1ffb1a869d0087e84f2faa60e1d00b45.ppt
- Количество слайдов: 24
 Jack-PC Security Rev A - 0206 Important!! Under NDA - Chip PC Proprietary and Confidential Information *CDC 02264*
Jack-PC Security Rev A - 0206 Important!! Under NDA - Chip PC Proprietary and Confidential Information *CDC 02264*
 Claim: “Jack PC is the most secured desktop available today. ” This presentation is all about proving this strong claim… 2
Claim: “Jack PC is the most secured desktop available today. ” This presentation is all about proving this strong claim… 2
 What makes for the most secure desktop? 1) Strong Physical security 2) Strong User Authentication 3) Strong Device Authentication 4) Strong Peripherals Authentication, tracking and logging 5) Strong Management security 6) Strong Image security 7) Chip PC high security environment, technologies and capabilities 3
What makes for the most secure desktop? 1) Strong Physical security 2) Strong User Authentication 3) Strong Device Authentication 4) Strong Peripherals Authentication, tracking and logging 5) Strong Management security 6) Strong Image security 7) Chip PC high security environment, technologies and capabilities 3
 Strongest Physical Device Security Concept: Physically securing the device and its cables. How? • • Special built-in mechanical lock • No exposed LAN jack / wiring • Strong metal anti-tampering structure • POE – No exposed power source • 4 No exposed components (wall mounting) No removable mass-storage (soldered DOC)
Strongest Physical Device Security Concept: Physically securing the device and its cables. How? • • Special built-in mechanical lock • No exposed LAN jack / wiring • Strong metal anti-tampering structure • POE – No exposed power source • 4 No exposed components (wall mounting) No removable mass-storage (soldered DOC)
 Jack PC Removed from Locking in Housing with Extraction Tool 5
Jack PC Removed from Locking in Housing with Extraction Tool 5
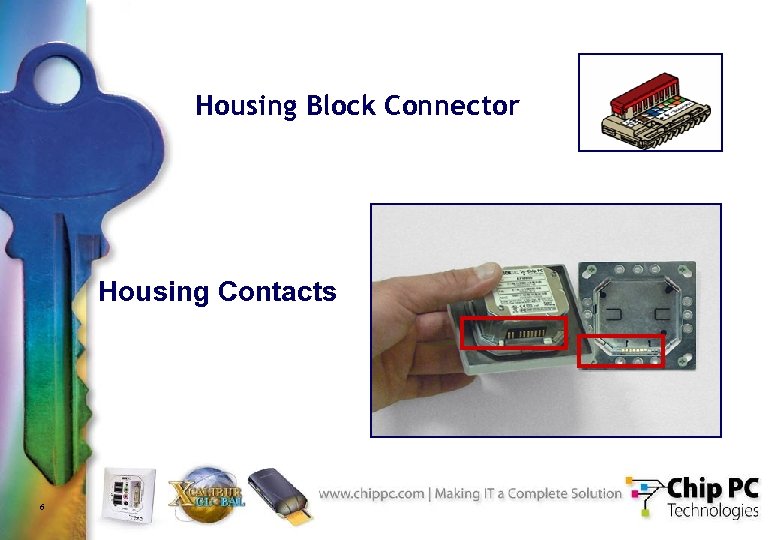 Housing Block Connector Housing Contacts 6
Housing Block Connector Housing Contacts 6
 Strongest User Authentication Concept: Identify device physical location. How? • • Support for most PC/SC PKI Smart-cards using external USB reader • Support for Biometrics authentication • Passed-through user authentication from XG server • 7 Patented local log-in authenticated against AD (similar to PC domain log-in) Fully configurable Kerberos, NTLM and other authentications.
Strongest User Authentication Concept: Identify device physical location. How? • • Support for most PC/SC PKI Smart-cards using external USB reader • Support for Biometrics authentication • Passed-through user authentication from XG server • 7 Patented local log-in authenticated against AD (similar to PC domain log-in) Fully configurable Kerberos, NTLM and other authentications.
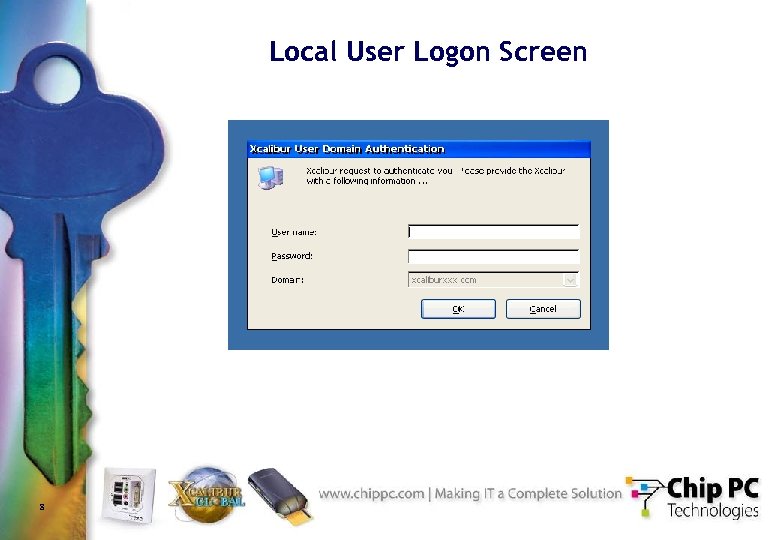 Local User Logon Screen 8
Local User Logon Screen 8
 Strongest Device Authentication Concept: Reliably identify the device. How? • • Soldered components with OTP (One Time Programming) chips • Reliance on properties that cannot be cloned / modified. • 9 Patented technology to enable strong matching of device unique properties with device identity Two side authentication device Management system
Strongest Device Authentication Concept: Reliably identify the device. How? • • Soldered components with OTP (One Time Programming) chips • Reliance on properties that cannot be cloned / modified. • 9 Patented technology to enable strong matching of device unique properties with device identity Two side authentication device Management system
 Strongest Peripherals Authentication Concept: Reliably control the connected peripherals How? • • Full peripherals control through XG policies based on device or user profile • Detection / logging of all peripherals connection / disconnection events • 10 Strongest USB usage control using patented detection and power signatures Option to implement keyboard authentication scheme
Strongest Peripherals Authentication Concept: Reliably control the connected peripherals How? • • Full peripherals control through XG policies based on device or user profile • Detection / logging of all peripherals connection / disconnection events • 10 Strongest USB usage control using patented detection and power signatures Option to implement keyboard authentication scheme
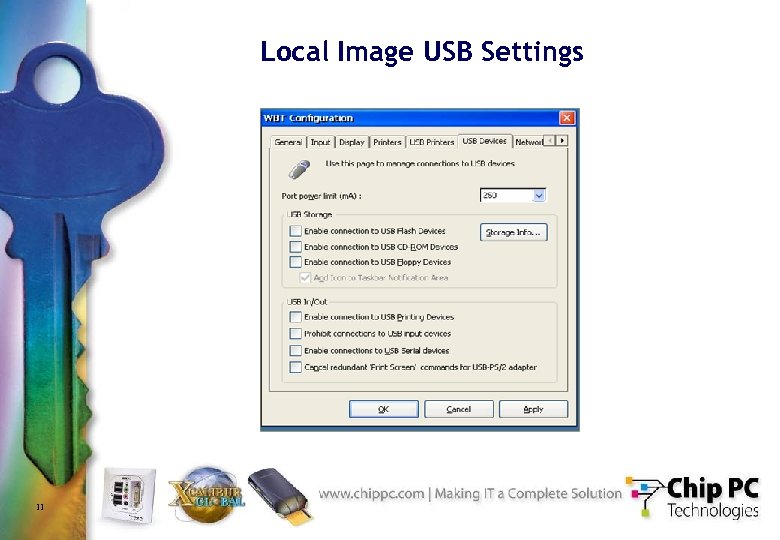 Local Image USB Settings 11
Local Image USB Settings 11
 Strongest Management Security Concept: Securing device management functions How? • • Full Multi-level administrative rights, delegation • Management protocols uses selectable highencryption, compression and port settings (non-SNMP) • Single Sign On using XG secured infrastructure • 12 Managed by XG – AD policies, leveraging Windows Security Scheme Security desk, logging and events
Strongest Management Security Concept: Securing device management functions How? • • Full Multi-level administrative rights, delegation • Management protocols uses selectable highencryption, compression and port settings (non-SNMP) • Single Sign On using XG secured infrastructure • 12 Managed by XG – AD policies, leveraging Windows Security Scheme Security desk, logging and events
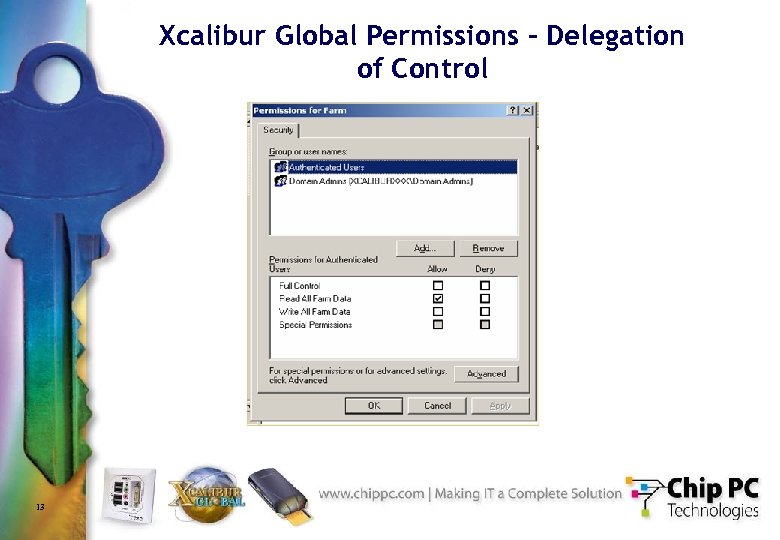 Xcalibur Global Permissions – Delegation of Control 13
Xcalibur Global Permissions – Delegation of Control 13
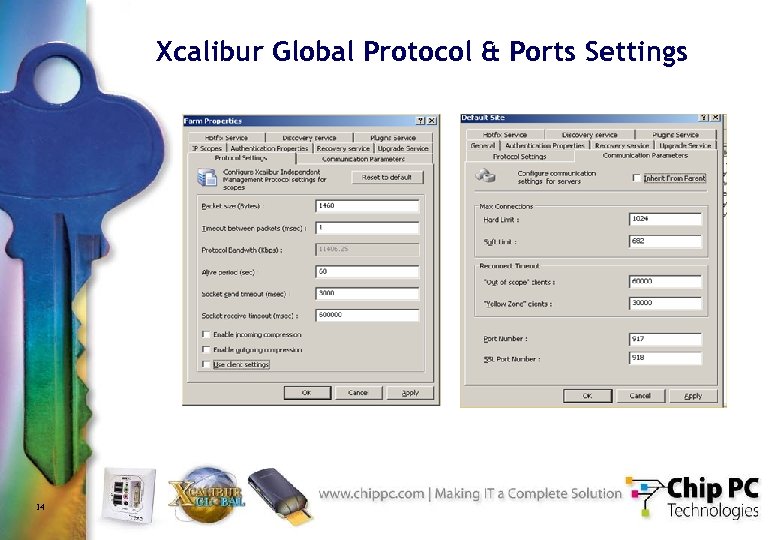 Xcalibur Global Protocol & Ports Settings 14
Xcalibur Global Protocol & Ports Settings 14
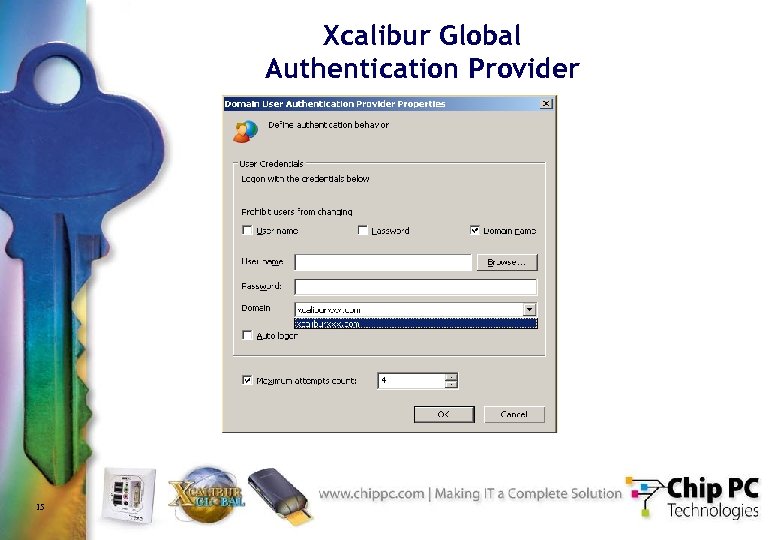 Xcalibur Global Authentication Provider 15
Xcalibur Global Authentication Provider 15
 Strongest Image Security Concept: Securing device management functions How? • • Immunity to viruses, worms and other malicious code • No security patches, vulnerabilities and anti-virus needed - EVER • Modular image does not require often re-imaging • No BIOS, no BIOS vulnerabilities • Truly stateless client design – no user information remains • 16 Highly secured patented software deployment mechanisms using signed XPIs Wide set of local VPNs
Strongest Image Security Concept: Securing device management functions How? • • Immunity to viruses, worms and other malicious code • No security patches, vulnerabilities and anti-virus needed - EVER • Modular image does not require often re-imaging • No BIOS, no BIOS vulnerabilities • Truly stateless client design – no user information remains • 16 Highly secured patented software deployment mechanisms using signed XPIs Wide set of local VPNs
 Strongest Image Security • • User can never access system files or settings • XP desktop without desktop vulnerabilities • Relies on Windows CE Kernel enhance and secured by Chip PC. Full access to source-code • Local user settings can be defined on per-function level. Only required settings are open • Enhanced and secured local IE browser with manageable kiosk mode, downloads and cookies • Secured VNC remote shadowing • 17 Encrypted image for each unique device Dynamic (per-user) software deployment enables on-the-fly role based device loading upon user log-in
Strongest Image Security • • User can never access system files or settings • XP desktop without desktop vulnerabilities • Relies on Windows CE Kernel enhance and secured by Chip PC. Full access to source-code • Local user settings can be defined on per-function level. Only required settings are open • Enhanced and secured local IE browser with manageable kiosk mode, downloads and cookies • Secured VNC remote shadowing • 17 Encrypted image for each unique device Dynamic (per-user) software deployment enables on-the-fly role based device loading upon user log-in
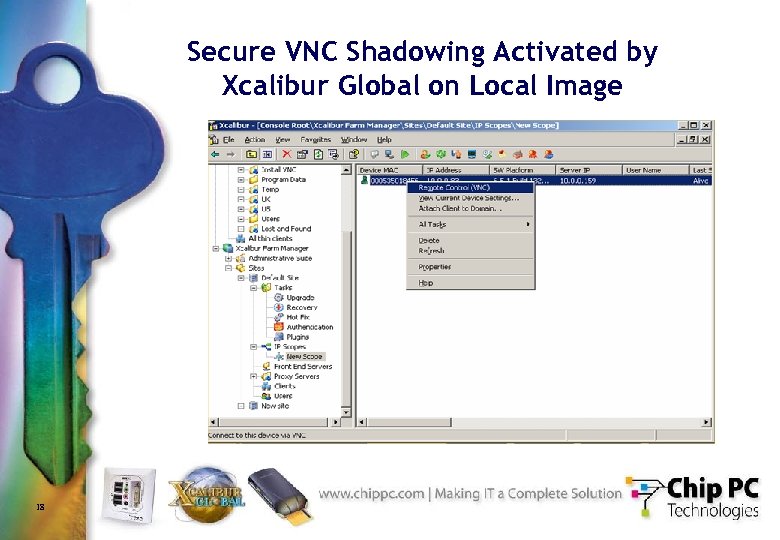 Secure VNC Shadowing Activated by Xcalibur Global on Local Image 18
Secure VNC Shadowing Activated by Xcalibur Global on Local Image 18
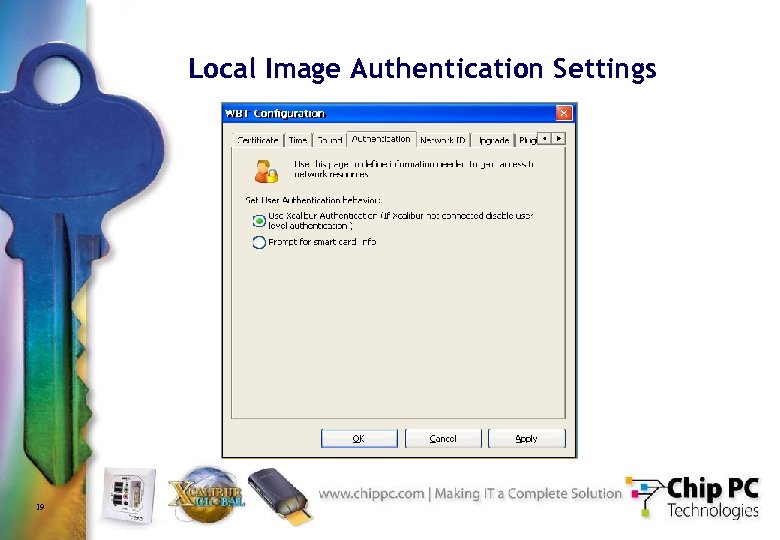 Local Image Authentication Settings 19
Local Image Authentication Settings 19
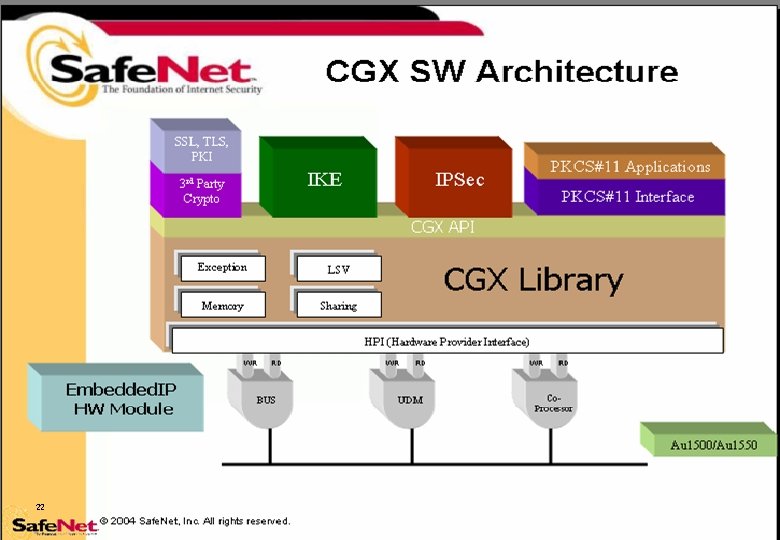
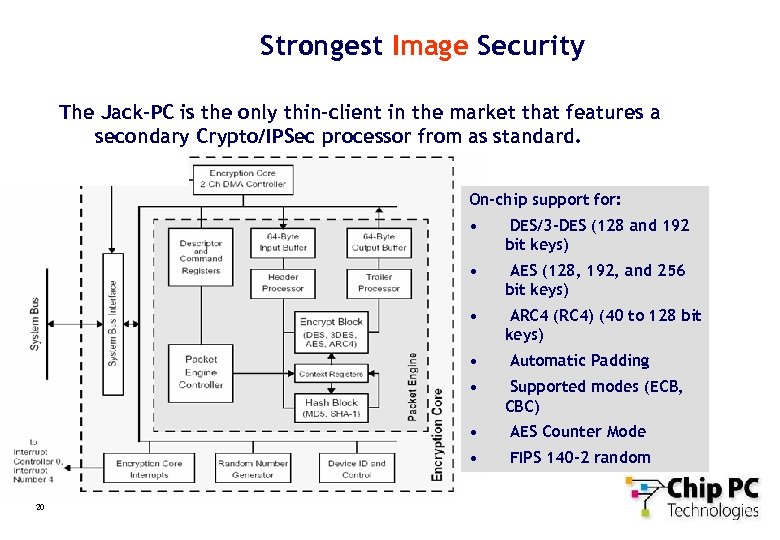 Strongest Image Security The Jack-PC is the only thin-client in the market that features a secondary Crypto/IPSec processor from as standard. On-chip support for: • DES/3 -DES (128 and 192 bit keys) • AES (128, 192, and 256 bit keys) • ARC 4 (RC 4) (40 to 128 bit keys) • • Automatic Padding Supported modes (ECB, CBC) • • 20 AES Counter Mode FIPS 140 -2 random
Strongest Image Security The Jack-PC is the only thin-client in the market that features a secondary Crypto/IPSec processor from as standard. On-chip support for: • DES/3 -DES (128 and 192 bit keys) • AES (128, 192, and 256 bit keys) • ARC 4 (RC 4) (40 to 128 bit keys) • • Automatic Padding Supported modes (ECB, CBC) • • 20 AES Counter Mode FIPS 140 -2 random
 21
21
 22
22
 Additional Security Products • • Fiber-optic based thin-clients • Custom images and plug-ins • Second signature by customer • Security audits preparations, analysis, testing, consultancy • Hybrid simulation lab for testing and simulations • Security experts on staff • Custom smart-cards and applications • 23 Special TEMPEST / MIL-STD thin-client products Optically isolated KVMs, Twin-clients
Additional Security Products • • Fiber-optic based thin-clients • Custom images and plug-ins • Second signature by customer • Security audits preparations, analysis, testing, consultancy • Hybrid simulation lab for testing and simulations • Security experts on staff • Custom smart-cards and applications • 23 Special TEMPEST / MIL-STD thin-client products Optically isolated KVMs, Twin-clients
 Chip PC Security Environment • • All manufacturing is done in high-security MIL-STD facilities • Common-Criteria to level 6 with similar products • Access to MS and Citrix source-code • Secured to top-secret development and production environments • Contingency and disaster recovery facilities (3 sites) • World’s highest security organizations are relying on Chip PC products • 24 Operate as a subsidiary of Israel’s largest defense conglomerate Internal security and procedures can be audited by customers
Chip PC Security Environment • • All manufacturing is done in high-security MIL-STD facilities • Common-Criteria to level 6 with similar products • Access to MS and Citrix source-code • Secured to top-secret development and production environments • Contingency and disaster recovery facilities (3 sites) • World’s highest security organizations are relying on Chip PC products • 24 Operate as a subsidiary of Israel’s largest defense conglomerate Internal security and procedures can be audited by customers


