825e397d33b454688cfb9f04606264ba.ppt
- Количество слайдов: 29
 ITIS 3200: Introduction to Information Security and Privacy Dr. Weichao Wang
ITIS 3200: Introduction to Information Security and Privacy Dr. Weichao Wang
 • Chap 7: Hybrid Policies – Chinese Wall – RBAC (Role based access control) – ORCON (Originator controlled) – Clinical Systems Model 2
• Chap 7: Hybrid Policies – Chinese Wall – RBAC (Role based access control) – ORCON (Originator controlled) – Clinical Systems Model 2
 Chinese Wall Model Try to handle both confidentiality and integrity Problem: – Tony advises American Bank about investments – He is asked to advise Toyland Bank about investments • Conflict of interest to accept, because his advice for either bank would affect his advice to the other bank – Something to think about: advertise for both Coke and Pepsi, and real estate broker 3
Chinese Wall Model Try to handle both confidentiality and integrity Problem: – Tony advises American Bank about investments – He is asked to advise Toyland Bank about investments • Conflict of interest to accept, because his advice for either bank would affect his advice to the other bank – Something to think about: advertise for both Coke and Pepsi, and real estate broker 3
 Organization • Organize entities into “conflict of interest” classes • Control subject accesses to each class • Control writing to all classes to ensure information is not passed along in violation of rules • Allow sanitized data to be viewed by everyone 4
Organization • Organize entities into “conflict of interest” classes • Control subject accesses to each class • Control writing to all classes to ensure information is not passed along in violation of rules • Allow sanitized data to be viewed by everyone 4
 Definitions • Objects: items of information related to a company • Company dataset (CD): contains objects related to a single company – CD(O): the data set that contains O • Conflict of interest class (COI): contains datasets of companies in competition – COI(O): the COI class that contains O – Assume: each object belongs to exactly one COI class 5
Definitions • Objects: items of information related to a company • Company dataset (CD): contains objects related to a single company – CD(O): the data set that contains O • Conflict of interest class (COI): contains datasets of companies in competition – COI(O): the COI class that contains O – Assume: each object belongs to exactly one COI class 5
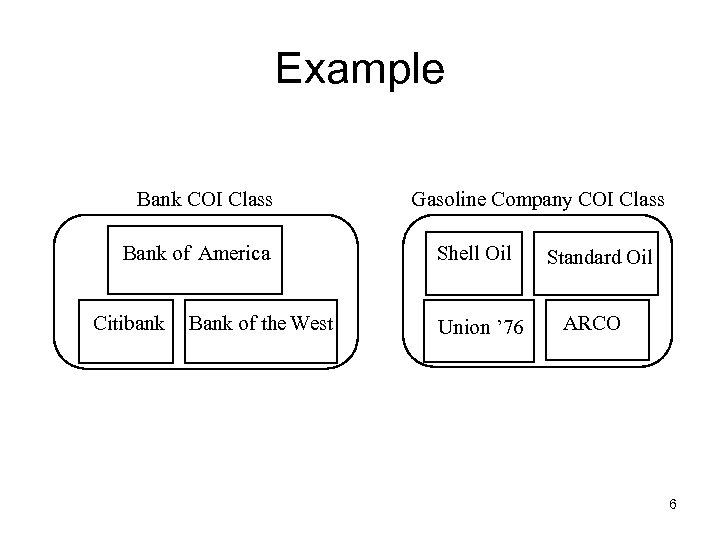 Example Bank COI Class Bank of America Citibank Bank of the West Gasoline Company COI Class Shell Oil Union ’ 76 Standard Oil ARCO 6
Example Bank COI Class Bank of America Citibank Bank of the West Gasoline Company COI Class Shell Oil Union ’ 76 Standard Oil ARCO 6
 Temporal Element • There is a temporal issue we have to consider: the information now may have impact for a following period of time • If Anthony reads any CD in a COI, he should not read another CD in that COI – Possible that information learned earlier may allow him to make decisions later – Let PR(S) be set of objects that S has already read (this keeps a record of history) – In real life, the temporal element usually has an expiration period: otherwise --7
Temporal Element • There is a temporal issue we have to consider: the information now may have impact for a following period of time • If Anthony reads any CD in a COI, he should not read another CD in that COI – Possible that information learned earlier may allow him to make decisions later – Let PR(S) be set of objects that S has already read (this keeps a record of history) – In real life, the temporal element usually has an expiration period: otherwise --7
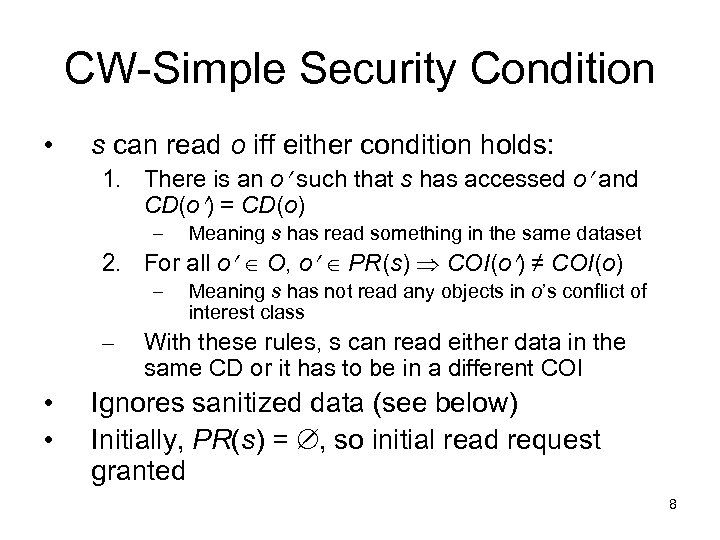 CW-Simple Security Condition • s can read o iff either condition holds: 1. There is an o such that s has accessed o and CD(o ) = CD(o) – Meaning s has read something in the same dataset 2. For all o O, o PR(s) COI(o ) ≠ COI(o) – – • • Meaning s has not read any objects in o’s conflict of interest class With these rules, s can read either data in the same CD or it has to be in a different COI Ignores sanitized data (see below) Initially, PR(s) = , so initial read request granted 8
CW-Simple Security Condition • s can read o iff either condition holds: 1. There is an o such that s has accessed o and CD(o ) = CD(o) – Meaning s has read something in the same dataset 2. For all o O, o PR(s) COI(o ) ≠ COI(o) – – • • Meaning s has not read any objects in o’s conflict of interest class With these rules, s can read either data in the same CD or it has to be in a different COI Ignores sanitized data (see below) Initially, PR(s) = , so initial read request granted 8
 • Some derived results – If s has read something in a COI, the only other data that she can read in that COI is from the same CD – If a COI contains n CD, we need to have at least n people if we want to make sure every CD can be read by someone 9
• Some derived results – If s has read something in a COI, the only other data that she can read in that COI is from the same CD – If a COI contains n CD, we need to have at least n people if we want to make sure every CD can be read by someone 9
 Sanitization • Public information may belong to a CD – – – As is publicly available, no conflicts of interest arise So, should not affect ability of analysts to read Typically, all sensitive data removed from such information before it is released publicly (called sanitization) • Add third condition to CW-Simple Security Condition: 3. o is a sanitized object 10
Sanitization • Public information may belong to a CD – – – As is publicly available, no conflicts of interest arise So, should not affect ability of analysts to read Typically, all sensitive data removed from such information before it is released publicly (called sanitization) • Add third condition to CW-Simple Security Condition: 3. o is a sanitized object 10
 Prevent Disclosure through Writing • • Anthony, Susan work in same trading house Anthony can read Bank 1’s CD, Gas 1’s CD Susan can read Bank 2’s CD, Gas 1’s CD If Anthony could write to Gas 1’s CD, Susan can read it – Anthony read from Bank 1’s CD, write to Gas 1’s CD, now Susan can read it – Hence, indirectly, she can read information from Bank 1’s CD, a clear conflict of interest 11
Prevent Disclosure through Writing • • Anthony, Susan work in same trading house Anthony can read Bank 1’s CD, Gas 1’s CD Susan can read Bank 2’s CD, Gas 1’s CD If Anthony could write to Gas 1’s CD, Susan can read it – Anthony read from Bank 1’s CD, write to Gas 1’s CD, now Susan can read it – Hence, indirectly, she can read information from Bank 1’s CD, a clear conflict of interest 11
 CW-*-Property • s can write to o iff both of the following hold: 1. The CW-simple security condition permits s to read o; and 2. For all unsanitized objects o , if s can read o , then CD(o ) = CD(o) • What is implied: if s can write to an object, then all the (unsanitized) objects it can read are in the same dataset 12
CW-*-Property • s can write to o iff both of the following hold: 1. The CW-simple security condition permits s to read o; and 2. For all unsanitized objects o , if s can read o , then CD(o ) = CD(o) • What is implied: if s can write to an object, then all the (unsanitized) objects it can read are in the same dataset 12
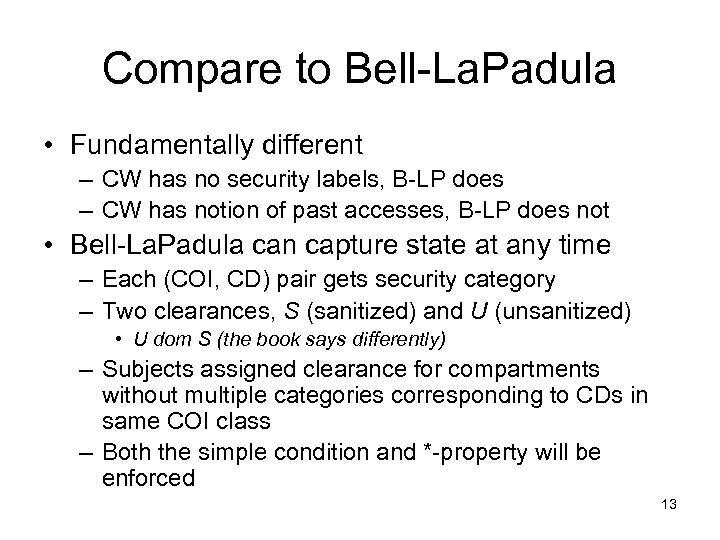 Compare to Bell-La. Padula • Fundamentally different – CW has no security labels, B-LP does – CW has notion of past accesses, B-LP does not • Bell-La. Padula can capture state at any time – Each (COI, CD) pair gets security category – Two clearances, S (sanitized) and U (unsanitized) • U dom S (the book says differently) – Subjects assigned clearance for compartments without multiple categories corresponding to CDs in same COI class – Both the simple condition and *-property will be enforced 13
Compare to Bell-La. Padula • Fundamentally different – CW has no security labels, B-LP does – CW has notion of past accesses, B-LP does not • Bell-La. Padula can capture state at any time – Each (COI, CD) pair gets security category – Two clearances, S (sanitized) and U (unsanitized) • U dom S (the book says differently) – Subjects assigned clearance for compartments without multiple categories corresponding to CDs in same COI class – Both the simple condition and *-property will be enforced 13
 Compare to Bell-La. Padula • Bell-La. Padula cannot track changes over time – Susan becomes ill, Anna needs to take over • C-W history lets Anna know if she can • No way for Bell-La. Padula to capture this • Access constraints change over time – Initially, subjects in C-W can read any object – Bell-La. Padula constrains set of objects that a subject can access • Can’t clear all subjects for all categories, because this violates CW-simple security condition 14
Compare to Bell-La. Padula • Bell-La. Padula cannot track changes over time – Susan becomes ill, Anna needs to take over • C-W history lets Anna know if she can • No way for Bell-La. Padula to capture this • Access constraints change over time – Initially, subjects in C-W can read any object – Bell-La. Padula constrains set of objects that a subject can access • Can’t clear all subjects for all categories, because this violates CW-simple security condition 14
 15
15
 RBAC • Access depends on function, not identity – Example: • Allison, bookkeeper for Math Dept, has access to financial records. • She leaves, so she does not have access • Betty is hired as the new bookkeeper, so she now has access to those records – The role of “bookkeeper” dictates access, not the identity of the individual. 16
RBAC • Access depends on function, not identity – Example: • Allison, bookkeeper for Math Dept, has access to financial records. • She leaves, so she does not have access • Betty is hired as the new bookkeeper, so she now has access to those records – The role of “bookkeeper” dictates access, not the identity of the individual. 16
 Definitions • Role r : collection of job functions – trans(r): set of authorized transactions for r • Active role of subject s : the role that subject s is currently performing – actr(s) • Authorized roles of a subject s : set of roles s is authorized to assume – authr(s) • canexec (s, t) iff subject s can execute transaction t at current time 17
Definitions • Role r : collection of job functions – trans(r): set of authorized transactions for r • Active role of subject s : the role that subject s is currently performing – actr(s) • Authorized roles of a subject s : set of roles s is authorized to assume – authr(s) • canexec (s, t) iff subject s can execute transaction t at current time 17
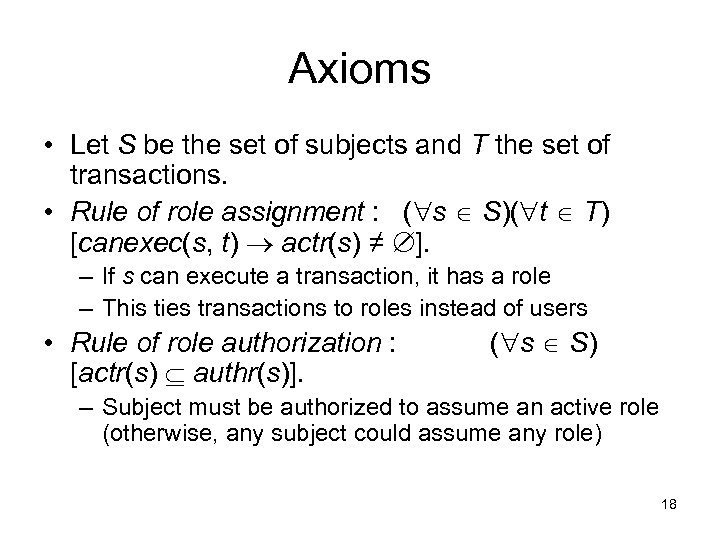 Axioms • Let S be the set of subjects and T the set of transactions. • Rule of role assignment : ( s S)( t T) [canexec(s, t) actr(s) ≠ ]. – If s can execute a transaction, it has a role – This ties transactions to roles instead of users • Rule of role authorization : [actr(s) authr(s)]. ( s S) – Subject must be authorized to assume an active role (otherwise, any subject could assume any role) 18
Axioms • Let S be the set of subjects and T the set of transactions. • Rule of role assignment : ( s S)( t T) [canexec(s, t) actr(s) ≠ ]. – If s can execute a transaction, it has a role – This ties transactions to roles instead of users • Rule of role authorization : [actr(s) authr(s)]. ( s S) – Subject must be authorized to assume an active role (otherwise, any subject could assume any role) 18
 Axiom • Rule of transaction authorization: ( s S) ( t T) [canexec(s, t) t trans(actr(s))]. – If a subject s can execute a transaction, then the transaction is an authorized one for the role s has assumed • Look at the arrows, they are one-directional: – Restrict the transactions that can be performed – Do not ensure that the allowed transactions can be executed 19
Axiom • Rule of transaction authorization: ( s S) ( t T) [canexec(s, t) t trans(actr(s))]. – If a subject s can execute a transaction, then the transaction is an authorized one for the role s has assumed • Look at the arrows, they are one-directional: – Restrict the transactions that can be performed – Do not ensure that the allowed transactions can be executed 19
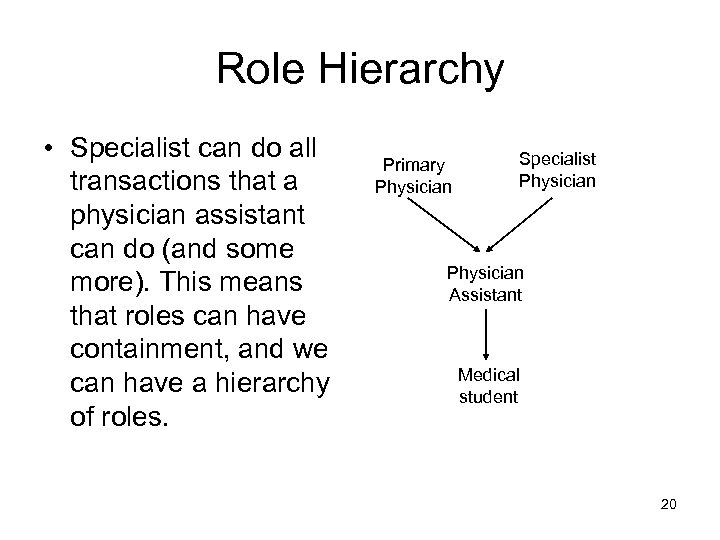 Role Hierarchy • Specialist can do all transactions that a physician assistant can do (and some more). This means that roles can have containment, and we can have a hierarchy of roles. Primary Physician Specialist Physician Assistant Medical student 20
Role Hierarchy • Specialist can do all transactions that a physician assistant can do (and some more). This means that roles can have containment, and we can have a hierarchy of roles. Primary Physician Specialist Physician Assistant Medical student 20
 Semantics of RH • User inheritance – r 1 >= r 2 means every user that is a member of r 1 is also a member of r 2 • Permission inheritance – r 1 >= r 2 means every permission that is authorized for r 2 is also authorized for r 1 • Activation inheritance – r 1 >= r 2 means user assigned to r 1 can activate junior (r 2) 21
Semantics of RH • User inheritance – r 1 >= r 2 means every user that is a member of r 1 is also a member of r 2 • Permission inheritance – r 1 >= r 2 means every permission that is authorized for r 2 is also authorized for r 1 • Activation inheritance – r 1 >= r 2 means user assigned to r 1 can activate junior (r 2) 21
 Separation of Duty • Let r be a role, and let s be a subject such that r auth(s). Then the predicate meauth(r) (for mutually exclusive authorizations) is the set of roles that s cannot assume because of the separation of duty requirement. • Separation of duty: ( r 1, r 2 R) [ r 2 meauth(r 1) [ ( s S) [ r 1 authr(s) r 2 authr(s) ] ] ] 22
Separation of Duty • Let r be a role, and let s be a subject such that r auth(s). Then the predicate meauth(r) (for mutually exclusive authorizations) is the set of roles that s cannot assume because of the separation of duty requirement. • Separation of duty: ( r 1, r 2 R) [ r 2 meauth(r 1) [ ( s S) [ r 1 authr(s) r 2 authr(s) ] ] ] 22
 23
23
 ORCON • Problem: organization creating document wants to control its dissemination – Example: Secretary of Agriculture writes a memo for distribution to her immediate subordinates, and she must give permission for it to be disseminated further. This is “originator controlled” (here, the “originator” is a person). – In real life, the originator could be an organization 24
ORCON • Problem: organization creating document wants to control its dissemination – Example: Secretary of Agriculture writes a memo for distribution to her immediate subordinates, and she must give permission for it to be disseminated further. This is “originator controlled” (here, the “originator” is a person). – In real life, the originator could be an organization 24
 Requirements • Subject s S marks object o O as ORCON on behalf of organization X. X allows o to be disclosed to subjects acting on behalf of organization Y with the following restrictions: • • o cannot be released to subjects acting on behalf of other organizations without X’s permission; and Any copies of o must have the same restrictions placed on it. • Data and metadata: how the data will be used 25
Requirements • Subject s S marks object o O as ORCON on behalf of organization X. X allows o to be disclosed to subjects acting on behalf of organization Y with the following restrictions: • • o cannot be released to subjects acting on behalf of other organizations without X’s permission; and Any copies of o must have the same restrictions placed on it. • Data and metadata: how the data will be used 25
 DAC Fails to enforce ORCON • Discretionary access control fails to enforce ORCON – Owner can set any desired permissions – This makes the second rule in the previous slide unenforceable 26
DAC Fails to enforce ORCON • Discretionary access control fails to enforce ORCON – Owner can set any desired permissions – This makes the second rule in the previous slide unenforceable 26
 MAC Fails to enforce ORCON • First problem: category explosion – You have to create a separate category for every (object, creator organization, owner organization) tuple. • Second problem: abstraction – MAC needs a centralized controller for category creation and access control – ORCON controlled locally by the originator 27
MAC Fails to enforce ORCON • First problem: category explosion – You have to create a separate category for every (object, creator organization, owner organization) tuple. • Second problem: abstraction – MAC needs a centralized controller for category creation and access control – ORCON controlled locally by the originator 27
 Combine Them • The owner of an object cannot change the access controls of the object. – The control does not go to owners • When an object is copied, the access control restrictions of that source are copied and bound to the target of the copy. – These are MAC (owner can’t control them) • The creator (originator) can alter the access control restrictions on a per-subject and perobject basis. – This is DAC (creator can control it) 28
Combine Them • The owner of an object cannot change the access controls of the object. – The control does not go to owners • When an object is copied, the access control restrictions of that source are copied and bound to the target of the copy. – These are MAC (owner can’t control them) • The creator (originator) can alter the access control restrictions on a per-subject and perobject basis. – This is DAC (creator can control it) 28
 29
29


