3e5504e7daf406c7b1d5e75fdfa96649.ppt
- Количество слайдов: 64
 IT Audit Methodologies IT Audit Methodoloies
IT Audit Methodologies IT Audit Methodoloies
 IT Audit Methodologies Cobi. T BS 7799 - Code of Practice (Co. P) BSI - IT Baseline Protection Manual ITSEC Common Criteria (CC) IT Audit Methodoloies
IT Audit Methodologies Cobi. T BS 7799 - Code of Practice (Co. P) BSI - IT Baseline Protection Manual ITSEC Common Criteria (CC) IT Audit Methodoloies
 IT Audit Methodologies - URLs Cobi. T: www. isaca. org BS 7799: www. bsi. org. uk/disc/ BSI: www. bsi. bund. de/gshb/english/menue. htm ITSEC: www. itsec. gov. uk CC: csrc. nist. gov/cc/ IT Audit Methodoloies
IT Audit Methodologies - URLs Cobi. T: www. isaca. org BS 7799: www. bsi. org. uk/disc/ BSI: www. bsi. bund. de/gshb/english/menue. htm ITSEC: www. itsec. gov. uk CC: csrc. nist. gov/cc/ IT Audit Methodoloies
 Main Areas of Use IT Audits Risk Analysis Health Checks (Security Benchmarking) Security Concepts Security Manuals / Handbooks IT Audit Methodoloies
Main Areas of Use IT Audits Risk Analysis Health Checks (Security Benchmarking) Security Concepts Security Manuals / Handbooks IT Audit Methodoloies
 Security Definition Confidentiality Integrity Correctness Completeness Availability IT Audit Methodoloies
Security Definition Confidentiality Integrity Correctness Completeness Availability IT Audit Methodoloies
 Cobi. T Governance, Control & Audit for IT Developed by ISACA Releases Cobi. T 1: 1996 32 Processes 271 Control Objectives Cobi. T 2: 1998 34 Processes 302 Control Objectives IT Audit Methodoloies
Cobi. T Governance, Control & Audit for IT Developed by ISACA Releases Cobi. T 1: 1996 32 Processes 271 Control Objectives Cobi. T 2: 1998 34 Processes 302 Control Objectives IT Audit Methodoloies
 Cobi. T - Model for IT Governance 36 Control models used as basis: Business control models (e. g. COSO) IT control models (e. g. DTI‘s Co. P) Cobi. T control model covers: Security (Confidentiality, Integrity, Availability) Fiduciary (Effectiveness, Efficiency, Compliance, Reliability of Information) IT Resources (Data, Application Systems, Technology, Facilities, People) IT Audit Methodoloies
Cobi. T - Model for IT Governance 36 Control models used as basis: Business control models (e. g. COSO) IT control models (e. g. DTI‘s Co. P) Cobi. T control model covers: Security (Confidentiality, Integrity, Availability) Fiduciary (Effectiveness, Efficiency, Compliance, Reliability of Information) IT Resources (Data, Application Systems, Technology, Facilities, People) IT Audit Methodoloies
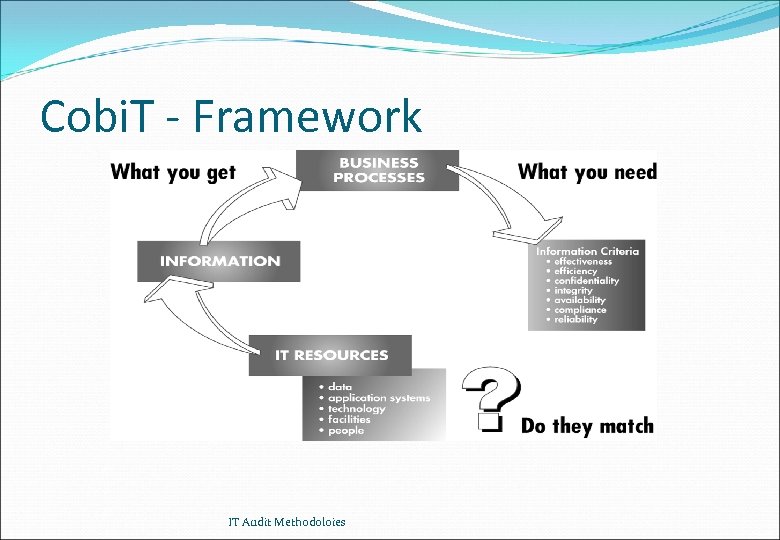 Cobi. T - Framework IT Audit Methodoloies
Cobi. T - Framework IT Audit Methodoloies
 Cobi. T - Structure 4 Domains PO - Planning & Organisation AI - Acquisition & Implementation 6 processes (high-level control objectives) DS - Delivery & Support 11 processes (high-level control objectives) 13 processes (high-level control objectives) M - Monitoring 4 processes (high-level control objectives) IT Audit Methodoloies
Cobi. T - Structure 4 Domains PO - Planning & Organisation AI - Acquisition & Implementation 6 processes (high-level control objectives) DS - Delivery & Support 11 processes (high-level control objectives) 13 processes (high-level control objectives) M - Monitoring 4 processes (high-level control objectives) IT Audit Methodoloies
 PO - Planning and Organisation PO 1 PO 2 PO 3 PO 4 PO 5 PO 6 PO 7 PO 8 PO 9 PO 10 PO 11 Define a Strategic IT Plan Define the Information Architecture Determine the Technological Direction Define the IT Organisation and Relationships Manage the IT Investment Communicate Management Aims and Direction Manage Human Resources Ensure Compliance with External Requirements Assess Risks Manage Projects Manage Quality IT Audit Methodoloies
PO - Planning and Organisation PO 1 PO 2 PO 3 PO 4 PO 5 PO 6 PO 7 PO 8 PO 9 PO 10 PO 11 Define a Strategic IT Plan Define the Information Architecture Determine the Technological Direction Define the IT Organisation and Relationships Manage the IT Investment Communicate Management Aims and Direction Manage Human Resources Ensure Compliance with External Requirements Assess Risks Manage Projects Manage Quality IT Audit Methodoloies
 AI - Acquisition and Implementation AI 1 Identify Solutions AI 2 AI 3 AI 4 AI 5 AI 6 Acquire and Maintain Application Software Acquire and Maintain Technology Architecture Develop and Maintain IT Procedures Install and Accredit Systems Manage Changes IT Audit Methodoloies
AI - Acquisition and Implementation AI 1 Identify Solutions AI 2 AI 3 AI 4 AI 5 AI 6 Acquire and Maintain Application Software Acquire and Maintain Technology Architecture Develop and Maintain IT Procedures Install and Accredit Systems Manage Changes IT Audit Methodoloies
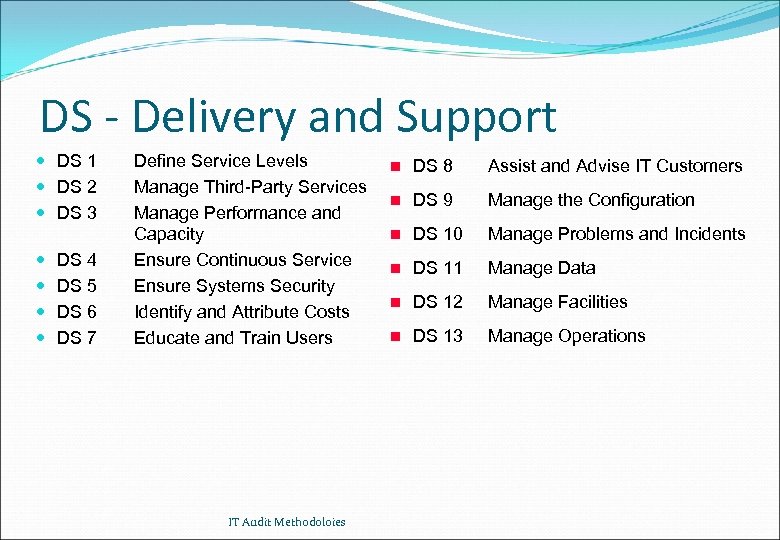 DS - Delivery and Support DS 1 DS 2 DS 3 DS 4 DS 5 DS 6 DS 7 Define Service Levels Manage Third-Party Services Manage Performance and Capacity Ensure Continuous Service Ensure Systems Security Identify and Attribute Costs Educate and Train Users IT Audit Methodoloies n DS 8 Assist and Advise IT Customers n DS 9 Manage the Configuration n DS 10 Manage Problems and Incidents n DS 11 Manage Data n DS 12 Manage Facilities n DS 13 Manage Operations
DS - Delivery and Support DS 1 DS 2 DS 3 DS 4 DS 5 DS 6 DS 7 Define Service Levels Manage Third-Party Services Manage Performance and Capacity Ensure Continuous Service Ensure Systems Security Identify and Attribute Costs Educate and Train Users IT Audit Methodoloies n DS 8 Assist and Advise IT Customers n DS 9 Manage the Configuration n DS 10 Manage Problems and Incidents n DS 11 Manage Data n DS 12 Manage Facilities n DS 13 Manage Operations
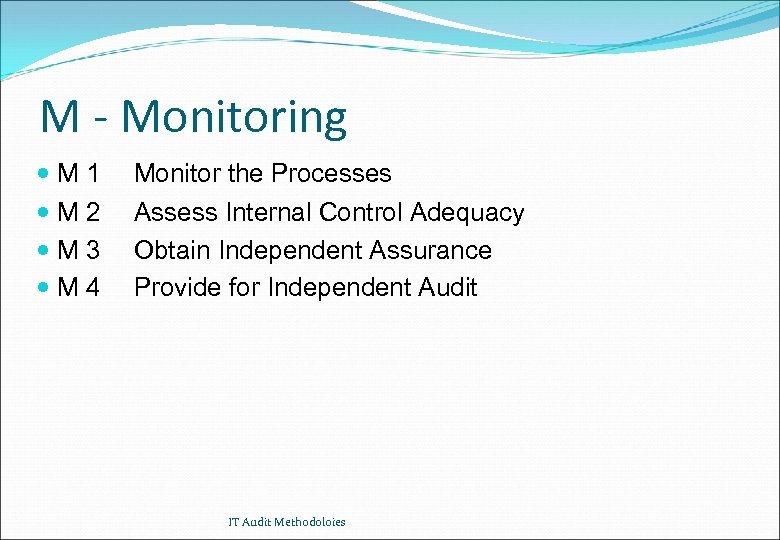 M - Monitoring M 1 Monitor the Processes M 2 M 3 M 4 Assess Internal Control Adequacy Obtain Independent Assurance Provide for Independent Audit IT Audit Methodoloies
M - Monitoring M 1 Monitor the Processes M 2 M 3 M 4 Assess Internal Control Adequacy Obtain Independent Assurance Provide for Independent Audit IT Audit Methodoloies
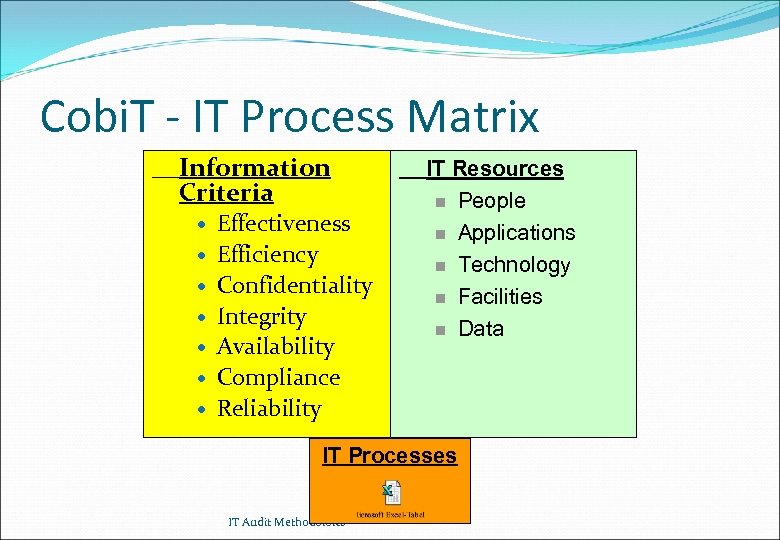 Cobi. T - IT Process Matrix Information Criteria Effectiveness Efficiency Confidentiality Integrity Availability Compliance Reliability IT Resources n People n Applications n Technology n Facilities n Data IT Processes IT Audit Methodoloies
Cobi. T - IT Process Matrix Information Criteria Effectiveness Efficiency Confidentiality Integrity Availability Compliance Reliability IT Resources n People n Applications n Technology n Facilities n Data IT Processes IT Audit Methodoloies
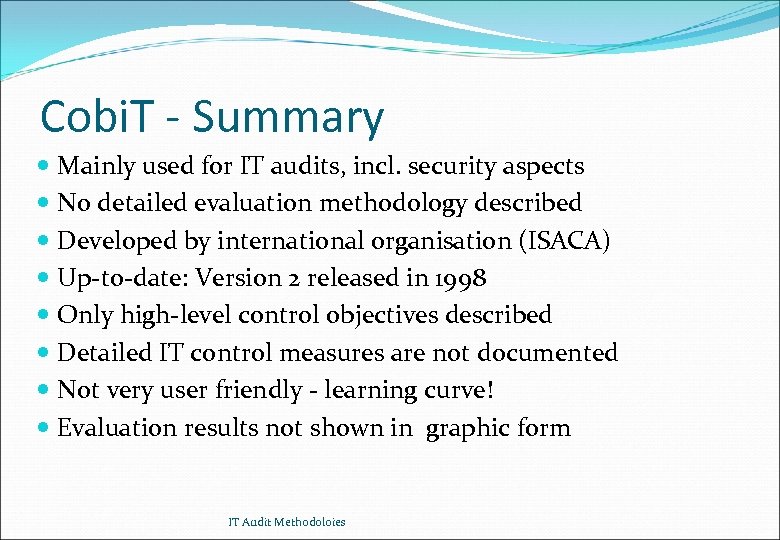 Cobi. T - Summary Mainly used for IT audits, incl. security aspects No detailed evaluation methodology described Developed by international organisation (ISACA) Up-to-date: Version 2 released in 1998 Only high-level control objectives described Detailed IT control measures are not documented Not very user friendly - learning curve! Evaluation results not shown in graphic form IT Audit Methodoloies
Cobi. T - Summary Mainly used for IT audits, incl. security aspects No detailed evaluation methodology described Developed by international organisation (ISACA) Up-to-date: Version 2 released in 1998 Only high-level control objectives described Detailed IT control measures are not documented Not very user friendly - learning curve! Evaluation results not shown in graphic form IT Audit Methodoloies
 Cobi. T - Summary May be used for self assessments Useful aid in implementing IT control systems No suitable basis to write security handbooks Cobi. T package from ISACA: $ 100. - 3 parts freely downloadable from ISACA site Software available from Methodware Ltd. , NZ (www. methodware. co. nz) Cobi. T Advisor 2 nd edition: IT Audit Methodoloies US$ 600. --
Cobi. T - Summary May be used for self assessments Useful aid in implementing IT control systems No suitable basis to write security handbooks Cobi. T package from ISACA: $ 100. - 3 parts freely downloadable from ISACA site Software available from Methodware Ltd. , NZ (www. methodware. co. nz) Cobi. T Advisor 2 nd edition: IT Audit Methodoloies US$ 600. --
 BS 7799 - Co. P Code of Practice for Inform. Security Manag. Developed by UK DTI, BSI: British Standard Releases Co. P: 1993 BS 7799: Part 1: 1995 BS 7799: Part 2: 1998 Certification & Accreditation scheme (c: cure) IT Audit Methodoloies
BS 7799 - Co. P Code of Practice for Inform. Security Manag. Developed by UK DTI, BSI: British Standard Releases Co. P: 1993 BS 7799: Part 1: 1995 BS 7799: Part 2: 1998 Certification & Accreditation scheme (c: cure) IT Audit Methodoloies
 BS 7799 - Security Baseline Controls 10 control categories 32 control groups 109 security controls 10 security key controls IT Audit Methodoloies
BS 7799 - Security Baseline Controls 10 control categories 32 control groups 109 security controls 10 security key controls IT Audit Methodoloies
 BS 7799 - Control Categories Information security policy Security organisation Assets classification & control Personnel security Physical & environmental security Computer & network management IT Audit Methodoloies
BS 7799 - Control Categories Information security policy Security organisation Assets classification & control Personnel security Physical & environmental security Computer & network management IT Audit Methodoloies
 BS 7799 - Control Categories System access control Systems development & maintenance Business continuity planning Compliance IT Audit Methodoloies
BS 7799 - Control Categories System access control Systems development & maintenance Business continuity planning Compliance IT Audit Methodoloies
 BS 7799 - 10 Key Controls Information security policy document Allocation of information security responsibilities Information security education and training Reporting of security incidents Virus controls IT Audit Methodoloies
BS 7799 - 10 Key Controls Information security policy document Allocation of information security responsibilities Information security education and training Reporting of security incidents Virus controls IT Audit Methodoloies
 BS 7799 - 10 Key Controls Business continuity planning process Control of proprietary software copying Safeguarding of organizational records Data protection Compliance with security policy IT Audit Methodoloies
BS 7799 - 10 Key Controls Business continuity planning process Control of proprietary software copying Safeguarding of organizational records Data protection Compliance with security policy IT Audit Methodoloies
 BS 7799 - Summary Main use: Security Concepts & Health Checks No evaluation methodology described British Standard, developed by UK DTI Certification scheme in place (c: cure) BS 7799, Part 1, 1995 is being revised in 1999 Lists 109 ready-to-use security controls No detailed security measures described Very user friendly - easy to learn IT Audit Methodoloies
BS 7799 - Summary Main use: Security Concepts & Health Checks No evaluation methodology described British Standard, developed by UK DTI Certification scheme in place (c: cure) BS 7799, Part 1, 1995 is being revised in 1999 Lists 109 ready-to-use security controls No detailed security measures described Very user friendly - easy to learn IT Audit Methodoloies
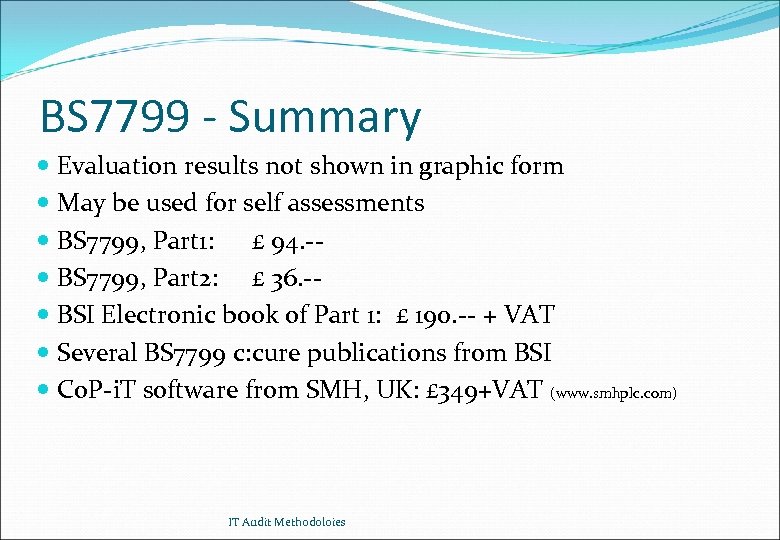 BS 7799 - Summary Evaluation results not shown in graphic form May be used for self assessments BS 7799, Part 1: £ 94. - BS 7799, Part 2: £ 36. - BSI Electronic book of Part 1: £ 190. -- + VAT Several BS 7799 c: cure publications from BSI Co. P-i. T software from SMH, UK: £ 349+VAT (www. smhplc. com) IT Audit Methodoloies
BS 7799 - Summary Evaluation results not shown in graphic form May be used for self assessments BS 7799, Part 1: £ 94. - BS 7799, Part 2: £ 36. - BSI Electronic book of Part 1: £ 190. -- + VAT Several BS 7799 c: cure publications from BSI Co. P-i. T software from SMH, UK: £ 349+VAT (www. smhplc. com) IT Audit Methodoloies
 BSI (Bundesamt für Sicherheit in der Informationstechnik) IT Baseline Protection Manual (IT- Grundschutzhandbuch ) Developed by German BSI (GISA: German Information Security Agency) Releases: IT security manual: 1992 IT baseline protection manual: 1995 New versions (paper and CD-ROM): each year IT Audit Methodoloies
BSI (Bundesamt für Sicherheit in der Informationstechnik) IT Baseline Protection Manual (IT- Grundschutzhandbuch ) Developed by German BSI (GISA: German Information Security Agency) Releases: IT security manual: 1992 IT baseline protection manual: 1995 New versions (paper and CD-ROM): each year IT Audit Methodoloies
 BSI - Approach IT Audit Methodoloies
BSI - Approach IT Audit Methodoloies
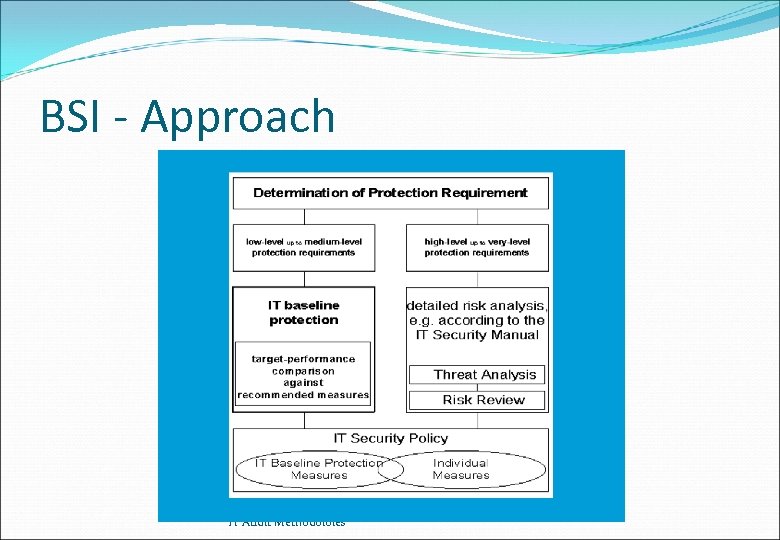
 BSI - Approach Used to determine IT security measures for medium-level protection requirements Straight forward approach since detailed risk analysis is not performed Based on generic & platform specific security requirements detailed protection measures are constructed using given building blocks List of assembled security measures may be used to establish or enhance baseline protection IT Audit Methodoloies
BSI - Approach Used to determine IT security measures for medium-level protection requirements Straight forward approach since detailed risk analysis is not performed Based on generic & platform specific security requirements detailed protection measures are constructed using given building blocks List of assembled security measures may be used to establish or enhance baseline protection IT Audit Methodoloies
 BSI - Structure IT security measures 7 areas 34 modules (building blocks) Safeguards catalogue 6 categories of security measures Threats catalogue 5 categories of threats IT Audit Methodoloies
BSI - Structure IT security measures 7 areas 34 modules (building blocks) Safeguards catalogue 6 categories of security measures Threats catalogue 5 categories of threats IT Audit Methodoloies
 BSI - Security Measures (Modules) Protection for generic components Infrastructure Non-networked systems LANs Data transfer systems Telecommunications Other IT components IT Audit Methodoloies
BSI - Security Measures (Modules) Protection for generic components Infrastructure Non-networked systems LANs Data transfer systems Telecommunications Other IT components IT Audit Methodoloies
 BSI - Generic Components 3. 1 Organisation 3. 2 Personnel 3. 3 Contingency Planning 3. 4 Data Protection IT Audit Methodoloies
BSI - Generic Components 3. 1 Organisation 3. 2 Personnel 3. 3 Contingency Planning 3. 4 Data Protection IT Audit Methodoloies
 BSI - Infrastructure 4. 1 Buildings 4. 2 Cabling 4. 3 Rooms 4. 3. 1 Office 4. 3. 2 Server Room 4. 3. 3 Storage Media Archives 4. 3. 4 Technical Infrastructure Room 4. 4 Protective cabinets 4. 5 Home working place IT Audit Methodoloies
BSI - Infrastructure 4. 1 Buildings 4. 2 Cabling 4. 3 Rooms 4. 3. 1 Office 4. 3. 2 Server Room 4. 3. 3 Storage Media Archives 4. 3. 4 Technical Infrastructure Room 4. 4 Protective cabinets 4. 5 Home working place IT Audit Methodoloies
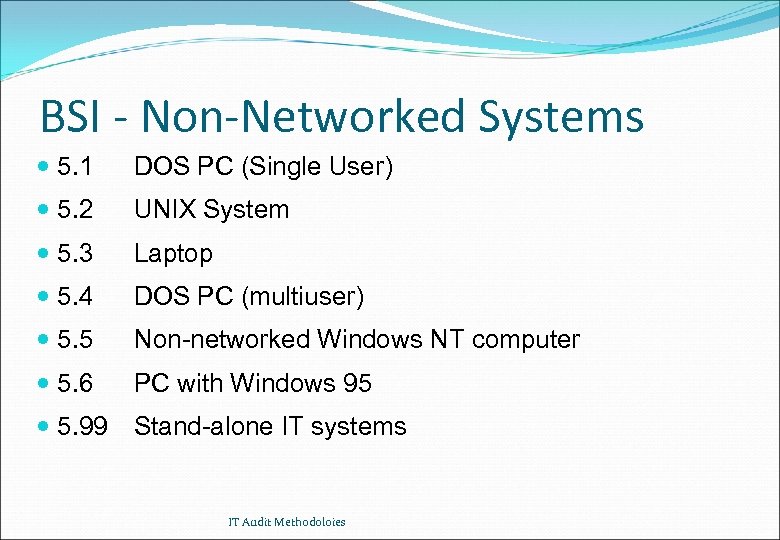 BSI - Non-Networked Systems 5. 1 DOS PC (Single User) 5. 2 UNIX System 5. 3 Laptop 5. 4 DOS PC (multiuser) 5. 5 Non-networked Windows NT computer 5. 6 PC with Windows 95 5. 99 Stand-alone IT systems IT Audit Methodoloies
BSI - Non-Networked Systems 5. 1 DOS PC (Single User) 5. 2 UNIX System 5. 3 Laptop 5. 4 DOS PC (multiuser) 5. 5 Non-networked Windows NT computer 5. 6 PC with Windows 95 5. 99 Stand-alone IT systems IT Audit Methodoloies
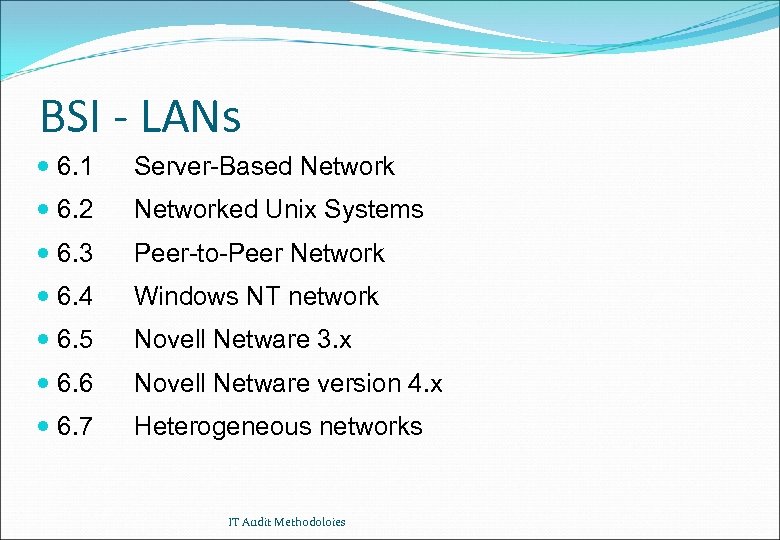 BSI - LANs 6. 1 Server-Based Network 6. 2 Networked Unix Systems 6. 3 Peer-to-Peer Network 6. 4 Windows NT network 6. 5 Novell Netware 3. x 6. 6 Novell Netware version 4. x 6. 7 Heterogeneous networks IT Audit Methodoloies
BSI - LANs 6. 1 Server-Based Network 6. 2 Networked Unix Systems 6. 3 Peer-to-Peer Network 6. 4 Windows NT network 6. 5 Novell Netware 3. x 6. 6 Novell Netware version 4. x 6. 7 Heterogeneous networks IT Audit Methodoloies
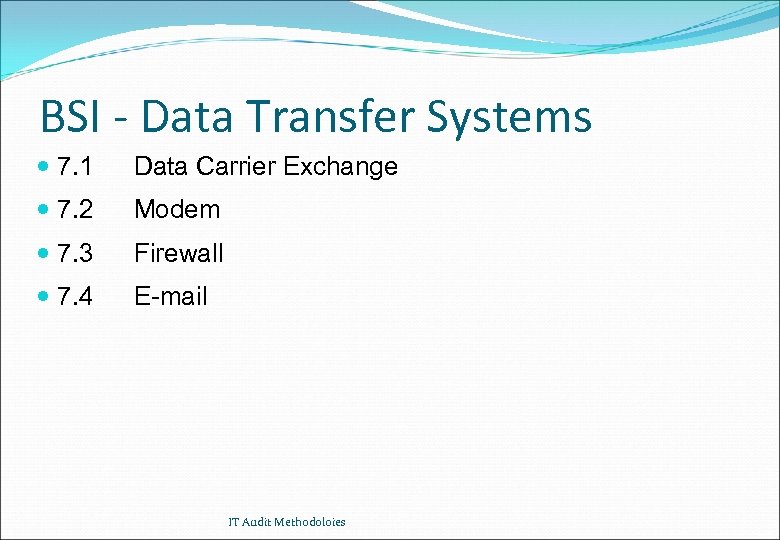 BSI - Data Transfer Systems 7. 1 Data Carrier Exchange 7. 2 Modem 7. 3 Firewall 7. 4 E-mail IT Audit Methodoloies
BSI - Data Transfer Systems 7. 1 Data Carrier Exchange 7. 2 Modem 7. 3 Firewall 7. 4 E-mail IT Audit Methodoloies
 BSI - Telecommunications 8. 1 Telecommunication system 8. 2 Fax Machine 8. 3 Telephone Answering Machine 8. 4 LAN integration of an IT system via ISDN IT Audit Methodoloies
BSI - Telecommunications 8. 1 Telecommunication system 8. 2 Fax Machine 8. 3 Telephone Answering Machine 8. 4 LAN integration of an IT system via ISDN IT Audit Methodoloies
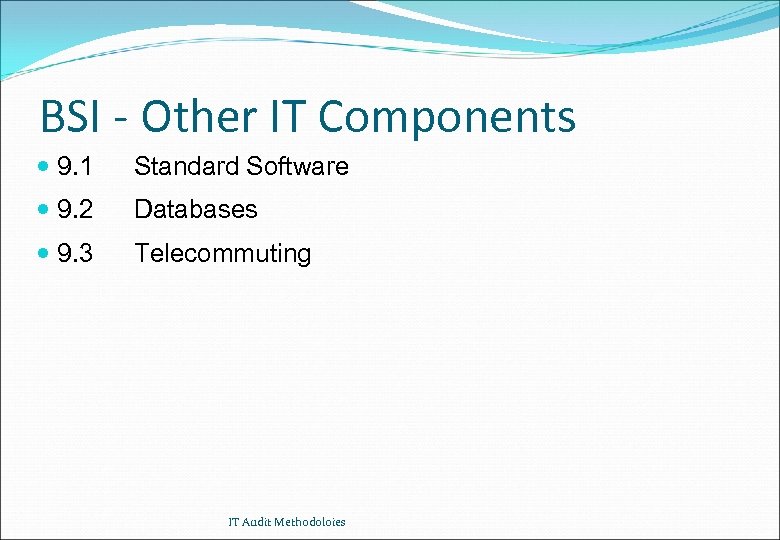 BSI - Other IT Components 9. 1 Standard Software 9. 2 Databases 9. 3 Telecommuting IT Audit Methodoloies
BSI - Other IT Components 9. 1 Standard Software 9. 2 Databases 9. 3 Telecommuting IT Audit Methodoloies
 BSI - Module „Data Protection“ (3. 4) Threats - Technical failure: T 4. 13 Loss of stored data Security Measures - Contingency planning: S 6. 36 Stipulating a minimum data protection concept S 6. 37 Documenting data protection procedures S 6. 33 Development of a data protection concept (optional) S 6. 34 Determining the factors influencing data protection (optional) S 6. 35 Stipulating data protection procedures (optional) S 6. 41 Training data reconstruction Security Measures - Organisation: S 2. 41 Employees' commitment to data protection IT Audit Methodoloies S 2. 137 Procurement of a suitable data backup system
BSI - Module „Data Protection“ (3. 4) Threats - Technical failure: T 4. 13 Loss of stored data Security Measures - Contingency planning: S 6. 36 Stipulating a minimum data protection concept S 6. 37 Documenting data protection procedures S 6. 33 Development of a data protection concept (optional) S 6. 34 Determining the factors influencing data protection (optional) S 6. 35 Stipulating data protection procedures (optional) S 6. 41 Training data reconstruction Security Measures - Organisation: S 2. 41 Employees' commitment to data protection IT Audit Methodoloies S 2. 137 Procurement of a suitable data backup system
 BSI - Safeguards (420 safeguards) S 1 - Infrastructure ( 45 safeguards) S 2 - Organisation (153 safeguards) S 3 - Personnel ( 22 safeguards) S 4 - Hardware & Software ( 83 safeguards) S 5 - Communications ( 62 safeguards) S 6 - Contingency Planning ( 55 safeguards) IT Audit Methodoloies
BSI - Safeguards (420 safeguards) S 1 - Infrastructure ( 45 safeguards) S 2 - Organisation (153 safeguards) S 3 - Personnel ( 22 safeguards) S 4 - Hardware & Software ( 83 safeguards) S 5 - Communications ( 62 safeguards) S 6 - Contingency Planning ( 55 safeguards) IT Audit Methodoloies
 BSI - S 1 -Infrastructure (45 safeguards) S 1. 7 Hand-held fire extinguishers S 1. 10 Use of safety doors S 1. 17 Entrance control service S 1. 18 Intruder and fire detection devices S 1. 27 Air conditioning S 1. 28 Local uninterruptible power supply [UPS] S 1. 36 Safekeeping of data carriers before and after dispatch IT Audit Methodoloies
BSI - S 1 -Infrastructure (45 safeguards) S 1. 7 Hand-held fire extinguishers S 1. 10 Use of safety doors S 1. 17 Entrance control service S 1. 18 Intruder and fire detection devices S 1. 27 Air conditioning S 1. 28 Local uninterruptible power supply [UPS] S 1. 36 Safekeeping of data carriers before and after dispatch IT Audit Methodoloies
 BSI - Security Threats (209 threats) T 1 - Force Majeure (10 threats) T 2 - Organisational Shortcomings (58 T 3 - Human Errors (31 threats) T 4 - Technical Failure (32 threats) T 5 - Deliberate acts (78 threats) IT Audit Methodoloies threats)
BSI - Security Threats (209 threats) T 1 - Force Majeure (10 threats) T 2 - Organisational Shortcomings (58 T 3 - Human Errors (31 threats) T 4 - Technical Failure (32 threats) T 5 - Deliberate acts (78 threats) IT Audit Methodoloies threats)
 BSI - T 3 -Human Errors T 3. 1 (31 threats) Loss of data confidentiality/integrity as a result of IT user error T 3. 3 Non-compliance with IT security measures T 3. 6 Threat posed by cleaning staff or outside staff T 3. 9 Incorrect management of the IT system T 3. 12 Loss of storage media during transfer T 3. 16 Incorrect administration of site and data access rights T 3. 24 Inadvertent manipulation of data T 3. 25 Negligent deletion of objects IT Audit Methodoloies
BSI - T 3 -Human Errors T 3. 1 (31 threats) Loss of data confidentiality/integrity as a result of IT user error T 3. 3 Non-compliance with IT security measures T 3. 6 Threat posed by cleaning staff or outside staff T 3. 9 Incorrect management of the IT system T 3. 12 Loss of storage media during transfer T 3. 16 Incorrect administration of site and data access rights T 3. 24 Inadvertent manipulation of data T 3. 25 Negligent deletion of objects IT Audit Methodoloies
 BSI - Summary Main use: Security concepts & manuals No evaluation methodology described Developed by German BSI (GISA) Updated version released each year Lists 209 threats & 420 security measures 34 modules cover generic & platform specific security requirements IT Audit Methodoloies
BSI - Summary Main use: Security concepts & manuals No evaluation methodology described Developed by German BSI (GISA) Updated version released each year Lists 209 threats & 420 security measures 34 modules cover generic & platform specific security requirements IT Audit Methodoloies
 BSI - Summary User friendly with a lot of security details Not suitable for security risk analysis Results of security coverage not shown in graphic form Manual in HTML format on BSI web server Manual in Winword format on CD-ROM (first CD free, additional CDs cost DM 50. -- each) Paper copy of manual: DM 118. - Software ‚BSI Tool‘ (only in German): DM 515. -- IT Audit Methodoloies
BSI - Summary User friendly with a lot of security details Not suitable for security risk analysis Results of security coverage not shown in graphic form Manual in HTML format on BSI web server Manual in Winword format on CD-ROM (first CD free, additional CDs cost DM 50. -- each) Paper copy of manual: DM 118. - Software ‚BSI Tool‘ (only in German): DM 515. -- IT Audit Methodoloies
 ITSEC, Common Criteria ITSEC: IT Security Evaluation Criteria Developed by UK, Germany, France, Netherl. and based primarily on USA TCSEC (Orange Book) Releases ITSEC: 1991 ITSEM: 1993 (IT Security Evaluation Manual) UK IT Security Evaluation & Certification scheme: 1994 IT Audit Methodoloies
ITSEC, Common Criteria ITSEC: IT Security Evaluation Criteria Developed by UK, Germany, France, Netherl. and based primarily on USA TCSEC (Orange Book) Releases ITSEC: 1991 ITSEM: 1993 (IT Security Evaluation Manual) UK IT Security Evaluation & Certification scheme: 1994 IT Audit Methodoloies
 ITSEC, Common Criteria (CC) Developed by USA, EC: based on ITSEC ISO International Standard Releases CC 1. 0: 1996 CC 2. 0: 1998 ISO IS 15408: 1999 IT Audit Methodoloies
ITSEC, Common Criteria (CC) Developed by USA, EC: based on ITSEC ISO International Standard Releases CC 1. 0: 1996 CC 2. 0: 1998 ISO IS 15408: 1999 IT Audit Methodoloies
 ITSEC - Methodology Based on systematic, documented approach for security evaluations of systems & products Open ended with regard to defined set of security objectives ITSEC Functionality classes; e. g. FC-C 2 CC protection profiles Evaluation steps: Definition of functionality Assurance: confidence in functionality IT Audit Methodoloies
ITSEC - Methodology Based on systematic, documented approach for security evaluations of systems & products Open ended with regard to defined set of security objectives ITSEC Functionality classes; e. g. FC-C 2 CC protection profiles Evaluation steps: Definition of functionality Assurance: confidence in functionality IT Audit Methodoloies
 ITSEC - Functionality Security objectives (Why) Risk analysis (Threats, Countermeasures) Security policy Security enforcing functions (What) technical & non-technical Security mechanisms (How) Evaluation levels IT Audit Methodoloies
ITSEC - Functionality Security objectives (Why) Risk analysis (Threats, Countermeasures) Security policy Security enforcing functions (What) technical & non-technical Security mechanisms (How) Evaluation levels IT Audit Methodoloies
 ITSEC - Assurance Goal: Confidence in functions & mechanisms Correctness Construction (development process & environment) Operation (process & environment) Effectiveness Suitability analysis Strength of mechanism analysis Vulnerabilities (construction & operation) IT Audit Methodoloies
ITSEC - Assurance Goal: Confidence in functions & mechanisms Correctness Construction (development process & environment) Operation (process & environment) Effectiveness Suitability analysis Strength of mechanism analysis Vulnerabilities (construction & operation) IT Audit Methodoloies
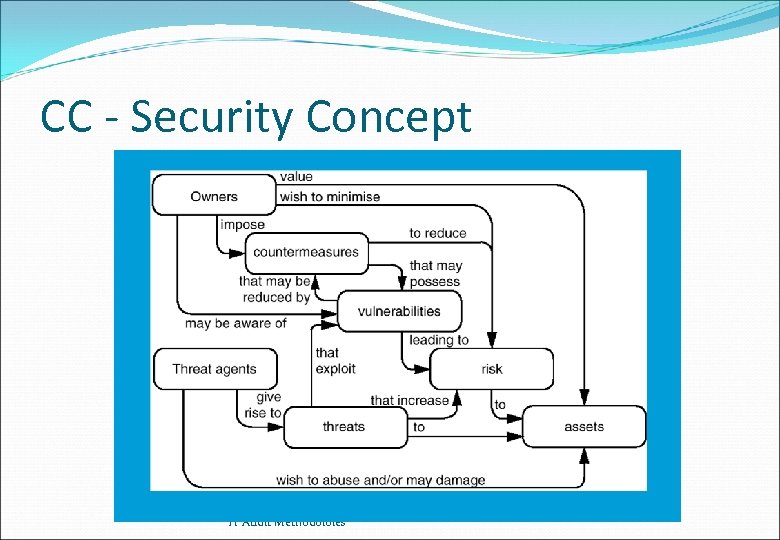 CC - Security Concept IT Audit Methodoloies
CC - Security Concept IT Audit Methodoloies
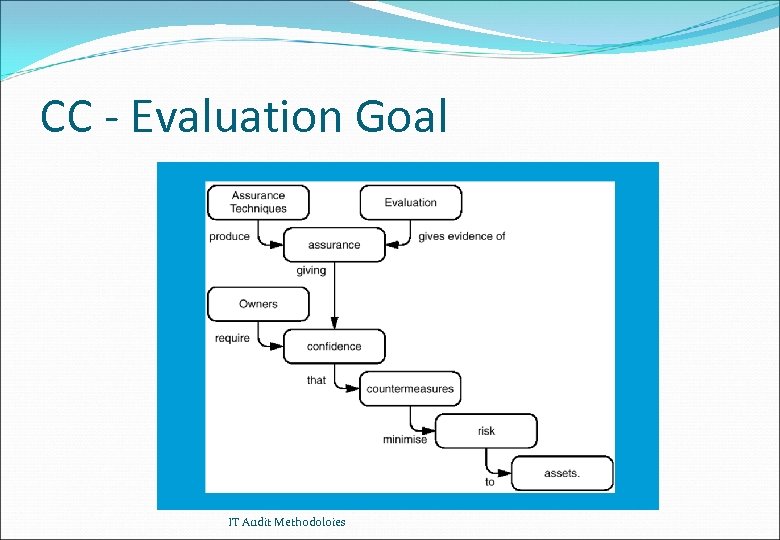 CC - Evaluation Goal IT Audit Methodoloies
CC - Evaluation Goal IT Audit Methodoloies
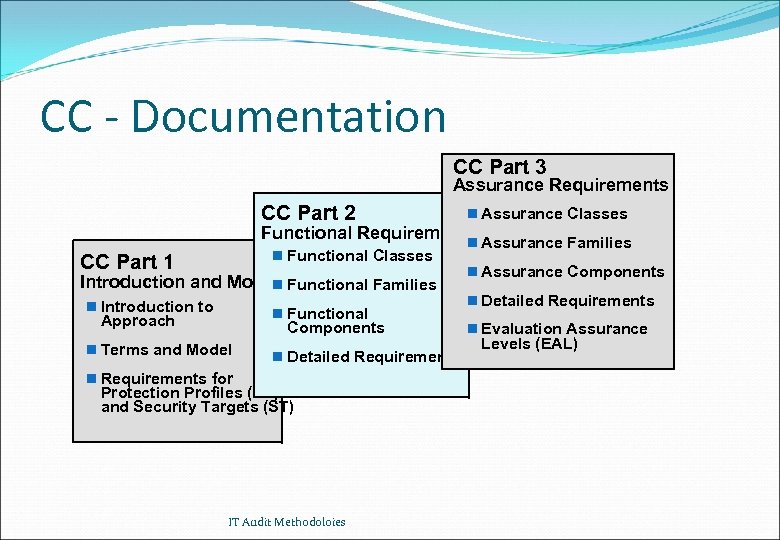 CC - Documentation CC Part 3 Assurance Requirements CC Part 2 n Assurance Classes Functional Requirements Assurance Families n n Functional Classes CC Part 1 Introduction and Model Functional Families n n Introduction to n Functional Approach Components n Terms and Model n Detailed Requirements n Requirements for Protection Profiles (PP) and Security Targets (ST) IT Audit Methodoloies n Assurance Components n Detailed Requirements n Evaluation Assurance Levels (EAL)
CC - Documentation CC Part 3 Assurance Requirements CC Part 2 n Assurance Classes Functional Requirements Assurance Families n n Functional Classes CC Part 1 Introduction and Model Functional Families n n Introduction to n Functional Approach Components n Terms and Model n Detailed Requirements n Requirements for Protection Profiles (PP) and Security Targets (ST) IT Audit Methodoloies n Assurance Components n Detailed Requirements n Evaluation Assurance Levels (EAL)
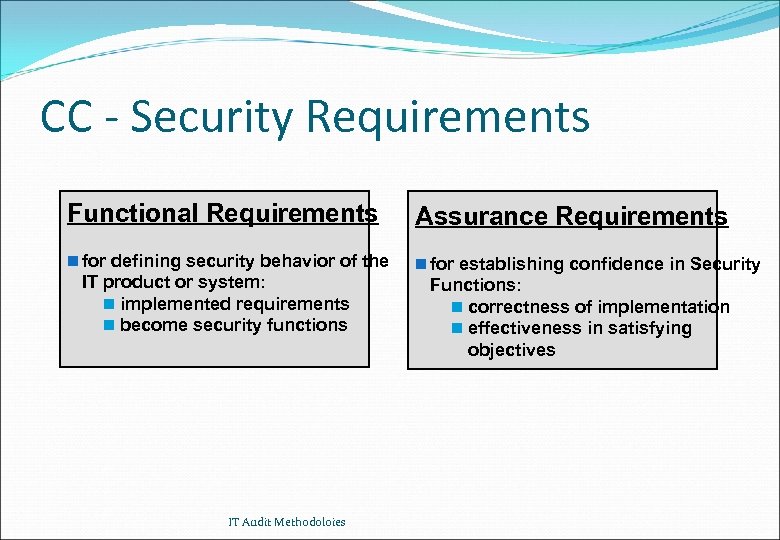 CC - Security Requirements Functional Requirements Assurance Requirements n for defining security behavior of the n for establishing confidence in Security IT product or system: n implemented requirements n become security functions IT Audit Methodoloies Functions: n correctness of implementation n effectiveness in satisfying objectives
CC - Security Requirements Functional Requirements Assurance Requirements n for defining security behavior of the n for establishing confidence in Security IT product or system: n implemented requirements n become security functions IT Audit Methodoloies Functions: n correctness of implementation n effectiveness in satisfying objectives
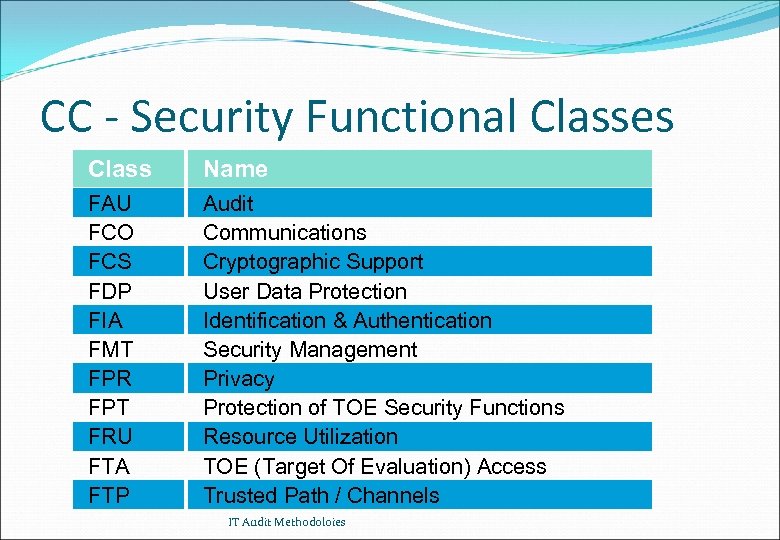 CC - Security Functional Classes Class Name FAU FCO FCS FDP FIA FMT FPR FPT FRU FTA FTP Audit Communications Cryptographic Support User Data Protection Identification & Authentication Security Management Privacy Protection of TOE Security Functions Resource Utilization TOE (Target Of Evaluation) Access Trusted Path / Channels IT Audit Methodoloies
CC - Security Functional Classes Class Name FAU FCO FCS FDP FIA FMT FPR FPT FRU FTA FTP Audit Communications Cryptographic Support User Data Protection Identification & Authentication Security Management Privacy Protection of TOE Security Functions Resource Utilization TOE (Target Of Evaluation) Access Trusted Path / Channels IT Audit Methodoloies
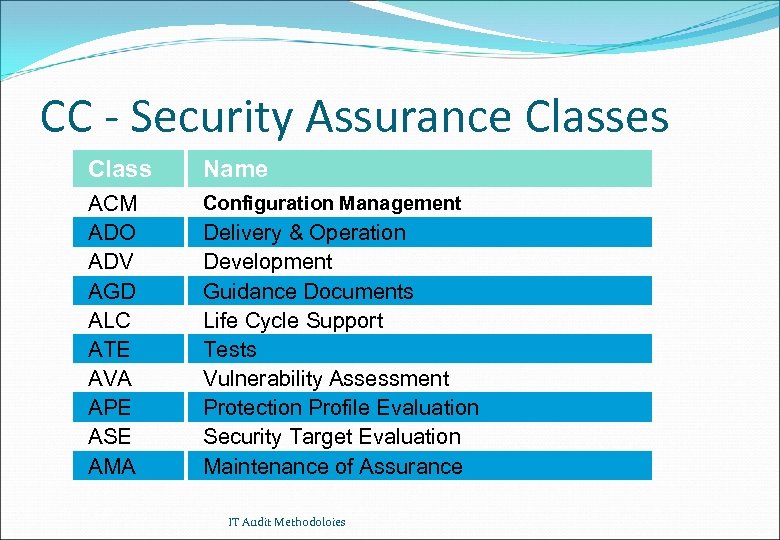 CC - Security Assurance Classes Class Name ACM ADO ADV AGD ALC ATE AVA APE ASE AMA Configuration Management Delivery & Operation Development Guidance Documents Life Cycle Support Tests Vulnerability Assessment Protection Profile Evaluation Security Target Evaluation Maintenance of Assurance IT Audit Methodoloies
CC - Security Assurance Classes Class Name ACM ADO ADV AGD ALC ATE AVA APE ASE AMA Configuration Management Delivery & Operation Development Guidance Documents Life Cycle Support Tests Vulnerability Assessment Protection Profile Evaluation Security Target Evaluation Maintenance of Assurance IT Audit Methodoloies
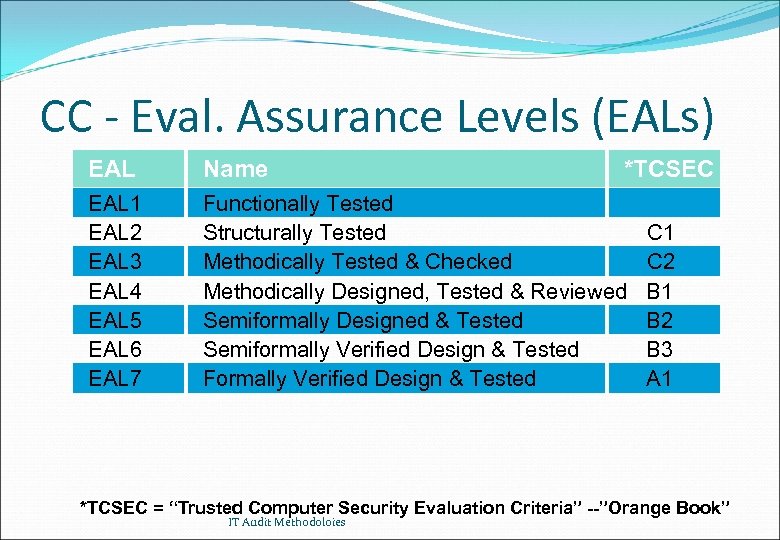 CC - Eval. Assurance Levels (EALs) EAL Name EAL 1 EAL 2 EAL 3 EAL 4 EAL 5 EAL 6 EAL 7 Functionally Tested Structurally Tested Methodically Tested & Checked Methodically Designed, Tested & Reviewed Semiformally Designed & Tested Semiformally Verified Design & Tested Formally Verified Design & Tested *TCSEC C 1 C 2 B 1 B 2 B 3 A 1 *TCSEC = “Trusted Computer Security Evaluation Criteria” --”Orange Book” IT Audit Methodoloies
CC - Eval. Assurance Levels (EALs) EAL Name EAL 1 EAL 2 EAL 3 EAL 4 EAL 5 EAL 6 EAL 7 Functionally Tested Structurally Tested Methodically Tested & Checked Methodically Designed, Tested & Reviewed Semiformally Designed & Tested Semiformally Verified Design & Tested Formally Verified Design & Tested *TCSEC C 1 C 2 B 1 B 2 B 3 A 1 *TCSEC = “Trusted Computer Security Evaluation Criteria” --”Orange Book” IT Audit Methodoloies
 ITSEC, CC - Summary Used primarily for security evaluations and not for generalized IT audits Defines evaluation methodology Based on International Standard (ISO 15408) Certification scheme in place Updated & enhanced on a yearly basis Includes extensible standard sets of security requirements (Protection Profile libraries) IT Audit Methodoloies
ITSEC, CC - Summary Used primarily for security evaluations and not for generalized IT audits Defines evaluation methodology Based on International Standard (ISO 15408) Certification scheme in place Updated & enhanced on a yearly basis Includes extensible standard sets of security requirements (Protection Profile libraries) IT Audit Methodoloies
 Comparison of Methods - Criteria Standardisation Independence Certifiability Applicability in practice Adaptability IT Audit Methodoloies
Comparison of Methods - Criteria Standardisation Independence Certifiability Applicability in practice Adaptability IT Audit Methodoloies
 Comparison of Methods - Criteria Extent of Scope Presentation of Results Efficiency Update frequency Ease of Use IT Audit Methodoloies
Comparison of Methods - Criteria Extent of Scope Presentation of Results Efficiency Update frequency Ease of Use IT Audit Methodoloies
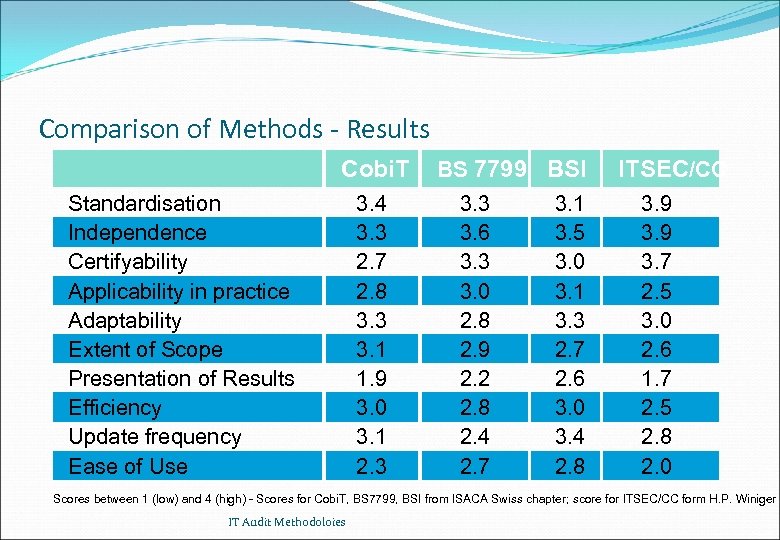 Comparison of Methods - Results Cobi. T Standardisation Independence Certifyability Applicability in practice Adaptability Extent of Scope Presentation of Results Efficiency Update frequency Ease of Use 3. 4 3. 3 2. 7 2. 8 3. 3 3. 1 1. 9 3. 0 3. 1 2. 3 BS 7799 BSI 3. 3 3. 6 3. 3 3. 0 2. 8 2. 9 2. 2 2. 8 2. 4 2. 7 3. 1 3. 5 3. 0 3. 1 3. 3 2. 7 2. 6 3. 0 3. 4 2. 8 ITSEC/CC 3. 9 3. 7 2. 5 3. 0 2. 6 1. 7 2. 5 2. 8 2. 0 Scores between 1 (low) and 4 (high) - Scores for Cobi. T, BS 7799, BSI from ISACA Swiss chapter; score for ITSEC/CC form H. P. Winiger IT Audit Methodoloies
Comparison of Methods - Results Cobi. T Standardisation Independence Certifyability Applicability in practice Adaptability Extent of Scope Presentation of Results Efficiency Update frequency Ease of Use 3. 4 3. 3 2. 7 2. 8 3. 3 3. 1 1. 9 3. 0 3. 1 2. 3 BS 7799 BSI 3. 3 3. 6 3. 3 3. 0 2. 8 2. 9 2. 2 2. 8 2. 4 2. 7 3. 1 3. 5 3. 0 3. 1 3. 3 2. 7 2. 6 3. 0 3. 4 2. 8 ITSEC/CC 3. 9 3. 7 2. 5 3. 0 2. 6 1. 7 2. 5 2. 8 2. 0 Scores between 1 (low) and 4 (high) - Scores for Cobi. T, BS 7799, BSI from ISACA Swiss chapter; score for ITSEC/CC form H. P. Winiger IT Audit Methodoloies
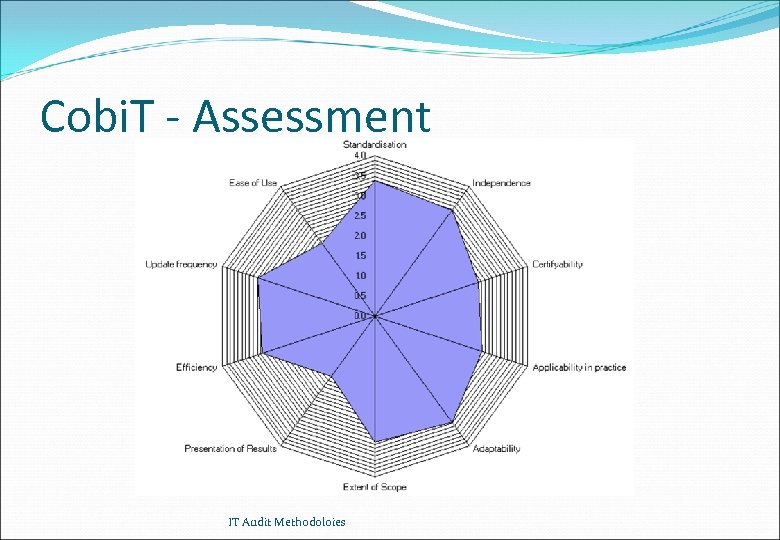 Cobi. T - Assessment IT Audit Methodoloies
Cobi. T - Assessment IT Audit Methodoloies
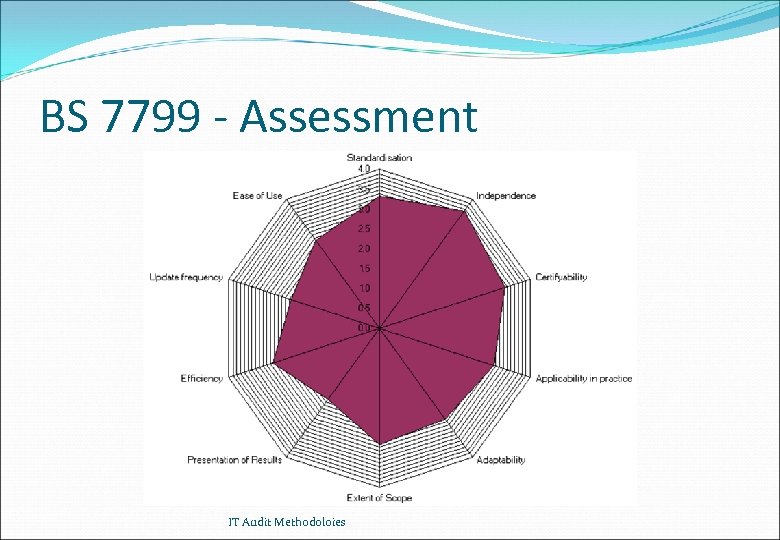 BS 7799 - Assessment IT Audit Methodoloies
BS 7799 - Assessment IT Audit Methodoloies
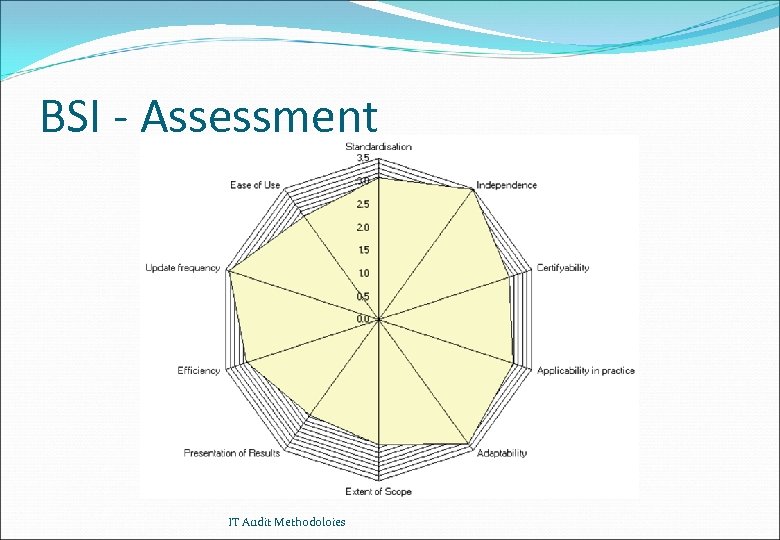 BSI - Assessment IT Audit Methodoloies
BSI - Assessment IT Audit Methodoloies
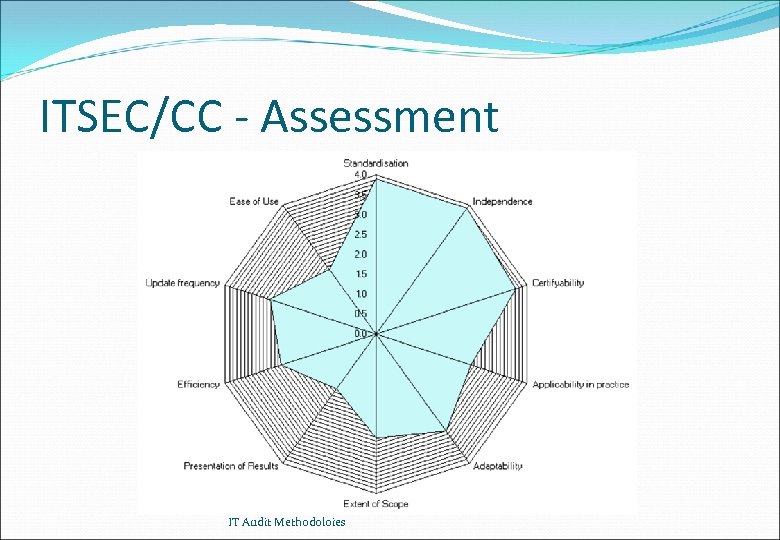 ITSEC/CC - Assessment IT Audit Methodoloies
ITSEC/CC - Assessment IT Audit Methodoloies
 Use of Methods for IT Audits Cobi. T: Audit method for all IT processes ITSEC, CC: Systematic approach for evaluations BS 7799, BSI: List of detailed security measures to be used as best practice documentation Detailed audit plans, checklists, tools for technical audits (operating systems, LANs, etc. ) What is needed in addition: Audit concept (general aspects, infrastructure audits, application audits) IT Audit Methodoloies
Use of Methods for IT Audits Cobi. T: Audit method for all IT processes ITSEC, CC: Systematic approach for evaluations BS 7799, BSI: List of detailed security measures to be used as best practice documentation Detailed audit plans, checklists, tools for technical audits (operating systems, LANs, etc. ) What is needed in addition: Audit concept (general aspects, infrastructure audits, application audits) IT Audit Methodoloies


