00bfb43806ad21a4021ce0b2303fa99c.ppt
- Количество слайдов: 88
 Java WS Core for Developers Rachana Ananthakrishnan Jarek Gawor 1
Java WS Core for Developers Rachana Ananthakrishnan Jarek Gawor 1
 Session Notes l Slides available at: u l l This session is for developers already familiar with Java WS Core Beginners please checkout ‘L 3: Build a Service Using GT 4’ lab u l http: //www. mcs. anl. gov/~gawor/gw Thursday 2 pm – 5: 45 pm Other relevant sessions at GW u COMM 12: Mini Symposium - Development Tools for GT 4 Service Programming l u Monday - but slides might be interesting L 4: The File. Buy Globus Based Resource Brokering System - A Practical Example l Friday 9 am - 1 pm 2
Session Notes l Slides available at: u l l This session is for developers already familiar with Java WS Core Beginners please checkout ‘L 3: Build a Service Using GT 4’ lab u l http: //www. mcs. anl. gov/~gawor/gw Thursday 2 pm – 5: 45 pm Other relevant sessions at GW u COMM 12: Mini Symposium - Development Tools for GT 4 Service Programming l u Monday - but slides might be interesting L 4: The File. Buy Globus Based Resource Brokering System - A Practical Example l Friday 9 am - 1 pm 2
 Overview l Two session parts 1. General programming guidelines 1. 2. Service implementation 3. Lifecycle management 4. Resource persistence and caching 5. Service communication 6. Background tasks 7. 2. WSDL Debugging and production tuning Security features of Java WS Core 3
Overview l Two session parts 1. General programming guidelines 1. 2. Service implementation 3. Lifecycle management 4. Resource persistence and caching 5. Service communication 6. Background tasks 7. 2. WSDL Debugging and production tuning Security features of Java WS Core 3
 Java WS Core l l l Development kit for building stateful Web Services Implementation of WS-Resource Framework (WSRF) and WS-Notification (WSN) family of specifications Provides lightweight hosting environment u l l Can also run in Tomcat, JBoss and other application servers Support for transport and message level security Implemented with ‘standard’ Apache software u u Axis 1 (SOAP engine) Addressing (WS-Addressing implementation) WSS 4 J (WS-Security implementation) and more 4
Java WS Core l l l Development kit for building stateful Web Services Implementation of WS-Resource Framework (WSRF) and WS-Notification (WSN) family of specifications Provides lightweight hosting environment u l l Can also run in Tomcat, JBoss and other application servers Support for transport and message level security Implemented with ‘standard’ Apache software u u Axis 1 (SOAP engine) Addressing (WS-Addressing implementation) WSS 4 J (WS-Security implementation) and more 4
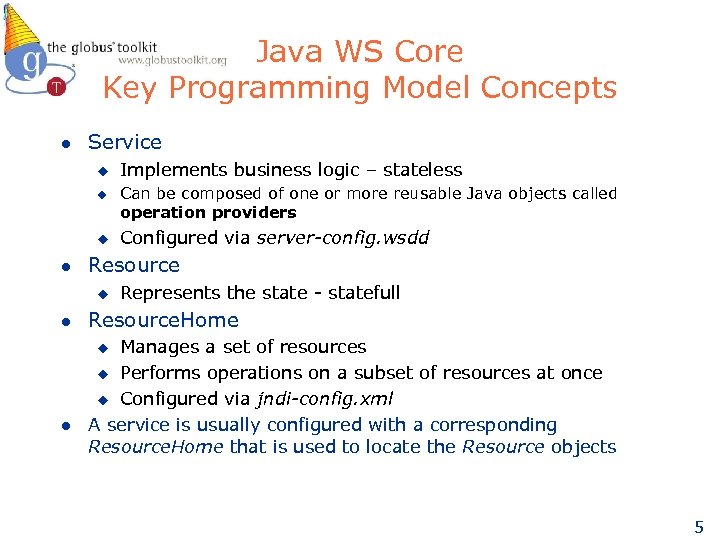 Java WS Core Key Programming Model Concepts l Service u u u l Can be composed of one or more reusable Java objects called operation providers Configured via server-config. wsdd Resource u l Implements business logic – stateless Represents the state - statefull Resource. Home Manages a set of resources u Performs operations on a subset of resources at once u Configured via jndi-config. xml A service is usually configured with a corresponding Resource. Home that is used to locate the Resource objects u l 5
Java WS Core Key Programming Model Concepts l Service u u u l Can be composed of one or more reusable Java objects called operation providers Configured via server-config. wsdd Resource u l Implements business logic – stateless Represents the state - statefull Resource. Home Manages a set of resources u Performs operations on a subset of resources at once u Configured via jndi-config. xml A service is usually configured with a corresponding Resource. Home that is used to locate the Resource objects u l 5
 Programming Guidelines and Best Practices 6
Programming Guidelines and Best Practices 6
 Service WSDL l Do not generate WSDL from existing code u l Create it by hand, modify existing one, etc. but follow the WSDL guidelines described next Tooling is still not perfect u Might generate non-interoperable WSDL 7
Service WSDL l Do not generate WSDL from existing code u l Create it by hand, modify existing one, etc. but follow the WSDL guidelines described next Tooling is still not perfect u Might generate non-interoperable WSDL 7
 WSDL Guidelines l WSDL has u u l l Use Document/Literal mode u Do not mix Literal with SOAP encoding in one WSDL Always validate your WSDL u l Document and RPC invocation style Literal and SOAP encoded mode Java WS Core does NOT validate it Follow WS-I Basic Profile 1. 1 guidelines u Improves interoperability 8
WSDL Guidelines l WSDL has u u l l Use Document/Literal mode u Do not mix Literal with SOAP encoding in one WSDL Always validate your WSDL u l Document and RPC invocation style Literal and SOAP encoded mode Java WS Core does NOT validate it Follow WS-I Basic Profile 1. 1 guidelines u Improves interoperability 8
 WSDL Doc/Lit Guidelines
WSDL Doc/Lit Guidelines
 WSDL Doc/Lit Guidelines
WSDL Doc/Lit Guidelines
 WSDL Doc/Lit Guidelines
WSDL Doc/Lit Guidelines
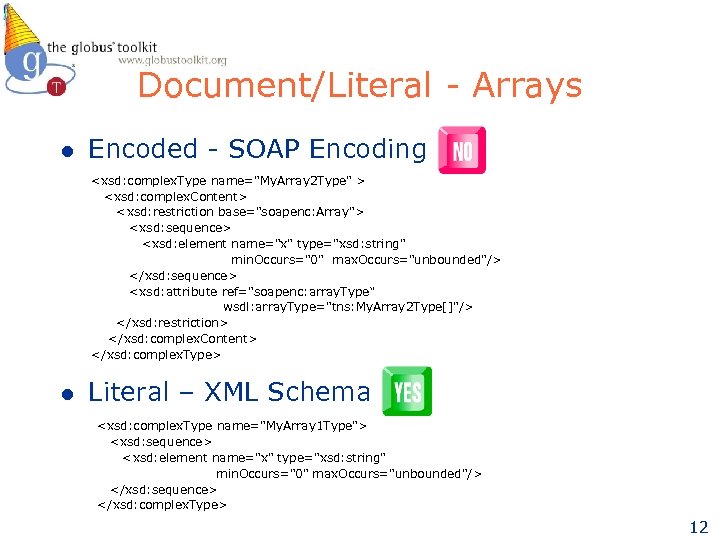 Document/Literal - Arrays l Encoded - SOAP Encoding
Document/Literal - Arrays l Encoded - SOAP Encoding
 Service Implementation l If you have an existing service code u u Do NOT generate WSDL from it and try to make it work somehow Instead: 1) 2) 3) 4) l Create WSDL by hand (or using some tools) Validate WSDL Generate Java code from WSDL Implement the generated service interface by delegating the calls to your existing service code In general, always implement the generated service interface u u Do NOT define your own service methods first In Document/Literal mode service methods will ALWAYS have 1 input parameter 13
Service Implementation l If you have an existing service code u u Do NOT generate WSDL from it and try to make it work somehow Instead: 1) 2) 3) 4) l Create WSDL by hand (or using some tools) Validate WSDL Generate Java code from WSDL Implement the generated service interface by delegating the calls to your existing service code In general, always implement the generated service interface u u Do NOT define your own service methods first In Document/Literal mode service methods will ALWAYS have 1 input parameter 13
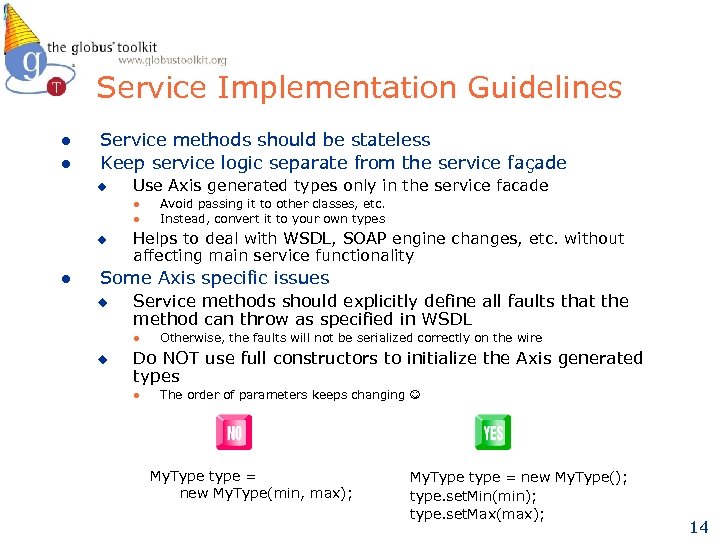 Service Implementation Guidelines l l Service methods should be stateless Keep service logic separate from the service façade u Use Axis generated types only in the service facade l l u l Avoid passing it to other classes, etc. Instead, convert it to your own types Helps to deal with WSDL, SOAP engine changes, etc. without affecting main service functionality Some Axis specific issues u Service methods should explicitly define all faults that the method can throw as specified in WSDL l u Otherwise, the faults will not be serialized correctly on the wire Do NOT use full constructors to initialize the Axis generated types l The order of parameters keeps changing My. Type type = new My. Type(min, max); My. Type type = new My. Type(); type. set. Min(min); type. set. Max(max); 14
Service Implementation Guidelines l l Service methods should be stateless Keep service logic separate from the service façade u Use Axis generated types only in the service facade l l u l Avoid passing it to other classes, etc. Instead, convert it to your own types Helps to deal with WSDL, SOAP engine changes, etc. without affecting main service functionality Some Axis specific issues u Service methods should explicitly define all faults that the method can throw as specified in WSDL l u Otherwise, the faults will not be serialized correctly on the wire Do NOT use full constructors to initialize the Axis generated types l The order of parameters keeps changing My. Type type = new My. Type(min, max); My. Type type = new My. Type(); type. set. Min(min); type. set. Max(max); 14
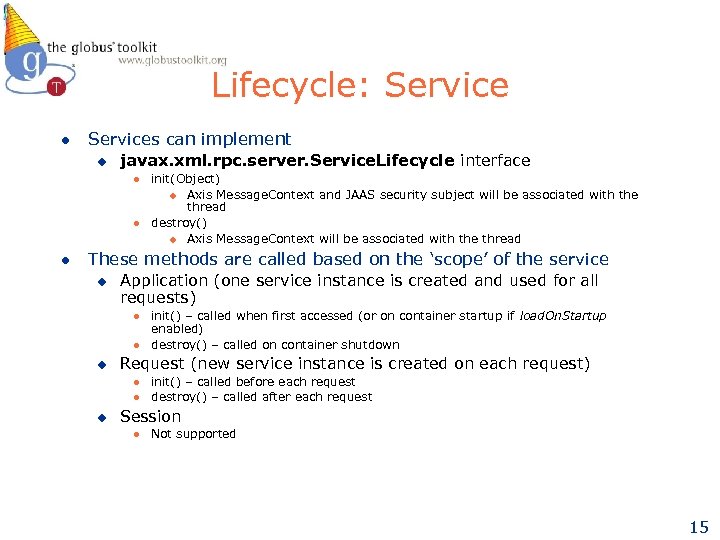 Lifecycle: Service l Services can implement u javax. xml. rpc. server. Service. Lifecycle interface l l l init(Object) u Axis Message. Context and JAAS security subject will be associated with the thread destroy() u Axis Message. Context will be associated with the thread These methods are called based on the ‘scope’ of the service u Application (one service instance is created and used for all requests) l l u Request (new service instance is created on each request) l l u init() – called when first accessed (or on container startup if load. On. Startup enabled) destroy() – called on container shutdown init() – called before each request destroy() – called after each request Session l Not supported 15
Lifecycle: Service l Services can implement u javax. xml. rpc. server. Service. Lifecycle interface l l l init(Object) u Axis Message. Context and JAAS security subject will be associated with the thread destroy() u Axis Message. Context will be associated with the thread These methods are called based on the ‘scope’ of the service u Application (one service instance is created and used for all requests) l l u Request (new service instance is created on each request) l l u init() – called when first accessed (or on container startup if load. On. Startup enabled) destroy() – called on container shutdown init() – called before each request destroy() – called after each request Session l Not supported 15
 Lifecycle: Resource. Home l Resource. Home can implement u org. globus. wsrf. jndi. Initializable interface l initialize() u u Called when first accessed (or on container startup if load. On. Startup is enabled) Called after all the parameters specified in the configuration file are set Axis Message. Context and JAAS security subject will be associated with the thread (Resource. Home only) org. globus. wsrf. jndi. Destroyable interface l destroy() u Called on container shutdown 16
Lifecycle: Resource. Home l Resource. Home can implement u org. globus. wsrf. jndi. Initializable interface l initialize() u u Called when first accessed (or on container startup if load. On. Startup is enabled) Called after all the parameters specified in the configuration file are set Axis Message. Context and JAAS security subject will be associated with the thread (Resource. Home only) org. globus. wsrf. jndi. Destroyable interface l destroy() u Called on container shutdown 16
 Lifecycle: Resource l Creation – resource creation is service specific u l No API defined Destruction - resource object can implement u org. globus. wsrf. Remove. Callback interface l u Resource. Home calls remove() when l l l remove() u Called by Resource. Home only Resource is destroyed explicitly u Service implements the Immediate. Resource. Termination port type of WS-Resource. Lifetime specification Resource’s lease expires u Service implements the Scheduled. Resource. Termination port type of WS-Resource. Lifetime specification Activation – persistent resource objects are usually activated on demand as a requests come in u Resource. Home could activate resources in its initialize() method 17
Lifecycle: Resource l Creation – resource creation is service specific u l No API defined Destruction - resource object can implement u org. globus. wsrf. Remove. Callback interface l u Resource. Home calls remove() when l l l remove() u Called by Resource. Home only Resource is destroyed explicitly u Service implements the Immediate. Resource. Termination port type of WS-Resource. Lifetime specification Resource’s lease expires u Service implements the Scheduled. Resource. Termination port type of WS-Resource. Lifetime specification Activation – persistent resource objects are usually activated on demand as a requests come in u Resource. Home could activate resources in its initialize() method 17
 Resource Persistence l Persistence mechanism is up to the service developers u l Java serialization, relational database, xml database, etc. Resource objects can implement u org. globus. wsrf. Persistent. Resource interface l l u load(Resource. Key) u Loads resource state » Does not need to load the entire resource state – only the necessary bits » Rest of the state can be loaded on demand u Does not need to be synchronized as called once to bring the resource into memory store() u Saves resource state u Must be synchronized as might be called from multiple threads at the same time Use with org. globus. wsrf. impl. Resource. Home. Impl 18
Resource Persistence l Persistence mechanism is up to the service developers u l Java serialization, relational database, xml database, etc. Resource objects can implement u org. globus. wsrf. Persistent. Resource interface l l u load(Resource. Key) u Loads resource state » Does not need to load the entire resource state – only the necessary bits » Rest of the state can be loaded on demand u Does not need to be synchronized as called once to bring the resource into memory store() u Saves resource state u Must be synchronized as might be called from multiple threads at the same time Use with org. globus. wsrf. impl. Resource. Home. Impl 18
 Resource Persistence l Persistence resource object must provide noargument constructor u Resource. Home. Impl attempts to load the resource by l Creating new instance of the resource object l Calling the load(Resource. Key) method u u l load() either loads the resource state, or Fails with No. Such. Resource exception Define separate constructors to distinguish between new resource creation and resource activation 19
Resource Persistence l Persistence resource object must provide noargument constructor u Resource. Home. Impl attempts to load the resource by l Creating new instance of the resource object l Calling the load(Resource. Key) method u u l load() either loads the resource state, or Fails with No. Such. Resource exception Define separate constructors to distinguish between new resource creation and resource activation 19
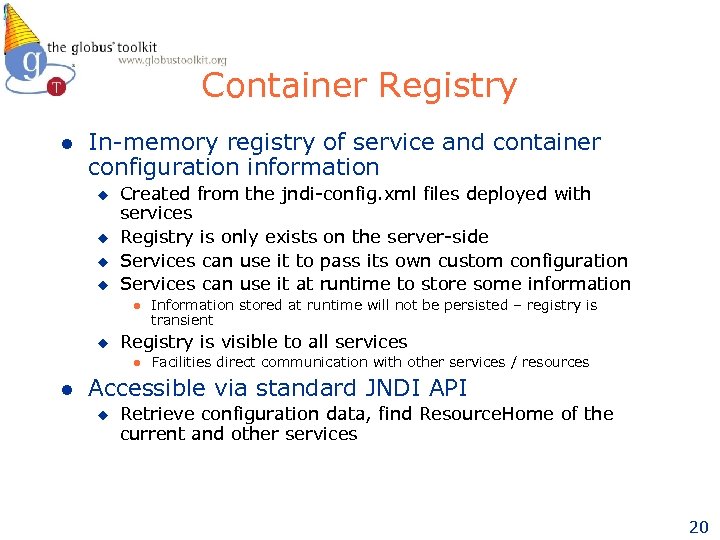 Container Registry l In-memory registry of service and container configuration information u u Created from the jndi-config. xml files deployed with services Registry is only exists on the server-side Services can use it to pass its own custom configuration Services can use it at runtime to store some information l u Registry is visible to all services l l Information stored at runtime will not be persisted – registry is transient Facilities direct communication with other services / resources Accessible via standard JNDI API u Retrieve configuration data, find Resource. Home of the current and other services 20
Container Registry l In-memory registry of service and container configuration information u u Created from the jndi-config. xml files deployed with services Registry is only exists on the server-side Services can use it to pass its own custom configuration Services can use it at runtime to store some information l u Registry is visible to all services l l Information stored at runtime will not be persisted – registry is transient Facilities direct communication with other services / resources Accessible via standard JNDI API u Retrieve configuration data, find Resource. Home of the current and other services 20
 Container Registry l Registry has a tree-like structure u java: comp/env - root of the tree l /services – all services are placed under this node u /Service. A – each service also has its own sub-node » home – service-specific resources are leaf nodes » resource. A u /Service. B » resource. B » … l resource. C – global resources are leaf nodes under root l resource. N l … 21
Container Registry l Registry has a tree-like structure u java: comp/env - root of the tree l /services – all services are placed under this node u /Service. A – each service also has its own sub-node » home – service-specific resources are leaf nodes » resource. A u /Service. B » resource. B » … l resource. C – global resources are leaf nodes under root l resource. N l … 21
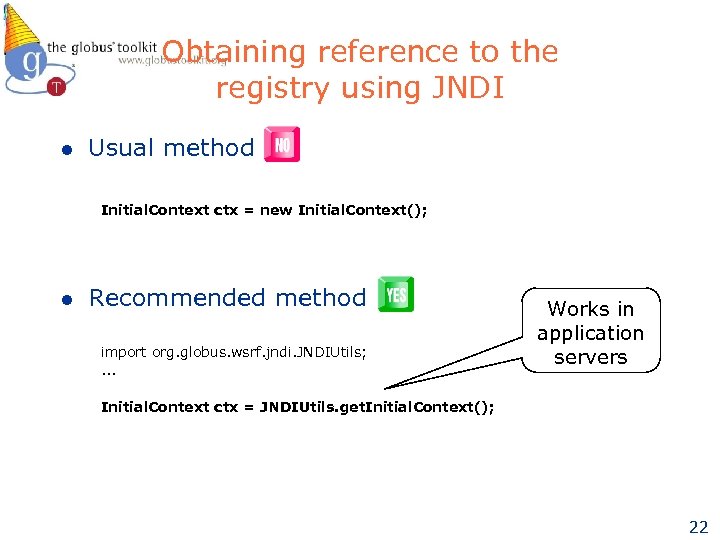 Obtaining reference to the registry using JNDI l Usual method Initial. Context ctx = new Initial. Context(); l Recommended method import org. globus. wsrf. jndi. JNDIUtils; . . . Works in application servers Initial. Context ctx = JNDIUtils. get. Initial. Context(); 22
Obtaining reference to the registry using JNDI l Usual method Initial. Context ctx = new Initial. Context(); l Recommended method import org. globus. wsrf. jndi. JNDIUtils; . . . Works in application servers Initial. Context ctx = JNDIUtils. get. Initial. Context(); 22
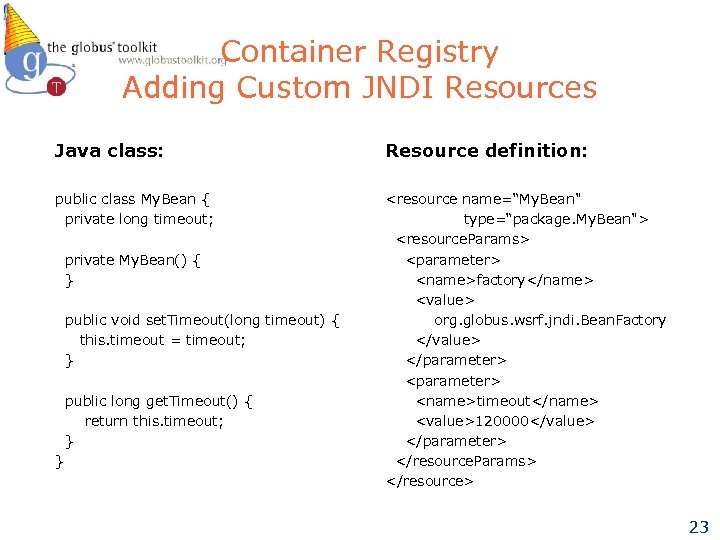 Container Registry Adding Custom JNDI Resources Java class: Resource definition: public class My. Bean { private long timeout;
Container Registry Adding Custom JNDI Resources Java class: Resource definition: public class My. Bean { private long timeout;
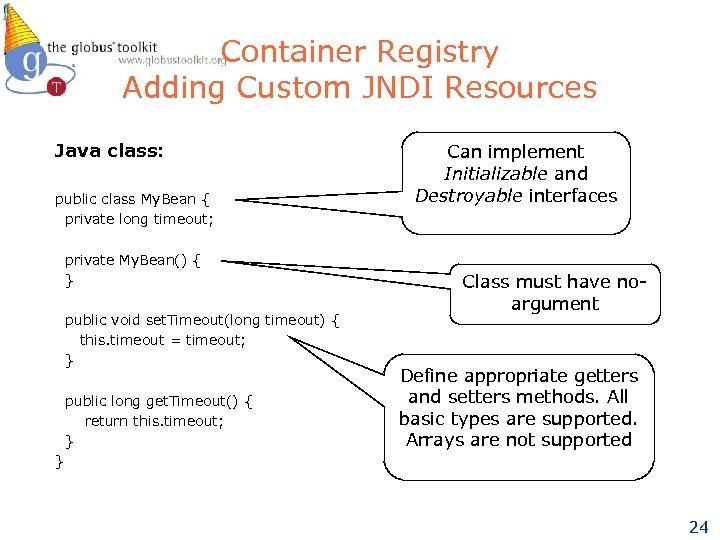 Container Registry Adding Custom JNDI Resources Java class: public class My. Bean { private long timeout; private My. Bean() { } public void set. Timeout(long timeout) { this. timeout = timeout; } public long get. Timeout() { return this. timeout; } } Can implement Initializable and Destroyable interfaces Class must have noargument Define appropriate getters and setters methods. All basic types are supported. Arrays are not supported 24
Container Registry Adding Custom JNDI Resources Java class: public class My. Bean { private long timeout; private My. Bean() { } public void set. Timeout(long timeout) { this. timeout = timeout; } public long get. Timeout() { return this. timeout; } } Can implement Initializable and Destroyable interfaces Class must have noargument Define appropriate getters and setters methods. All basic types are supported. Arrays are not supported 24
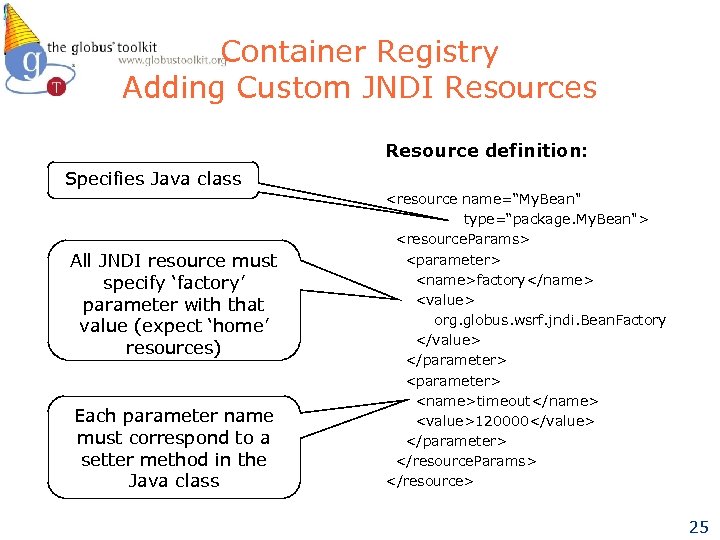 Container Registry Adding Custom JNDI Resources Resource definition: Specifies Java class All JNDI resource must specify ‘factory’ parameter with that value (expect ‘home’ resources) Each parameter name must correspond to a setter method in the Java class
Container Registry Adding Custom JNDI Resources Resource definition: Specifies Java class All JNDI resource must specify ‘factory’ parameter with that value (expect ‘home’ resources) Each parameter name must correspond to a setter method in the Java class
 Resource Cache l Works only with org. globus. wsrf. impl. Resource. Home. Impl and persistent resources u Resource. Home. Impl maps resource keys to resource objects wrapped in Java Soft. References u Soft. References allow the JVM to automatically garbage collect the resource objects if nothing else references them l u Thus, reduces memory usage and improves scalability However, sometimes with Soft. References resource objects might get GCed too frequently l Resource Cache prevents that by keeping temporary hard references to the resource objects u Cache can have size limit or time limit or both u Cache uses Least Recently Used (LRU) algorithm 26
Resource Cache l Works only with org. globus. wsrf. impl. Resource. Home. Impl and persistent resources u Resource. Home. Impl maps resource keys to resource objects wrapped in Java Soft. References u Soft. References allow the JVM to automatically garbage collect the resource objects if nothing else references them l u Thus, reduces memory usage and improves scalability However, sometimes with Soft. References resource objects might get GCed too frequently l Resource Cache prevents that by keeping temporary hard references to the resource objects u Cache can have size limit or time limit or both u Cache uses Least Recently Used (LRU) algorithm 26
…
 Communication Between Services l Regular invocations u u l Standard HTTP/S calls Service can be remote or local Local invocations u In-memory, server-side only calls between services l l No HTTP/S transport - uses ‘local: //’ protocol u Extra setup is necessary to use local invocation in Tomcat or other application servers SOAP serialization/deserialization is performed Security is enforced (message level) Direct invocations u In-memory, server-side only calls between services l l l Regular Java method calls achieved using JNDI u Can invoke things published in JNDI but cannot invoke actual service method SOAP serialization/deserialization is not performed Security is not enforced 29
Communication Between Services l Regular invocations u u l Standard HTTP/S calls Service can be remote or local Local invocations u In-memory, server-side only calls between services l l No HTTP/S transport - uses ‘local: //’ protocol u Extra setup is necessary to use local invocation in Tomcat or other application servers SOAP serialization/deserialization is performed Security is enforced (message level) Direct invocations u In-memory, server-side only calls between services l l l Regular Java method calls achieved using JNDI u Can invoke things published in JNDI but cannot invoke actual service method SOAP serialization/deserialization is not performed Security is not enforced 29
 Regular Invocation Example URL url = new URL(“http: //localhost: 8080/wsrf/services/My. Service"); My. Service. Addressing. Locator locator = new My. Service. Addressing. Locator(); My. Service port = locator. get. My. Service. Port(url); port. hello(); 30
Regular Invocation Example URL url = new URL(“http: //localhost: 8080/wsrf/services/My. Service"); My. Service. Addressing. Locator locator = new My. Service. Addressing. Locator(); My. Service port = locator. get. My. Service. Port(url); port. hello(); 30
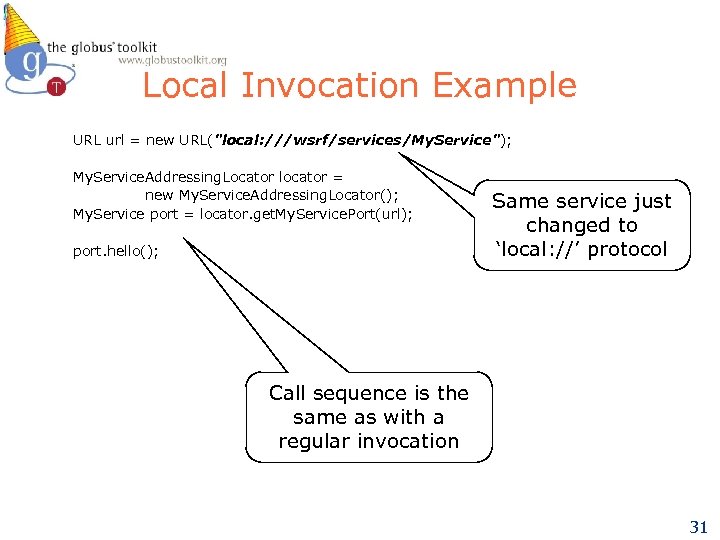 Local Invocation Example URL url = new URL("local: ///wsrf/services/My. Service"); My. Service. Addressing. Locator locator = new My. Service. Addressing. Locator(); My. Service port = locator. get. My. Service. Port(url); port. hello(); Same service just changed to ‘local: //’ protocol Call sequence is the same as with a regular invocation 31
Local Invocation Example URL url = new URL("local: ///wsrf/services/My. Service"); My. Service. Addressing. Locator locator = new My. Service. Addressing. Locator(); My. Service port = locator. get. My. Service. Port(url); port. hello(); Same service just changed to ‘local: //’ protocol Call sequence is the same as with a regular invocation 31
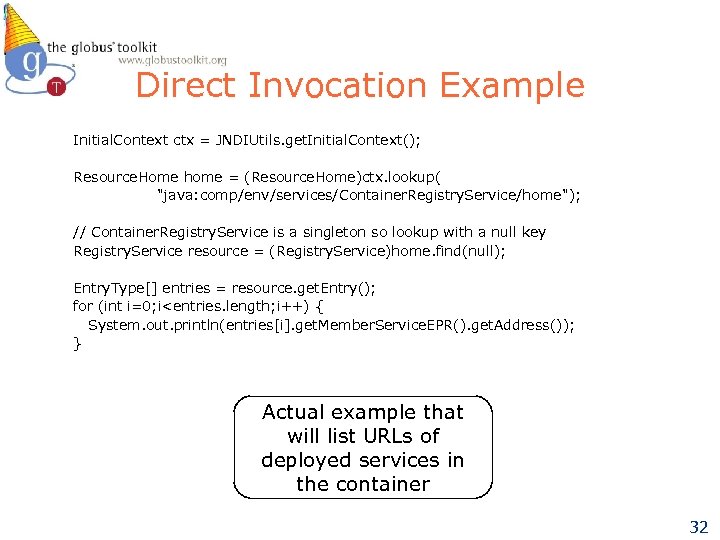 Direct Invocation Example Initial. Context ctx = JNDIUtils. get. Initial. Context(); Resource. Home home = (Resource. Home)ctx. lookup( "java: comp/env/services/Container. Registry. Service/home"); // Container. Registry. Service is a singleton so lookup with a null key Registry. Service resource = (Registry. Service)home. find(null); Entry. Type[] entries = resource. get. Entry(); for (int i=0; i
Direct Invocation Example Initial. Context ctx = JNDIUtils. get. Initial. Context(); Resource. Home home = (Resource. Home)ctx. lookup( "java: comp/env/services/Container. Registry. Service/home"); // Container. Registry. Service is a singleton so lookup with a null key Registry. Service resource = (Registry. Service)home. find(null); Entry. Type[] entries = resource. get. Entry(); for (int i=0; i
 Background Tasks l Instead of creating separate Threads use u Work. Manager l u Timer. Manager l l Used for executing periodic tasks Both use thread pools u l Use for executing ‘one-time’ tasks u No while (true) {. . } type of things! Do not queue tasks that wait synchronously for results from other tasks If you have to create separate Threads u u Limit the number of the threads Have an explicit way to stop them 33
Background Tasks l Instead of creating separate Threads use u Work. Manager l u Timer. Manager l l Used for executing periodic tasks Both use thread pools u l Use for executing ‘one-time’ tasks u No while (true) {. . } type of things! Do not queue tasks that wait synchronously for results from other tasks If you have to create separate Threads u u Limit the number of the threads Have an explicit way to stop them 33
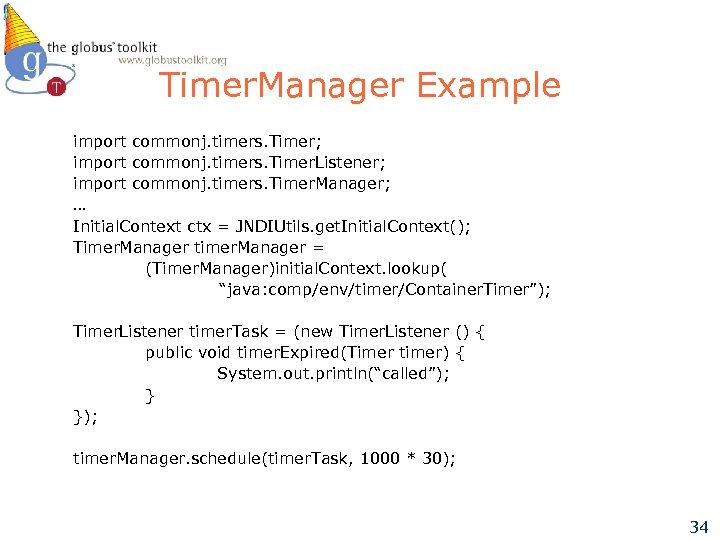 Timer. Manager Example import commonj. timers. Timer; import commonj. timers. Timer. Listener; import commonj. timers. Timer. Manager; … Initial. Context ctx = JNDIUtils. get. Initial. Context(); Timer. Manager timer. Manager = (Timer. Manager)initial. Context. lookup( “java: comp/env/timer/Container. Timer”); Timer. Listener timer. Task = (new Timer. Listener () { public void timer. Expired(Timer timer) { System. out. println(“called”); } }); timer. Manager. schedule(timer. Task, 1000 * 30); 34
Timer. Manager Example import commonj. timers. Timer; import commonj. timers. Timer. Listener; import commonj. timers. Timer. Manager; … Initial. Context ctx = JNDIUtils. get. Initial. Context(); Timer. Manager timer. Manager = (Timer. Manager)initial. Context. lookup( “java: comp/env/timer/Container. Timer”); Timer. Listener timer. Task = (new Timer. Listener () { public void timer. Expired(Timer timer) { System. out. println(“called”); } }); timer. Manager. schedule(timer. Task, 1000 * 30); 34
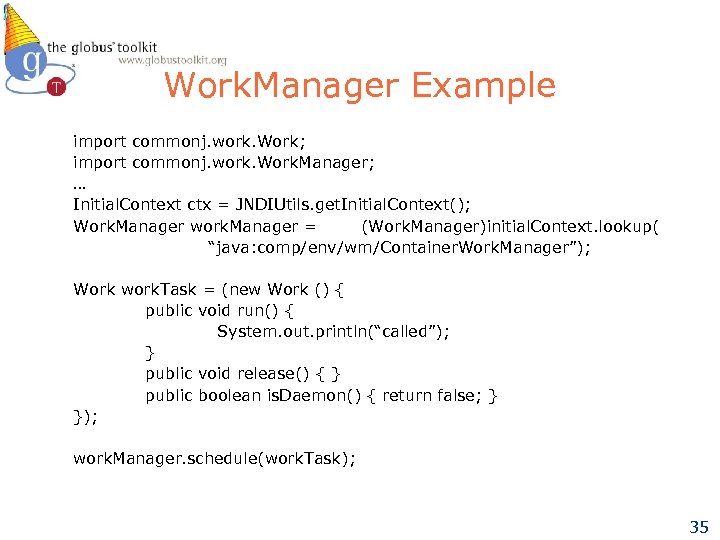 Work. Manager Example import commonj. work. Work; import commonj. work. Work. Manager; … Initial. Context ctx = JNDIUtils. get. Initial. Context(); Work. Manager work. Manager = (Work. Manager)initial. Context. lookup( “java: comp/env/wm/Container. Work. Manager”); Work work. Task = (new Work () { public void run() { System. out. println(“called”); } public void release() { } public boolean is. Daemon() { return false; } }); work. Manager. schedule(work. Task); 35
Work. Manager Example import commonj. work. Work; import commonj. work. Work. Manager; … Initial. Context ctx = JNDIUtils. get. Initial. Context(); Work. Manager work. Manager = (Work. Manager)initial. Context. lookup( “java: comp/env/wm/Container. Work. Manager”); Work work. Task = (new Work () { public void run() { System. out. println(“called”); } public void release() { } public boolean is. Daemon() { return false; } }); work. Manager. schedule(work. Task); 35
 Production Tuning l Settings to watch for in production environment u JVM max/min heap size u File descriptors per process u Container service thread pool 36
Production Tuning l Settings to watch for in production environment u JVM max/min heap size u File descriptors per process u Container service thread pool 36
 JVM Heap Size l Most JVM use 64 MB max heap size by default u This might be too small for some applications u Indication of the problem l java. lang. Out. Of. Memory. Error u l Of course, could also indicate a memory leak in application To adjust, pass –Xmx
JVM Heap Size l Most JVM use 64 MB max heap size by default u This might be too small for some applications u Indication of the problem l java. lang. Out. Of. Memory. Error u l Of course, could also indicate a memory leak in application To adjust, pass –Xmx
 File Descriptors l Most OS limit the number of opened file descriptors to 1024 per process u File descriptors = incoming connections + outgoing connections + opened files + pipes u This might be too small for some applications u Indication of the problem l java. io. IOException: Too many open files u Of course, could also indicate a problem in application » Forgetting to close connections, files, etc. l To adjust, see your OS documentation on how to increase this limit 38
File Descriptors l Most OS limit the number of opened file descriptors to 1024 per process u File descriptors = incoming connections + outgoing connections + opened files + pipes u This might be too small for some applications u Indication of the problem l java. io. IOException: Too many open files u Of course, could also indicate a problem in application » Forgetting to close connections, files, etc. l To adjust, see your OS documentation on how to increase this limit 38
 Container Thread Pool l Java WS Core container uses a thread pool for serving requests u u Requests are also put into a queue The maximum thread pool size is 20 by default l l Used to be 8 in GT 4. 0. 2 and older Might be too small for some applications Can lead to “java. net. Socket. Timeout. Exception: Read timed out” exceptions u When lots of requests queue up and there are no available threads to service them To adjust, edit $G_L/etc/globus_wsrf_core/serverconfig. wsdd file and add or modify the following parameter u
Container Thread Pool l Java WS Core container uses a thread pool for serving requests u u Requests are also put into a queue The maximum thread pool size is 20 by default l l Used to be 8 in GT 4. 0. 2 and older Might be too small for some applications Can lead to “java. net. Socket. Timeout. Exception: Read timed out” exceptions u When lots of requests queue up and there are no available threads to service them To adjust, edit $G_L/etc/globus_wsrf_core/serverconfig. wsdd file and add or modify the following parameter u
 General Debugging Tips l Use a profiler tool! l Read JVM troubleshooting documentation u Sun JVM l u http: //java. sun. com/j 2 se/1. 5/pdf/jdk 50_ts_guide. pdf IBM JVM l http: //publib. boulder. ibm. com/infocenter/javasdk/v 5 r 0 40
General Debugging Tips l Use a profiler tool! l Read JVM troubleshooting documentation u Sun JVM l u http: //java. sun. com/j 2 se/1. 5/pdf/jdk 50_ts_guide. pdf IBM JVM l http: //publib. boulder. ibm. com/infocenter/javasdk/v 5 r 0 40
 Some Useful Debugging Tips l JVM Thread Dump u u Useful for detecting deadlocks or seeing the status of threads On Unix l u On Windows l l kill –QUIT
Some Useful Debugging Tips l JVM Thread Dump u u Useful for detecting deadlocks or seeing the status of threads On Unix l u On Windows l l kill –QUIT
 New Features in GT 4. 2 l HTTP/S connection persistence u l WS-Enumeration support u u l Improves performance especially for HTTPS connections Large XML datasets can be returned a chunk at a time Service API for adding WS-Enumeration capabilities to any service Targeted. XPath query dialect u Improved, more efficient XPath querying of resource properties l l l Use namespace prefixes reliably in the query expression u Explicit namespace mappings sent with the query Query a particular resource property instead of the entire resource property document Return query results as WS-Enumeration 42
New Features in GT 4. 2 l HTTP/S connection persistence u l WS-Enumeration support u u l Improves performance especially for HTTPS connections Large XML datasets can be returned a chunk at a time Service API for adding WS-Enumeration capabilities to any service Targeted. XPath query dialect u Improved, more efficient XPath querying of resource properties l l l Use namespace prefixes reliably in the query expression u Explicit namespace mappings sent with the query Query a particular resource property instead of the entire resource property document Return query results as WS-Enumeration 42
 New Features in GT 4. 2 l Dynamic Deployment (standalone container only) u u l SOAP with Attachments u u l Deploy or undeploy (remotely) a service from the container without restarting it Direct the container to reinitialize itself (after configuration change) Standalone container will now handle attachments DIME, MTOM formats supported Other u u u Updated 3 rd party libraries (including Axis) Automatic validation of WSDD, JNDI, security descriptor files Error codes in error messages 43
New Features in GT 4. 2 l Dynamic Deployment (standalone container only) u u l SOAP with Attachments u u l Deploy or undeploy (remotely) a service from the container without restarting it Direct the container to reinitialize itself (after configuration change) Standalone container will now handle attachments DIME, MTOM formats supported Other u u u Updated 3 rd party libraries (including Axis) Automatic validation of WSDD, JNDI, security descriptor files Error codes in error messages 43
 Questions? l More information u GT 4. 0. x l u Latest documentation (for GT 4. 2) l l http: //www. globus. org/toolkit/docs/4. 0/common/javawscore/ http: //www. globus. org/toolkit/docs/development/4. 2 drafts/common/javawscore/ Contribute to Java WS Core u http: //dev. globus. org/wiki/Java_WS_Core 44
Questions? l More information u GT 4. 0. x l u Latest documentation (for GT 4. 2) l l http: //www. globus. org/toolkit/docs/4. 0/common/javawscore/ http: //www. globus. org/toolkit/docs/development/4. 2 drafts/common/javawscore/ Contribute to Java WS Core u http: //dev. globus. org/wiki/Java_WS_Core 44
 GT Java WS Security 45
GT Java WS Security 45
 Security Concepts Overview l Authentication u l Establish identity of an entity Message Protection Integrity u Privacy u l Delegation u l Empower an entity with rights of another Authorization u Ascertain and enforce rights of an identity 46
Security Concepts Overview l Authentication u l Establish identity of an entity Message Protection Integrity u Privacy u l Delegation u l Empower an entity with rights of another Authorization u Ascertain and enforce rights of an identity 46
 Outline 1. Authentication Framework u Message Protection 2. Delegation 3. Authorization Framework u Attribute Processing 4. Security Descriptor Framework 5. Writing secure service, resource and client 47
Outline 1. Authentication Framework u Message Protection 2. Delegation 3. Authorization Framework u Attribute Processing 4. Security Descriptor Framework 5. Writing secure service, resource and client 47
 Authentication Framework 48
Authentication Framework 48
 Authentication Schemes l Secure Transport u u Anonymous access support u l Secure Sockets (https) Container-level configuration Secure Message u u l Each individual message is secured Replay Attack Prevention Secure Conversation u Handshake to establish secure context u Anonymous access support 49
Authentication Schemes l Secure Transport u u Anonymous access support u l Secure Sockets (https) Container-level configuration Secure Message u u l Each individual message is secured Replay Attack Prevention Secure Conversation u Handshake to establish secure context u Anonymous access support 49
 Server-side features l Message Protection options u l Integrity and Privacy Configure required authentication as policy u u l At service or resource level Programmatic or security descriptors Server response u Same authentication scheme as request 50
Server-side features l Message Protection options u l Integrity and Privacy Configure required authentication as policy u u l At service or resource level Programmatic or security descriptors Server response u Same authentication scheme as request 50
 Client-side features l Configurable client side authentication u u Properties on the Stub u l Per invocation granularity Programmatically or Security Descriptors Message Protection options u Integrity and Privacy u Default: Integrity protection 51
Client-side features l Configurable client side authentication u u Properties on the Stub u l Per invocation granularity Programmatically or Security Descriptors Message Protection options u Integrity and Privacy u Default: Integrity protection 51
 Related Utility API l To get peer’s subject: u l Security. Manager. get. Manager(). get. Peer. Subject () To get peer’s identity u Security. Manager. get. Manager(). get. Caller() 52
Related Utility API l To get peer’s subject: u l Security. Manager. get. Manager(). get. Peer. Subject () To get peer’s identity u Security. Manager. get. Manager(). get. Caller() 52
 Delegation 53
Delegation 53
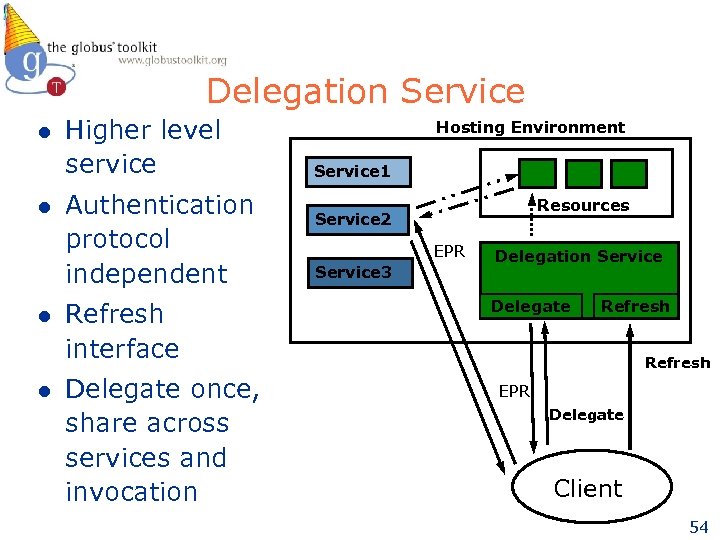 Delegation Service l l Higher level service Authentication protocol independent Refresh interface Delegate once, share across services and invocation Hosting Environment Service 1 Resources Service 2 EPR Service 3 Delegation Service Delegate Refresh EPR Delegate Client 54
Delegation Service l l Higher level service Authentication protocol independent Refresh interface Delegate once, share across services and invocation Hosting Environment Service 1 Resources Service 2 EPR Service 3 Delegation Service Delegate Refresh EPR Delegate Client 54
 Delegation l Secure Conversation u Can delegate as part of protocol u Extra round trip with delegation u l Delegation Service is preferred way of delegating Secure Message and Secure Transport u Cannot delegate as part of protocol 55
Delegation l Secure Conversation u Can delegate as part of protocol u Extra round trip with delegation u l Delegation Service is preferred way of delegating Secure Message and Secure Transport u Cannot delegate as part of protocol 55
 Authorization Framework 56
Authorization Framework 56
 Server-side Authorization Framework l Establishes if a client is allowed to invoke an operation on a resource l Only authenticated calls are authorized l Authorization policy configurable at resource, service or container level 57
Server-side Authorization Framework l Establishes if a client is allowed to invoke an operation on a resource l Only authenticated calls are authorized l Authorization policy configurable at resource, service or container level 57
 Server-side Authorization Framework l Policy Information Points (PIPs) u u l Collect attributes (subject, action, resource) Ex: Parameter PIP Policy Decision Points (PDPs) u u l Evaluate authorization policy Ex: Grid. Map Authorization, Self Authorization Engine u Orchestrates authorization process u Enforce authorization policy u Combining algorithm to renders a decision 58
Server-side Authorization Framework l Policy Information Points (PIPs) u u l Collect attributes (subject, action, resource) Ex: Parameter PIP Policy Decision Points (PDPs) u u l Evaluate authorization policy Ex: Grid. Map Authorization, Self Authorization Engine u Orchestrates authorization process u Enforce authorization policy u Combining algorithm to renders a decision 58
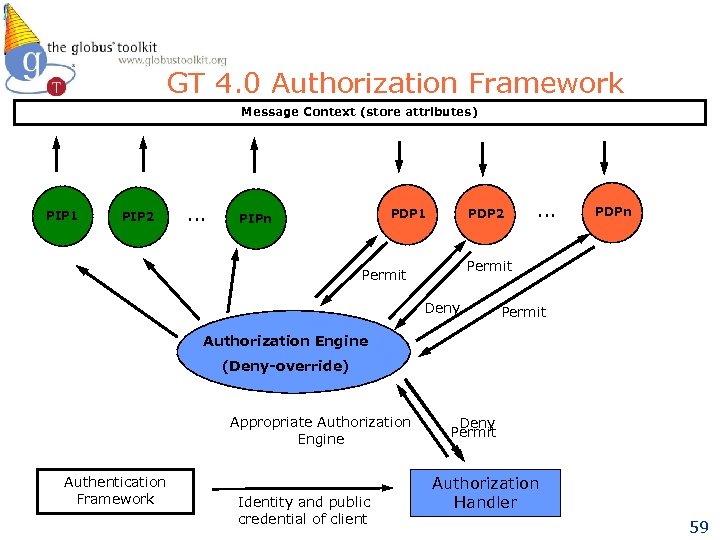 GT 4. 0 Authorization Framework Message Context (store attributes) PIP 1 PIP 2 … PDP 2 PDP 1 PIPn … PDPn Permit Deny Permit Authorization Engine (Deny-override) Appropriate Authorization Engine Authentication Framework Identity and public credential of client Deny Permit Authorization Handler 59
GT 4. 0 Authorization Framework Message Context (store attributes) PIP 1 PIP 2 … PDP 2 PDP 1 PIPn … PDPn Permit Deny Permit Authorization Engine (Deny-override) Appropriate Authorization Engine Authentication Framework Identity and public credential of client Deny Permit Authorization Handler 59
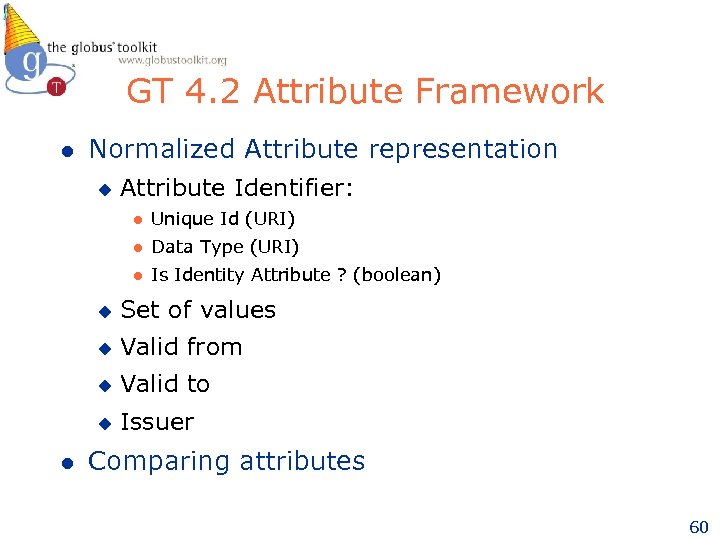 GT 4. 2 Attribute Framework l Normalized Attribute representation u Attribute Identifier: l Unique Id (URI) l Data Type (URI) l Is Identity Attribute ? (boolean) u u Valid from u Valid to u l Set of values Issuer Comparing attributes 60
GT 4. 2 Attribute Framework l Normalized Attribute representation u Attribute Identifier: l Unique Id (URI) l Data Type (URI) l Is Identity Attribute ? (boolean) u u Valid from u Valid to u l Set of values Issuer Comparing attributes 60
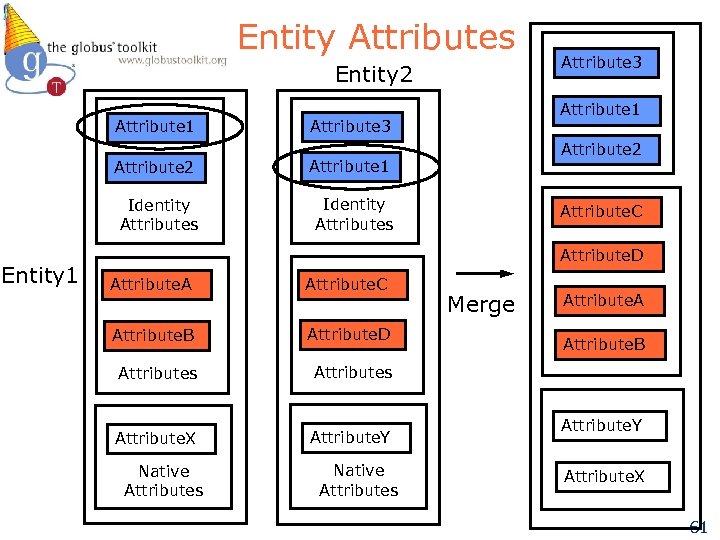 Entity Attributes Entity 2 Attribute 1 Attribute 2 Attribute 1 Identity Attributes Entity 1 Attribute 3 Attribute 2 Attribute 3 Identity Attributes Attribute. C Attribute. D Attribute. A Attribute. C Attribute. B Attribute. D Attributes Attribute. X Attribute. Y Native Attributes Merge Attribute. A Attribute. B Attribute. Y Attribute. X 61
Entity Attributes Entity 2 Attribute 1 Attribute 2 Attribute 1 Identity Attributes Entity 1 Attribute 3 Attribute 2 Attribute 3 Identity Attributes Attribute. C Attribute. D Attribute. A Attribute. C Attribute. B Attribute. D Attributes Attribute. X Attribute. Y Native Attributes Merge Attribute. A Attribute. B Attribute. Y Attribute. X 61
 GT 4. 2 Attribute Framework l Bootstrap PIP u u Collects attributes about the request: subject, action and resource Example: X 509 Bootstrap. PIP 62
GT 4. 2 Attribute Framework l Bootstrap PIP u u Collects attributes about the request: subject, action and resource Example: X 509 Bootstrap. PIP 62
 GT 4. 2 PDP Interface l Access rights u l Administrative rights u l can. Access() can. Admin() Return type: Decision u PERMIT/DENY/INDETERMINATE u Issuer of decision u Validity u Exception, if any 63
GT 4. 2 PDP Interface l Access rights u l Administrative rights u l can. Access() can. Admin() Return type: Decision u PERMIT/DENY/INDETERMINATE u Issuer of decision u Validity u Exception, if any 63
 GT 4. 2 Authorization Engine l Pluggable combining algorithm l Abstract. Engine. java u Initializes PIPs and PDPs with configured parameters u Invokes collect. Attributes() on all PIPs u Merges the entity attributes returned by PIPs u Abstract method engine. Authorize process PDPs l l l Combines decisions from individual PDPs Returns Decision Default combining algorithm u u Permit override with delegation of rights At-least one decision chain from resource owner to requestor for a PERMIT 64
GT 4. 2 Authorization Engine l Pluggable combining algorithm l Abstract. Engine. java u Initializes PIPs and PDPs with configured parameters u Invokes collect. Attributes() on all PIPs u Merges the entity attributes returned by PIPs u Abstract method engine. Authorize process PDPs l l l Combines decisions from individual PDPs Returns Decision Default combining algorithm u u Permit override with delegation of rights At-least one decision chain from resource owner to requestor for a PERMIT 64
![GT 4. 2 Authorization Framework b. PIP 1 [owner 1] … b. PIPn [owner. GT 4. 2 Authorization Framework b. PIP 1 [owner 1] … b. PIPn [owner.](https://present5.com/presentation/00bfb43806ad21a4021ce0b2303fa99c/image-65.jpg) GT 4. 2 Authorization Framework b. PIP 1 [owner 1] … b. PIPn [owner. N] Request Attributes PIP 1 [owner 1] … PIPn PDP 1 [owner 1] [owner. N] can. Admin Attributes … PDPn [owner. N] can. Access Authorization Engine PIP Attribute Processing PDP Combining Algorithm Appropriate Authorization Engine Authentication Framework Identity and public credential of client Decision Authorization Handler 65
GT 4. 2 Authorization Framework b. PIP 1 [owner 1] … b. PIPn [owner. N] Request Attributes PIP 1 [owner 1] … PIPn PDP 1 [owner 1] [owner. N] can. Admin Attributes … PDPn [owner. N] can. Access Authorization Engine PIP Attribute Processing PDP Combining Algorithm Appropriate Authorization Engine Authentication Framework Identity and public credential of client Decision Authorization Handler 65
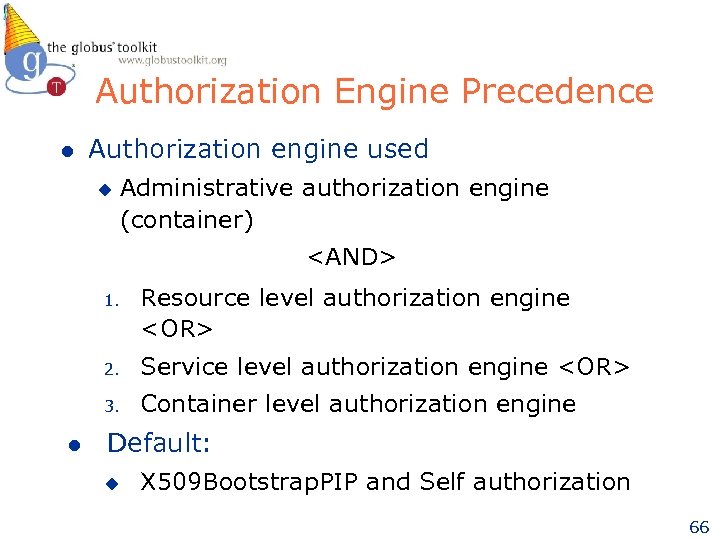 Authorization Engine Precedence l Authorization engine used u Administrative authorization engine (container)
Authorization Engine Precedence l Authorization engine used u Administrative authorization engine (container)
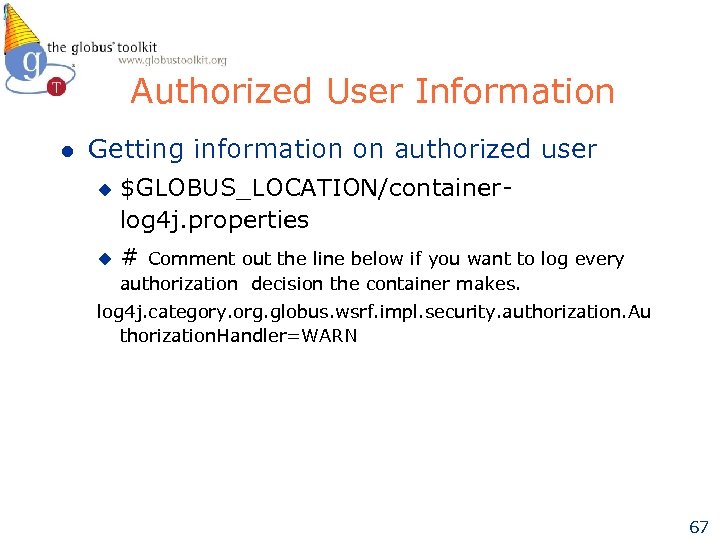 Authorized User Information l Getting information on authorized user u u $GLOBUS_LOCATION/containerlog 4 j. properties # Comment out the line below if you want to log every authorization decision the container makes. log 4 j. category. org. globus. wsrf. impl. security. authorization. Au thorization. Handler=WARN 67
Authorized User Information l Getting information on authorized user u u $GLOBUS_LOCATION/containerlog 4 j. properties # Comment out the line below if you want to log every authorization decision the container makes. log 4 j. category. org. globus. wsrf. impl. security. authorization. Au thorization. Handler=WARN 67
 Client-side Authorization l Determines if said service/resource is allowed to cater to the client’s request l Pluggable authorization scheme u Defined interface, implement custom schemes l Configured as property on stub or using security descriptors l Examples: Self, Host, Identity, None l Default: Host l Required when secure conversation is used with delegation 68
Client-side Authorization l Determines if said service/resource is allowed to cater to the client’s request l Pluggable authorization scheme u Defined interface, implement custom schemes l Configured as property on stub or using security descriptors l Examples: Self, Host, Identity, None l Default: Host l Required when secure conversation is used with delegation 68
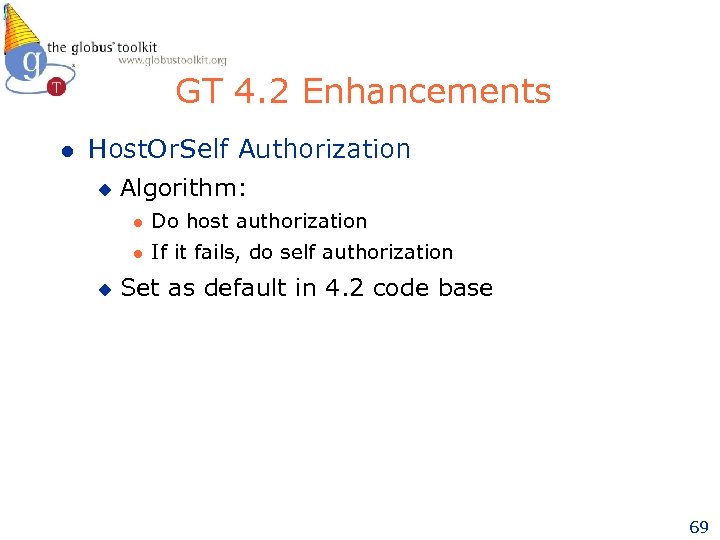 GT 4. 2 Enhancements l Host. Or. Self Authorization u Algorithm: l l u Do host authorization If it fails, do self authorization Set as default in 4. 2 code base 69
GT 4. 2 Enhancements l Host. Or. Self Authorization u Algorithm: l l u Do host authorization If it fails, do self authorization Set as default in 4. 2 code base 69
 Security Descriptor Framework 70
Security Descriptor Framework 70
 Security Descriptor Overview l Used to configure security properties l Declarative security u Configure properties in files l Different types of descriptors for container, service, resource and client security properties l GT 4. 2 Enhancements u Defined schema for each descriptor 71
Security Descriptor Overview l Used to configure security properties l Declarative security u Configure properties in files l Different types of descriptors for container, service, resource and client security properties l GT 4. 2 Enhancements u Defined schema for each descriptor 71
 Server-side Security Descriptor l Container descriptor in global section of deployment descriptor u u u l Service descriptor in service’s deployment descriptor u l Parameter: security. Descriptor Resource descriptor set programmatically u l $GLOBUS_LOCATION/etc/globus_wsrf_core/serverconfig. wsdd Parameter: container. Sec. Desc Can be done only in this file Load from file or use Resource. Security. Descriptor object Loaded as file or resource stream 72
Server-side Security Descriptor l Container descriptor in global section of deployment descriptor u u u l Service descriptor in service’s deployment descriptor u l Parameter: security. Descriptor Resource descriptor set programmatically u l $GLOBUS_LOCATION/etc/globus_wsrf_core/serverconfig. wsdd Parameter: container. Sec. Desc Can be done only in this file Load from file or use Resource. Security. Descriptor object Loaded as file or resource stream 72
 GT 4. 2 Credentials Configure l Proxy file name
GT 4. 2 Credentials Configure l Proxy file name
 GT 4. 2 Service Authentication Policy l Default for all operation:
GT 4. 2 Service Authentication Policy l Default for all operation:
 GT 4. 2 Run-as Configuration l Determines the credential to associate with current thread l Options: caller, system, service, resource l All methods: u l
GT 4. 2 Run-as Configuration l Determines the credential to associate with current thread l Options: caller, system, service, resource l All methods: u l
 GT 4. 2 Authorization Configuration Permit Override with delegation
GT 4. 2 Authorization Configuration Permit Override with delegation
 GT 4. 2 Authorization Parameters
GT 4. 2 Authorization Parameters
 Related Utility API l To get resource credential u l To get service credential u l Security. Manager. get. Manager(). get. Service. Subject() To get container credential u l Security. Manager. get. Manager(). get. Resource. Subject() Security. Manager. get. Manager(). get. System. Subject() To get effective credential u Security. Manager. get. Manager(). get. Subject() 78
Related Utility API l To get resource credential u l To get service credential u l Security. Manager. get. Manager(). get. Service. Subject() To get container credential u l Security. Manager. get. Manager(). get. Resource. Subject() Security. Manager. get. Manager(). get. System. Subject() To get effective credential u Security. Manager. get. Manager(). get. Subject() 78
 Client side descriptor l Security descriptor file u u l ((Stub)port). set. Property(Constants. CLIENT_DESCRI PTOR_FILE, file. Name); Absolute path or as resource stream or relative to $GLOBUS_LOCATION Security descriptor object u ((Stub)port). set. Property(Constants. CLIENT_DESCRI PTOR, instance of Client. Security. Descriptor); 79
Client side descriptor l Security descriptor file u u l ((Stub)port). set. Property(Constants. CLIENT_DESCRI PTOR_FILE, file. Name); Absolute path or as resource stream or relative to $GLOBUS_LOCATION Security descriptor object u ((Stub)port). set. Property(Constants. CLIENT_DESCRI PTOR, instance of Client. Security. Descriptor); 79
 GT 4. 2 Authentication Configuration l GSI Secure Transport
GT 4. 2 Authentication Configuration l GSI Secure Transport
 GT 4. 2 Authorization Configuration l Authorization Element u l
GT 4. 2 Authorization Configuration l Authorization Element u l
 Writing secure service, resource and client 82
Writing secure service, resource and client 82
 Writing Secure Service l Create security descriptor file u Typically placed in service source/etc l Ensure your build process picks up etc directory into gar Part of the source jar u Name file *security-config. xml u l Add parameter to deployment descriptor u
Writing Secure Service l Create security descriptor file u Typically placed in service source/etc l Ensure your build process picks up etc directory into gar Part of the source jar u Name file *security-config. xml u l Add parameter to deployment descriptor u
 Writing Secure Service l Write security properties in descriptor file l Deploy service l GT 4. 2, Run validate tool u globus-validate-descriptors u All files *security-config. xml are validated 84
Writing Secure Service l Write security properties in descriptor file l Deploy service l GT 4. 2, Run validate tool u globus-validate-descriptors u All files *security-config. xml are validated 84
 Writing Secure Resource public class Test. Resource implement Secure. Resource { Resource. Security. Descriptor desc = null; public Test. Resource() { this. desc = new Resource. Security. Descriptor(); this. desc = new Resource. Security. Descriptor(desc. File. Name); // set properties programmatically } this. desc. set. Default. Run. As. Type(Run. As. Value. _caller); public Resource. Security. Descriptor get. Security. Descriptor() { return this. desc; } } 85
Writing Secure Resource public class Test. Resource implement Secure. Resource { Resource. Security. Descriptor desc = null; public Test. Resource() { this. desc = new Resource. Security. Descriptor(); this. desc = new Resource. Security. Descriptor(desc. File. Name); // set properties programmatically } this. desc. set. Default. Run. As. Type(Run. As. Value. _caller); public Resource. Security. Descriptor get. Security. Descriptor() { return this. desc; } } 85
 Writing Secure Client l Construct Client. Security. Descriptor u u l l l From file Programmatically Extend from org. globus. wsrf. client. Base. Client u Parses standard security parameters u Use set. Options(stub) to set relevant security parameters If using GSI Secure Transport, Util. register. Secure. Transport() If contacted service uses GSI Secure Transport, container’s identity should be expected 86
Writing Secure Client l Construct Client. Security. Descriptor u u l l l From file Programmatically Extend from org. globus. wsrf. client. Base. Client u Parses standard security parameters u Use set. Options(stub) to set relevant security parameters If using GSI Secure Transport, Util. register. Secure. Transport() If contacted service uses GSI Secure Transport, container’s identity should be expected 86
 Questions? l Future Work: u l Documentation: u l http: //www. globus. org/toolkit/docs/development/4. 2 -drafts/security/index. html Code: u l http: //www. globus. org/roadmap/Projects. cgi#securit y http: //viewcvs. globus. org/viewcvs. cgi/wsrf/ Contributions: u http: //dev. globus. org/wiki/Java_WS_Core 87
Questions? l Future Work: u l Documentation: u l http: //www. globus. org/toolkit/docs/development/4. 2 -drafts/security/index. html Code: u l http: //www. globus. org/roadmap/Projects. cgi#securit y http: //viewcvs. globus. org/viewcvs. cgi/wsrf/ Contributions: u http: //dev. globus. org/wiki/Java_WS_Core 87
 Question: Do you see a Fun & Exciting Career in my future? Magic 8 Ball: All Signs Point to YES Say YES to Great Career Opportunities SOFTWARE ENGINEER/ARCHITECT Mathematics and Computer Science Division, Argonne National Laboratory The Grid is one of today's hottest technologies, and our team in the Distributed Systems Laboratory (www. mcs. anl. gov/dsl) is at the heart of it. Send us a resume through the Argonne site (www. anl. gov/Careers/), requisition number MCS-310886. SOFTWARE DEVELOPERS Computation Institute, University of Chicago Join a world-class team developing pioneering e. Science technologies and applications. Apply using the University's online employment application (http: //jobs. uchicago. edu/, click "Job Opportunities" and search for requisition numbers 072817 and 072442). See our Posting on the Globus. World Job Board or Talk to Any of our Globus Folks. 88
Question: Do you see a Fun & Exciting Career in my future? Magic 8 Ball: All Signs Point to YES Say YES to Great Career Opportunities SOFTWARE ENGINEER/ARCHITECT Mathematics and Computer Science Division, Argonne National Laboratory The Grid is one of today's hottest technologies, and our team in the Distributed Systems Laboratory (www. mcs. anl. gov/dsl) is at the heart of it. Send us a resume through the Argonne site (www. anl. gov/Careers/), requisition number MCS-310886. SOFTWARE DEVELOPERS Computation Institute, University of Chicago Join a world-class team developing pioneering e. Science technologies and applications. Apply using the University's online employment application (http: //jobs. uchicago. edu/, click "Job Opportunities" and search for requisition numbers 072817 and 072442). See our Posting on the Globus. World Job Board or Talk to Any of our Globus Folks. 88


