bac2d0bbbd6832a96dafaae81bd63a63.ppt
- Количество слайдов: 51
 Intrusion Detection Methods “Intrusion detection is the process of identifying and responding to malicious activity targeted at computing and networking resources. ”
Intrusion Detection Methods “Intrusion detection is the process of identifying and responding to malicious activity targeted at computing and networking resources. ”
 The Seven Fundamentals 1. What are the methods used 2. 3. 4. 5. 6. 7. How are IDS organized What is an intrusion How do we trace and how do they hide How do we correlate information How can we trap intruders Incident response
The Seven Fundamentals 1. What are the methods used 2. 3. 4. 5. 6. 7. How are IDS organized What is an intrusion How do we trace and how do they hide How do we correlate information How can we trap intruders Incident response
 Some fundamental questions • Are ID methods only suited for manual use by experts? • Are ID methods well defined enough to be automated? • What are some of the manual methods used by experts? • What ID methods are available in tools today?
Some fundamental questions • Are ID methods only suited for manual use by experts? • Are ID methods well defined enough to be automated? • What are some of the manual methods used by experts? • What ID methods are available in tools today?
 ID methods • • Audit trail processing On-the-fly processing Profiles of normal behavior Signatures of abnormal behavior • Parameter pattern matching or anomaly discovery Are the above methods independent? Dependant? Mutually exclusive?
ID methods • • Audit trail processing On-the-fly processing Profiles of normal behavior Signatures of abnormal behavior • Parameter pattern matching or anomaly discovery Are the above methods independent? Dependant? Mutually exclusive?
 Audit Trail Processing • Activities are first logged and stored in a log file via audit probs. • Audit probes are [mostly] selected based on what constitutes security critical events. • System and security administrators (and designers) are changed with enabling/disabling probs. What are the TCSEC requirements for Audit? (See Auditing vs. Performance? What are the issues? Page 40)
Audit Trail Processing • Activities are first logged and stored in a log file via audit probs. • Audit probes are [mostly] selected based on what constitutes security critical events. • System and security administrators (and designers) are changed with enabling/disabling probs. What are the TCSEC requirements for Audit? (See Auditing vs. Performance? What are the issues? Page 40)
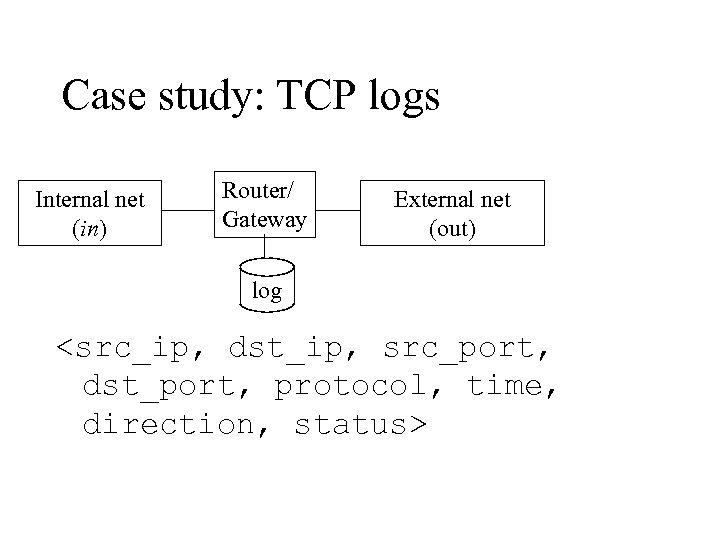 Case study: TCP logs Internal net (in) Router/ Gateway External net (out) log
Case study: TCP logs Internal net (in) Router/ Gateway External net (out) log
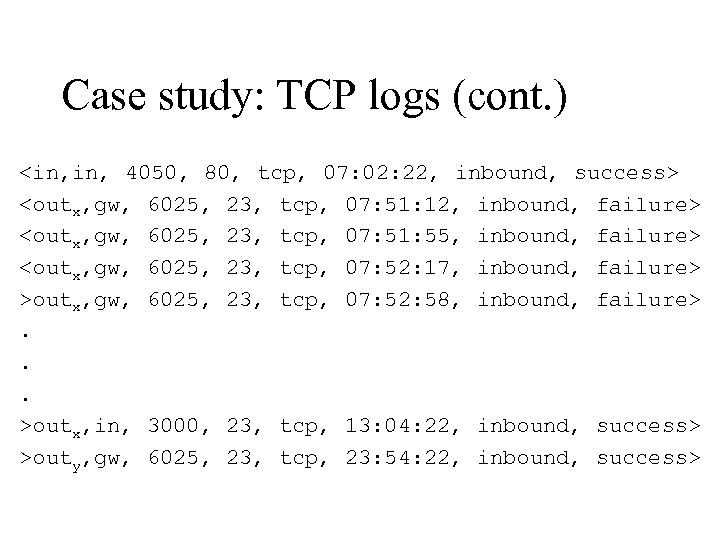 Case study: TCP logs (cont. )
Case study: TCP logs (cont. )
 How much of the previous discussion can be automated?
How much of the previous discussion can be automated?
 Examples of things to watch for! • • • Users logging in at strange hours Unexpected reboots or clock changes Unusual error messages Failed login attempts Unauthorized use of the su command • Users logging from unusual locations
Examples of things to watch for! • • • Users logging in at strange hours Unexpected reboots or clock changes Unusual error messages Failed login attempts Unauthorized use of the su command • Users logging from unusual locations
 Problems to be considered while using logging systems Most administrators don’t collect audits, and if they do, they rarely process them!
Problems to be considered while using logging systems Most administrators don’t collect audits, and if they do, they rarely process them!
 Problems to be considered while using logging systems (cont. ) • Large size of audit files - About 5 M per week for a workgroup server - Becomes more problematic for centralized logging 11
Problems to be considered while using logging systems (cont. ) • Large size of audit files - About 5 M per week for a workgroup server - Becomes more problematic for centralized logging 11
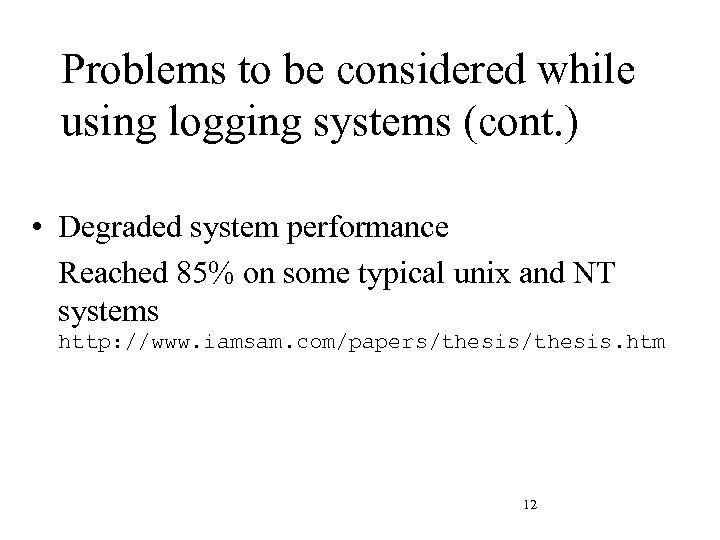 Problems to be considered while using logging systems (cont. ) • Degraded system performance Reached 85% on some typical unix and NT systems http: //www. iamsam. com/papers/thesis. htm 12
Problems to be considered while using logging systems (cont. ) • Degraded system performance Reached 85% on some typical unix and NT systems http: //www. iamsam. com/papers/thesis. htm 12
 Problems to be considered while using logging systems (cont. ) • Difficulty in protecting the log - Log files growing smaller! - Print everything 13
Problems to be considered while using logging systems (cont. ) • Difficulty in protecting the log - Log files growing smaller! - Print everything 13
 Problems to be considered while using logging systems (cont. ) • Unknown storage duration of logs How long should logs be kept? How long are they kept on your linux system? 14
Problems to be considered while using logging systems (cont. ) • Unknown storage duration of logs How long should logs be kept? How long are they kept on your linux system? 14
 Unix Syslog • Syslogd is a daemon (background process) • Receives message for the log file from: – User processes running on the same mchaine (as syslogd) via /dev/log – Kernel routines (/dev/klog) – Processes on another machine via UDP port 514 • Syslogd defines an associated API for application authors
Unix Syslog • Syslogd is a daemon (background process) • Receives message for the log file from: – User processes running on the same mchaine (as syslogd) via /dev/log – Kernel routines (/dev/klog) – Processes on another machine via UDP port 514 • Syslogd defines an associated API for application authors
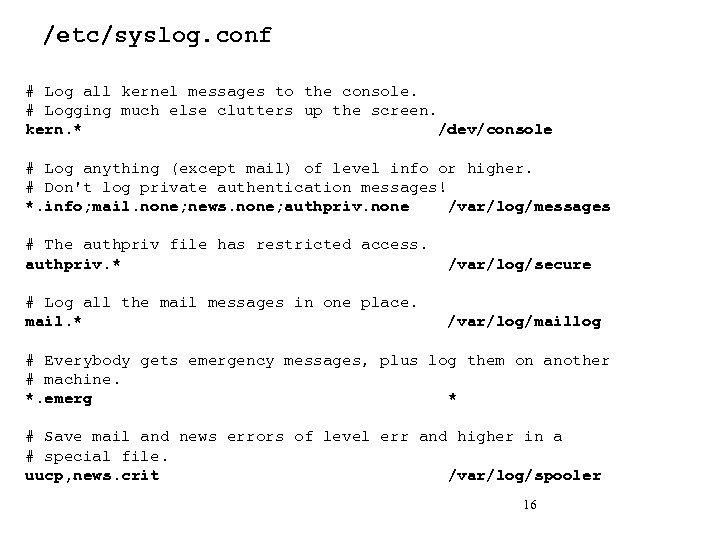 /etc/syslog. conf # Log all kernel messages to the console. # Logging much else clutters up the screen. kern. * /dev/console # Log anything (except mail) of level info or higher. # Don't log private authentication messages! *. info; mail. none; news. none; authpriv. none /var/log/messages # The authpriv file has restricted access. authpriv. * /var/log/secure # Log all the mail messages in one place. mail. * /var/log/maillog # Everybody gets emergency messages, plus log them on another # machine. *. emerg * # Save mail and news errors of level err and higher in a # special file. uucp, news. crit /var/log/spooler 16
/etc/syslog. conf # Log all kernel messages to the console. # Logging much else clutters up the screen. kern. * /dev/console # Log anything (except mail) of level info or higher. # Don't log private authentication messages! *. info; mail. none; news. none; authpriv. none /var/log/messages # The authpriv file has restricted access. authpriv. * /var/log/secure # Log all the mail messages in one place. mail. * /var/log/maillog # Everybody gets emergency messages, plus log them on another # machine. *. emerg * # Save mail and news errors of level err and higher in a # special file. uucp, news. crit /var/log/spooler 16
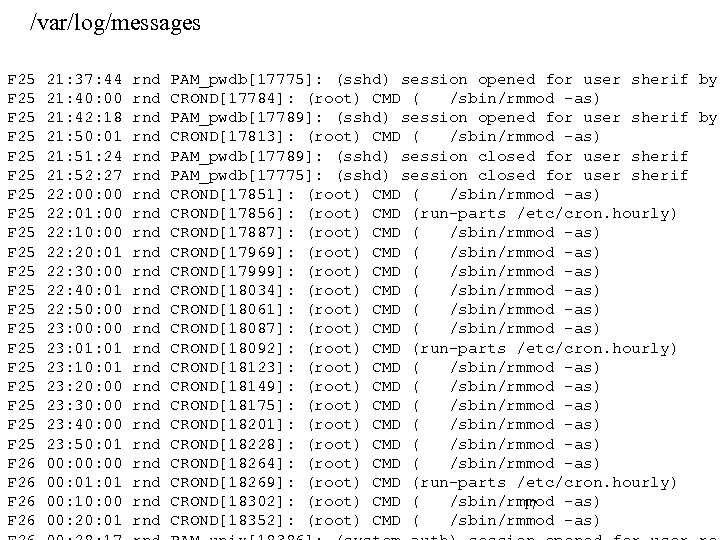 /var/log/messages F 25 F 25 F 25 F 25 F 25 F 26 21: 37: 44 21: 40: 00 21: 42: 18 21: 50: 01 21: 51: 24 21: 52: 27 22: 00 22: 01: 00 22: 10: 00 22: 20: 01 22: 30: 00 22: 40: 01 22: 50: 00 23: 01: 01 23: 10: 01 23: 20: 00 23: 30: 00 23: 40: 00 23: 50: 01 00: 00 00: 01 00: 10: 00 00: 20: 01 rnd rnd rnd rnd rnd rnd PAM_pwdb[17775]: (sshd) session opened for user sherif by CROND[17784]: (root) CMD ( /sbin/rmmod -as) PAM_pwdb[17789]: (sshd) session opened for user sherif by CROND[17813]: (root) CMD ( /sbin/rmmod -as) PAM_pwdb[17789]: (sshd) session closed for user sherif PAM_pwdb[17775]: (sshd) session closed for user sherif CROND[17851]: (root) CMD ( /sbin/rmmod -as) CROND[17856]: (root) CMD (run-parts /etc/cron. hourly) CROND[17887]: (root) CMD ( /sbin/rmmod -as) CROND[17969]: (root) CMD ( /sbin/rmmod -as) CROND[17999]: (root) CMD ( /sbin/rmmod -as) CROND[18034]: (root) CMD ( /sbin/rmmod -as) CROND[18061]: (root) CMD ( /sbin/rmmod -as) CROND[18087]: (root) CMD ( /sbin/rmmod -as) CROND[18092]: (root) CMD (run-parts /etc/cron. hourly) CROND[18123]: (root) CMD ( /sbin/rmmod -as) CROND[18149]: (root) CMD ( /sbin/rmmod -as) CROND[18175]: (root) CMD ( /sbin/rmmod -as) CROND[18201]: (root) CMD ( /sbin/rmmod -as) CROND[18228]: (root) CMD ( /sbin/rmmod -as) CROND[18264]: (root) CMD ( /sbin/rmmod -as) CROND[18269]: (root) CMD (run-parts /etc/cron. hourly) CROND[18302]: (root) CMD ( /sbin/rmmod -as) 17 CROND[18352]: (root) CMD ( /sbin/rmmod -as)
/var/log/messages F 25 F 25 F 25 F 25 F 25 F 26 21: 37: 44 21: 40: 00 21: 42: 18 21: 50: 01 21: 51: 24 21: 52: 27 22: 00 22: 01: 00 22: 10: 00 22: 20: 01 22: 30: 00 22: 40: 01 22: 50: 00 23: 01: 01 23: 10: 01 23: 20: 00 23: 30: 00 23: 40: 00 23: 50: 01 00: 00 00: 01 00: 10: 00 00: 20: 01 rnd rnd rnd rnd rnd rnd PAM_pwdb[17775]: (sshd) session opened for user sherif by CROND[17784]: (root) CMD ( /sbin/rmmod -as) PAM_pwdb[17789]: (sshd) session opened for user sherif by CROND[17813]: (root) CMD ( /sbin/rmmod -as) PAM_pwdb[17789]: (sshd) session closed for user sherif PAM_pwdb[17775]: (sshd) session closed for user sherif CROND[17851]: (root) CMD ( /sbin/rmmod -as) CROND[17856]: (root) CMD (run-parts /etc/cron. hourly) CROND[17887]: (root) CMD ( /sbin/rmmod -as) CROND[17969]: (root) CMD ( /sbin/rmmod -as) CROND[17999]: (root) CMD ( /sbin/rmmod -as) CROND[18034]: (root) CMD ( /sbin/rmmod -as) CROND[18061]: (root) CMD ( /sbin/rmmod -as) CROND[18087]: (root) CMD ( /sbin/rmmod -as) CROND[18092]: (root) CMD (run-parts /etc/cron. hourly) CROND[18123]: (root) CMD ( /sbin/rmmod -as) CROND[18149]: (root) CMD ( /sbin/rmmod -as) CROND[18175]: (root) CMD ( /sbin/rmmod -as) CROND[18201]: (root) CMD ( /sbin/rmmod -as) CROND[18228]: (root) CMD ( /sbin/rmmod -as) CROND[18264]: (root) CMD ( /sbin/rmmod -as) CROND[18269]: (root) CMD (run-parts /etc/cron. hourly) CROND[18302]: (root) CMD ( /sbin/rmmod -as) 17 CROND[18352]: (root) CMD ( /sbin/rmmod -as)
![/var/log/mail F 25 22: 32: 22 rnd sendmail[18009]: g 1 PKU 1 x 18007: /var/log/mail F 25 22: 32: 22 rnd sendmail[18009]: g 1 PKU 1 x 18007:](https://present5.com/presentation/bac2d0bbbd6832a96dafaae81bd63a63/image-18.jpg) /var/log/mail F 25 22: 32: 22 rnd sendmail[18009]: g 1 PKU 1 x 18007: to=
/var/log/mail F 25 22: 32: 22 rnd sendmail[18009]: g 1 PKU 1 x 18007: to=
![SWATCH • Simple and effective tool • Written in perl /pattern/[, /pattern/] action[, action] SWATCH • Simple and effective tool • Written in perl /pattern/[, /pattern/] action[, action]](https://present5.com/presentation/bac2d0bbbd6832a96dafaae81bd63a63/image-19.jpg) SWATCH • Simple and effective tool • Written in perl /pattern/[, /pattern/] action[, action] duration
SWATCH • Simple and effective tool • Written in perl /pattern/[, /pattern/] action[, action] duration
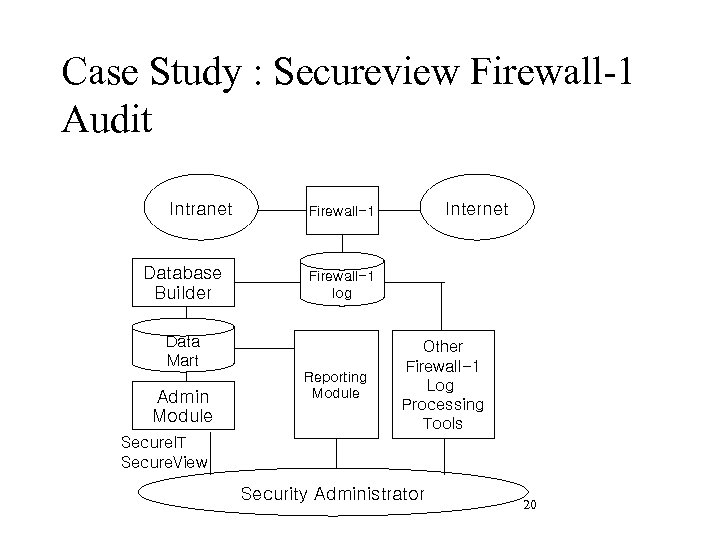 Case Study : Secureview Firewall-1 Audit Intranet Database Builder Firewall-1 log Data Mart Admin Module Internet Firewall-1 Reporting Module Other Firewall-1 Log Processing Tools Secure. IT Secure. View Security Administrator 20
Case Study : Secureview Firewall-1 Audit Intranet Database Builder Firewall-1 log Data Mart Admin Module Internet Firewall-1 Reporting Module Other Firewall-1 Log Processing Tools Secure. IT Secure. View Security Administrator 20
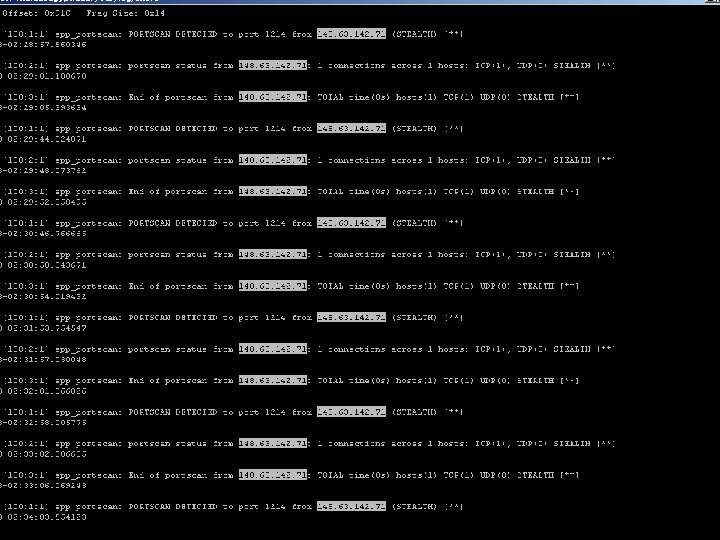
 Mar 2 23: 51 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 54: 33 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 55: 39 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 56: 44 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 57: 50 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 58: 49 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 00 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 01 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 02: 05 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 03: 11 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 04: 14 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** 21
Mar 2 23: 51 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 54: 33 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 55: 39 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 56: 44 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 57: 50 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 2 23: 58: 49 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 00 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 01 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 02: 05 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 03: 11 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** Mar 3 00: 04: 14 148. 63. 149. 144: 1072 -> 208. 160. 134. 38: 1214 VECNA ****P*** 21
 22
22
 23
23
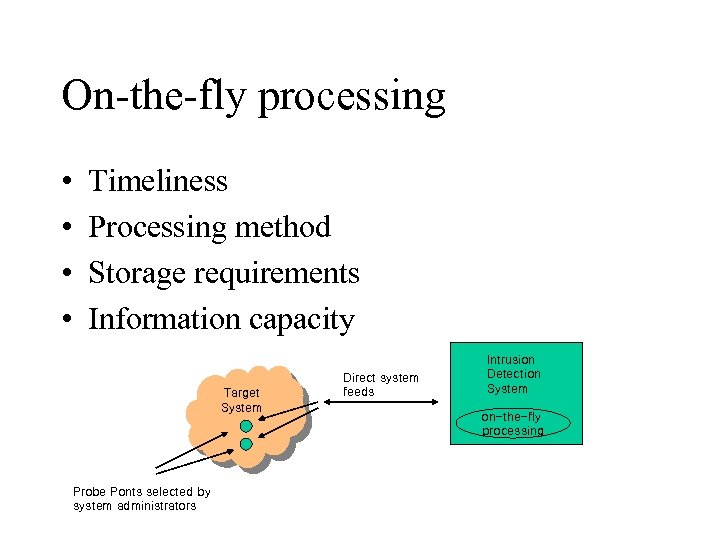 On-the-fly processing • • Timeliness Processing method Storage requirements Information capacity Target System Probe Ponts selected by system administrators Direct system feeds Intrusion Detection System on-the-fly processing
On-the-fly processing • • Timeliness Processing method Storage requirements Information capacity Target System Probe Ponts selected by system administrators Direct system feeds Intrusion Detection System on-the-fly processing
 Network management and NIDS • Use SNMP and RMON (RFC 1271) as a basis for ID collection and processing – Analyze traffic history and statistics – Examine network trends – initiate alarms – Traffic generation for testing
Network management and NIDS • Use SNMP and RMON (RFC 1271) as a basis for ID collection and processing – Analyze traffic history and statistics – Examine network trends – initiate alarms – Traffic generation for testing
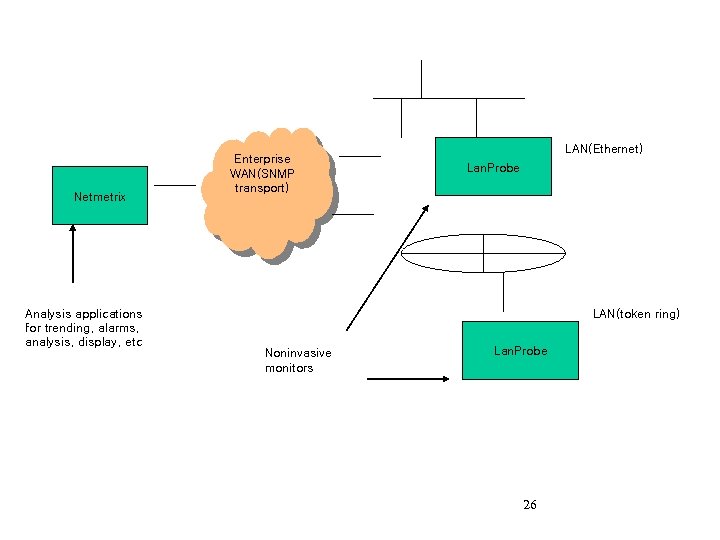 Netmetrix Analysis applications for trending, alarms, analysis, display, etc Enterprise WAN(SNMP transport) LAN(Ethernet) Lan. Probe LAN(token ring) Noninvasive monitors Lan. Probe 26
Netmetrix Analysis applications for trending, alarms, analysis, display, etc Enterprise WAN(SNMP transport) LAN(Ethernet) Lan. Probe LAN(token ring) Noninvasive monitors Lan. Probe 26
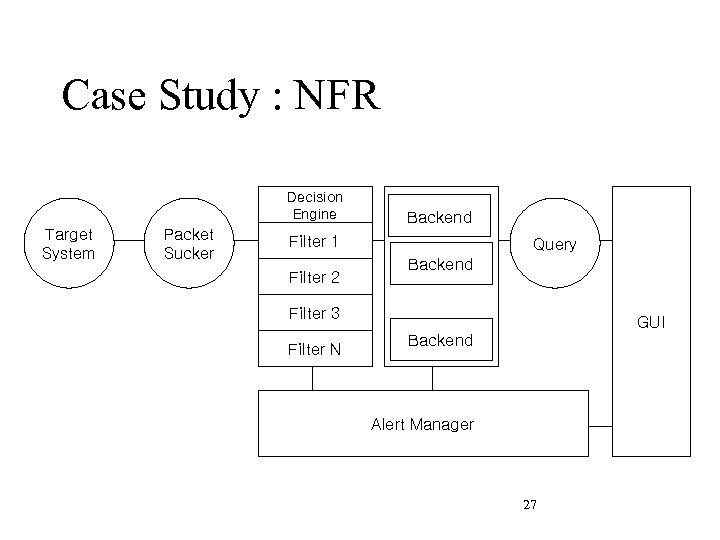 Case Study : NFR Decision Engine Target System Packet Sucker Backend Filter 1 Filter 2 Query Backend Filter 3 Filter N GUI Backend Alert Manager 27
Case Study : NFR Decision Engine Target System Packet Sucker Backend Filter 1 Filter 2 Query Backend Filter 3 Filter N GUI Backend Alert Manager 27
 Methods for extracting traffic from the network for processing • In-line diversion of traffic by network components • Off-line extraction (passive sniffing) – Most used: Ethernet promiscuous mode – Other examples: • Serial lines • Wireless networks • Tempest effect aka The van Eck effect
Methods for extracting traffic from the network for processing • In-line diversion of traffic by network components • Off-line extraction (passive sniffing) – Most used: Ethernet promiscuous mode – Other examples: • Serial lines • Wireless networks • Tempest effect aka The van Eck effect
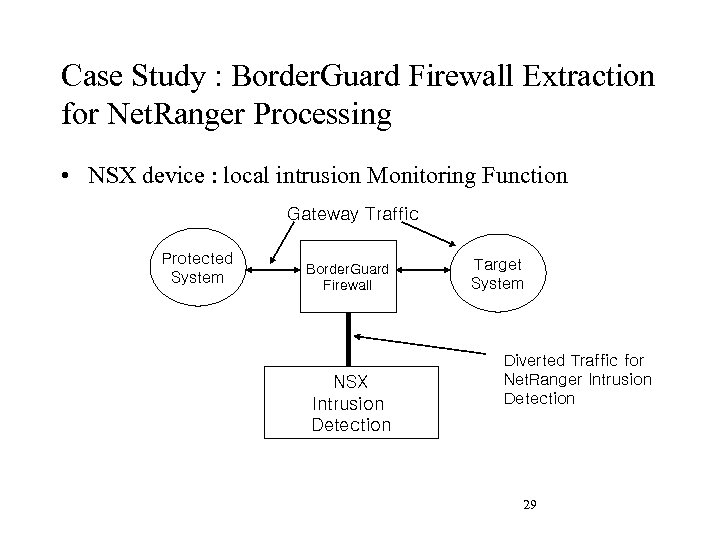 Case Study : Border. Guard Firewall Extraction for Net. Ranger Processing • NSX device : local intrusion Monitoring Function Gateway Traffic Protected System Border. Guard Firewall NSX Intrusion Detection Target System Diverted Traffic for Net. Ranger Intrusion Detection 29
Case Study : Border. Guard Firewall Extraction for Net. Ranger Processing • NSX device : local intrusion Monitoring Function Gateway Traffic Protected System Border. Guard Firewall NSX Intrusion Detection Target System Diverted Traffic for Net. Ranger Intrusion Detection 29
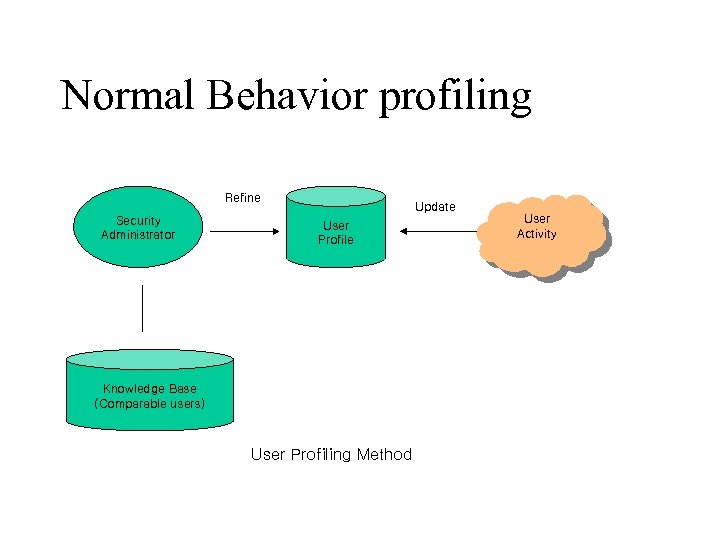 Normal Behavior profiling Refine Security Administrator Update User Profile Knowledge Base (Comparable users) User Profiling Method User Activity
Normal Behavior profiling Refine Security Administrator Update User Profile Knowledge Base (Comparable users) User Profiling Method User Activity
 Normal Behavior profiling • Initial profiling of new systems and users based on estimations of expected behavior • Observed user and system behavior should be used to fine-tune profiles • Information from other (external) resources is used to improve the accuracy of prediction
Normal Behavior profiling • Initial profiling of new systems and users based on estimations of expected behavior • Observed user and system behavior should be used to fine-tune profiles • Information from other (external) resources is used to improve the accuracy of prediction
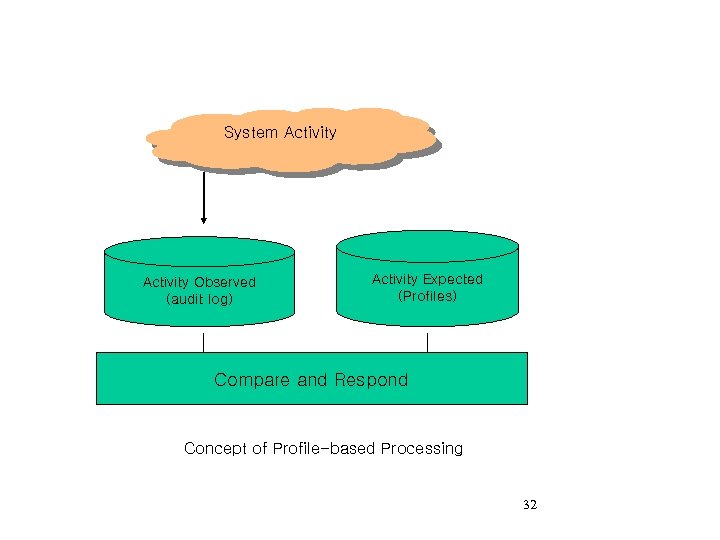 System Activity Observed (audit log) Activity Expected (Profiles) Compare and Respond Concept of Profile-based Processing 32
System Activity Observed (audit log) Activity Expected (Profiles) Compare and Respond Concept of Profile-based Processing 32
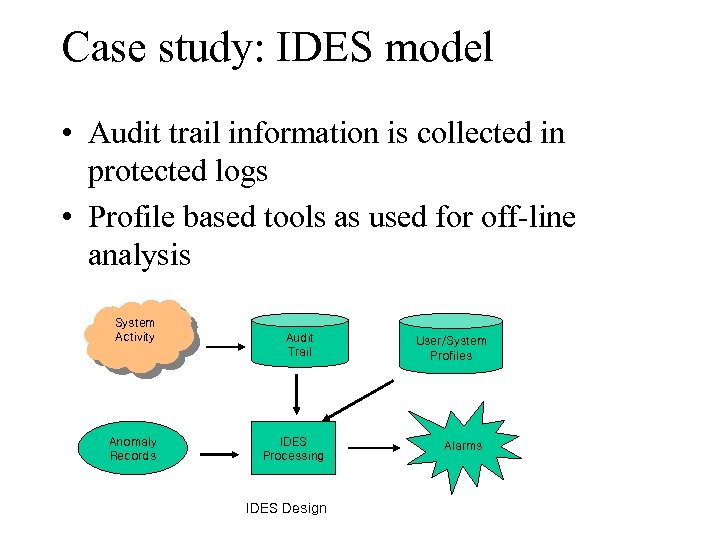 Case study: IDES model • Audit trail information is collected in protected logs • Profile based tools as used for off-line analysis System Activity Anomaly Records Audit Trail IDES Processing IDES Design User/System Profiles Alarms
Case study: IDES model • Audit trail information is collected in protected logs • Profile based tools as used for off-line analysis System Activity Anomaly Records Audit Trail IDES Processing IDES Design User/System Profiles Alarms
 Case study: IDES model (cont. )
Case study: IDES model (cont. )
 Case study: IDES model (cont. ) • Profile: Characterization of behavior • Audit records: the data structures used to capture the system’s observed behavior • Anomaly records: the data structures used to capture anomalous behavior • Alarms: problem reporting methods
Case study: IDES model (cont. ) • Profile: Characterization of behavior • Audit records: the data structures used to capture the system’s observed behavior • Anomaly records: the data structures used to capture anomalous behavior • Alarms: problem reporting methods
 Toll fraud and similar problems • How can toll fraud-like problems be solved using “Normal Behavior profiling? ” • How about credit card fraud? • Phone card fraud?
Toll fraud and similar problems • How can toll fraud-like problems be solved using “Normal Behavior profiling? ” • How about credit card fraud? • Phone card fraud?
 http: //www. atcomm. com/advisor/basics/call-account. htm • Boost Security – Highlight Suspicious Activity and Review Unrecognizable Call Data for Hacker Detection – Prevent/Locate Unauthorized System Access – Real Time Notification of Exception Calling – Track After Hours Security Guards – Detect Bomb Threats – Selective Reporting/Display for Top Secret/Sensitive Materials – Account for Calls But Delete Detail (Call Processing) – Password Security to Prevent Moving from Call Processing – Keyboard Macro Available to Provide Additional Security
http: //www. atcomm. com/advisor/basics/call-account. htm • Boost Security – Highlight Suspicious Activity and Review Unrecognizable Call Data for Hacker Detection – Prevent/Locate Unauthorized System Access – Real Time Notification of Exception Calling – Track After Hours Security Guards – Detect Bomb Threats – Selective Reporting/Display for Top Secret/Sensitive Materials – Account for Calls But Delete Detail (Call Processing) – Password Security to Prevent Moving from Call Processing – Keyboard Macro Available to Provide Additional Security
 The Abnormal Behavior (Attack) Signature Method • Commonly used in on-the-fly IDS • Attack signatures – May require temporal and state machine like modeling • Special character strings – E. g. : /etc/password in an ftp session
The Abnormal Behavior (Attack) Signature Method • Commonly used in on-the-fly IDS • Attack signatures – May require temporal and state machine like modeling • Special character strings – E. g. : /etc/password in an ftp session
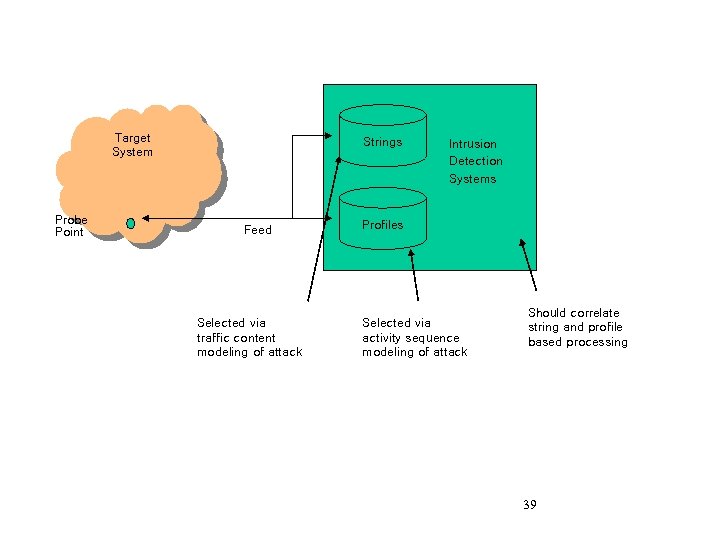 Target System Probe Point Strings Feed Selected via traffic content modeling of attack Intrusion Detection Systems Profiles Selected via activity sequence modeling of attack Should correlate string and profile based processing 39
Target System Probe Point Strings Feed Selected via traffic content modeling of attack Intrusion Detection Systems Profiles Selected via activity sequence modeling of attack Should correlate string and profile based processing 39
 Case Study: SNORT rules • http: //www. snort. org/docs/writing_rules/
Case Study: SNORT rules • http: //www. snort. org/docs/writing_rules/
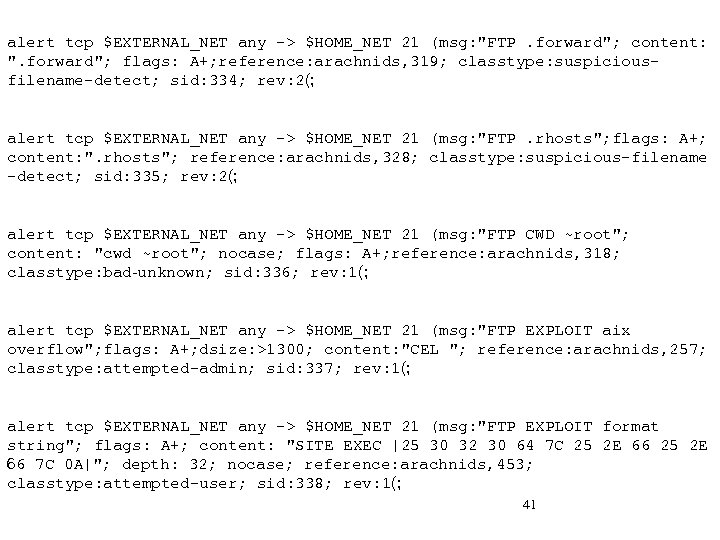 alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP. forward"; content: ". forward"; flags: A+; reference: arachnids, 319; classtype: suspiciousfilename-detect; sid: 334; rev: 2(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP. rhosts"; flags: A+; content: ". rhosts"; reference: arachnids, 328; classtype: suspicious-filename -detect; sid: 335; rev: 2(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP CWD ~root"; content: "cwd ~root"; nocase; flags: A+; reference: arachnids, 318; classtype: bad-unknown; sid: 336; rev: 1(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP EXPLOIT aix overflow"; flags: A+; dsize: >1300; content: "CEL "; reference: arachnids, 257; classtype: attempted-admin; sid: 337; rev: 1(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP EXPLOIT format string"; flags: A+; content: "SITE EXEC |25 30 32 30 64 7 C 25 2 E 66 7 C 0 A|"; depth: 32; nocase; reference: arachnids, 453; classtype: attempted-user; sid: 338; rev: 1(; 41
alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP. forward"; content: ". forward"; flags: A+; reference: arachnids, 319; classtype: suspiciousfilename-detect; sid: 334; rev: 2(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP. rhosts"; flags: A+; content: ". rhosts"; reference: arachnids, 328; classtype: suspicious-filename -detect; sid: 335; rev: 2(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP CWD ~root"; content: "cwd ~root"; nocase; flags: A+; reference: arachnids, 318; classtype: bad-unknown; sid: 336; rev: 1(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP EXPLOIT aix overflow"; flags: A+; dsize: >1300; content: "CEL "; reference: arachnids, 257; classtype: attempted-admin; sid: 337; rev: 1(; alert tcp $EXTERNAL_NET any -> $HOME_NET 21 (msg: "FTP EXPLOIT format string"; flags: A+; content: "SITE EXEC |25 30 32 30 64 7 C 25 2 E 66 7 C 0 A|"; depth: 32; nocase; reference: arachnids, 453; classtype: attempted-user; sid: 338; rev: 1(; 41
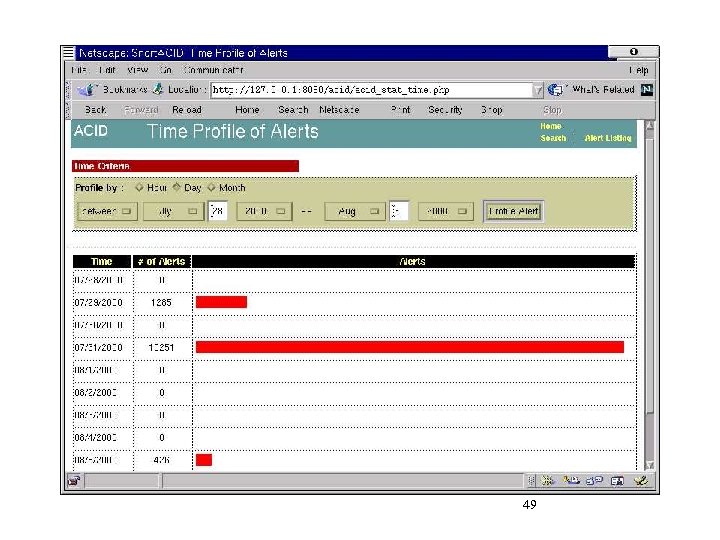
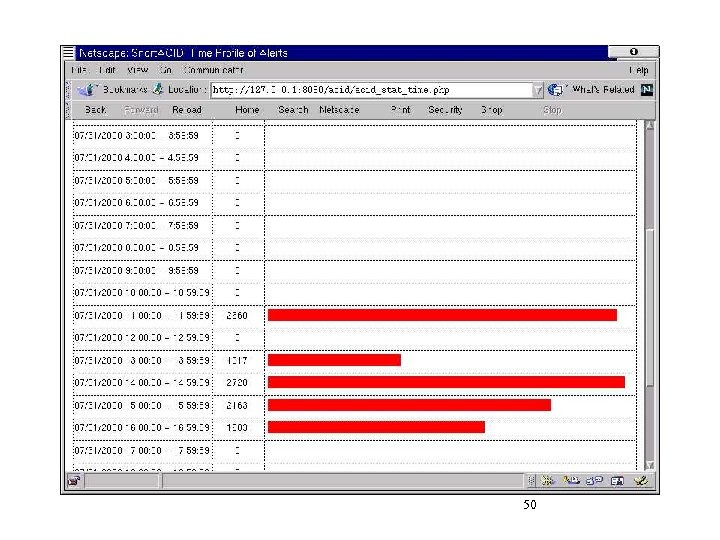
 Parameter pattern matching or anomaly discovery • Based on continuous monitoring of network and systems attributes • The monitoring is not necessary security focused • The use of day-to-day operational experience and the basis for detecting anomalies
Parameter pattern matching or anomaly discovery • Based on continuous monitoring of network and systems attributes • The monitoring is not necessary security focused • The use of day-to-day operational experience and the basis for detecting anomalies
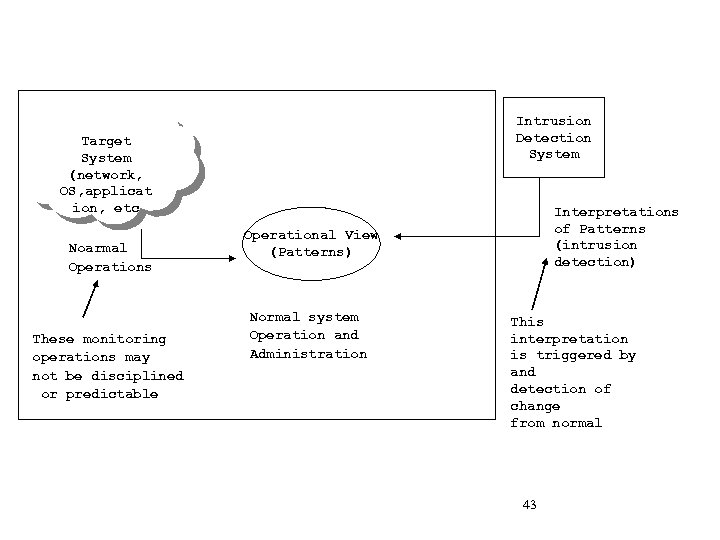 Intrusion Detection System Target System (network, OS, applicat ion, etc Noarmal Operations These monitoring operations may not be disciplined or predictable Interpretations of Patterns (intrusion detection) Operational View (Patterns) Normal system Operation and Administration This interpretation is triggered by and detection of change from normal 43
Intrusion Detection System Target System (network, OS, applicat ion, etc Noarmal Operations These monitoring operations may not be disciplined or predictable Interpretations of Patterns (intrusion detection) Operational View (Patterns) Normal system Operation and Administration This interpretation is triggered by and detection of change from normal 43
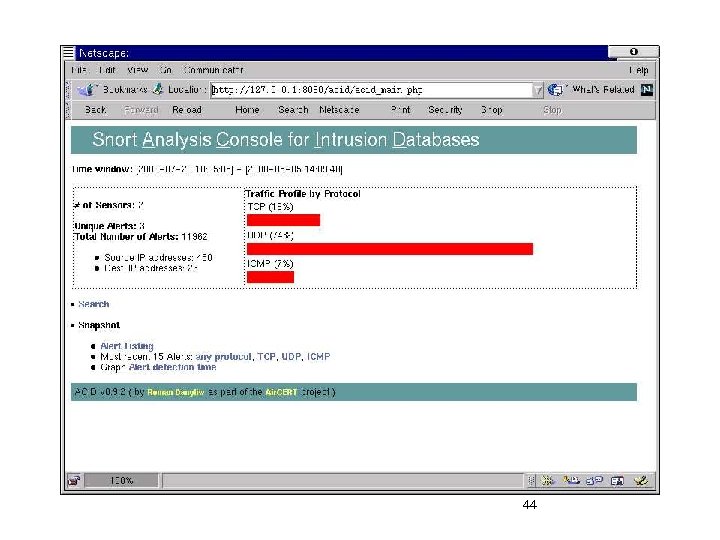 44
44
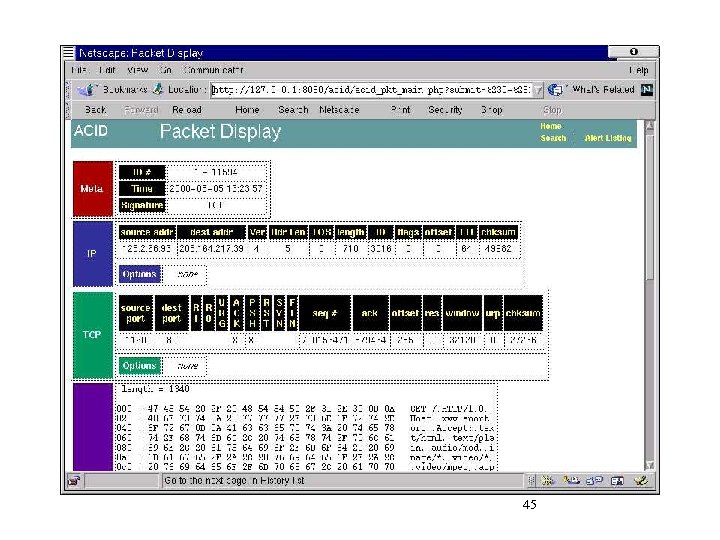 45
45
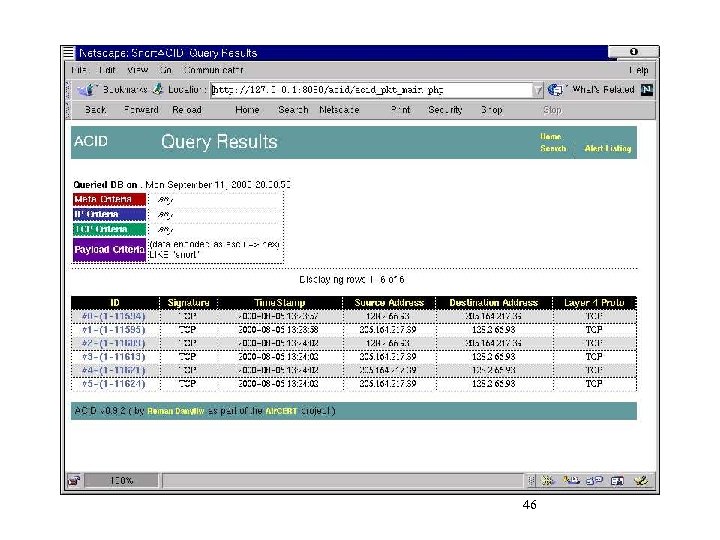 46
46
 47
47
 48
48
 49
49
 50
50
 recent criticism of intrusion detection method • • • on the fly traffic interpretation problem server audit interpretation problem fail-open nature of intrusion detection methods may be vulnerable to insertion attacks intrusion detection methods may be vulnerable to evasion attacks Intrusion detection methods may be vulnerable to denial of service attacks 51
recent criticism of intrusion detection method • • • on the fly traffic interpretation problem server audit interpretation problem fail-open nature of intrusion detection methods may be vulnerable to insertion attacks intrusion detection methods may be vulnerable to evasion attacks Intrusion detection methods may be vulnerable to denial of service attacks 51


