d3f63e7d35d8ed70f32c70690c9a7f2f.ppt
- Количество слайдов: 31

ISSAP Session 4 Cryptography 2 12 September 2011

Cryptography 2 • Questions from Session 3 ? • Session 1, 2, &3 handout is posted on www. silverbulletinc. com/DM 2 • Contact Shelton Lee for credentials – Shelton. lee@lmco. com • Should have book by now. If not contact Paola Aviles (paola. aviles @lmco. com – Must have
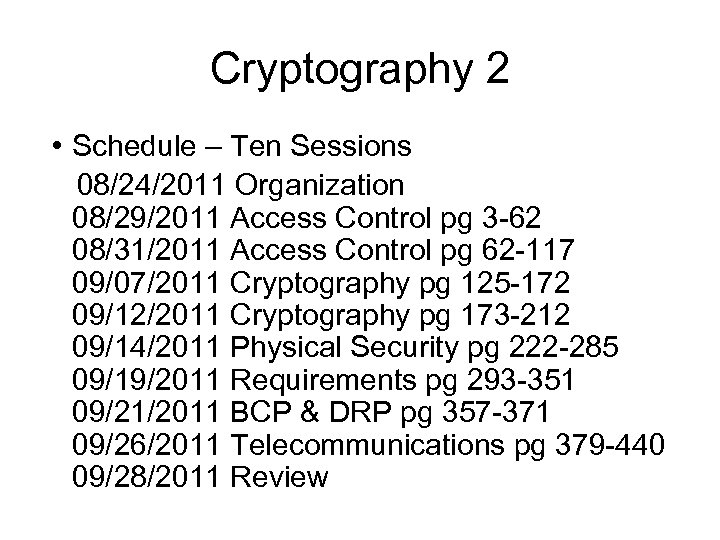
Cryptography 2 • Schedule – Ten Sessions 08/24/2011 Organization 08/29/2011 Access Control pg 3 -62 08/31/2011 Access Control pg 62 -117 09/07/2011 Cryptography pg 125 -172 09/12/2011 Cryptography pg 173 -212 09/14/2011 Physical Security pg 222 -285 09/19/2011 Requirements pg 293 -351 09/21/2011 BCP & DRP pg 357 -371 09/26/2011 Telecommunications pg 379 -440 09/28/2011 Review

Cryptography 2 • Public Key Infrastructure (PKI) – Certificates, Certificate Framework (RFC 3647), Certificate Policy Statements (CPS), Key Recovery Policy (KRP), & Certificate Revocation List (CRL) • "a CPS is a statement of the practices which a certification authority employs in issuing certificates. " – Is a matter of trust • Subscribers • Relying Parties • Certificate Authority

Cryptography 2 • Single Key Pair – All that is needed technically – Lawyers made complicated • One for encryption (may be ecrowed) • One for signing (must be non-repudiatable) • One for Identification (cannot use signing key for. ID) • Interoperability and Integration – Federal Bridge – Federation

Cryptography 2 • Key Distribution – Symmetric keys require secure distrobution – Public Key does not • Private key must be kept secure • Only one party has private key – Best Security: private keys never leave physical device • No backup or recovery – Binding: Public key is bound to individual through signing by CA
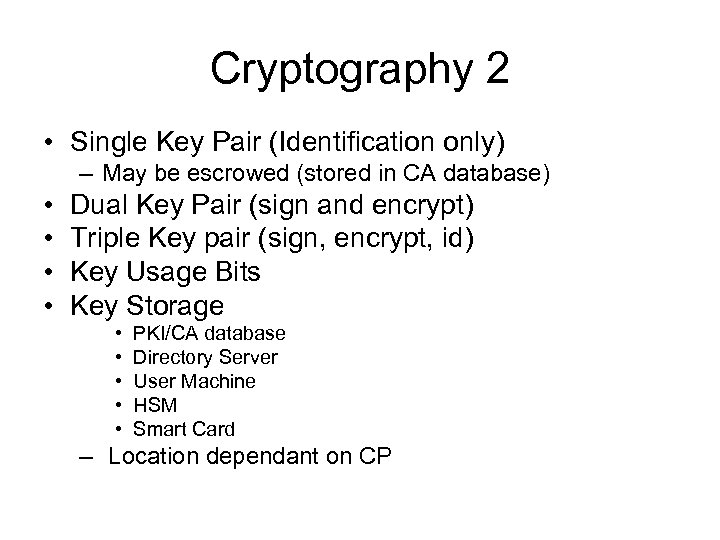
Cryptography 2 • Single Key Pair (Identification only) – May be escrowed (stored in CA database) • • Dual Key Pair (sign and encrypt) Triple Key pair (sign, encrypt, id) Key Usage Bits Key Storage • • • PKI/CA database Directory Server User Machine HSM Smart Card – Location dependant on CP

Cryptography 2 10 02 1: . . INTEGER 2 13 02 16: . . INTEGER : . . . 7 C 09 A 1 D 1 9 B DD 2 E BC 4 F D 1 27 0 C 10 AE 8 F 9 B 33 06 9: . . . OBJECT IDENTIFIER : . . sha 1 with. RSAEncryption (1 2 840 113549 1 1 5) 53 06 3: . . . OBJECT IDENTIFIER country. Name (2 5 4 6) 58 13 2: . . . Printable. String 'US' 66 06 3: . . . OBJECT IDENTIFIER state. Or. Province. Name (2 5 4 8) 71 13 7: . . . Printable. String 'Florida' 89 13 7: . . . Printable. String 'Orlando' 107 13 27: . . . Printable. String 'Lockheed Martin Corporation' 145 13 3: . . . Printable. String 'EIS' 159 13 35: . . . Printable. String 'Lockheed Martin Corporation Root CA' 198 17 13: . . . UTCTime '021205150439 Z' 213 17 13: . . . UTCTime '130509171644 Z' 235 06 3: . . . OBJECT IDENTIFIER country. Name (2 5 4 6) 240 13 2: . . . Printable. String 'US' 253 13 7: . . . Printable. String 'Florida' 271 13 7: . . . Printable. String 'Orlando' 289 13 27: . . . Printable. String 'Lockheed Martin Corporation' 327 13 3: . . . Printable. String 'EIS' 341 13 35: . . . Printable. String 'Lockheed Martin Corporation Root CA'
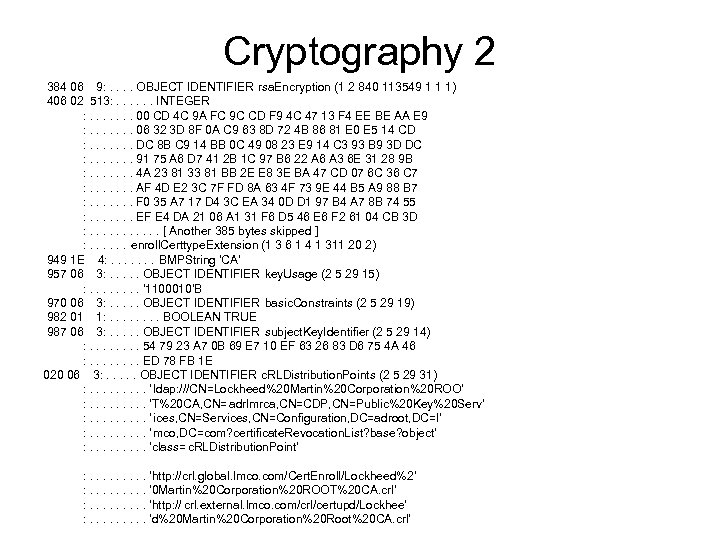
Cryptography 2 384 06 9: . . OBJECT IDENTIFIER rsa. Encryption (1 2 840 113549 1 1 1) 406 02 513: . . . INTEGER : . . . . 00 CD 4 C 9 A FC 9 C CD F 9 4 C 47 13 F 4 EE BE AA E 9 : . . . . 06 32 3 D 8 F 0 A C 9 63 8 D 72 4 B 86 81 E 0 E 5 14 CD : . . . . DC 8 B C 9 14 BB 0 C 49 08 23 E 9 14 C 3 93 B 9 3 D DC : . . . . 91 75 A 6 D 7 41 2 B 1 C 97 B 6 22 A 6 A 3 6 E 31 28 9 B : . . . . 4 A 23 81 33 81 BB 2 E E 8 3 E BA 47 CD 07 6 C 36 C 7 : . . . . AF 4 D E 2 3 C 7 F FD 8 A 63 4 F 73 9 E 44 B 5 A 9 88 B 7 : . . . . F 0 35 A 7 17 D 4 3 C EA 34 0 D D 1 97 B 4 A 7 8 B 74 55 : . . . . EF E 4 DA 21 06 A 1 31 F 6 D 5 46 E 6 F 2 61 04 CB 3 D : . . . [ Another 385 bytes skipped ] : . . . enroll. Certtype. Extension (1 3 6 1 4 1 311 20 2) 949 1 E 4: . . . . BMPString 'CA' 957 06 3: . . . OBJECT IDENTIFIER key. Usage (2 5 29 15) : . . . . '1100010'B 970 06 3: . . . OBJECT IDENTIFIER basic. Constraints (2 5 29 19) 982 01 1: . . . . BOOLEAN TRUE 987 06 3: . . . OBJECT IDENTIFIER subject. Key. Identifier (2 5 29 14) : . . . . 54 79 23 A 7 0 B 69 E 7 10 EF 63 26 83 D 6 75 4 A 46 : . . . . ED 78 FB 1 E 020 06 3: . . . OBJECT IDENTIFIER c. RLDistribution. Points (2 5 29 31) : . . ' ldap: ///CN=Lockheed%20 Martin%20 Corporation%20 ROO' : . . 'T%20 CA, CN= adrlmrca, CN=CDP, CN=Public%20 Key%20 Serv' : . . ' ices, CN=Services, CN=Configuration, DC=adroot, DC=l' : . . ' mco, DC=com? certificate. Revocation. List? base? object' : . . 'class= c. RLDistribution. Point' : . . 'http: //crl. global. lmco. com/Cert. Enroll/Lockheed%2' : . . '0 Martin%20 Corporation%20 ROOT%20 CA. crl' : . . 'http: // crl. external. lmco. com/crl/certupd/Lockhee' : . . 'd%20 Martin%20 Corporation%20 Root%20 CA. crl'

Cryptography 2 : . . . authority. Info. Access (1 3 6 1 5 5 7 1 1) : . . ca. Issuers (1 3 6 1 5 5 7 48 2) : . . ' ldap: ///CN=Lockheed%20 Martin%20 Corporation%20 ROO' : . . 'T%20 CA, CN=AIA, CN=Public%20 Key%20 Services, CN=Serv' : . . ' ices, CN=Configuration, DC=adroot, DC=lmco, DC=com? c' : . . ' ACertificate? base? objectclass=certification. Autho' : . . ' rity' : . . ca. Issuers (1 3 6 1 5 5 7 48 2) : . . 'http: // crl. global. lmco. com/Cert. Enroll/adrlmrca. a' : . . 'droot. lmco. com_Lockheed%20 Martin%20 Corporation%2' : . . '0 Root%20 CA(9). crt' : . . 'http: // crl. external. lmco. com/crl/certupd/Lockhee' : . . 'd%20 Martin%20 Corporation%20 Root%20 CA(9). crt' 1938 06 9: . . OBJECT IDENTIFIER : . . . sha 1 with. RSAEncryption (1 2 840 113549 1 1 5) 1949 05 0: . . NULL : . . } 1951 03 513: . BIT STRING 0 unused bits : . . 7 C 77 55 2 A EF C 8 E 2 31 9 C F 4 14 B 1 6 B 55 7 E E 0 : . . 74 32 42 F 9 63 29 91 23 E 0 07 AF 86 C 8 02 44 BE : . . B 3 BC EE 18 AC D 7 A 4 59 4 B 64 F 4 21 B 7 87 61 19 : . . BB 87 AD 86 6 E 14 EA E 4 A 7 D 2 FE 48 4 C D 3 E 6 : . . 07 43 51 A 8 04 EA 57 11 F 0 4 E E 3 D 6 4 E D 9 A 6 5 B : . . 81 3 B CA 9 D 76 89 14 F 2 64 FB D 8 3 F 28 AD 36 80 : . . 54 5 D ED 2 B AD 7 D 5 E 1 D 6 C 3 D BB 14 28 05 8 E 9 B : . . 68 F 3 B 5 6 E F 0 4 D 32 0 A A 6 FA F 9 13 B 4 78 2 E 00 : . . . [ Another 384 bytes skipped ]

Cryptography 2 RFC 2457 Key. Usage : : = BIT STRING { (reversed in ASN 1 digital. Signature (0), 0 00000001 non. Repudiation (1), 0 00000010 key. Encipherment (2), 0 00000100 data. Encipherment (3), 0 00001000 key. Agreement (4), 0 00010000 key. Cert. Sign (5), 0 00100000 c. RLSign (6), 0 01000000 encipher. Only (7), 0 10000000 decipher. Only (8), 1 0000 "The digital. Signature bit is asserted when the subject public key is used with a digital signature mechanism to support security services other than non-repudiation " (e. g ID cert. LM Root Cert 01100010 Non-Repudiation, Certificate Signing, CRL Signing ) Few get it right

Cryptography 2 • PKI Registration – Many components: Technical Infrastructure, Policies, Procedures, People (PKIREGAG) • Acronym seems unique to publication – Depends on Certificate policy • Can get a Verisign class 1 for my cat. – Poof of organization, entity, key • Proofing/vetting an important part of cert • Federations require levels of proofing • I-9 authentication – Immigration Reform and Control Act (IRCA) of 1986

Cryptography 2 • Individual Authentication – Password – Challenge response question – Face to Face (Personal recognition) • Expensive • High risk, responsibility, value – Proof of possession • Have private key • Prior certification

Cryptography 2 • Certificate Issuance • X. 509 – Key usage bit – Trusted as signer is trusted – Certificate Template (part of CPS) • Trust Models • PKI represents trust relationship – Root CA is anchor – Intermediate part of chain – Inherited trust

Cryptography 2 • Subordinate CAs – Different functions/policies e. g. signing vs encryption. – Can be any number of levels providing each can do signing • Cross-certified mesh – Good for non-inheritable – Each signs other’s – More than two: web of trust • Bridge CA – Federal Bridge • Has own specific requirements • Manages cross certification • Large number of “trusted roots”

Cryptography 2 • Certificate chain – Validity and life of complete chain • If any element expires, so does trust – Higher levels require higher security – CRL publishing – Hierarchial mode • Certificate Revocation – Private key compromised or person loses trust – Described in CPL – Included in Cert • Relying party only required to check CRL • CRL may get very large – One reason to retire CA
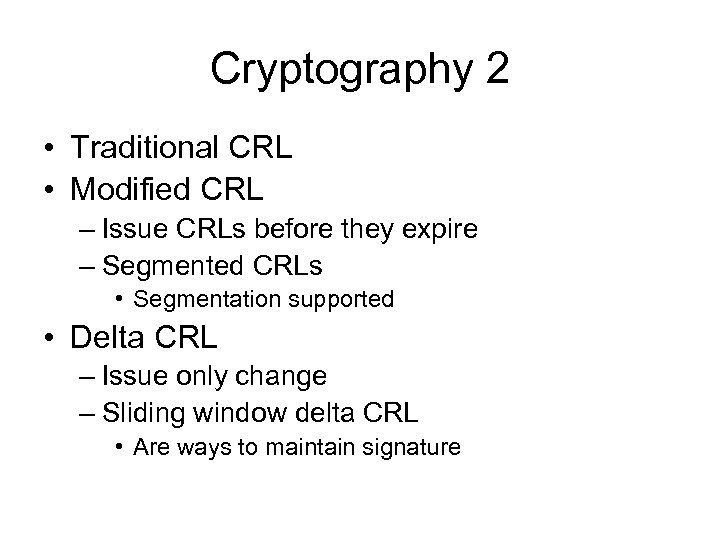
Cryptography 2 • Traditional CRL • Modified CRL – Issue CRLs before they expire – Segmented CRLs • Segmentation supported • Delta CRL – Issue only change – Sliding window delta CRL • Are ways to maintain signature

Cryptography 2 • OCSP Online Certificate Status Protocol – Signed response – Asks if valid (Good, Revoked, Unknown)

Cryptography 2 • Cross Certification – Each signs other’s root – Each root can verify other – Each root can request other’s CRL • A’s key is in B’s directory – Online or offline – Cross certification revocation • Can be done by any • Effect is local

Cryptography 2 • Cross Certification with bridge – Bridge signs each member’s key – Each member trusts bridge – Can accept or revoke bridge but bridge must revoke members

Cryptography 2 • Cytanalytic attack – Cypertext only • Brute force • Most difficult • Hard to recognize success – Known plain text • Final test can be XOR • All trials assume – Chosen Plaintext • Forced crypto • Seed issue in SSL – Chosen ciphertext • Look for patterns

Cryptography 2 • Assymetric Attacks – So far all take years (theoretically) – Largest “crack” was RSA 129 (430 bits) • Even 1024 is exponentially more difficult • NIST moving to 2048 bit minimum • Hash function attacks – MD 5 broken – SHA not broken but deprecated – Crack vs collision (birthday)

Cryptography 2 • Network based attacks – Man in the Middle (MITM) • SSL – Relies on parties not validating – May work with v 2 not with v 3/TLS – Replay attack • Hashed passwords (Netware 4. 0) • IPSec has protections – Traffic analysis • May provide “known plaintext”

Cryptography 2 • Attacks against keys – Meet in the middle • Attack against 3 DES (encrypt-decrypt-encrypt) • Why 2 DES never worked • Reduces effect of 3 DES to 112 bits – Related Key • WEP – clear IV/RC 4 • Brute Force – Simply trying every possible key – Last resort unless key is short – NTLM and Rainbow Tables

Cryptography 2 • Side Channel Attacks – Leakage – Timing – Differential Fault – Differential power consumption

Cryptography 2 • Risk Based Cryptographic Architecture – Hardware and software based components – Security of cryptographic modules – Network environment – Algorithms and key length – Key Management – Hosting infrastructure – User interface/acceptance/training • Include social engineering

Cryptography 2 • Identifying risk – Table from NIST 800 -21 • Cryptographic Compliance Monitoring – Use only FIPS evaluated products – NSA suite B

Cryptography 2 • Compliance Defects – Authentication of user – Authenticate the CA – CRLs – Private key management – Passphrase quality

Cryptography 2 • Regulation – SB 1386 – PCI DSS (2. 0) – HIPAA • • • Access controls Audit controls Integrity Person or entity authentication Transmission security DS – integrity, non-repudiation, authentication

Cryptography 2 • International Laws – EU Data Protection Article 17 • “appropriate controls and technical measures” • Audit – All elements must support auditability • Say what you do, do what you say.

Cryptography 2 • End of Cryptography session 2 • Will continue with Physical Security on 14 September • Questions ?
d3f63e7d35d8ed70f32c70690c9a7f2f.ppt