79cd10aa723232b384495be1f1b69f90.ppt
- Количество слайдов: 36
 Jessica Cassano 497 -00 -6092 www. umsl. edu/~lacity/int 480 a. htm 1
Jessica Cassano 497 -00 -6092 www. umsl. edu/~lacity/int 480 a. htm 1
 The CYBER GANG www. umsl. edu/~lacity/int 480 a. htm 2
The CYBER GANG www. umsl. edu/~lacity/int 480 a. htm 2
 A Comprehensive Approach to Managing Cyber-Security (including Privacy Considerations) Darin Hancock La. Wanda Jones (2007 PMBA UMSL Cohorts) 11/2005 Prepared for: IS 6800 3
A Comprehensive Approach to Managing Cyber-Security (including Privacy Considerations) Darin Hancock La. Wanda Jones (2007 PMBA UMSL Cohorts) 11/2005 Prepared for: IS 6800 3
 Common Types of Potential Cyber Threats VIRUS WORM TROJAN Do. S (Denial of Service) SPAM SALAMI PHISHING PHREAKING ONLINE FRAUD, IDENTITY & DATA THEFT DUMPSTER DIVING SOCIAL ENGINEERING NATURAL DISASTER www. thefreedictionary. com viewed 10/05 4
Common Types of Potential Cyber Threats VIRUS WORM TROJAN Do. S (Denial of Service) SPAM SALAMI PHISHING PHREAKING ONLINE FRAUD, IDENTITY & DATA THEFT DUMPSTER DIVING SOCIAL ENGINEERING NATURAL DISASTER www. thefreedictionary. com viewed 10/05 4
 Definitions An infectious program that reproduces itself, destroying data along the way. VIRUS The practice of sifting refuse from an office or technical installation to extract confidential data. DUMPSTER DIVING An infectious program that reproduces itself over & over using up memory. WORM A network assault that floods the system with multiple requests. DENIAL OF SERVICE (Do. S) A program that appears legitimate, but performs some illicit activity when it is run. TROJAN An anonymous or disguised, unsolicited email sent in mass delivery. SPAM A scam to steal info thru the use of “official” looking emails or websites. PHISHING A series of minor computer crimes that together result in a larger crime. SALAMI ATTACK The art and science of cracking the telephone network. . PHREAKING An emergency situation posing significant danger to life and property that results from a natural cause. NATURAL DISASTER Intentional deception resulting in injury to another person. ONLINE FRAUD, IDENTITY & DATA THEFT To trick people into revealing passwords or other sensitive information. SOCIAL ENGINEERING www. thefreedictionary. com viewed 10/05 5
Definitions An infectious program that reproduces itself, destroying data along the way. VIRUS The practice of sifting refuse from an office or technical installation to extract confidential data. DUMPSTER DIVING An infectious program that reproduces itself over & over using up memory. WORM A network assault that floods the system with multiple requests. DENIAL OF SERVICE (Do. S) A program that appears legitimate, but performs some illicit activity when it is run. TROJAN An anonymous or disguised, unsolicited email sent in mass delivery. SPAM A scam to steal info thru the use of “official” looking emails or websites. PHISHING A series of minor computer crimes that together result in a larger crime. SALAMI ATTACK The art and science of cracking the telephone network. . PHREAKING An emergency situation posing significant danger to life and property that results from a natural cause. NATURAL DISASTER Intentional deception resulting in injury to another person. ONLINE FRAUD, IDENTITY & DATA THEFT To trick people into revealing passwords or other sensitive information. SOCIAL ENGINEERING www. thefreedictionary. com viewed 10/05 5
 6
6
 The Melissa Virus • Date of Attack – March 26, 1999 • Attacker – 30 year old David Smith • Victims – thousands of Microsoft Word 97 and Word 2000 email users • Damage - $80 million http: //www. usdoj. gov/criminal/cybercrime/melissa. htm viewed 10/05 www. viruslist. com viewed 10/05 7
The Melissa Virus • Date of Attack – March 26, 1999 • Attacker – 30 year old David Smith • Victims – thousands of Microsoft Word 97 and Word 2000 email users • Damage - $80 million http: //www. usdoj. gov/criminal/cybercrime/melissa. htm viewed 10/05 www. viruslist. com viewed 10/05 7
 The WANK Worm • Date of Attack – October 16, 1989; 2 days prior to a scheduled space shuttle take off mission • Attacker – 2 teenagers, Electron & Phoenix, from Melbourne, Australia • Victim - NASA • Damage – initial network infection at the Kennedy Space Station in Florida, then weeks later to other sites around the globe, including other agencies: US Dept. of Energy’s Fermi National Accelerator Lab (IL, US) European Center for Nuclear Research (Switzerland) Riken Accelerator Facility (Japan) 8 www. theage. com. au/articles/2003/05/24 viewed 11/05
The WANK Worm • Date of Attack – October 16, 1989; 2 days prior to a scheduled space shuttle take off mission • Attacker – 2 teenagers, Electron & Phoenix, from Melbourne, Australia • Victim - NASA • Damage – initial network infection at the Kennedy Space Station in Florida, then weeks later to other sites around the globe, including other agencies: US Dept. of Energy’s Fermi National Accelerator Lab (IL, US) European Center for Nuclear Research (Switzerland) Riken Accelerator Facility (Japan) 8 www. theage. com. au/articles/2003/05/24 viewed 11/05
 SPAM • • Date of Attack – 1997 to present Attacker – Commercial Advertisers Victim – All email users Damage – Valuable time expended to sort thru mail that penetrated anti-spam filtration Case: James Burdis, Smurfit Stone Sr. VP & CIO, estimates that of the 1. 2 million emails received monthly, 80% is spam; and approx. 82% of the 80% penetrates their anti-spam blocks. 9 www. viruslist. com viewed 10/05
SPAM • • Date of Attack – 1997 to present Attacker – Commercial Advertisers Victim – All email users Damage – Valuable time expended to sort thru mail that penetrated anti-spam filtration Case: James Burdis, Smurfit Stone Sr. VP & CIO, estimates that of the 1. 2 million emails received monthly, 80% is spam; and approx. 82% of the 80% penetrates their anti-spam blocks. 9 www. viruslist. com viewed 10/05
 Cisco Systems Data Theft • • Date of Attack – April 2001 Attacker – 2 Cisco employees Victim - Cisco Damage – approx. $6. 3 million of stolen stock shares 10 www. depts. washington. edu viewed 10/05
Cisco Systems Data Theft • • Date of Attack – April 2001 Attacker – 2 Cisco employees Victim - Cisco Damage – approx. $6. 3 million of stolen stock shares 10 www. depts. washington. edu viewed 10/05
 Losses (quantified & unquantified) • • • Productivity Disruption Time Delays Redirection of Staff Tasks Down & Damaged Networks Data Corruption Profit Loss Disclosure of Sensitive Data Damage to Interdependent Companies Loss of Customers 11 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005
Losses (quantified & unquantified) • • • Productivity Disruption Time Delays Redirection of Staff Tasks Down & Damaged Networks Data Corruption Profit Loss Disclosure of Sensitive Data Damage to Interdependent Companies Loss of Customers 11 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005
 RED ALERT!!! 12
RED ALERT!!! 12
 You Have Been Hacked Ø Hacking first began as a positive execution of computer improvements Ø Although not widely used, “Cracking” is the term for abusive hacking Ø Ill intent hacking occurred as early as the 1970 s case: in 1991 Cap N Crunch hacker, John Draper used a toy whistle from a cereal box to obtain free phone usage Ø Occurrences increase each year Ø New terms: cyberterrorism, information warfare, economic espionage, data pirating www. cert. org viewed 10/05 www. viruslist. com/en/hackers viewed 10/05 13
You Have Been Hacked Ø Hacking first began as a positive execution of computer improvements Ø Although not widely used, “Cracking” is the term for abusive hacking Ø Ill intent hacking occurred as early as the 1970 s case: in 1991 Cap N Crunch hacker, John Draper used a toy whistle from a cereal box to obtain free phone usage Ø Occurrences increase each year Ø New terms: cyberterrorism, information warfare, economic espionage, data pirating www. cert. org viewed 10/05 www. viruslist. com/en/hackers viewed 10/05 13
 Parties Involved in the Cyber-Security World Hackers Computer Researchers Companies Individuals 14
Parties Involved in the Cyber-Security World Hackers Computer Researchers Companies Individuals 14
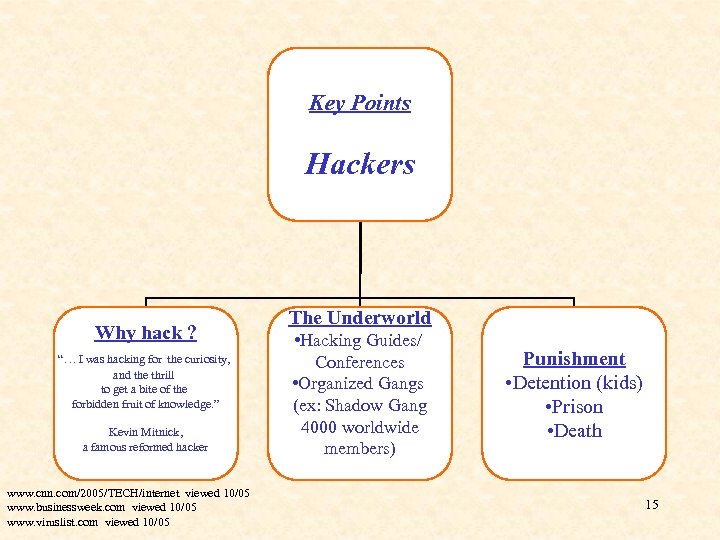 Key Points Hackers Why hack ? “… I was hacking for the curiosity, and the thrill to get a bite of the forbidden fruit of knowledge. ” Kevin Mitnick, a famous reformed hacker www. cnn. com/2005/TECH/internet viewed 10/05 www. businessweek. com viewed 10/05 www. viruslist. com viewed 10/05 The Underworld • Hacking Guides/ Conferences • Organized Gangs (ex: Shadow Gang 4000 worldwide members) Punishment • Detention (kids) • Prison • Death 15
Key Points Hackers Why hack ? “… I was hacking for the curiosity, and the thrill to get a bite of the forbidden fruit of knowledge. ” Kevin Mitnick, a famous reformed hacker www. cnn. com/2005/TECH/internet viewed 10/05 www. businessweek. com viewed 10/05 www. viruslist. com viewed 10/05 The Underworld • Hacking Guides/ Conferences • Organized Gangs (ex: Shadow Gang 4000 worldwide members) Punishment • Detention (kids) • Prison • Death 15
 Key Points Computer Researcher OOPs it was an Accident Case: Nov. 1988, the Morris Worm erroneously launched by Robert Morris infected several thousand systems around the country 16 www. viruslist. com/en/hackers viewed 10/05
Key Points Computer Researcher OOPs it was an Accident Case: Nov. 1988, the Morris Worm erroneously launched by Robert Morris infected several thousand systems around the country 16 www. viruslist. com/en/hackers viewed 10/05
 Key Points Companies – the Victims Ø High profile companies are hacker targets “I’d begun targeting specific systems I saw as high profile or high challenge. ” Electron – NASA break Ø Hesitant to disclose attacks to public Ø On the average, companies have meager security standards Ø Security & Privacy is ranked the top 3 rd management concern Ø Although, companies are the shepards of massive amounts of sensitive information, information mismanagement is frequent www. theage. com. au/articles/2003/05/24 viewed 11/05 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005 17
Key Points Companies – the Victims Ø High profile companies are hacker targets “I’d begun targeting specific systems I saw as high profile or high challenge. ” Electron – NASA break Ø Hesitant to disclose attacks to public Ø On the average, companies have meager security standards Ø Security & Privacy is ranked the top 3 rd management concern Ø Although, companies are the shepards of massive amounts of sensitive information, information mismanagement is frequent www. theage. com. au/articles/2003/05/24 viewed 11/05 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005 17
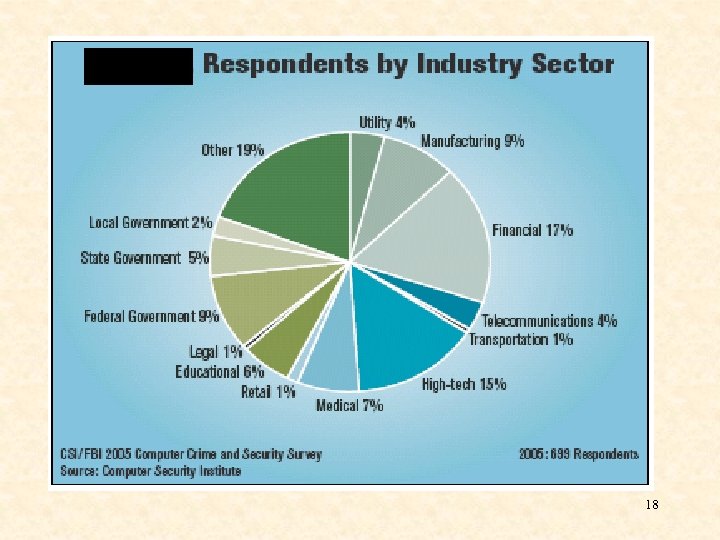 18
18
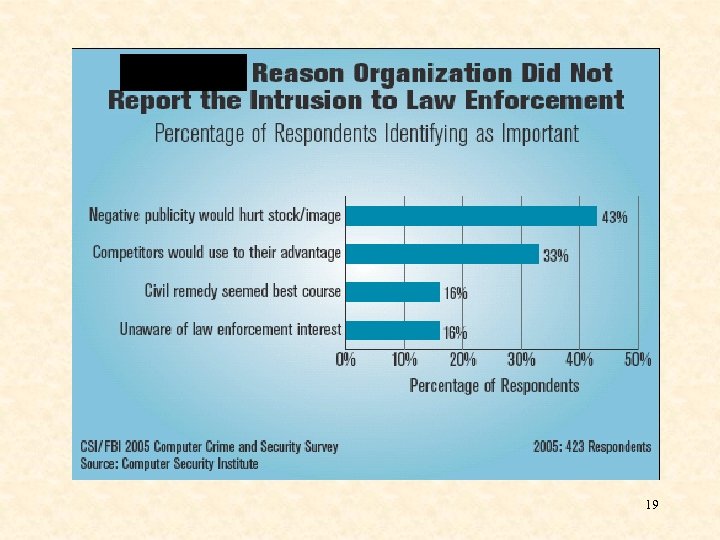 19
19
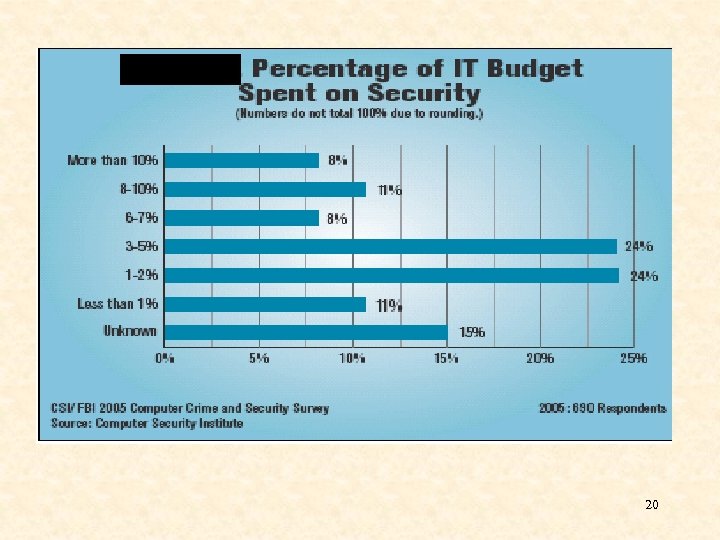 20
20
 Invasion of the Privacy Snatchers 21
Invasion of the Privacy Snatchers 21
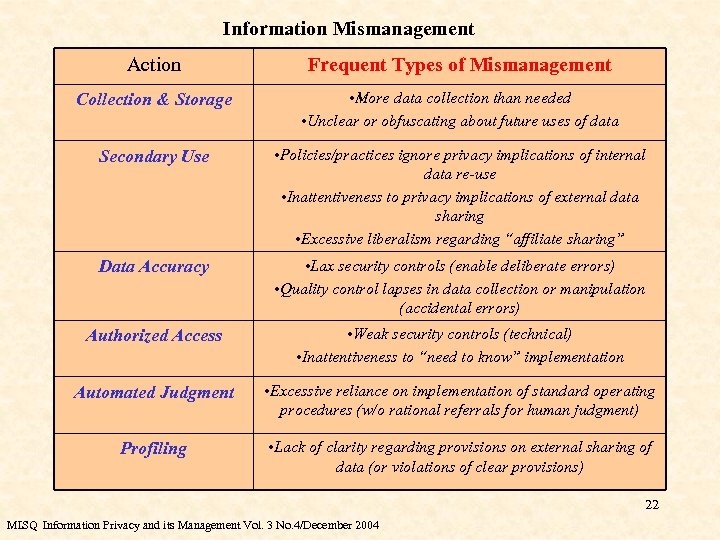 Information Mismanagement Action Frequent Types of Mismanagement Collection & Storage • More data collection than needed • Unclear or obfuscating about future uses of data Secondary Use • Policies/practices ignore privacy implications of internal data re-use • Inattentiveness to privacy implications of external data sharing • Excessive liberalism regarding “affiliate sharing” Data Accuracy • Lax security controls (enable deliberate errors) • Quality control lapses in data collection or manipulation (accidental errors) Authorized Access • Weak security controls (technical) • Inattentiveness to “need to know” implementation Automated Judgment • Excessive reliance on implementation of standard operating procedures (w/o rational referrals for human judgment) Profiling • Lack of clarity regarding provisions on external sharing of data (or violations of clear provisions) 22 MISQ Information Privacy and its Management Vol. 3 No. 4/December 2004
Information Mismanagement Action Frequent Types of Mismanagement Collection & Storage • More data collection than needed • Unclear or obfuscating about future uses of data Secondary Use • Policies/practices ignore privacy implications of internal data re-use • Inattentiveness to privacy implications of external data sharing • Excessive liberalism regarding “affiliate sharing” Data Accuracy • Lax security controls (enable deliberate errors) • Quality control lapses in data collection or manipulation (accidental errors) Authorized Access • Weak security controls (technical) • Inattentiveness to “need to know” implementation Automated Judgment • Excessive reliance on implementation of standard operating procedures (w/o rational referrals for human judgment) Profiling • Lack of clarity regarding provisions on external sharing of data (or violations of clear provisions) 22 MISQ Information Privacy and its Management Vol. 3 No. 4/December 2004
 Key Points Individuals – the Indirect Victims Ø Rarely targeted directly “There attacks that can be done, but its unlikely that I’ll be targeted as an individual. ” Kevin Mitnick, hacker poster boy Ø Indirect Victims primarily due to lax company security measures & practices Ø Privacy concerns raised because of frequent company information mismanagement 23 www. cnn. com/2005/TECH/internet viewed 10/05
Key Points Individuals – the Indirect Victims Ø Rarely targeted directly “There attacks that can be done, but its unlikely that I’ll be targeted as an individual. ” Kevin Mitnick, hacker poster boy Ø Indirect Victims primarily due to lax company security measures & practices Ø Privacy concerns raised because of frequent company information mismanagement 23 www. cnn. com/2005/TECH/internet viewed 10/05
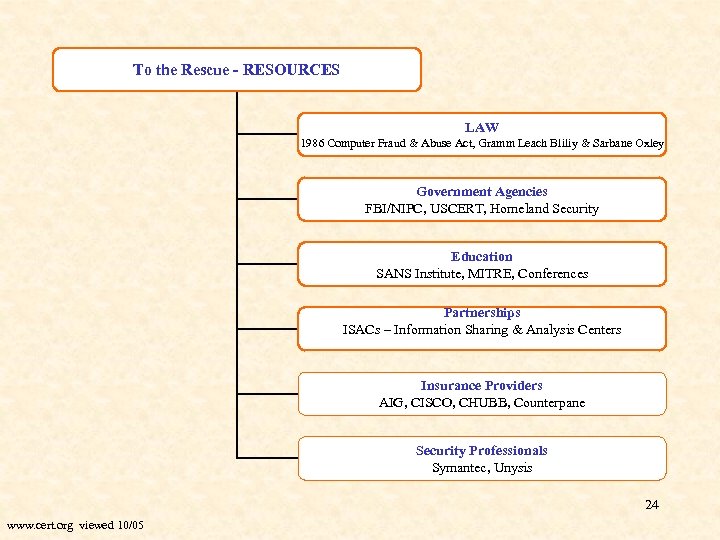 To the Rescue - RESOURCES LAW 1986 Computer Fraud & Abuse Act, Gramm Leach Bliliy & Sarbane Oxley Government Agencies FBI/NIPC, USCERT, Homeland Security Education SANS Institute, MITRE, Conferences Partnerships ISACs – Information Sharing & Analysis Centers Insurance Providers AIG, CISCO, CHUBB, Counterpane Security Professionals Symantec, Unysis 24 www. cert. org viewed 10/05
To the Rescue - RESOURCES LAW 1986 Computer Fraud & Abuse Act, Gramm Leach Bliliy & Sarbane Oxley Government Agencies FBI/NIPC, USCERT, Homeland Security Education SANS Institute, MITRE, Conferences Partnerships ISACs – Information Sharing & Analysis Centers Insurance Providers AIG, CISCO, CHUBB, Counterpane Security Professionals Symantec, Unysis 24 www. cert. org viewed 10/05
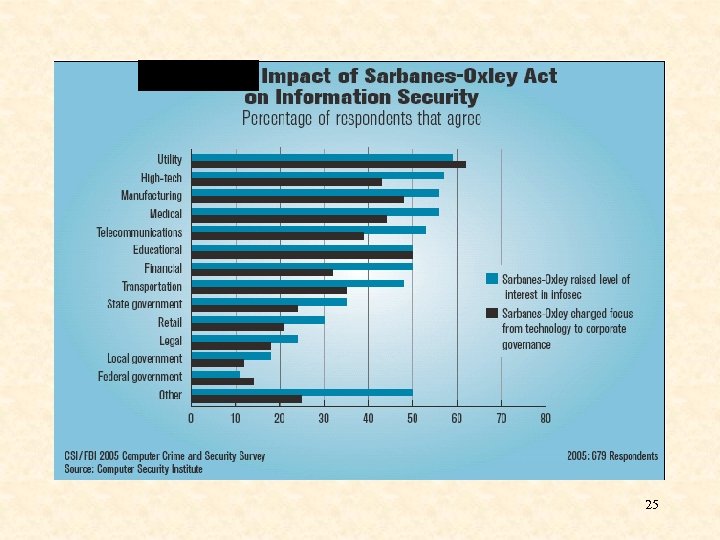 25
25
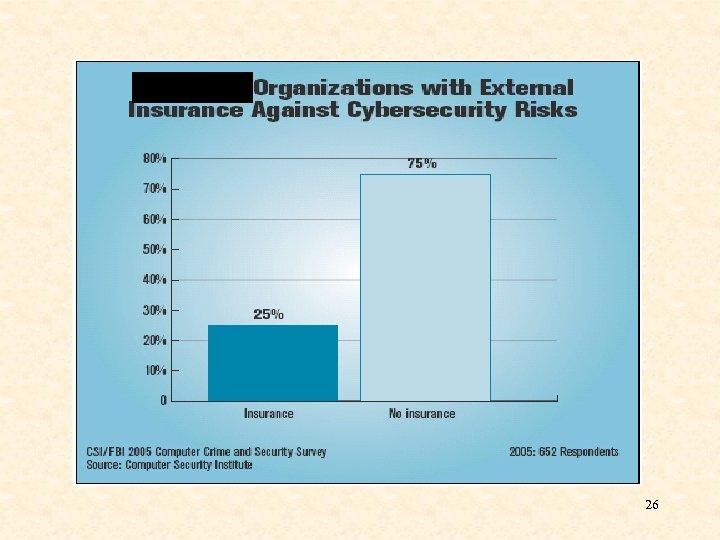 26
26
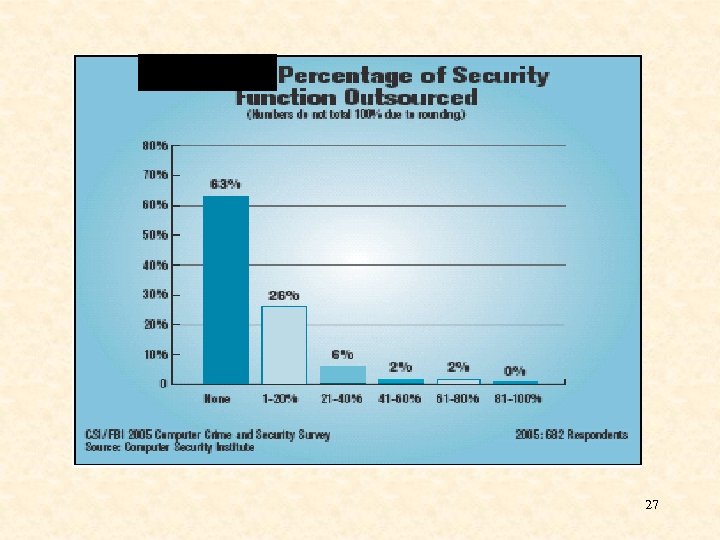 27
27
 The Future • Continued Hacking at an increased pace with more sophistication, thought: potential for large grids of electricity to be damaged thereby crippling thousands of people, businesses, & emergency services • Enhanced cyber-security technology, • Additional privacy concerns with new wireless technology (RFIDs), • Increased company spending expected for cyber-security defenses, • Stronger alliances, • Additional regulations/laws expected, and • Better international collaboration anticipated. 28
The Future • Continued Hacking at an increased pace with more sophistication, thought: potential for large grids of electricity to be damaged thereby crippling thousands of people, businesses, & emergency services • Enhanced cyber-security technology, • Additional privacy concerns with new wireless technology (RFIDs), • Increased company spending expected for cyber-security defenses, • Stronger alliances, • Additional regulations/laws expected, and • Better international collaboration anticipated. 28
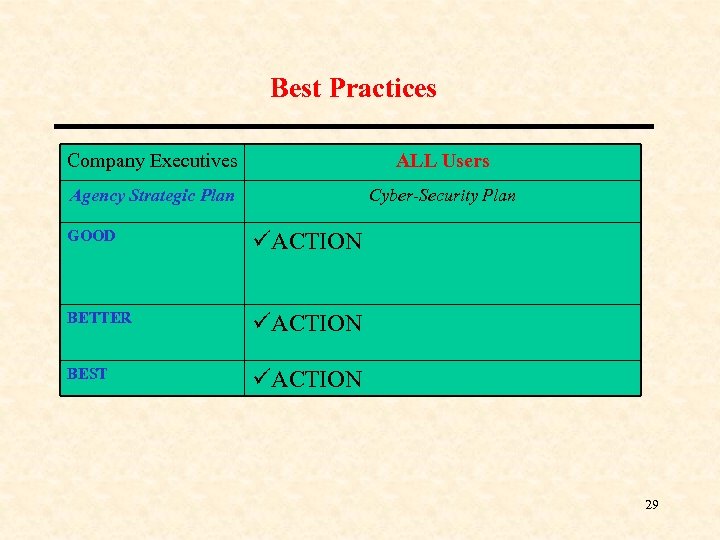 Best Practices Company Executives ALL Users Agency Strategic Plan Cyber-Security Plan GOOD üACTION BETTER üACTION BEST üACTION 29
Best Practices Company Executives ALL Users Agency Strategic Plan Cyber-Security Plan GOOD üACTION BETTER üACTION BEST üACTION 29
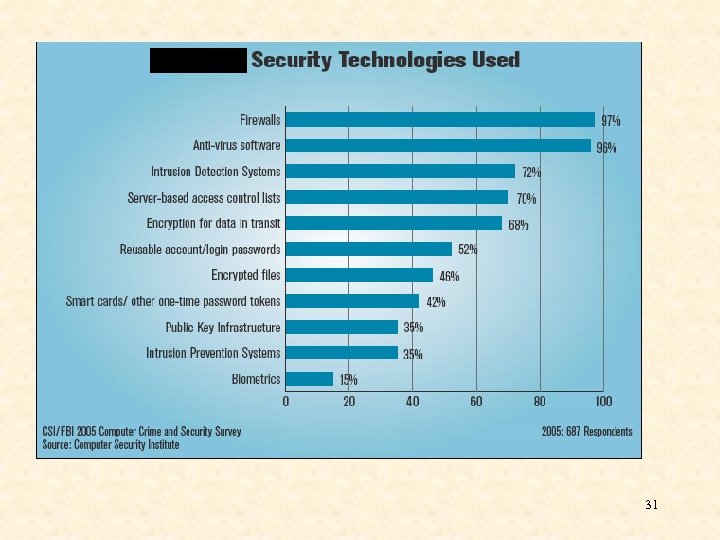
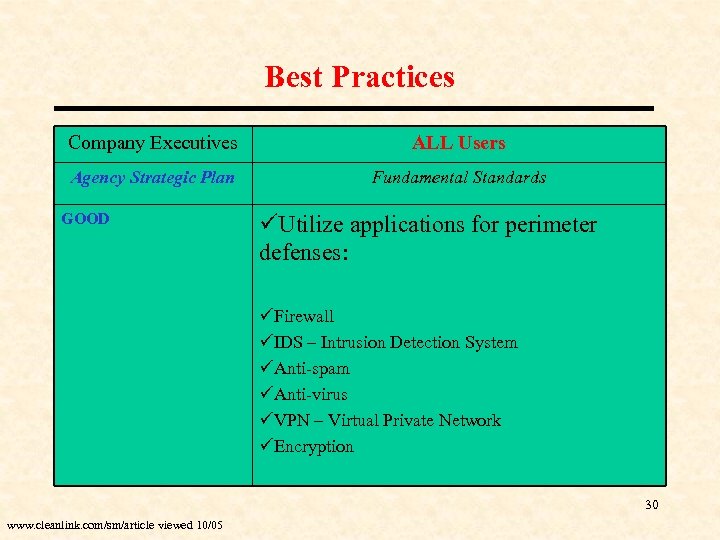 Best Practices Company Executives ALL Users Agency Strategic Plan Fundamental Standards GOOD üUtilize applications for perimeter defenses: üFirewall üIDS – Intrusion Detection System üAnti-spam üAnti-virus üVPN – Virtual Private Network üEncryption 30 www. cleanlink. com/sm/article viewed 10/05
Best Practices Company Executives ALL Users Agency Strategic Plan Fundamental Standards GOOD üUtilize applications for perimeter defenses: üFirewall üIDS – Intrusion Detection System üAnti-spam üAnti-virus üVPN – Virtual Private Network üEncryption 30 www. cleanlink. com/sm/article viewed 10/05
 31
31
 Best Practices Company Executives ALL Users Agency Strategic Plan Cbyer-Security Plan BETTER www. cleanlink. com/sm/article viewed 10/05 www. toptechnews. com/story viewed 10/05 üShred Paper üPassword Protection/ Better Selection üSystem Removal (old employees) üTraining üEstablish process for all users (identify steps; answer who, what, how) üTrack attacks üBetter Information Management üTop level buy in 32
Best Practices Company Executives ALL Users Agency Strategic Plan Cbyer-Security Plan BETTER www. cleanlink. com/sm/article viewed 10/05 www. toptechnews. com/story viewed 10/05 üShred Paper üPassword Protection/ Better Selection üSystem Removal (old employees) üTraining üEstablish process for all users (identify steps; answer who, what, how) üTrack attacks üBetter Information Management üTop level buy in 32
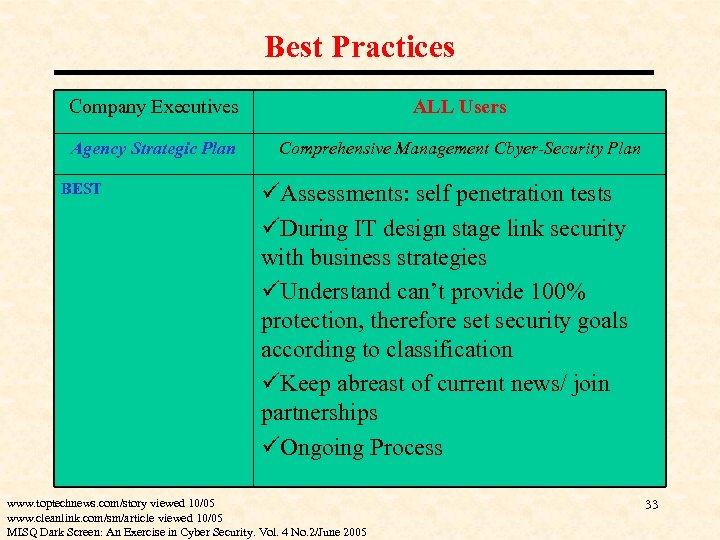 Best Practices Company Executives ALL Users Agency Strategic Plan Comprehensive Management Cbyer-Security Plan BEST üAssessments: self penetration tests üDuring IT design stage link security with business strategies üUnderstand can’t provide 100% protection, therefore set security goals according to classification üKeep abreast of current news/ join partnerships üOngoing Process www. toptechnews. com/story viewed 10/05 www. cleanlink. com/sm/article viewed 10/05 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005 33
Best Practices Company Executives ALL Users Agency Strategic Plan Comprehensive Management Cbyer-Security Plan BEST üAssessments: self penetration tests üDuring IT design stage link security with business strategies üUnderstand can’t provide 100% protection, therefore set security goals according to classification üKeep abreast of current news/ join partnerships üOngoing Process www. toptechnews. com/story viewed 10/05 www. cleanlink. com/sm/article viewed 10/05 MISQ Dark Screen: An Exercise in Cyber Security. Vol. 4 No. 2/June 2005 33
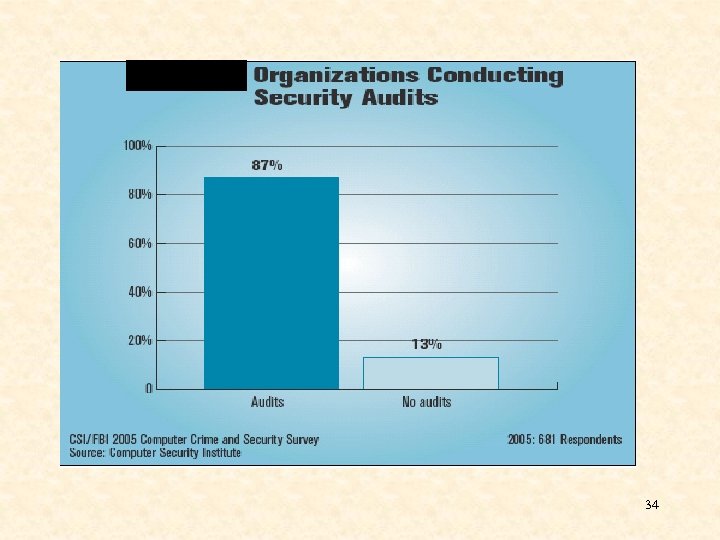 34
34
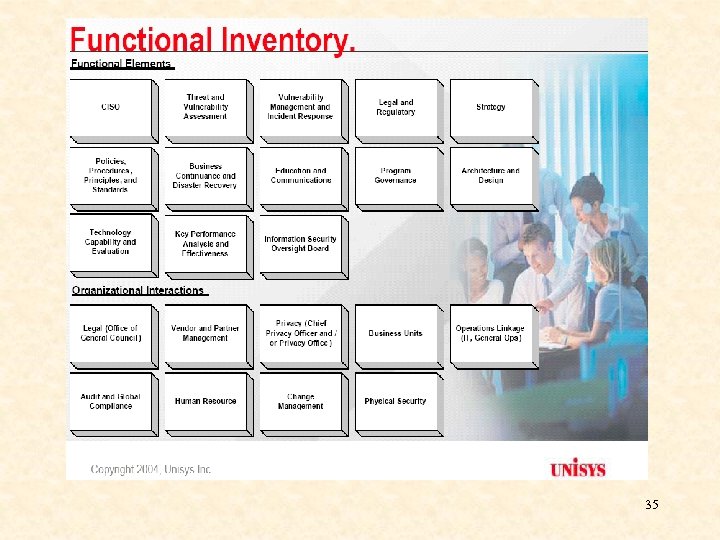 35
35
 SUMMARY Sensitive transactions call for increased security. More sophisticated hacking calls for increased security. Awareness: Know what’s going on in the cyber-security community. Emerging policies logical for companies to interact to provide their input vs being strictly mandated to. Create a company specific comprehensive security plan. Plan align with business strategy. Plan to indicate proper management of information to help eliminate privacy concerns. Understand that security plan should concentrate on the process not the technological applications. And that this process is ongoing. “You have to continue to train and implement new security. It needs to be something you do everyday. ” Steve Epner of Brown Smith Wallace, a St. Louis technology consulting firm 36 www. cleanlink. com/sm/article viewed 10/05
SUMMARY Sensitive transactions call for increased security. More sophisticated hacking calls for increased security. Awareness: Know what’s going on in the cyber-security community. Emerging policies logical for companies to interact to provide their input vs being strictly mandated to. Create a company specific comprehensive security plan. Plan align with business strategy. Plan to indicate proper management of information to help eliminate privacy concerns. Understand that security plan should concentrate on the process not the technological applications. And that this process is ongoing. “You have to continue to train and implement new security. It needs to be something you do everyday. ” Steve Epner of Brown Smith Wallace, a St. Louis technology consulting firm 36 www. cleanlink. com/sm/article viewed 10/05


