7a58204dd5a2cc85aeb313f8655cf14c.ppt
- Количество слайдов: 50

Java. Script Heap Analysis: From Browser Exploits to Safe Java. Script Subsets Adam Barth Joel Weinberger Matt Finifter Dawn Song University of California, Berkeley This presentation is copyright © 2009 Joel Weinberger
Java. Script Contexts Java. Script Context 1 Java. Script Context 2 Java. Script Context 3

Overview • Current Java. Script Security Model • Cross-Origin Java. Script Capability Leaks • Capability Leak Detection • Browser Defense Mechanism • Safe Java. Script Subsets
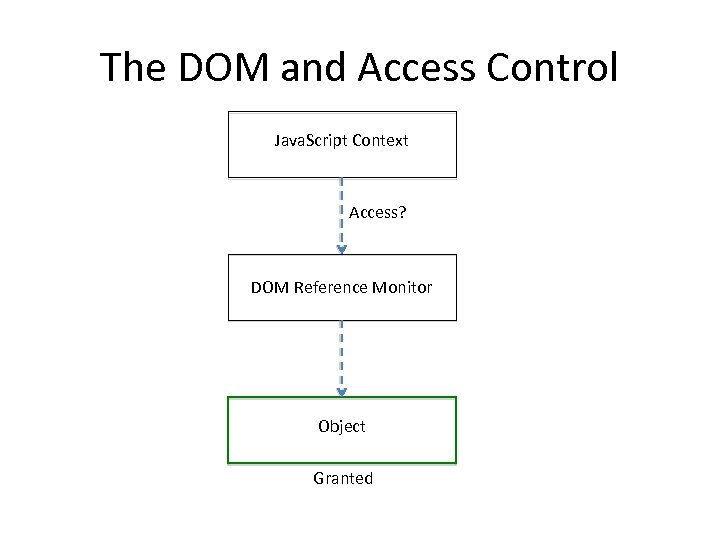
The DOM and Access Control Java. Script Context Access? DOM Reference Monitor Object Granted
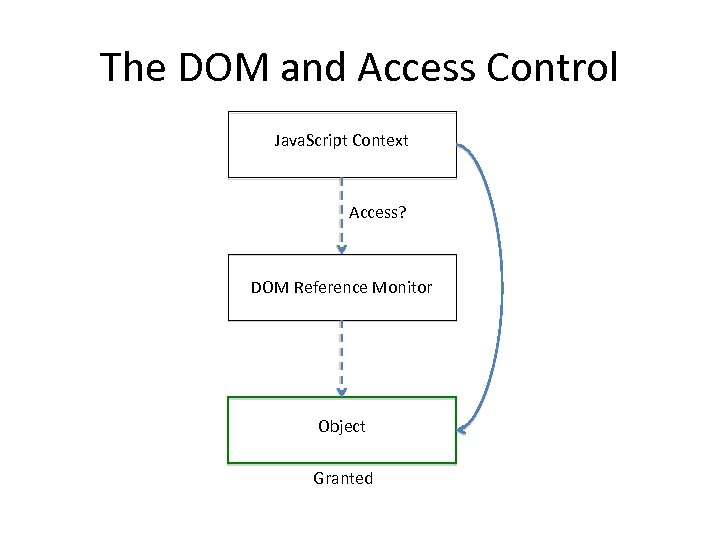
The DOM and Access Control Java. Script Context Access? DOM Reference Monitor Object Granted
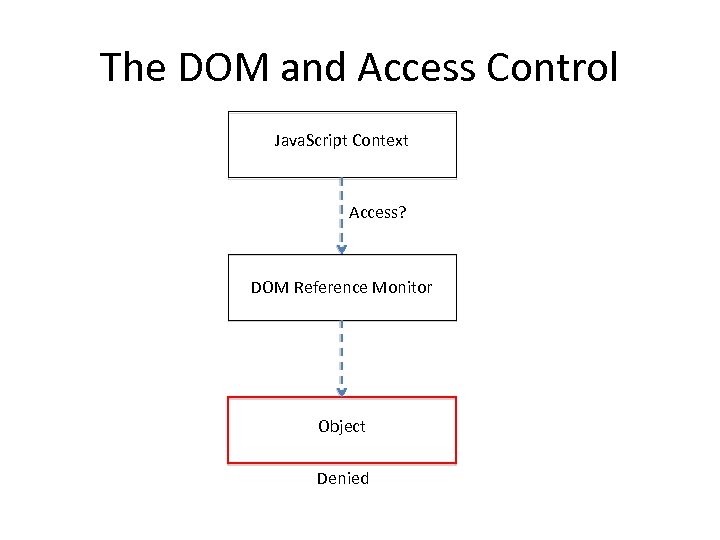
The DOM and Access Control Java. Script Context Access? DOM Reference Monitor Object Denied
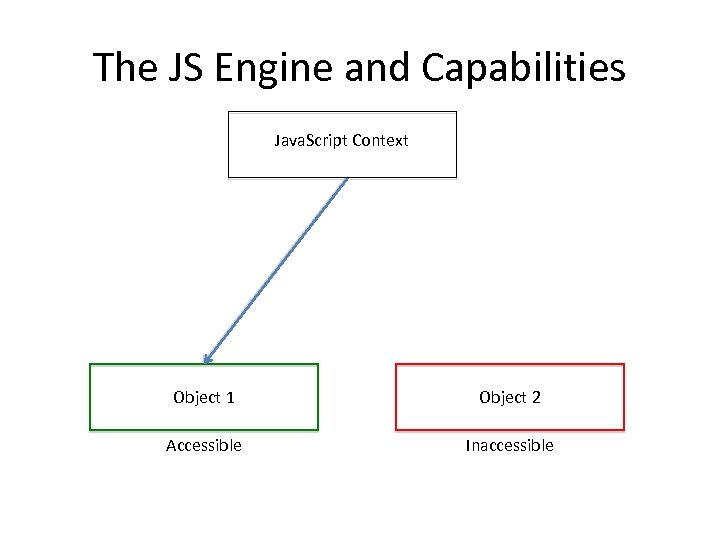
The JS Engine and Capabilities Java. Script Context Object 1 Object 2 Accessible Inaccessible
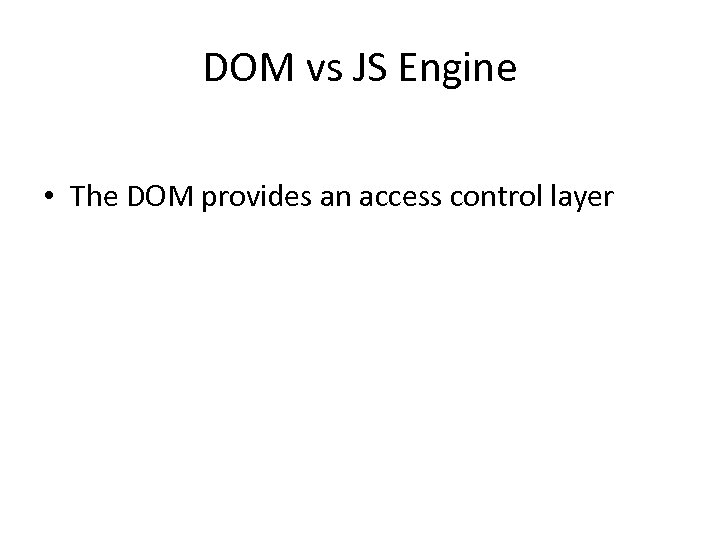
DOM vs JS Engine • The DOM provides an access control layer
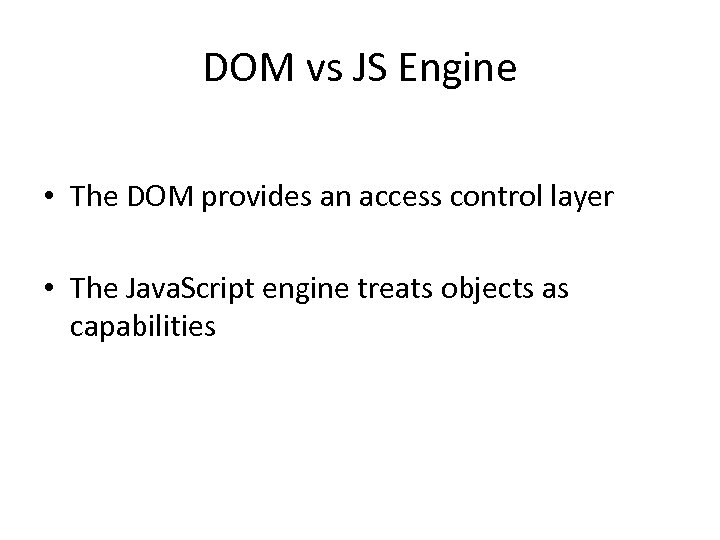
DOM vs JS Engine • The DOM provides an access control layer • The Java. Script engine treats objects as capabilities

Overview • Current Java. Script Security Model • Cross-Origin Java. Script Capability Leaks • Capability Leak Detection • Browser Defense Mechanism • Safe Java. Script Subsets
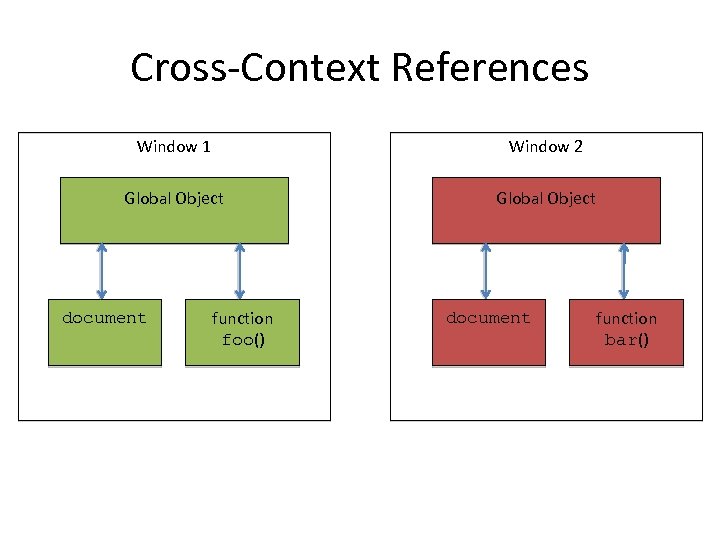
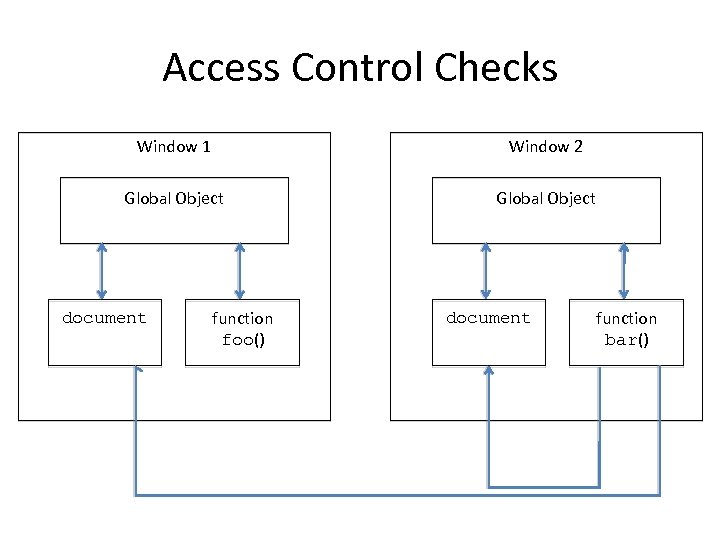
Cross-Context References Window 1 Window 2 Global Object document function foo() document function bar()
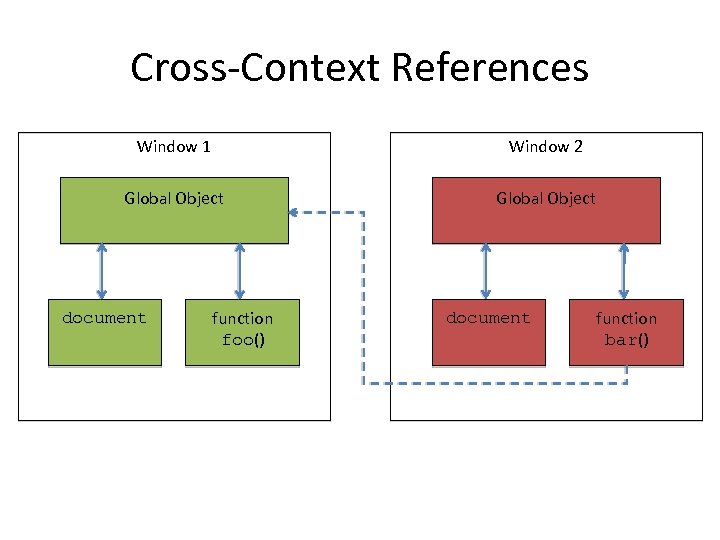
Cross-Context References Window 1 Window 2 Global Object document function foo() document function bar()
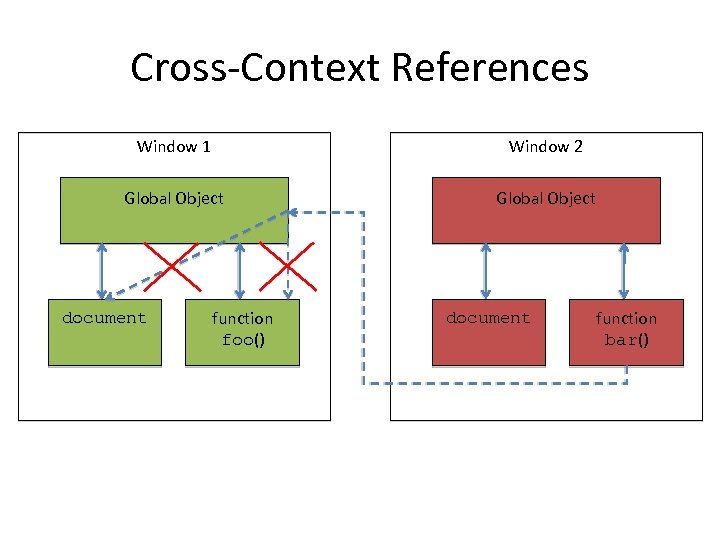
Cross-Context References Window 1 Window 2 Global Object document function foo() document function bar()
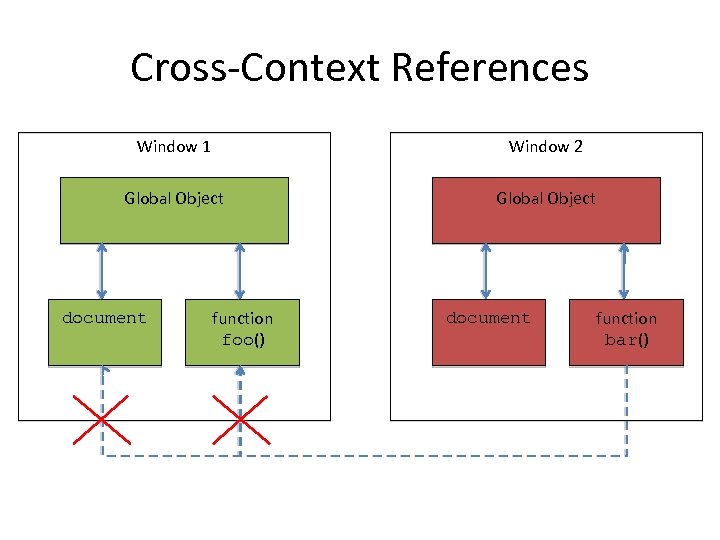
Cross-Context References Window 1 Window 2 Global Object document function foo() document function bar()
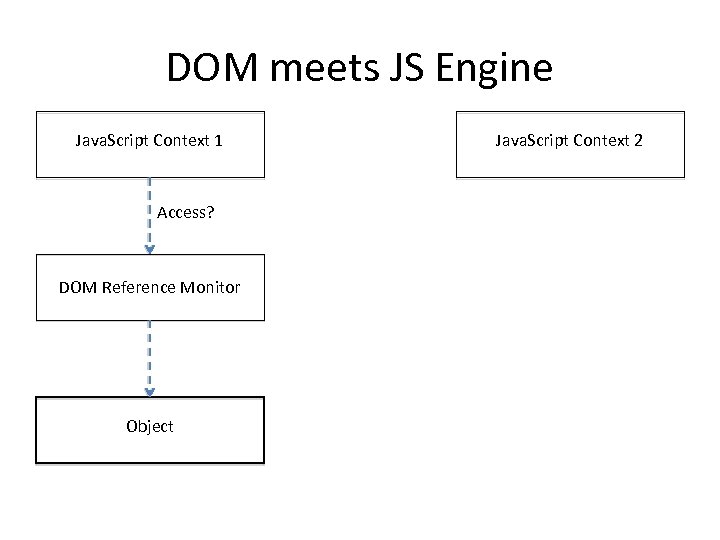
DOM meets JS Engine Java. Script Context 1 Access? DOM Reference Monitor Object Java. Script Context 2
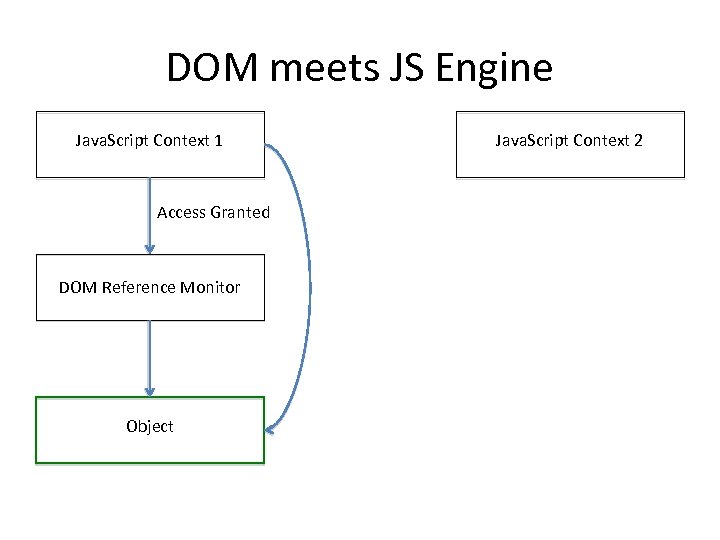
DOM meets JS Engine Java. Script Context 1 Access Granted DOM Reference Monitor Object Java. Script Context 2
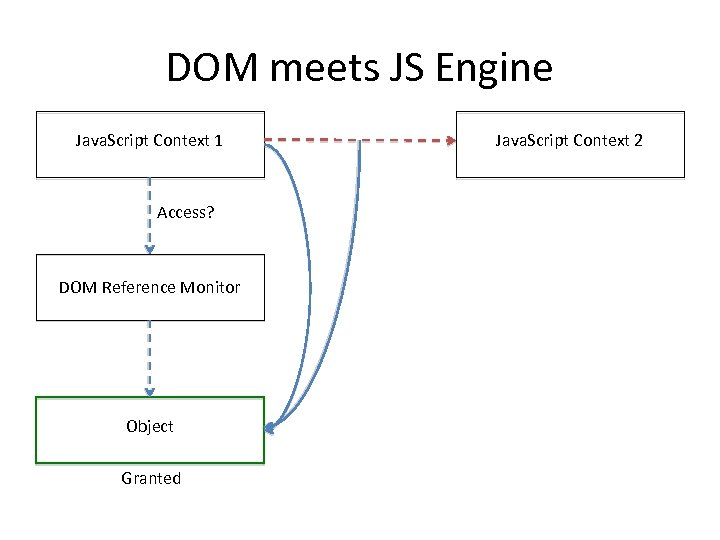
DOM meets JS Engine Java. Script Context 1 Access? DOM Reference Monitor Object Granted Java. Script Context 2
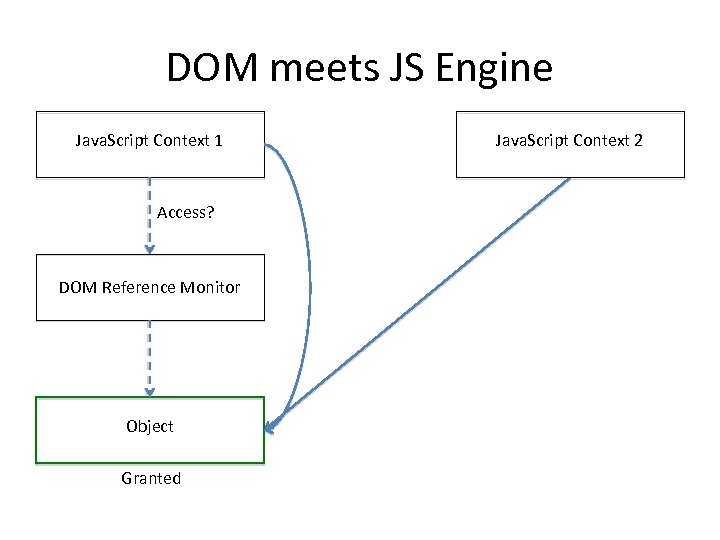
DOM meets JS Engine Java. Script Context 1 Access? DOM Reference Monitor Object Granted Java. Script Context 2
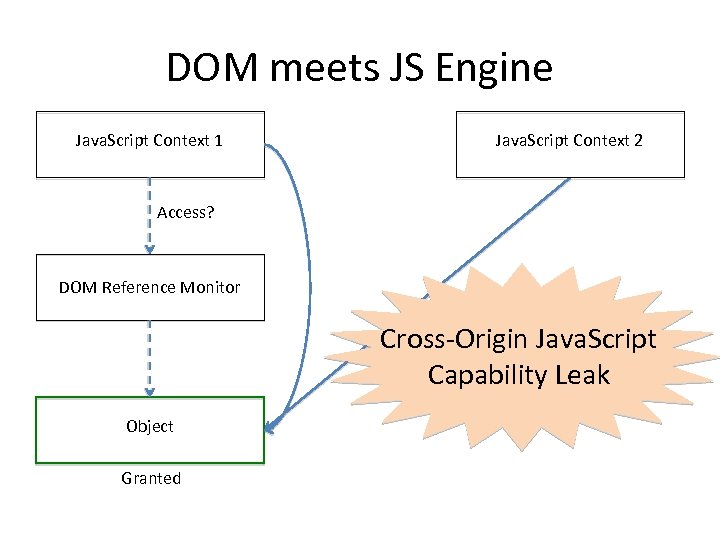
DOM meets JS Engine Java. Script Context 1 Java. Script Context 2 Access? DOM Reference Monitor Cross-Origin Java. Script Capability Leak Object Granted

Overview • Current Java. Script Security Model • Cross-Origin Java. Script Capability Leaks • Capability Leak Detection • Browser Defense Mechanism • Safe Java. Script Subsets
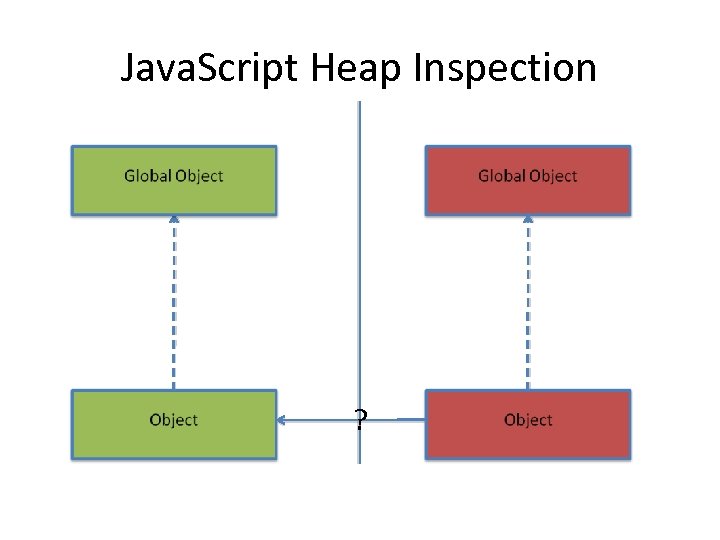
Java. Script Heap Inspection ?
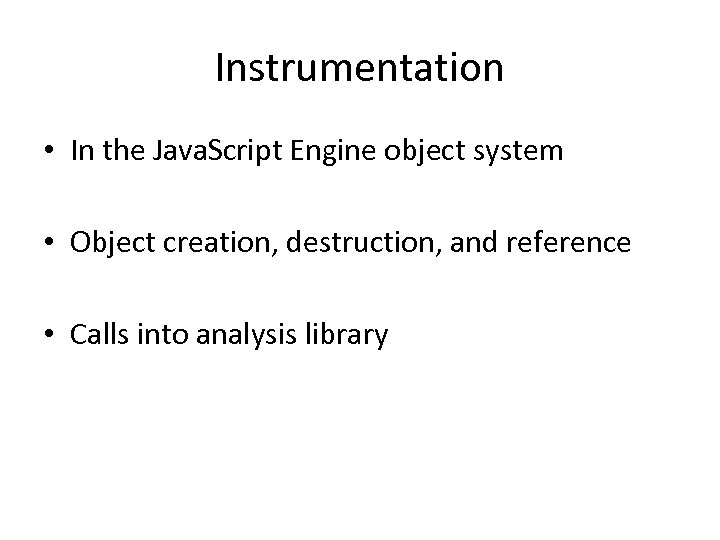
Instrumentation • In the Java. Script Engine object system • Object creation, destruction, and reference • Calls into analysis library
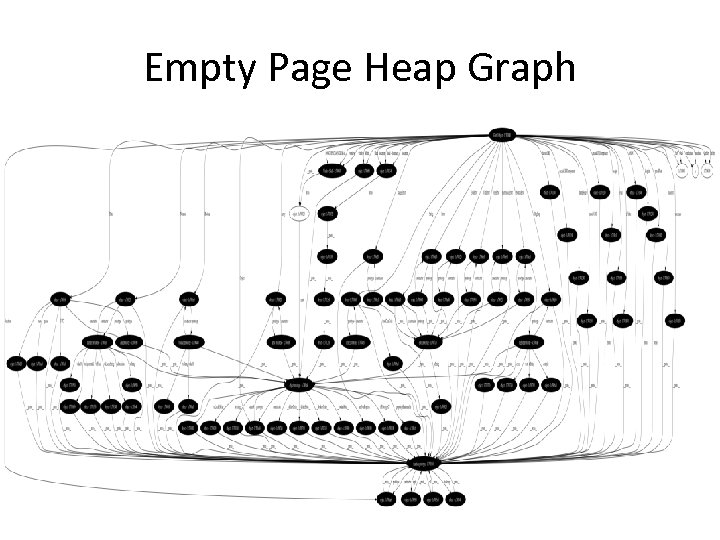
Empty Page Heap Graph
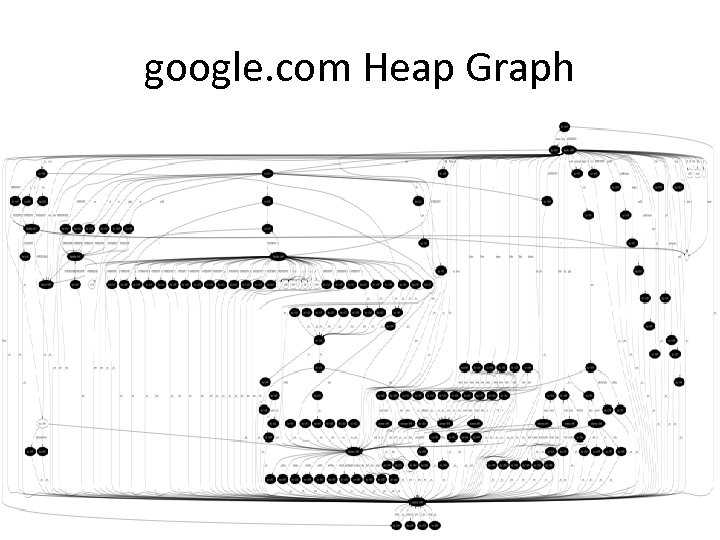
google. com Heap Graph
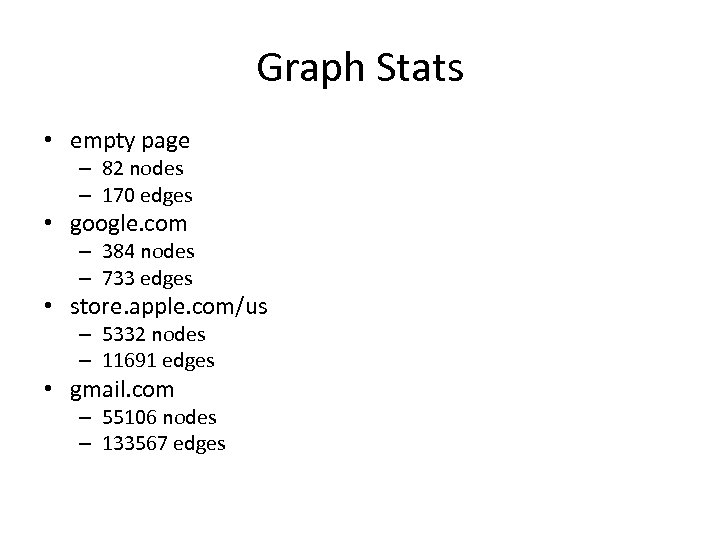
Graph Stats • empty page – 82 nodes – 170 edges • google. com – 384 nodes – 733 edges • store. apple. com/us – 5332 nodes – 11691 edges • gmail. com – 55106 nodes – 133567 edges
Computing Java. Script Contexts Global Object Prototype
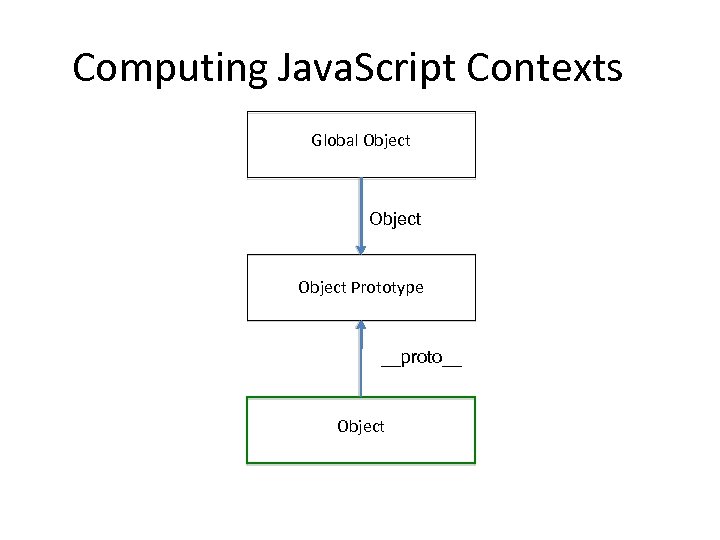
Computing Java. Script Contexts Global Object Prototype __proto__ Object

Generated Coverage • Total Web. Kit tests: – 9957 tests • …but most of these tests are for drawing • Security tests: – 143 tests
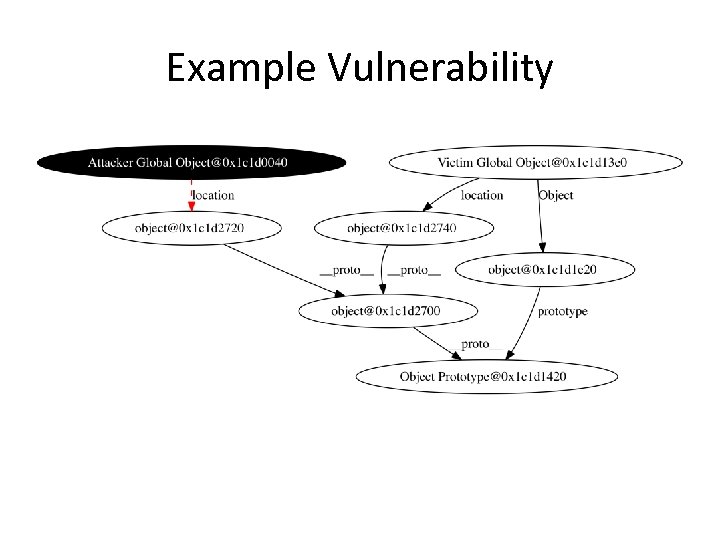
Example Vulnerability
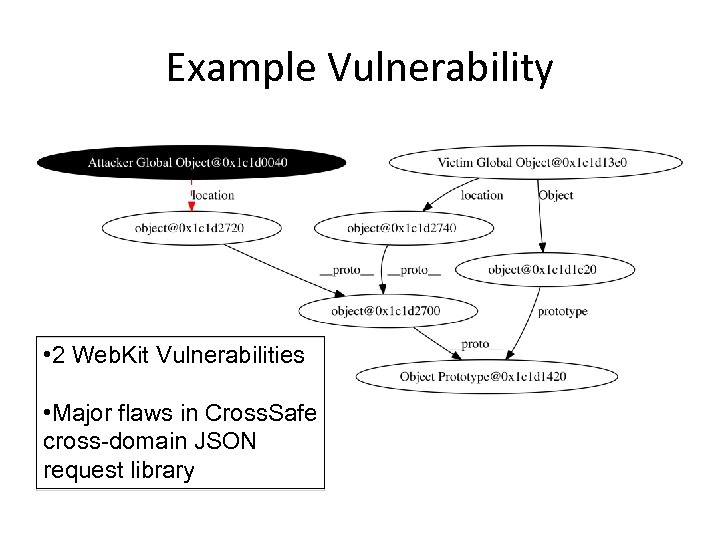
Example Vulnerability • 2 Web. Kit Vulnerabilities • Major flaws in Cross. Safe cross-domain JSON request library

Overview • Current Java. Script Security Model • Cross-Origin Java. Script Capability Leaks • Capability Leak Detection • Browser Defense Mechanism • Safe Java. Script Subsets
Access Control Checks Window 1 Window 2 Global Object document function foo() document function bar()
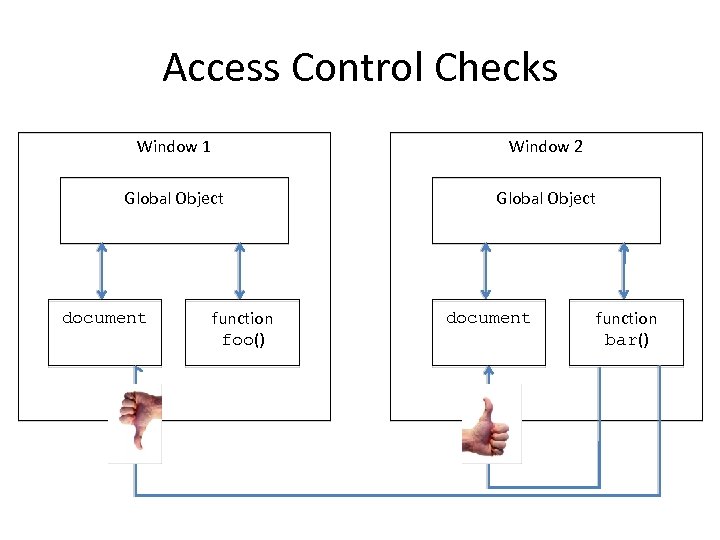
Access Control Checks Window 1 Window 2 Global Object document function foo() document function bar()
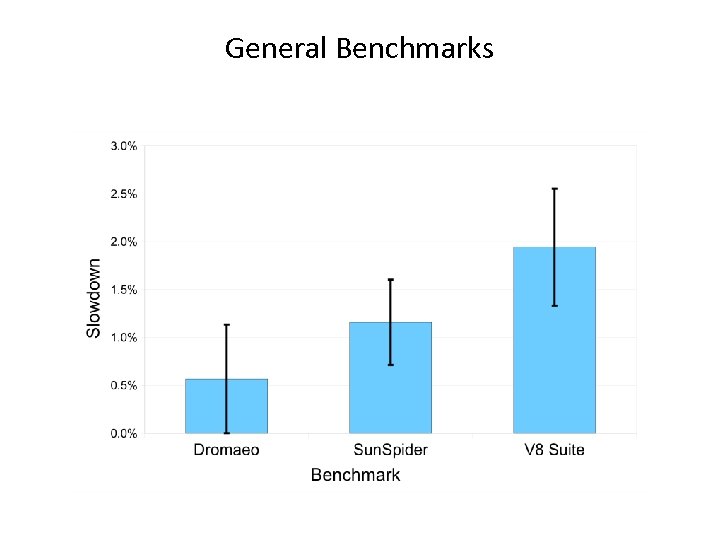
General Benchmarks

Overview • Current Java. Script Security Model • Cross-Origin Java. Script Capability Leaks • Capability Leak Detection • Browser Defense Mechanism • Safe Java. Script Subsets
Safe Java. Script Subets
Safe Java. Script Subets
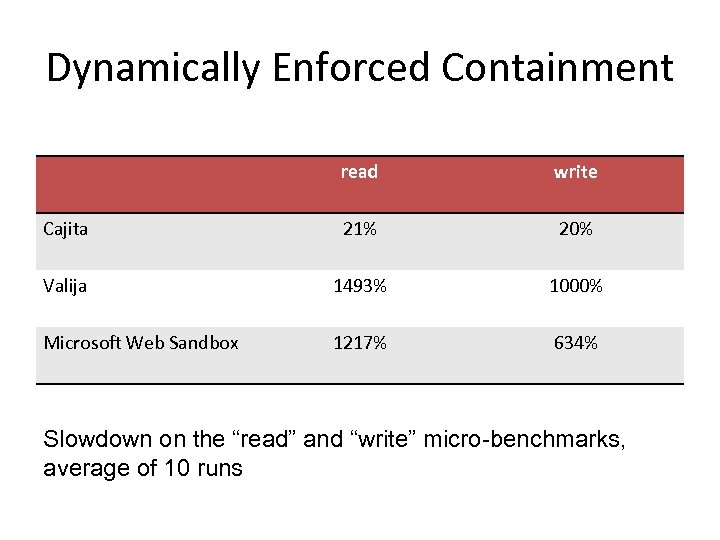
Dynamically Enforced Containment read write Cajita 21% 20% Valija 1493% 1000% Microsoft Web Sandbox 1217% 634% Slowdown on the “read” and “write” micro-benchmarks, average of 10 runs
Statically Verified Containment • ADsafe • Dojo Secure • Jacaranda
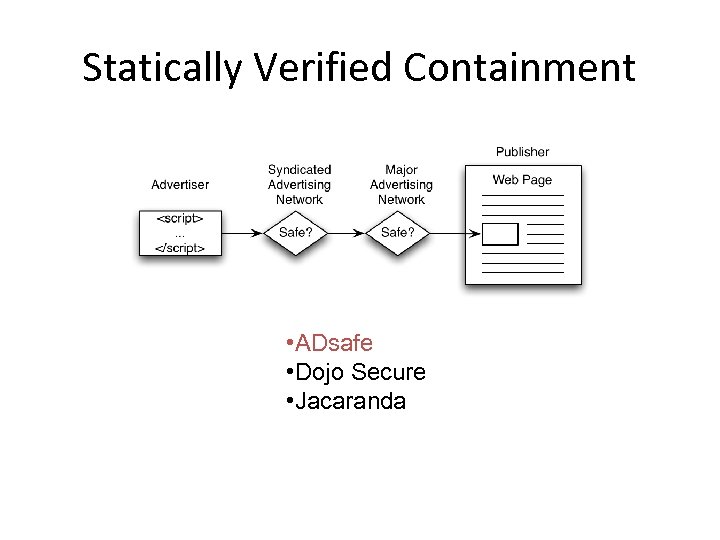
Statically Verified Containment • ADsafe • Dojo Secure • Jacaranda
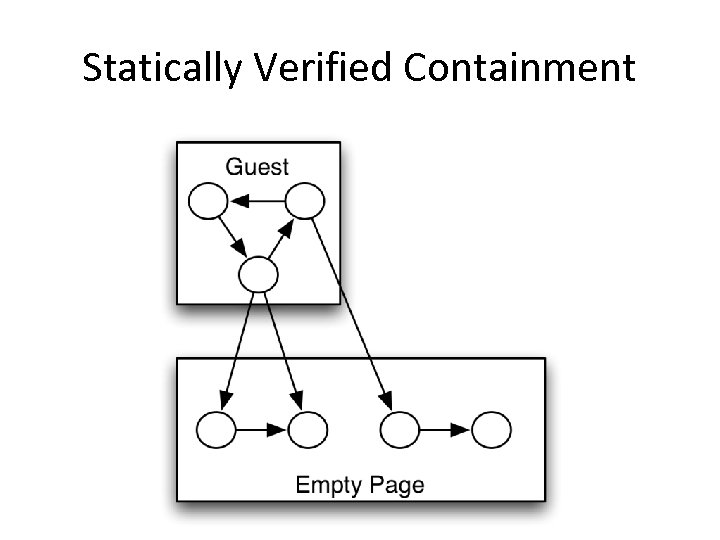
Statically Verified Containment
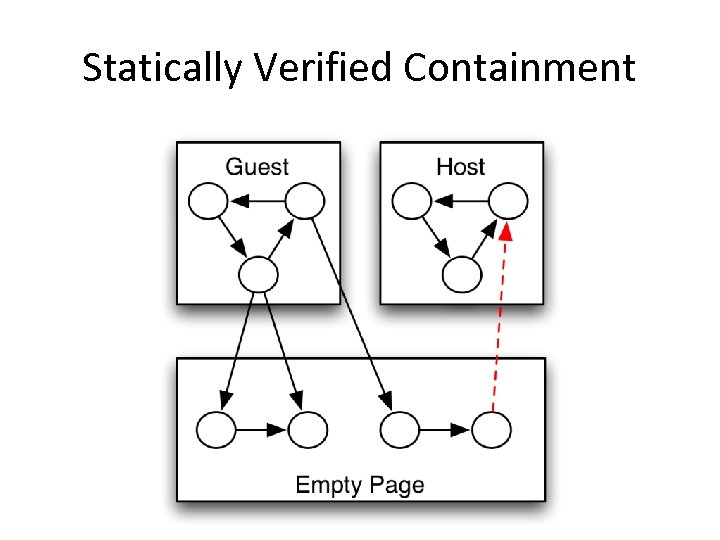
Statically Verified Containment
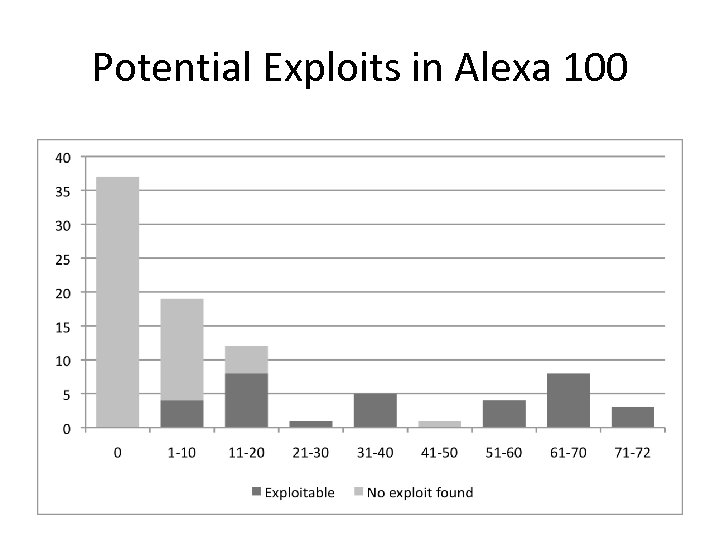
Potential Exploits in Alexa 100
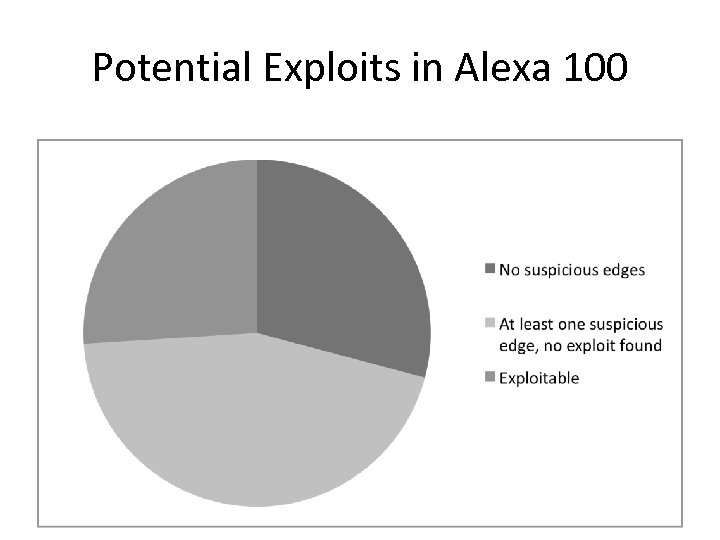
Potential Exploits in Alexa 100
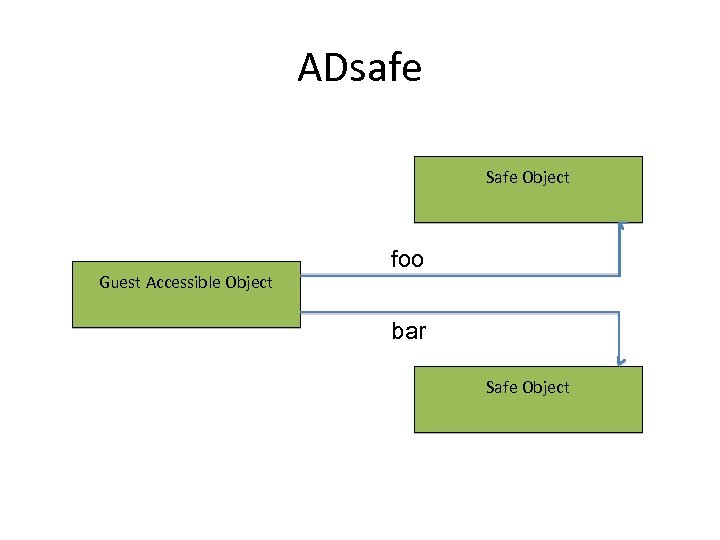
ADsafe Safe Object Guest Accessible Object foo bar Safe Object
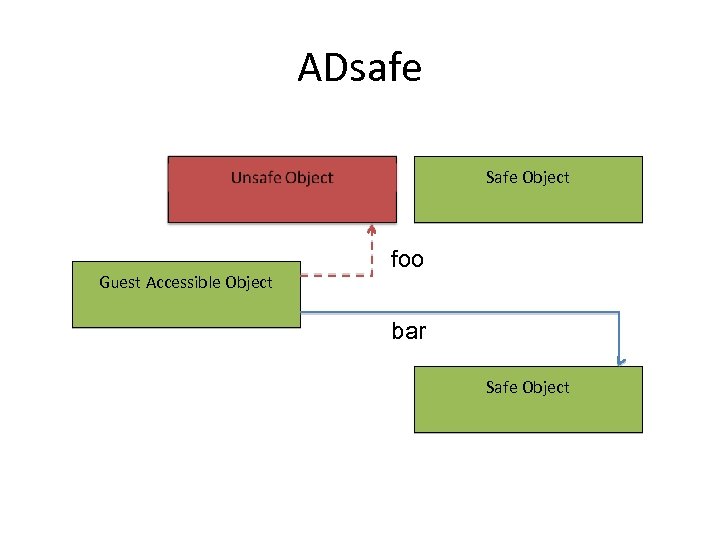
ADsafe Safe Object Guest Accessible Object foo bar Safe Object
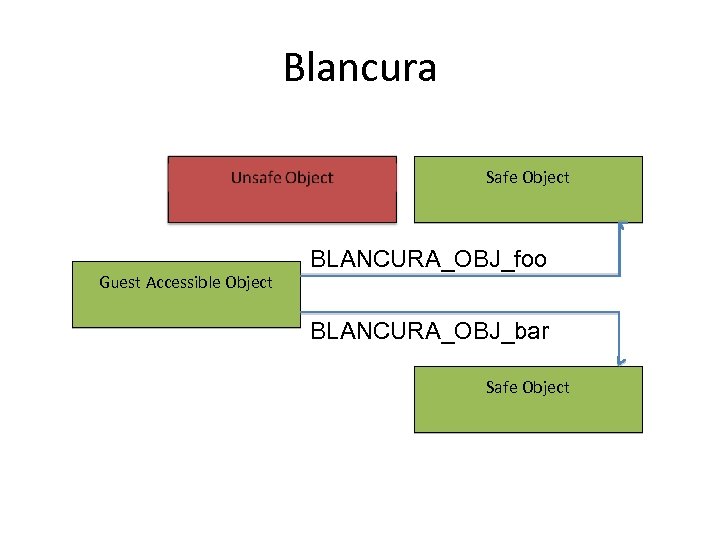
Blancura Safe Object Guest Accessible Object BLANCURA_OBJ_foo BLANCURA_OBJ_bar Safe Object
Conclusion • Heap Graph Analysis can be used to find vulnerabilities in web browsers – And these exploits can be eliminated • Heap Graph Analysis can reveal properties of Java. Script code • Static Containment for Java. Script subsets can be useful and safe

Conclusion • Check out http: //webblaze. cs. berkeley. edu • http: //webblaze. cs. berkeley. edu/2009/heapgraph – Heap Graph Tool and Access Control Prototype for Web. Kit – USENIX Security 2009 Paper
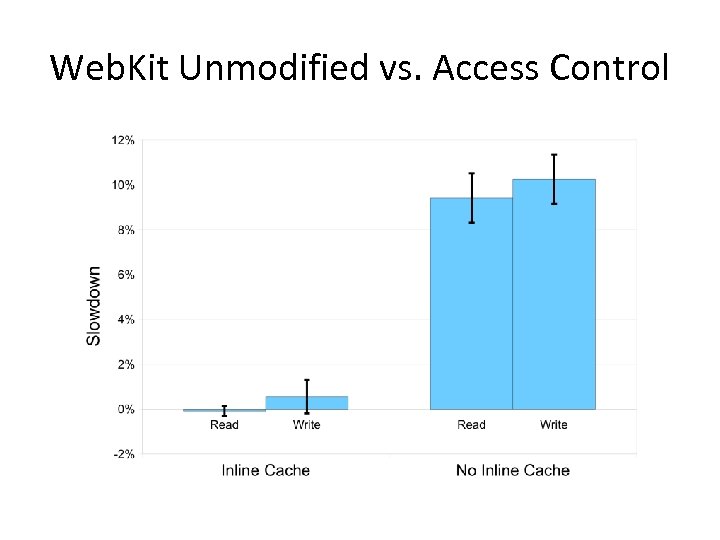
Web. Kit Unmodified vs. Access Control
7a58204dd5a2cc85aeb313f8655cf14c.ppt