00330cb0be4d7f6db6c00035eec8f78b.ppt
- Количество слайдов: 18

ISTPA Privacy Framework John T. Sabo Computer Associates IAPP-TRUSTe Symposium June 9, 2004 Copyright © 1999 -2003 International Security, Trust & Privacy Alliance All Rights Reserved

Context-Hard Problem u Multidimensional Privacy § Legal, regulatory, social, economic, political, moral and ethical dimensions u Variable Nature § Changes with context, audience “privacy is contextual and personal” u Privacy is plagued by lack of a: § Common vocabulary § Shared reference model and framework § Structured and uniform means of analysis u Sort out the issues, understand communicate the underlining requirements 2

ISTPA’s Approach n Resolution-Solution Focus u Transform Privacy Policy to Privacy Science & Engineering Discipline u Build and Forward Open Multidisciplinary Standards, Specifications and Unified Approach (Methodology) § Shared privacy vocabulary (terms, notation) § Open policy configurable framework § Standardized Set of Industry Specific Use Cases u Privacy Framework as Platform for Multidisciplinary Collaboration § Regulators, lawyers, law makers, corporate policy makers, business and product managers, citizen-consumers, privacy advocates, IT and security professionals, technologist 3

Framework Defined n Privacy Framework u An open, policy configurable set of collaborating services and capabilities used to guide the analysis, design and implementation and assessment of security, trust and privacy solutions and infrastructure 4

ISTPA Privacy Framework Services & Capabilities n n n n n Audit – independent, verifiable accountability Certification – credentials, trusted processes Control - only permissible access to data Enforcement - redress when violation Interaction - manages data/preferences Negotiation – of agreements, rules, privileges Validation - checks accuracy of personal information Access - subject can correct/update information Agent – software that acts on behalf of data subject Usage – data use, aggregation, anonymization 5

ISTPA Privacy Framework 6

Framework: PI Container n Binding of n PI n Contract n Credentials n 7

ISTPA Privacy Framework n n n 8 A set of collaborating services and capabilities (layer) Security Foundation (layer) Legal, Regulatory & Policy Context

Layers and Context 9

Translating Privacy Law and Practices into Infrastructure n Privacy Fair Information Practices and Translation to the Real World Infrastructure 10
Services, Capabilities vs. Mechanisms u u Services & Capabilities – Defined functionality (what) supporting privacy and security requirements Mechanisms –Specific service and capability implementations (how) supporting defined services and capabilities § Protocols, technologies, infrastructure – Smart cards, Trusted platforms, SAML, cryptographic tools, secure hash, symmetric keys, P 3 P, EPAL, XACML 11

Reference Model Approach ISTPA Privacy Framework as Reference Model Service/Capability Certification Validation Negotiation Usage Function Organizations/Protocols/Mechanisms credentials, trusted processes BBBOnline, Better. Web, E-Safe, Global Trust Alliance, Guardian e. Commerce Security, Net-Ethix, Privacy License, Privacy Secure, Inc. , Privacy. Bot. com, Secure. Biz, TRUSTe, Web. Trust checks accuracy of personal information Audit Check Services, Certificate Authorities, Credit Check Services, of agreements, rules, privileges APPEL, P 3 P, License Script, FDRM, ODRL, Xr. ML data use, aggregation, anonymization Trusted Computing Group, Trusted Platforms, Smartcards, Secure Tokens Security Foundation Mechanisms AES, MD 5, Authentication, Non-Repudiation, Access Control, Integrity, Confidentiality, Availability, PKI Legal Context Legal, Regulatory, Policy EU Data Protection Directive, HIPAA, GLBA, COPPA, Privacy Act 12

ISTPA Project Areas n Framework Projects ISO Publicly Available Specification (PAS) u Privacy Capability Maturity Model u Privacy Tools & Technology u § Privacy Rule Language (IBM’s EPAL) § Identity Management Systems 13

Questions? John T. Sabo john. t. sabo@ca. com www. istpa. org 14

Backup

Privacy Framework Services Service / Capability Description Audit Handles the recording and maintenance of events in any service to capture the data that is necessary to ensure compliance with the terms and policies of an agreement and any applicable regulations. Certification Manages and validates the credentials of any party or process involved in processing of a PI transaction. Control Enforcement Interaction Negotiation Validation Functions as “repository gatekeeper” to ensure that access to PI which is stored by a data collection entity complies with the terms and policies of an agreement and any applicable regulations. Handles redress when a data collection entity is not in conformance with the terms and policies of an agreement and any applicable regulations. Presents proposed agreements from a data collection entity to the data subject; receives the subject’s personal information, preferences, and actions; confirms actions; manages movement of data into and out of the Framework. To the extent the data subject is represented by an agent, this service comprises the interface to the agent. Handles arbitration of a proposal between a data collection entity and a data subject. Successful negotiation results in an agreement. Humans, agents, or any combination, can handle negotiation. Checks for accuracy of PI at any point in its life cycle. 16

Privacy Framework Capabilities Service / Capability Description A capability that allows the data subject to both access the Access individual’s PI that is held by a data collection entity, and to correct or update it as necessary. Agent A software capability that acts on behalf of a data subject or a requestor. The Agent Capability engages with one or more of the other services defined in this Framework. Agent can also refer to the human data subject in the case of a manual process. Usage Functions as “processing monitor” to ensure that active use of PI complies with the terms and policies of an agreement and any applicable regulations. Such uses may include transfer, derivation, aggregation, anonymization, linking, and inference of data. 17
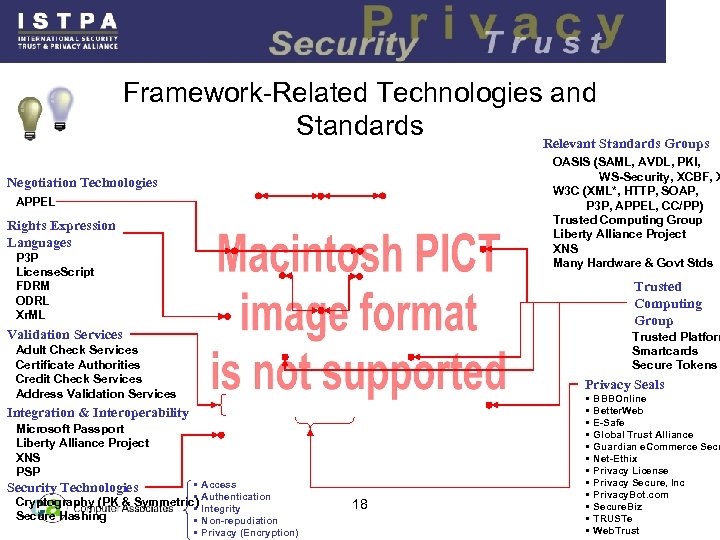
Framework-Related Technologies and Standards Relevant Standards Groups OASIS (SAML, AVDL, PKI, WS-Security, XCBF, X W 3 C (XML*, HTTP, SOAP, P 3 P, APPEL, CC/PP) Trusted Computing Group Liberty Alliance Project XNS Many Hardware & Govt Stds Negotiation Technologies APPEL Rights Expression Languages P 3 P License. Script FDRM ODRL Xr. ML Trusted Computing Group Validation Services Trusted Platform Smartcards Secure Tokens Adult Check Services Certificate Authorities Credit Check Services Address Validation Services Privacy Seals Integration & Interoperability Microsoft Passport Liberty Alliance Project XNS PSP • Access • Authentication Cryptography (PK & Symmetric) Integrity • Secure Hashing • Non-repudiation • Privacy (Encryption) Security Technologies 18 • • • BBBOnline Better. Web E-Safe Global Trust Alliance Guardian e. Commerce Secu Net-Ethix Privacy License Privacy Secure, Inc Privacy. Bot. com Secure. Biz TRUSTe Web. Trust
00330cb0be4d7f6db6c00035eec8f78b.ppt