7f9d7dbfcd8366fbe2d0429d355cb502.ppt
- Количество слайдов: 37
 IP Security and VPN Most of the slides are derived from the slides (Chapter-8) by the authors of «Computer Networking: A Top Down Approach» , and from the slides of Prof. Yan Chen from Northwestern University. 8 -1
IP Security and VPN Most of the slides are derived from the slides (Chapter-8) by the authors of «Computer Networking: A Top Down Approach» , and from the slides of Prof. Yan Chen from Northwestern University. 8 -1
 IP Security v Have a range of application specific security mechanisms § eg. PGP, SSL/HTTPS v v However there are security concerns that cut across protocol layers Would like security implemented by the network for all applications 8 -2
IP Security v Have a range of application specific security mechanisms § eg. PGP, SSL/HTTPS v v However there are security concerns that cut across protocol layers Would like security implemented by the network for all applications 8 -2
 What is network-layer confidentiality ? between two network entities: v sending entity encrypts datagram payload, payload could be: § TCP or UDP segment, ICMP message, OSPF message …. v all data sent from one entity to other would be hidden: § web pages, e-mail, P 2 P file transfers, TCP SYN packets … v “blanket coverage” 8 -3
What is network-layer confidentiality ? between two network entities: v sending entity encrypts datagram payload, payload could be: § TCP or UDP segment, ICMP message, OSPF message …. v all data sent from one entity to other would be hidden: § web pages, e-mail, P 2 P file transfers, TCP SYN packets … v “blanket coverage” 8 -3
 Virtual Private Networks (VPNs) motivation: vinstitutions often want private networks for security. § costly: separate routers, links, DNS infrastructure. v. VPN: institution’s inter-office traffic is sent over public Internet instead § encrypted before entering public Internet § logically separate from other traffic 8 -4
Virtual Private Networks (VPNs) motivation: vinstitutions often want private networks for security. § costly: separate routers, links, DNS infrastructure. v. VPN: institution’s inter-office traffic is sent over public Internet instead § encrypted before entering public Internet § logically separate from other traffic 8 -4
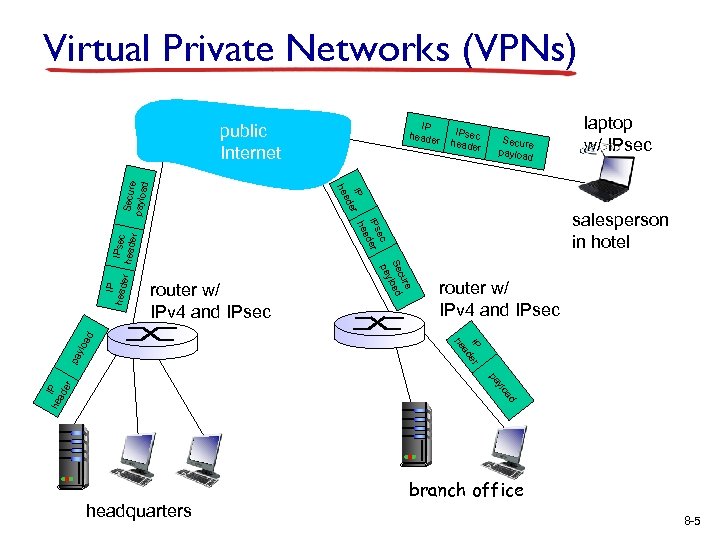 Virtual Private Networks (VPNs) IP header Secure payloa d IPsec heade r r router w/ IPv 4 and IPsec pa IP er ad he ylo a d router w/ IPv 4 and IPsec laptop w/ IPsec salesperson in hotel e cur Se load y pa IP heade IPsec header ec IPs der ea IP r h e ad he Secur e payloa d public Internet ad ylo I he P ad er pa headquarters branch office 8 -5
Virtual Private Networks (VPNs) IP header Secure payloa d IPsec heade r r router w/ IPv 4 and IPsec pa IP er ad he ylo a d router w/ IPv 4 and IPsec laptop w/ IPsec salesperson in hotel e cur Se load y pa IP heade IPsec header ec IPs der ea IP r h e ad he Secur e payloa d public Internet ad ylo I he P ad er pa headquarters branch office 8 -5
 Benefits of IPSec v v v In a firewall/router provides strong security to all traffic crossing the perimeter In a firewall/router is resistant to bypass Is below transport layer, hence transparent to applications Can be transparent to end users Can provide security for individual users Secures routing architecture 8 -6
Benefits of IPSec v v v In a firewall/router provides strong security to all traffic crossing the perimeter In a firewall/router is resistant to bypass Is below transport layer, hence transparent to applications Can be transparent to end users Can provide security for individual users Secures routing architecture 8 -6
 IPsec services v data integrity origin authentication replay attack prevention confidentiality v two protocols providing different service models: v v v § AH § ESP 8 -7
IPsec services v data integrity origin authentication replay attack prevention confidentiality v two protocols providing different service models: v v v § AH § ESP 8 -7
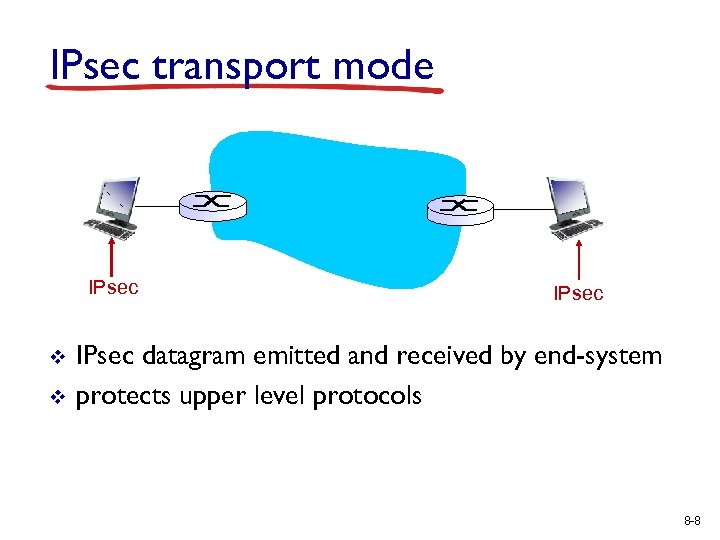 IPsec transport mode IPsec v v IPsec datagram emitted and received by end-system protects upper level protocols 8 -8
IPsec transport mode IPsec v v IPsec datagram emitted and received by end-system protects upper level protocols 8 -8
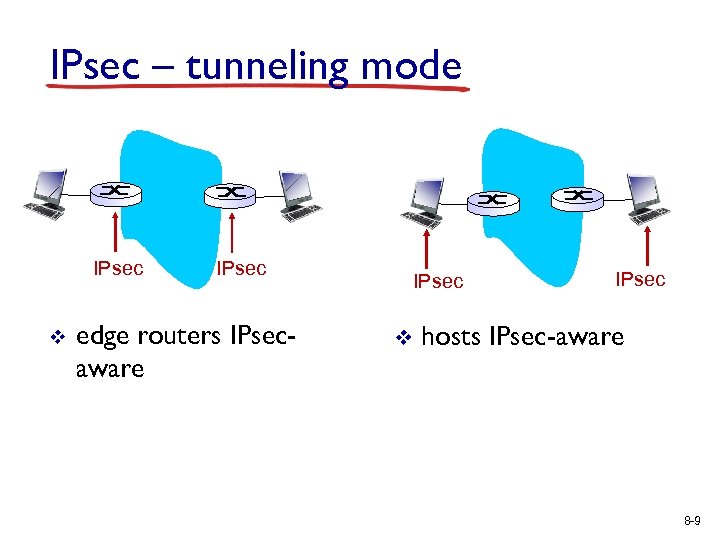 IPsec – tunneling mode IPsec v IPsec edge routers IPsecaware IPsec v IPsec hosts IPsec-aware 8 -9
IPsec – tunneling mode IPsec v IPsec edge routers IPsecaware IPsec v IPsec hosts IPsec-aware 8 -9
 Two IPsec protocols v Authentication Header (AH) protocol § provides source authentication & data integrity but not confidentiality v Encapsulation Security Protocol (ESP) § provides source authentication, data integrity, and confidentiality § more widely used than AH 8 -10
Two IPsec protocols v Authentication Header (AH) protocol § provides source authentication & data integrity but not confidentiality v Encapsulation Security Protocol (ESP) § provides source authentication, data integrity, and confidentiality § more widely used than AH 8 -10
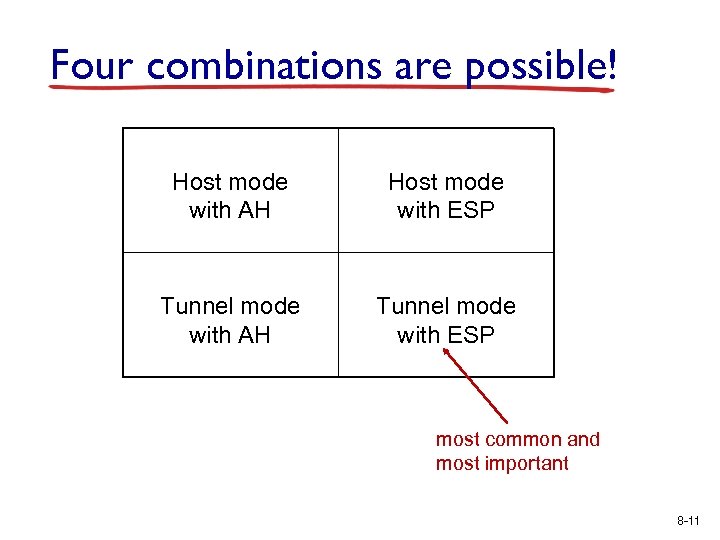 Four combinations are possible! Host mode with AH Host mode with ESP Tunnel mode with AH Tunnel mode with ESP most common and most important 8 -11
Four combinations are possible! Host mode with AH Host mode with ESP Tunnel mode with AH Tunnel mode with ESP most common and most important 8 -11
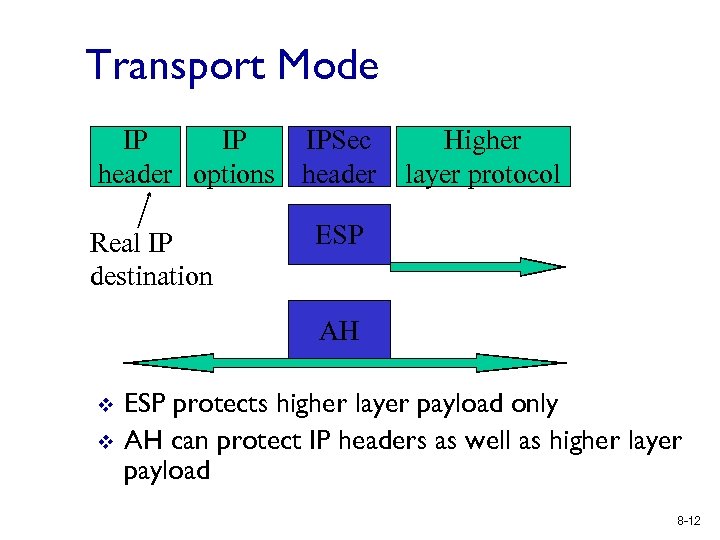 Transport Mode IP IP IPSec header options header Real IP destination Higher layer protocol ESP AH v v ESP protects higher layer payload only AH can protect IP headers as well as higher layer payload 8 -12
Transport Mode IP IP IPSec header options header Real IP destination Higher layer protocol ESP AH v v ESP protects higher layer payload only AH can protect IP headers as well as higher layer payload 8 -12
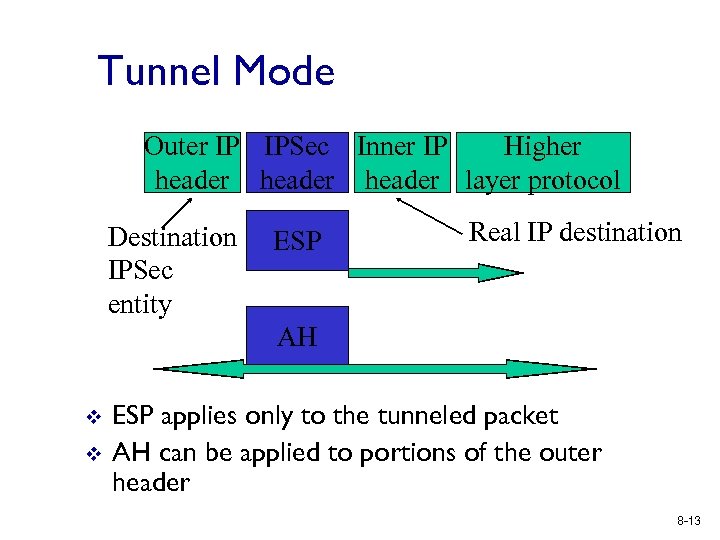 Tunnel Mode Outer IP IPSec Inner IP Higher header layer protocol Destination IPSec entity ESP Real IP destination AH v v ESP applies only to the tunneled packet AH can be applied to portions of the outer header 8 -13
Tunnel Mode Outer IP IPSec Inner IP Higher header layer protocol Destination IPSec entity ESP Real IP destination AH v v ESP applies only to the tunneled packet AH can be applied to portions of the outer header 8 -13
 Security associations (SAs) v before sending data, “security association (SA)” established from sending to receiving entity § SAs are simplex: for only one direction v ending, receiving entitles maintain state information about SA § recall: TCP endpoints also maintain state info § IP is connectionless; IPsec is connection-oriented! v how many SAs in VPN w/ headquarters, branch office, and n traveling salespeople? 8 -14
Security associations (SAs) v before sending data, “security association (SA)” established from sending to receiving entity § SAs are simplex: for only one direction v ending, receiving entitles maintain state information about SA § recall: TCP endpoints also maintain state info § IP is connectionless; IPsec is connection-oriented! v how many SAs in VPN w/ headquarters, branch office, and n traveling salespeople? 8 -14
 Security Association (SA) v Defined by 3 parameters: § Security Parameters Index (SPI) § IP Destination Address § Security Protocol Identifier v v Have a database of Security Associations Determine IPSec processing for senders Determine IPSec decoding for destination SAs are not fixed! Generated and customized per traffic flows 8 -15
Security Association (SA) v Defined by 3 parameters: § Security Parameters Index (SPI) § IP Destination Address § Security Protocol Identifier v v Have a database of Security Associations Determine IPSec processing for senders Determine IPSec decoding for destination SAs are not fixed! Generated and customized per traffic flows 8 -15
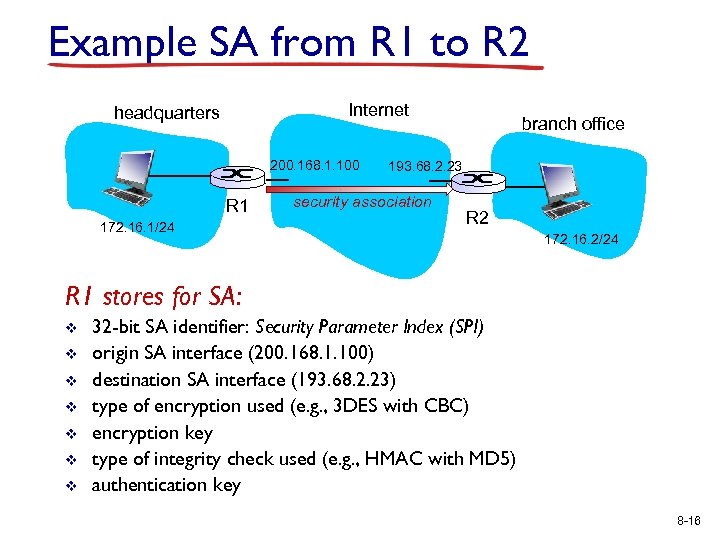 Example SA from R 1 to R 2 Internet headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 branch office 193. 68. 2. 23 security association R 2 172. 16. 2/24 R 1 stores for SA: v v v v 32 -bit SA identifier: Security Parameter Index (SPI) origin SA interface (200. 168. 1. 100) destination SA interface (193. 68. 2. 23) type of encryption used (e. g. , 3 DES with CBC) encryption key type of integrity check used (e. g. , HMAC with MD 5) authentication key 8 -16
Example SA from R 1 to R 2 Internet headquarters 200. 168. 1. 100 R 1 172. 16. 1/24 branch office 193. 68. 2. 23 security association R 2 172. 16. 2/24 R 1 stores for SA: v v v v 32 -bit SA identifier: Security Parameter Index (SPI) origin SA interface (200. 168. 1. 100) destination SA interface (193. 68. 2. 23) type of encryption used (e. g. , 3 DES with CBC) encryption key type of integrity check used (e. g. , HMAC with MD 5) authentication key 8 -16
 Security Association Database (SAD) endpoint holds SA state in security association database (SAD), where it can locate them during processing. v with n salespersons, 2 + 2 n SAs in R 1’s SAD v when sending IPsec datagram, R 1 accesses SAD to determine how to process datagram. v when IPsec datagram arrives to R 2, R 2 examines SPI in IPsec datagram, indexes SAD with SPI, and processes datagram accordingly. v 8 -17
Security Association Database (SAD) endpoint holds SA state in security association database (SAD), where it can locate them during processing. v with n salespersons, 2 + 2 n SAs in R 1’s SAD v when sending IPsec datagram, R 1 accesses SAD to determine how to process datagram. v when IPsec datagram arrives to R 2, R 2 examines SPI in IPsec datagram, indexes SAD with SPI, and processes datagram accordingly. v 8 -17
 Authenticated Header (AH) v Data integrity § Entire packet has not been tampered with v Authentication § Can “trust” IP address source § Use MAC to authenticate • Symmetric encryption, e. g, DES • One-way hash functions, e. g, HMAC-MD 5 -96 or HMAC-SHA-196 v v Anti-replay feature Integrity check value 8 -18
Authenticated Header (AH) v Data integrity § Entire packet has not been tampered with v Authentication § Can “trust” IP address source § Use MAC to authenticate • Symmetric encryption, e. g, DES • One-way hash functions, e. g, HMAC-MD 5 -96 or HMAC-SHA-196 v v Anti-replay feature Integrity check value 8 -18
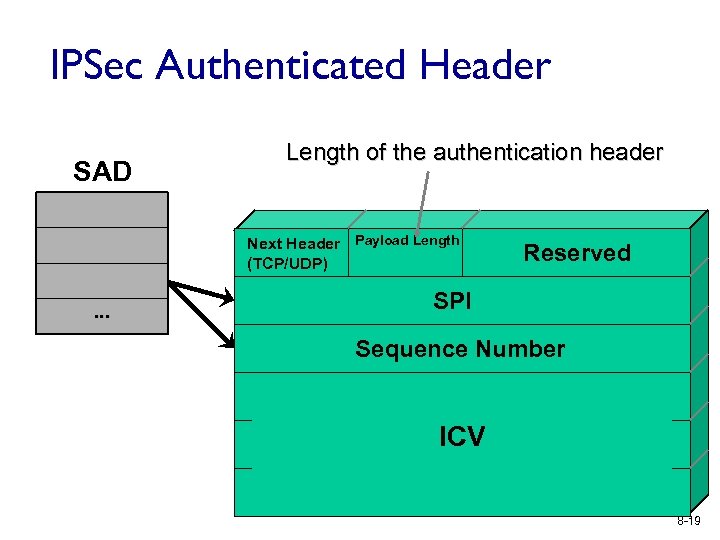 IPSec Authenticated Header SAD Length of the authentication header Next Header Payload Length (TCP/UDP) … Reserved SPI Sequence Number ICV 8 -19
IPSec Authenticated Header SAD Length of the authentication header Next Header Payload Length (TCP/UDP) … Reserved SPI Sequence Number ICV 8 -19
 Integrity Check Value - ICV v Keyed Message authentication code (MAC) calculated over § IP header field that do not change or are predictable • Source IP address, destination IP, header length, etc. • Prevent spoofing • Mutable fields excluded: e. g. , time-to-live (TTL), IP header checksum, etc. § IPSec protocol header except the ICV value field § Upper-level data v Code may be truncated to first 96 bits 8 -20
Integrity Check Value - ICV v Keyed Message authentication code (MAC) calculated over § IP header field that do not change or are predictable • Source IP address, destination IP, header length, etc. • Prevent spoofing • Mutable fields excluded: e. g. , time-to-live (TTL), IP header checksum, etc. § IPSec protocol header except the ICV value field § Upper-level data v Code may be truncated to first 96 bits 8 -20
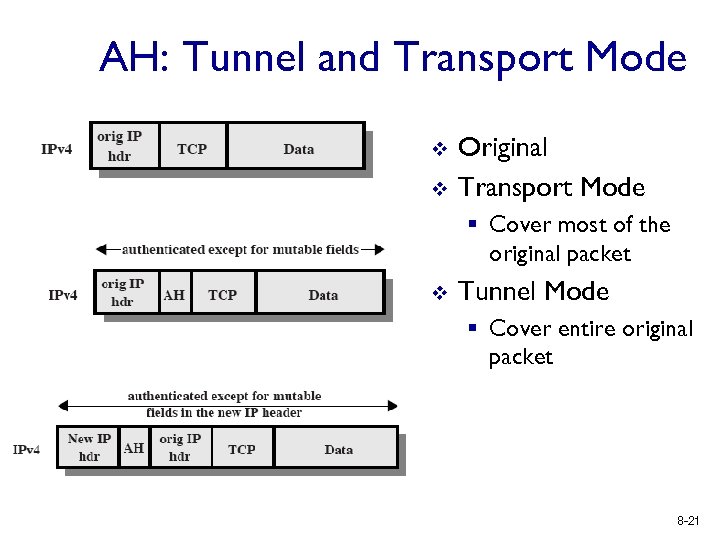 AH: Tunnel and Transport Mode v v Original Transport Mode § Cover most of the original packet v Tunnel Mode § Cover entire original packet 8 -21
AH: Tunnel and Transport Mode v v Original Transport Mode § Cover most of the original packet v Tunnel Mode § Cover entire original packet 8 -21
 Encapsulating Security Payload (ESP) v v Provide message content confidentiality Provide limited traffic flow confidentiality Can optionally provide the same authentication services as AH Supports range of ciphers, modes, padding § Incl. DES, Triple-DES, RC 5, IDEA, CAST etc § A variant of DES most common § Pad to meet blocksize, for traffic flow 8 -22
Encapsulating Security Payload (ESP) v v Provide message content confidentiality Provide limited traffic flow confidentiality Can optionally provide the same authentication services as AH Supports range of ciphers, modes, padding § Incl. DES, Triple-DES, RC 5, IDEA, CAST etc § A variant of DES most common § Pad to meet blocksize, for traffic flow 8 -22
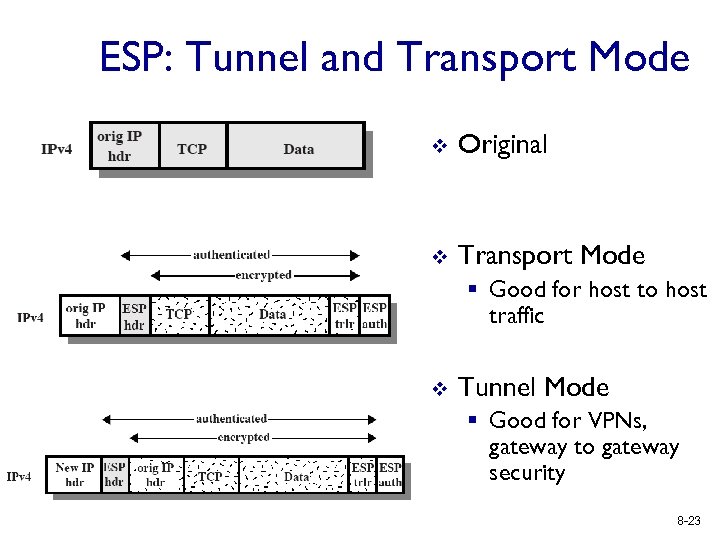 ESP: Tunnel and Transport Mode v Original v Transport Mode § Good for host to host traffic v Tunnel Mode § Good for VPNs, gateway to gateway security 8 -23
ESP: Tunnel and Transport Mode v Original v Transport Mode § Good for host to host traffic v Tunnel Mode § Good for VPNs, gateway to gateway security 8 -23
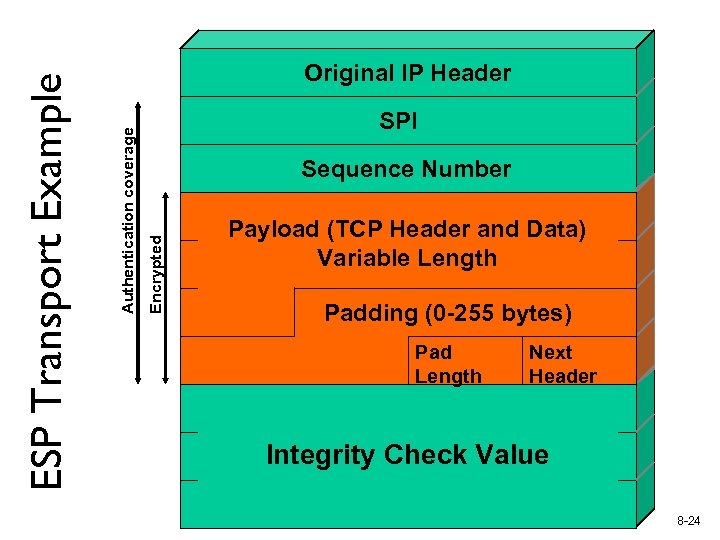 SPI Sequence Number Encrypted Authentication coverage ESP Transport Example Original IP Header Payload (TCP Header and Data) Variable Length Padding (0 -255 bytes) Pad Length Next Header Integrity Check Value 8 -24
SPI Sequence Number Encrypted Authentication coverage ESP Transport Example Original IP Header Payload (TCP Header and Data) Variable Length Padding (0 -255 bytes) Pad Length Next Header Integrity Check Value 8 -24
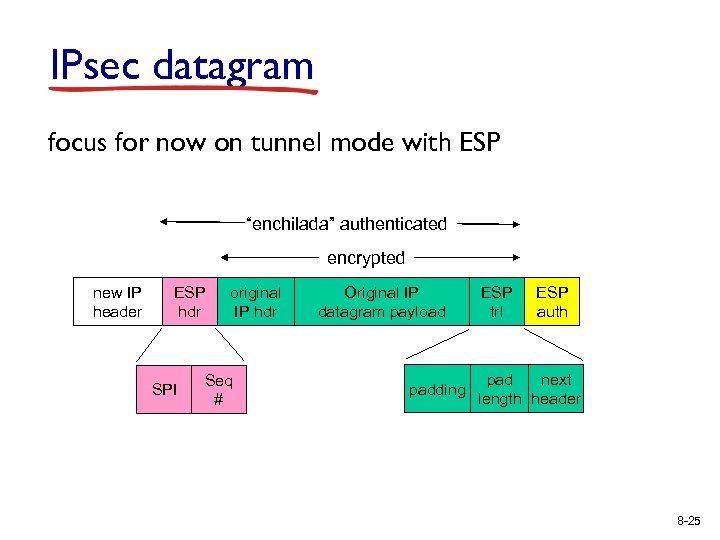 IPsec datagram focus for now on tunnel mode with ESP “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 8 -25
IPsec datagram focus for now on tunnel mode with ESP “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 8 -25
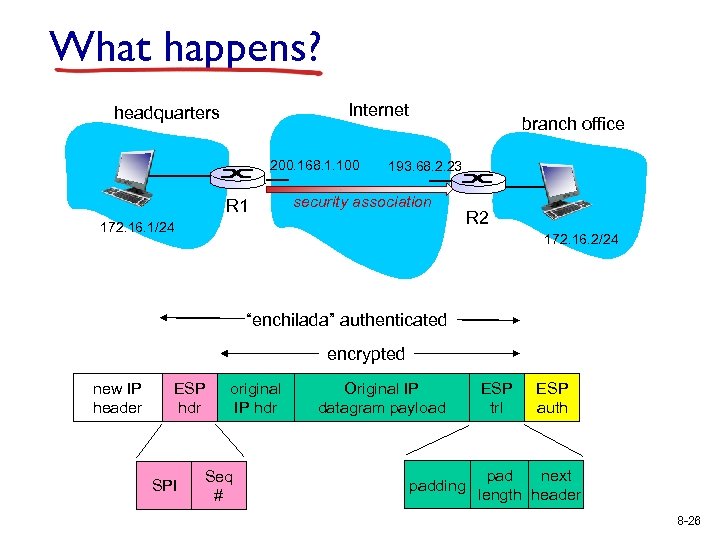 What happens? Internet headquarters 200. 168. 1. 100 R 1 branch office 193. 68. 2. 23 security association 172. 16. 1/24 R 2 172. 16. 2/24 “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 8 -26
What happens? Internet headquarters 200. 168. 1. 100 R 1 branch office 193. 68. 2. 23 security association 172. 16. 1/24 R 2 172. 16. 2/24 “enchilada” authenticated encrypted new IP header ESP hdr SPI original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header 8 -26
 R 1: convert original datagram to IPsec datagram v v v appends to back of original datagram (which includes original header fields!) an “ESP trailer” field. encrypts result using algorithm & key specified by SA. appends to front of this encrypted quantity the “ESP header, creating “enchilada”. creates authentication MAC over the whole enchilada, using algorithm and key specified in SA; appends MAC to back of enchilada, forming payload; creates brand new IP header, with all the classic IPv 4 header fields, which it appends before payload. 8 -27
R 1: convert original datagram to IPsec datagram v v v appends to back of original datagram (which includes original header fields!) an “ESP trailer” field. encrypts result using algorithm & key specified by SA. appends to front of this encrypted quantity the “ESP header, creating “enchilada”. creates authentication MAC over the whole enchilada, using algorithm and key specified in SA; appends MAC to back of enchilada, forming payload; creates brand new IP header, with all the classic IPv 4 header fields, which it appends before payload. 8 -27
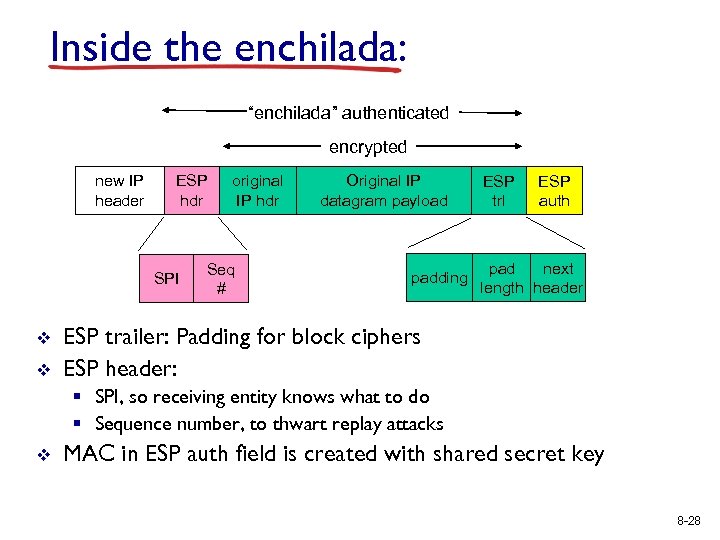 Inside the enchilada: “enchilada” authenticated encrypted new IP header ESP hdr SPI v v original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header ESP trailer: Padding for block ciphers ESP header: § SPI, so receiving entity knows what to do § Sequence number, to thwart replay attacks v MAC in ESP auth field is created with shared secret key 8 -28
Inside the enchilada: “enchilada” authenticated encrypted new IP header ESP hdr SPI v v original IP hdr Seq # Original IP datagram payload padding ESP trl ESP auth pad next length header ESP trailer: Padding for block ciphers ESP header: § SPI, so receiving entity knows what to do § Sequence number, to thwart replay attacks v MAC in ESP auth field is created with shared secret key 8 -28
 IPsec sequence numbers v v for new SA, sender initializes seq. # to 0 each time datagram is sent on SA: § sender increments seq # counter § places value in seq # field v goal: § prevent attacker from sniffing and replaying a packet § receipt of duplicate, authenticated IP packets may disrupt service v method: § destination checks for duplicates § doesn’t keep track of all received packets; instead uses a window 8 -29
IPsec sequence numbers v v for new SA, sender initializes seq. # to 0 each time datagram is sent on SA: § sender increments seq # counter § places value in seq # field v goal: § prevent attacker from sniffing and replaying a packet § receipt of duplicate, authenticated IP packets may disrupt service v method: § destination checks for duplicates § doesn’t keep track of all received packets; instead uses a window 8 -29
 Security Policy Database (SPD) v v policy: For a given datagram, sending entity needs to know if it should use IPsec needs also to know which SA to use § may use: source and destination IP address; protocol number v v info in SPD indicates “what” to do with arriving datagram info in SAD indicates “how” to do it 8 -30
Security Policy Database (SPD) v v policy: For a given datagram, sending entity needs to know if it should use IPsec needs also to know which SA to use § may use: source and destination IP address; protocol number v v info in SPD indicates “what” to do with arriving datagram info in SAD indicates “how” to do it 8 -30
 SPD Entry Actions v Discard § Do not let in or out v Bypass § Outbound: do not apply IPSec § Inbound: do not expect IPSec v Protect – will point to an SA or SA bundle § Outbound: apply security § Inbound: check that security must have been applied 8 -31
SPD Entry Actions v Discard § Do not let in or out v Bypass § Outbound: do not apply IPSec § Inbound: do not expect IPSec v Protect – will point to an SA or SA bundle § Outbound: apply security § Inbound: check that security must have been applied 8 -31
 SPD Protect Action v If the SA does not exist… § Outbound processing: use IKE to generate SA dynamically § Inbound processing: drop packet 8 -32
SPD Protect Action v If the SA does not exist… § Outbound processing: use IKE to generate SA dynamically § Inbound processing: drop packet 8 -32
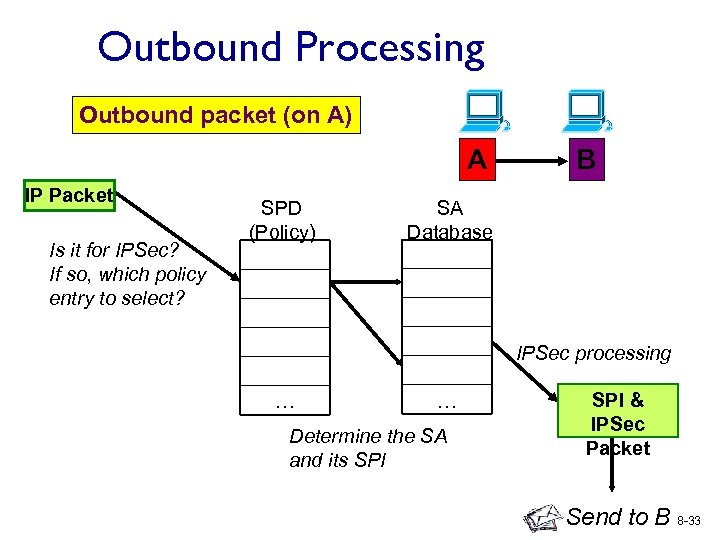 Outbound Processing Outbound packet (on A) A IP Packet Is it for IPSec? If so, which policy entry to select? SPD (Policy) B SA Database IPSec processing … … Determine the SA and its SPI & IPSec Packet Send to B 8 -33
Outbound Processing Outbound packet (on A) A IP Packet Is it for IPSec? If so, which policy entry to select? SPD (Policy) B SA Database IPSec processing … … Determine the SA and its SPI & IPSec Packet Send to B 8 -33
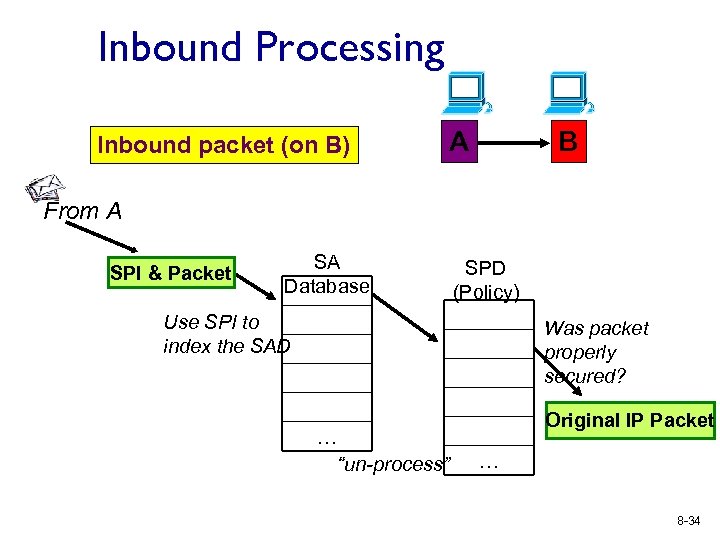 Inbound Processing Inbound packet (on B) A B From A SPI & Packet SA Database SPD (Policy) Use SPI to index the SAD Was packet properly secured? Original IP Packet … “un-process” … 8 -34
Inbound Processing Inbound packet (on B) A B From A SPI & Packet SA Database SPD (Policy) Use SPI to index the SAD Was packet properly secured? Original IP Packet … “un-process” … 8 -34
 Key Management v v Handles key generation & distribution Typically need 2 pairs of keys § 2 per direction for AH & ESP v Manual key management § Sysadmin manually configures every system (IPSec SAs are manually established. ) v Automated key management § manual keying is impractical for VPN with 100 s of endpoints § instead use IPsec IKE (Internet Key Exchange) § IKE PKI: both sides start with public/private key pair, certificate • Similar to SSL handshake 8 -35
Key Management v v Handles key generation & distribution Typically need 2 pairs of keys § 2 per direction for AH & ESP v Manual key management § Sysadmin manually configures every system (IPSec SAs are manually established. ) v Automated key management § manual keying is impractical for VPN with 100 s of endpoints § instead use IPsec IKE (Internet Key Exchange) § IKE PKI: both sides start with public/private key pair, certificate • Similar to SSL handshake 8 -35
 Summary: IPsec services v suppose Trudy sits somewhere between R 1 and R 2. she doesn’t know the keys. § will Trudy be able to see original contents of datagram? How about source, dest IP address, transport protocol, application port? § flip bits without detection? § masquerade as R 1 using R 1’s IP address? § replay a datagram? 8 -36
Summary: IPsec services v suppose Trudy sits somewhere between R 1 and R 2. she doesn’t know the keys. § will Trudy be able to see original contents of datagram? How about source, dest IP address, transport protocol, application port? § flip bits without detection? § masquerade as R 1 using R 1’s IP address? § replay a datagram? 8 -36
 IPsec summary v v v Either AH or ESP protocol (or both) § AH provides integrity, source authentication § ESP protocol (with AH) additionally provides encryption IPsec peers can be two end systems, two routers/firewalls, or a router/firewall and an end system IKE message exchange for algorithms, secret keys, SPI numbers 8 -37
IPsec summary v v v Either AH or ESP protocol (or both) § AH provides integrity, source authentication § ESP protocol (with AH) additionally provides encryption IPsec peers can be two end systems, two routers/firewalls, or a router/firewall and an end system IKE message exchange for algorithms, secret keys, SPI numbers 8 -37


