8535e2ea51fa03cbef8d3a3afd09b414.ppt
- Количество слайдов: 55
 Jan. 29, 2011 Sean C. Crandall Registered Patent Attorney Jackson Walker L. L. P. scrandall@jw. com • 210. 978. 7714 http: //www. jw. com/scrandall UTSA CITE Entrepreneurship Boot Camp Intellectual Property for Entrepreneurs © 2011 Sean C. Crandall, all rights reserved.
Jan. 29, 2011 Sean C. Crandall Registered Patent Attorney Jackson Walker L. L. P. scrandall@jw. com • 210. 978. 7714 http: //www. jw. com/scrandall UTSA CITE Entrepreneurship Boot Camp Intellectual Property for Entrepreneurs © 2011 Sean C. Crandall, all rights reserved.
 Objectives • You want to make money • You cannot compete with Big Business on a level playing field. • Your IP is probably your only asset of competitive significance – Patents – Copyright – Trademark – Trade Secret
Objectives • You want to make money • You cannot compete with Big Business on a level playing field. • Your IP is probably your only asset of competitive significance – Patents – Copyright – Trademark – Trade Secret
 TRADEMARK © 2011 Sean C. Crandall, all rights reserved.
TRADEMARK © 2011 Sean C. Crandall, all rights reserved.
 Trademark • What is it? – Protection for “source identifiers. ” – Right to exclude others from riding the coattails of your good will. • Duration – Perpetual if: • Continual use • Continues to be a source identifier
Trademark • What is it? – Protection for “source identifiers. ” – Right to exclude others from riding the coattails of your good will. • Duration – Perpetual if: • Continual use • Continues to be a source identifier
 Hypothetical • E incorporates under the name “Seraph Image Manipulation LLC” and receives an assumed name certificate. • B starts selling a software program called “Seraphimage. ” • What result?
Hypothetical • E incorporates under the name “Seraph Image Manipulation LLC” and receives an assumed name certificate. • B starts selling a software program called “Seraphimage. ” • What result?
 Priority • Incorporation and Assumed Name Certificate HAVE NO TRADEMARK VALUE
Priority • Incorporation and Assumed Name Certificate HAVE NO TRADEMARK VALUE
 Priority • Acquiring Priority – Use in commerce – File federal TM application • Including Intent to Use • Knowing junior user loses – Actual notice – Constructive notice
Priority • Acquiring Priority – Use in commerce – File federal TM application • Including Intent to Use • Knowing junior user loses – Actual notice – Constructive notice
 Genericization • Victim of your own success • All of the following used to be trademarks: – – – – zipper thermos escalator linoleum aspirin heroin butterscotch netbook
Genericization • Victim of your own success • All of the following used to be trademarks: – – – – zipper thermos escalator linoleum aspirin heroin butterscotch netbook
 Genericization • Trademarks in Danger: – – – Xerox Kleenex Vaseline Band-Aid Rollerblade • Saved by Timely Obsolescence? – Polaroid – Walkman • If it ceases to identify a source of goods and instead comes to identify the goods themselves, it is no longer a trademark.
Genericization • Trademarks in Danger: – – – Xerox Kleenex Vaseline Band-Aid Rollerblade • Saved by Timely Obsolescence? – Polaroid – Walkman • If it ceases to identify a source of goods and instead comes to identify the goods themselves, it is no longer a trademark.
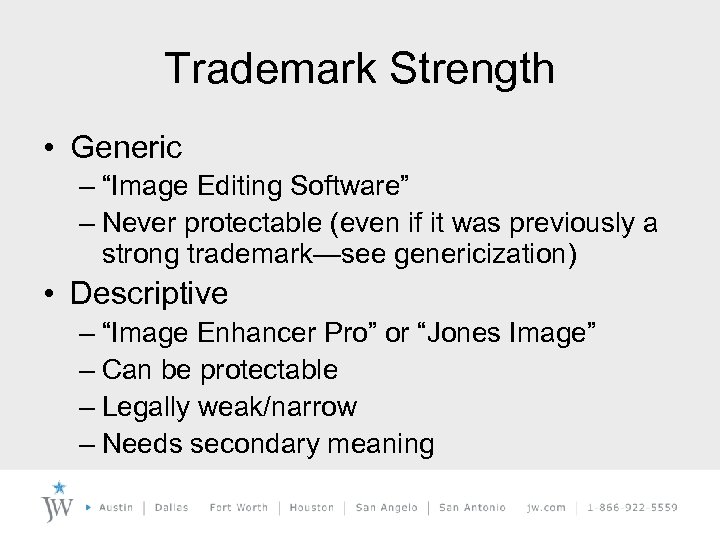 Trademark Strength • Generic – “Image Editing Software” – Never protectable (even if it was previously a strong trademark—see genericization) • Descriptive – “Image Enhancer Pro” or “Jones Image” – Can be protectable – Legally weak/narrow – Needs secondary meaning
Trademark Strength • Generic – “Image Editing Software” – Never protectable (even if it was previously a strong trademark—see genericization) • Descriptive – “Image Enhancer Pro” or “Jones Image” – Can be protectable – Legally weak/narrow – Needs secondary meaning
 Trademark Strength • Suggestive – “Photo Nirvana” – Protectable • Arbitrary and Fanciful – – “Seraphimage” Protectable and legally strong Initially weak from a marketing standpoint With time, can become practically invincible from both legal and marketing standpoint (Kodak, Exxon), except genericization
Trademark Strength • Suggestive – “Photo Nirvana” – Protectable • Arbitrary and Fanciful – – “Seraphimage” Protectable and legally strong Initially weak from a marketing standpoint With time, can become practically invincible from both legal and marketing standpoint (Kodak, Exxon), except genericization
 Infringement • Elements of a Lawsuit – Priority – Protectability – Likelihood of Confusion
Infringement • Elements of a Lawsuit – Priority – Protectability – Likelihood of Confusion
 Infringement • Likelihood of Confusion – Jury Question • Do you find by a preponderance of the evidence that potential customers are likely to confuse “Guardian Angel” with “Seraphimage”?
Infringement • Likelihood of Confusion – Jury Question • Do you find by a preponderance of the evidence that potential customers are likely to confuse “Guardian Angel” with “Seraphimage”?
 Action Steps • Promptly file a federal application – Nationwide priority – Helps make the mark protectable – Trumps state registrations
Action Steps • Promptly file a federal application – Nationwide priority – Helps make the mark protectable – Trumps state registrations
 Action Steps • Investigate junior users before sending nasty letters – If mark is not registered, may have territorial rights. – If junior user has rights, your nasty letter makes his case for him
Action Steps • Investigate junior users before sending nasty letters – If mark is not registered, may have territorial rights. – If junior user has rights, your nasty letter makes his case for him
 COPYRIGHT © 2011 Sean C. Crandall, all rights reserved.
COPYRIGHT © 2011 Sean C. Crandall, all rights reserved.
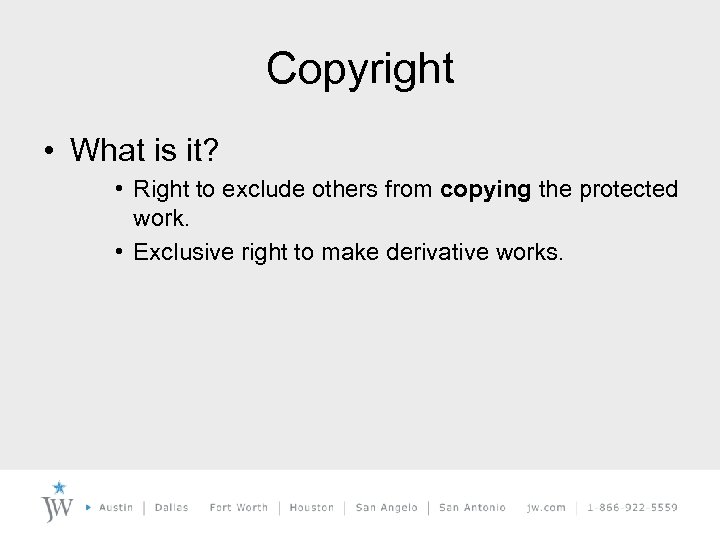 Copyright • What is it? • Right to exclude others from copying the protected work. • Exclusive right to make derivative works.
Copyright • What is it? • Right to exclude others from copying the protected work. • Exclusive right to make derivative works.
 Duration • Life + 70 (individual author) • 95 – 120 years (works for hire) • Created before Jan. 1, 1978 = different rules (very messy). • Published in U. S. before 1923 = public domain.
Duration • Life + 70 (individual author) • 95 – 120 years (works for hire) • Created before Jan. 1, 1978 = different rules (very messy). • Published in U. S. before 1923 = public domain.
 Acquiring a Copyright • When you play God, the result is copyrighted – Except: Ideas, methods, functional products, de minimis creativity Protected Expression Form Creativity Not Protected Ideas and Facts Function and Content Effort and Aggregation
Acquiring a Copyright • When you play God, the result is copyrighted – Except: Ideas, methods, functional products, de minimis creativity Protected Expression Form Creativity Not Protected Ideas and Facts Function and Content Effort and Aggregation
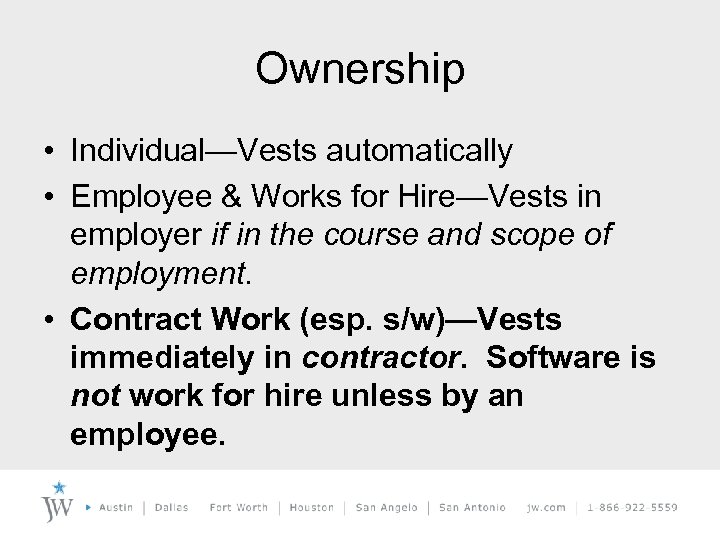 Ownership • Individual—Vests automatically • Employee & Works for Hire—Vests in employer if in the course and scope of employment. • Contract Work (esp. s/w)—Vests immediately in contractor. Software is not work for hire unless by an employee.
Ownership • Individual—Vests automatically • Employee & Works for Hire—Vests in employer if in the course and scope of employment. • Contract Work (esp. s/w)—Vests immediately in contractor. Software is not work for hire unless by an employee.
 Hypothetical • E swears a blood oath to convey copyright to B in the presence of a Catholic Priest, Jewish Rabbi, Mormon Bishop, Protestant Pastor and Baptist Preacher. • Result?
Hypothetical • E swears a blood oath to convey copyright to B in the presence of a Catholic Priest, Jewish Rabbi, Mormon Bishop, Protestant Pastor and Baptist Preacher. • Result?
 Assignments and Licenses • Assignments must be in writing • Exclusive licenses must be in writing • Non-exclusive licenses may be in writing, oral, by course of performance, or implied by the circumstances.
Assignments and Licenses • Assignments must be in writing • Exclusive licenses must be in writing • Non-exclusive licenses may be in writing, oral, by course of performance, or implied by the circumstances.
 Tiers of Protection • Automatic – Attaches at moment of creation • Notice – (c) 2011 Your Name, All rights reserved. • Registration – Online form at http: //www. copyright. gov – $40 filing fee – Easy Peasy! (Except maybe software)
Tiers of Protection • Automatic – Attaches at moment of creation • Notice – (c) 2011 Your Name, All rights reserved. • Registration – Online form at http: //www. copyright. gov – $40 filing fee – Easy Peasy! (Except maybe software)
 Hypothetical • E writes Seraphimage program. • B hires E’s former employee, who copies code (abt. 1%). Total sales = $50 M. • E registers and sues. • Defenses – No knowledge. – Prior non-infringing version successful. – Can’t prove lost sales. • What result?
Hypothetical • E writes Seraphimage program. • B hires E’s former employee, who copies code (abt. 1%). Total sales = $50 M. • E registers and sues. • Defenses – No knowledge. – Prior non-infringing version successful. – Can’t prove lost sales. • What result?
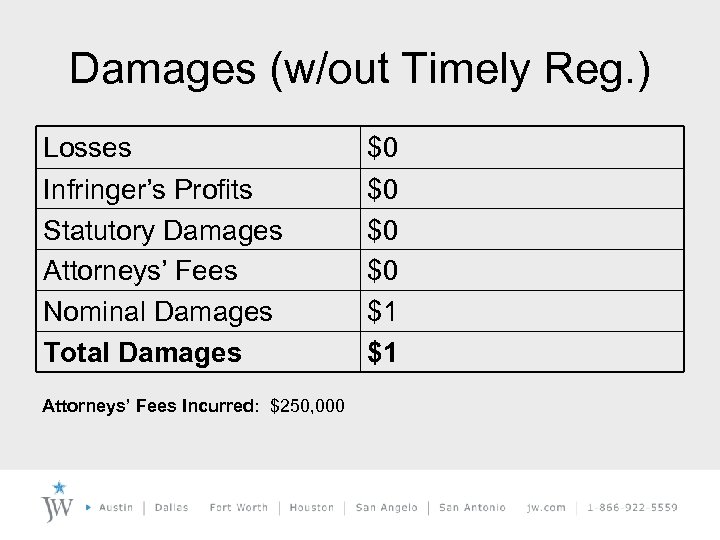 Damages (w/out Timely Reg. ) Losses Infringer’s Profits Statutory Damages Attorneys’ Fees Nominal Damages Total Damages Attorneys’ Fees Incurred: $250, 000 $0 $0 $1 $1
Damages (w/out Timely Reg. ) Losses Infringer’s Profits Statutory Damages Attorneys’ Fees Nominal Damages Total Damages Attorneys’ Fees Incurred: $250, 000 $0 $0 $1 $1
 Hypothetical • Same as before, but E registers one day before B starts infringing.
Hypothetical • Same as before, but E registers one day before B starts infringing.
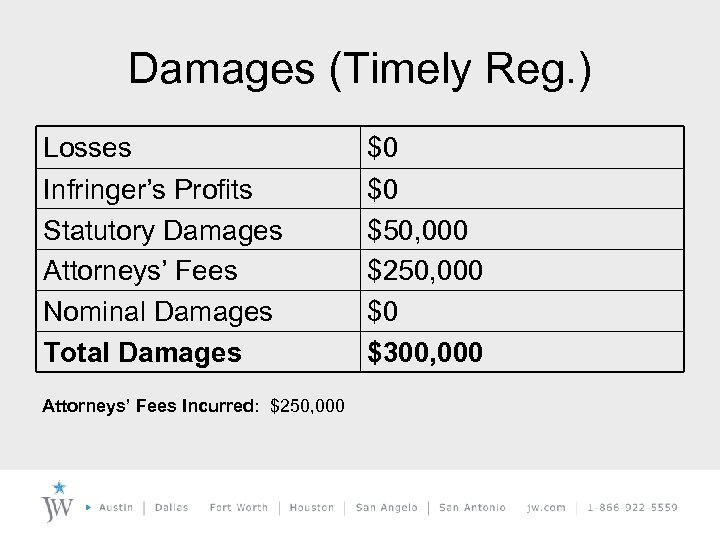 Damages (Timely Reg. ) Losses Infringer’s Profits Statutory Damages Attorneys’ Fees Nominal Damages Total Damages Attorneys’ Fees Incurred: $250, 000 $0 $0 $50, 000 $250, 000 $0 $300, 000
Damages (Timely Reg. ) Losses Infringer’s Profits Statutory Damages Attorneys’ Fees Nominal Damages Total Damages Attorneys’ Fees Incurred: $250, 000 $0 $0 $50, 000 $250, 000 $0 $300, 000
 Infringement • There must be copying. – Substantial similarity + access. • Compare allegedly infringing work to registered work (not necessarily the work copied). • Abstraction – Girl falls in love with a boy who turns out to be a vampire. – A girl named Bella falls in love with a good vampire named Edward, who has sparkly skin, but a boy named Jacob with Indian heritage, who is also a werewolf, is also in love with Bella, and some bad vampires want to kill Bella …
Infringement • There must be copying. – Substantial similarity + access. • Compare allegedly infringing work to registered work (not necessarily the work copied). • Abstraction – Girl falls in love with a boy who turns out to be a vampire. – A girl named Bella falls in love with a good vampire named Edward, who has sparkly skin, but a boy named Jacob with Indian heritage, who is also a werewolf, is also in love with Bella, and some bad vampires want to kill Bella …
 Hypothetical • E requires online activation (stops working after 30 days). • H purchases a legal copy but hacks around activation key. • Has H violated E’s copyright?
Hypothetical • E requires online activation (stops working after 30 days). • H purchases a legal copy but hacks around activation key. • Has H violated E’s copyright?
 DMCA • DMCA § 1201: “No person shall circumvent a technological measure that effectively controls access to a work protected under this title. ” • No copyright infringement is required • Ownership and fair use are not valid defenses – Maybe—see MGE UPS Systems Inc v. GE Consumer and Industrial Inc, et al. , 08 -10521(5 th Cir. Jul. 20, 2010).
DMCA • DMCA § 1201: “No person shall circumvent a technological measure that effectively controls access to a work protected under this title. ” • No copyright infringement is required • Ownership and fair use are not valid defenses – Maybe—see MGE UPS Systems Inc v. GE Consumer and Industrial Inc, et al. , 08 -10521(5 th Cir. Jul. 20, 2010).
 Benefits • Why use “effective technological measures”? – May get attorneys’ fees and statutory damages even without timely registration • Up to $2, 500 per act of circumvention. – Stiff criminal penalties
Benefits • Why use “effective technological measures”? – May get attorneys’ fees and statutory damages even without timely registration • Up to $2, 500 per act of circumvention. – Stiff criminal penalties
 DMCA Exceptions • http: //www. copyright. gov/1201/ • Examples: – Breaking CSS on DVDs for criticism or commentary (notably, not to just watch a DVD that you lawfully own). – Jailbreaking your i. Phone. – Obsolete or damaged dongles.
DMCA Exceptions • http: //www. copyright. gov/1201/ • Examples: – Breaking CSS on DVDs for criticism or commentary (notably, not to just watch a DVD that you lawfully own). – Jailbreaking your i. Phone. – Obsolete or damaged dongles.
 PATENTS © 2011 Sean C. Crandall, all rights reserved.
PATENTS © 2011 Sean C. Crandall, all rights reserved.
 Patents • What are they? – Right to exclude others from making, selling, using, or importing the claimed subject matter. – Does not grant a right to make, use, sell, or import. • Duration – About 20 years
Patents • What are they? – Right to exclude others from making, selling, using, or importing the claimed subject matter. – Does not grant a right to make, use, sell, or import. • Duration – About 20 years
 Subject Matter • Statutory Subject Matter: – Machines – Compositions – Articles of manufacture – Software (sort of? ) • “Everything under the sun made by man” (sort of)
Subject Matter • Statutory Subject Matter: – Machines – Compositions – Articles of manufacture – Software (sort of? ) • “Everything under the sun made by man” (sort of)
 Statutory Requirements • Utility – No perpetual motion machines • Novelty – Identical disclosure – Bar dates • Nonobviousness – PHOSITA has all prior art in front of him and has ordinary ingenuity
Statutory Requirements • Utility – No perpetual motion machines • Novelty – Identical disclosure – Bar dates • Nonobviousness – PHOSITA has all prior art in front of him and has ordinary ingenuity
 Patent Claims • Invention: – – A B C D • Subtract Prior Art: -AB • Subtract Obvious Improvements: -ABC • Patentable Claim: ABCD – Note that ABC is a better claim if you can get it. • If your attorney leaves “killer features” out of some of your claims, that may be a good thing.
Patent Claims • Invention: – – A B C D • Subtract Prior Art: -AB • Subtract Obvious Improvements: -ABC • Patentable Claim: ABCD – Note that ABC is a better claim if you can get it. • If your attorney leaves “killer features” out of some of your claims, that may be a good thing.
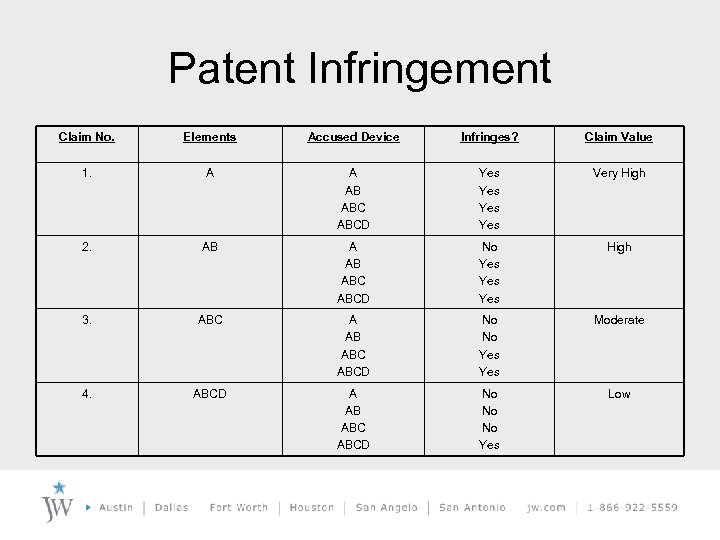 Patent Infringement Claim No. Elements Accused Device Infringes? Claim Value 1. A A AB ABCD Yes Yes Very High 2. AB ABC ABCD No Yes Yes High 3. ABC A AB ABCD No No Yes Moderate 4. ABCD A AB ABCD No No No Yes Low
Patent Infringement Claim No. Elements Accused Device Infringes? Claim Value 1. A A AB ABCD Yes Yes Very High 2. AB ABC ABCD No Yes Yes High 3. ABC A AB ABCD No No Yes Moderate 4. ABCD A AB ABCD No No No Yes Low
 Business Methods and Software May be patentable
Business Methods and Software May be patentable
 Bilski I • Machine or Transformation Test – Tied to a “particular machine” • Need guidance on whether a general-purpose computer is a “particular machine” – Transforms matter • Transforming data that directly represent matter may be sufficient • Mo. T is absolutely not the sole test for method claim eligibility. But it is the only test that matters.
Bilski I • Machine or Transformation Test – Tied to a “particular machine” • Need guidance on whether a general-purpose computer is a “particular machine” – Transforms matter • Transforming data that directly represent matter may be sufficient • Mo. T is absolutely not the sole test for method claim eligibility. But it is the only test that matters.
 Avoid Subject Matter Problems • Designing Around Bilski – Tie in hardware where possible (“A method for removing red eye from a photograph comprising … receiving a digital photograph from a digital camera …. ”) – Use Beauregard claims (“…a tangible storage medium having stored thereon executable software instructions, the software instructions configured to instruct the processor to …. ”)
Avoid Subject Matter Problems • Designing Around Bilski – Tie in hardware where possible (“A method for removing red eye from a photograph comprising … receiving a digital photograph from a digital camera …. ”) – Use Beauregard claims (“…a tangible storage medium having stored thereon executable software instructions, the software instructions configured to instruct the processor to …. ”)
 Patent Drafting • Get a registered patent attorney • Do not ever, under any circumstances, try to write a patent yourself. • No, not even if you’re really smart. • Your tax attorney can’t write a patent for you. You need a registered patent attorney.
Patent Drafting • Get a registered patent attorney • Do not ever, under any circumstances, try to write a patent yourself. • No, not even if you’re really smart. • Your tax attorney can’t write a patent for you. You need a registered patent attorney.
 Hypothetical • E invents a new image editing algorithm and incorporates into Seraphimage. • Academic paper published Sep. 11, 2010. • Commercial product ready in Feb. 2012. • E applies for a patent application Feb. 1, 2012. • What result?
Hypothetical • E invents a new image editing algorithm and incorporates into Seraphimage. • Academic paper published Sep. 11, 2010. • Commercial product ready in Feb. 2012. • E applies for a patent application Feb. 1, 2012. • What result?
 Bar Dates • What is It? – Date by which you must file a patent application, or lose your right to get a patent • Bar Dates Events Include: – Sale of a product that embodies the invention you want to patent – Offer for sale – Publication including an enabling disclosure – Non-experimental public use or disclosure
Bar Dates • What is It? – Date by which you must file a patent application, or lose your right to get a patent • Bar Dates Events Include: – Sale of a product that embodies the invention you want to patent – Offer for sale – Publication including an enabling disclosure – Non-experimental public use or disclosure
 Bar Date • Calculating Bar Dates – U. S. has 1 year grace period • Barring event happens on 1/20/11. Bar date is 1/29/12. You must file your patent application by Jan. 29, 2012, or your invention is barred. – Most foreign countries have no grace period • Barring event happens on 1/29/11. You must file by Jan. 29, 2011, or you cannot get a patent in “absolute novelty” countries.
Bar Date • Calculating Bar Dates – U. S. has 1 year grace period • Barring event happens on 1/20/11. Bar date is 1/29/12. You must file your patent application by Jan. 29, 2012, or your invention is barred. – Most foreign countries have no grace period • Barring event happens on 1/29/11. You must file by Jan. 29, 2011, or you cannot get a patent in “absolute novelty” countries.
 Excuses • Events That Will Not Excuse Missing a Bar Date: – I didn’t know about the bar date. – The offer for sale was rejected. – The offer for sale was illegal. – My spouse and children were killed by a drunk driver the week before the bar date. – Sapient aliens made first contact on the bar date and the entire earth stood still.
Excuses • Events That Will Not Excuse Missing a Bar Date: – I didn’t know about the bar date. – The offer for sale was rejected. – The offer for sale was illegal. – My spouse and children were killed by a drunk driver the week before the bar date. – Sapient aliens made first contact on the bar date and the entire earth stood still.
 Excuses • Events That Will Excuse Missing a Bar Date: – Nothing.
Excuses • Events That Will Excuse Missing a Bar Date: – Nothing.
 TRADE SECRET © 2011 Sean C. Crandall, all rights reserved.
TRADE SECRET © 2011 Sean C. Crandall, all rights reserved.
 Trade Secret • Elements – It’s a SECRET. – Confers a competitive advantage – Reasonable efforts to keep it SECRET • Examples: – Formula for Coca-Cola – The Colonel’s 11 herbs and spices – Your source tree
Trade Secret • Elements – It’s a SECRET. – Confers a competitive advantage – Reasonable efforts to keep it SECRET • Examples: – Formula for Coca-Cola – The Colonel’s 11 herbs and spices – Your source tree
 Trade Secret • Protecting a Trade Secret – No registration – KEEP IT A SECRET! – Non-disclosure agreements (get an attorney) – Employee confidentiality agreements (the more draconian, the better) – Posted notices • Duration – As long as you KEEP IT SECRET
Trade Secret • Protecting a Trade Secret – No registration – KEEP IT A SECRET! – Non-disclosure agreements (get an attorney) – Employee confidentiality agreements (the more draconian, the better) – Posted notices • Duration – As long as you KEEP IT SECRET
 Security • Think ahead – Which story do you want the jury to hear? • “There were hundreds of copies of the process just lying around everywhere. I didn’t even realize it was considered secret. ” vs. • “After agreeing to the $10, 000 penalty for disclosing the secret process, I disabled the armed guard with a drugged dart. I had to wear an insulating body suit to defeat the heat sensors, then climb up into the air duct. Getting around the laser grid took some time, but the real problem was the motion sensors. I spent hours getting across the room. Since the safe was impossible to crack, I had to bug the CEO’s bedroom and listen to him talk in his sleep for months. Then I had to painstakingly copy the process by hand, since it was on blue non-copy paper. Once I had my copy, I had to carefully replace the wax seal and mark it with the duplicate signet ring I had carefully constructed from the putty impression of the real signet ring I’d gotten when I …”
Security • Think ahead – Which story do you want the jury to hear? • “There were hundreds of copies of the process just lying around everywhere. I didn’t even realize it was considered secret. ” vs. • “After agreeing to the $10, 000 penalty for disclosing the secret process, I disabled the armed guard with a drugged dart. I had to wear an insulating body suit to defeat the heat sensors, then climb up into the air duct. Getting around the laser grid took some time, but the real problem was the motion sensors. I spent hours getting across the room. Since the safe was impossible to crack, I had to bug the CEO’s bedroom and listen to him talk in his sleep for months. Then I had to painstakingly copy the process by hand, since it was on blue non-copy paper. Once I had my copy, I had to carefully replace the wax seal and mark it with the duplicate signet ring I had carefully constructed from the putty impression of the real signet ring I’d gotten when I …”
 Hypothetical • E develops red eye removal algorithm. E hires 10 programmers. • Signed confidentiality agreements. • Copies of process individually water marked. • Policy is to keep process in locked drawers. • Flow chart posted by receptionists desk. • Weekly meetings to discuss security program. • What result?
Hypothetical • E develops red eye removal algorithm. E hires 10 programmers. • Signed confidentiality agreements. • Copies of process individually water marked. • Policy is to keep process in locked drawers. • Flow chart posted by receptionists desk. • Weekly meetings to discuss security program. • What result?
 Security • Designing a Security Program – Put Everyone on Notice – Signed Confidentiality Agreements – Restrict Access – Log Access – Termination Procedures – Non-compete Agreements – Periodic Audits
Security • Designing a Security Program – Put Everyone on Notice – Signed Confidentiality Agreements – Restrict Access – Log Access – Termination Procedures – Non-compete Agreements – Periodic Audits
 Questions? © 2011 Sean C. Crandall, all rights reserved.
Questions? © 2011 Sean C. Crandall, all rights reserved.
 Support Materials • Protecting Software: http: //www. jw. com/site/jsp/publicationinfo. jsp? id=14 09 • IP Basics: http: //www. jw. com/site/jsp/publicationinfo. jsp? id=35 1 • A Practical Guide to the GNU GPL: • http: //www. jw. com/site/jsp/publicationinfo. jsp? id=14 © 2011 Sean C. Crandall, all rights reserved. 53
Support Materials • Protecting Software: http: //www. jw. com/site/jsp/publicationinfo. jsp? id=14 09 • IP Basics: http: //www. jw. com/site/jsp/publicationinfo. jsp? id=35 1 • A Practical Guide to the GNU GPL: • http: //www. jw. com/site/jsp/publicationinfo. jsp? id=14 © 2011 Sean C. Crandall, all rights reserved. 53


