a0f4c9b8ab503838a7c9f7c7a10582d3.ppt
- Количество слайдов: 56
 IPv 6 Transition Mechanisms and Strategies DPS: Emerging Technologies II Team 2 02/18/06 Pace University 1
IPv 6 Transition Mechanisms and Strategies DPS: Emerging Technologies II Team 2 02/18/06 Pace University 1
 Agenda n IPv 6 Overview n Backward Compatibility/Integration n Transition Mechanisms n Tunneling n Translation n Mobile Environments n References and Appendices Pace University 2
Agenda n IPv 6 Overview n Backward Compatibility/Integration n Transition Mechanisms n Tunneling n Translation n Mobile Environments n References and Appendices Pace University 2
 IPv 6 Transition Overview n Myths: n Transition requires major fork-lift n Transition starts in the network backbone n Transition Plan defines Flag-Day deployment n Deployment is very expensive Pace University 3
IPv 6 Transition Overview n Myths: n Transition requires major fork-lift n Transition starts in the network backbone n Transition Plan defines Flag-Day deployment n Deployment is very expensive Pace University 3
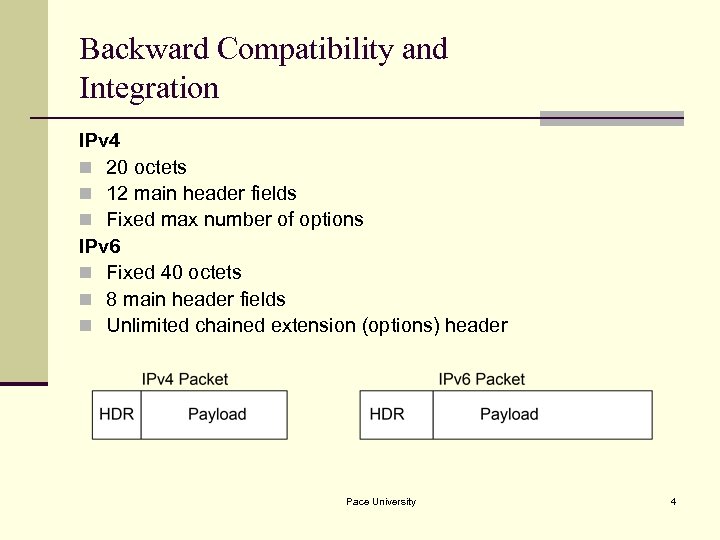 Backward Compatibility and Integration IPv 4 n 20 octets n 12 main header fields n Fixed max number of options IPv 6 n Fixed 40 octets n 8 main header fields n Unlimited chained extension (options) header Pace University 4
Backward Compatibility and Integration IPv 4 n 20 octets n 12 main header fields n Fixed max number of options IPv 6 n Fixed 40 octets n 8 main header fields n Unlimited chained extension (options) header Pace University 4
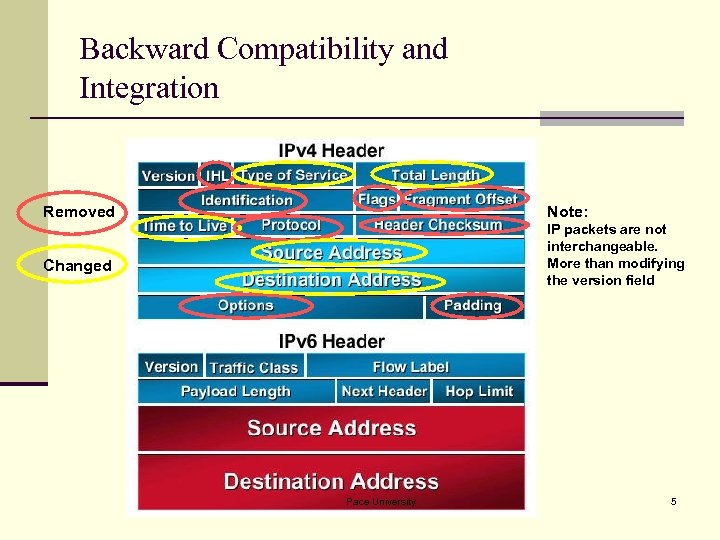 Backward Compatibility and Integration Removed Note: IP packets are not interchangeable. More than modifying the version field Changed Pace University 5
Backward Compatibility and Integration Removed Note: IP packets are not interchangeable. More than modifying the version field Changed Pace University 5
 IPv 4 and IPv 6 addresses n 192. 210. 145. 112 – IPv 4 address – 32 bits (decimal form divided into octets) n 192. 210. 145. 112/24 – 24 bit subnet mask n 2001: CE 8 B: 0011: 0 A 00: 8000: 0000: ABCF: 0001 – IPv 6 address – 128 bits (hex form divided into 8 units, 16 bits ea. ) n 2001: CE 8 B: 11: A 00: 8000: : ABCF: 1 – compressed n 2001: CE 8 B: 11: A 00: : /64 – 64 bit prefix Pace University 6
IPv 4 and IPv 6 addresses n 192. 210. 145. 112 – IPv 4 address – 32 bits (decimal form divided into octets) n 192. 210. 145. 112/24 – 24 bit subnet mask n 2001: CE 8 B: 0011: 0 A 00: 8000: 0000: ABCF: 0001 – IPv 6 address – 128 bits (hex form divided into 8 units, 16 bits ea. ) n 2001: CE 8 B: 11: A 00: 8000: : ABCF: 1 – compressed n 2001: CE 8 B: 11: A 00: : /64 – 64 bit prefix Pace University 6
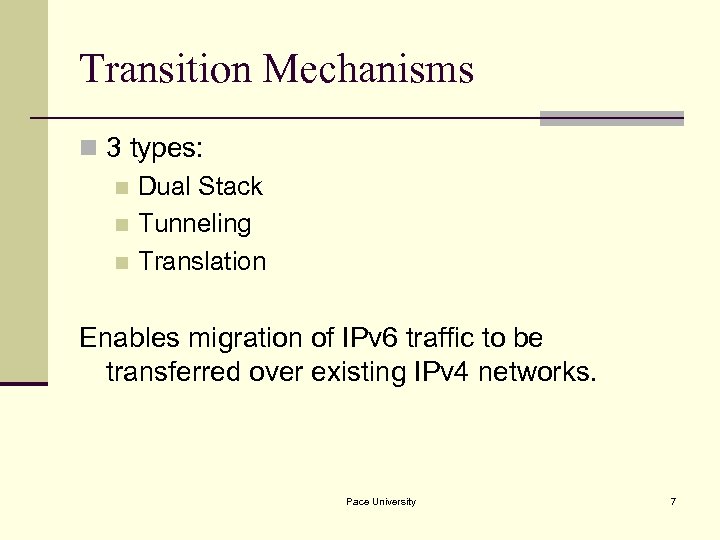 Transition Mechanisms n 3 types: n Dual Stack n Tunneling n Translation Enables migration of IPv 6 traffic to be transferred over existing IPv 4 networks. Pace University 7
Transition Mechanisms n 3 types: n Dual Stack n Tunneling n Translation Enables migration of IPv 6 traffic to be transferred over existing IPv 4 networks. Pace University 7
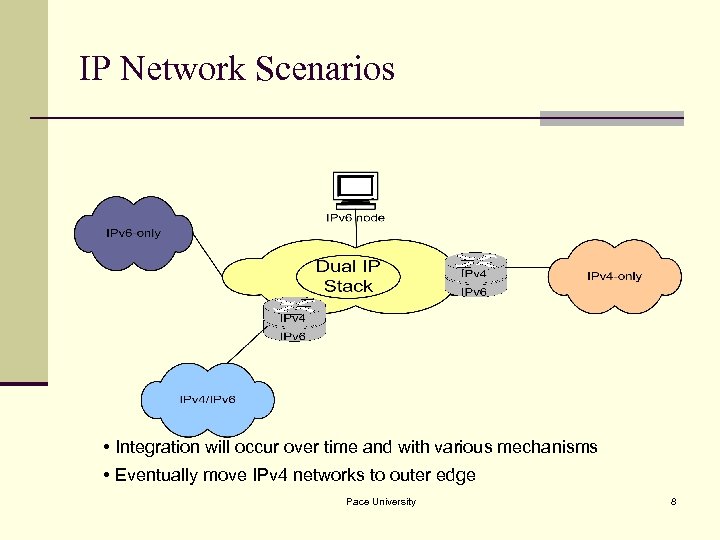 IP Network Scenarios • Integration will occur over time and with various mechanisms • Eventually move IPv 4 networks to outer edge Pace University 8
IP Network Scenarios • Integration will occur over time and with various mechanisms • Eventually move IPv 4 networks to outer edge Pace University 8
 Dual-Stack Network Deployment n A dual-stack network is one that has both IPv 4 and IPv 6 on every interface n “Ships in the night” n Generally considered
Dual-Stack Network Deployment n A dual-stack network is one that has both IPv 4 and IPv 6 on every interface n “Ships in the night” n Generally considered
 Tunneling – Issues and Advantages n Tunneling mechanisms allow other protocols to be carried over a different protocol network n Tunneling “encapsulates” the passenger protocol within the payload of the hosting protocol n IPv 6 -only to IPv 6 -only nodes between two sites where IPv 4 transport is in the middle Pace University 10
Tunneling – Issues and Advantages n Tunneling mechanisms allow other protocols to be carried over a different protocol network n Tunneling “encapsulates” the passenger protocol within the payload of the hosting protocol n IPv 6 -only to IPv 6 -only nodes between two sites where IPv 4 transport is in the middle Pace University 10
 Translation – Issues and Advantages n Translation allows IPv 4 and IPv 6 nodes to talk to each other, through a translation function n Translation can be more complex, and introduces the same issues as IPv 4 NAT, plus others n IPv 6 community positioning translation as last -resort mechanism Pace University 11
Translation – Issues and Advantages n Translation allows IPv 4 and IPv 6 nodes to talk to each other, through a translation function n Translation can be more complex, and introduces the same issues as IPv 4 NAT, plus others n IPv 6 community positioning translation as last -resort mechanism Pace University 11
 Naming Services n DNS must be included in transition strategy n Resolving Names: n IPv 4 specifies “A” records n IPv 6 specifies “AAAA” records n Applications should be aware of both records n Will require development update and thorough testing n Tools like “Scrubber” by Sun make it easy Pace University 12
Naming Services n DNS must be included in transition strategy n Resolving Names: n IPv 4 specifies “A” records n IPv 6 specifies “AAAA” records n Applications should be aware of both records n Will require development update and thorough testing n Tools like “Scrubber” by Sun make it easy Pace University 12
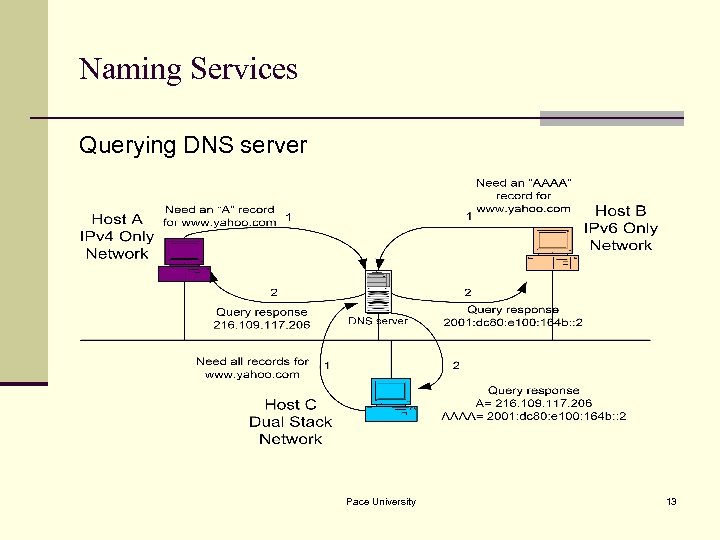 Naming Services Querying DNS server Pace University 13
Naming Services Querying DNS server Pace University 13
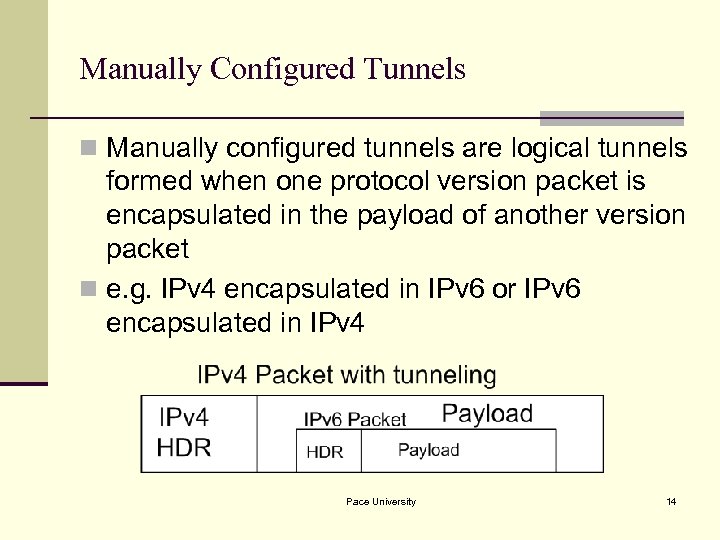 Manually Configured Tunnels n Manually configured tunnels are logical tunnels formed when one protocol version packet is encapsulated in the payload of another version packet n e. g. IPv 4 encapsulated in IPv 6 or IPv 6 encapsulated in IPv 4 Pace University 14
Manually Configured Tunnels n Manually configured tunnels are logical tunnels formed when one protocol version packet is encapsulated in the payload of another version packet n e. g. IPv 4 encapsulated in IPv 6 or IPv 6 encapsulated in IPv 4 Pace University 14
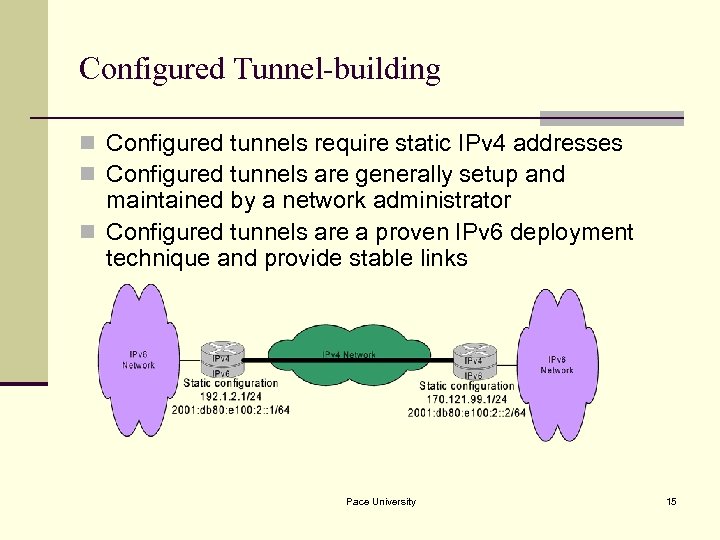 Configured Tunnel-building n Configured tunnels require static IPv 4 addresses n Configured tunnels are generally setup and maintained by a network administrator n Configured tunnels are a proven IPv 6 deployment technique and provide stable links Pace University 15
Configured Tunnel-building n Configured tunnels require static IPv 4 addresses n Configured tunnels are generally setup and maintained by a network administrator n Configured tunnels are a proven IPv 6 deployment technique and provide stable links Pace University 15
 Potential Tunnel Issues n MTU fragmentation n ICMPv 4 error handling n Filtering protocol 41 n NAT (Network Address Translation) Pace University 16
Potential Tunnel Issues n MTU fragmentation n ICMPv 4 error handling n Filtering protocol 41 n NAT (Network Address Translation) Pace University 16
 ISATAP n ISATAP (Intra-Site Automatic Tunneling Addressing Protocol) an automatic tunneling mechanism used inside an organization that has an IPv 4 -dominant backbone, but has selected users that need IPv 6 capability Pace University 17
ISATAP n ISATAP (Intra-Site Automatic Tunneling Addressing Protocol) an automatic tunneling mechanism used inside an organization that has an IPv 4 -dominant backbone, but has selected users that need IPv 6 capability Pace University 17
 ISATAP Functions n ISATAP connects dual-stack nodes, isolated within an IPv 4 -only network n n To exchange IPv 6 traffic with each other (host ISATAP) To exchange traffic with the global IPv 6 Internet n ISATAP is a mechanism with minimal configuration required n ISATAP is ideal when there are relatively few, relatively scattered individual nodes that need service Pace University 18
ISATAP Functions n ISATAP connects dual-stack nodes, isolated within an IPv 4 -only network n n To exchange IPv 6 traffic with each other (host ISATAP) To exchange traffic with the global IPv 6 Internet n ISATAP is a mechanism with minimal configuration required n ISATAP is ideal when there are relatively few, relatively scattered individual nodes that need service Pace University 18
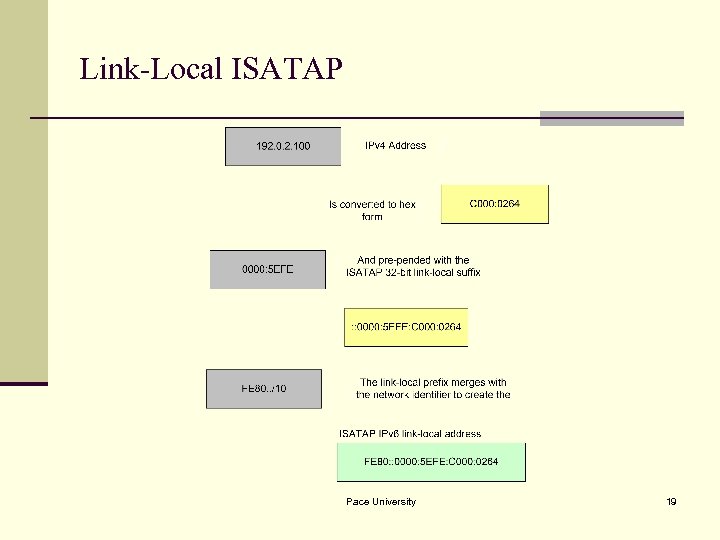 Link-Local ISATAP Pace University 19
Link-Local ISATAP Pace University 19
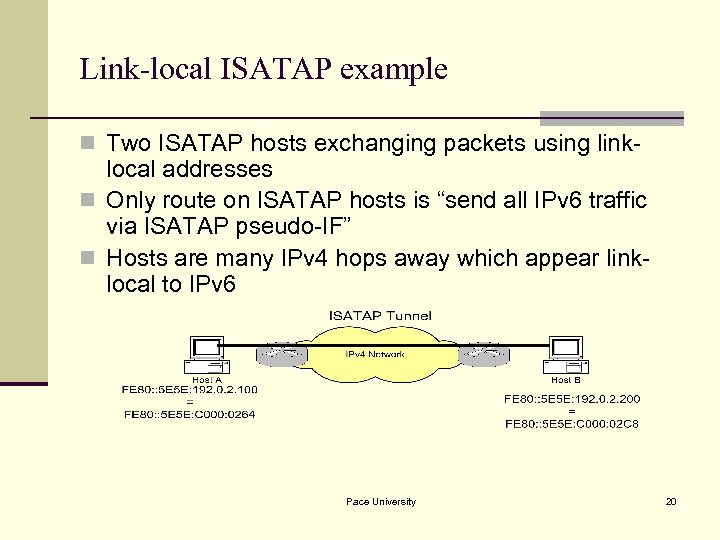 Link-local ISATAP example n Two ISATAP hosts exchanging packets using link- local addresses n Only route on ISATAP hosts is “send all IPv 6 traffic via ISATAP pseudo-IF” n Hosts are many IPv 4 hops away which appear linklocal to IPv 6 Pace University 20
Link-local ISATAP example n Two ISATAP hosts exchanging packets using link- local addresses n Only route on ISATAP hosts is “send all IPv 6 traffic via ISATAP pseudo-IF” n Hosts are many IPv 4 hops away which appear linklocal to IPv 6 Pace University 20
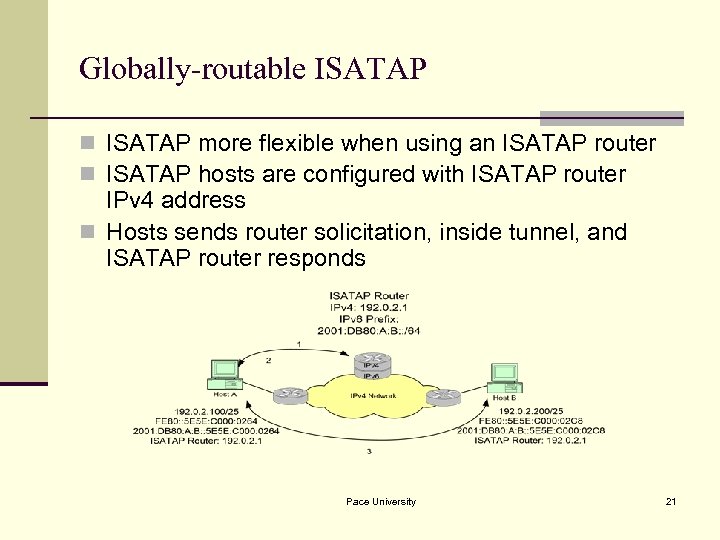 Globally-routable ISATAP n ISATAP more flexible when using an ISATAP router n ISATAP hosts are configured with ISATAP router IPv 4 address n Hosts sends router solicitation, inside tunnel, and ISATAP router responds Pace University 21
Globally-routable ISATAP n ISATAP more flexible when using an ISATAP router n ISATAP hosts are configured with ISATAP router IPv 4 address n Hosts sends router solicitation, inside tunnel, and ISATAP router responds Pace University 21
 ISATAP Summary n ISATAP scales better than manually configured tunnels inside the enterprise n Decapsulate-from-anywhere issues (like 6 to 4) mitigated by internal deployment n No authentication provided – any dual stack node that knows ISATAP router address can obtain services n May need to look at other alternatives if security is required Pace University 22
ISATAP Summary n ISATAP scales better than manually configured tunnels inside the enterprise n Decapsulate-from-anywhere issues (like 6 to 4) mitigated by internal deployment n No authentication provided – any dual stack node that knows ISATAP router address can obtain services n May need to look at other alternatives if security is required Pace University 22
 Tunnel Broker n Tunnel Brokers provide a semi-automated mechanism for building configured tunnels – often with advance features Pace University 23
Tunnel Broker n Tunnel Brokers provide a semi-automated mechanism for building configured tunnels – often with advance features Pace University 23
 Tunnel Broker Operational Model n Tunnel Broker (TB) provides a capability to easily configure an IPv 6 -in-IPv 4 tunnel n TB systems typically include a tunnel client, tunnel broker, and tunnel endpoints n TB systems can be used on the Internet or inside the enterprise Product Example: Hexago http: //www. hexago. com/docs/hexago-migration-broker-product-description-200310. pdf Pace University 24
Tunnel Broker Operational Model n Tunnel Broker (TB) provides a capability to easily configure an IPv 6 -in-IPv 4 tunnel n TB systems typically include a tunnel client, tunnel broker, and tunnel endpoints n TB systems can be used on the Internet or inside the enterprise Product Example: Hexago http: //www. hexago. com/docs/hexago-migration-broker-product-description-200310. pdf Pace University 24
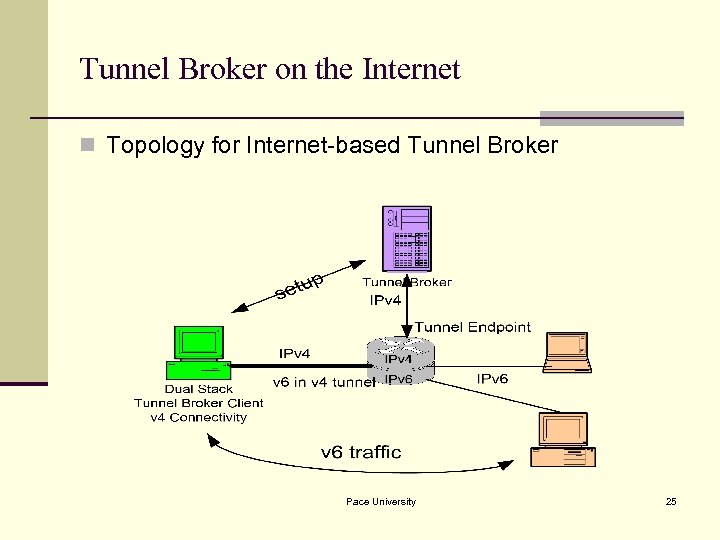 Tunnel Broker on the Internet n Topology for Internet-based Tunnel Broker Pace University 25
Tunnel Broker on the Internet n Topology for Internet-based Tunnel Broker Pace University 25
 Tunnel Broker in the Enterprise n TB is an effective solution for an organization’s Intranet/Extranet n Advantages over ISATAP: Authentication n NAT Traversal n Stable IPv 6 address n DNS registration n n ISATAP Advantage over TB: n Lower capital costs Pace University 26
Tunnel Broker in the Enterprise n TB is an effective solution for an organization’s Intranet/Extranet n Advantages over ISATAP: Authentication n NAT Traversal n Stable IPv 6 address n DNS registration n n ISATAP Advantage over TB: n Lower capital costs Pace University 26
 IPv 6 6 to 4 Transition Mechanism n 6 to 4 is an automatic tunneling mechanism that provides v 6 capability to a dual-stack node or v 6 -capable site that has only IPv 4 connectivity to the site Pace University 27
IPv 6 6 to 4 Transition Mechanism n 6 to 4 is an automatic tunneling mechanism that provides v 6 capability to a dual-stack node or v 6 -capable site that has only IPv 4 connectivity to the site Pace University 27
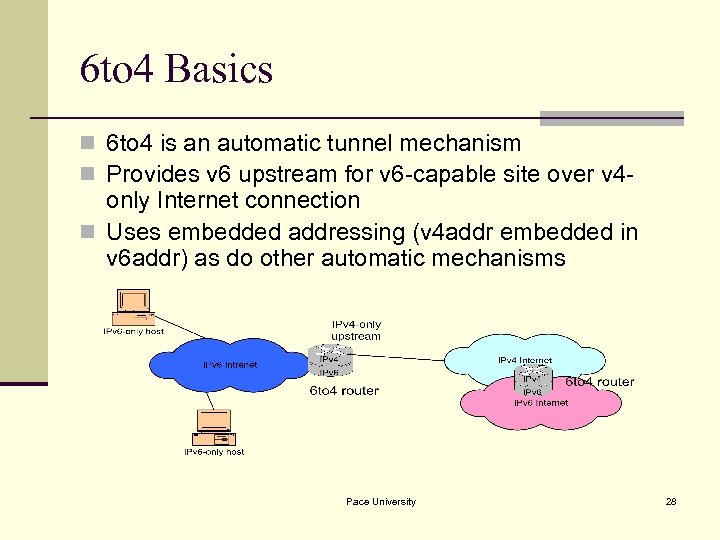 6 to 4 Basics n 6 to 4 is an automatic tunnel mechanism n Provides v 6 upstream for v 6 -capable site over v 4 - only Internet connection n Uses embedded addressing (v 4 addr embedded in v 6 addr) as do other automatic mechanisms Pace University 28
6 to 4 Basics n 6 to 4 is an automatic tunnel mechanism n Provides v 6 upstream for v 6 -capable site over v 4 - only Internet connection n Uses embedded addressing (v 4 addr embedded in v 6 addr) as do other automatic mechanisms Pace University 28
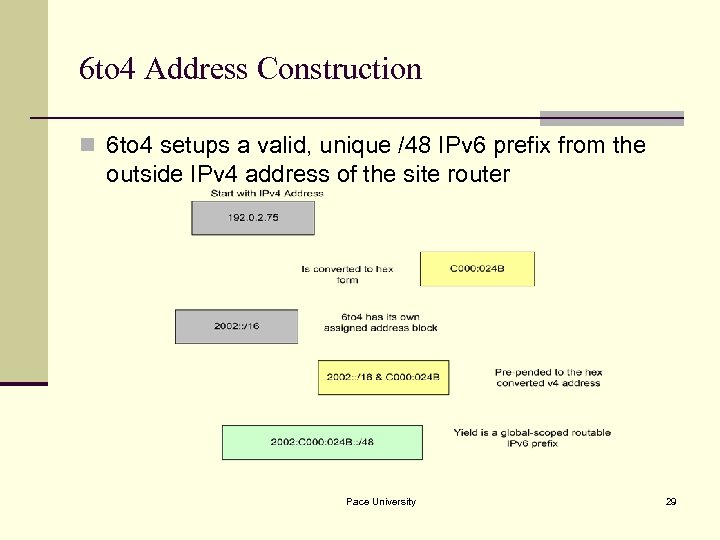 6 to 4 Address Construction n 6 to 4 setups a valid, unique /48 IPv 6 prefix from the outside IPv 4 address of the site router Pace University 29
6 to 4 Address Construction n 6 to 4 setups a valid, unique /48 IPv 6 prefix from the outside IPv 4 address of the site router Pace University 29
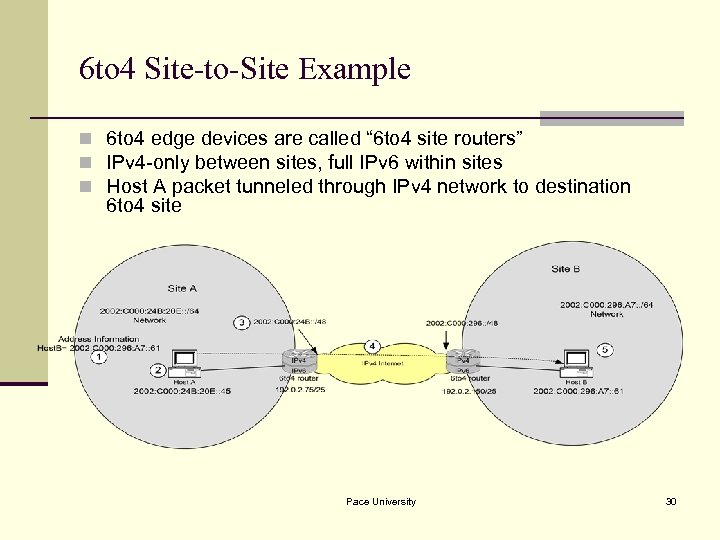 6 to 4 Site-to-Site Example n 6 to 4 edge devices are called “ 6 to 4 site routers” n IPv 4 -only between sites, full IPv 6 within sites n Host A packet tunneled through IPv 4 network to destination 6 to 4 site Pace University 30
6 to 4 Site-to-Site Example n 6 to 4 edge devices are called “ 6 to 4 site routers” n IPv 4 -only between sites, full IPv 6 within sites n Host A packet tunneled through IPv 4 network to destination 6 to 4 site Pace University 30
 Teredo Transition Mechanism n Teredo (a. k. a. Shipworm) is a tunneling mechanism that allows nodes located behind NAT devices to obtain global IPv 6 connectivity Pace University 31
Teredo Transition Mechanism n Teredo (a. k. a. Shipworm) is a tunneling mechanism that allows nodes located behind NAT devices to obtain global IPv 6 connectivity Pace University 31
 Teredo for Unmanaged Environments n Teredo is needed for home users with PCs with non-routable addresses n Protocol 41 tunneling not supported by many DSL modems n Protocol 41 tunneling requires routable address on PC Pace University 32
Teredo for Unmanaged Environments n Teredo is needed for home users with PCs with non-routable addresses n Protocol 41 tunneling not supported by many DSL modems n Protocol 41 tunneling requires routable address on PC Pace University 32
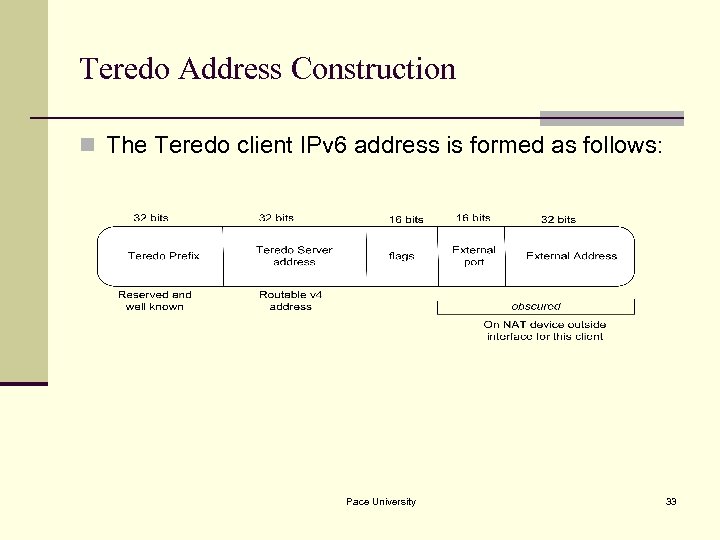 Teredo Address Construction n The Teredo client IPv 6 address is formed as follows: Pace University 33
Teredo Address Construction n The Teredo client IPv 6 address is formed as follows: Pace University 33
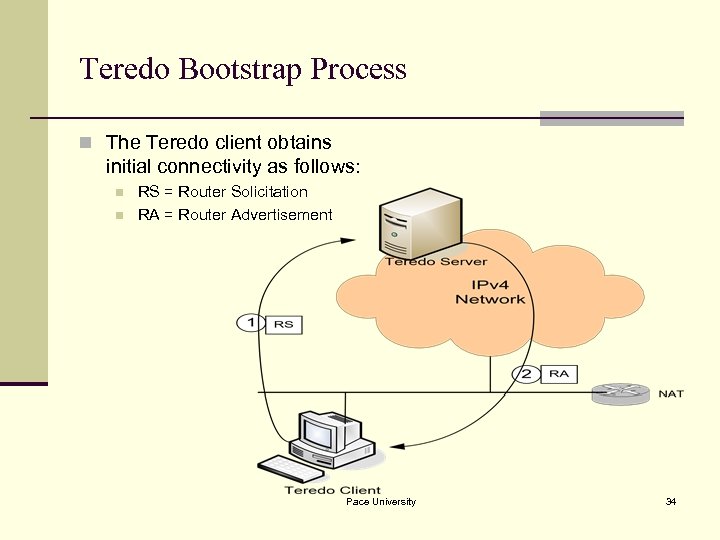 Teredo Bootstrap Process n The Teredo client obtains initial connectivity as follows: n n RS = Router Solicitation RA = Router Advertisement Pace University 34
Teredo Bootstrap Process n The Teredo client obtains initial connectivity as follows: n n RS = Router Solicitation RA = Router Advertisement Pace University 34
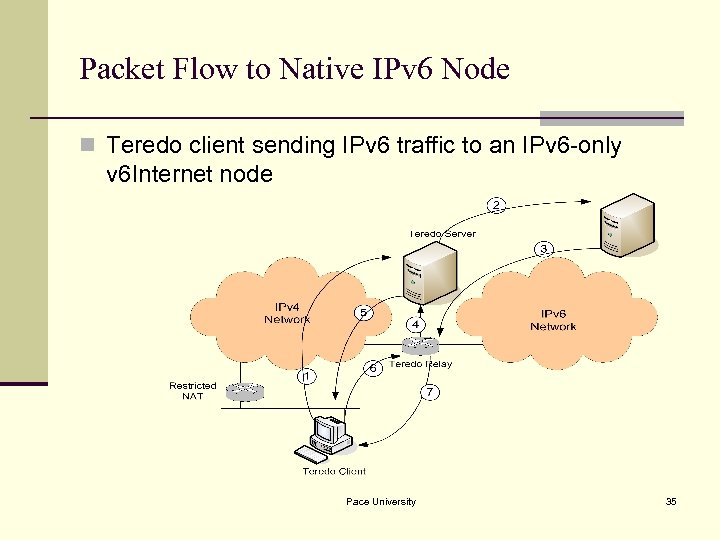 Packet Flow to Native IPv 6 Node n Teredo client sending IPv 6 traffic to an IPv 6 -only v 6 Internet node Pace University 35
Packet Flow to Native IPv 6 Node n Teredo client sending IPv 6 traffic to an IPv 6 -only v 6 Internet node Pace University 35
 Teredo Summary n Teredo is complex, so performance will suffer – may consider as last resort n Several single points of failure in system n Components target for Do. S (Denial of Service) attacks with overwhelming packet ingress rates n Teredo client “circumvents” weak security protections provided by IPv 4 NAT device Pace University 36
Teredo Summary n Teredo is complex, so performance will suffer – may consider as last resort n Several single points of failure in system n Components target for Do. S (Denial of Service) attacks with overwhelming packet ingress rates n Teredo client “circumvents” weak security protections provided by IPv 4 NAT device Pace University 36
 DSTM n Dual Stack Transition Mechanism (DSTM) provides an IPv 4 -over-IPv 6 tunnel capability, n Includes a mechanism for the client to obtain temporary use of an IPv 4 address n Assures communication with IPv 4 applications in an IPv 6 dominant network Pace University 37
DSTM n Dual Stack Transition Mechanism (DSTM) provides an IPv 4 -over-IPv 6 tunnel capability, n Includes a mechanism for the client to obtain temporary use of an IPv 4 address n Assures communication with IPv 4 applications in an IPv 6 dominant network Pace University 37
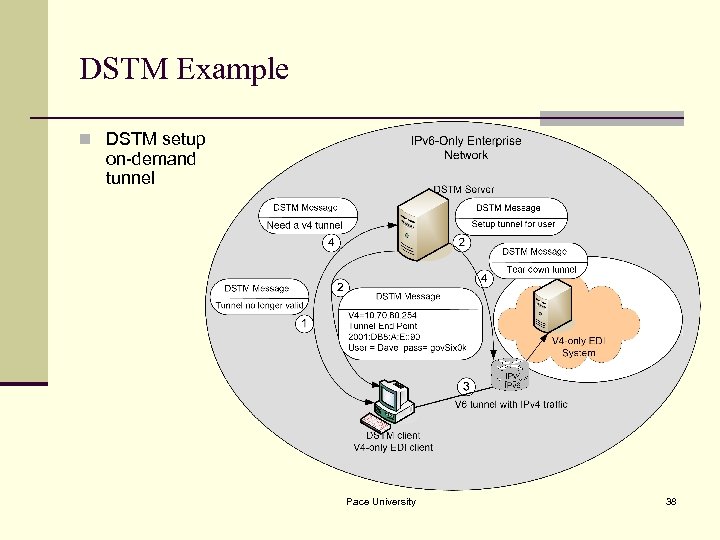 DSTM Example n DSTM setup on-demand tunnel Pace University 38
DSTM Example n DSTM setup on-demand tunnel Pace University 38
 DSTM Summary n DSTM has affinity issue with TB and DHCPv 4 Server n DSTM may be better alternative to translation mechanisms Pace University 39
DSTM Summary n DSTM has affinity issue with TB and DHCPv 4 Server n DSTM may be better alternative to translation mechanisms Pace University 39
 Translation Mechanisms n Other Mechanisms not presented in detail but listed for reference: n n n Network level translators n Stateless IP/ICMP Translation Algorithm (SIIT)(RFC 2765) n NAT-PT (RFC 2766) n Bump in the Stack (BIS) (RFC 2767) Transport level translators n Transport Relay Translator (TRT) (RFC 3142) Application level translators n Bump in the API (BIA)(RFC 3338) n SOCKS 64 (RFC 3089) n Application Level Gateways (ALG) Pace University 40
Translation Mechanisms n Other Mechanisms not presented in detail but listed for reference: n n n Network level translators n Stateless IP/ICMP Translation Algorithm (SIIT)(RFC 2765) n NAT-PT (RFC 2766) n Bump in the Stack (BIS) (RFC 2767) Transport level translators n Transport Relay Translator (TRT) (RFC 3142) Application level translators n Bump in the API (BIA)(RFC 3338) n SOCKS 64 (RFC 3089) n Application Level Gateways (ALG) Pace University 40
 NAT-PT n Network Address Translation – Protocol Translation (NAT-PT) allows IPv 4 -only and IPv 6 -only nodes to communicate through an intermediate translator device Pace University 41
NAT-PT n Network Address Translation – Protocol Translation (NAT-PT) allows IPv 4 -only and IPv 6 -only nodes to communicate through an intermediate translator device Pace University 41
 NAT-PT Functions and Overview n NAT-PT translates IP packets (header and payload) between v 4 and v 6 and manages IP sessions n Several NAT-PT deployment scenarios exist n Issues are similar as regular NAT n V 6 community suggest translation mechanism as last resort Pace University 42
NAT-PT Functions and Overview n NAT-PT translates IP packets (header and payload) between v 4 and v 6 and manages IP sessions n Several NAT-PT deployment scenarios exist n Issues are similar as regular NAT n V 6 community suggest translation mechanism as last resort Pace University 42
 Mobile Environments n Roaming nodes and networks n Changing IP addresses n Need for transition optimization n Seamless connectivity n Secured and reliable sessions Pace University 43
Mobile Environments n Roaming nodes and networks n Changing IP addresses n Need for transition optimization n Seamless connectivity n Secured and reliable sessions Pace University 43
 Internet Control Messages n ICMPv 4 vs. ICMPv 6 n Management tasks (i. e. Discovery of transition methods) n Gather all IP addresses within the network for the determination of transition mechanisms n Error Messages Pace University 44
Internet Control Messages n ICMPv 4 vs. ICMPv 6 n Management tasks (i. e. Discovery of transition methods) n Gather all IP addresses within the network for the determination of transition mechanisms n Error Messages Pace University 44
 Mobile IPv 6 n All TCP/IP apps are unaware that nodes are moving and changing their point of attachment to the Internet Only IP protocol and lower layers are aware of mobility n Higher protocol layers (e. g. TCP and UDP) and applications are not aware of mobility n Pace University 45
Mobile IPv 6 n All TCP/IP apps are unaware that nodes are moving and changing their point of attachment to the Internet Only IP protocol and lower layers are aware of mobility n Higher protocol layers (e. g. TCP and UDP) and applications are not aware of mobility n Pace University 45
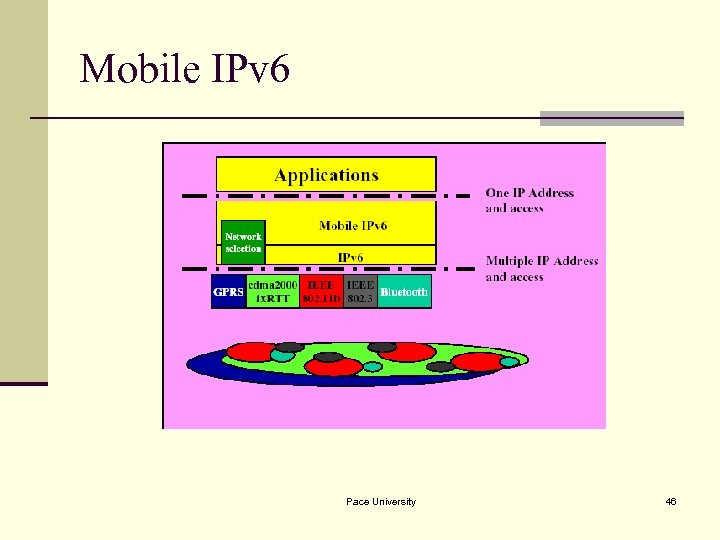 Mobile IPv 6 Pace University 46
Mobile IPv 6 Pace University 46
 Mobile IPv 6 n Home Address is the primary IP address which is permanent and used for Identifications n The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) n A Mobile Host (MH) is allowed to roam to any IP network while other nodes connect using the original home address n The binding of the two addresses are kept at the home agent (e. g. router) Pace University 47
Mobile IPv 6 n Home Address is the primary IP address which is permanent and used for Identifications n The Care-of-Address is the second IP address that is related to a foreign network, and that changes each time the host attaches to a different physical network (used for routing) n A Mobile Host (MH) is allowed to roam to any IP network while other nodes connect using the original home address n The binding of the two addresses are kept at the home agent (e. g. router) Pace University 47
 Transparent IPv 6 (TIP 6) n Mechanism that provides benefits of IPv 6 addressing while minimizing the changes in the existing IPv 4 infrastructure n Employed by Mobile IP wireless technologies without any software modification n IPv 4 host will be mapped to an IPv 6 address n TIP 6 Gateway (TIPG) is key element n IPv 4 hosts require TIPG, default gw, and DNS Pace University 48
Transparent IPv 6 (TIP 6) n Mechanism that provides benefits of IPv 6 addressing while minimizing the changes in the existing IPv 4 infrastructure n Employed by Mobile IP wireless technologies without any software modification n IPv 4 host will be mapped to an IPv 6 address n TIP 6 Gateway (TIPG) is key element n IPv 4 hosts require TIPG, default gw, and DNS Pace University 48
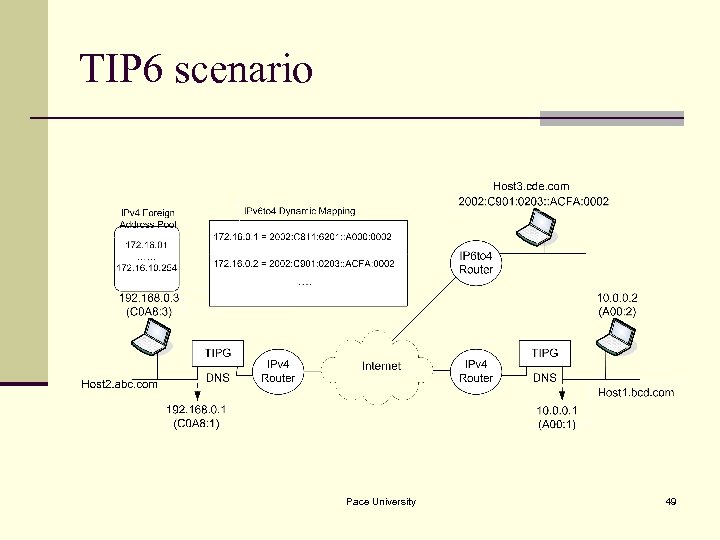 TIP 6 scenario Pace University 49
TIP 6 scenario Pace University 49
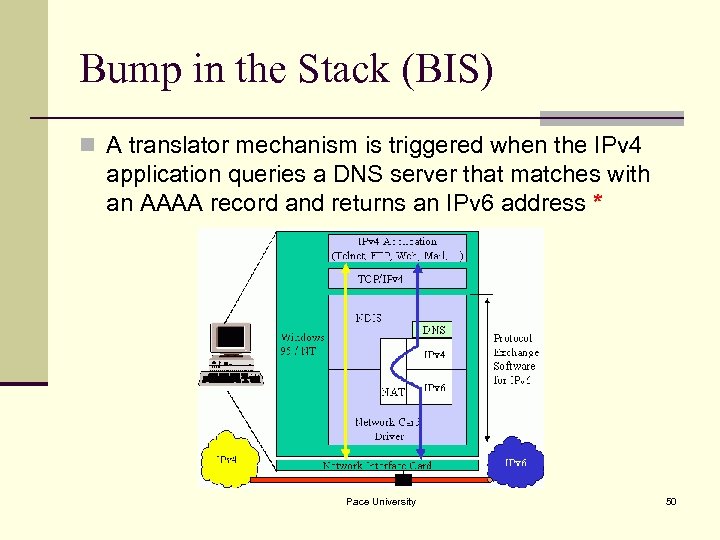 Bump in the Stack (BIS) n A translator mechanism is triggered when the IPv 4 application queries a DNS server that matches with an AAAA record and returns an IPv 6 address * Pace University 50
Bump in the Stack (BIS) n A translator mechanism is triggered when the IPv 4 application queries a DNS server that matches with an AAAA record and returns an IPv 6 address * Pace University 50
 Do. Co. Mo’s Mechanism n Paper did not provide a name for the mechanism -- to support the roaming of an IPv 6 host to a private IPv 4 network n Registration and communication method for mobile communications systems …. . n A Mobile Host (MH) is allowed to roam to any private IPv 4 network or any IPv 6 network while other nodes connect using the original home address Pace University 51
Do. Co. Mo’s Mechanism n Paper did not provide a name for the mechanism -- to support the roaming of an IPv 6 host to a private IPv 4 network n Registration and communication method for mobile communications systems …. . n A Mobile Host (MH) is allowed to roam to any private IPv 4 network or any IPv 6 network while other nodes connect using the original home address Pace University 51
 References n Jamhour, E. Storz, Simone, “Global Mobile IPv 6 Addressing Using Transition Mechanisms”, Proceedings of the 27 th Annual IEEE Conference on Local Computer Networks (LCN’ 02). n Thakolsri S. , Prehofer C. , Kellerer W. , “Transition Mechanism in IP-based Wireless Networks”, Proceedings of the 2004 International Symposium on Applications and the Internet Workshops (SAINTW’ 04). n Hsieh, I. , Kao S. , “Managing the Co-existing Network of IPv 6 and IPv 4 under Various Transition Mechanisms”, Proceedings of the Third International Conference of Information Technology and Applications (ICITA’ 05). Pace University 52
References n Jamhour, E. Storz, Simone, “Global Mobile IPv 6 Addressing Using Transition Mechanisms”, Proceedings of the 27 th Annual IEEE Conference on Local Computer Networks (LCN’ 02). n Thakolsri S. , Prehofer C. , Kellerer W. , “Transition Mechanism in IP-based Wireless Networks”, Proceedings of the 2004 International Symposium on Applications and the Internet Workshops (SAINTW’ 04). n Hsieh, I. , Kao S. , “Managing the Co-existing Network of IPv 6 and IPv 4 under Various Transition Mechanisms”, Proceedings of the Third International Conference of Information Technology and Applications (ICITA’ 05). Pace University 52
 References n http: //www. ietf. org/html. charters/v 6 ops-charter. html n Evaluation of Transition Mechanisms for Unmanaged n n n n Networks (RFC 3904) Unmanaged Networks IPv 6 Transition Scenarios (RFC 3750) Basic Transition Mechanisms for IPv 6 Hosts and Routers (RFC 4213) IPv 6 Enterprise Network Scenarios (RFC 4057) Application Aspects of IPv 6 Transition (RFC 4038) Reasons to Move NAT-PT to Experimental (IETF draft) IPv 6 Enterprise Network Analysis (IETF draft) Hagen, Silvia, “IPv 6 Essentials”, O’Reilly, 2002. Pace University 53
References n http: //www. ietf. org/html. charters/v 6 ops-charter. html n Evaluation of Transition Mechanisms for Unmanaged n n n n Networks (RFC 3904) Unmanaged Networks IPv 6 Transition Scenarios (RFC 3750) Basic Transition Mechanisms for IPv 6 Hosts and Routers (RFC 4213) IPv 6 Enterprise Network Scenarios (RFC 4057) Application Aspects of IPv 6 Transition (RFC 4038) Reasons to Move NAT-PT to Experimental (IETF draft) IPv 6 Enterprise Network Analysis (IETF draft) Hagen, Silvia, “IPv 6 Essentials”, O’Reilly, 2002. Pace University 53
 Appendix A n IETF – International Engineering Task Force (http: //www. ietf. org): organization that governs Internet Protocol standards from drafts to standards n IAB – Internet Architecture Board (http: //www. iab. org): committee of IETF and advisory to ISOC. They provide architectural oversight of IETF activities n ISOC – Internet Society (http: //www. isoc. org): provides leadership in addressing issues that confront the future of the Internet; home of Internet Infrastructure standards n IANA – Internet Assigned Numbers Authority (http: //www. iana. org: preserves the central coordinating functions of the Internet (Regional Registries: ARIN, RIPE-NCC, APNIC, LACNIC, Afri. NIC) n ARIN – American Registry for Internet Numbers (http: //www. arin. net): develop policies for IP address allocations n Global IPv 6 Forum (http: //www. ipv 6 forum. com): promote IPv 6 development and deployment. They support est. 35 Task Force sub chapters mostly by country n North American IPv 6 Task Force (http: //www. nav 6 tf. org): provide technical leadership and innovative thought for the successful integration of IPv 6 into all facets of networking and telecommunications infrastructure n IPv 6 6 Bone Test. Bed: http: //www. 6 bone. net/ Pace University 54
Appendix A n IETF – International Engineering Task Force (http: //www. ietf. org): organization that governs Internet Protocol standards from drafts to standards n IAB – Internet Architecture Board (http: //www. iab. org): committee of IETF and advisory to ISOC. They provide architectural oversight of IETF activities n ISOC – Internet Society (http: //www. isoc. org): provides leadership in addressing issues that confront the future of the Internet; home of Internet Infrastructure standards n IANA – Internet Assigned Numbers Authority (http: //www. iana. org: preserves the central coordinating functions of the Internet (Regional Registries: ARIN, RIPE-NCC, APNIC, LACNIC, Afri. NIC) n ARIN – American Registry for Internet Numbers (http: //www. arin. net): develop policies for IP address allocations n Global IPv 6 Forum (http: //www. ipv 6 forum. com): promote IPv 6 development and deployment. They support est. 35 Task Force sub chapters mostly by country n North American IPv 6 Task Force (http: //www. nav 6 tf. org): provide technical leadership and innovative thought for the successful integration of IPv 6 into all facets of networking and telecommunications infrastructure n IPv 6 6 Bone Test. Bed: http: //www. 6 bone. net/ Pace University 54
 Appendix B The IPv 6 Portal (no longer http: //hs 247. com) n Microsoft Technet: IPv 6 Overview n Microsoft XP IPv 6 Install n HP/Compaq IPv 6 Website n IPv 6 enablement at IBM n Cisco IPv 6 Introduction n Sun IPv 6 Overview n Peter Bieringer Linux: IPv 6 n C: > ping 6 ff 02: : 1 (ping all local nodes using multicast address) Pace University 55
Appendix B The IPv 6 Portal (no longer http: //hs 247. com) n Microsoft Technet: IPv 6 Overview n Microsoft XP IPv 6 Install n HP/Compaq IPv 6 Website n IPv 6 enablement at IBM n Cisco IPv 6 Introduction n Sun IPv 6 Overview n Peter Bieringer Linux: IPv 6 n C: > ping 6 ff 02: : 1 (ping all local nodes using multicast address) Pace University 55
 Appendix C n Apple instructions: MAC OS X IPv 6 man page n From IPv 6 Portal: To enable IPv 6 on OS X follow these instructions: Open up a terminal. Type /sbin/ifconfig -a to list your devices. You should see something like: en 0: flags=8863 mtu 1500 inet 6 fe 80: : 203: 93 ff: fe 67: 80 b 2%en 0 prefixlen 64 scopeid 0 x 4 ether 00: 03: 93: 67: 80: b 2 inet 192. 168. 1. 101 netmask 0 xffffff 00 broadcast 192. 168. 1. 255 media: autoselect (none) status: active Find the one that says “status: active”, usually this is en 0. If it’s not, be sure to replace en 0 with whatever it is in later instructions. Type: sudo ip 6 config start-v 6 en 0; sudo ip 6 config start-stf en 0 Pace University 56
Appendix C n Apple instructions: MAC OS X IPv 6 man page n From IPv 6 Portal: To enable IPv 6 on OS X follow these instructions: Open up a terminal. Type /sbin/ifconfig -a to list your devices. You should see something like: en 0: flags=8863 mtu 1500 inet 6 fe 80: : 203: 93 ff: fe 67: 80 b 2%en 0 prefixlen 64 scopeid 0 x 4 ether 00: 03: 93: 67: 80: b 2 inet 192. 168. 1. 101 netmask 0 xffffff 00 broadcast 192. 168. 1. 255 media: autoselect (none) status: active Find the one that says “status: active”, usually this is en 0. If it’s not, be sure to replace en 0 with whatever it is in later instructions. Type: sudo ip 6 config start-v 6 en 0; sudo ip 6 config start-stf en 0 Pace University 56


