2883e86e195f320180377b5c1f1933fb.ppt
- Количество слайдов: 8

John Douglass, Developer Ron Hutchins, Dir. Engineering Herbert Baines, Dir. Info. Sec

Issuing Digital Credentials • Relying upon our current Kerberos implementation • Attributes stored depend upon certificate type: • Affiliate Certificate: No user information stored other than a CA generated CN. • Identity Certificate: CN, userid, OU, O, L, SP, C • Not in widespread use (still in development stage other than GTRI) relying on IP based access control.

Institute Repositories • Campus wide data warehouse (Oracle) retrieves data from Banner and People. Soft • LDAP directory fed from data warehouse • PH directory fed from Kerberos database • Pilot Active Directory fed from data warehouse.

Current Repository Applications • • • VPN use authorization via LDAP Phonebook (LDAP, Ph) Campus DHCP Registration Bulk mailing list generation Web. CT
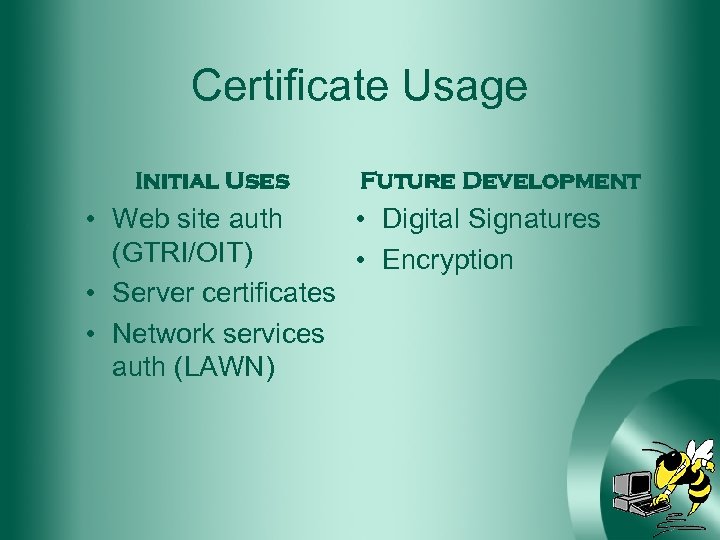
Certificate Usage Initial Uses Future Development • Web site auth • Digital Signatures (GTRI/OIT) • Encryption • Server certificates • Network services auth (LAWN)

PKI Deployment • The initial groups for certificate use will be GTRI, library, and CBT users. • Utilizing GT developed CA software (PERL, My. SQL, Open. SSL, Apache) running on a Sun Ultra 2 (Solaris 8)

Content Providers • Access currently limited by IP address range. • Developed a Check. Point VPN solution as an interim solution.

Are We Ready? • The Certificate Authority software (“Papyrus”) is ready to distribute certificates. • Documentation is available, but does not cover everything. • Browser support is often times unreliable. • User education will be greatest challenge.
2883e86e195f320180377b5c1f1933fb.ppt