a68cc9b2075291cf858660ef7ce7fa05.ppt
- Количество слайдов: 44
 IP-guard www. ip-guard. com
IP-guard www. ip-guard. com
 IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
 IP-guard Security Challenges form Computerized Corporation Data-Stealing Data Disclosure Removable storage device, email, P 2 P Application, spyware, illegal intrusion, hacker… Security Risks system vulnerability, virus attack, malicious deletion or modification printing… Creative design, VIP customer information, sensitive financial data …
IP-guard Security Challenges form Computerized Corporation Data-Stealing Data Disclosure Removable storage device, email, P 2 P Application, spyware, illegal intrusion, hacker… Security Risks system vulnerability, virus attack, malicious deletion or modification printing… Creative design, VIP customer information, sensitive financial data …
 IP-guard Drawbacks of Information Technology Play games · Trade Stocks · Chat Online Browse Web Pages · Print Personal Stuffs Online Movies · Radio · Download Music Cannot Troubleshoot Remote Computer Cannot Track Computer Assets Changes Administrator Faces Heavy Workload
IP-guard Drawbacks of Information Technology Play games · Trade Stocks · Chat Online Browse Web Pages · Print Personal Stuffs Online Movies · Radio · Download Music Cannot Troubleshoot Remote Computer Cannot Track Computer Assets Changes Administrator Faces Heavy Workload
 IP-guard The significance of Protecting Intranet Security ll wall Corporation e Anti-virus Software M alw ar s Intranet Security Management Fire V i ru Fir ew a l To resist external risks To prevent internal breaches Intranet Security Management l Hacker
IP-guard The significance of Protecting Intranet Security ll wall Corporation e Anti-virus Software M alw ar s Intranet Security Management Fire V i ru Fir ew a l To resist external risks To prevent internal breaches Intranet Security Management l Hacker
 IP-guard The Core Values of IP-guard Protect data security; Safeguard intellectual property. Adjust employee behavior; Improve work efficiency. Centrally manage system; Keep system stable. Effective and Comprehensive Management
IP-guard The Core Values of IP-guard Protect data security; Safeguard intellectual property. Adjust employee behavior; Improve work efficiency. Centrally manage system; Keep system stable. Effective and Comprehensive Management
 IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
 IP-guard 14 Modules of IP-guard Basic Management Application Management Document Management Website Management Print Management Bandwidth Management Device Management IP-guard Network Management Removable Storage Management Screen Monitoring Email Management Remote Maintenance Instant Messaging Management IT Asset Management Be composed freely; Be selected optionally.
IP-guard 14 Modules of IP-guard Basic Management Application Management Document Management Website Management Print Management Bandwidth Management Device Management IP-guard Network Management Removable Storage Management Screen Monitoring Email Management Remote Maintenance Instant Messaging Management IT Asset Management Be composed freely; Be selected optionally.
 IP-guard Basic Management Module Basic and essential module of IP-guard. It’s a mandatory module. l Basic Events Log Ø l Basic Control Ø l Record computer startup, logon, logoff, shutdown to check when do your employee start working and what time do they leave their workstations Remotely lock, log off, restart and turn off agent computers to manage computers or stop illegal operations Basic Policy Ø Block users from randomly modify system setting in order to prevent accidental and intentional destruction and improve system security.
IP-guard Basic Management Module Basic and essential module of IP-guard. It’s a mandatory module. l Basic Events Log Ø l Basic Control Ø l Record computer startup, logon, logoff, shutdown to check when do your employee start working and what time do they leave their workstations Remotely lock, log off, restart and turn off agent computers to manage computers or stop illegal operations Basic Policy Ø Block users from randomly modify system setting in order to prevent accidental and intentional destruction and improve system security.
 IP-guard Document Management Module Control and monitor document actions to safeguard intellectual property l Document Control Ø l Document Backup Ø l Effectively control document actions to prevent unauthorized actions, malicious modification and deletion. Back up documents before they are modified or deleted to make sure the security of important documents Document Logging Ø Ø Record document actions in detail Record document actions of any computer on shared documents
IP-guard Document Management Module Control and monitor document actions to safeguard intellectual property l Document Control Ø l Document Backup Ø l Effectively control document actions to prevent unauthorized actions, malicious modification and deletion. Back up documents before they are modified or deleted to make sure the security of important documents Document Logging Ø Ø Record document actions in detail Record document actions of any computer on shared documents
 IP-guard Print Management Monitor file printing to prevent data leakage l Print Control Ø Ø l Print Logging Ø l Control printing permission to prevent data leakage Reasonably assign print resource to stop wasting print resource Record print actions in detail for administrator to evaluate the effective usage of print resource Print Backup Ø Back up the image of printed file
IP-guard Print Management Monitor file printing to prevent data leakage l Print Control Ø Ø l Print Logging Ø l Control printing permission to prevent data leakage Reasonably assign print resource to stop wasting print resource Record print actions in detail for administrator to evaluate the effective usage of print resource Print Backup Ø Back up the image of printed file
 IP-guard Device Management Control and monitor the usage of various devices to prevent data leakage l Device Control Ø Block external devices from connecting to the intranet to Ø Detailed and specific control protect data security and stop data breaches
IP-guard Device Management Control and monitor the usage of various devices to prevent data leakage l Device Control Ø Block external devices from connecting to the intranet to Ø Detailed and specific control protect data security and stop data breaches
 Device Management IP-guard - List of Controlled Device Ø Storage Devices ü Ø Communications Devices ü Ø Wireless LAN Adapter, Virtual LAN Adapter, Pn. P Adapter (USB, PCAMCIA) Others ü Ø USB hard disk, USB CDROME、USB LAN Adapter, USB Image Device, etc. Network Devices ü Ø Dial-up Connection USB Devices ü Ø COM, LTP, Bluetooth, Infrared, SCSI Controller, etc. Dialup ü Ø Floppy, CDROM, Burning Device, Tape, Removable Storage Device Audio device, Virtual LAN Adapter Any added new devices
Device Management IP-guard - List of Controlled Device Ø Storage Devices ü Ø Communications Devices ü Ø Wireless LAN Adapter, Virtual LAN Adapter, Pn. P Adapter (USB, PCAMCIA) Others ü Ø USB hard disk, USB CDROME、USB LAN Adapter, USB Image Device, etc. Network Devices ü Ø Dial-up Connection USB Devices ü Ø COM, LTP, Bluetooth, Infrared, SCSI Controller, etc. Dialup ü Ø Floppy, CDROM, Burning Device, Tape, Removable Storage Device Audio device, Virtual LAN Adapter Any added new devices
 IP-guard Removable Storage Management Authorize and encrypt removable storage device to protect your valuable data anywhere at anytime. l Permission Control Ø l Automatic Encryption & Decryption Ø l Strictly control file in motion to protect data Automatically encrypt data when files are written to any removable storage device to enhance the security level of data in motion Whole Disk Encryption Ø Ø Format corporate removable storage device as encrypted removable storage device. Automatically encrypt and decrypt data stored on the encrypted removable storage device within the corporate environment. * NOTE: Encrypted removable storage device only can be used within the corporate environment
IP-guard Removable Storage Management Authorize and encrypt removable storage device to protect your valuable data anywhere at anytime. l Permission Control Ø l Automatic Encryption & Decryption Ø l Strictly control file in motion to protect data Automatically encrypt data when files are written to any removable storage device to enhance the security level of data in motion Whole Disk Encryption Ø Ø Format corporate removable storage device as encrypted removable storage device. Automatically encrypt and decrypt data stored on the encrypted removable storage device within the corporate environment. * NOTE: Encrypted removable storage device only can be used within the corporate environment
 IP-guard Email Management Control and monitor incoming and outgoing emails to prevent data leakage l Email Control Ø l Block sending specified POP 3/SMTP emails or Exchanges emails out of the organization via email to prevent data leakage Email Logging Ø Ø Fully record sender, recipient, subject, text and attachment Support POP 3/SMTP email, Exchange email, webmail, and Lotus email
IP-guard Email Management Control and monitor incoming and outgoing emails to prevent data leakage l Email Control Ø l Block sending specified POP 3/SMTP emails or Exchanges emails out of the organization via email to prevent data leakage Email Logging Ø Ø Fully record sender, recipient, subject, text and attachment Support POP 3/SMTP email, Exchange email, webmail, and Lotus email
 IP-guard Instant Messaging Management Control and monitor instant messaging to safeguard data security and improve work efficiency l IM Logging Ø l File Transfer Control Ø l Completely record instant messages, participants, time to prevent data leaking out via IM applications Block sending files out of the corporation over limited size or with limited file names File Backup Ø Back up transferred file
IP-guard Instant Messaging Management Control and monitor instant messaging to safeguard data security and improve work efficiency l IM Logging Ø l File Transfer Control Ø l Completely record instant messages, participants, time to prevent data leaking out via IM applications Block sending files out of the corporation over limited size or with limited file names File Backup Ø Back up transferred file
 IP-guard Application Management Control and monitor application usage to improve work efficiency l Application Statistics Ø l Application Control Ø Ø l Gather statistics by category, name, detail and group to let you know your employee’s work performance Filter non-work related applications to make your employees concentrate on work business Block malicious application to protect computer security Application Log Ø Record application start, stop, window switch to track the application activity of staff
IP-guard Application Management Control and monitor application usage to improve work efficiency l Application Statistics Ø l Application Control Ø Ø l Gather statistics by category, name, detail and group to let you know your employee’s work performance Filter non-work related applications to make your employees concentrate on work business Block malicious application to protect computer security Application Log Ø Record application start, stop, window switch to track the application activity of staff
 IP-guard Website Management Record staff’s web browsing activities; limit web site access right to regulate staff’s online activity l Website Statistics Ø l Website Management Ø Ø l Gather statistics by different ways to let you know your staff’s web browsing activity Filter non-work related websites during a specified time period Block malicious and inappropriate websites Website Log Ø Record the URL, caption, and time of the visited websites to track what your staff were browsing during office hours
IP-guard Website Management Record staff’s web browsing activities; limit web site access right to regulate staff’s online activity l Website Statistics Ø l Website Management Ø Ø l Gather statistics by different ways to let you know your staff’s web browsing activity Filter non-work related websites during a specified time period Block malicious and inappropriate websites Website Log Ø Record the URL, caption, and time of the visited websites to track what your staff were browsing during office hours
 IP-guard Bandwidth Management Limit and control bandwidth to avoid any bandwidth abuse l Traffic Statistics Ø l Gather statistics by different ways to assist administrator to analyze traffic consumption Bandwidth Control Ø Ø Limit bandwidth by IP address or port to help administrator reasonably assign various bandwidth to different users Limit BT download, online video watching to make sure that you have sufficient bandwidth for business use
IP-guard Bandwidth Management Limit and control bandwidth to avoid any bandwidth abuse l Traffic Statistics Ø l Gather statistics by different ways to assist administrator to analyze traffic consumption Bandwidth Control Ø Ø Limit bandwidth by IP address or port to help administrator reasonably assign various bandwidth to different users Limit BT download, online video watching to make sure that you have sufficient bandwidth for business use
 IP-guard Network Management Prevent unauthorized external computers from accessing internal network l Network Control Ø l Offer firewall function and block unauthorized computer from communication with internal computers in order to protect intranet security Network Intrusion Detection Ø Scan the whole network to immediately stop unauthorized computers from connecting to the internal network so as to safeguard information security
IP-guard Network Management Prevent unauthorized external computers from accessing internal network l Network Control Ø l Offer firewall function and block unauthorized computer from communication with internal computers in order to protect intranet security Network Intrusion Detection Ø Scan the whole network to immediately stop unauthorized computers from connecting to the internal network so as to safeguard information security
 IP-guard Screen Monitoring Record and replay screen snapshot to let you know what your employees do step by step l Screen Monitoring Ø Ø Ø l View the real-time desktop screen of any computer Monitor computers with multi displays Centrally monitor multi computers at one time Screen Record Ø Ø Completely record screen history for your latter review Set different intervals to capture screen snapshot when different application are being used so as to pay attention to risky applications Can save a lot of screen snapshots due to effective compression Screen history can be exported to wmv format.
IP-guard Screen Monitoring Record and replay screen snapshot to let you know what your employees do step by step l Screen Monitoring Ø Ø Ø l View the real-time desktop screen of any computer Monitor computers with multi displays Centrally monitor multi computers at one time Screen Record Ø Ø Completely record screen history for your latter review Set different intervals to capture screen snapshot when different application are being used so as to pay attention to risky applications Can save a lot of screen snapshots due to effective compression Screen history can be exported to wmv format.
 IP-guard Remote Maintenance Support remote maintenance so as to let you shorten the downtime and quickly solve the system problem l Remote Troubleshooting Ø Ø l Remote Control Ø l Check the real-time running processes of client computers Remotely analyze the running status, system fault and device status of client computers Perform remote assistance or demonstrate operational instruction Remote File Transfer Ø Remotely transfer files from remote computers to local computer, and from local computer to remote computers in order to quickly gather fault samples to diagnose the problem and update files
IP-guard Remote Maintenance Support remote maintenance so as to let you shorten the downtime and quickly solve the system problem l Remote Troubleshooting Ø Ø l Remote Control Ø l Check the real-time running processes of client computers Remotely analyze the running status, system fault and device status of client computers Perform remote assistance or demonstrate operational instruction Remote File Transfer Ø Remotely transfer files from remote computers to local computer, and from local computer to remote computers in order to quickly gather fault samples to diagnose the problem and update files
 IP-guard IT Asset Management Easily manage IT asset to reduce management cost l Asset Information Ø Ø l Automatically collect software and hardware information and provide asset inventory to facilitate administrator’s management Offer non-IT asset management function Asset Change Ø Ø Record software and hardware changes in detail Instant alert on asset changes
IP-guard IT Asset Management Easily manage IT asset to reduce management cost l Asset Information Ø Ø l Automatically collect software and hardware information and provide asset inventory to facilitate administrator’s management Offer non-IT asset management function Asset Change Ø Ø Record software and hardware changes in detail Instant alert on asset changes
 IP-guard IT Asset Management l Vulnerability Management Ø l Patch Management Ø Ø l Automatically scan system vulnerability of agent computer and provide easy-to-read report and solutions Check Microsoft for new patches at regular intervals Automatically download and deploy new patches to agent computers Software Deployment Ø Ø Deploy files and programs with ease Support breakpoint transmission to facilitate background installation and interactive installation
IP-guard IT Asset Management l Vulnerability Management Ø l Patch Management Ø Ø l Automatically scan system vulnerability of agent computer and provide easy-to-read report and solutions Check Microsoft for new patches at regular intervals Automatically download and deploy new patches to agent computers Software Deployment Ø Ø Deploy files and programs with ease Support breakpoint transmission to facilitate background installation and interactive installation
 IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
 IP-guard Data Loss Prevention Solution Data Security Management Email Management Print Management Removable Storage Management Document Management Device Management Instant Messaging Management Screen Monitoring Network Management
IP-guard Data Loss Prevention Solution Data Security Management Email Management Print Management Removable Storage Management Document Management Device Management Instant Messaging Management Screen Monitoring Network Management
 IP-guard Data Loss Prevention Solution Pre-Control In-Control Post-Control Based on business and management needs to set specific policies When unpermitted actions trigger the policies, actions will be immediately blocked so as to protect data security. All activities on computer are recorded in logs and in other formats.
IP-guard Data Loss Prevention Solution Pre-Control In-Control Post-Control Based on business and management needs to set specific policies When unpermitted actions trigger the policies, actions will be immediately blocked so as to protect data security. All activities on computer are recorded in logs and in other formats.
 IP-guard Data Loss Prevention Solution Pre-Control Based on business and management needs to set specific policies
IP-guard Data Loss Prevention Solution Pre-Control Based on business and management needs to set specific policies
 IP-guard Data Loss Prevention Solution General Control Document Management Email Management In-Control Print Management Instant Messaging Management Device Management Offline Control Policies are still effective when computers are offline in order to always protect data security. When unpermitted actions trigger the policies, actions will be immediately blocked so as to protect data security. Document Backup * Back up original files before they are modified or deleted * Back up files before they are sent out of the company Transparent Removable Storage Encryption and Document Encryption Active defense. Maximumly safeguard data security.
IP-guard Data Loss Prevention Solution General Control Document Management Email Management In-Control Print Management Instant Messaging Management Device Management Offline Control Policies are still effective when computers are offline in order to always protect data security. When unpermitted actions trigger the policies, actions will be immediately blocked so as to protect data security. Document Backup * Back up original files before they are modified or deleted * Back up files before they are sent out of the company Transparent Removable Storage Encryption and Document Encryption Active defense. Maximumly safeguard data security.
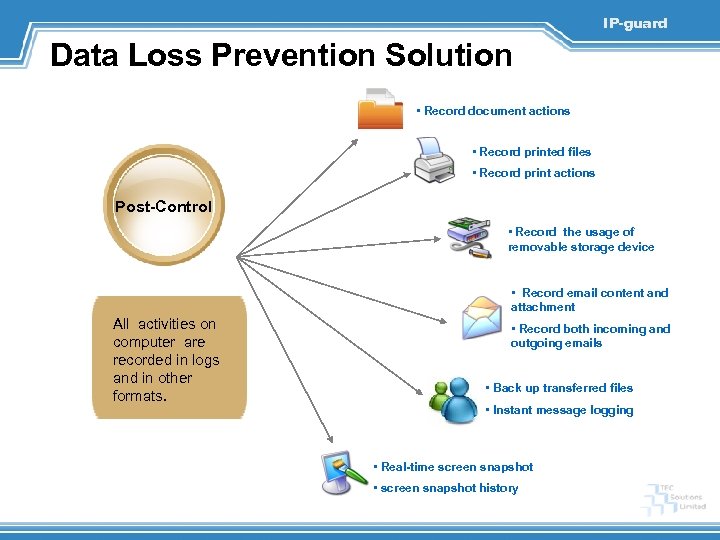 IP-guard Data Loss Prevention Solution • Record document actions • Record printed files • Record print actions Post-Control • Record the usage of removable storage device • Record email content and attachment All activities on computer are recorded in logs and in other formats. • Record both incoming and outgoing emails • Back up transferred files • Instant message logging • Real-time screen snapshot • screen snapshot history
IP-guard Data Loss Prevention Solution • Record document actions • Record printed files • Record print actions Post-Control • Record the usage of removable storage device • Record email content and attachment All activities on computer are recorded in logs and in other formats. • Record both incoming and outgoing emails • Back up transferred files • Instant message logging • Real-time screen snapshot • screen snapshot history
 IP-guard Customer Benefits l l l Avoid lawsuit and data leakage risks Raise the core competitive power of enterprise Improve the reputation of enterprise
IP-guard Customer Benefits l l l Avoid lawsuit and data leakage risks Raise the core competitive power of enterprise Improve the reputation of enterprise
 Employee Activity Management Solution IP-guard Device Management Application Management • Control device usage • Control application usage • Gather statistics on application usage • Record application activity Bandwidth Management Activity Management Screen Monitoring • Control bandwidth usage • Real-time screen snapshot • Gather statistics on traffic consumption • Screen snapshot history Website Management • Filter unwanted websites • Gather statistics on websites visited • Record websites visited Network Management • Control network communications • Detect intrusion
Employee Activity Management Solution IP-guard Device Management Application Management • Control device usage • Control application usage • Gather statistics on application usage • Record application activity Bandwidth Management Activity Management Screen Monitoring • Control bandwidth usage • Real-time screen snapshot • Gather statistics on traffic consumption • Screen snapshot history Website Management • Filter unwanted websites • Gather statistics on websites visited • Record websites visited Network Management • Control network communications • Detect intrusion
 IP-guard Employee Activity Management Manage employee’s online and computer activity
IP-guard Employee Activity Management Manage employee’s online and computer activity
 IP-guard Employee Activity Management Instant Warning Message Optionally do NOT compulsively block users using gaming applications, browsing shopping websites, sending private emails, and much more. But when they are doing non-work related things, warning messages can be automatically sent to users. Warning messages help them comply with the company policy. Powerful Control Function This solution not only can allow or block specified employees from using specified application, email, removable media and other things, but also can control employees’ activity by customized group during different time periods.
IP-guard Employee Activity Management Instant Warning Message Optionally do NOT compulsively block users using gaming applications, browsing shopping websites, sending private emails, and much more. But when they are doing non-work related things, warning messages can be automatically sent to users. Warning messages help them comply with the company policy. Powerful Control Function This solution not only can allow or block specified employees from using specified application, email, removable media and other things, but also can control employees’ activity by customized group during different time periods.
 IP-guard Customer Benefits • Adjust employees’ work behavior to improve work efficiency • Avoid network abuse and network choking to make sure that there is enough bandwidth to support the smooth development of key business
IP-guard Customer Benefits • Adjust employees’ work behavior to improve work efficiency • Avoid network abuse and network choking to make sure that there is enough bandwidth to support the smooth development of key business
 IP-guard Systems Management Solution System Management IT Asset Management • Software & hardware Management • Patch Management • Vulnerability Management • Software Deployment Remote Control • Remote Troubleshooting • Remote Control • Remote File Transfer
IP-guard Systems Management Solution System Management IT Asset Management • Software & hardware Management • Patch Management • Vulnerability Management • Software Deployment Remote Control • Remote Troubleshooting • Remote Control • Remote File Transfer
 IP-guard Customer Benefits • Get a grip on your IT inventory • Make quick response to system faults • Greatly improve system administrators’ work efficiency • Maintain system stability and enforce system security
IP-guard Customer Benefits • Get a grip on your IT inventory • Make quick response to system faults • Greatly improve system administrators’ work efficiency • Maintain system stability and enforce system security
 IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
IP-guard Contents 1 Brief Introduction 2 14 Modules of IP-guard 3 Solutions 4 Components and Basic System Architecture
 IP-guard Components of IP-guard Console Server Store data n Manage policy n Agent Collect data n Execute policy n View data n Set policy n Perform real-time maintenance n
IP-guard Components of IP-guard Console Server Store data n Manage policy n Agent Collect data n Execute policy n View data n Set policy n Perform real-time maintenance n
 IP-guard System Architecture
IP-guard System Architecture
 IP-guard System Requirements Components Requirements Database SQL Server 2000 SP 4, MSDE SP 4, SQL Server 2005 SP 1, SQL Server 2005 Express SP 1 OS Supported Microsoft Vista, 2003, XP, 2000, Me, and 98 Recommended CPU: Pentium® 4 RAM: 512 MB Free disk space: 1 GB OS Supported Microsoft Windows Vista, 2003 SP 1, XP SP 2, and 2000 SP 4 Recommended CPU: Dual Core or Quad Core RAM: 2 GB Free space: 60 GB OS Supported Microsoft Windows Vista, 2003, XP, and 2000 Recommended CPU: Pentium 4 RAM: 512 MB Free space: 1 GB Agent Server Console
IP-guard System Requirements Components Requirements Database SQL Server 2000 SP 4, MSDE SP 4, SQL Server 2005 SP 1, SQL Server 2005 Express SP 1 OS Supported Microsoft Vista, 2003, XP, 2000, Me, and 98 Recommended CPU: Pentium® 4 RAM: 512 MB Free disk space: 1 GB OS Supported Microsoft Windows Vista, 2003 SP 1, XP SP 2, and 2000 SP 4 Recommended CPU: Dual Core or Quad Core RAM: 2 GB Free space: 60 GB OS Supported Microsoft Windows Vista, 2003, XP, and 2000 Recommended CPU: Pentium 4 RAM: 512 MB Free space: 1 GB Agent Server Console
 IP-guard Installation l Server Installation Ø l Generally, sever is installed on a server-class computer with high performance and a lot of free disk space. The server computer should use the Operating System which IP-guard server is supported. Agent Installation Ø Agents are installed on the computers you want to monitor or manage. * Manually direct installation * Remote Installation * Logon Script Installation l Console Installation Ø Consoles are installed on manager and supervisor’s computers.
IP-guard Installation l Server Installation Ø l Generally, sever is installed on a server-class computer with high performance and a lot of free disk space. The server computer should use the Operating System which IP-guard server is supported. Agent Installation Ø Agents are installed on the computers you want to monitor or manage. * Manually direct installation * Remote Installation * Logon Script Installation l Console Installation Ø Consoles are installed on manager and supervisor’s computers.
 IP-guard Conclusion 1 2 3 What is IP-guard ? How IP-guard can help corporations ? Why choose IP-guard?
IP-guard Conclusion 1 2 3 What is IP-guard ? How IP-guard can help corporations ? Why choose IP-guard?



