7f8acc14a53ac8f871519e74b74292db.ppt
- Количество слайдов: 47
 IP Security
IP Security
 IP Security n Have a range of application specific security mechanisms u eg. S/MIME, PGP, Kerberos, SSL/HTTPS However there are security concerns that cut across protocol layers n Would like security implemented by the network for all applications n
IP Security n Have a range of application specific security mechanisms u eg. S/MIME, PGP, Kerberos, SSL/HTTPS However there are security concerns that cut across protocol layers n Would like security implemented by the network for all applications n
 IPSec General IP Security mechanisms n Provides n u authentication u confidentiality u key management n Applicable to use over LANs, across public & private WANs, & for the Internet
IPSec General IP Security mechanisms n Provides n u authentication u confidentiality u key management n Applicable to use over LANs, across public & private WANs, & for the Internet
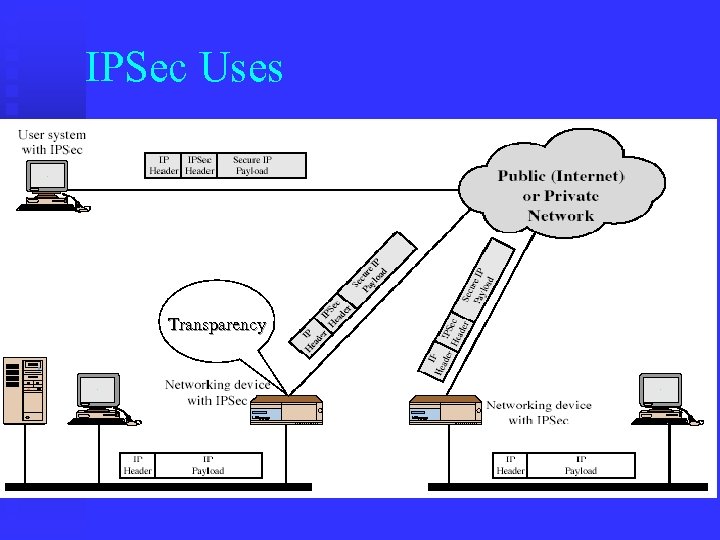 IPSec Uses Transparency
IPSec Uses Transparency
 VPN n Application-level VPN u E. g. , tunnel through ssh u Analogous to app-level gateways n IPSec-based VPN u Analogous to packet-filtering firewalls
VPN n Application-level VPN u E. g. , tunnel through ssh u Analogous to app-level gateways n IPSec-based VPN u Analogous to packet-filtering firewalls
 Benefits of IPSec In a firewall/router, provides strong security to all traffic crossing the perimeter n Is below transport layer, hence transparent to applications n Can be transparent to end users n Can provide security for individual even mobile users n Secures routing architecture n
Benefits of IPSec In a firewall/router, provides strong security to all traffic crossing the perimeter n Is below transport layer, hence transparent to applications n Can be transparent to end users n Can provide security for individual even mobile users n Secures routing architecture n
 IP Security Architecture Specification is quite complex n Defined in numerous RFC’s n u incl. RFC 2401/2402/2406/2408 u many others, grouped by category Mandatory in IPv 6, optional in IPv 4 n Have two security header extensions: n u Authentication Header (AH) u Encapsulating Security Payload (ESP)
IP Security Architecture Specification is quite complex n Defined in numerous RFC’s n u incl. RFC 2401/2402/2406/2408 u many others, grouped by category Mandatory in IPv 6, optional in IPv 4 n Have two security header extensions: n u Authentication Header (AH) u Encapsulating Security Payload (ESP)
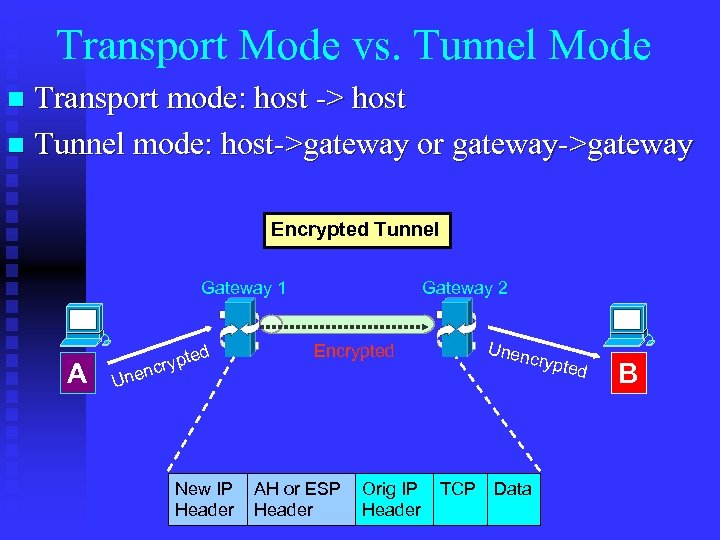 Transport Mode vs. Tunnel Mode Transport mode: host -> host n Tunnel mode: host->gateway or gateway->gateway n Encrypted Tunnel Gateway 1 A ed rypt c Gateway 2 Unen Encrypted crypt U nen New IP Header AH or ESP Header Orig IP Header TCP Data ed B
Transport Mode vs. Tunnel Mode Transport mode: host -> host n Tunnel mode: host->gateway or gateway->gateway n Encrypted Tunnel Gateway 1 A ed rypt c Gateway 2 Unen Encrypted crypt U nen New IP Header AH or ESP Header Orig IP Header TCP Data ed B
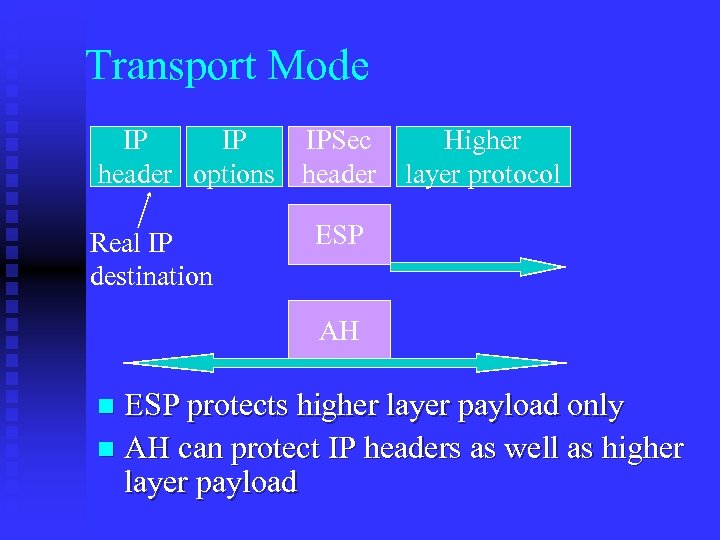 Transport Mode IP IP IPSec header options header Real IP destination Higher layer protocol ESP AH ESP protects higher layer payload only n AH can protect IP headers as well as higher layer payload n
Transport Mode IP IP IPSec header options header Real IP destination Higher layer protocol ESP AH ESP protects higher layer payload only n AH can protect IP headers as well as higher layer payload n
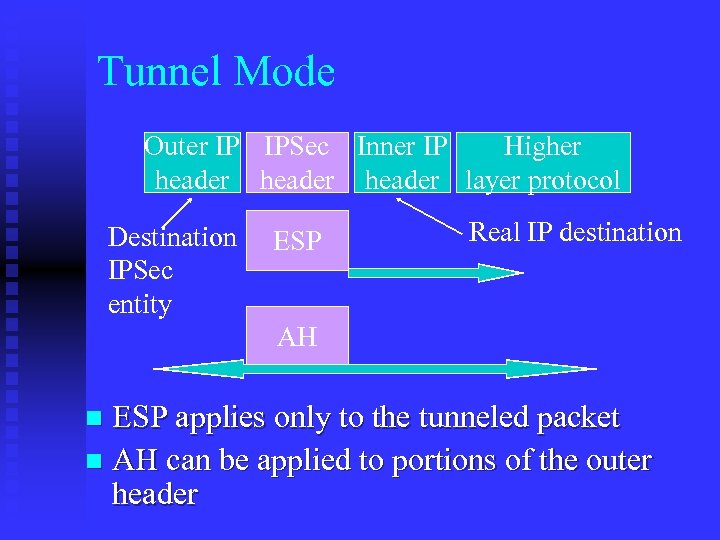 Tunnel Mode Outer IP IPSec Inner IP Higher header layer protocol Destination IPSec entity ESP Real IP destination AH ESP applies only to the tunneled packet n AH can be applied to portions of the outer header n
Tunnel Mode Outer IP IPSec Inner IP Higher header layer protocol Destination IPSec entity ESP Real IP destination AH ESP applies only to the tunneled packet n AH can be applied to portions of the outer header n
 IPSec Pros Hides the identity of your network n Provides secure channel: confidentiality, authenticity, and integrity n Connects sites (e. g. , branch offices) with a costeffective secure network compared with leased lines n Allows user to work from home and mobile hosts n
IPSec Pros Hides the identity of your network n Provides secure channel: confidentiality, authenticity, and integrity n Connects sites (e. g. , branch offices) with a costeffective secure network compared with leased lines n Allows user to work from home and mobile hosts n
 IPSec Cons A single failure in the path disconnect the entire network. Also cause performance bottlenecks. n Incompatible with NAT/PAT depending on the architecture n Tunneled traffic is undetected by IDS n VPN gateways might be compromised which leads to uncovering protected data n
IPSec Cons A single failure in the path disconnect the entire network. Also cause performance bottlenecks. n Incompatible with NAT/PAT depending on the architecture n Tunneled traffic is undetected by IDS n VPN gateways might be compromised which leads to uncovering protected data n
 Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
 Authentication Header n Data integrity u Entire packet has not been tampered with n Authentication u Can “trust” IP address source Anti-replay feature n Integrity check value n
Authentication Header n Data integrity u Entire packet has not been tampered with n Authentication u Can “trust” IP address source Anti-replay feature n Integrity check value n
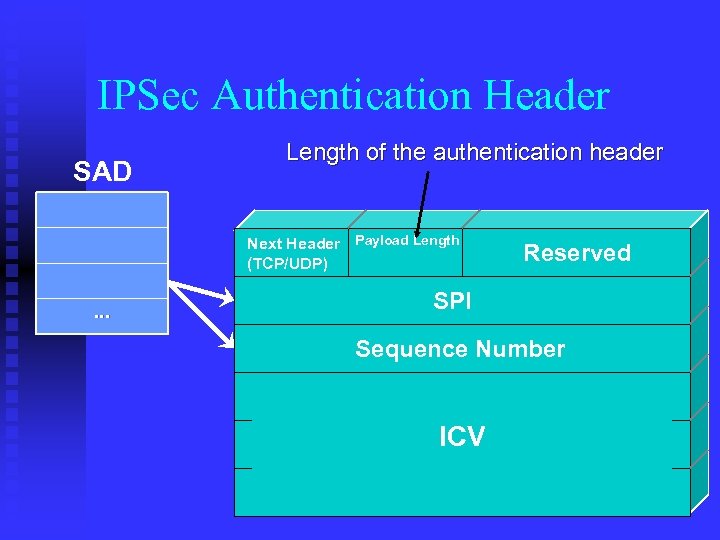 IPSec Authentication Header SAD Length of the authentication header Next Header Payload Length (TCP/UDP) … Reserved SPI Sequence Number ICV
IPSec Authentication Header SAD Length of the authentication header Next Header Payload Length (TCP/UDP) … Reserved SPI Sequence Number ICV
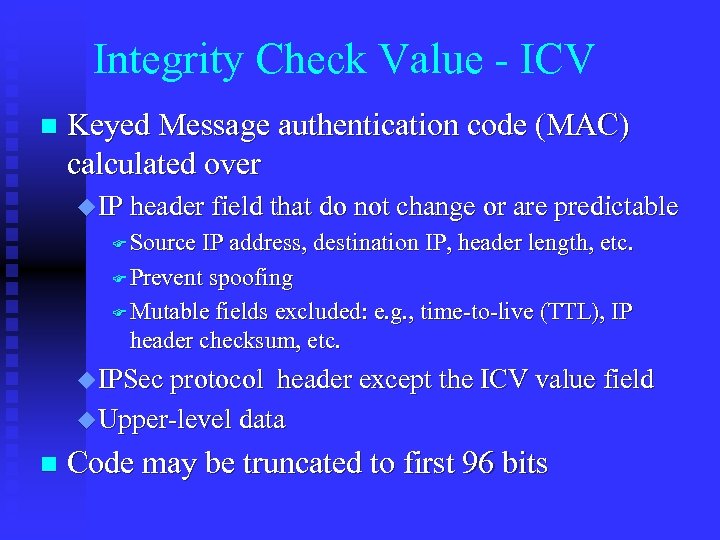 Integrity Check Value - ICV n Keyed Message authentication code (MAC) calculated over u IP header field that do not change or are predictable F Source IP address, destination IP, header length, etc. F Prevent spoofing F Mutable fields excluded: e. g. , time-to-live (TTL), IP header checksum, etc. u IPSec protocol header except the ICV value field u Upper-level data n Code may be truncated to first 96 bits
Integrity Check Value - ICV n Keyed Message authentication code (MAC) calculated over u IP header field that do not change or are predictable F Source IP address, destination IP, header length, etc. F Prevent spoofing F Mutable fields excluded: e. g. , time-to-live (TTL), IP header checksum, etc. u IPSec protocol header except the ICV value field u Upper-level data n Code may be truncated to first 96 bits
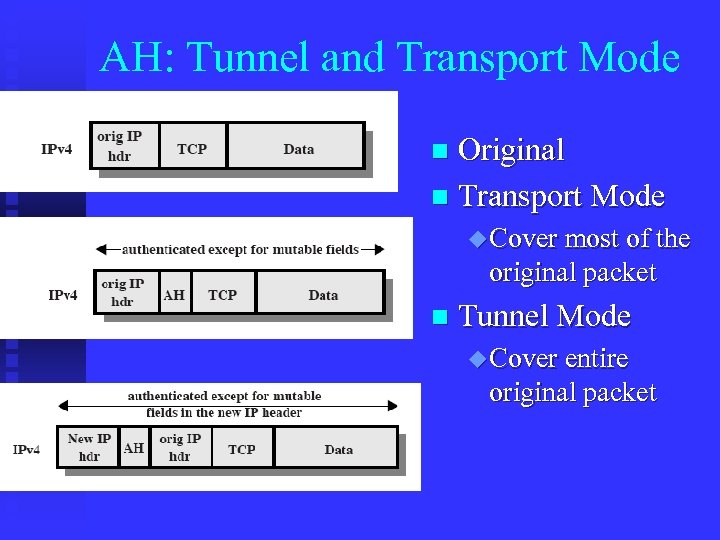 AH: Tunnel and Transport Mode Original n Transport Mode n u Cover most of the original packet n Tunnel Mode u Cover entire original packet
AH: Tunnel and Transport Mode Original n Transport Mode n u Cover most of the original packet n Tunnel Mode u Cover entire original packet
 Encapsulating Security Payload (ESP) Provide message content confidentiality n Provide limited traffic flow confidentiality n Can optionally provide the same authentication services as AH n Supports range of ciphers, modes, padding n u Incl. DES, Triple-DES, RC 5, IDEA, CAST etc u Pad to meet blocksize, for traffic flow
Encapsulating Security Payload (ESP) Provide message content confidentiality n Provide limited traffic flow confidentiality n Can optionally provide the same authentication services as AH n Supports range of ciphers, modes, padding n u Incl. DES, Triple-DES, RC 5, IDEA, CAST etc u Pad to meet blocksize, for traffic flow
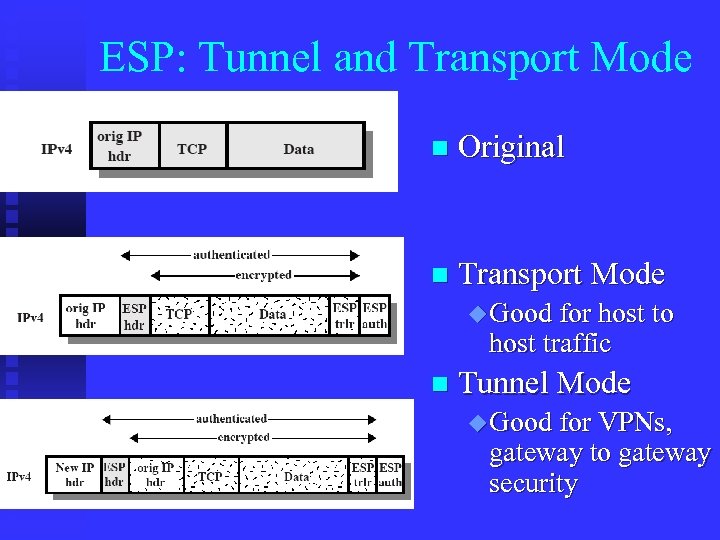 ESP: Tunnel and Transport Mode n Original n Transport Mode u Good for host to host traffic n Tunnel Mode u Good for VPNs, gateway to gateway security
ESP: Tunnel and Transport Mode n Original n Transport Mode u Good for host to host traffic n Tunnel Mode u Good for VPNs, gateway to gateway security
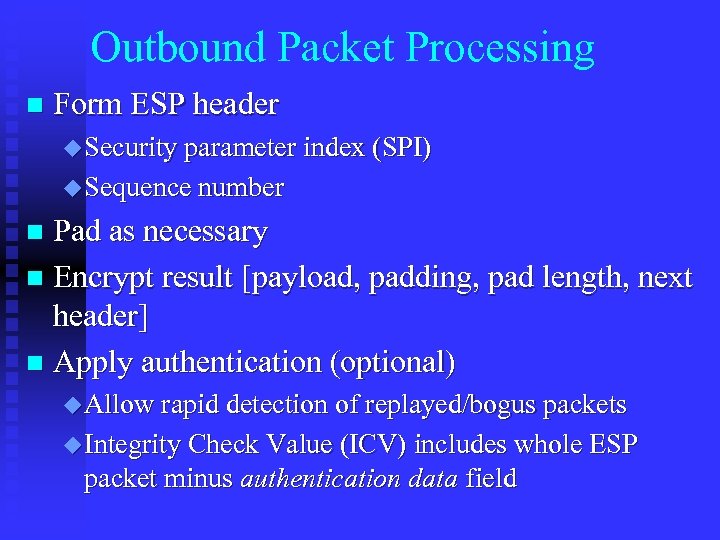 Outbound Packet Processing n Form ESP header u Security parameter index (SPI) u Sequence number Pad as necessary n Encrypt result [payload, padding, pad length, next header] n Apply authentication (optional) n u Allow rapid detection of replayed/bogus packets u Integrity Check Value (ICV) includes whole ESP packet minus authentication data field
Outbound Packet Processing n Form ESP header u Security parameter index (SPI) u Sequence number Pad as necessary n Encrypt result [payload, padding, pad length, next header] n Apply authentication (optional) n u Allow rapid detection of replayed/bogus packets u Integrity Check Value (ICV) includes whole ESP packet minus authentication data field
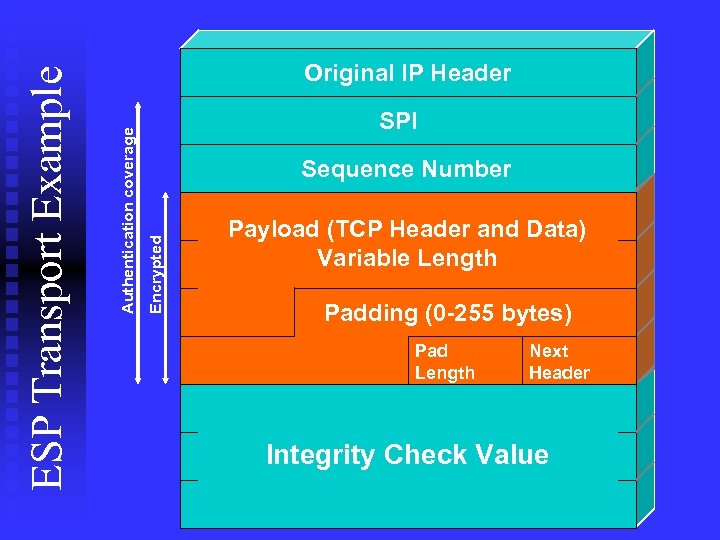 SPI Sequence Number Encrypted Authentication coverage ESP Transport Example Original IP Header Payload (TCP Header and Data) Variable Length Padding (0 -255 bytes) Pad Length Next Header Integrity Check Value
SPI Sequence Number Encrypted Authentication coverage ESP Transport Example Original IP Header Payload (TCP Header and Data) Variable Length Padding (0 -255 bytes) Pad Length Next Header Integrity Check Value
 Inbound Packet Processing. . . n Sequence number checking u Duplicates are rejected! n Packet decryption u Decrypt quantity [ESP payload, padding, pad length, next header] per SA specification u Processing (stripping) padding per encryption algorithm u Reconstruct the original IP datagram n Authentication verification (optional) u Allow potential parallel processing - decryption & verifying authentication code
Inbound Packet Processing. . . n Sequence number checking u Duplicates are rejected! n Packet decryption u Decrypt quantity [ESP payload, padding, pad length, next header] per SA specification u Processing (stripping) padding per encryption algorithm u Reconstruct the original IP datagram n Authentication verification (optional) u Allow potential parallel processing - decryption & verifying authentication code
 Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
 NATs n n Network address translation = local, LAN-specific address space translated to small number of globally routable IP addresses Motivation: u Scarce address space u Security: prevent unsolicited inbound requests n Prevalence of NATs u Claim: 50% of broadband users are behind NATs u All Linksys/D-Link/Netgear home routers are NATs
NATs n n Network address translation = local, LAN-specific address space translated to small number of globally routable IP addresses Motivation: u Scarce address space u Security: prevent unsolicited inbound requests n Prevalence of NATs u Claim: 50% of broadband users are behind NATs u All Linksys/D-Link/Netgear home routers are NATs
 NAT types All use net-10/8 (10. *. *. *) or 192. 168/16 n Address translation n Address-and-port translation (NAPT) n u most common form today, still called NAT u one external (global) IP address n Change IP header and TCP/UDP headers
NAT types All use net-10/8 (10. *. *. *) or 192. 168/16 n Address translation n Address-and-port translation (NAPT) n u most common form today, still called NAT u one external (global) IP address n Change IP header and TCP/UDP headers
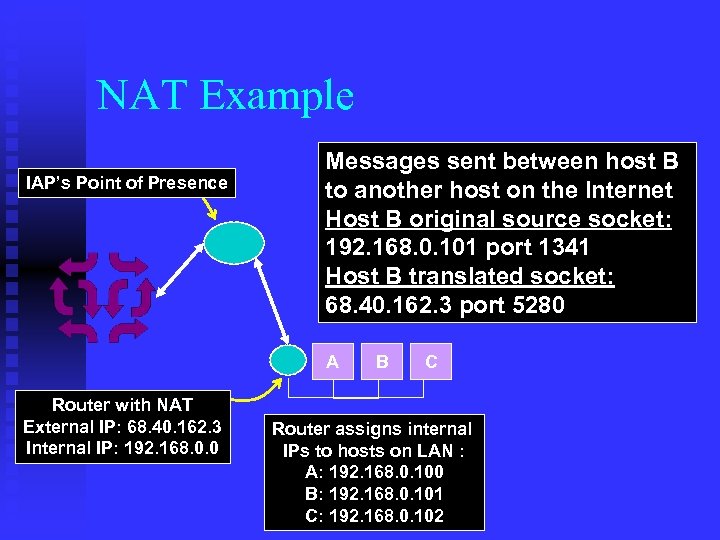 NAT Example IAP’s Point of Presence Messages sent between host B to another host on the Internet Host B original source socket: 192. 168. 0. 101 port 1341 Host B translated socket: 68. 40. 162. 3 port 5280 A Router with NAT External IP: 68. 40. 162. 3 Internal IP: 192. 168. 0. 0 B C Router assigns internal IPs to hosts on LAN : A: 192. 168. 0. 100 B: 192. 168. 0. 101 C: 192. 168. 0. 102
NAT Example IAP’s Point of Presence Messages sent between host B to another host on the Internet Host B original source socket: 192. 168. 0. 101 port 1341 Host B translated socket: 68. 40. 162. 3 port 5280 A Router with NAT External IP: 68. 40. 162. 3 Internal IP: 192. 168. 0. 0 B C Router assigns internal IPs to hosts on LAN : A: 192. 168. 0. 100 B: 192. 168. 0. 101 C: 192. 168. 0. 102
 Will IPSec Work with NAT ? n n n Consider both AH and ESP protocols. For NAT, only source IP changes (no port # change) Consider both transport and tunnel modes. For tunnel mode, consider the following two cases u u n n Sender – NAT – IPSec Gateway 1 – IPSec Gateway 2 – Receiver Sender – IPSec Gateway 1 – NAT – IPSec Gateway 2 – Receiver What about with port # translation? Practical solutions for NAT to work w/ IPSec u u IPSec – NAC Compatibility Requirements: RFC 3715 UDP Encapsulation of IPsec ESP Packets: RFC 3948
Will IPSec Work with NAT ? n n n Consider both AH and ESP protocols. For NAT, only source IP changes (no port # change) Consider both transport and tunnel modes. For tunnel mode, consider the following two cases u u n n Sender – NAT – IPSec Gateway 1 – IPSec Gateway 2 – Receiver Sender – IPSec Gateway 1 – NAT – IPSec Gateway 2 – Receiver What about with port # translation? Practical solutions for NAT to work w/ IPSec u u IPSec – NAC Compatibility Requirements: RFC 3715 UDP Encapsulation of IPsec ESP Packets: RFC 3948
 Backup Slides
Backup Slides
 Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
Architecture & Concepts Tunnel vs. Transport mode n Security association (SA) n u Security parameter index (SPI) u Security policy database (SPD) u SA database (SAD) Authentication header (AH) n Encapsulating security payload (ESP) n Practical Issues w/ NAT n
 Security Association - SA Have a database of Security Associations n Determine IPSec processing for senders n Determine IPSec decoding for destination n SAs are not fixed! Generated and customized per traffic flows n
Security Association - SA Have a database of Security Associations n Determine IPSec processing for senders n Determine IPSec decoding for destination n SAs are not fixed! Generated and customized per traffic flows n
 Security Parameters Index - SPI Can be up to 32 bits large n The SPI allows the destination to select the correct SA under which the received packet will be processed n u According to the agreement with the sender u The SPI is sent with the packet by the sender n SPI + Dest IP address + IPSec Protocol (AH or ESP) uniquely identifies a SA
Security Parameters Index - SPI Can be up to 32 bits large n The SPI allows the destination to select the correct SA under which the received packet will be processed n u According to the agreement with the sender u The SPI is sent with the packet by the sender n SPI + Dest IP address + IPSec Protocol (AH or ESP) uniquely identifies a SA
 SA Database - SAD n Holds parameters for each SA u Lifetime of this SA u AH and ESP information u Tunnel or transport mode n Every host or gateway participating in IPSec has their own SA database
SA Database - SAD n Holds parameters for each SA u Lifetime of this SA u AH and ESP information u Tunnel or transport mode n Every host or gateway participating in IPSec has their own SA database
 Security Policy Database - SPD What traffic to protect? n Policy entries define which SA or SA bundles to use on IP traffic n Each host or gateway has their own SPD n Index into SPD by Selector fields n u Dest IP, Source IP, IPSec Protocol, Transport Protocol, Source & Dest Ports, …
Security Policy Database - SPD What traffic to protect? n Policy entries define which SA or SA bundles to use on IP traffic n Each host or gateway has their own SPD n Index into SPD by Selector fields n u Dest IP, Source IP, IPSec Protocol, Transport Protocol, Source & Dest Ports, …
 Security Policy Database - SPD What traffic to protect? n Policy entries define which SA or SA bundles to use on IP traffic n Each host or gateway has their own SPD n Index into SPD by Selector fields n u Dest IP, Source IP, IPSec Protocol, Transport Protocol, Source & Dest Ports, …
Security Policy Database - SPD What traffic to protect? n Policy entries define which SA or SA bundles to use on IP traffic n Each host or gateway has their own SPD n Index into SPD by Selector fields n u Dest IP, Source IP, IPSec Protocol, Transport Protocol, Source & Dest Ports, …
 SPD Entry Actions n Discard u Do not let in or out n Bypass u Outbound: do not apply IPSec u Inbound: do not expect IPSec n Protect – will point to an SA or SA bundle u Outbound: apply security u Inbound: check that security must have been applied
SPD Entry Actions n Discard u Do not let in or out n Bypass u Outbound: do not apply IPSec u Inbound: do not expect IPSec n Protect – will point to an SA or SA bundle u Outbound: apply security u Inbound: check that security must have been applied
 SPD Protect Action n If the SA does not exist… u Outbound processing: use IKE to generate SA dynamically u Inbound processing: drop packet
SPD Protect Action n If the SA does not exist… u Outbound processing: use IKE to generate SA dynamically u Inbound processing: drop packet
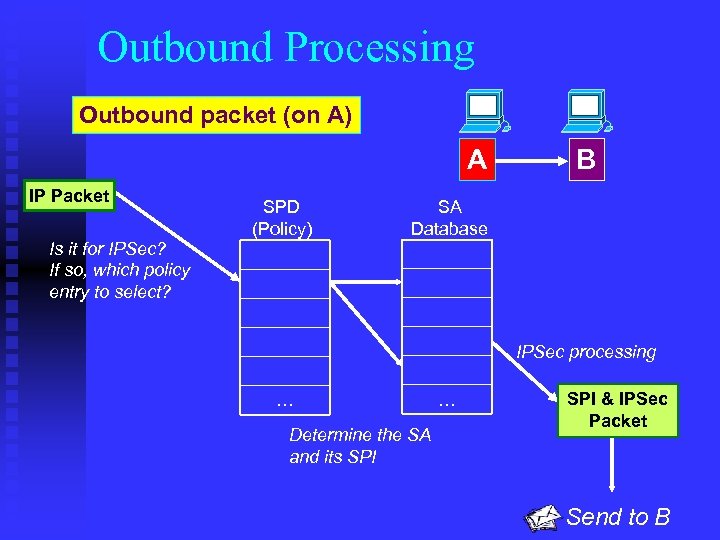 Outbound Processing Outbound packet (on A) A IP Packet Is it for IPSec? If so, which policy entry to select? SPD (Policy) B SA Database IPSec processing … Determine the SA and its SPI … SPI & IPSec Packet Send to B
Outbound Processing Outbound packet (on A) A IP Packet Is it for IPSec? If so, which policy entry to select? SPD (Policy) B SA Database IPSec processing … Determine the SA and its SPI … SPI & IPSec Packet Send to B
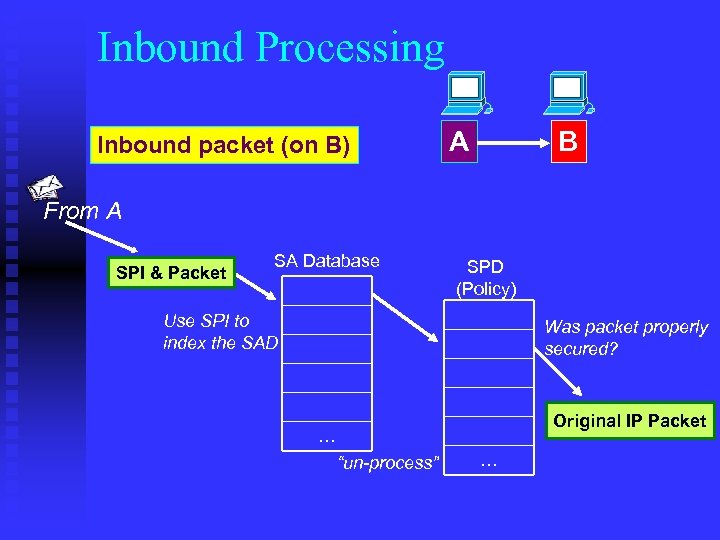 Inbound Processing Inbound packet (on B) A B From A SPI & Packet SA Database SPD (Policy) Use SPI to index the SAD Was packet properly secured? Original IP Packet … “un-process” …
Inbound Processing Inbound packet (on B) A B From A SPI & Packet SA Database SPD (Policy) Use SPI to index the SAD Was packet properly secured? Original IP Packet … “un-process” …
 Combining Security Associations SA’s can implement either AH or ESP n to implement both need to combine SA’s n u form a security association bundle u may terminate at different or same endpoints u combined by F transport adjacency F iterated tunneling n issue of authentication & encryption order
Combining Security Associations SA’s can implement either AH or ESP n to implement both need to combine SA’s n u form a security association bundle u may terminate at different or same endpoints u combined by F transport adjacency F iterated tunneling n issue of authentication & encryption order
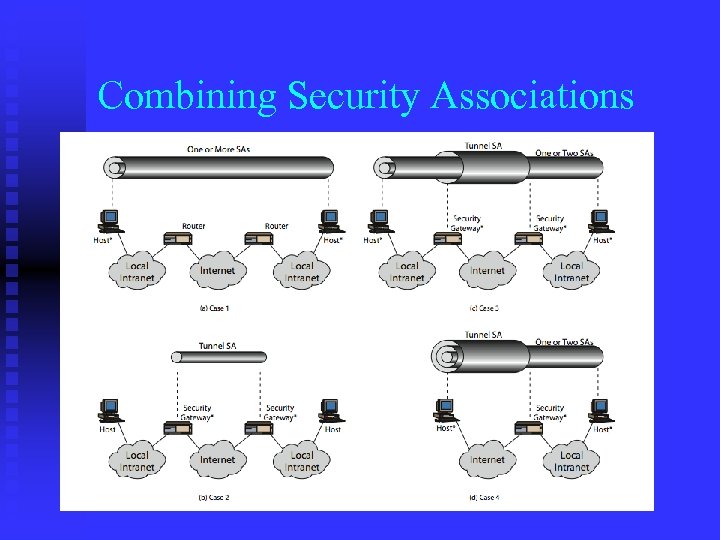 Combining Security Associations
Combining Security Associations
 SA Bundle More than 1 SA can apply to a packet n Example: ESP does not authenticate new IP header. How to authenticate? n u Use SA to apply ESP w/o authentication to original packet u Use 2 nd SA to apply AH
SA Bundle More than 1 SA can apply to a packet n Example: ESP does not authenticate new IP header. How to authenticate? n u Use SA to apply ESP w/o authentication to original packet u Use 2 nd SA to apply AH
 Outbound Packet Processing. . . n Integrity Check Value (ICV) calculation u ICV includes whole ESP packet minus authentication data field u Implicit padding of ‘ 0’s between next header and authentication data is used to satisfy block size requirement for ICV algorithm
Outbound Packet Processing. . . n Integrity Check Value (ICV) calculation u ICV includes whole ESP packet minus authentication data field u Implicit padding of ‘ 0’s between next header and authentication data is used to satisfy block size requirement for ICV algorithm
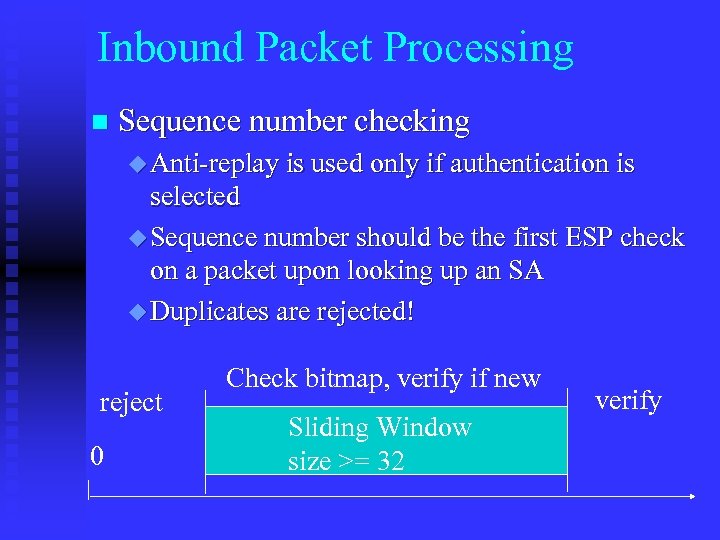 Inbound Packet Processing n Sequence number checking u Anti-replay is used only if authentication is selected u Sequence number should be the first ESP check on a packet upon looking up an SA u Duplicates are rejected! reject 0 Check bitmap, verify if new Sliding Window size >= 32 verify
Inbound Packet Processing n Sequence number checking u Anti-replay is used only if authentication is selected u Sequence number should be the first ESP check on a packet upon looking up an SA u Duplicates are rejected! reject 0 Check bitmap, verify if new Sliding Window size >= 32 verify
 Anti-replay Feature Optional n Information to enforce held in SA entry n Sequence number counter - 32 bit for outgoing IPSec packets n Anti-replay window n u 32 -bit u Bit-map for detecting replayed packets
Anti-replay Feature Optional n Information to enforce held in SA entry n Sequence number counter - 32 bit for outgoing IPSec packets n Anti-replay window n u 32 -bit u Bit-map for detecting replayed packets
 Anti-replay Sliding Window should not be advanced until the packet has been authenticated n Without authentication, malicious packets with large sequence numbers can advance window unnecessarily n u Valid packets would be dropped!
Anti-replay Sliding Window should not be advanced until the packet has been authenticated n Without authentication, malicious packets with large sequence numbers can advance window unnecessarily n u Valid packets would be dropped!
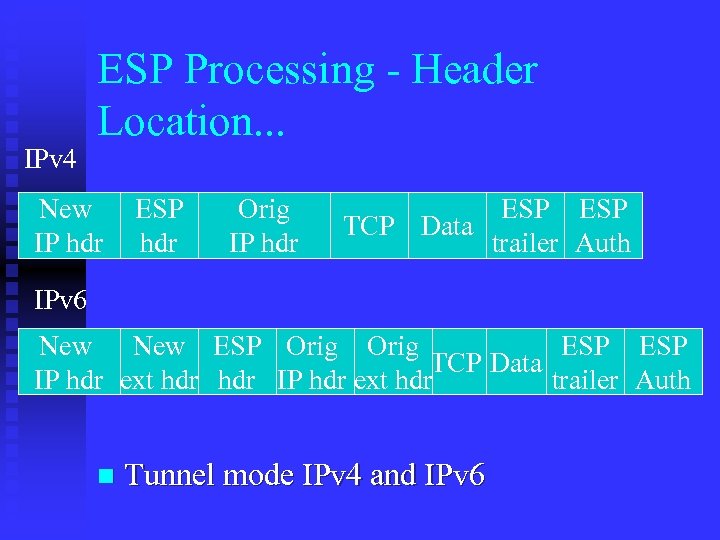 IPv 4 ESP Processing - Header Location. . . New IP hdr ESP hdr Orig IP hdr ESP TCP Data trailer Auth IPv 6 New ESP Orig ESP TCP Data IP hdr ext hdr trailer Auth n Tunnel mode IPv 4 and IPv 6
IPv 4 ESP Processing - Header Location. . . New IP hdr ESP hdr Orig IP hdr ESP TCP Data trailer Auth IPv 6 New ESP Orig ESP TCP Data IP hdr ext hdr trailer Auth n Tunnel mode IPv 4 and IPv 6
 Key Management Handles key generation & distribution n Typically need 2 pairs of keys n u 2 per direction for AH & ESP n Manual key management u Sysadmin manually configures every system n Automated key management u Automated system for on demand creation of keys for SA’s in large systems
Key Management Handles key generation & distribution n Typically need 2 pairs of keys n u 2 per direction for AH & ESP n Manual key management u Sysadmin manually configures every system n Automated key management u Automated system for on demand creation of keys for SA’s in large systems


