58c9647e08c701c98bebd9c98f13cac4.ppt
- Количество слайдов: 44
 Introductory Concepts Rudra Dutta CSC 401 - Fall 2011
Introductory Concepts Rudra Dutta CSC 401 - Fall 2011
 Digital Communication l Digital representation of information Reduces diverse information to same form – Allows infinite replication – Allows general purpose manipulation (computers) – Allows transmission from one computer to another – l Digital communication Revolution in our times – Created digital economy – Large number of products and services seen as information – Copyright Fall 2011, Rudra Dutta, NCSU 2
Digital Communication l Digital representation of information Reduces diverse information to same form – Allows infinite replication – Allows general purpose manipulation (computers) – Allows transmission from one computer to another – l Digital communication Revolution in our times – Created digital economy – Large number of products and services seen as information – Copyright Fall 2011, Rudra Dutta, NCSU 2
 Components for Communication Nodes (computers, …) l Links l Communication primitive l Copyright Fall 2011, Rudra Dutta, NCSU 3
Components for Communication Nodes (computers, …) l Links l Communication primitive l Copyright Fall 2011, Rudra Dutta, NCSU 3
 Scalability Copyright Fall 2011, Rudra Dutta, NCSU 4
Scalability Copyright Fall 2011, Rudra Dutta, NCSU 4
 Cooperation Nodes - endpoint nodes and intermediate nodes l Links l Communication primitive l Copyright Fall 2011, Rudra Dutta, NCSU 5
Cooperation Nodes - endpoint nodes and intermediate nodes l Links l Communication primitive l Copyright Fall 2011, Rudra Dutta, NCSU 5
 Forwarding l Performed by intermediate node – l Process of copying data off one incoming link, on some outgoing link May be performed at physical layer (Sub-bitpipe) – Utilize physical phenomena - “Switching” – Electrical circuit, etc. – l May be at higher layer Bits or some organization of bits – “Forwarding” – “Routing” (ambiguity) – Copyright Fall 2011, Rudra Dutta, NCSU 6
Forwarding l Performed by intermediate node – l Process of copying data off one incoming link, on some outgoing link May be performed at physical layer (Sub-bitpipe) – Utilize physical phenomena - “Switching” – Electrical circuit, etc. – l May be at higher layer Bits or some organization of bits – “Forwarding” – “Routing” (ambiguity) – Copyright Fall 2011, Rudra Dutta, NCSU 6
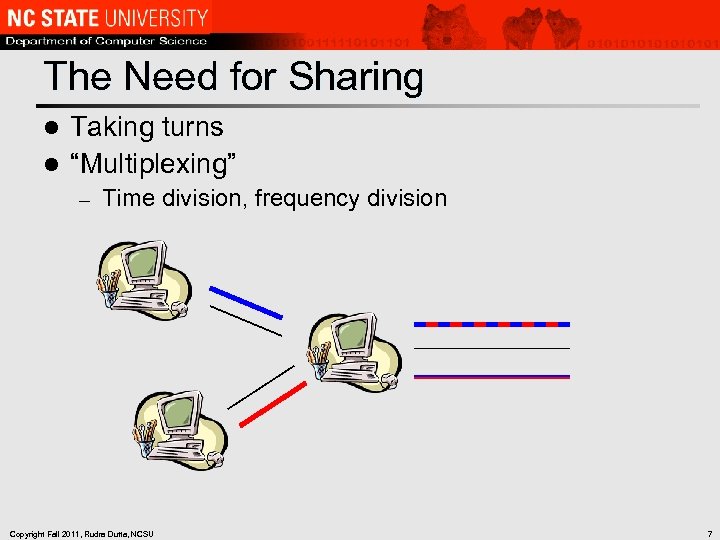 The Need for Sharing Taking turns l “Multiplexing” l – Time division, frequency division Copyright Fall 2011, Rudra Dutta, NCSU 7
The Need for Sharing Taking turns l “Multiplexing” l – Time division, frequency division Copyright Fall 2011, Rudra Dutta, NCSU 7
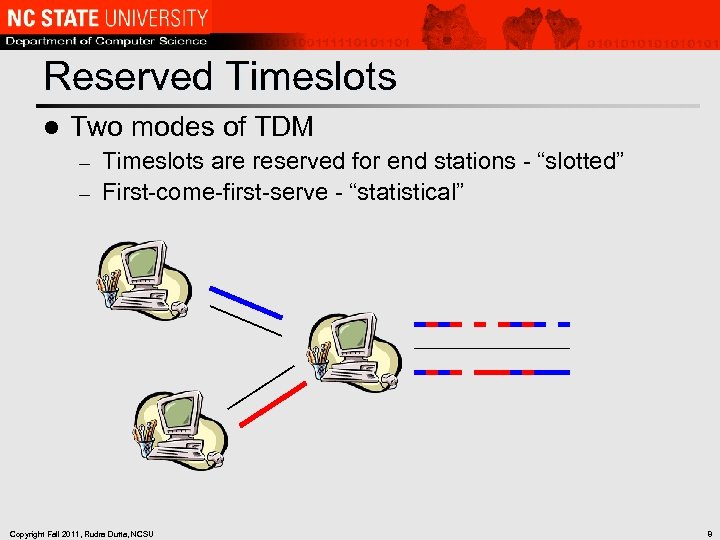 Reserved Timeslots l Two modes of TDM Timeslots are reserved for end stations - “slotted” – First-come-first-serve - “statistical” – Copyright Fall 2011, Rudra Dutta, NCSU 8
Reserved Timeslots l Two modes of TDM Timeslots are reserved for end stations - “slotted” – First-come-first-serve - “statistical” – Copyright Fall 2011, Rudra Dutta, NCSU 8
 Protocols On = “ 1” or “ 0” ? “Rule set”, “language” l Standards for communication hardware/software l Common guidelines for implementations l Different implementations of same protocol – Standards bodies make protocols – l – ITU-T, IETF, IEEE Software manufacturers produce implementations Copyright Fall 2011, Rudra Dutta, NCSU 9
Protocols On = “ 1” or “ 0” ? “Rule set”, “language” l Standards for communication hardware/software l Common guidelines for implementations l Different implementations of same protocol – Standards bodies make protocols – l – ITU-T, IETF, IEEE Software manufacturers produce implementations Copyright Fall 2011, Rudra Dutta, NCSU 9
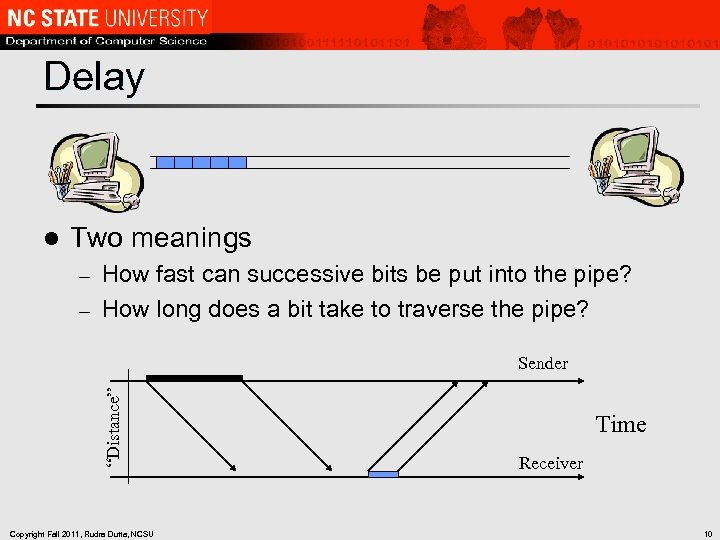 Delay l Two meanings How fast can successive bits be put into the pipe? – How long does a bit take to traverse the pipe? – “Distance” Sender Copyright Fall 2011, Rudra Dutta, NCSU Time Receiver 10
Delay l Two meanings How fast can successive bits be put into the pipe? – How long does a bit take to traverse the pipe? – “Distance” Sender Copyright Fall 2011, Rudra Dutta, NCSU Time Receiver 10
 Concept Problem l Imagine you have trained your St. Bernard, Bernie, to carry a box of three 8 mm tapes instead of a flask of brandy. (When your disk fills up, you consider that an emergency. ) These tapes each contain 7 gigabytes. The dog can travel to your side, wherever you may be, at 18 km/hour. (a) For what range of distances does Bernie have a higher data rate than a transmission line whose data rate (excluding overhead) is 150 Mbps? (b) We distinguished between two types of delay: – – – Propagation Delay: The time from when the first bit of the message is sent to when the first bit of the message is received. Often called simply delay. Transmission Delay: The time from when the first bit is sent (received) to when the last bit is sent (received). This can be considered as the ratio of the time taken to the number of bits in the message. Often the reciprocal of this ratio is considered very important, and is called bit rate, or throughput. In the problem in part (a) of this question, which of the above two quantities are you being asked to compare, or what combination of them? Copyright Fall 2011, Rudra Dutta, NCSU 11
Concept Problem l Imagine you have trained your St. Bernard, Bernie, to carry a box of three 8 mm tapes instead of a flask of brandy. (When your disk fills up, you consider that an emergency. ) These tapes each contain 7 gigabytes. The dog can travel to your side, wherever you may be, at 18 km/hour. (a) For what range of distances does Bernie have a higher data rate than a transmission line whose data rate (excluding overhead) is 150 Mbps? (b) We distinguished between two types of delay: – – – Propagation Delay: The time from when the first bit of the message is sent to when the first bit of the message is received. Often called simply delay. Transmission Delay: The time from when the first bit is sent (received) to when the last bit is sent (received). This can be considered as the ratio of the time taken to the number of bits in the message. Often the reciprocal of this ratio is considered very important, and is called bit rate, or throughput. In the problem in part (a) of this question, which of the above two quantities are you being asked to compare, or what combination of them? Copyright Fall 2011, Rudra Dutta, NCSU 11
 Throughput l Total number of bits transferred, over given time Related obviously to the transmission delay – Propagation delay often referred to simply as “delay” or “latency” – Throughput sometimes referred to as “bandwidth” – “Bandwidth-delay product” - filling the pipe – Copyright Fall 2011, Rudra Dutta, NCSU 12
Throughput l Total number of bits transferred, over given time Related obviously to the transmission delay – Propagation delay often referred to simply as “delay” or “latency” – Throughput sometimes referred to as “bandwidth” – “Bandwidth-delay product” - filling the pipe – Copyright Fall 2011, Rudra Dutta, NCSU 12
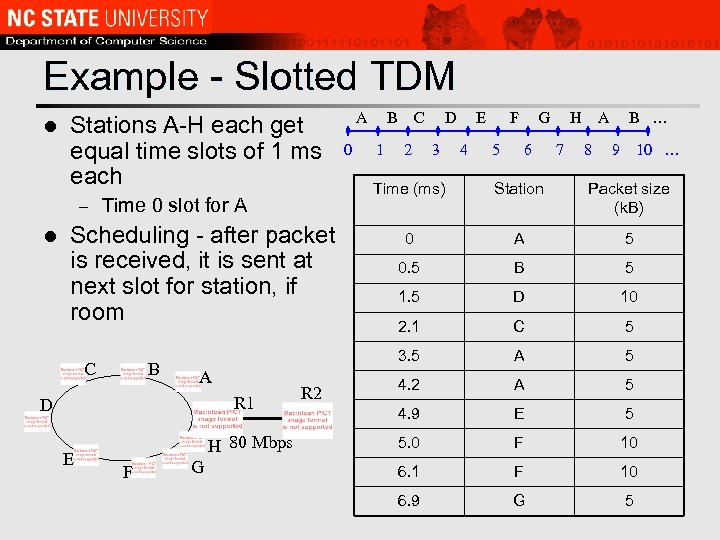 Example - Slotted TDM l Stations A-H each get equal time slots of 1 ms each – l Scheduling - after packet is received, it is sent at next slot for station, if room B A R 1 D E H 80 Mbps F 0 B C 1 2 D 3 E 4 F 5 G 6 H 7 A 8 B … 9 10 … G R 2 Time (ms) Station Packet size (k. B) 0 A 5 0. 5 B 5 1. 5 D 10 2. 1 C 5 3. 5 Time 0 slot for A C A A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
Example - Slotted TDM l Stations A-H each get equal time slots of 1 ms each – l Scheduling - after packet is received, it is sent at next slot for station, if room B A R 1 D E H 80 Mbps F 0 B C 1 2 D 3 E 4 F 5 G 6 H 7 A 8 B … 9 10 … G R 2 Time (ms) Station Packet size (k. B) 0 A 5 0. 5 B 5 1. 5 D 10 2. 1 C 5 3. 5 Time 0 slot for A C A A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
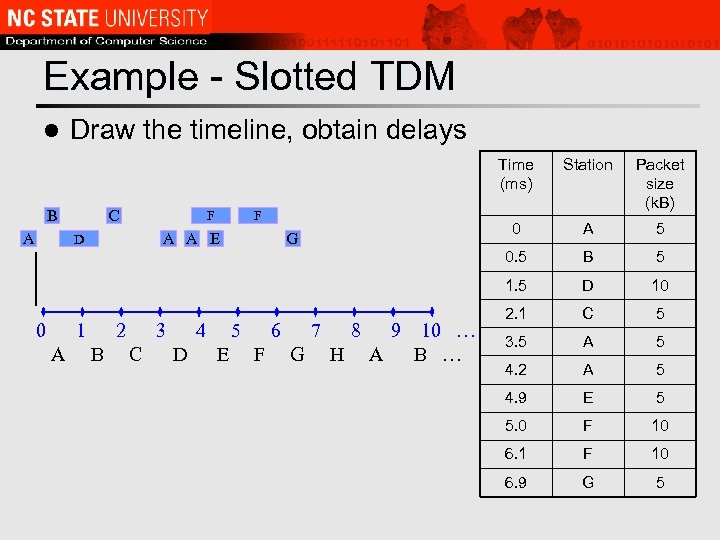 Example - Slotted TDM l Draw the timeline, obtain delays Time (ms) F 0 1 A F A A E D 2 B 3 C 4 D 0 G 5 E 6 F 7 G 8 H 9 A 10 … B … A 5 B 5 1. 5 A C Packet size (k. B) 0. 5 B Station D 10 2. 1 C 5 3. 5 A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
Example - Slotted TDM l Draw the timeline, obtain delays Time (ms) F 0 1 A F A A E D 2 B 3 C 4 D 0 G 5 E 6 F 7 G 8 H 9 A 10 … B … A 5 B 5 1. 5 A C Packet size (k. B) 0. 5 B Station D 10 2. 1 C 5 3. 5 A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
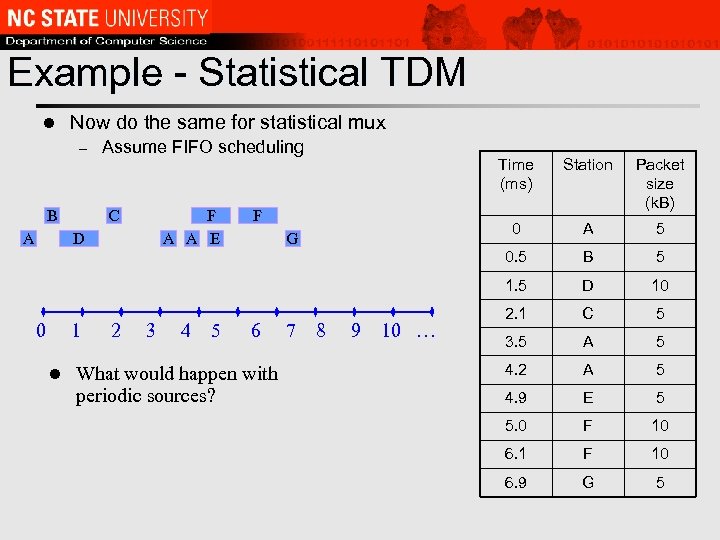 Example - Statistical TDM l Now do the same for statistical mux – Assume FIFO scheduling F A A E D 0 1 l 2 3 4 5 0 F G 6 What would happen with periodic sources? 7 8 9 10 … Packet size (k. B) A 5 B 5 1. 5 A C Station 0. 5 B Time (ms) D 10 2. 1 C 5 3. 5 A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
Example - Statistical TDM l Now do the same for statistical mux – Assume FIFO scheduling F A A E D 0 1 l 2 3 4 5 0 F G 6 What would happen with periodic sources? 7 8 9 10 … Packet size (k. B) A 5 B 5 1. 5 A C Station 0. 5 B Time (ms) D 10 2. 1 C 5 3. 5 A 5 4. 2 A 5 4. 9 E 5 5. 0 F 10 6. 1 F 10 6. 9 G 5
 Software Protocols Syntax of a message – what fields does it contain? – in what format? l Semantics of a message – what does a message mean? – for example, not-OK message means receiver got a corrupted file l Actions to take on receipt of a message – for example, on receiving not-OK message, retransmit the entire file l Copyright Fall 2011, Rudra Dutta, NCSU 16
Software Protocols Syntax of a message – what fields does it contain? – in what format? l Semantics of a message – what does a message mean? – for example, not-OK message means receiver got a corrupted file l Actions to take on receipt of a message – for example, on receiving not-OK message, retransmit the entire file l Copyright Fall 2011, Rudra Dutta, NCSU 16
 Service view of protocol A protocol is a software module providing a service l ftp provides reliable file transfer service l Peer entities use a protocol to provide a service to a higher-level peer entity l – l for example, postal workers use a protocol to present customers with the abstraction unreliable letter transfer service Service interaction between modules constrained to very specific pattern layering Copyright Fall 2011, Rudra Dutta, NCSU 17
Service view of protocol A protocol is a software module providing a service l ftp provides reliable file transfer service l Peer entities use a protocol to provide a service to a higher-level peer entity l – l for example, postal workers use a protocol to present customers with the abstraction unreliable letter transfer service Service interaction between modules constrained to very specific pattern layering Copyright Fall 2011, Rudra Dutta, NCSU 17
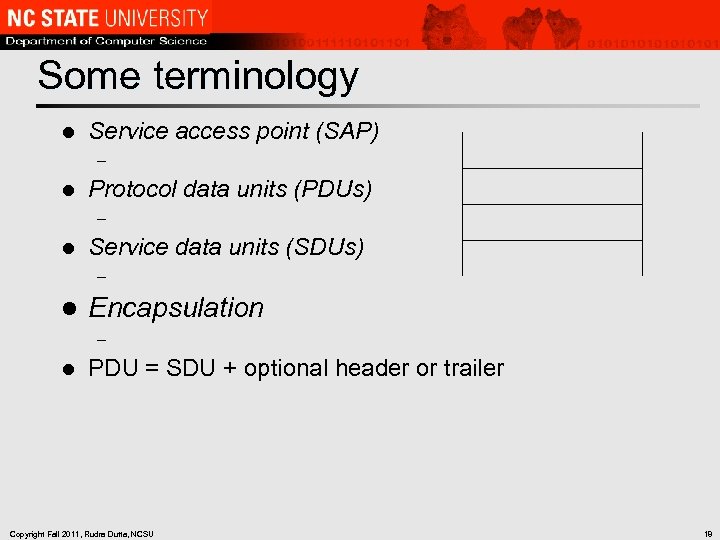 Some terminology l Service access point (SAP) – l Protocol data units (PDUs) – l Service data units (SDUs) – l Encapsulation – l PDU = SDU + optional header or trailer Copyright Fall 2011, Rudra Dutta, NCSU 18
Some terminology l Service access point (SAP) – l Protocol data units (PDUs) – l Service data units (SDUs) – l Encapsulation – l PDU = SDU + optional header or trailer Copyright Fall 2011, Rudra Dutta, NCSU 18
 The importance of being layered Breaks up a complex problem into smaller manageable pieces – can compose simple service to provide complex ones – for example, WWW (HTTP) is Java layered over TCP over IP (and uses DNS, ARP, DHCP, RIP, OSPF, BGP, PPP, ICMP) l Abstraction (hiding) of implementation details – separation of implementation and specification – can change implementation as long as service interface is maintained l Can reuse functionality l Copyright Fall 2011, Rudra Dutta, NCSU 19
The importance of being layered Breaks up a complex problem into smaller manageable pieces – can compose simple service to provide complex ones – for example, WWW (HTTP) is Java layered over TCP over IP (and uses DNS, ARP, DHCP, RIP, OSPF, BGP, PPP, ICMP) l Abstraction (hiding) of implementation details – separation of implementation and specification – can change implementation as long as service interface is maintained l Can reuse functionality l Copyright Fall 2011, Rudra Dutta, NCSU 19
 ISO OSI reference model A set of protocols is open if – protocol details are publicly available – changes are managed by an organization whose membership and transactions are open to the public l A system that implements open protocols is called an open system l International Organization for Standards (ISO) prescribes a standard to connect open systems – open system interconnect (OSI) l Has greatly influenced thinking on protocol stacks l Copyright Fall 2011, Rudra Dutta, NCSU 20
ISO OSI reference model A set of protocols is open if – protocol details are publicly available – changes are managed by an organization whose membership and transactions are open to the public l A system that implements open protocols is called an open system l International Organization for Standards (ISO) prescribes a standard to connect open systems – open system interconnect (OSI) l Has greatly influenced thinking on protocol stacks l Copyright Fall 2011, Rudra Dutta, NCSU 20
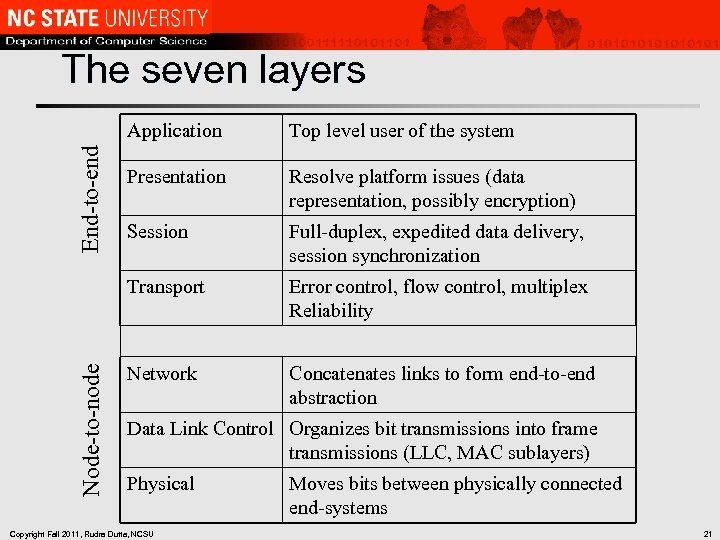 The seven layers Node-to-node Top level user of the system Presentation Resolve platform issues (data representation, possibly encryption) Session Full-duplex, expedited data delivery, session synchronization Transport End-to-end Application Error control, flow control, multiplex Reliability Network Concatenates links to form end-to-end abstraction Data Link Control Organizes bit transmissions into frame transmissions (LLC, MAC sublayers) Physical Copyright Fall 2011, Rudra Dutta, NCSU Moves bits between physically connected end-systems 21
The seven layers Node-to-node Top level user of the system Presentation Resolve platform issues (data representation, possibly encryption) Session Full-duplex, expedited data delivery, session synchronization Transport End-to-end Application Error control, flow control, multiplex Reliability Network Concatenates links to form end-to-end abstraction Data Link Control Organizes bit transmissions into frame transmissions (LLC, MAC sublayers) Physical Copyright Fall 2011, Rudra Dutta, NCSU Moves bits between physically connected end-systems 21
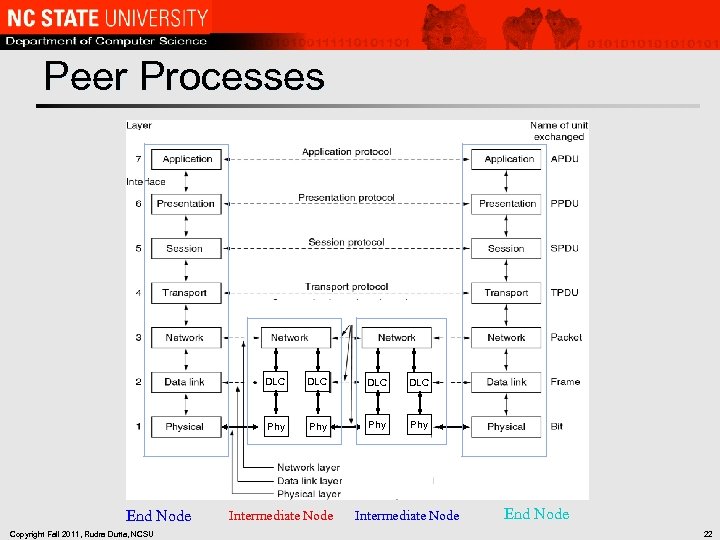 Peer Processes DLC Copyright Fall 2011, Rudra Dutta, NCSU DLC Phy End Node DLC Phy Phy Intermediate Node End Node 22
Peer Processes DLC Copyright Fall 2011, Rudra Dutta, NCSU DLC Phy End Node DLC Phy Phy Intermediate Node End Node 22
 Network Components Different network components function at different layers l Embody service at different protocol layers l Nomenclature is not very well standardized, and is changing l Mixed, “layer-blurring” devices complicate matters l Copyright Fall 2011, Rudra Dutta, NCSU 23
Network Components Different network components function at different layers l Embody service at different protocol layers l Nomenclature is not very well standardized, and is changing l Mixed, “layer-blurring” devices complicate matters l Copyright Fall 2011, Rudra Dutta, NCSU 23
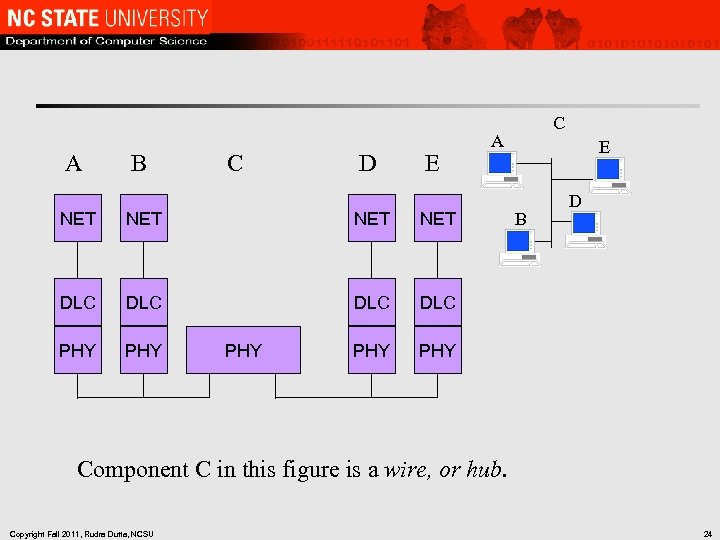 A B C D E NET NET DLC PHY E D DLC PHY A NET DLC C PHY B Component C in this figure is a wire, or hub. Copyright Fall 2011, Rudra Dutta, NCSU 24
A B C D E NET NET DLC PHY E D DLC PHY A NET DLC C PHY B Component C in this figure is a wire, or hub. Copyright Fall 2011, Rudra Dutta, NCSU 24
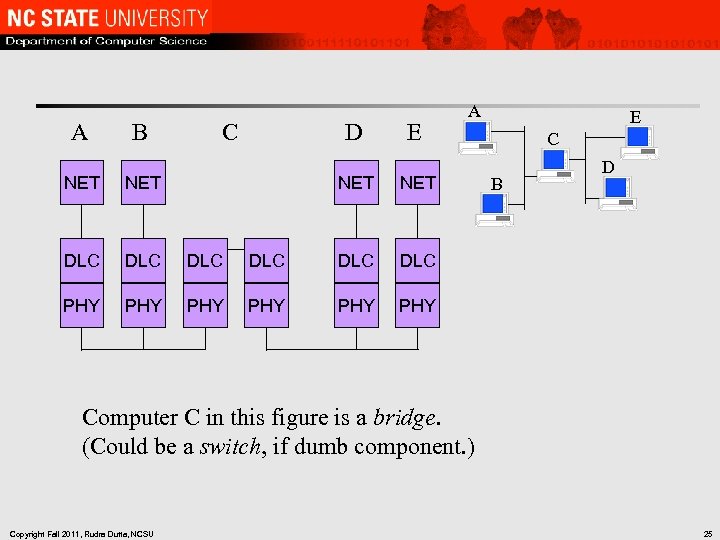 A B C NET DLC DLC PHY PHY D E NET DLC PHY E C D DLC PHY A PHY B Computer C in this figure is a bridge. (Could be a switch, if dumb component. ) Copyright Fall 2011, Rudra Dutta, NCSU 25
A B C NET DLC DLC PHY PHY D E NET DLC PHY E C D DLC PHY A PHY B Computer C in this figure is a bridge. (Could be a switch, if dumb component. ) Copyright Fall 2011, Rudra Dutta, NCSU 25
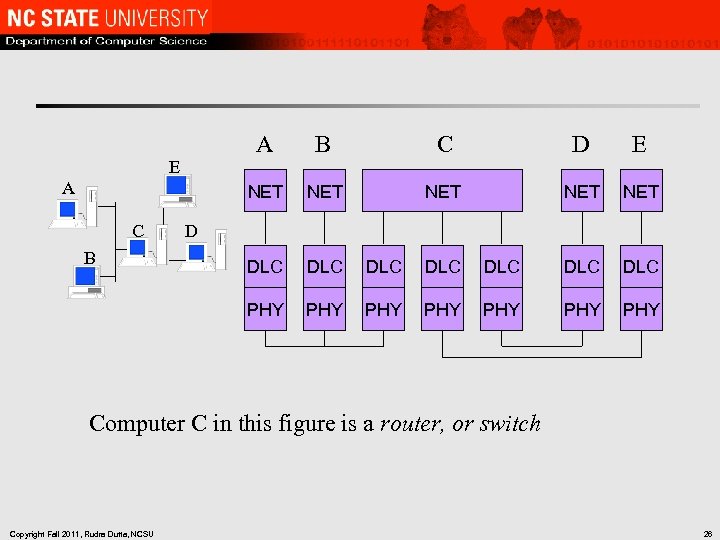 A C B D E NET NET DLC DLC PHY A C NET E B PHY PHY PHY D Computer C in this figure is a router, or switch Copyright Fall 2011, Rudra Dutta, NCSU 26
A C B D E NET NET DLC DLC PHY A C NET E B PHY PHY PHY D Computer C in this figure is a router, or switch Copyright Fall 2011, Rudra Dutta, NCSU 26
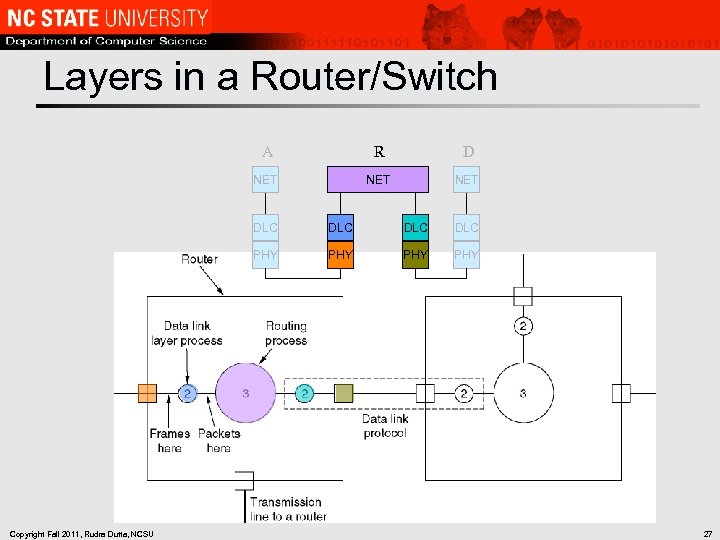 Layers in a Router/Switch A R D NET NET DLC DLC PHY Copyright Fall 2011, Rudra Dutta, NCSU DLC PHY PHY 27
Layers in a Router/Switch A R D NET NET DLC DLC PHY Copyright Fall 2011, Rudra Dutta, NCSU DLC PHY PHY 27
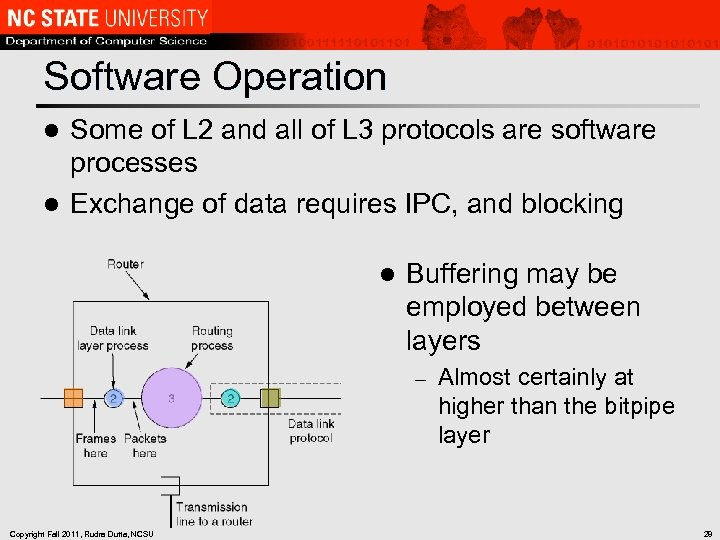 Software Operation Some of L 2 and all of L 3 protocols are software processes l Exchange of data requires IPC, and blocking l l Buffering may be employed between layers – Copyright Fall 2011, Rudra Dutta, NCSU Almost certainly at higher than the bitpipe layer 28
Software Operation Some of L 2 and all of L 3 protocols are software processes l Exchange of data requires IPC, and blocking l l Buffering may be employed between layers – Copyright Fall 2011, Rudra Dutta, NCSU Almost certainly at higher than the bitpipe layer 28
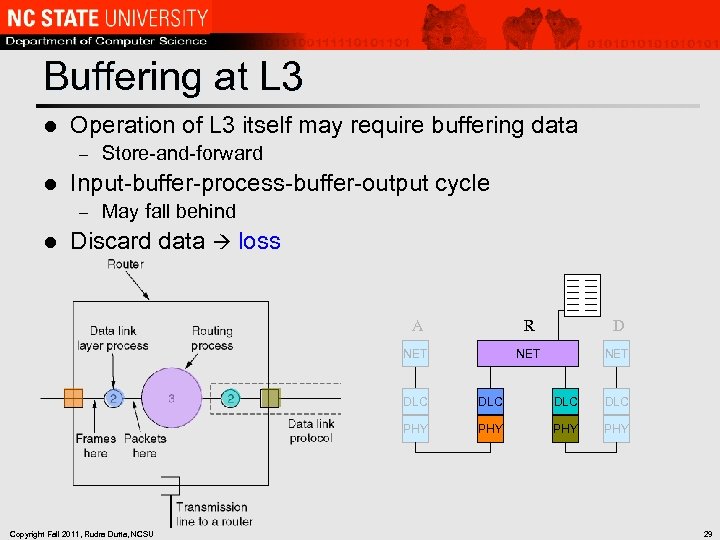 Buffering at L 3 l Operation of L 3 itself may require buffering data – l Input-buffer-process-buffer-output cycle – l Store-and-forward May fall behind Discard data loss A R D NET NET DLC DLC PHY Copyright Fall 2011, Rudra Dutta, NCSU DLC PHY PHY 29
Buffering at L 3 l Operation of L 3 itself may require buffering data – l Input-buffer-process-buffer-output cycle – l Store-and-forward May fall behind Discard data loss A R D NET NET DLC DLC PHY Copyright Fall 2011, Rudra Dutta, NCSU DLC PHY PHY 29
 Layering l We have broken a complex problem into smaller, simpler pieces Provides the application with sophisticated services – Each layer provides a clean abstraction to the layer above – l HOWEVER - sacrifices efficiency Might even sacrifice functionality, or optimality – Recently, cross-layer approaches have started gaining ground – l Example - power-aware routing in ad-hoc networks Copyright Fall 2011, Rudra Dutta, NCSU 30
Layering l We have broken a complex problem into smaller, simpler pieces Provides the application with sophisticated services – Each layer provides a clean abstraction to the layer above – l HOWEVER - sacrifices efficiency Might even sacrifice functionality, or optimality – Recently, cross-layer approaches have started gaining ground – l Example - power-aware routing in ad-hoc networks Copyright Fall 2011, Rudra Dutta, NCSU 30
 Layer Overhead l l Suppose that a certain communications protocol stack involves an overhead on the application layer PDU of 100 bytes for headers and framing. We send 1 million bytes of data using this application and this protocol stack; however, exactly one data byte is corrupted during transmission, and the packet containing it is thus lost and must be retransmitted. What is the total number of overhead + loss bytes retransmitted, for packet data sizes (not including overhead) of 100, 500, 1000, and 2000 bytes? Copyright Fall 2011, Rudra Dutta, NCSU 31
Layer Overhead l l Suppose that a certain communications protocol stack involves an overhead on the application layer PDU of 100 bytes for headers and framing. We send 1 million bytes of data using this application and this protocol stack; however, exactly one data byte is corrupted during transmission, and the packet containing it is thus lost and must be retransmitted. What is the total number of overhead + loss bytes retransmitted, for packet data sizes (not including overhead) of 100, 500, 1000, and 2000 bytes? Copyright Fall 2011, Rudra Dutta, NCSU 31
 Network Performance l Ultimately, measured in quantities the end-user cares about Delay, throughput – Other metrics derived from these – l More sophisticated metrics Predictability / Reliability / Survivability – Variability of delay or throughput – Guarantees - Quality of Service contracts – Security – Copyright Fall 2011, Rudra Dutta, NCSU 32
Network Performance l Ultimately, measured in quantities the end-user cares about Delay, throughput – Other metrics derived from these – l More sophisticated metrics Predictability / Reliability / Survivability – Variability of delay or throughput – Guarantees - Quality of Service contracts – Security – Copyright Fall 2011, Rudra Dutta, NCSU 32
 Traffic Characterization l Traffic - that which is carried by network Generated and consumed by end-nodes – “Demand” for networking services: b/w and switching – l Magnitude (bandwidth) – l Lifetime – l Could vary with time, if “reasonably long” life How long it is resident in the network Arrival and departure patterns Call (like telephony) arrival and departure – Increment and decrement – Periodic (scheduled) – Static (long-term) – l Requirement of performance – Hard or statistical Copyright Fall 2011, Rudra Dutta, NCSU 33
Traffic Characterization l Traffic - that which is carried by network Generated and consumed by end-nodes – “Demand” for networking services: b/w and switching – l Magnitude (bandwidth) – l Lifetime – l Could vary with time, if “reasonably long” life How long it is resident in the network Arrival and departure patterns Call (like telephony) arrival and departure – Increment and decrement – Periodic (scheduled) – Static (long-term) – l Requirement of performance – Hard or statistical Copyright Fall 2011, Rudra Dutta, NCSU 33
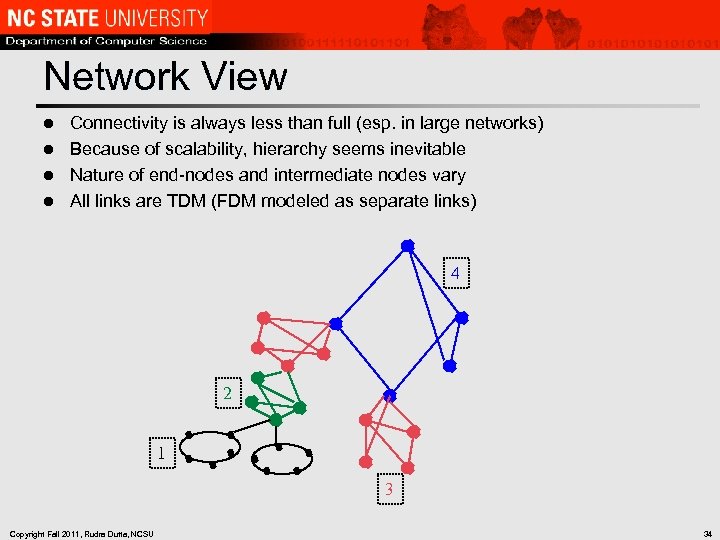 Network View Connectivity is always less than full (esp. in large networks) l Because of scalability, hierarchy seems inevitable l Nature of end-nodes and intermediate nodes vary l All links are TDM (FDM modeled as separate links) l 4 2 1 3 Copyright Fall 2011, Rudra Dutta, NCSU 34
Network View Connectivity is always less than full (esp. in large networks) l Because of scalability, hierarchy seems inevitable l Nature of end-nodes and intermediate nodes vary l All links are TDM (FDM modeled as separate links) l 4 2 1 3 Copyright Fall 2011, Rudra Dutta, NCSU 34
 Traffic Aggregation - Static Traffic Consider lowest level networks l Assume each station injects traffic steadily l – l Due to aggregation, magnitude increases as traffic climbs hierarchy – l Number of bits injected per time unit is constant for each source But constant nature of traffic remains Aggregation/dis-aggregation process is straightforward for intermediate nodes – Effectively same as slotted TDM Therefore static traffic is stable - remains static at higher levels of hierarchy l Magnitude and therefore capacity, of course, must increase at higher levels l Copyright Fall 2011, Rudra Dutta, NCSU 35
Traffic Aggregation - Static Traffic Consider lowest level networks l Assume each station injects traffic steadily l – l Due to aggregation, magnitude increases as traffic climbs hierarchy – l Number of bits injected per time unit is constant for each source But constant nature of traffic remains Aggregation/dis-aggregation process is straightforward for intermediate nodes – Effectively same as slotted TDM Therefore static traffic is stable - remains static at higher levels of hierarchy l Magnitude and therefore capacity, of course, must increase at higher levels l Copyright Fall 2011, Rudra Dutta, NCSU 35
 Bursty Traffic l Traffic is generated intermittently at each end node – l Assume (peak) rates are known Question of capacity and aggregation become intertwined – One approach: pretend each end node is a steady source at its peak rate, then provision as before l – Aggregation will be easy Another approach: provision for average Do bursts arrive deterministically? l Sometimes link will be busy when traffic arrives to use it l Must store-and-forward, or discard l Question of slotting TDM comes in - work conservation l Copyright Fall 2011, Rudra Dutta, NCSU 36
Bursty Traffic l Traffic is generated intermittently at each end node – l Assume (peak) rates are known Question of capacity and aggregation become intertwined – One approach: pretend each end node is a steady source at its peak rate, then provision as before l – Aggregation will be easy Another approach: provision for average Do bursts arrive deterministically? l Sometimes link will be busy when traffic arrives to use it l Must store-and-forward, or discard l Question of slotting TDM comes in - work conservation l Copyright Fall 2011, Rudra Dutta, NCSU 36
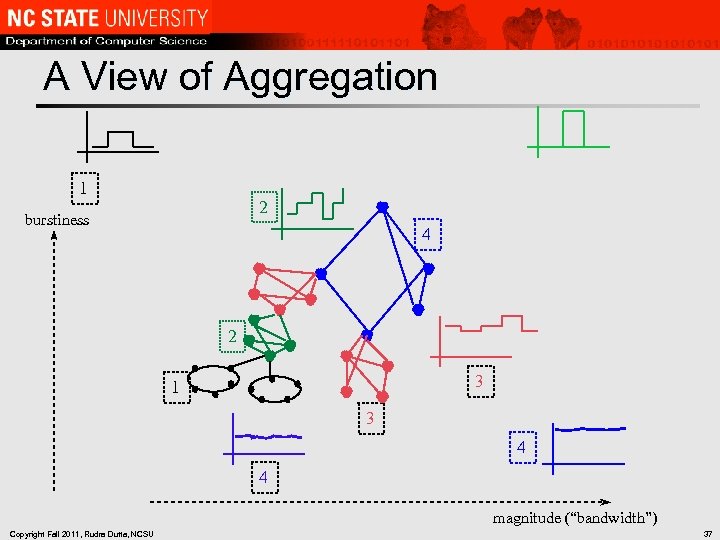 A View of Aggregation 1 2 burstiness 4 2 3 1 3 4 4 magnitude (“bandwidth”) Copyright Fall 2011, Rudra Dutta, NCSU 37
A View of Aggregation 1 2 burstiness 4 2 3 1 3 4 4 magnitude (“bandwidth”) Copyright Fall 2011, Rudra Dutta, NCSU 37
 Static Traffic in Real Networks Aggregation can tend to cancel out bursts l Finite capacity of pipe will appear as static-ness of traffic to next level of aggregation l – Also: Concept of “elastic traffic” Source-to-destination traffic flows in the Internet are not static as generated, but congestion slows down bursts l In response, flow duration will increase l l Empirical observation tends to confirm For example, CAIDA data – Exhibits “busy hour” traffic patterns – l Changes from hour to hour, but each pattern stable over days and weeks Copyright Fall 2011, Rudra Dutta, NCSU 38
Static Traffic in Real Networks Aggregation can tend to cancel out bursts l Finite capacity of pipe will appear as static-ness of traffic to next level of aggregation l – Also: Concept of “elastic traffic” Source-to-destination traffic flows in the Internet are not static as generated, but congestion slows down bursts l In response, flow duration will increase l l Empirical observation tends to confirm For example, CAIDA data – Exhibits “busy hour” traffic patterns – l Changes from hour to hour, but each pattern stable over days and weeks Copyright Fall 2011, Rudra Dutta, NCSU 38
 About Loss l Loss may occur on the link Usually very little in guided medium - ignore – Usually handled by L 2 transmissions or ignored – l Loss may occur at intermediate nodes Store-and-forward buffers are finite - may overflow – Other mechanism at intermediate node may discard – l Does retransmission occur? May not be required / desired – If desired, – May be at L 2, on link l May be at L 4, E 2 E l Copyright Fall 2011, Rudra Dutta, NCSU 39
About Loss l Loss may occur on the link Usually very little in guided medium - ignore – Usually handled by L 2 transmissions or ignored – l Loss may occur at intermediate nodes Store-and-forward buffers are finite - may overflow – Other mechanism at intermediate node may discard – l Does retransmission occur? May not be required / desired – If desired, – May be at L 2, on link l May be at L 4, E 2 E l Copyright Fall 2011, Rudra Dutta, NCSU 39
 Providing Guarantees - About Delay l Controversial proposition: “If delay is not important, capacity is not important” – “If delay is important, capacity must be large OR aggregation must be slotted OR both” – l Links must Provide connectivity – Have capacity to carry traffic – Routers must have memory and processor capacity to switch traffic l Network design / resource provisioning problem l Copyright Fall 2011, Rudra Dutta, NCSU 40
Providing Guarantees - About Delay l Controversial proposition: “If delay is not important, capacity is not important” – “If delay is important, capacity must be large OR aggregation must be slotted OR both” – l Links must Provide connectivity – Have capacity to carry traffic – Routers must have memory and processor capacity to switch traffic l Network design / resource provisioning problem l Copyright Fall 2011, Rudra Dutta, NCSU 40
 Two Modes of Networking Traffic Networks and Transport Networks l Traffic networks: where stochastic demand picture is operative l Short term switching/routing – Design for connectivity – l Transport networks: where traffic demands of static magnitude are seen to be operative (Semi-) Permanent – Qo. S considerations paramount – Demands seen to be injected at transport network nodes, lower level networks not visible – Design for connectivity and capacity – Copyright Fall 2011, Rudra Dutta, NCSU 41
Two Modes of Networking Traffic Networks and Transport Networks l Traffic networks: where stochastic demand picture is operative l Short term switching/routing – Design for connectivity – l Transport networks: where traffic demands of static magnitude are seen to be operative (Semi-) Permanent – Qo. S considerations paramount – Demands seen to be injected at transport network nodes, lower level networks not visible – Design for connectivity and capacity – Copyright Fall 2011, Rudra Dutta, NCSU 41
 Network Design l Static traffic / slotted TDM aggregation Small, constant delay should result – Performance metric is global – demands satisfied, global delay – l Bursty traffic / statistical TDM Larger range of delay, but statistically smaller – Design for statistical delay, or simply connectivity – l Circuits – canonical telephony Very small and constant delay – Operative performance metric is blocking ratio – Copyright Fall 2011, Rudra Dutta, NCSU 42
Network Design l Static traffic / slotted TDM aggregation Small, constant delay should result – Performance metric is global – demands satisfied, global delay – l Bursty traffic / statistical TDM Larger range of delay, but statistically smaller – Design for statistical delay, or simply connectivity – l Circuits – canonical telephony Very small and constant delay – Operative performance metric is blocking ratio – Copyright Fall 2011, Rudra Dutta, NCSU 42
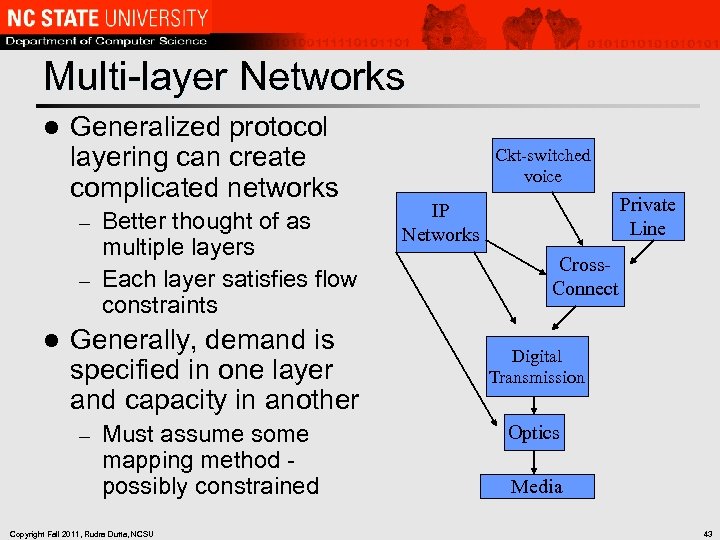 Multi-layer Networks l Generalized protocol layering can create complicated networks Better thought of as multiple layers – Each layer satisfies flow constraints – l Generally, demand is specified in one layer and capacity in another – Must assume some mapping method possibly constrained Copyright Fall 2011, Rudra Dutta, NCSU Ckt-switched voice Private Line IP Networks Cross. Connect Digital Transmission Optics Media 43
Multi-layer Networks l Generalized protocol layering can create complicated networks Better thought of as multiple layers – Each layer satisfies flow constraints – l Generally, demand is specified in one layer and capacity in another – Must assume some mapping method possibly constrained Copyright Fall 2011, Rudra Dutta, NCSU Ckt-switched voice Private Line IP Networks Cross. Connect Digital Transmission Optics Media 43
 Review l l l l Networks have varied and extensive current and future uses Computers communicate digital information over physical media / links Network components perform cooperative effort Protocols enable communication, arranged in layers Holistic concepts such as connection-orientation, circuit-switching, emerge Traffic is “demand” for network Resource provisioning + protocols and policies produce measurable performance metrics experienced by traffic demand Copyright Fall 2011, Rudra Dutta, NCSU 44
Review l l l l Networks have varied and extensive current and future uses Computers communicate digital information over physical media / links Network components perform cooperative effort Protocols enable communication, arranged in layers Holistic concepts such as connection-orientation, circuit-switching, emerge Traffic is “demand” for network Resource provisioning + protocols and policies produce measurable performance metrics experienced by traffic demand Copyright Fall 2011, Rudra Dutta, NCSU 44


