 IP addressing Lecture 6
IP addressing Lecture 6
 Outlook n Classful IP addressing structure n IP addressing: problems and reasons n Ways to prevent IP addresses exhaustion n Classless IP addressing n Variable Length Subnet Mask (VLSM) n Network address translation (NAT) n IPv 6 protocol 2
Outlook n Classful IP addressing structure n IP addressing: problems and reasons n Ways to prevent IP addresses exhaustion n Classless IP addressing n Variable Length Subnet Mask (VLSM) n Network address translation (NAT) n IPv 6 protocol 2
 ARPANET 3
ARPANET 3
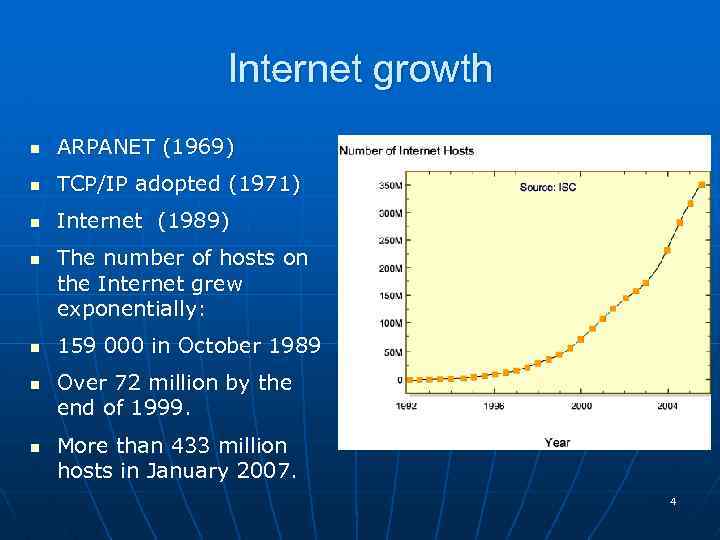 Internet growth n ARPANET (1969) n TCP/IP adopted (1971) n Internet (1989) n n The number of hosts on the Internet grew exponentially: 159 000 in October 1989 Over 72 million by the end of 1999. More than 433 million hosts in January 2007. 4
Internet growth n ARPANET (1969) n TCP/IP adopted (1971) n Internet (1989) n n The number of hosts on the Internet grew exponentially: 159 000 in October 1989 Over 72 million by the end of 1999. More than 433 million hosts in January 2007. 4
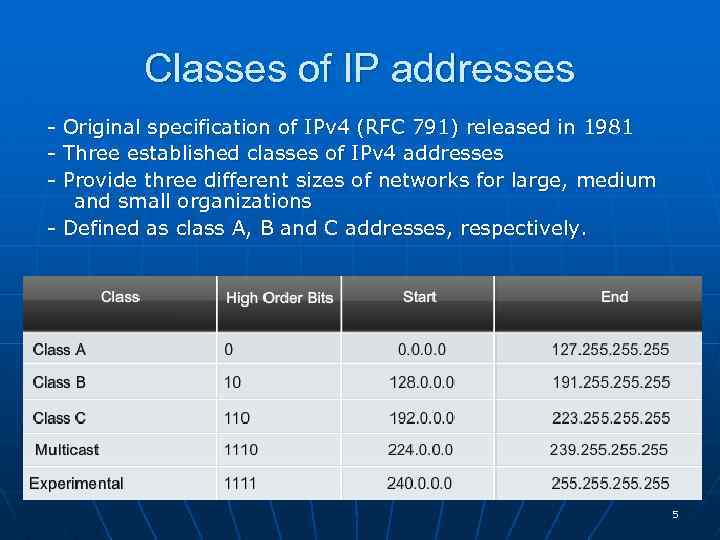 Classes of IP addresses - Original specification of IPv 4 (RFC 791) released in 1981 - Three established classes of IPv 4 addresses - Provide three different sizes of networks for large, medium and small organizations - Defined as class A, B and C addresses, respectively. 5
Classes of IP addresses - Original specification of IPv 4 (RFC 791) released in 1981 - Three established classes of IPv 4 addresses - Provide three different sizes of networks for large, medium and small organizations - Defined as class A, B and C addresses, respectively. 5
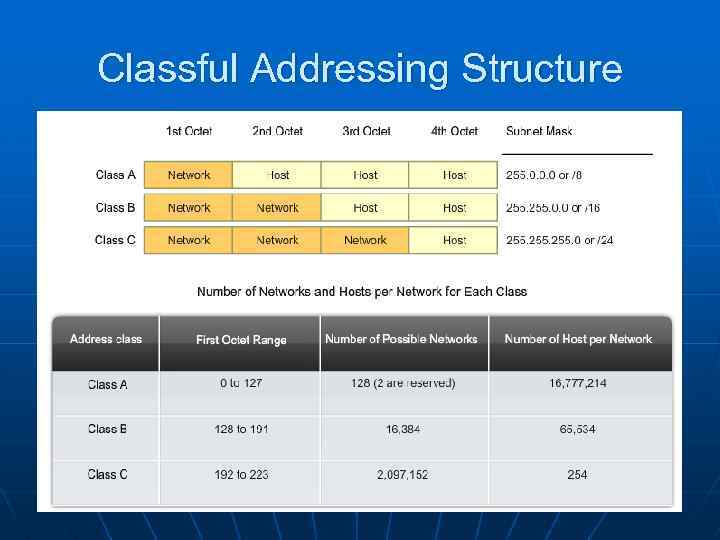 Classful Addressing Structure 6
Classful Addressing Structure 6
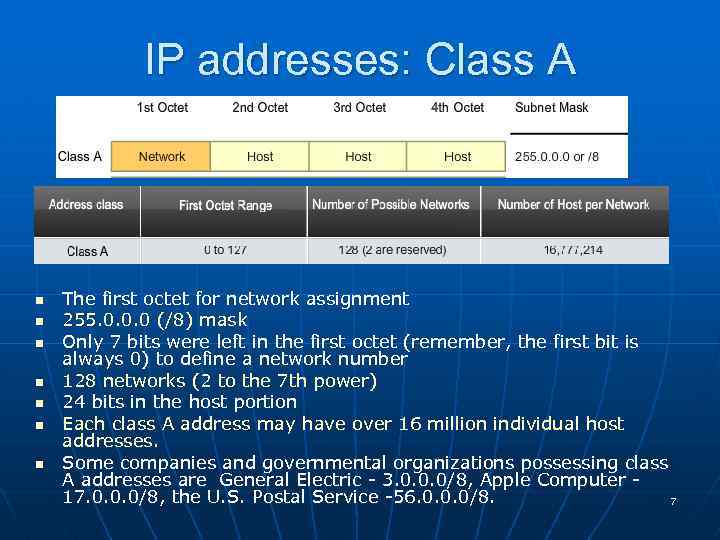 IP addresses: Class A n n n n The first octet for network assignment 255. 0. 0. 0 (/8) mask Only 7 bits were left in the first octet (remember, the first bit is always 0) to define a network number 128 networks (2 to the 7 th power) 24 bits in the host portion Each class A address may have over 16 million individual host addresses. Some companies and governmental organizations possessing class A addresses are General Electric - 3. 0. 0. 0/8, Apple Computer 17. 0. 0. 0/8, the U. S. Postal Service -56. 0. 0. 0/8. 7
IP addresses: Class A n n n n The first octet for network assignment 255. 0. 0. 0 (/8) mask Only 7 bits were left in the first octet (remember, the first bit is always 0) to define a network number 128 networks (2 to the 7 th power) 24 bits in the host portion Each class A address may have over 16 million individual host addresses. Some companies and governmental organizations possessing class A addresses are General Electric - 3. 0. 0. 0/8, Apple Computer 17. 0. 0. 0/8, the U. S. Postal Service -56. 0. 0. 0/8. 7
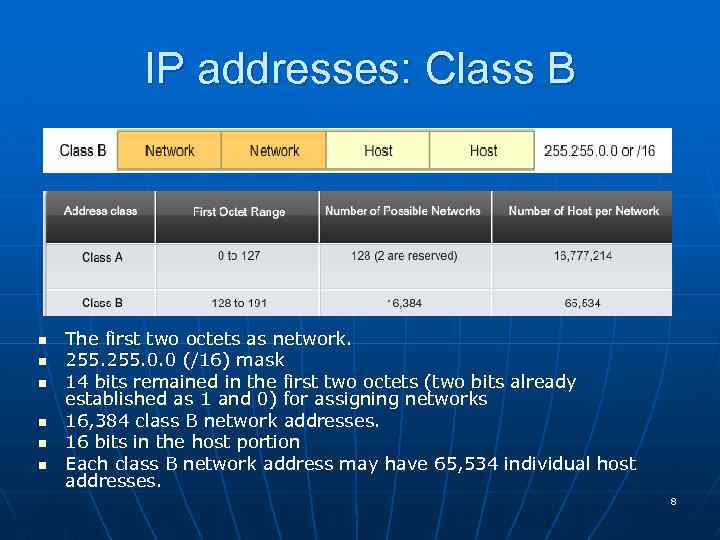 IP addresses: Class B n n n The first two octets as network. 255. 0. 0 (/16) mask 14 bits remained in the first two octets (two bits already established as 1 and 0) for assigning networks 16, 384 class B network addresses. 16 bits in the host portion Each class B network address may have 65, 534 individual host addresses. 8
IP addresses: Class B n n n The first two octets as network. 255. 0. 0 (/16) mask 14 bits remained in the first two octets (two bits already established as 1 and 0) for assigning networks 16, 384 class B network addresses. 16 bits in the host portion Each class B network address may have 65, 534 individual host addresses. 8
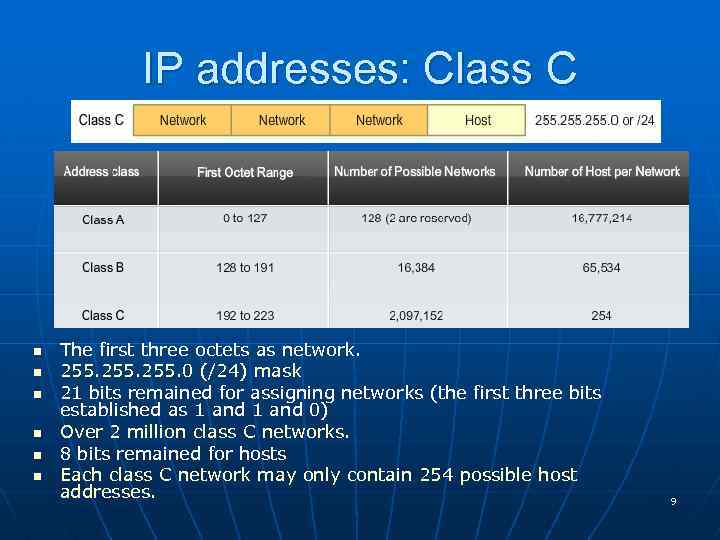 IP addresses: Class C n n n The first three octets as network. 255. 0 (/24) mask 21 bits remained for assigning networks (the first three bits established as 1 and 0) Over 2 million class C networks. 8 bits remained for hosts Each class C network may only contain 254 possible host addresses. 9
IP addresses: Class C n n n The first three octets as network. 255. 0 (/24) mask 21 bits remained for assigning networks (the first three bits established as 1 and 0) Over 2 million class C networks. 8 bits remained for hosts Each class C network may only contain 254 possible host addresses. 9
 IP addresses depletion n In November 2005, Cisco estimated that there were approximately 973 million Internet users. This number has doubled since then. n IPv 4 address space: 4. 3 billion unique addresses. n Only 3. 7 billion addresses are assignable. n In January 2007, about 2. 4 billion of the available IPv 4 addresses are already assigned to end users or ISPs. n Every organization received an entire classful network IP address - either class B with 65, 534 host addresses or a class C with 254 host addresses. n Unused addresses cannot be assigned to someone else. n No class existed to serve a mid-sized organization. n 1. 3 billion addresses are still available from the IPv 4 address space. n IPv 4 address exhaustion by 2013. 10
IP addresses depletion n In November 2005, Cisco estimated that there were approximately 973 million Internet users. This number has doubled since then. n IPv 4 address space: 4. 3 billion unique addresses. n Only 3. 7 billion addresses are assignable. n In January 2007, about 2. 4 billion of the available IPv 4 addresses are already assigned to end users or ISPs. n Every organization received an entire classful network IP address - either class B with 65, 534 host addresses or a class C with 254 host addresses. n Unused addresses cannot be assigned to someone else. n No class existed to serve a mid-sized organization. n 1. 3 billion addresses are still available from the IPv 4 address space. n IPv 4 address exhaustion by 2013. 10
 Class B Address Allocation, 2007 11
Class B Address Allocation, 2007 11
 Ways to prevent IP addresses exhaustion n n Variable Length Subnet Masks (VLSM) Classful Inter-Domain Routing (CIDR) Private Addressing Network Address Translation (NAT) IP v 6 Protocol 12
Ways to prevent IP addresses exhaustion n n Variable Length Subnet Masks (VLSM) Classful Inter-Domain Routing (CIDR) Private Addressing Network Address Translation (NAT) IP v 6 Protocol 12
 Classless Addressing: subnets (підмережі) n n n n Subnetting allows for creating multiple logical networks from a single address block. Subnets are created by using one or more of the host bits as network bits. The mask is extended to borrow some of the bits from the host portion of the address to create additional network bits. The more host bits used, the more subnets that can be defined. For each bit borrowed, we double the number of subnetworks available. However, with each bit we borrow, fewer host addresses are available per subnet. Use this formula to calculate the number of subnets: 2^n, where n = the number of bits borrowed To calculate the number of hosts per network, we use the formula of 2^m – 2, where m = the number of bits left for hosts. 13
Classless Addressing: subnets (підмережі) n n n n Subnetting allows for creating multiple logical networks from a single address block. Subnets are created by using one or more of the host bits as network bits. The mask is extended to borrow some of the bits from the host portion of the address to create additional network bits. The more host bits used, the more subnets that can be defined. For each bit borrowed, we double the number of subnetworks available. However, with each bit we borrow, fewer host addresses are available per subnet. Use this formula to calculate the number of subnets: 2^n, where n = the number of bits borrowed To calculate the number of hosts per network, we use the formula of 2^m – 2, where m = the number of bits left for hosts. 13
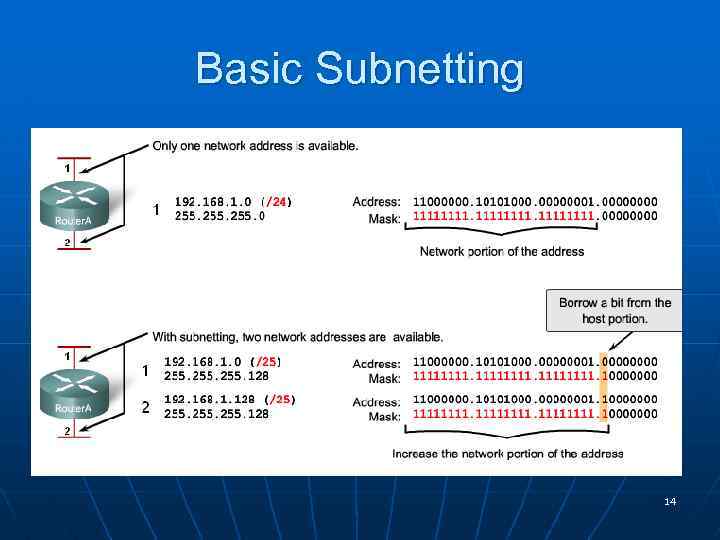 Basic Subnetting 14
Basic Subnetting 14
 VLSM n n The network address is no longer determined by the class of the address. Variable Length Subnet Masks (VLSM, підмережеві маски різної довжини) : subnets with different masks are used in one network system n The mask length is determined by the number of hosts in each subnet. n Less IP addresses are wasted, left unallocated. n To use VLSM: n Determine the total number of hosts required in the entire corporate network (end user devices, servers, intermediate devices, router interfaces, allowing for future growth). n Determine the number and size of the networks n Each WAN link is a network of two hosts (connected interfaces of the routers). 15
VLSM n n The network address is no longer determined by the class of the address. Variable Length Subnet Masks (VLSM, підмережеві маски різної довжини) : subnets with different masks are used in one network system n The mask length is determined by the number of hosts in each subnet. n Less IP addresses are wasted, left unallocated. n To use VLSM: n Determine the total number of hosts required in the entire corporate network (end user devices, servers, intermediate devices, router interfaces, allowing for future growth). n Determine the number and size of the networks n Each WAN link is a network of two hosts (connected interfaces of the routers). 15
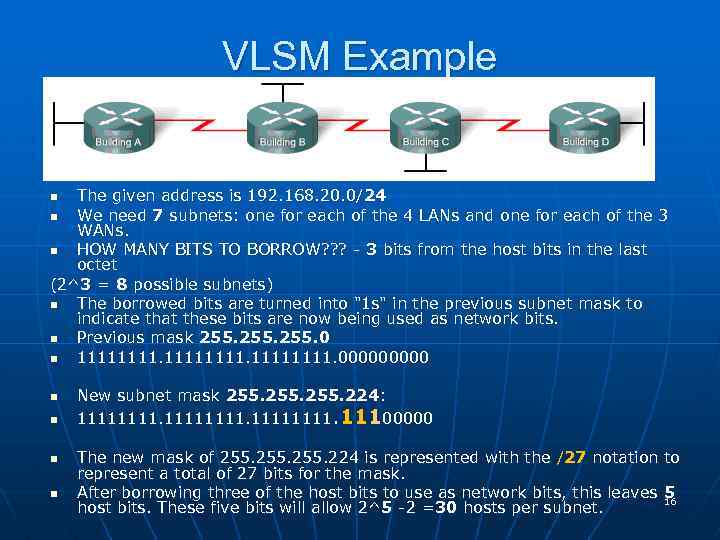 VLSM Example The given address is 192. 168. 20. 0/24 n We need 7 subnets: one for each of the 4 LANs and one for each of the 3 WANs. n HOW MANY BITS TO BORROW? ? ? - 3 bits from the host bits in the last octet (2^3 = 8 possible subnets) n The borrowed bits are turned into "1 s" in the previous subnet mask to indicate that these bits are now being used as network bits. n Previous mask 255. 0 n 11111111. 00000 n n n New subnet mask 255. 224: 11111111. 11100000 The new mask of 255. 224 is represented with the /27 notation to represent a total of 27 bits for the mask. After borrowing three of the host bits to use as network bits, this leaves 16 5 host bits. These five bits will allow 2^5 -2 =30 hosts per subnet.
VLSM Example The given address is 192. 168. 20. 0/24 n We need 7 subnets: one for each of the 4 LANs and one for each of the 3 WANs. n HOW MANY BITS TO BORROW? ? ? - 3 bits from the host bits in the last octet (2^3 = 8 possible subnets) n The borrowed bits are turned into "1 s" in the previous subnet mask to indicate that these bits are now being used as network bits. n Previous mask 255. 0 n 11111111. 00000 n n n New subnet mask 255. 224: 11111111. 11100000 The new mask of 255. 224 is represented with the /27 notation to represent a total of 27 bits for the mask. After borrowing three of the host bits to use as network bits, this leaves 16 5 host bits. These five bits will allow 2^5 -2 =30 hosts per subnet.
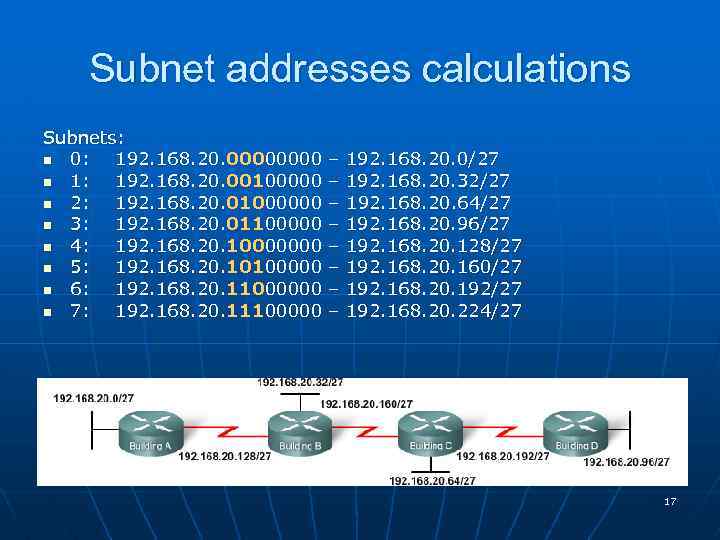 Subnet addresses calculations Subnets: n 0: 192. 168. 20. 0000 n 1: 192. 168. 20. 00100000 n 2: 192. 168. 20. 01000000 n 3: 192. 168. 20. 01100000 n 4: 192. 168. 20. 10000000 n 5: 192. 168. 20. 10100000 n 6: 192. 168. 20. 11000000 n 7: 192. 168. 20. 11100000 – – – – 192. 168. 20. 0/27 192. 168. 20. 32/27 192. 168. 20. 64/27 192. 168. 20. 96/27 192. 168. 20. 128/27 192. 168. 20. 160/27 192. 168. 20. 192/27 192. 168. 20. 224/27 17
Subnet addresses calculations Subnets: n 0: 192. 168. 20. 0000 n 1: 192. 168. 20. 00100000 n 2: 192. 168. 20. 01000000 n 3: 192. 168. 20. 01100000 n 4: 192. 168. 20. 10000000 n 5: 192. 168. 20. 10100000 n 6: 192. 168. 20. 11000000 n 7: 192. 168. 20. 11100000 – – – – 192. 168. 20. 0/27 192. 168. 20. 32/27 192. 168. 20. 64/27 192. 168. 20. 96/27 192. 168. 20. 128/27 192. 168. 20. 160/27 192. 168. 20. 192/27 192. 168. 20. 224/27 17
 More subnetting n Subnets were still created with a significant waste of unused addresses. n Only two addresses are needed in each subnet for the WAN links. n There are 28 unused addresses in each of the three WAN subnets. n We can further divide unused subnets into many smaller subnets. n To create subnets of two hosts for the WAN links, let’s begin with 192. 168. 20. 192/27. n To provide address blocks for the WANS with two addresses each, we will borrow three additional host bits to be used as network bits. Address: 192. 168. 20. 192 Mask: 255. 252 30 Bits in binary: 11111111. 11111100 18
More subnetting n Subnets were still created with a significant waste of unused addresses. n Only two addresses are needed in each subnet for the WAN links. n There are 28 unused addresses in each of the three WAN subnets. n We can further divide unused subnets into many smaller subnets. n To create subnets of two hosts for the WAN links, let’s begin with 192. 168. 20. 192/27. n To provide address blocks for the WANS with two addresses each, we will borrow three additional host bits to be used as network bits. Address: 192. 168. 20. 192 Mask: 255. 252 30 Bits in binary: 11111111. 11111100 18
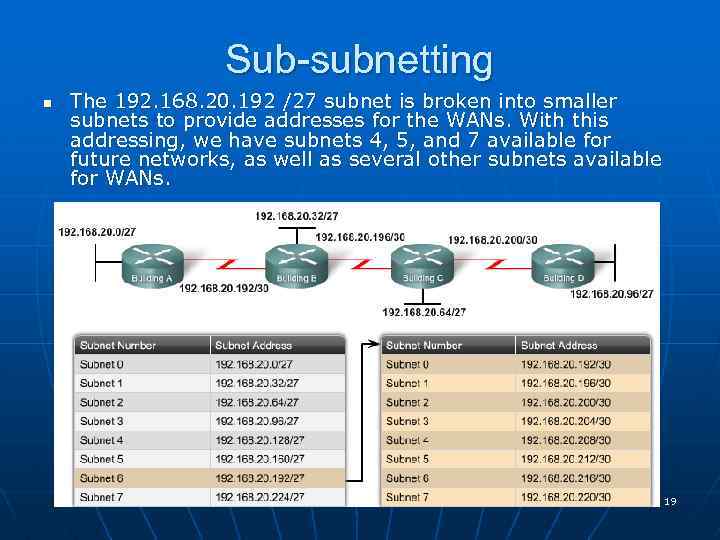 Sub-subnetting n The 192. 168. 20. 192 /27 subnet is broken into smaller subnets to provide addresses for the WANs. With this addressing, we have subnets 4, 5, and 7 available for future networks, as well as several other subnets available for WANs. 19
Sub-subnetting n The 192. 168. 20. 192 /27 subnet is broken into smaller subnets to provide addresses for the WANs. With this addressing, we have subnets 4, 5, and 7 available for future networks, as well as several other subnets available for WANs. 19
 Public and Private IP addresses n n n Public IP addresses are designated for use in networks that are accessible on the Internet. All public Internet addresses must be registered with a Regional Internet Registry (RIR). Organizations can lease public addresses from an ISP. n Private addresses, grouped in blocks, are used in networks that require limited or no Internet access. n The private address blocks are: 10. 0 - 10. 255 (10. 0 /8) 172. 16. 0. 0 - 172. 31. 255 (172. 16. 0. 0 /12) 192. 168. 0. 0 - 192. 168. 255 (192. 168. 0. 0 /16) n n n Private addresses are for private, internal network use only. Private addresses are not routed over the Internet. Unlike public IP addresses, private IP addresses are a reserved block of numbers that can be used by anyone. 20
Public and Private IP addresses n n n Public IP addresses are designated for use in networks that are accessible on the Internet. All public Internet addresses must be registered with a Regional Internet Registry (RIR). Organizations can lease public addresses from an ISP. n Private addresses, grouped in blocks, are used in networks that require limited or no Internet access. n The private address blocks are: 10. 0 - 10. 255 (10. 0 /8) 172. 16. 0. 0 - 172. 31. 255 (172. 16. 0. 0 /12) 192. 168. 0. 0 - 192. 168. 255 (192. 168. 0. 0 /16) n n n Private addresses are for private, internal network use only. Private addresses are not routed over the Internet. Unlike public IP addresses, private IP addresses are a reserved block of numbers that can be used by anyone. 20
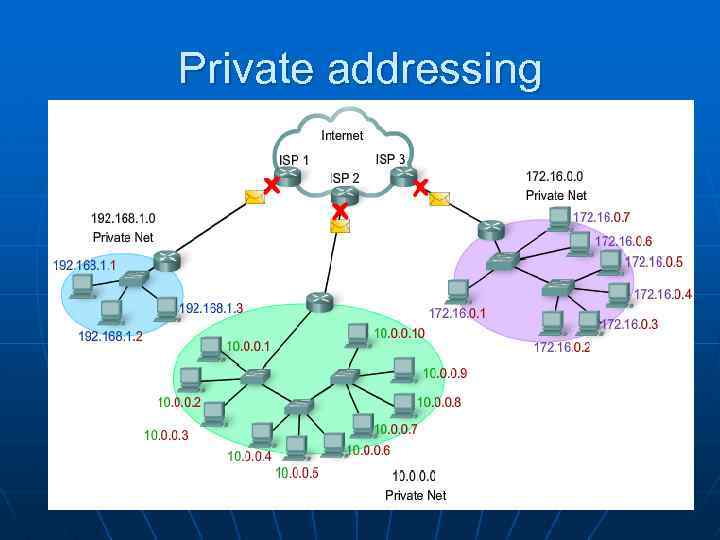 Private addressing 21
Private addressing 21
 Network Address Translation n Packets with private addresses cannot be routed outside the local network. n Each host should be identified over the Internet. n There are not enough public addresses to allow organizations to provide one to each host. n n Network Address Translation (NAT) is a mechanism, which transforms private addresses to public addresses at the edge of their network that works in both directions. Without a translation system, private hosts behind a router in the network of one organization cannot connect with private hosts behind a router in other organizations over the Internet. 22
Network Address Translation n Packets with private addresses cannot be routed outside the local network. n Each host should be identified over the Internet. n There are not enough public addresses to allow organizations to provide one to each host. n n Network Address Translation (NAT) is a mechanism, which transforms private addresses to public addresses at the edge of their network that works in both directions. Without a translation system, private hosts behind a router in the network of one organization cannot connect with private hosts behind a router in other organizations over the Internet. 22
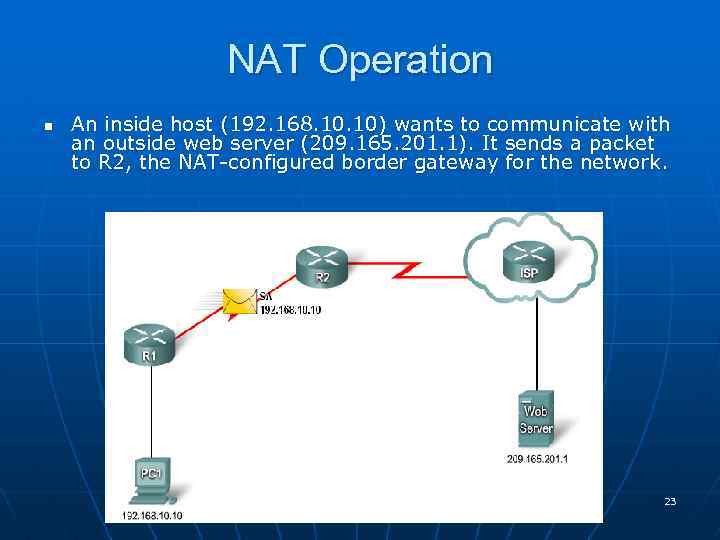 NAT Operation n An inside host (192. 168. 10) wants to communicate with an outside web server (209. 165. 201. 1). It sends a packet to R 2, the NAT-configured border gateway for the network. 23
NAT Operation n An inside host (192. 168. 10) wants to communicate with an outside web server (209. 165. 201. 1). It sends a packet to R 2, the NAT-configured border gateway for the network. 23
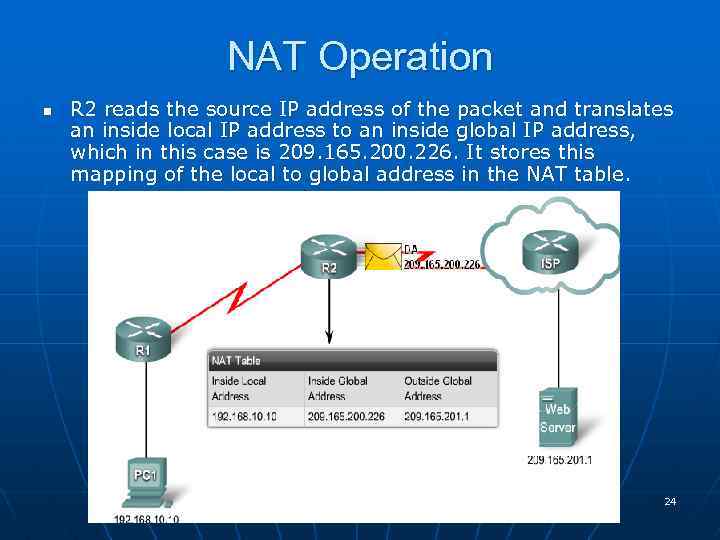 NAT Operation n R 2 reads the source IP address of the packet and translates an inside local IP address to an inside global IP address, which in this case is 209. 165. 200. 226. It stores this mapping of the local to global address in the NAT table. 24
NAT Operation n R 2 reads the source IP address of the packet and translates an inside local IP address to an inside global IP address, which in this case is 209. 165. 200. 226. It stores this mapping of the local to global address in the NAT table. 24
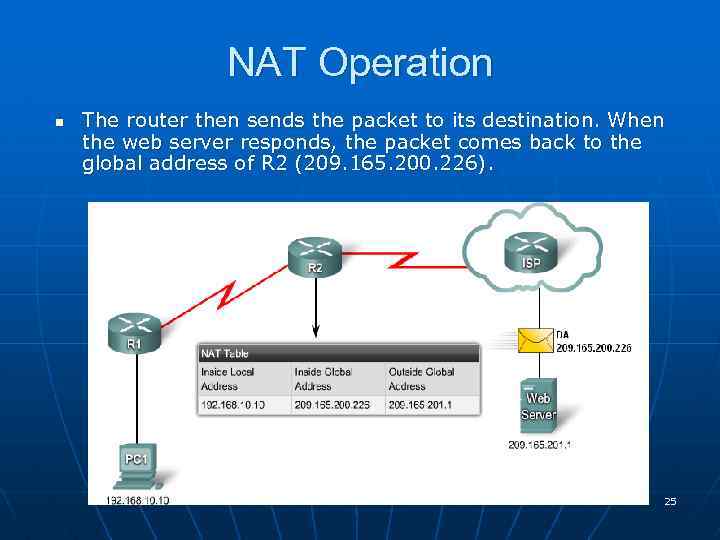 NAT Operation n The router then sends the packet to its destination. When the web server responds, the packet comes back to the global address of R 2 (209. 165. 200. 226). 25
NAT Operation n The router then sends the packet to its destination. When the web server responds, the packet comes back to the global address of R 2 (209. 165. 200. 226). 25
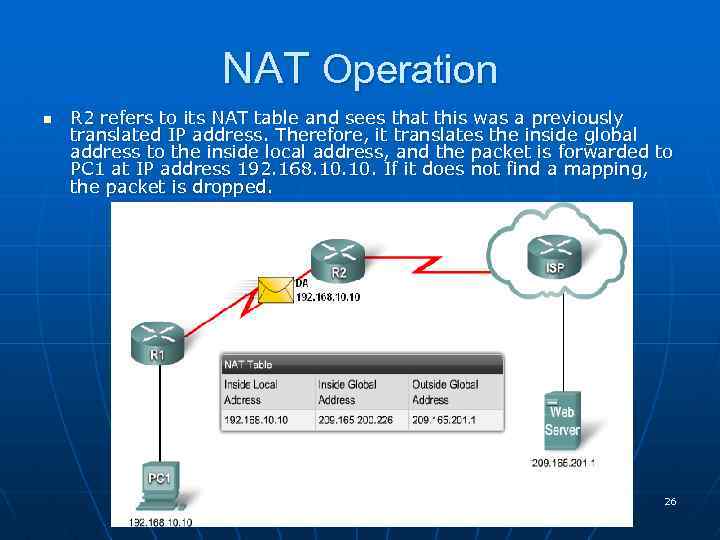 NAT Operation n R 2 refers to its NAT table and sees that this was a previously translated IP address. Therefore, it translates the inside global address to the inside local address, and the packet is forwarded to PC 1 at IP address 192. 168. 10. If it does not find a mapping, the packet is dropped. 26
NAT Operation n R 2 refers to its NAT table and sees that this was a previously translated IP address. Therefore, it translates the inside global address to the inside local address, and the packet is forwarded to PC 1 at IP address 192. 168. 10. If it does not find a mapping, the packet is dropped. 26
 NAT Types n n Dynamic NAT uses a pool of public addresses and assigns them on a first-come, first-served basis. When a host with a private IP address requests access to the Internet, dynamic NAT chooses an IP address from the pool that is not already in use by another host. Static NAT uses a one-to-one mapping of local and global addresses, and these mappings remain constant. Static NAT is particularly useful for web servers or hosts that must have a consistent address that is accessible from the Internet. The addresses to be translated are specified by access control lists, created in NAT configuration. 27
NAT Types n n Dynamic NAT uses a pool of public addresses and assigns them on a first-come, first-served basis. When a host with a private IP address requests access to the Internet, dynamic NAT chooses an IP address from the pool that is not already in use by another host. Static NAT uses a one-to-one mapping of local and global addresses, and these mappings remain constant. Static NAT is particularly useful for web servers or hosts that must have a consistent address that is accessible from the Internet. The addresses to be translated are specified by access control lists, created in NAT configuration. 27
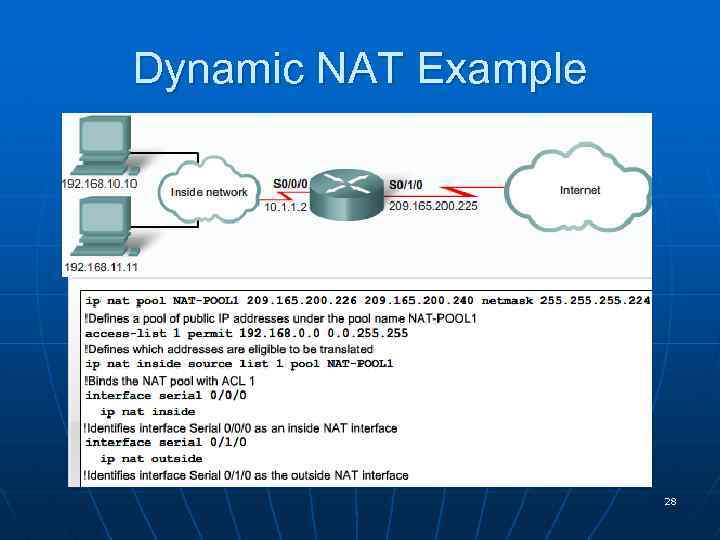 Dynamic NAT Example 28
Dynamic NAT Example 28
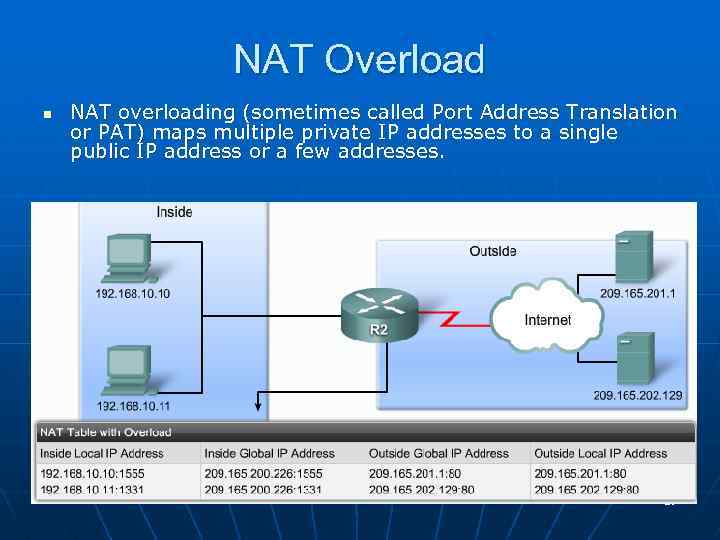 NAT Overload n NAT overloading (sometimes called Port Address Translation or PAT) maps multiple private IP addresses to a single public IP address or a few addresses. 29
NAT Overload n NAT overloading (sometimes called Port Address Translation or PAT) maps multiple private IP addresses to a single public IP address or a few addresses. 29
 NAT Benefits n NAT conserves the legally registered addressing scheme by allowing the privatization of intranets. With NAT overload, internal hosts can share a single public IP address for all external communications. In this type of configuration, very few external addresses are required to support many internal hosts. n NAT provides consistency for internal network addressing schemes. NAT allows the existing address scheme to remain while supporting a new public addressing scheme. This means an organization could change ISPs and not need to change any of its inside clients. n NAT provides network security. Because private networks do not advertise their addresses or internal topology, they remain reasonably secure when used in conjunction with NAT to gain controlled external access. 30
NAT Benefits n NAT conserves the legally registered addressing scheme by allowing the privatization of intranets. With NAT overload, internal hosts can share a single public IP address for all external communications. In this type of configuration, very few external addresses are required to support many internal hosts. n NAT provides consistency for internal network addressing schemes. NAT allows the existing address scheme to remain while supporting a new public addressing scheme. This means an organization could change ISPs and not need to change any of its inside clients. n NAT provides network security. Because private networks do not advertise their addresses or internal topology, they remain reasonably secure when used in conjunction with NAT to gain controlled external access. 30
 NAT Disadvantages n n NAT affects performance and increases delays because the translation of each IP address within the packet headers takes time. Many Internet protocols and applications depend on end-to-end functionality, with unmodified packets forwarded from the source to the destination. By changing end-to-end addresses, NAT prevents some applications that use IP addressing. n End-to-end IP traceability is also lost. It becomes much more difficult n Using NAT also complicates tunneling protocols, such as IPsec, to trace packets that undergo numerous packet address changes over multiple NAT hops, making troubleshooting challenging. On the other hand, hackers who want to determine the source of a packet find it difficult to trace or obtain the original source or destination address. because NAT modifies values in the headers that interfere with the integrity checks done by IPsec and other tunneling protocols. 31
NAT Disadvantages n n NAT affects performance and increases delays because the translation of each IP address within the packet headers takes time. Many Internet protocols and applications depend on end-to-end functionality, with unmodified packets forwarded from the source to the destination. By changing end-to-end addresses, NAT prevents some applications that use IP addressing. n End-to-end IP traceability is also lost. It becomes much more difficult n Using NAT also complicates tunneling protocols, such as IPsec, to trace packets that undergo numerous packet address changes over multiple NAT hops, making troubleshooting challenging. On the other hand, hackers who want to determine the source of a packet find it difficult to trace or obtain the original source or destination address. because NAT modifies values in the headers that interfere with the integrity checks done by IPsec and other tunneling protocols. 31
 IP version 6 Protocol n n n n In the early 1990 s, the Internet Engineering Task Force (IETF) grew concerned about the exhaustion of the IPv 4 network addresses and began to look for a replacement for this protocol. This activity led to the development of what is now known as IPv 6 features are as follows: Enhanced IP addressing Simplified packet header Improved packet handling Increased scalability and mobility Qo. S mechanisms Integrated security 32
IP version 6 Protocol n n n n In the early 1990 s, the Internet Engineering Task Force (IETF) grew concerned about the exhaustion of the IPv 4 network addresses and began to look for a replacement for this protocol. This activity led to the development of what is now known as IPv 6 features are as follows: Enhanced IP addressing Simplified packet header Improved packet handling Increased scalability and mobility Qo. S mechanisms Integrated security 32
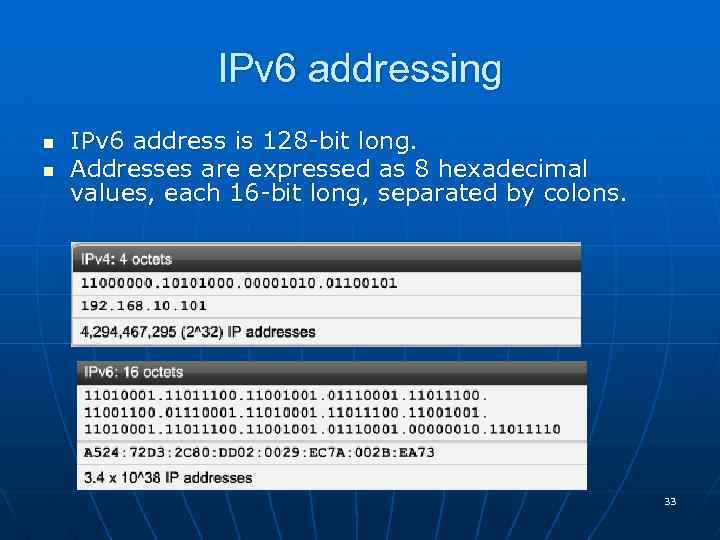 IPv 6 addressing n n IPv 6 address is 128 -bit long. Addresses are expressed as 8 hexadecimal values, each 16 -bit long, separated by colons. 33
IPv 6 addressing n n IPv 6 address is 128 -bit long. Addresses are expressed as 8 hexadecimal values, each 16 -bit long, separated by colons. 33
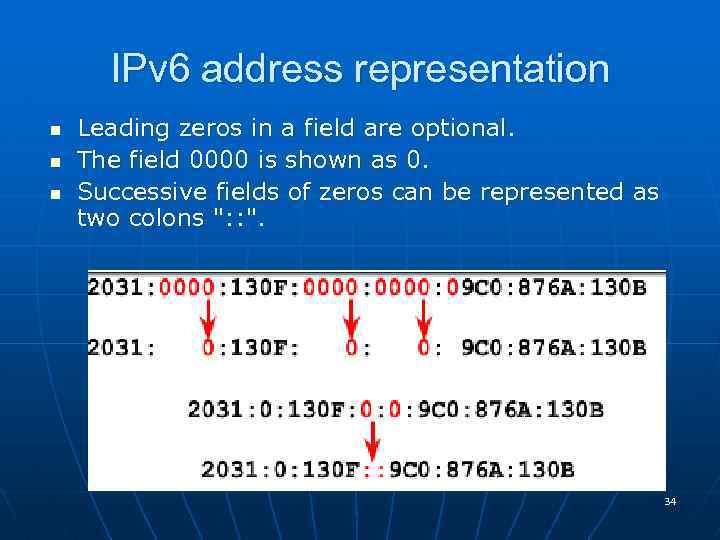 IPv 6 address representation n Leading zeros in a field are optional. The field 0000 is shown as 0. Successive fields of zeros can be represented as two colons ": : ". 34
IPv 6 address representation n Leading zeros in a field are optional. The field 0000 is shown as 0. Successive fields of zeros can be represented as two colons ": : ". 34
 35
35
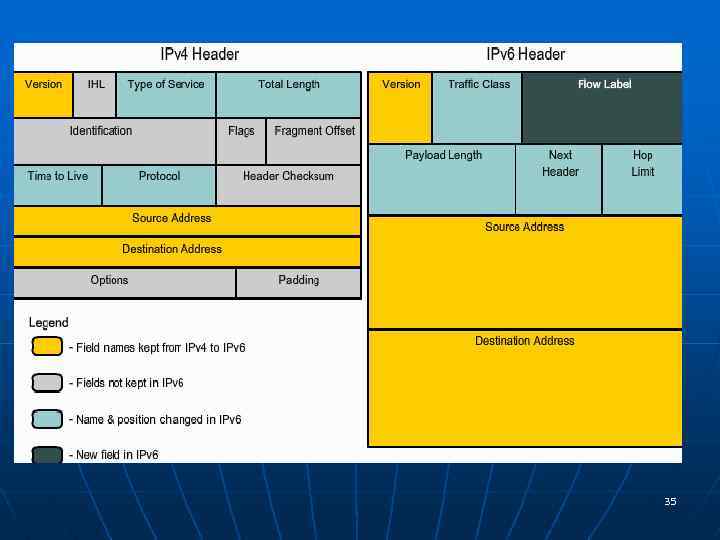
 The IPv 6 simplified header n n n Better routing efficiency for performance and forwarding-rate scalability No broadcasts and thus no potential threat of broadcast storms No requirement for processing checksums Simplified and more efficient extension header mechanisms Flow labels for per-flow processing with no need to open the transport inner packet to identify the various traffic flows. 36
The IPv 6 simplified header n n n Better routing efficiency for performance and forwarding-rate scalability No broadcasts and thus no potential threat of broadcast storms No requirement for processing checksums Simplified and more efficient extension header mechanisms Flow labels for per-flow processing with no need to open the transport inner packet to identify the various traffic flows. 36
 37
37


