dc1641aa741a82fbe49fa06b7156e2e7.ppt
- Количество слайдов: 37

INTRUSION TOLERANT SYSTEMS WORKSHOP Williamsburg, Virginia 5 - 6 October 1999 Jaynarayan H. Lala ITS Program Manager Information Systems Office 1

ITS WORKSHOP AGENDA (1 of 2) Tuesday 8: 00 - 12: 30 PRESENTATIONS l Workshop Goals, DARPA IA&S & ITS Programs l l l l l J. Lala Intrusion Detection State-of-the-Art & Challenges R. Maxion ABFT & Other Error Detection Techniques J. Abraham Security & Fault Tolerance Perspectives J. Rushby Mission & Safety-Critical Architectures L. Alger Threats to Information Systems D. Faatz Abstractions for Building Fault-Tolerant Distr. S/W R. Schlichting Attack / Intrusion Tolerance D. Powell State Restoration D. Siewiorek DICOTS and Stackguard C. Landwehr 2

ITS WORKSHOP AGENDA (2 of 2) Tue 1: 30 - 4: 30 Tue 4: 30 - 5: 30 Reports Working Group Sessions Working Group Preliminary Wed 8: 00 - 11: 30 Working Group Sessions Wed 11: 30 - 12: 30 Working Group Final Reports 3

PRESENTATION OUTLINE l Workshop Goals l DARPA’s Information Assurance & Survivability Programs Overview l Intrusion Tolerant Systems Program Overview l Bridging Fault Tolerance & Intrusion/Attack Tolerance 4

WORKSHOP GOALS l Bring together experts from dependable computing / fault tolerant domain and security domain to exchange ideas that might benefit ITS program l Several prior attempts at exploring applicability of fault tolerance technology to information assurance problems u Matching solutions from one domain to problems from the other domain has not been a successful endeavor l One possible reason: both disciplines are very broad 5

WORKSHOP FOCUS l Current workshop is very narrowly focused on u Applicability of fault tolerance techniques designed for accidental and (unintentional) design faults to certain subset of information assurance (availability & integrity) with respect to intentional faults and attacks u Specifically, use of redundancy, in all its forms, for detecting abnormal behavior and tolerating intentional faults and attacks l Workshop focus is NOT on reconciling terminology of the two communities or solving fault tolerance problems. 6

INFORMATION ASSURANCE & SURVIVABILTY (IA&S) PROGRAMS OVERVIEW Jay Lala, Douglas Maughan, Cathy Mc. Collum, Sami Saydjari, Mike Skroch, Brian Witten Project Managers Information Systems & Technology Offices Tolerance Detection Prevention Attacks 7

Challenging questions Commander’s attack triage questions l Am I under attack ? l What is the nature of the attack ? u Class, mechanism, from where ? l What is mission impact ? u Urgency, damage assessment & control, initial response l When did attack start ? u Follow-on damage assessment, what have I done wrong ? l Who is attacking u What are they trying to do, what is their next step ? l What can I do about it ? u Course of action analysis, collateral damage risk, reversibility of action l Can I survive the attack? l Long term solution Currently, we are Blind and Powerless at all echelons 8
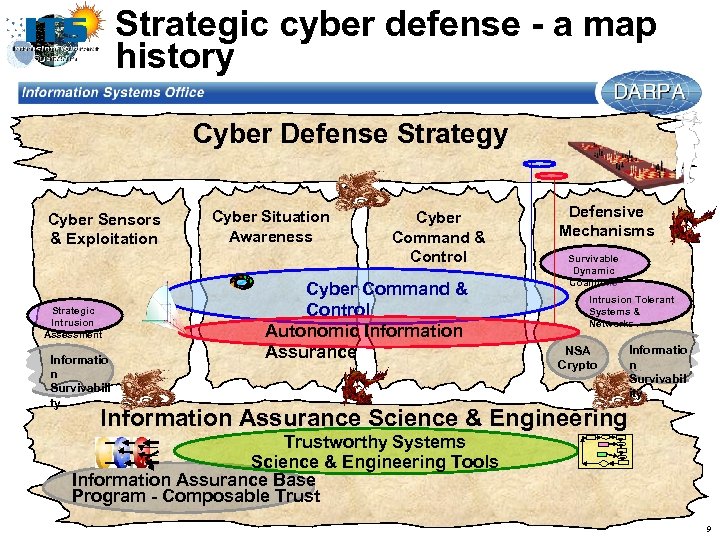
Strategic cyber defense - a map history Cyber Defense Strategy Cyber Sensors & Exploitation Strategic Intrusion Assessment Informatio n Survivabili ty Cyber Situation Awareness Cyber Command & Control Autonomic Information Assurance Defensive Mechanisms Survivable Dynamic Coalitions Intrusion Tolerant Systems & Networks NSA Crypto Informatio n Survivabil ity Information Assurance Science & Engineering Trustworthy Systems Science & Engineering Tools Information Assurance Base Program - Composable Trust 9
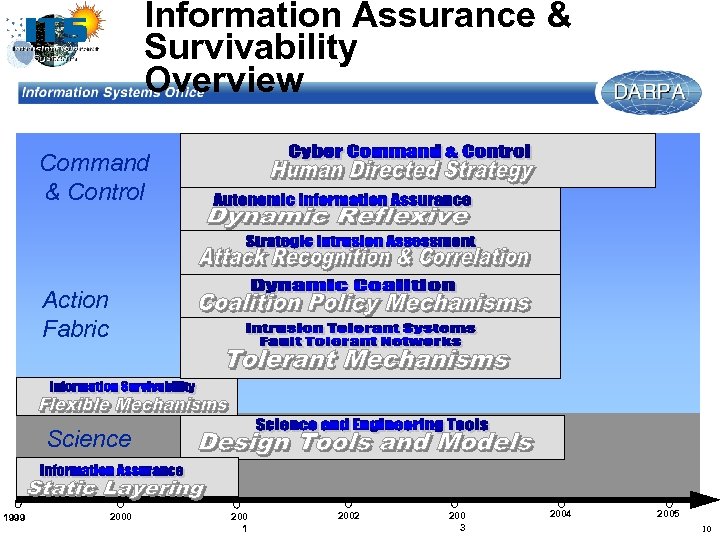
Information Assurance & Survivability Overview Command & Control Action Fabric Science 1999 2000 200 1 2002 200 3 2004 2005 10
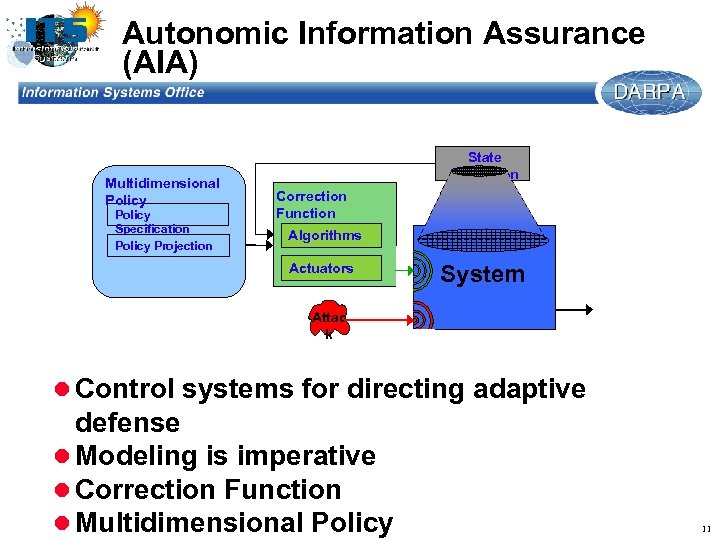
Autonomic Information Assurance (AIA) Multidimensional Policy Specification Policy Projection State Projection Correction Function Algorithms Actuators System Attac k l Control systems for directing adaptive defense l Modeling is imperative l Correction Function l Multidimensional Policy 11
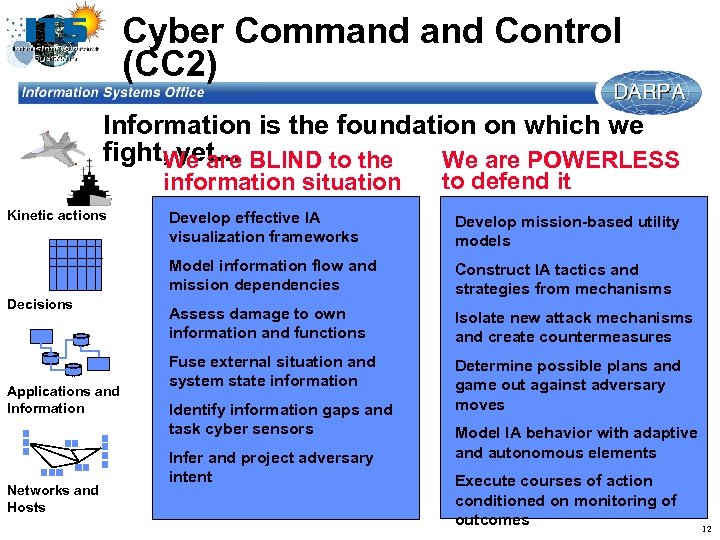
Cyber Command Control (CC 2) Information is the foundation on which we fight, yet. . . BLIND to the We are POWERLESS We are information situation Kinetic actions to defend it Applications and Information Networks and Hosts Develop mission-based utility models Model information flow and mission dependencies Decisions Develop effective IA visualization frameworks Construct IA tactics and strategies from mechanisms Assess damage to own information and functions Isolate new attack mechanisms and create countermeasures Fuse external situation and system state information Determine possible plans and game out against adversary moves Identify information gaps and task cyber sensors Infer and project adversary intent Model IA behavior with adaptive and autonomous elements Execute courses of action conditioned on monitoring of outcomes 12
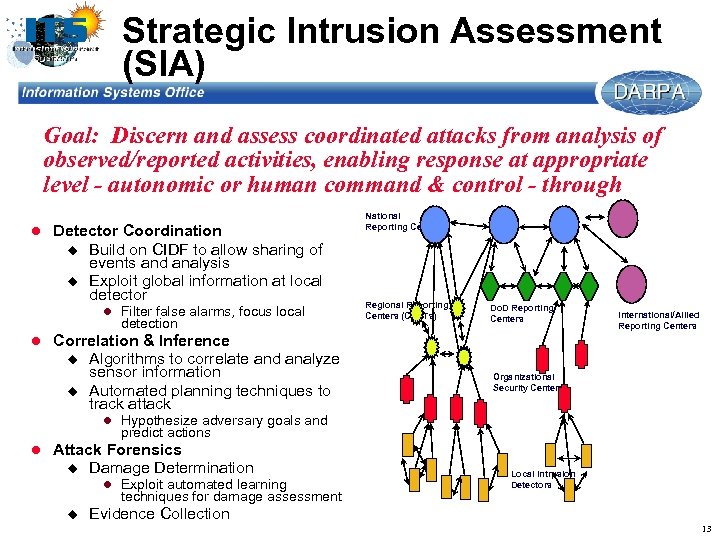
Strategic Intrusion Assessment (SIA) Goal: Discern and assess coordinated attacks from analysis of observed/reported activities, enabling response at appropriate level - autonomic or human command & control - through l Detector Coordination u u Build on CIDF to allow sharing of events and analysis Exploit global information at local detector l Filter false alarms, focus local detection National Reporting Centers Regional Reporting Centers (CERTs) Do. D Reporting Centers International/Allied Reporting Centers l Correlation & Inference u u Algorithms to correlate and analyze sensor information Automated planning techniques to track attack Organizational Security Centers l Hypothesize adversary goals and predict actions l Attack Forensics u Damage Determination l Exploit automated learning techniques for damage assessment u Local Intrusion Detectors Evidence Collection 13
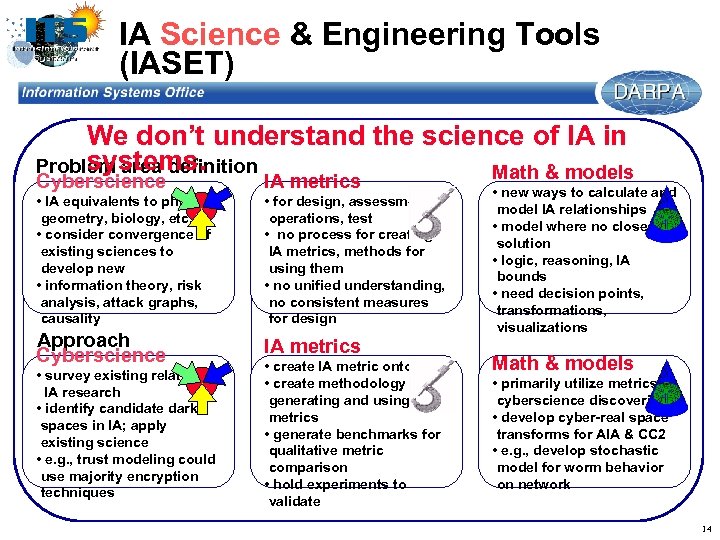
IA Science & Engineering Tools (IASET) We don’t understand the science of IA in systems. Problem area definition Math & models Cyberscience IA metrics • IA equivalents to physics, geometry, biology, etc. • consider convergence of existing sciences to develop new • information theory, risk analysis, attack graphs, causality • for design, assessment, operations, test • no process for creating IA metrics, methods for using them • no unified understanding, no consistent measures for design Approach Cyberscience IA metrics • survey existing related IA research • identify candidate dark spaces in IA; apply existing science • e. g. , trust modeling could use majority encryption techniques • create IA metric ontology • create methodology for generating and using IA metrics • generate benchmarks for qualitative metric comparison • hold experiments to validate • new ways to calculate and model IA relationships • model where no closed solution • logic, reasoning, IA bounds • need decision points, transformations, visualizations Math & models • primarily utilize metrics & cyberscience discoveries • develop cyber-real space transforms for AIA & CC 2 • e. g. , develop stochastic model for worm behavior on network 14
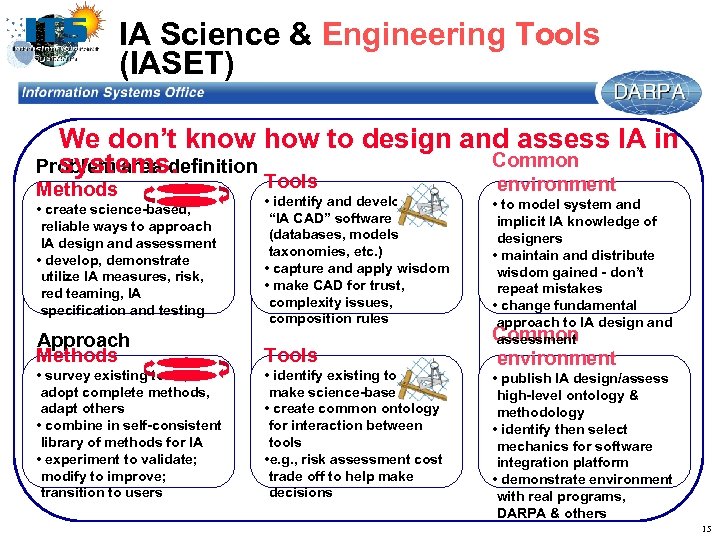
IA Science & Engineering Tools (IASET) We don’t know how to design and assess IA in Common Problem area definition systems. Methods Tools • create science-based, reliable ways to approach IA design and assessment • develop, demonstrate utilize IA measures, risk, red teaming, IA specification and testing • identify and develop “IA CAD” software (databases, models taxonomies, etc. ) • capture and apply wisdom • make CAD for trust, complexity issues, composition rules Approach Methods Tools • survey existing tools, adopt complete methods, adapt others • combine in self-consistent library of methods for IA • experiment to validate; modify to improve; transition to users • identify existing tools, make science-based • create common ontology for interaction between tools • e. g. , risk assessment cost trade off to help make decisions environment • to model system and implicit IA knowledge of designers • maintain and distribute wisdom gained - don’t repeat mistakes • change fundamental approach to IA design and Common assessment environment • publish IA design/assess high-level ontology & methodology • identify then select mechanics for software integration platform • demonstrate environment with real programs, DARPA & others 15

INTRUSION TOLERANT SYSTEMS PROGRAM OVERVIEW 16

BACKGROUND l So far, emphasis has been on making information systems secure by keeping intruders out. l Confidentiality and integrity have been achieved by encrypting critical information and limiting access to it only to authenticated users. l Trusted computing bases, highly classified limited access networks, boundary controllers, in conjunction with physical security, have met the security needs of a relatively small community of highly 17

BACKGROUND l Costs of these techniques, as measured in performance, functionality and affordability, have been high. l Commercial marketplace now dominated by COTS components u the control over the detailed design of hardware, software and architecture necessary to implement these techniques is no longer cost-effective 18

INTRUSION TOLERANT SYSTEMS l Premise u Attacks will happen; some will be successful u Attacks may be coordinated across multiple sites l Hypothesis u Attacks can be detected, contained, and tolerated, enabling continued correct progress of mission critical applications 19

INTRUSION TOLERANT SYSTEMS l Programmatic/Technical Approach u Identify processing system and network vulnerabilities u Develop innovative technologies to solve welldefined portion of vulnerabilities u Apply systems engineering discipline rigorously l Borrow heavily from practices and principles used successfully to engineer fault tolerant computers for mission- and life-critical applications l Support DARPA’s Strategic Cyber Defense vision u Transition to commercial practice 12 20

INTRUSION TOLERANT SYSTEMS l Definition: An intrusion tolerant system is one that can continue to function correctly and provide the intended services to the user in a timely manner even in the face of an attack. l Goal: To conceive, design, develop, implement, demonstrate, and validate tools and techniques that would allow fielding of intrusion tolerant systems. 21

DEPENDABILITY PROPERTIES* l Availability is the readiness for usage. l Reliability is the continuity of service. l Maintainability is the ease of performing maintenance actions. l Safety is the avoidance of catastrophic consequences on the environment. l Security is the prevention of unauthorized access (Confidentiality) and/or handling of information (Integrity). * Dependability: Basic Concepts & Terminology, J. C. Laprie (Ed), Springer-Verlag, New York, 1992 22 8

INFORMATION ASSURANCE ATTRIBUTES* l Availability: Timely, reliable access to data and services l Integrity: No unauthorized modification (including destruction) of data l Identification & Authentication: Certainty of user or receiver identity and authorization to receive specific categories of information l Confidentiality: No unauthorized disclosure l Non-repudiation: Proof of message receipt and sender identification, so neither can deny having processed the data 23

INFORMATION ASSURANCE* l Information Operations that protect and defend information and information systems by ensuring their availability, integrity, authentication, confidentiality, and non-repudiation. l This includes providing for restoration of information systems by incorporating protection, detection, and reaction capabilities. * Do. D Directive 12/9/96 S-3600. 1 Subject: Information Operations 24

ITS PROGRAM EMPHASIS l Availability (Protection against Denial-of- Service Attacks) l Integrity 25
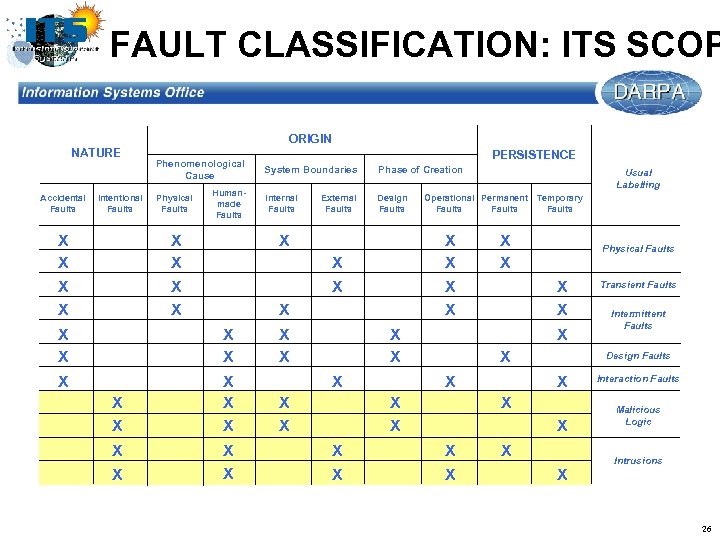
FAULT CLASSIFICATION: ITS SCOP ORIGIN NATURE Accidental Faults Intentional Faults X X Phenomenological Cause Physical Faults Humanmade Faults X X PERSISTENCE System Boundaries Phase of Creation Internal Faults Design Faults External Faults X X X X X Operational Permanent Temporary Faults X X X X Physical Faults X X X X Usual Labelling Intermittent Faults Design Faults X X X Transient Faults X X Interaction Faults Malicious Logic Intrusions 26

ITS TECHNICAL APPROACHES: CURRENT PROJECTS l Eleven projects that span formal methods to sand-boxing techniques u Proof Carrying Code u Execution Time Monitors: Wrappers, Software Insertion u Fragmentation & Encoding u Watermarks 27

CURRENT PROJECTS 28
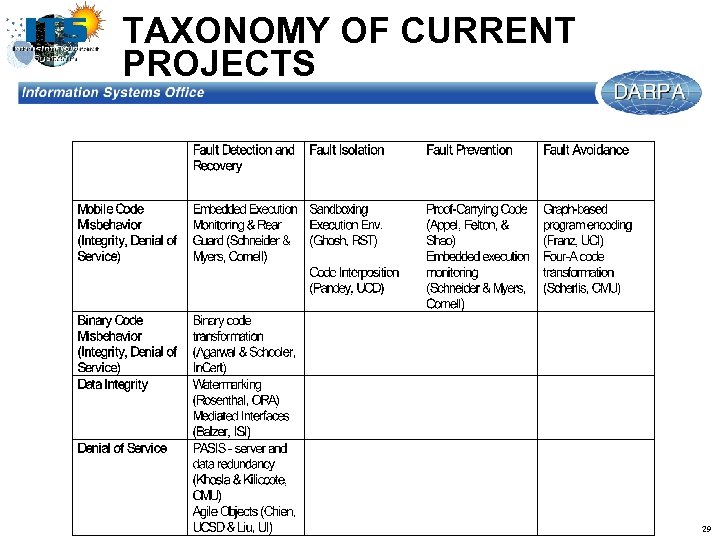
TAXONOMY OF CURRENT PROJECTS 29

BRIDGING FAULT TOLERANCE & INTRUSION / ATTACK TOLERANCE 30

PARALLELS TO FAULT TOLERANCE l Many of the functions that must be performed to tolerate intentional faults/attacks are the same as those required to tolerate accidental faults. u Many hard problems have been solved in the design, development and implementation of these functions. 31

FAULT TOLERANCE-SECURITY: KNOWLEDGE EXCHANGE l Security community should become aware of the required functions and techniques as well as the problems posed and solutions discovered. l Fault tolerance community should become familiar with the types of intentional faults/attacks to which information infrastructure is vulnerable so as to adapt solutions to security domain. 32

EXAMPLES OF FAULT TOLERANCE FUNCTIONS & TECHNIQUES 33

FAULT TOLERANCE FUNCTIONS: EXAMPLES l Error/Damage Confinement l Error Detection* l Error Isolation/ Identification l Error Masking l Fail-Silent l Fail-Stop l Graceful Degradation l State Restoration* l Reconfiguration l Repair / Replacement 34
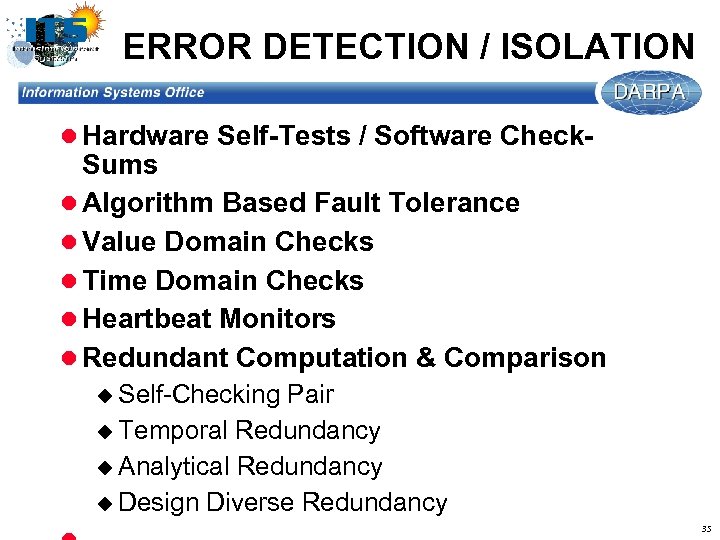
ERROR DETECTION / ISOLATION l Hardware Self-Tests / Software Check- Sums l Algorithm Based Fault Tolerance l Value Domain Checks l Time Domain Checks l Heartbeat Monitors l Redundant Computation & Comparison u Self-Checking Pair u Temporal Redundancy u Analytical Redundancy u Design Diverse Redundancy 35

STATE RESTORATION l Check-Point / Rollback l Roll-Forward l Switch to Backup u Hot, warm, cold l Majority Vote Restore l Repair / Replace & Restart l Software Rejuvenation 36

CHALLENGES l What fault tolerance functions are relevant to intrusion / attack tolerance? What additional functions must be performed by ITS? l Can FT techniques be adapted to intrusion/attack tolerance? If yes, how? If not, what innovative techniques are necessary to tolerate attacks /intrusions? l What additional vulnerabilities do these techniques introduce that can be exploited by attackers? l How to counter these additional 37
dc1641aa741a82fbe49fa06b7156e2e7.ppt