN Service § Choose WAN connection & Deploy Device Base System Cost + WAN I/F Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 21 21
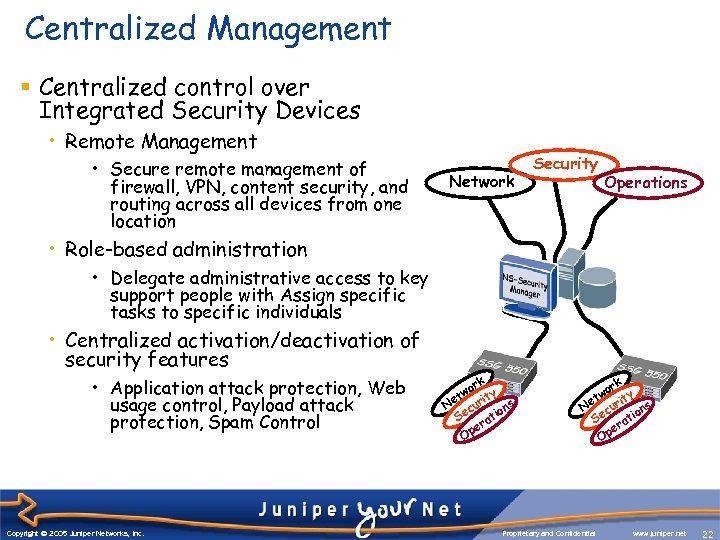 Centralized Management § Centralized control over Integrated Security Devices • Remote Management • Secure remote management of firewall, VPN, content security, and routing across all devices from one location Network Security Operations • Role-based administration • Delegate administrative access to key support people with Assign specific tasks to specific individuals • Centralized activation/deactivation of security features • Application attack protection, Web usage control, Payload attack protection, Spam Control Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. rk wo ity t Ne cur ons Se rati e Op Proprietary and Confidential www. juniper. net 22 22
Centralized Management § Centralized control over Integrated Security Devices • Remote Management • Secure remote management of firewall, VPN, content security, and routing across all devices from one location Network Security Operations • Role-based administration • Delegate administrative access to key support people with Assign specific tasks to specific individuals • Centralized activation/deactivation of security features • Application attack protection, Web usage control, Payload attack protection, Spam Control Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. rk wo ity t Ne cur ons Se rati e Op Proprietary and Confidential www. juniper. net 22 22
 Thanks Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 23 23
Thanks Copyright © 2003 Juniper Networks, Inc. Copyright © 2005 Juniper Networks, Inc. Proprietary and Confidential www. juniper. net 23 23


