websec-training-authentication.pptx
- Количество слайдов: 59
Introduction to Web Security. Part I: Authentication

Introduction • Alexander Berezhnoy • Application Security Analyst • w 3 af project contributor • OSCP • alexander. berezhnoy@gmail. com

Agenda • Scope and concepts • Web authentication threats • Countermeasures • Threat modeling process • Types of authentication

Scope and Concepts
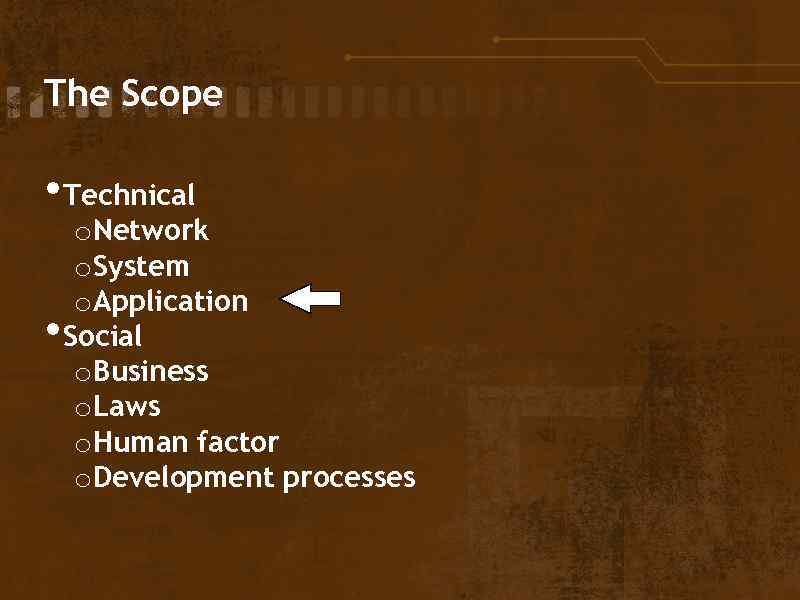
The Scope • Technical • o. Network o. System o. Application Social o. Business o. Laws o. Human factor o. Development processes

Technical Areas • Security Features • • • o. Access Control § Authentication § Authorization o. Data protection Secure Logic Time & State Data Handling • Design Practices • Error Handling

Glossary • Threat: a goal that an adversary may pursue • Vulnerability: a weakness which is ready to use • Weakness: a (potential) security flaw • Attack: a method which can be used by an adversary

Starting the Assessment

Phases of Access Control • Identification o. Who are you? • Authentication o. Prove it! • Authorization o. Here is what you are allowed to do.

Glossary: Authentication • Authentication: a process of determining if a user is who is he claims to be Password-based authentication is being considered.

Threat Modeling • Determine the high-level threats • Decompose the system • Determine the relevant entities • Repeat the same for each entity • Update the requirements or test cases

UC 1: Authentication

Authentication

Threats • Wrong man is recognized as a good one o. Correct credentials are entered o. Vulnerability in application is used

Threats • Wrong man is recognized as a good one o. Correct credentials are entered § They are stolen § They are guessed § They are tampered with o. Vulnerability in application is used

Password is stolen: how?

What can help phishers • User's bad habits • • • o. Massive emails from you o. Asking for secret details o. Unclear or hidden address bar Frames Pop-ups Unvalidated redirects HTML Injection and XSS Images hotlinking o. Cross-site authentication attacks
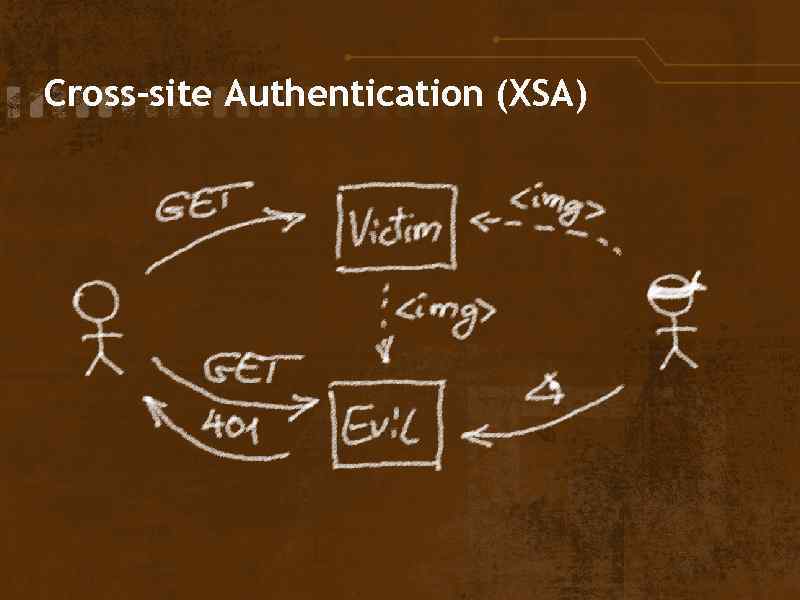
Cross-site Authentication (XSA)
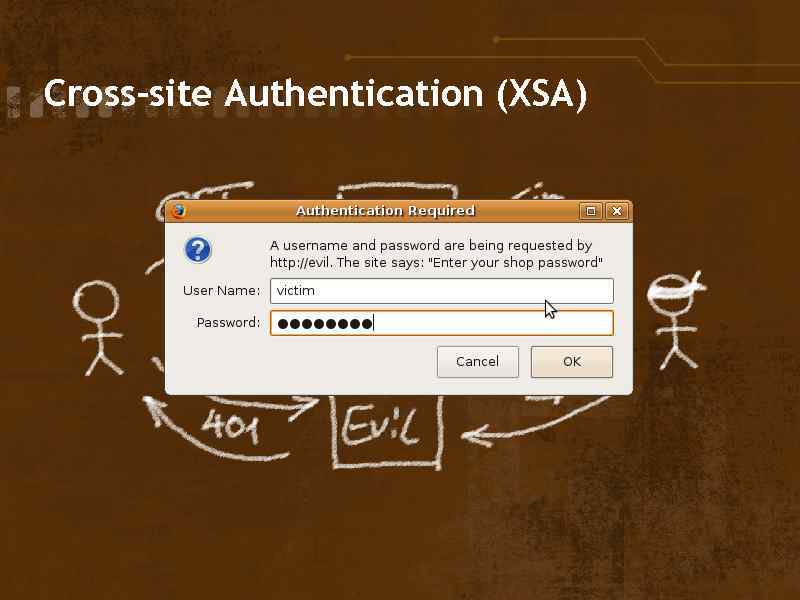
Cross-site Authentication (XSA)

Password is stolen: how?
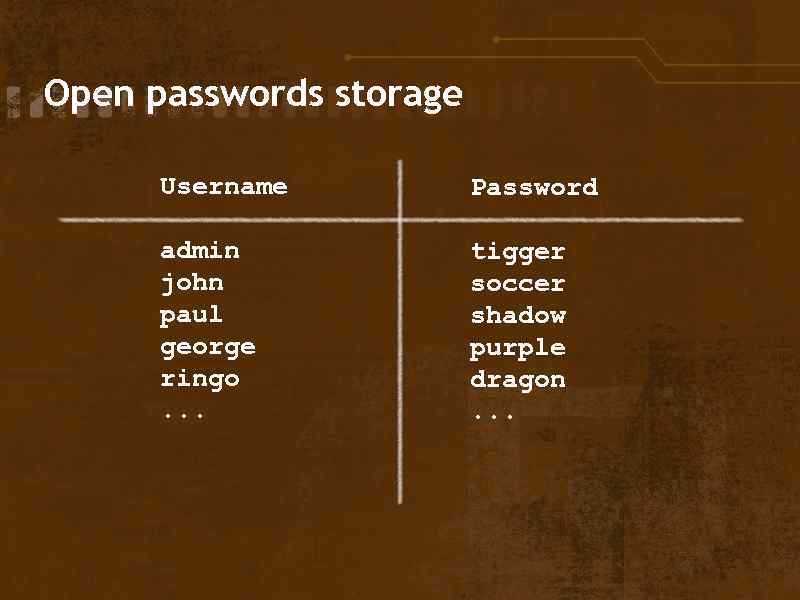
Open passwords storage Username admin john paul george ringo. . . Password tigger soccer shadow purple dragon. . .
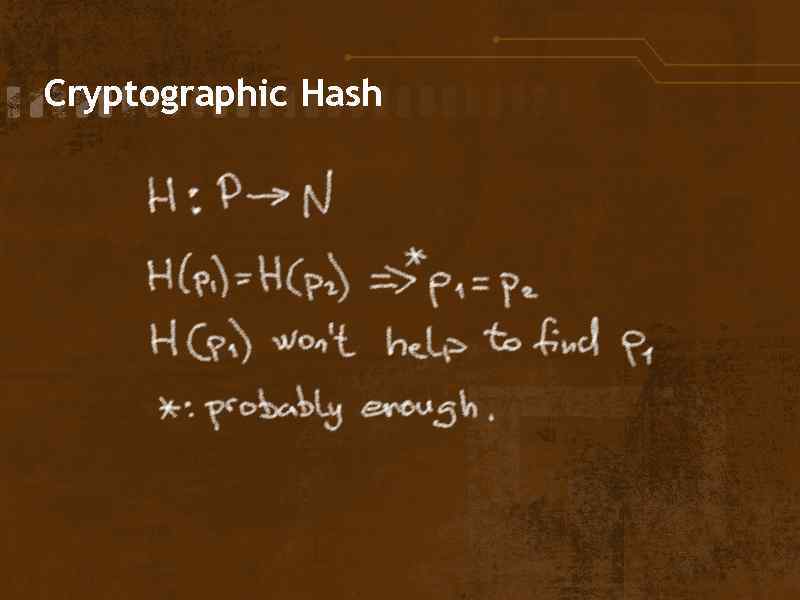
Cryptographic Hash
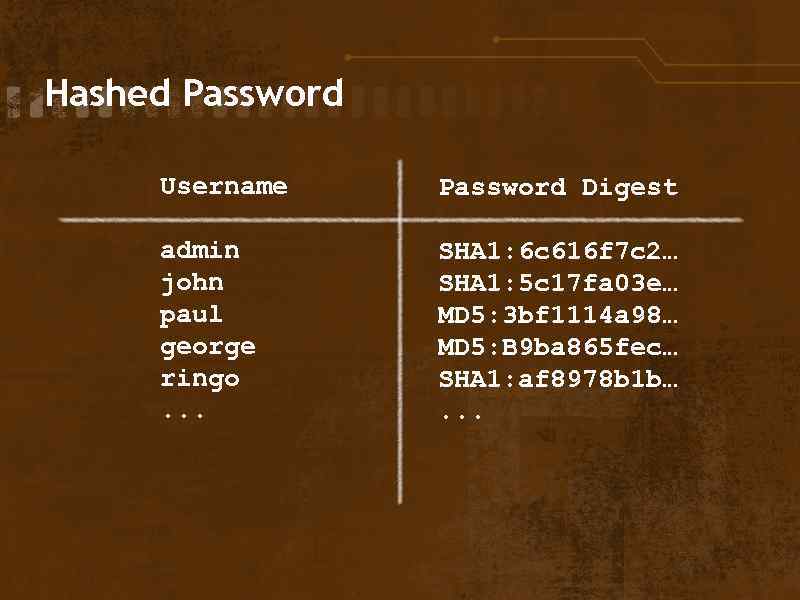
Hashed Password Username admin john paul george ringo. . . Password Digest SHA 1: 6 c 616 f 7 c 2… SHA 1: 5 c 17 fa 03 e… MD 5: 3 bf 1114 a 98… MD 5: B 9 ba 865 fec… SHA 1: af 8978 b 1 b…. . .
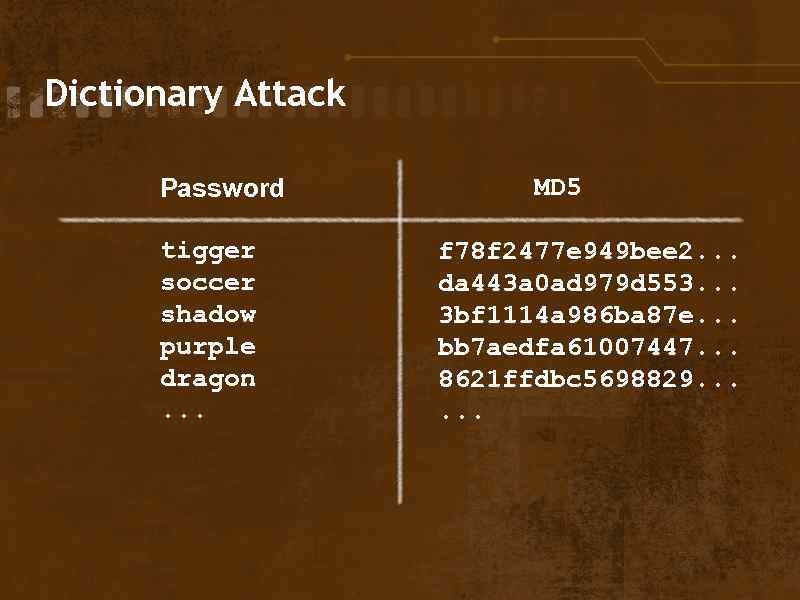
Dictionary Attack Password tigger soccer shadow purple dragon. . . MD 5 f 78 f 2477 e 949 bee 2. . . da 443 a 0 ad 979 d 553. . . 3 bf 1114 a 986 ba 87 e. . . bb 7 aedfa 61007447. . . 8621 ffdbc 5698829. . .

Rainbow Table

Cryptographic Salt • Generate a random number • Mix with password before hashing • Store in open form with the password
Requirements Update • Help a user to detect phising • Do not write passwords to logs • Use SSL • Store passwords as salted hashes
Password is guessed: how?

Passwords Policy • Password strength • Password change period

Bruteforce Mitigation • Detect • React • Mitigate

Bruteforce Mitigation • Detect o. Count the attempts • React • o. Block the account § But mind the Do. S o. Display CAPTCHA Mitigate o. Do not tell what's wrong with the credentials

CAPTCHA • Completely • Automated • Public • Turing Test To Tell • Computer and • Human • Apart

CAPTCHA Threats • Automated recognition • Bad randomness • Implementation flaws • Legal issues

CAPTCHA Threats • Automated recognition • Bad randomness • Implementation flaws • Legal issues
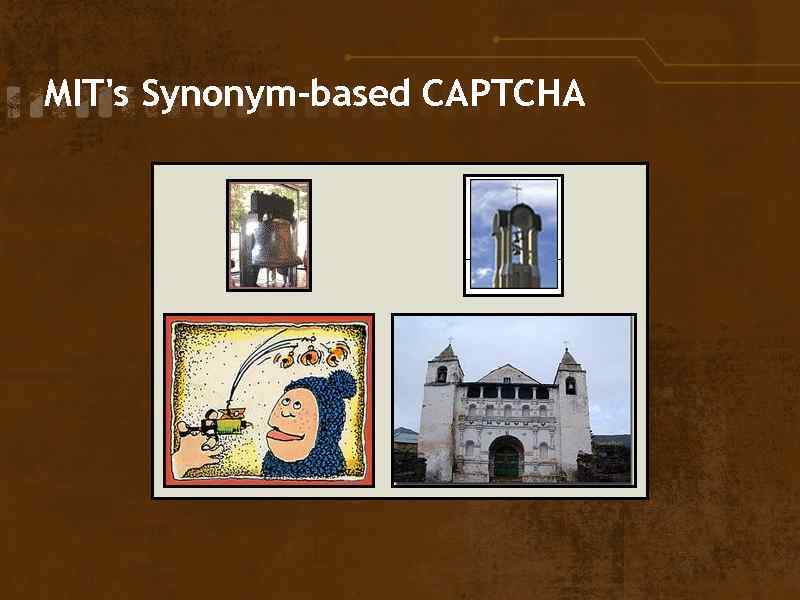
MIT's Synonym-based CAPTCHA
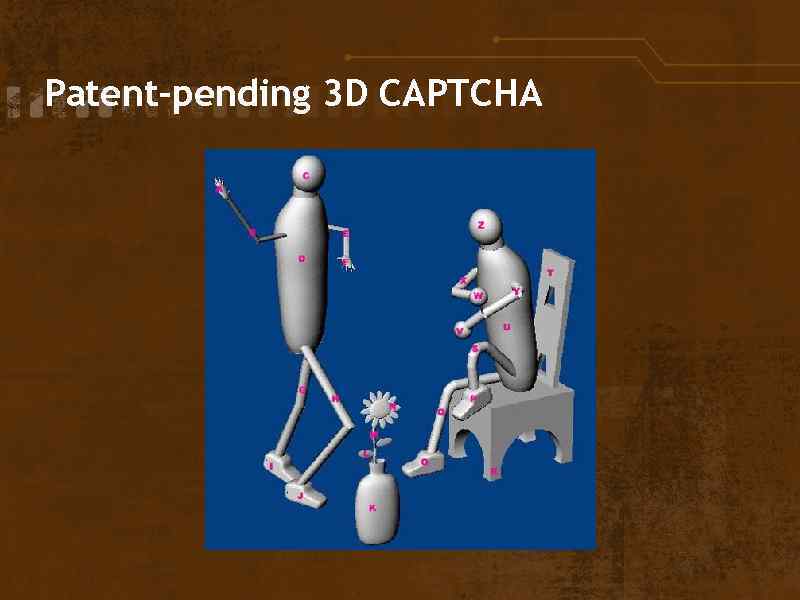
Patent-pending 3 D CAPTCHA
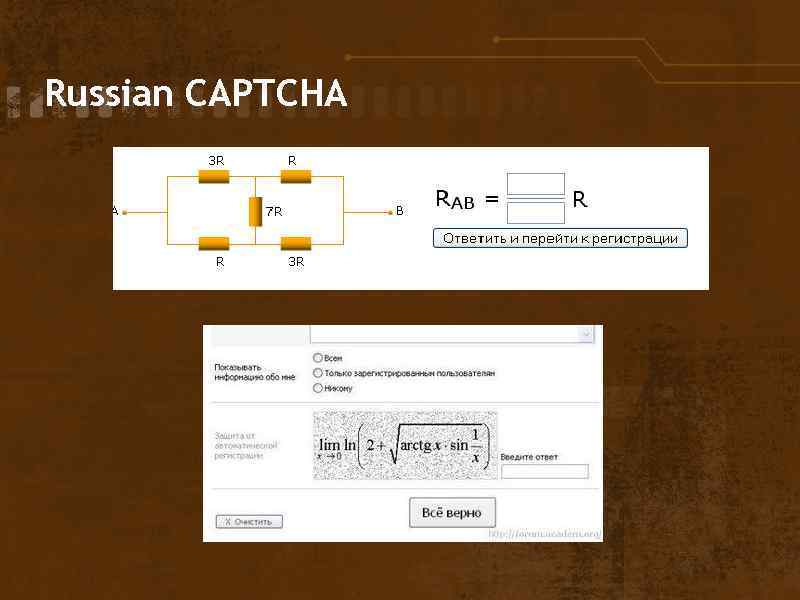
Russian CAPTCHA
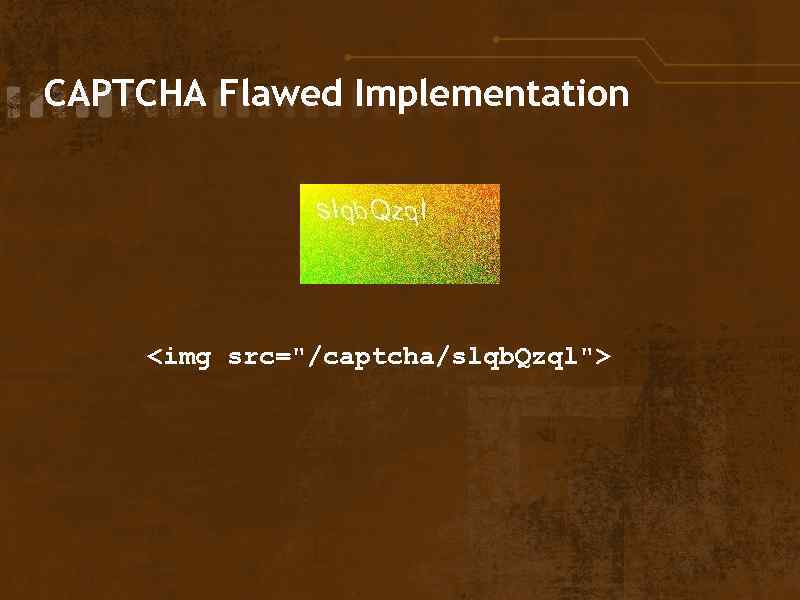
CAPTCHA Flawed Implementation <img src="/captcha/slqb. Qzql">

CAPTCHA Flawed Implementation

CAPTCHA Replay

Password is tampered with: how?

Requirements Update • Define password policy • Detect the brute force attempts • • • o. And count properly o. And mind other ways to enumerate CAPTCHA o. Really random and unique o. Generated, reset and validated properly Do not disclose unnecessary information Re-authenticate before the sensitive actions

UC 2: Recovery

Password Recovery • How to recover • o. Remind the password o. Allow to reset o. Reset and send How to verify o. Other channels: SMS, e-mail o. Secret Questions o. Account-specific information

Authentication-related Attacks

Authentication Weaknesses • Trusted relations • o. No Application-layer authentication o. Relying on the network layer Injections
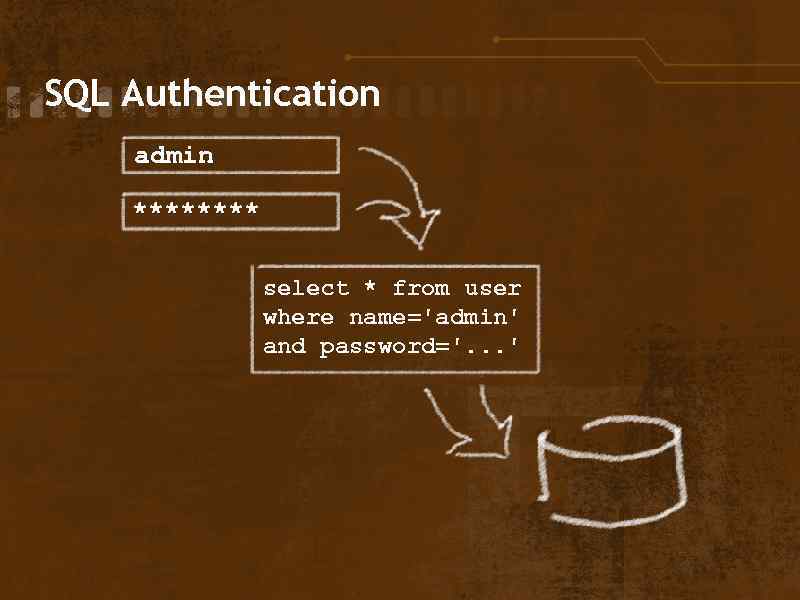
SQL Authentication admin **** select * from user where name='admin' and password='. . . '
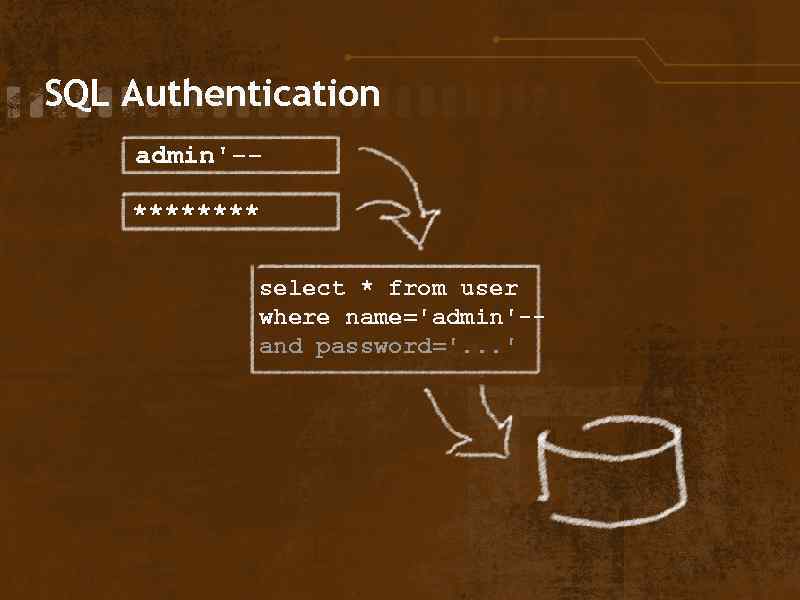
SQL Authentication admin'-**** select * from user where name='admin'-- and password='. . . '
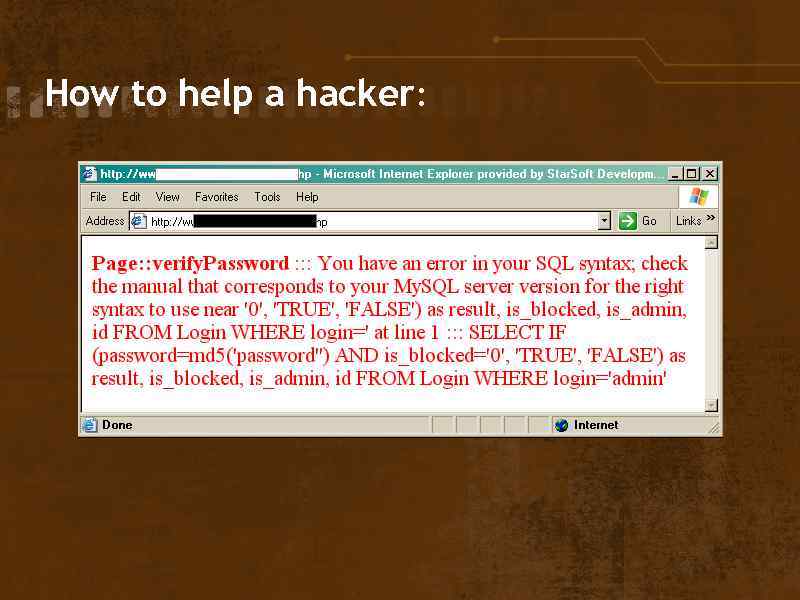
How to help a hacker:

How to help a hacker:

Kinds of Injection • SQL • HQL • LDAP • XPath • OS Shell

Requirements Update • Implement application-layer authentication • Validate and sanitize the input o. Request parameters, cookie, configuration • Use prepared statements

Methods of Authentication

Methods of Authentication • Basic • Digest • Form-based
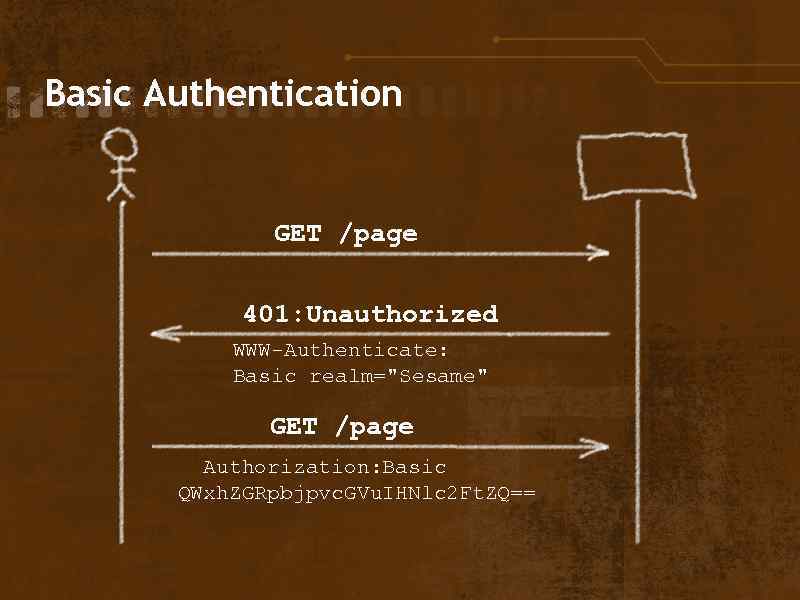
Basic Authentication GET /page 401: Unauthorized WWW-Authenticate: Basic realm="Sesame" GET /page Authorization: Basic QWxh. ZGRpbjpvc. GVu. IHNlc 2 Ft. ZQ==
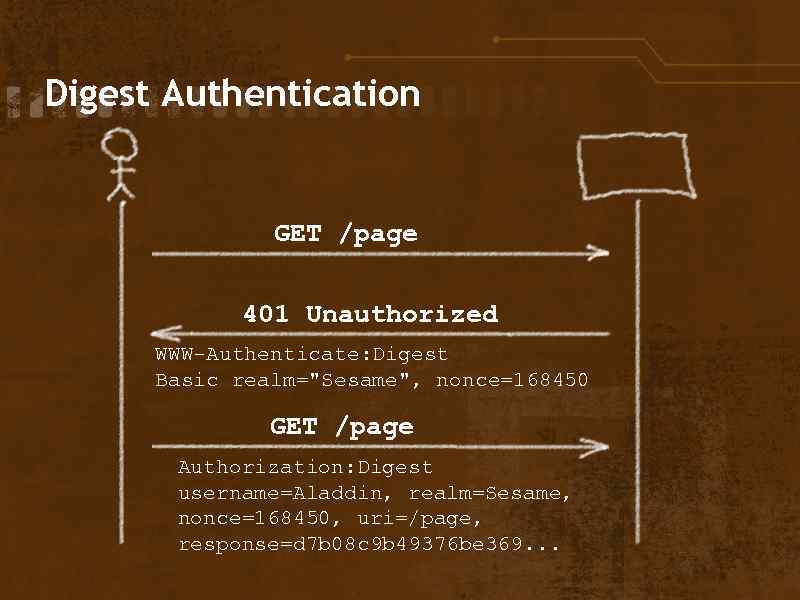
Digest Authentication GET /page 401 Unauthorized WWW-Authenticate: Digest Basic realm="Sesame", nonce=168450 GET /page Authorization: Digest username=Aladdin, realm=Sesame, nonce=168450, uri=/page, response=d 7 b 08 c 9 b 49376 be 369. . .
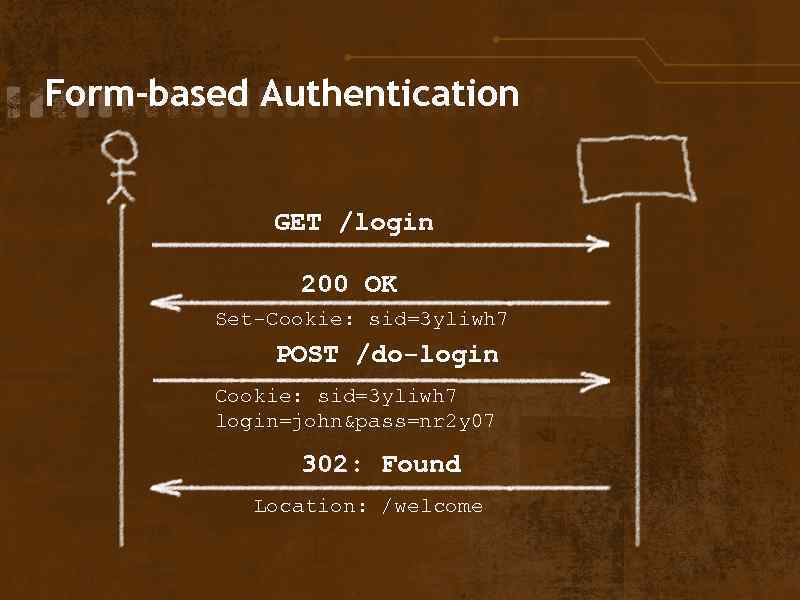
Form-based Authentication GET /login 200 OK Set-Cookie: sid=3 yliwh 7 POST /do-login Cookie: sid=3 yliwh 7 login=john&pass=nr 2 y 07 302: Found Location: /welcome

References • OWASP, http: //owasp. org o Especially, OWASP Security Testing Guide v 3 • Common Weakness Enumeration, http: //cwe. mitre. org
Thank you!
websec-training-authentication.pptx