 IPSec In Depth
IPSec In Depth
 Encapsulated Security Payload (ESP) • Must encrypt and/or authenticate in each packet • Encryption occurs before authentication • Authentication is applied to data in the IPSec header as well as the data contained as payload
Encapsulated Security Payload (ESP) • Must encrypt and/or authenticate in each packet • Encryption occurs before authentication • Authentication is applied to data in the IPSec header as well as the data contained as payload
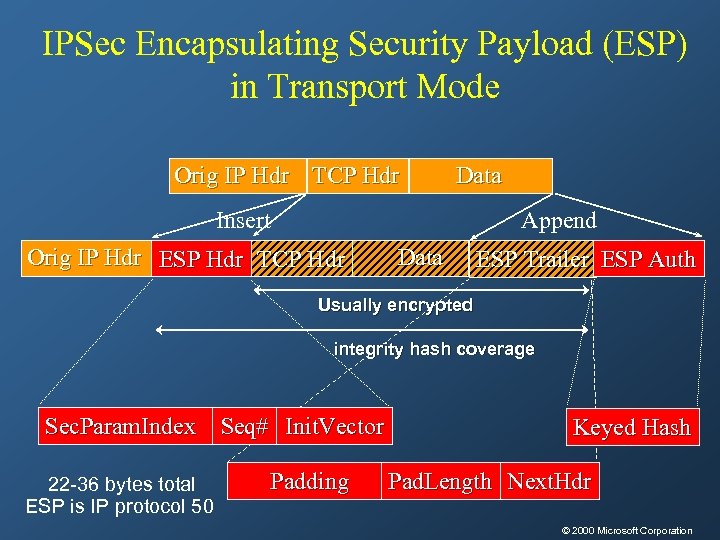 IPSec Encapsulating Security Payload (ESP) in Transport Mode Orig IP Hdr TCP Hdr Data Insert Append Orig IP Hdr ESP Hdr TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage Sec. Param. Index Seq# Init. Vector 22 -36 bytes total ESP is IP protocol 50 Padding Keyed Hash Pad. Length Next. Hdr © 2000 Microsoft Corporation
IPSec Encapsulating Security Payload (ESP) in Transport Mode Orig IP Hdr TCP Hdr Data Insert Append Orig IP Hdr ESP Hdr TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage Sec. Param. Index Seq# Init. Vector 22 -36 bytes total ESP is IP protocol 50 Padding Keyed Hash Pad. Length Next. Hdr © 2000 Microsoft Corporation
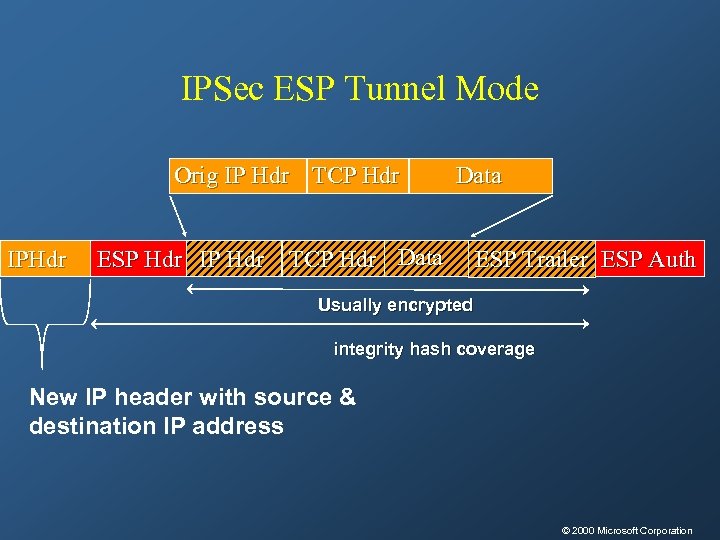 IPSec ESP Tunnel Mode Orig IP Hdr TCP Hdr IPHdr ESP Hdr IP Hdr Data TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage New IP header with source & destination IP address © 2000 Microsoft Corporation
IPSec ESP Tunnel Mode Orig IP Hdr TCP Hdr IPHdr ESP Hdr IP Hdr Data TCP Hdr Data ESP Trailer ESP Auth Usually encrypted integrity hash coverage New IP header with source & destination IP address © 2000 Microsoft Corporation
 Authentication Header (AH) • Authentication is applied to the entire packet, with the mutable fields in the IP header zeroed out • If both ESP and AH are applied to a packet, AH follows ESP
Authentication Header (AH) • Authentication is applied to the entire packet, with the mutable fields in the IP header zeroed out • If both ESP and AH are applied to a packet, AH follows ESP
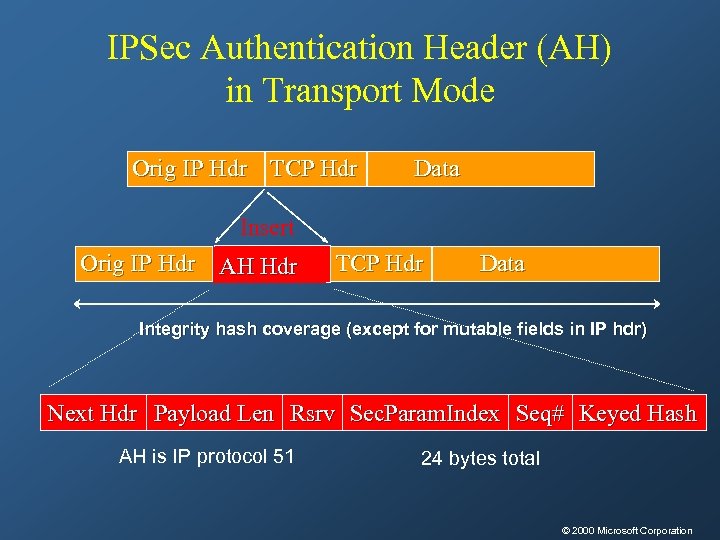 IPSec Authentication Header (AH) in Transport Mode Orig IP Hdr TCP Hdr Data Insert Orig IP Hdr AH Hdr TCP Hdr Data Integrity hash coverage (except for mutable fields in IP hdr) Next Hdr Payload Len Rsrv Sec. Param. Index Seq# Keyed Hash AH is IP protocol 51 24 bytes total © 2000 Microsoft Corporation
IPSec Authentication Header (AH) in Transport Mode Orig IP Hdr TCP Hdr Data Insert Orig IP Hdr AH Hdr TCP Hdr Data Integrity hash coverage (except for mutable fields in IP hdr) Next Hdr Payload Len Rsrv Sec. Param. Index Seq# Keyed Hash AH is IP protocol 51 24 bytes total © 2000 Microsoft Corporation
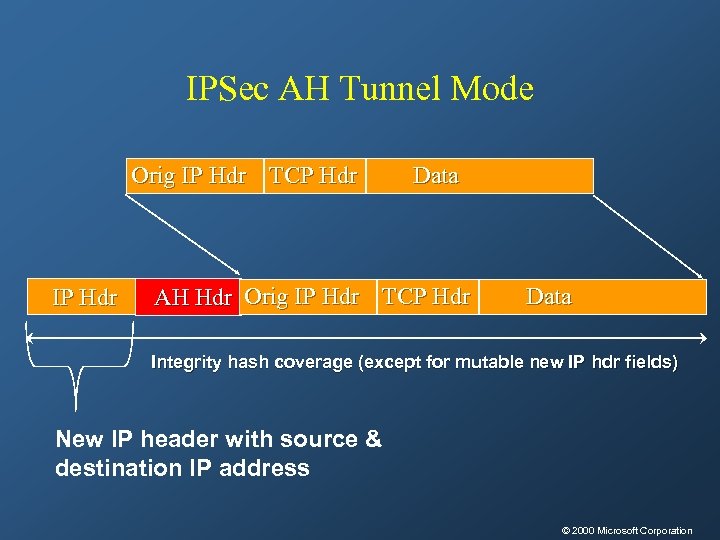 IPSec AH Tunnel Mode Orig IP Hdr TCP Hdr IP Hdr Data AH Hdr Orig IP Hdr TCP Hdr Data Integrity hash coverage (except for mutable new IP hdr fields) New IP header with source & destination IP address © 2000 Microsoft Corporation
IPSec AH Tunnel Mode Orig IP Hdr TCP Hdr IP Hdr Data AH Hdr Orig IP Hdr TCP Hdr Data Integrity hash coverage (except for mutable new IP hdr fields) New IP header with source & destination IP address © 2000 Microsoft Corporation
 Internet Key Exchange (IKE) • Phase I – Establish a secure channel(ISAKMP SA) – Authenticate computer identity • Phase II – Establishes a secure channel between computers intended for the transmission of data (IPSec SA)
Internet Key Exchange (IKE) • Phase I – Establish a secure channel(ISAKMP SA) – Authenticate computer identity • Phase II – Establishes a secure channel between computers intended for the transmission of data (IPSec SA)
 Main Mode • Main mode negotiates an ISAKMP SA which will be used to create IPSec Sas • Three steps – SA negotiation – Diffie-Hellman and nonce exchange – Authentication
Main Mode • Main mode negotiates an ISAKMP SA which will be used to create IPSec Sas • Three steps – SA negotiation – Diffie-Hellman and nonce exchange – Authentication
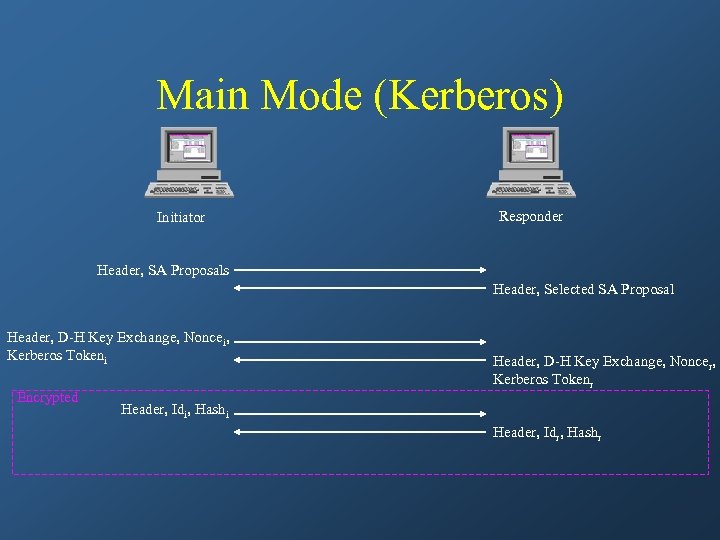 Main Mode (Kerberos) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei, Kerberos Tokeni Encrypted Header, D-H Key Exchange, Noncer, Kerberos Tokenr Header, Idi, Hashi Header, Idr, Hashr
Main Mode (Kerberos) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei, Kerberos Tokeni Encrypted Header, D-H Key Exchange, Noncer, Kerberos Tokenr Header, Idi, Hashi Header, Idr, Hashr
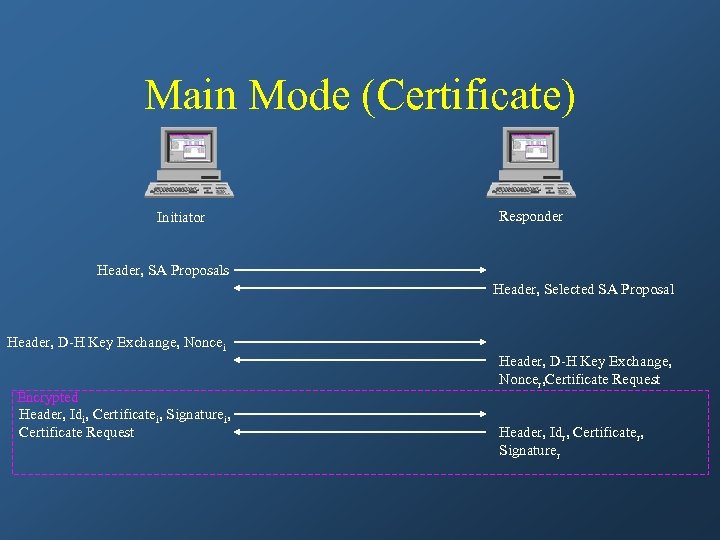 Main Mode (Certificate) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei Encrypted Header, Idi, Certificatei, Signaturei, Certificate Request Header, D-H Key Exchange, Noncer, Certificate Request Header, Idr, Certificater, Signaturer
Main Mode (Certificate) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei Encrypted Header, Idi, Certificatei, Signaturei, Certificate Request Header, D-H Key Exchange, Noncer, Certificate Request Header, Idr, Certificater, Signaturer
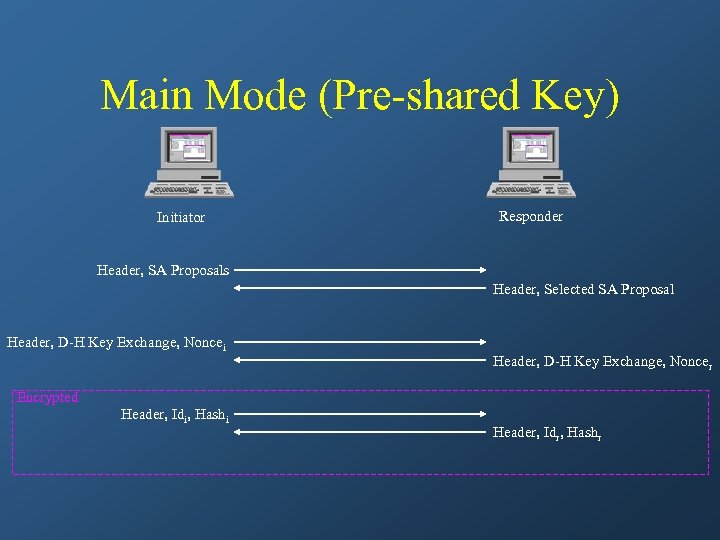 Main Mode (Pre-shared Key) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei Header, D-H Key Exchange, Noncer Encrypted Header, Idi, Hashi Header, Idr, Hashr
Main Mode (Pre-shared Key) Initiator Responder Header, SA Proposals Header, Selected SA Proposal Header, D-H Key Exchange, Noncei Header, D-H Key Exchange, Noncer Encrypted Header, Idi, Hashi Header, Idr, Hashr
 Quick Mode • All traffic is encrypted using the ISAKMP Security Association • Each quick mode negotiation results in two IPSec Security Associations (one inbound, one outbound)
Quick Mode • All traffic is encrypted using the ISAKMP Security Association • Each quick mode negotiation results in two IPSec Security Associations (one inbound, one outbound)
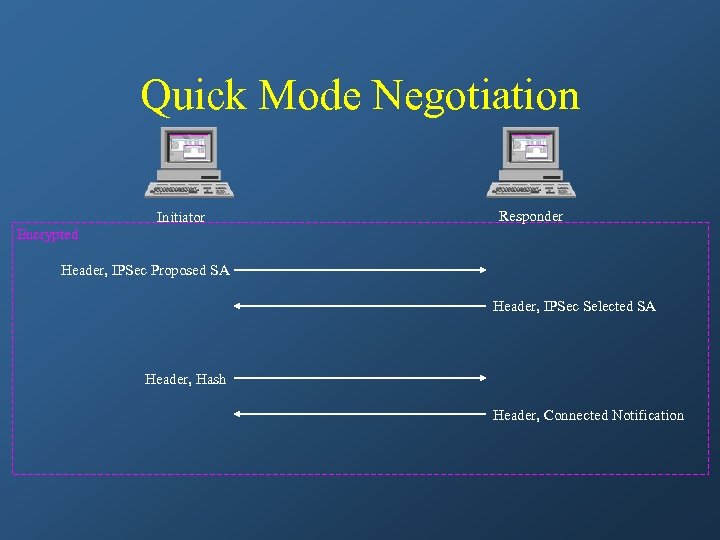 Quick Mode Negotiation Initiator Responder Encrypted Header, IPSec Proposed SA Header, IPSec Selected SA Header, Hash Header, Connected Notification
Quick Mode Negotiation Initiator Responder Encrypted Header, IPSec Proposed SA Header, IPSec Selected SA Header, Hash Header, Connected Notification