cbd08cc19bde58fa18566ecd76fb3a7e.ppt
- Количество слайдов: 56
 ISA 662 Information System Security Authentication 1
ISA 662 Information System Security Authentication 1
 Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 2
Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 2
 Basic Concept n Authentication: to prove an identity n n Based on n n Strong authentication: without transmitting password What the user knows – e. g. , password, PIN What the user possesses – e. g. , ID card, ticket What the user is – e. g. , fingerprint, eye scanning, DNA Attack n n Active: e. g. , password guessing, stealing password file from server, authentication replay Passive: e. g. , password sniffer 3
Basic Concept n Authentication: to prove an identity n n Based on n n Strong authentication: without transmitting password What the user knows – e. g. , password, PIN What the user possesses – e. g. , ID card, ticket What the user is – e. g. , fingerprint, eye scanning, DNA Attack n n Active: e. g. , password guessing, stealing password file from server, authentication replay Passive: e. g. , password sniffer 3
 Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 4
Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 4
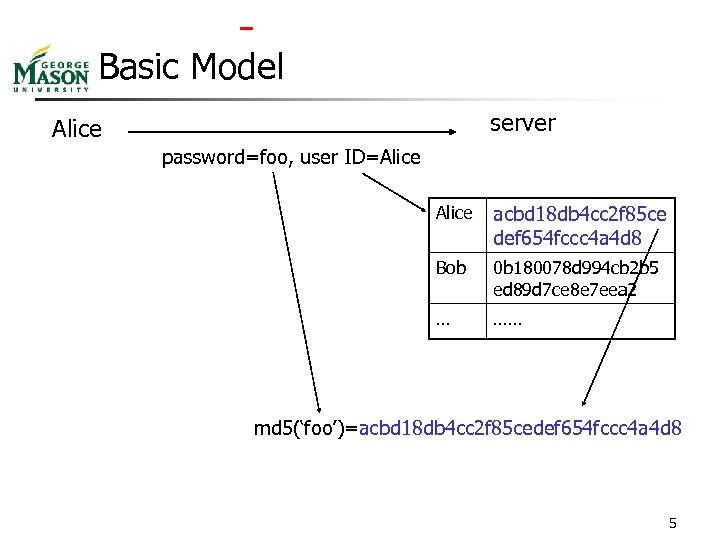 Basic Model server Alice password=foo, user ID=Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 Bob 0 b 180078 d 994 cb 2 b 5 ed 89 d 7 ce 8 e 7 eea 2 … …… md 5(‘foo’)=acbd 18 db 4 cc 2 f 85 cedef 654 fccc 4 a 4 d 8 5
Basic Model server Alice password=foo, user ID=Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 Bob 0 b 180078 d 994 cb 2 b 5 ed 89 d 7 ce 8 e 7 eea 2 … …… md 5(‘foo’)=acbd 18 db 4 cc 2 f 85 cedef 654 fccc 4 a 4 d 8 5
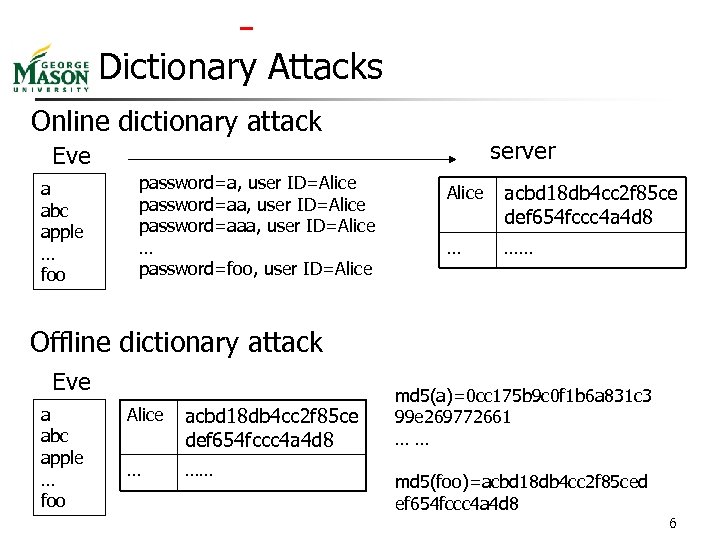 Dictionary Attacks Online dictionary attack server Eve a abc apple … foo password=a, user ID=Alice password=aaa, user ID=Alice … password=foo, user ID=Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… Offline dictionary attack Eve a abc apple … foo Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… md 5(a)=0 cc 175 b 9 c 0 f 1 b 6 a 831 c 3 99 e 269772661 …… md 5(foo)=acbd 18 db 4 cc 2 f 85 ced ef 654 fccc 4 a 4 d 8 6
Dictionary Attacks Online dictionary attack server Eve a abc apple … foo password=a, user ID=Alice password=aaa, user ID=Alice … password=foo, user ID=Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… Offline dictionary attack Eve a abc apple … foo Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… md 5(a)=0 cc 175 b 9 c 0 f 1 b 6 a 831 c 3 99 e 269772661 …… md 5(foo)=acbd 18 db 4 cc 2 f 85 ced ef 654 fccc 4 a 4 d 8 6
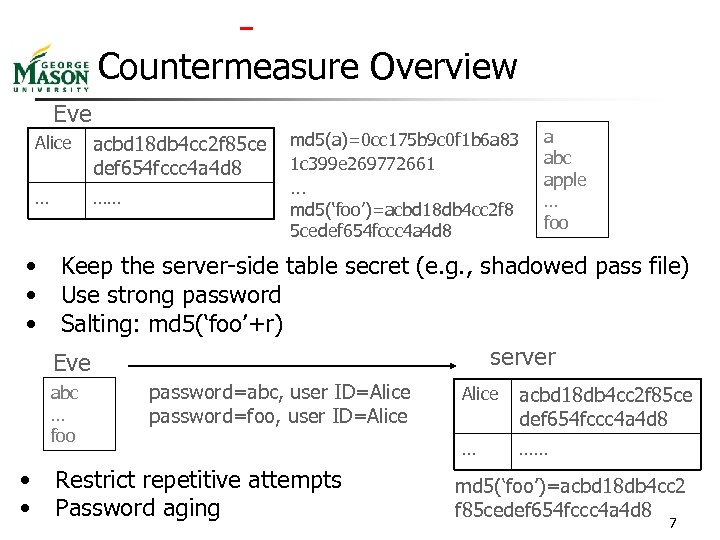 Countermeasure Overview Eve Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… • • • … md 5(‘foo’)=acbd 18 db 4 cc 2 f 8 5 cedef 654 fccc 4 a 4 d 8 a abc apple … foo Keep the server-side table secret (e. g. , shadowed pass file) Use strong password Salting: md 5(‘foo’+r) server Eve abc … foo • • md 5(a)=0 cc 175 b 9 c 0 f 1 b 6 a 83 1 c 399 e 269772661 password=abc, user ID=Alice password=foo, user ID=Alice Restrict repetitive attempts Password aging Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… md 5(‘foo’)=acbd 18 db 4 cc 2 f 85 cedef 654 fccc 4 a 4 d 8 7
Countermeasure Overview Eve Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… • • • … md 5(‘foo’)=acbd 18 db 4 cc 2 f 8 5 cedef 654 fccc 4 a 4 d 8 a abc apple … foo Keep the server-side table secret (e. g. , shadowed pass file) Use strong password Salting: md 5(‘foo’+r) server Eve abc … foo • • md 5(a)=0 cc 175 b 9 c 0 f 1 b 6 a 83 1 c 399 e 269772661 password=abc, user ID=Alice password=foo, user ID=Alice Restrict repetitive attempts Password aging Alice acbd 18 db 4 cc 2 f 85 ce def 654 fccc 4 a 4 d 8 … …… md 5(‘foo’)=acbd 18 db 4 cc 2 f 85 cedef 654 fccc 4 a 4 d 8 7
 Choice of Passwords n Dilemma n Password should be random n n n Uniform distribution maximizes entropy (hence dictionary) Password should be easy to remember Attacker sorts dictionary in descending order of likelihood n An easy-to-remember password requires less time to guess 8
Choice of Passwords n Dilemma n Password should be random n n n Uniform distribution maximizes entropy (hence dictionary) Password should be easy to remember Attacker sorts dictionary in descending order of likelihood n An easy-to-remember password requires less time to guess 8
 Choice of Passwords (Cont’d) n Users tend to choose weak passwords n n Based on user ID, user or relative’s name, computer name, place name, DOB English words Too short, digits only, letters only License plates, acronyms, SSN, pet name, job, etc. 9
Choice of Passwords (Cont’d) n Users tend to choose weak passwords n n Based on user ID, user or relative’s name, computer name, place name, DOB English words Too short, digits only, letters only License plates, acronyms, SSN, pet name, job, etc. 9
 Choice of Passwords (Still Cont’d) n Force user to choose good passwords n n Through education and policy Through proactive mechanism n n n Cannot be bypassed Knows what is bad password Discriminate on per-user, per-site basis 10
Choice of Passwords (Still Cont’d) n Force user to choose good passwords n n Through education and policy Through proactive mechanism n n n Cannot be bypassed Knows what is bad password Discriminate on per-user, per-site basis 10
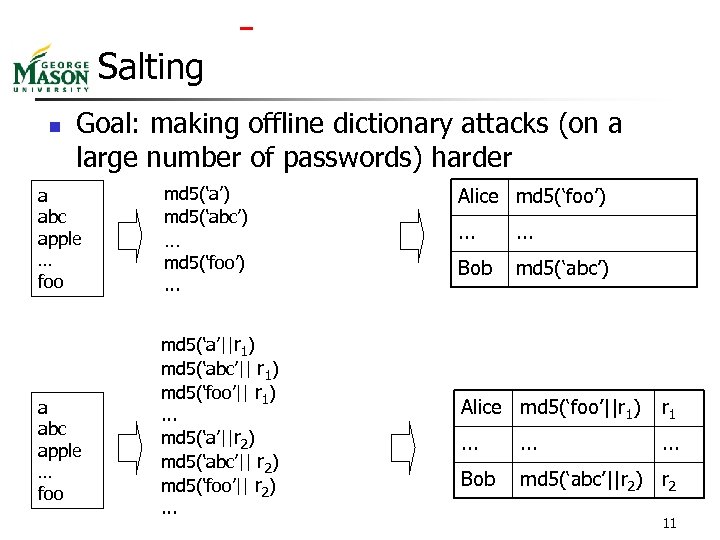 Salting n Goal: making offline dictionary attacks (on a large number of passwords) harder a abc apple … foo md 5(‘a’) md 5(‘abc’) … md 5(‘foo’). . . md 5(‘a’||r 1) md 5(‘abc’|| r 1) md 5(‘foo’|| r 1). . . md 5(‘a’||r 2) md 5(‘abc’|| r 2) md 5(‘foo’|| r 2). . . Alice md 5(‘foo’). . . Bob md 5(‘abc’) Alice md 5(‘foo’||r 1) r 1 . . Bob md 5(‘abc’||r 2) r 2 11
Salting n Goal: making offline dictionary attacks (on a large number of passwords) harder a abc apple … foo md 5(‘a’) md 5(‘abc’) … md 5(‘foo’). . . md 5(‘a’||r 1) md 5(‘abc’|| r 1) md 5(‘foo’|| r 1). . . md 5(‘a’||r 2) md 5(‘abc’|| r 2) md 5(‘foo’|| r 2). . . Alice md 5(‘foo’). . . Bob md 5(‘abc’) Alice md 5(‘foo’||r 1) r 1 . . Bob md 5(‘abc’||r 2) r 2 11
 Example: UNIX Password n UNIX system password authentication n n n First 8 characters of input password Concatenated by a 12 bit salt Used as a key To encrypt a constant For 25 times The result and the salt stored in password file 12
Example: UNIX Password n UNIX system password authentication n n n First 8 characters of input password Concatenated by a 12 bit salt Used as a key To encrypt a constant For 25 times The result and the salt stored in password file 12
 Prevent Repetitive Attempts n Make online attacks harder n n Backoff: wait 2 n seconds before nth attempt Disconnection: modem user Disabling: only administrators can reactivate OSF 1 uses both backoff and disconnection 13
Prevent Repetitive Attempts n Make online attacks harder n n Backoff: wait 2 n seconds before nth attempt Disconnection: modem user Disabling: only administrators can reactivate OSF 1 uses both backoff and disconnection 13
 Password Aging n Force users to change passwords after some time has expired n How do you force users not to re-use passwords? n n n Record previous passwords Block changes for a period of time Give users time to think of good passwords n Warn them of expiration days in advance 14
Password Aging n Force users to change passwords after some time has expired n How do you force users not to re-use passwords? n n n Record previous passwords Block changes for a period of time Give users time to think of good passwords n Warn them of expiration days in advance 14
 Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 15
Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 15
 One-Time Password n Password replay n n Use password exactly once! n n n sniff password then replay How do user and server synchronize? Lamport’s scheme Challenge-response mechanism n View response as the password 16
One-Time Password n Password replay n n Use password exactly once! n n n sniff password then replay How do user and server synchronize? Lamport’s scheme Challenge-response mechanism n View response as the password 16
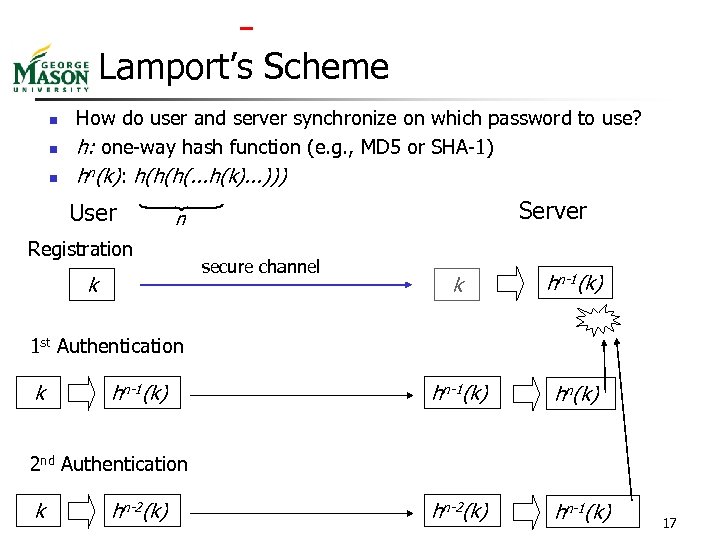 Lamport’s Scheme n n n How do user and server synchronize on which password to use? h: one-way hash function (e. g. , MD 5 or SHA-1) hn(k): h(h(h(. . . h(k). . . ))) User Server n Registration k secure channel k n-1(k) hn(k) hn-2(k) hn-1(k) 1 st Authentication k hn-1(k) 2 nd Authentication k hn-2(k) 17
Lamport’s Scheme n n n How do user and server synchronize on which password to use? h: one-way hash function (e. g. , MD 5 or SHA-1) hn(k): h(h(h(. . . h(k). . . ))) User Server n Registration k secure channel k n-1(k) hn(k) hn-2(k) hn-1(k) 1 st Authentication k hn-1(k) 2 nd Authentication k hn-2(k) 17
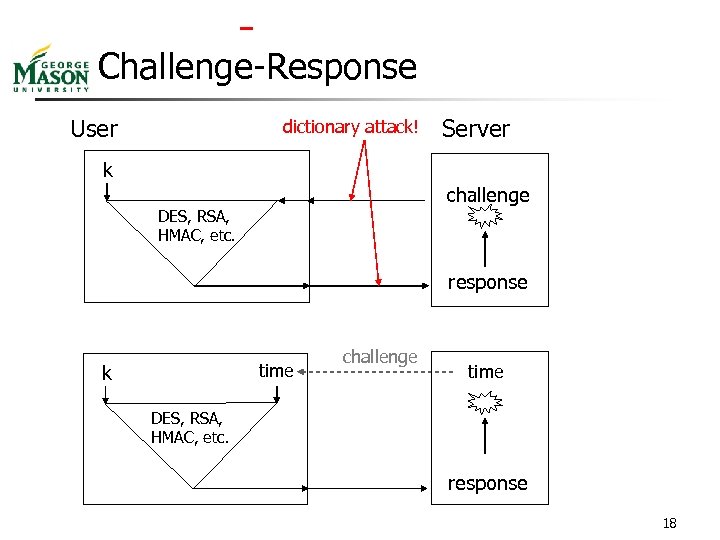 Challenge-Response User dictionary attack! Server k challenge DES, RSA, HMAC, etc. response time k challenge time DES, RSA, HMAC, etc. response 18
Challenge-Response User dictionary attack! Server k challenge DES, RSA, HMAC, etc. response time k challenge time DES, RSA, HMAC, etc. response 18
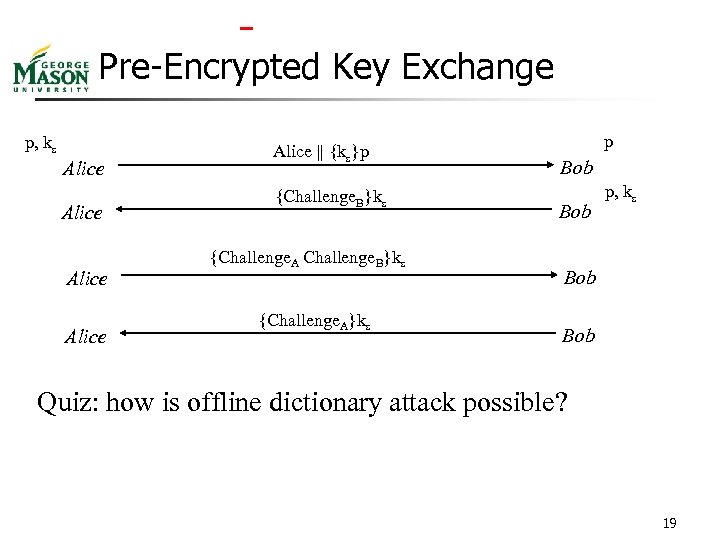 Pre-Encrypted Key Exchange p, ks Alice Alice || {ks}p {Challenge. B}ks {Challenge. A}ks p Bob p, ks Bob Quiz: how is offline dictionary attack possible? 19
Pre-Encrypted Key Exchange p, ks Alice Alice || {ks}p {Challenge. B}ks {Challenge. A}ks p Bob p, ks Bob Quiz: how is offline dictionary attack possible? 19
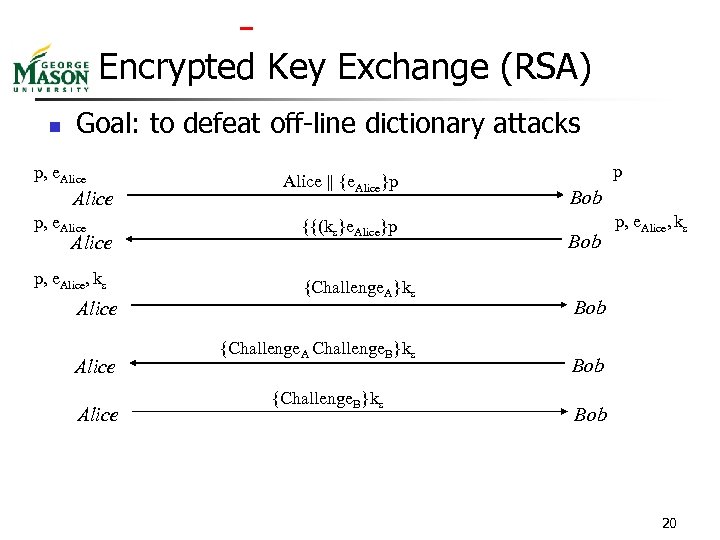 Encrypted Key Exchange (RSA) n Goal: to defeat off-line dictionary attacks p, e. Alice || {e. Alice}p p, e. Alice {{(ks}e. Alice}p p, e. Alice, ks {Challenge. A}ks Alice {Challenge. A Challenge. B}ks {Challenge. B}ks p Bob p, e. Alice, ks Bob Bob 20
Encrypted Key Exchange (RSA) n Goal: to defeat off-line dictionary attacks p, e. Alice || {e. Alice}p p, e. Alice {{(ks}e. Alice}p p, e. Alice, ks {Challenge. A}ks Alice {Challenge. A Challenge. B}ks {Challenge. B}ks p Bob p, e. Alice, ks Bob Bob 20
 Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 21
Chapter 12: Authentication n n Basic Concept Password Challenge-Response Biometrics n and gummy bears 21
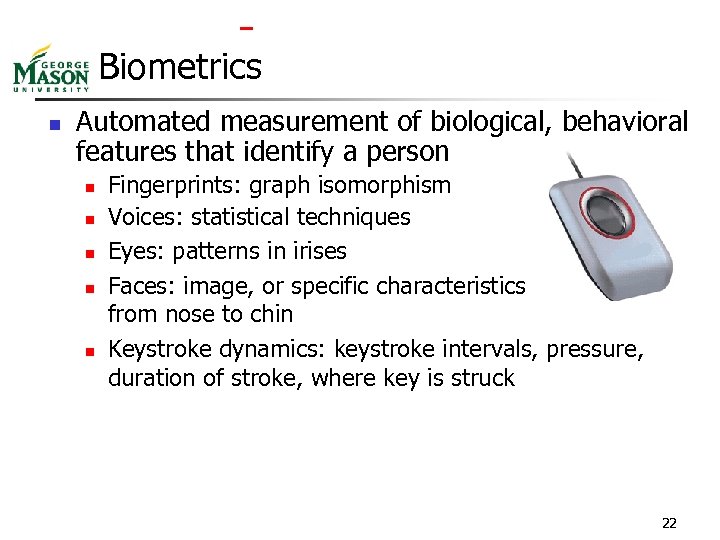 Biometrics n Automated measurement of biological, behavioral features that identify a person n n Fingerprints: graph isomorphism Voices: statistical techniques Eyes: patterns in irises Faces: image, or specific characteristics like distance from nose to chin Keystroke dynamics: keystroke intervals, pressure, duration of stroke, where key is struck 22
Biometrics n Automated measurement of biological, behavioral features that identify a person n n Fingerprints: graph isomorphism Voices: statistical techniques Eyes: patterns in irises Faces: image, or specific characteristics like distance from nose to chin Keystroke dynamics: keystroke intervals, pressure, duration of stroke, where key is struck 22
 Can Biometrics Save the World? n n n Gummy bears say: No! Fingerprint scanners are believed to be very secure, until It was shown they can be reliably fooled with $10 worth of household supplies n n n From both real fingers or residue fingerprints Can wear a transparent fake finger on real finger Using n n n Gelatin, what Gummy Bears are made out of Digital camera, inkjet printer, photo-sensitive PCB, etc. Fool all 11 commercial fingerprint scanners, 80% of time For more details, refer to Tsutomu Matsumoto’s talk ‘Importance of Open Discussion on Adversarial Analyses for Mobile Security Technology’ whose link is on class web page 23
Can Biometrics Save the World? n n n Gummy bears say: No! Fingerprint scanners are believed to be very secure, until It was shown they can be reliably fooled with $10 worth of household supplies n n n From both real fingers or residue fingerprints Can wear a transparent fake finger on real finger Using n n n Gelatin, what Gummy Bears are made out of Digital camera, inkjet printer, photo-sensitive PCB, etc. Fool all 11 commercial fingerprint scanners, 80% of time For more details, refer to Tsutomu Matsumoto’s talk ‘Importance of Open Discussion on Adversarial Analyses for Mobile Security Technology’ whose link is on class web page 23
 Key Points n Authentication is based on n n n what users know what they possess what they are Passwords are here to stay How to use passwords is important Remember the Gummy bears 24
Key Points n Authentication is based on n n n what users know what they possess what they are Passwords are here to stay How to use passwords is important Remember the Gummy bears 24
 ISA 662 Information System Security Identity 25
ISA 662 Information System Security Identity 25
 Overview n n Certificate and distinguished name Web identity and anonymity 26
Overview n n Certificate and distinguished name Web identity and anonymity 26
 Certificates and Identity n Certificates issued to a user n n n User must be uniquely identified for this purpose What to be the identity? Name: usually ambiguous n “Your name please; your address please; your telephone no. please; your last 4 -digit SSN please” 27
Certificates and Identity n Certificates issued to a user n n n User must be uniquely identified for this purpose What to be the identity? Name: usually ambiguous n “Your name please; your address please; your telephone no. please; your last 4 -digit SSN please” 27
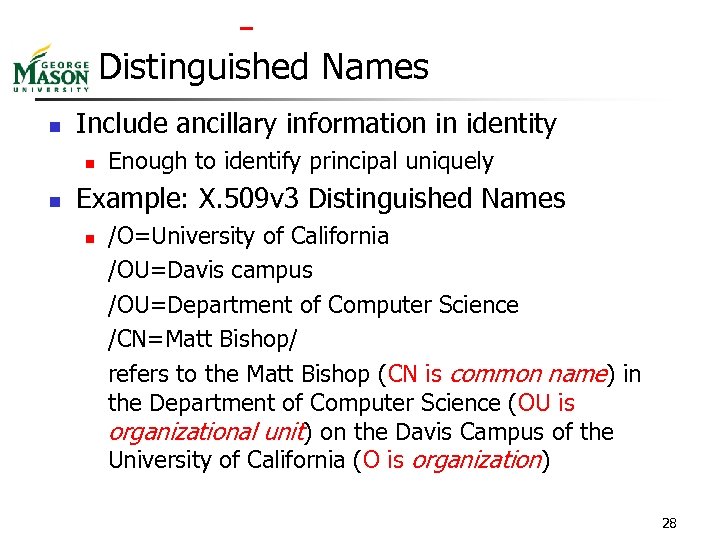 Distinguished Names n Include ancillary information in identity n n Enough to identify principal uniquely Example: X. 509 v 3 Distinguished Names n /O=University of California /OU=Davis campus /OU=Department of Computer Science /CN=Matt Bishop/ refers to the Matt Bishop (CN is common name) in the Department of Computer Science (OU is organizational unit) on the Davis Campus of the University of California (O is organization) 28
Distinguished Names n Include ancillary information in identity n n Enough to identify principal uniquely Example: X. 509 v 3 Distinguished Names n /O=University of California /OU=Davis campus /OU=Department of Computer Science /CN=Matt Bishop/ refers to the Matt Bishop (CN is common name) in the Department of Computer Science (OU is organizational unit) on the Davis Campus of the University of California (O is organization) 28
 CAs and Policies n Matt Bishop wants a certificate from Certs-from-Us n n n How does Certs-from-Us know this is “Matt Bishop”? CA’s authentication policy says what type and strength of authentication is needed to identify Matt Bishop to satisfy the CA that this is, in fact, Matt Bishop CA authenticates user and embed its trust in certificate, later the certificate is used by others for authentication and that trust propagates 29
CAs and Policies n Matt Bishop wants a certificate from Certs-from-Us n n n How does Certs-from-Us know this is “Matt Bishop”? CA’s authentication policy says what type and strength of authentication is needed to identify Matt Bishop to satisfy the CA that this is, in fact, Matt Bishop CA authenticates user and embed its trust in certificate, later the certificate is used by others for authentication and that trust propagates 29
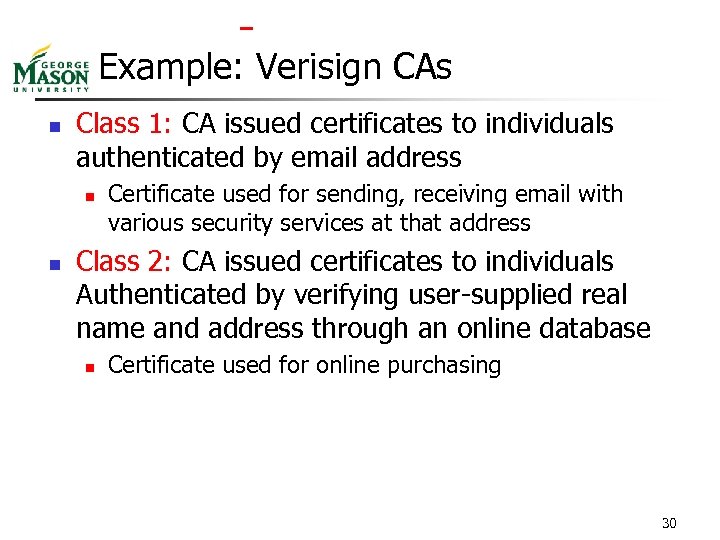 Example: Verisign CAs n Class 1: CA issued certificates to individuals authenticated by email address n n Certificate used for sending, receiving email with various security services at that address Class 2: CA issued certificates to individuals Authenticated by verifying user-supplied real name and address through an online database n Certificate used for online purchasing 30
Example: Verisign CAs n Class 1: CA issued certificates to individuals authenticated by email address n n Certificate used for sending, receiving email with various security services at that address Class 2: CA issued certificates to individuals Authenticated by verifying user-supplied real name and address through an online database n Certificate used for online purchasing 30
 Example: Verisign CAs (Cont’d) n Class 3: CA issued certificates to individuals Authenticated by background check from investigative service n n Higher level of assurance of identity than Class 1 and Class 2 CAs Class 4: CA issued certificates to web servers n n Same authentication policy as Class 3 CA Consumers using these sites had high degree of assurance the web site was not spoofed 31
Example: Verisign CAs (Cont’d) n Class 3: CA issued certificates to individuals Authenticated by background check from investigative service n n Higher level of assurance of identity than Class 1 and Class 2 CAs Class 4: CA issued certificates to web servers n n Same authentication policy as Class 3 CA Consumers using these sites had high degree of assurance the web site was not spoofed 31
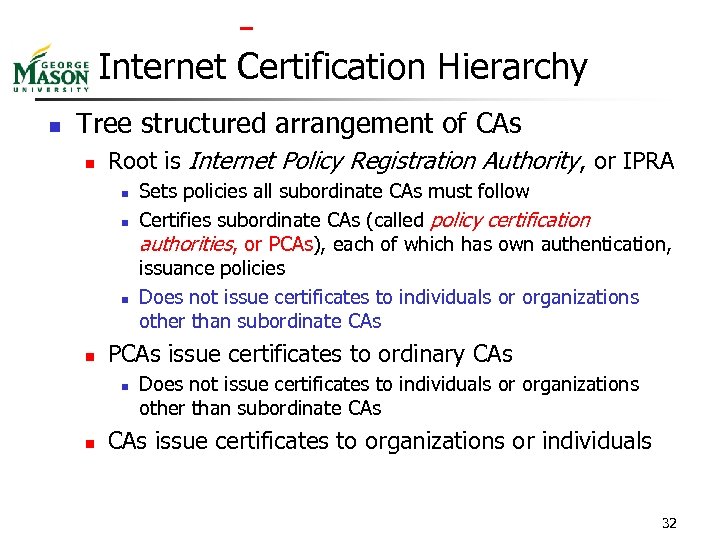 Internet Certification Hierarchy n Tree structured arrangement of CAs n Root is Internet Policy Registration Authority, or IPRA n n PCAs issue certificates to ordinary CAs n n Sets policies all subordinate CAs must follow Certifies subordinate CAs (called policy certification authorities, or PCAs), each of which has own authentication, issuance policies Does not issue certificates to individuals or organizations other than subordinate CAs CAs issue certificates to organizations or individuals 32
Internet Certification Hierarchy n Tree structured arrangement of CAs n Root is Internet Policy Registration Authority, or IPRA n n PCAs issue certificates to ordinary CAs n n Sets policies all subordinate CAs must follow Certifies subordinate CAs (called policy certification authorities, or PCAs), each of which has own authentication, issuance policies Does not issue certificates to individuals or organizations other than subordinate CAs CAs issue certificates to organizations or individuals 32
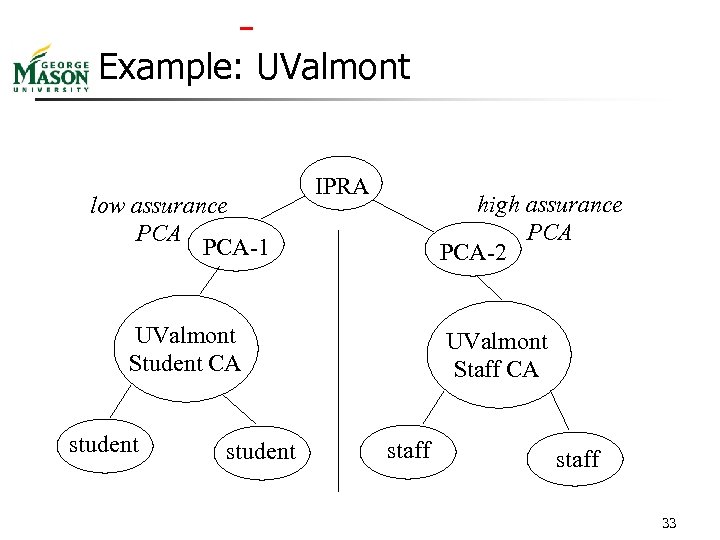 Example: UValmont low assurance PCA-1 IPRA high assurance PCA-2 UValmont Student CA student UValmont Staff CA staff 33
Example: UValmont low assurance PCA-1 IPRA high assurance PCA-2 UValmont Student CA student UValmont Staff CA staff 33
 Certificate Differences n Student, staff certificates signed using different private keys (for different CAs) n n n Student’s signed by key corresponding to low assurance certificate signed by first PCA Staff’s signed by key corresponding to high assurance certificate signed by second PCA To see how much trust should be placed in the certificate (what policy used to authenticate): n n Determine CA signing certificate, check its policy Also go to PCA that signed CA’s certificate n CAs are restricted by PCA’s policy, but CA can (only) restrict itself further 34
Certificate Differences n Student, staff certificates signed using different private keys (for different CAs) n n n Student’s signed by key corresponding to low assurance certificate signed by first PCA Staff’s signed by key corresponding to high assurance certificate signed by second PCA To see how much trust should be placed in the certificate (what policy used to authenticate): n n Determine CA signing certificate, check its policy Also go to PCA that signed CA’s certificate n CAs are restricted by PCA’s policy, but CA can (only) restrict itself further 34
 Types of Certificates n Organizational certificate n n n Issued based on principal’s affiliation with organization Example Distinguished Name /O=University of Valmont/OU=Computer Science Department/CN=Marsha Merteuille/ Residential certificate n n n Issued based on where principal lives No affiliation with organization implied Example Distinguished Name /C=US/SP=Louisiana/L=Valmont/PA=1 Express Way/CN=Marsha Merteuille/ 35
Types of Certificates n Organizational certificate n n n Issued based on principal’s affiliation with organization Example Distinguished Name /O=University of Valmont/OU=Computer Science Department/CN=Marsha Merteuille/ Residential certificate n n n Issued based on where principal lives No affiliation with organization implied Example Distinguished Name /C=US/SP=Louisiana/L=Valmont/PA=1 Express Way/CN=Marsha Merteuille/ 35
 Types of Certificates (Cont’d) n Certificate tied to a role n UValmont wants comptroller to have a certificate n n This way, she can sign contracts and documents digitally Distinguished Name /O=University of Valmont/OU=Office of the Big Bucks/RN=Comptroller where “RN” is role name; note the individual using the certificate is not named, so no CN 36
Types of Certificates (Cont’d) n Certificate tied to a role n UValmont wants comptroller to have a certificate n n This way, she can sign contracts and documents digitally Distinguished Name /O=University of Valmont/OU=Office of the Big Bucks/RN=Comptroller where “RN” is role name; note the individual using the certificate is not named, so no CN 36
 Naming Conflicts n John Smith, John Smith Jr. live at same address n n John Smith Jr. applies for residential certificate from Certs-from-Us, getting the DN of: /C=US/SP=Maine/L=Portland/PA=1 First Ave. /CN=John Smith/ Now his father applies for residential certificate from Quick-Certs, getting DN of: /C=US/SP=Maine/L=Portland/PA=1 First Ave. /CN=John Smith/ because Quick-Certs has no way of knowing that DN has been taken 37
Naming Conflicts n John Smith, John Smith Jr. live at same address n n John Smith Jr. applies for residential certificate from Certs-from-Us, getting the DN of: /C=US/SP=Maine/L=Portland/PA=1 First Ave. /CN=John Smith/ Now his father applies for residential certificate from Quick-Certs, getting DN of: /C=US/SP=Maine/L=Portland/PA=1 First Ave. /CN=John Smith/ because Quick-Certs has no way of knowing that DN has been taken 37
 Solutions n Organizational certificates n n All CA DNs must be superior to that of the principal Example: for Marsha Merteuille’s DN: /O=University of Valmont/OU=Computer Science Department/CN=Marsha Merteuille/ DN of the CA must be either: /O=University of Valmont/ (the issuer being the University) or /O=University of Valmont/OU=Computer Science Department/ (the issuer being the Department) 38
Solutions n Organizational certificates n n All CA DNs must be superior to that of the principal Example: for Marsha Merteuille’s DN: /O=University of Valmont/OU=Computer Science Department/CN=Marsha Merteuille/ DN of the CA must be either: /O=University of Valmont/ (the issuer being the University) or /O=University of Valmont/OU=Computer Science Department/ (the issuer being the Department) 38
 Related Problem n n Single CA issues two types of certificates under two different PCAs Example n n UValmont issues both low assurance, high assurance certificates under two different PCAs How does validator know under which PCA the certificate was issued? n Reflects on assurance of the identity of the principal to whom certificate was issued 39
Related Problem n n Single CA issues two types of certificates under two different PCAs Example n n UValmont issues both low assurance, high assurance certificates under two different PCAs How does validator know under which PCA the certificate was issued? n Reflects on assurance of the identity of the principal to whom certificate was issued 39
 Solution n CA Distinguished Names need not be unique CA (Distinguished Name, public key) pair must be unique Example n n In earlier UValmont example, student validation required using first PCA’s public key; validation using second PCA’s public key would fail Keys used to sign certificate indicate the PCA, and the policy, under which certificate is issued 40
Solution n CA Distinguished Names need not be unique CA (Distinguished Name, public key) pair must be unique Example n n In earlier UValmont example, student validation required using first PCA’s public key; validation using second PCA’s public key would fail Keys used to sign certificate indicate the PCA, and the policy, under which certificate is issued 40
 Persona Certificate n Anonymous certificate n n Certificate with meaningless Distinguished Name Example: n Government requires all citizens with gene X to register because people with this gene more likely commit crimes n n Government employee wants to alert media n n n No scientific evidence, and government wants no civil rights fuss Government will deny plan, change approach Government employee will be fired, prosecuted Must notify media anonymously 41
Persona Certificate n Anonymous certificate n n Certificate with meaningless Distinguished Name Example: n Government requires all citizens with gene X to register because people with this gene more likely commit crimes n n Government employee wants to alert media n n n No scientific evidence, and government wants no civil rights fuss Government will deny plan, change approach Government employee will be fired, prosecuted Must notify media anonymously 41
 Persona Certificate (Cont’d) n Employee gets persona certificate, sends copy of plan to media n n Media knows message unchanged during transit (data integrity) But they do not know who sent it (no authentication) Government denies plan, changes it Employee sends copy of new plan signed using same certificate n n Media can tell it’s from original whistleblower (linkability) Media cannot track back whom that whistleblower is 42
Persona Certificate (Cont’d) n Employee gets persona certificate, sends copy of plan to media n n Media knows message unchanged during transit (data integrity) But they do not know who sent it (no authentication) Government denies plan, changes it Employee sends copy of new plan signed using same certificate n n Media can tell it’s from original whistleblower (linkability) Media cannot track back whom that whistleblower is 42
 Overview n n Certificate and distinguished name Web identity and anonymity 43
Overview n n Certificate and distinguished name Web identity and anonymity 43
 Host Identity n Host identity at different layers n n These can be spoofed n n Ethernet address: 00: 05: 02: 6 B: A 8: 21 IP address: 192. 168. 35. 89 Host name: cherry. orchard. chekhov. ru Write your own Ethernet frames Fake source IP address Fake host name Above protocols rely on spoofed identity 44
Host Identity n Host identity at different layers n n These can be spoofed n n Ethernet address: 00: 05: 02: 6 B: A 8: 21 IP address: 192. 168. 35. 89 Host name: cherry. orchard. chekhov. ru Write your own Ethernet frames Fake source IP address Fake host name Above protocols rely on spoofed identity 44
 Domain Name Server n Maps transport identifiers (host names) to network identifiers (host addresses) n Forward records: host names IP addresses n n Reverse records: IP addresses host names n n PING NSLOOKUP Weak authentication n Not cryptographically based E. g. , reverse domain name lookup IP -> host name via DNS -> IP via DNS -> matching the two IPs 45
Domain Name Server n Maps transport identifiers (host names) to network identifiers (host addresses) n Forward records: host names IP addresses n n Reverse records: IP addresses host names n n PING NSLOOKUP Weak authentication n Not cryptographically based E. g. , reverse domain name lookup IP -> host name via DNS -> IP via DNS -> matching the two IPs 45
 DHCP and NAT n n DHCP server dynamically assigns clients unused IP addresses Gateway assigns clients internal address n n n NAT translates all outgoing and incoming packets Invisible to both inside clients and outsiders Your desktop/laptop -> router (DHCP and NAT) -> Internet 46
DHCP and NAT n n DHCP server dynamically assigns clients unused IP addresses Gateway assigns clients internal address n n n NAT translates all outgoing and incoming packets Invisible to both inside clients and outsiders Your desktop/laptop -> router (DHCP and NAT) -> Internet 46
 Attacks on DNS n n Change records on server Cache poisoning n n n Attacker sends victim request that must be resolved by asking attacker Legitimately piggyback extra record to response, but have fake name/IP association in the record The fake record will be cached 47
Attacks on DNS n n Change records on server Cache poisoning n n n Attacker sends victim request that must be resolved by asking attacker Legitimately piggyback extra record to response, but have fake name/IP association in the record The fake record will be cached 47
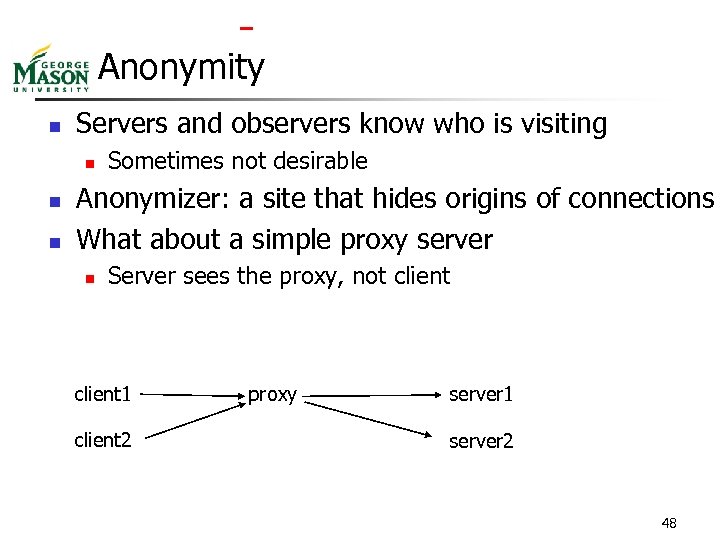 Anonymity n Servers and observers know who is visiting n n n Sometimes not desirable Anonymizer: a site that hides origins of connections What about a simple proxy server n Server sees the proxy, not client 1 client 2 proxy server 1 server 2 48
Anonymity n Servers and observers know who is visiting n n n Sometimes not desirable Anonymizer: a site that hides origins of connections What about a simple proxy server n Server sees the proxy, not client 1 client 2 proxy server 1 server 2 48
 Problem With Simple Proxy n The proxy knows who are the client and server n n Example: anon. penet. fi n n n And we all know this fact Anonymous re-mailer Material claimed to be copyrighted sent through site Finnish court directed owner to reveal mapping so plaintiffs could determine sender Owner appealed, subsequently shut down site What about a chain of proxies? 49
Problem With Simple Proxy n The proxy knows who are the client and server n n Example: anon. penet. fi n n n And we all know this fact Anonymous re-mailer Material claimed to be copyrighted sent through site Finnish court directed owner to reveal mapping so plaintiffs could determine sender Owner appealed, subsequently shut down site What about a chain of proxies? 49
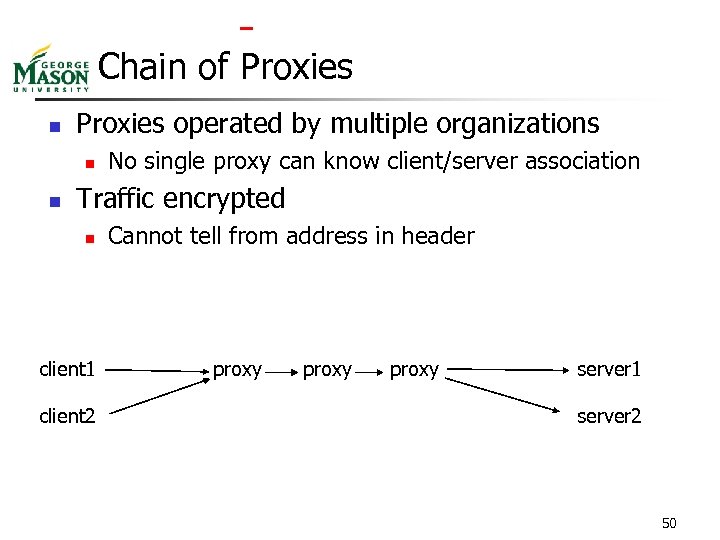 Chain of Proxies n Proxies operated by multiple organizations n n No single proxy can know client/server association Traffic encrypted n client 1 client 2 Cannot tell from address in header proxy server 1 server 2 50
Chain of Proxies n Proxies operated by multiple organizations n n No single proxy can know client/server association Traffic encrypted n client 1 client 2 Cannot tell from address in header proxy server 1 server 2 50
 Weaknesses of Chain of Proxies n First and last proxy collude n n One knows client one knows server Traffic analysis n Observes in, out flows of traffic n n n timing message size What if we mix multiple messages 51
Weaknesses of Chain of Proxies n First and last proxy collude n n One knows client one knows server Traffic analysis n Observes in, out flows of traffic n n n timing message size What if we mix multiple messages 51
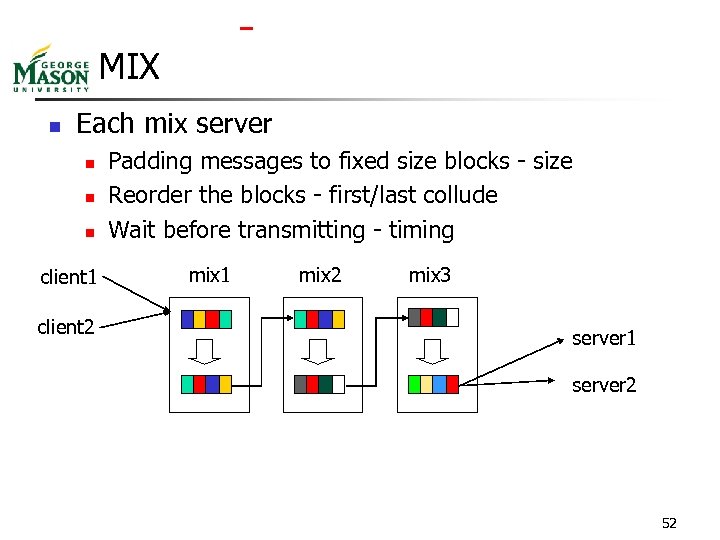 MIX n Each mix server n n n client 1 client 2 Padding messages to fixed size blocks - size Reorder the blocks - first/last collude Wait before transmitting - timing mix 1 mix 2 mix 3 server 1 server 2 52
MIX n Each mix server n n n client 1 client 2 Padding messages to fixed size blocks - size Reorder the blocks - first/last collude Wait before transmitting - timing mix 1 mix 2 mix 3 server 1 server 2 52
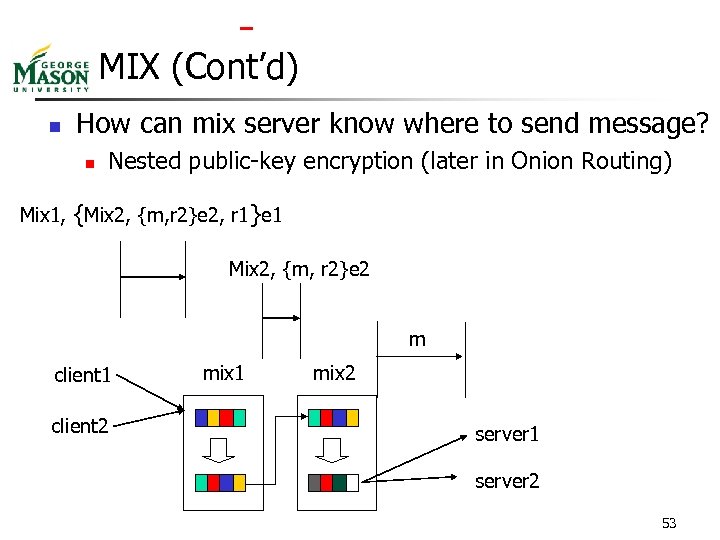 MIX (Cont’d) n How can mix server know where to send message? n Nested public-key encryption (later in Onion Routing) Mix 1, {Mix 2, {m, r 2}e 2, r 1}e 1 Mix 2, {m, r 2}e 2 m client 1 client 2 mix 1 mix 2 server 1 server 2 53
MIX (Cont’d) n How can mix server know where to send message? n Nested public-key encryption (later in Onion Routing) Mix 1, {Mix 2, {m, r 2}e 2, r 1}e 1 Mix 2, {m, r 2}e 2 m client 1 client 2 mix 1 mix 2 server 1 server 2 53
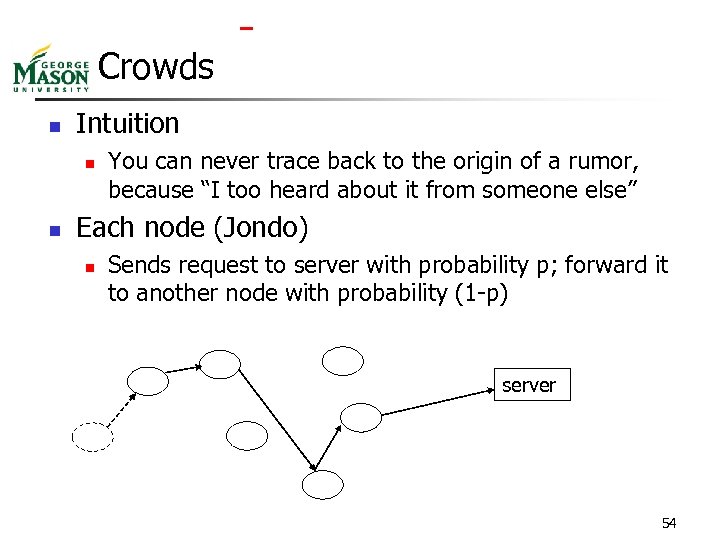 Crowds n Intuition n n You can never trace back to the origin of a rumor, because “I too heard about it from someone else” Each node (Jondo) n Sends request to server with probability p; forward it to another node with probability (1 -p) server 54
Crowds n Intuition n n You can never trace back to the origin of a rumor, because “I too heard about it from someone else” Each node (Jondo) n Sends request to server with probability p; forward it to another node with probability (1 -p) server 54
 Privacy n n Anonymity protects privacy by obstructing amalgamation of individual records Important, because amalgamation poses 3 risks: n n n Incorrect conclusions from misinterpreted data Harm from erroneous information Not being let alone Also hinders monitoring to deter or prevent crime Conclusion: anonymity can be used for good or ill n Right to remain anonymous entails responsibility to use that right wisely 55
Privacy n n Anonymity protects privacy by obstructing amalgamation of individual records Important, because amalgamation poses 3 risks: n n n Incorrect conclusions from misinterpreted data Harm from erroneous information Not being let alone Also hinders monitoring to deter or prevent crime Conclusion: anonymity can be used for good or ill n Right to remain anonymous entails responsibility to use that right wisely 55
 Key Points n n n Certificates use Distinguished name as identity Web identity based on addresses is weak Anonymity can be achieved with sophisticated proxies 56
Key Points n n n Certificates use Distinguished name as identity Web identity based on addresses is weak Anonymity can be achieved with sophisticated proxies 56


