b2d4fd3c8f795639975d76bc1cfcf1d7.ppt
- Количество слайдов: 40
 Introduction to Systems Security (January 11, 2012) © Abdou Illia – Spring 2012
Introduction to Systems Security (January 11, 2012) © Abdou Illia – Spring 2012
 Learning Objectives n Discuss main security threats n Discuss types of systems’ attacks n Discuss types of defense systems 2
Learning Objectives n Discuss main security threats n Discuss types of systems’ attacks n Discuss types of defense systems 2
 2010 Computer Crime and Security Survey (2010 CSI Security Report) Survey Summary online n Survey conducted by the Computer Security Institute (http: //www. gocsi. com). n Copy of Survey report on course web site n Based on replies from 494 U. S. Computer Security Professionals. 3
2010 Computer Crime and Security Survey (2010 CSI Security Report) Survey Summary online n Survey conducted by the Computer Security Institute (http: //www. gocsi. com). n Copy of Survey report on course web site n Based on replies from 494 U. S. Computer Security Professionals. 3
 2009 CSI Report: Types of attacks or Misuse in last 12 months 4
2009 CSI Report: Types of attacks or Misuse in last 12 months 4
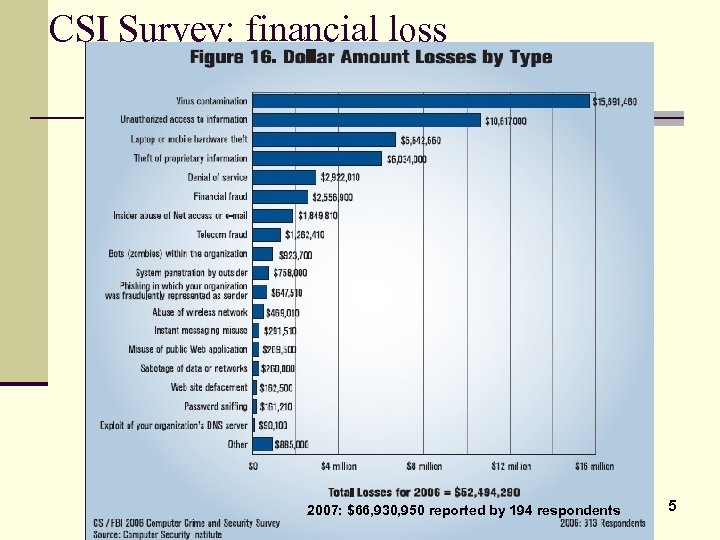 CSI Survey: financial loss 2007: $66, 930, 950 reported by 194 respondents 5
CSI Survey: financial loss 2007: $66, 930, 950 reported by 194 respondents 5
 Attack Trends n Growing Incident Frequency until 2001 n Incidents reported to the Computer Emergency Response Team/Coordination Center 1998 1999 2000 2001 - Present 3, 474 9, 859 21, 756 52, 658 Decline in # of attacks n Growing Malevolence since 2000 n Most early attacks were not malicious n Malicious attacks are the norm today 6
Attack Trends n Growing Incident Frequency until 2001 n Incidents reported to the Computer Emergency Response Team/Coordination Center 1998 1999 2000 2001 - Present 3, 474 9, 859 21, 756 52, 658 Decline in # of attacks n Growing Malevolence since 2000 n Most early attacks were not malicious n Malicious attacks are the norm today 6
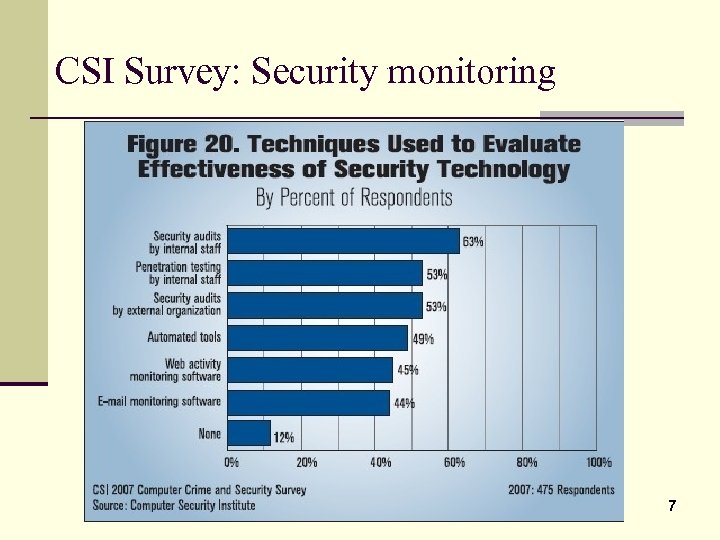 CSI Survey: Security monitoring 7
CSI Survey: Security monitoring 7
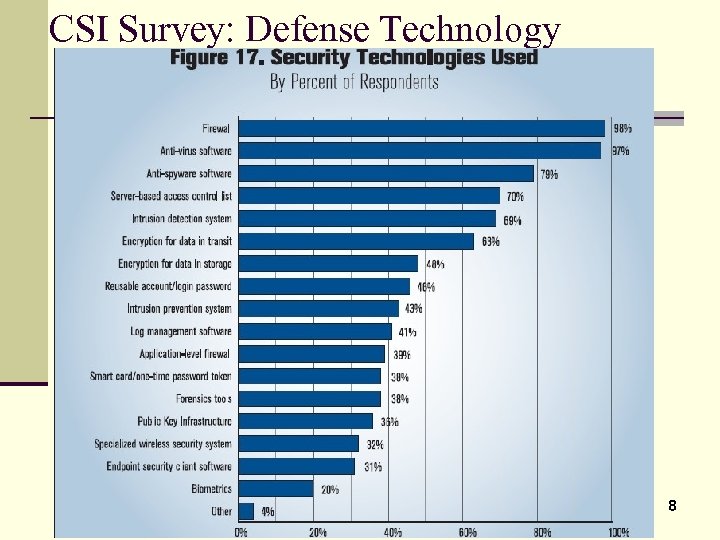 CSI Survey: Defense Technology 8
CSI Survey: Defense Technology 8
 2011 Sophos Security Threat Report n Report focused on Sophos’ security software n General discovery * 9 * Infected USB drives take advantage of computers that have auto-run enabled, which allow the automated execution of code contained on the flash drive.
2011 Sophos Security Threat Report n Report focused on Sophos’ security software n General discovery * 9 * Infected USB drives take advantage of computers that have auto-run enabled, which allow the automated execution of code contained on the flash drive.
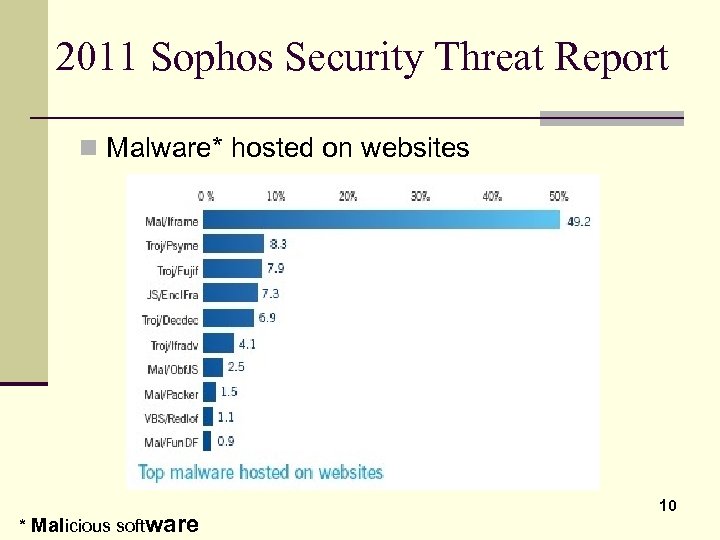 2011 Sophos Security Threat Report n Malware* hosted on websites * Malicious software 10
2011 Sophos Security Threat Report n Malware* hosted on websites * Malicious software 10
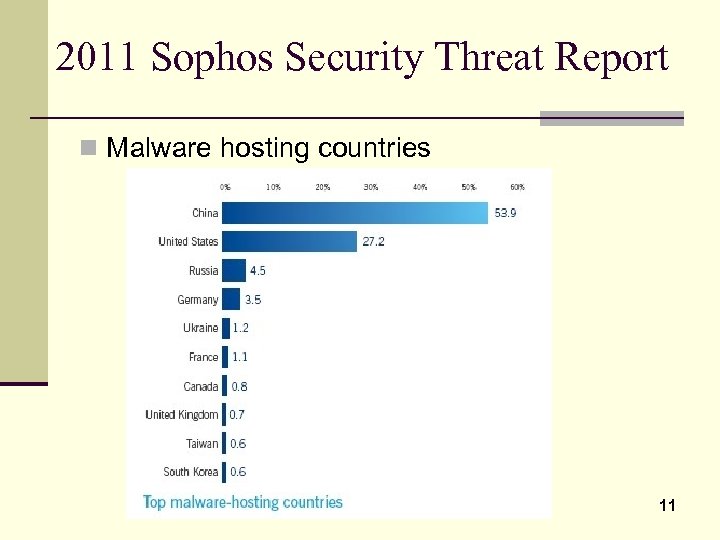 2011 Sophos Security Threat Report n Malware hosting countries 11
2011 Sophos Security Threat Report n Malware hosting countries 11
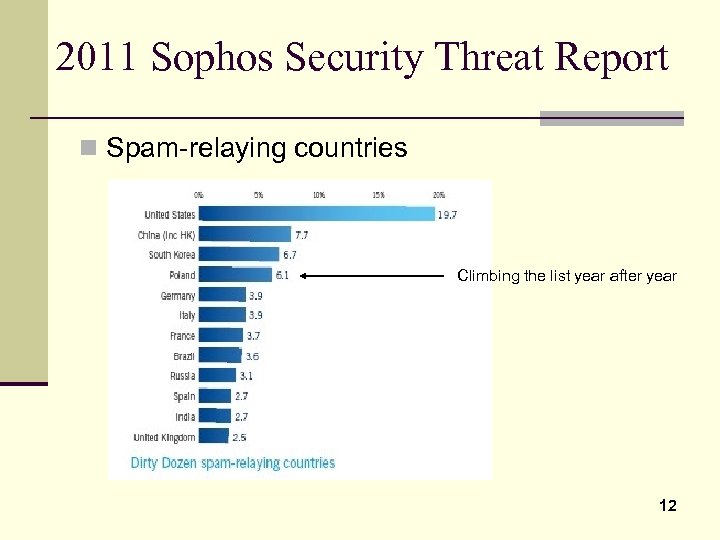 2011 Sophos Security Threat Report n Spam-relaying countries Climbing the list year after year 12
2011 Sophos Security Threat Report n Spam-relaying countries Climbing the list year after year 12
 2011 Sophos Security Threat Report n Web server’s software affected Web server software Apache IIS Sun. ONE Operating System Computer hardware RAM chip HD Processor Web server computer n As of March 2010 Apache served 58% of all web servers n Apache available for Microsoft Windows, Novell Net. Ware and Unix-like OS 13
2011 Sophos Security Threat Report n Web server’s software affected Web server software Apache IIS Sun. ONE Operating System Computer hardware RAM chip HD Processor Web server computer n As of March 2010 Apache served 58% of all web servers n Apache available for Microsoft Windows, Novell Net. Ware and Unix-like OS 13
 Other Empirical Attack Data n Security. Focus n Data from 10, 000 firms in 2010 n Attack Targets n 31 million Windows-specific attacks n 22 million UNIX/LINUX attacks n 7 million Cisco IOS attacks n All operating systems are attacked! 14
Other Empirical Attack Data n Security. Focus n Data from 10, 000 firms in 2010 n Attack Targets n 31 million Windows-specific attacks n 22 million UNIX/LINUX attacks n 7 million Cisco IOS attacks n All operating systems are attacked! 14
 Summary Questions (Part 1) 1. What does malware refer to? 2. Systems running Microsoft operating systems are more likely to be attacked than others. T F 3. With Windows OS, you can use IIS or another web server software like Apache. T F 4. What web server software is most affected by web threats today? 5. What types of email-attached file could/could not hide a malware? 6. Could USB drives be used as means for infecting a system with malware? How? 15
Summary Questions (Part 1) 1. What does malware refer to? 2. Systems running Microsoft operating systems are more likely to be attacked than others. T F 3. With Windows OS, you can use IIS or another web server software like Apache. T F 4. What web server software is most affected by web threats today? 5. What types of email-attached file could/could not hide a malware? 6. Could USB drives be used as means for infecting a system with malware? How? 15
 Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees Cyber vandals Cyber terrorists n Hacking n intentional access without authorization or in excess of authorization n Elite Hackers n Characterized by technical expertise and dogged persistence, not just a bag of tools n n Use attack scripts to automate actions, but this is not the essence of what they do Could hack to steal info, to do damage, or just to prove their status 16
Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees Cyber vandals Cyber terrorists n Hacking n intentional access without authorization or in excess of authorization n Elite Hackers n Characterized by technical expertise and dogged persistence, not just a bag of tools n n Use attack scripts to automate actions, but this is not the essence of what they do Could hack to steal info, to do damage, or just to prove their status 16
 Systems attackers n Elite Hackers (cont. ) n n Black hat hackers break in for their own purposes White hat hackers can mean multiple things n n n Strictest: Hack only by invitation as part of vulnerability testing Some hack without permission but report vulnerabilities (not for pay) Ethical hackers n Hired by organizations to perform hacking activities in order to § Test the performance of systems’ security § Develop/propose solutions 17
Systems attackers n Elite Hackers (cont. ) n n Black hat hackers break in for their own purposes White hat hackers can mean multiple things n n n Strictest: Hack only by invitation as part of vulnerability testing Some hack without permission but report vulnerabilities (not for pay) Ethical hackers n Hired by organizations to perform hacking activities in order to § Test the performance of systems’ security § Develop/propose solutions 17
 Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Script Kiddies Cyber vandals Cyber terrorists n “Kids” that use pre-written attack scripts (kiddie scripts) n Called “lamers” by elite hackers n Their large number makes them dangerous n Noise of kiddie script attacks masks more sophisticated attacks 18
Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Script Kiddies Cyber vandals Cyber terrorists n “Kids” that use pre-written attack scripts (kiddie scripts) n Called “lamers” by elite hackers n Their large number makes them dangerous n Noise of kiddie script attacks masks more sophisticated attacks 18
 Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Virus Writers and Releasers n Writing virus code is not a crime n Cyber terrorists Virus writers versus virus releasers n Cyber vandals Only releasing viruses is punishable 19
Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Virus Writers and Releasers n Writing virus code is not a crime n Cyber terrorists Virus writers versus virus releasers n Cyber vandals Only releasing viruses is punishable 19
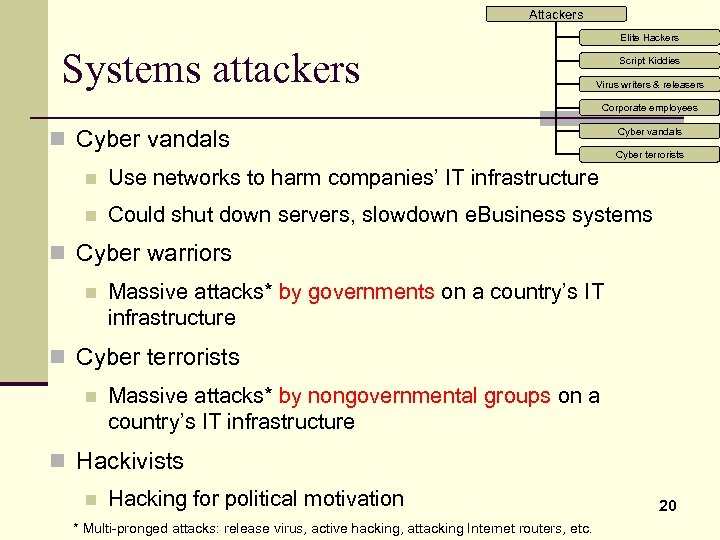 Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Cyber vandals Cyber terrorists n Use networks to harm companies’ IT infrastructure n Could shut down servers, slowdown e. Business systems n Cyber warriors n Massive attacks* by governments on a country’s IT infrastructure n Cyber terrorists n Massive attacks* by nongovernmental groups on a country’s IT infrastructure n Hackivists n Hacking for political motivation * Multi-pronged attacks: release virus, active hacking, attacking Internet routers, etc. 20
Attackers Elite Hackers Systems attackers Script Kiddies Virus writers & releasers Corporate employees n Cyber vandals Cyber terrorists n Use networks to harm companies’ IT infrastructure n Could shut down servers, slowdown e. Business systems n Cyber warriors n Massive attacks* by governments on a country’s IT infrastructure n Cyber terrorists n Massive attacks* by nongovernmental groups on a country’s IT infrastructure n Hackivists n Hacking for political motivation * Multi-pronged attacks: release virus, active hacking, attacking Internet routers, etc. 20
 Summary Questions (Part 2) 1. What is meant by elite hacker, white hat hacker, ethical hacker? 2. What is the difference between script kiddies and elite hackers? 3. Is releasing a virus a crime in the U. S. ? 4. What is the difference between cyber war and cyber terrorism? 21
Summary Questions (Part 2) 1. What is meant by elite hacker, white hat hacker, ethical hacker? 2. What is the difference between script kiddies and elite hackers? 3. Is releasing a virus a crime in the U. S. ? 4. What is the difference between cyber war and cyber terrorism? 21
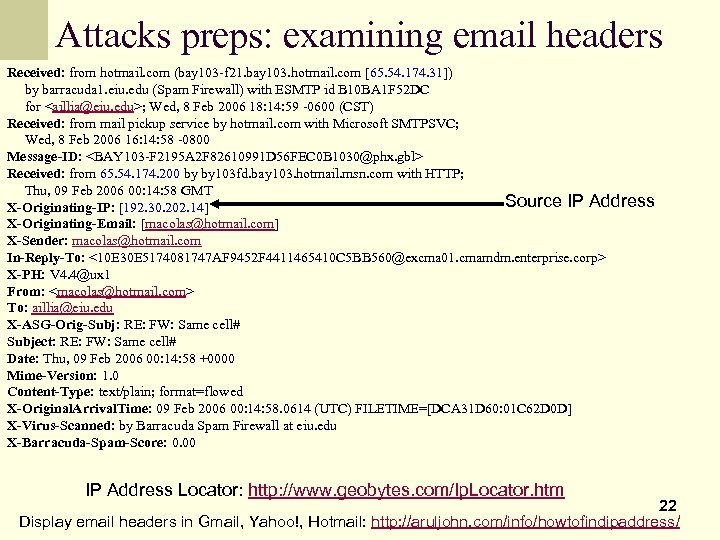 Attacks preps: examining email headers Received: from hotmail. com (bay 103 -f 21. bay 103. hotmail. com [65. 54. 174. 31]) by barracuda 1. eiu. edu (Spam Firewall) with ESMTP id B 10 BA 1 F 52 DC for
Attacks preps: examining email headers Received: from hotmail. com (bay 103 -f 21. bay 103. hotmail. com [65. 54. 174. 31]) by barracuda 1. eiu. edu (Spam Firewall) with ESMTP id B 10 BA 1 F 52 DC for
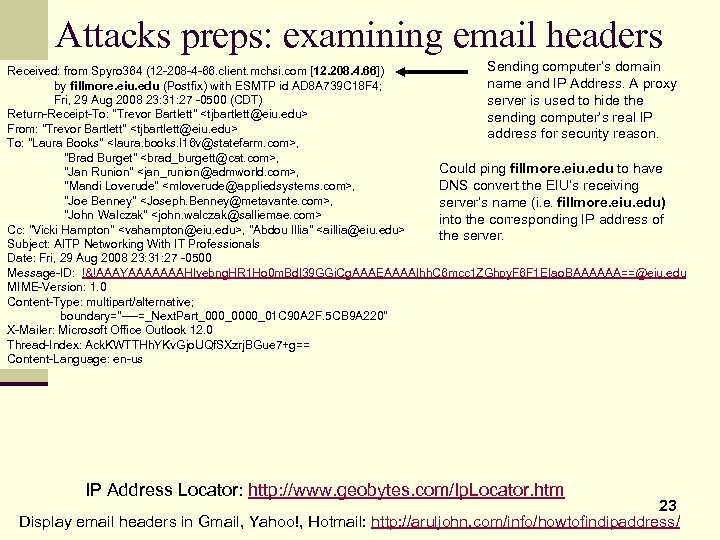 Attacks preps: examining email headers Sending computer’s domain Received: from Spyro 364 (12 -208 -4 -66. client. mchsi. com [12. 208. 4. 66]) name and IP Address. A proxy by fillmore. eiu. edu (Postfix) with ESMTP id AD 8 A 739 C 18 F 4; Fri, 29 Aug 2008 23: 31: 27 -0500 (CDT) server is used to hide the Return-Receipt-To: "Trevor Bartlett"
Attacks preps: examining email headers Sending computer’s domain Received: from Spyro 364 (12 -208 -4 -66. client. mchsi. com [12. 208. 4. 66]) name and IP Address. A proxy by fillmore. eiu. edu (Postfix) with ESMTP id AD 8 A 739 C 18 F 4; Fri, 29 Aug 2008 23: 31: 27 -0500 (CDT) server is used to hide the Return-Receipt-To: "Trevor Bartlett"
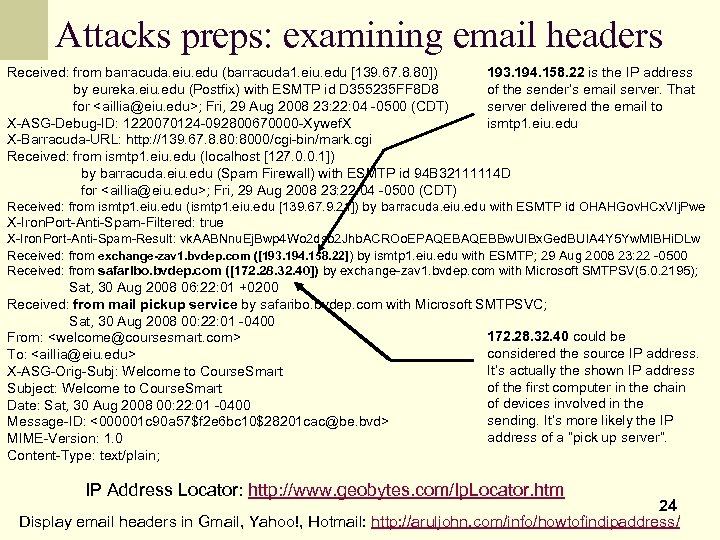 Attacks preps: examining email headers 193. 194. 158. 22 is the IP address Received: from barracuda. eiu. edu (barracuda 1. eiu. edu [139. 67. 8. 80]) of the sender’s email server. That by eureka. eiu. edu (Postfix) with ESMTP id D 355235 FF 8 D 8 server delivered the email to for
Attacks preps: examining email headers 193. 194. 158. 22 is the IP address Received: from barracuda. eiu. edu (barracuda 1. eiu. edu [139. 67. 8. 80]) of the sender’s email server. That by eureka. eiu. edu (Postfix) with ESMTP id D 355235 FF 8 D 8 server delivered the email to for
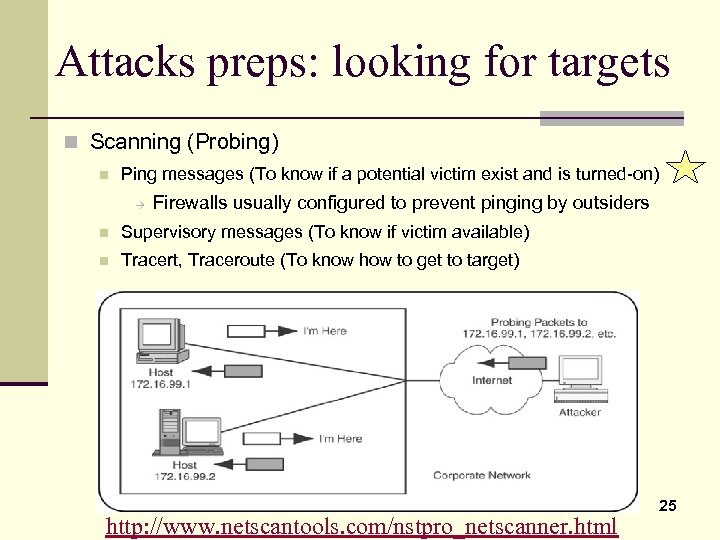 Attacks preps: looking for targets n Scanning (Probing) n Ping messages (To know if a potential victim exist and is turned-on) à Firewalls usually configured to prevent pinging by outsiders n Supervisory messages (To know if victim available) n Tracert, Traceroute (To know how to get to target) http: //www. netscantools. com/nstpro_netscanner. html 25
Attacks preps: looking for targets n Scanning (Probing) n Ping messages (To know if a potential victim exist and is turned-on) à Firewalls usually configured to prevent pinging by outsiders n Supervisory messages (To know if victim available) n Tracert, Traceroute (To know how to get to target) http: //www. netscantools. com/nstpro_netscanner. html 25
 Attacks preps: identifying targets n Examining scanning result reveals n n n IP addresses of potential victims What services victims are running. Different services have different weaknesses Host’s operating system, version number, etc. n Whois database at Network. Solutions. com also used when ping scans fail n Social engineering n Tricking employees into giving out info (passwords, keys, etc. ) n Deciding the type of attacks to launch given available info 26
Attacks preps: identifying targets n Examining scanning result reveals n n n IP addresses of potential victims What services victims are running. Different services have different weaknesses Host’s operating system, version number, etc. n Whois database at Network. Solutions. com also used when ping scans fail n Social engineering n Tricking employees into giving out info (passwords, keys, etc. ) n Deciding the type of attacks to launch given available info 26
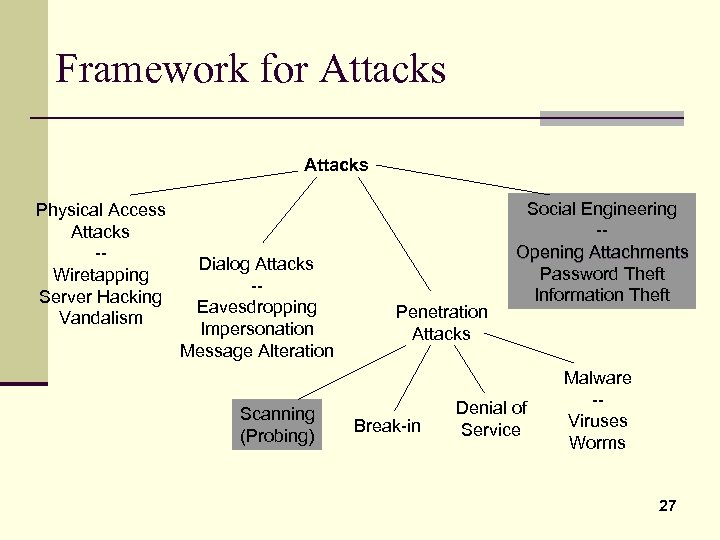 Framework for Attacks Physical Access Attacks -Wiretapping Server Hacking Vandalism Dialog Attacks -Eavesdropping Impersonation Message Alteration Scanning (Probing) Penetration Attacks Break-in Social Engineering -Opening Attachments Password Theft Information Theft Denial of Service Malware -Viruses Worms 27
Framework for Attacks Physical Access Attacks -Wiretapping Server Hacking Vandalism Dialog Attacks -Eavesdropping Impersonation Message Alteration Scanning (Probing) Penetration Attacks Break-in Social Engineering -Opening Attachments Password Theft Information Theft Denial of Service Malware -Viruses Worms 27
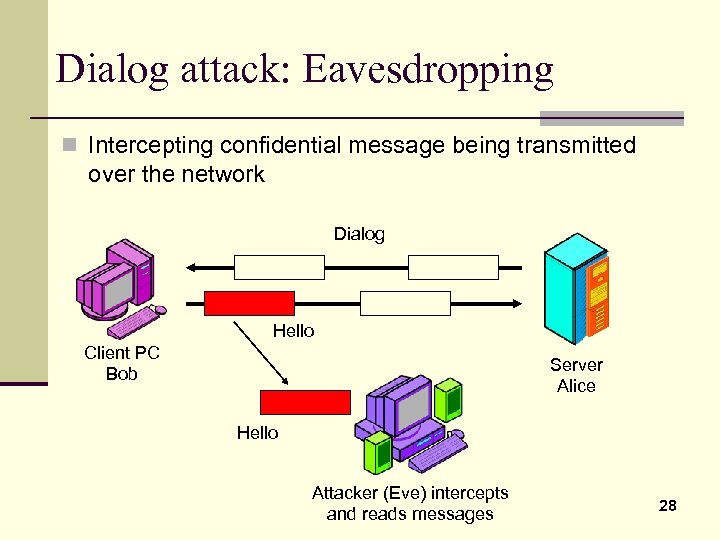 Dialog attack: Eavesdropping n Intercepting confidential message being transmitted over the network Dialog Hello Client PC Bob Server Alice Hello Attacker (Eve) intercepts and reads messages 28
Dialog attack: Eavesdropping n Intercepting confidential message being transmitted over the network Dialog Hello Client PC Bob Server Alice Hello Attacker (Eve) intercepts and reads messages 28
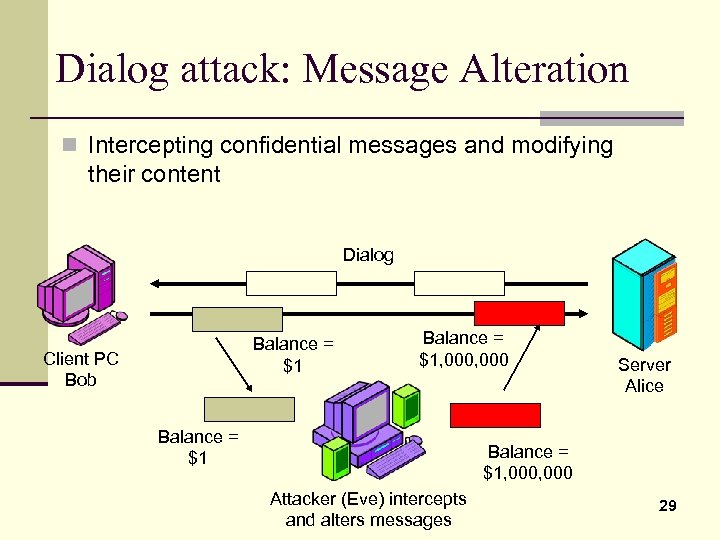 Dialog attack: Message Alteration n Intercepting confidential messages and modifying their content Dialog Balance = $1 Client PC Bob Balance = $1, 000 Balance = $1 Server Alice Balance = $1, 000 Attacker (Eve) intercepts and alters messages 29
Dialog attack: Message Alteration n Intercepting confidential messages and modifying their content Dialog Balance = $1 Client PC Bob Balance = $1, 000 Balance = $1 Server Alice Balance = $1, 000 Attacker (Eve) intercepts and alters messages 29
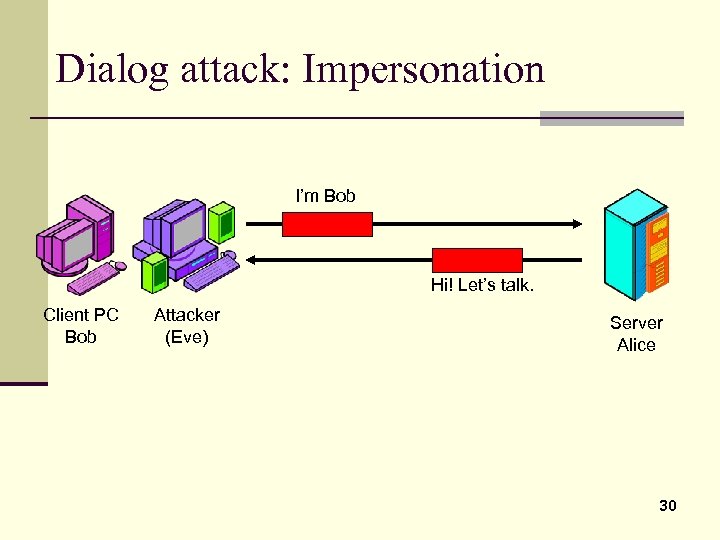 Dialog attack: Impersonation I’m Bob Hi! Let’s talk. Client PC Bob Attacker (Eve) Server Alice 30
Dialog attack: Impersonation I’m Bob Hi! Let’s talk. Client PC Bob Attacker (Eve) Server Alice 30
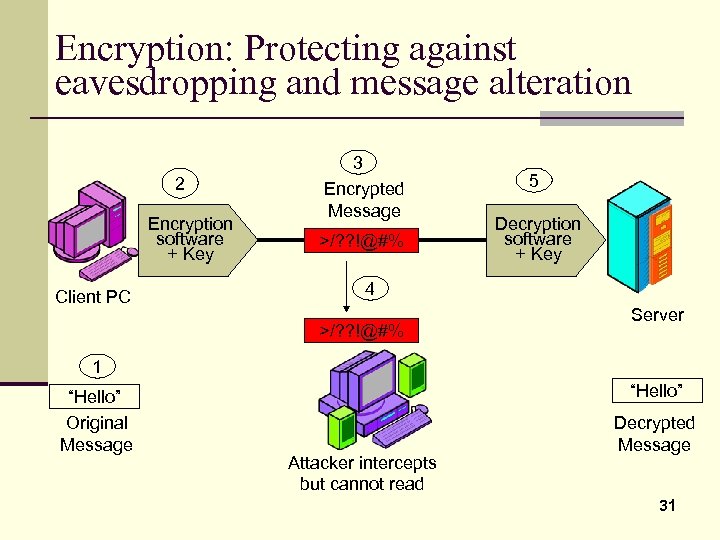 Encryption: Protecting against eavesdropping and message alteration 2 Encryption software + Key Client PC 3 Encrypted Message >/? ? !@#% 5 Decryption software + Key 4 >/? ? !@#% Server 1 “Hello” Original Message “Hello” Attacker intercepts but cannot read Decrypted Message 31
Encryption: Protecting against eavesdropping and message alteration 2 Encryption software + Key Client PC 3 Encrypted Message >/? ? !@#% 5 Decryption software + Key 4 >/? ? !@#% Server 1 “Hello” Original Message “Hello” Attacker intercepts but cannot read Decrypted Message 31
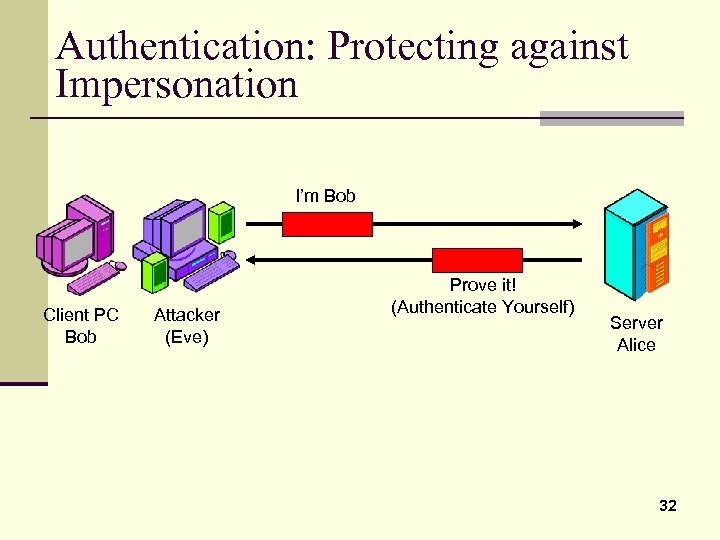 Authentication: Protecting against Impersonation I’m Bob Client PC Bob Attacker (Eve) Prove it! (Authenticate Yourself) Server Alice 32
Authentication: Protecting against Impersonation I’m Bob Client PC Bob Attacker (Eve) Prove it! (Authenticate Yourself) Server Alice 32
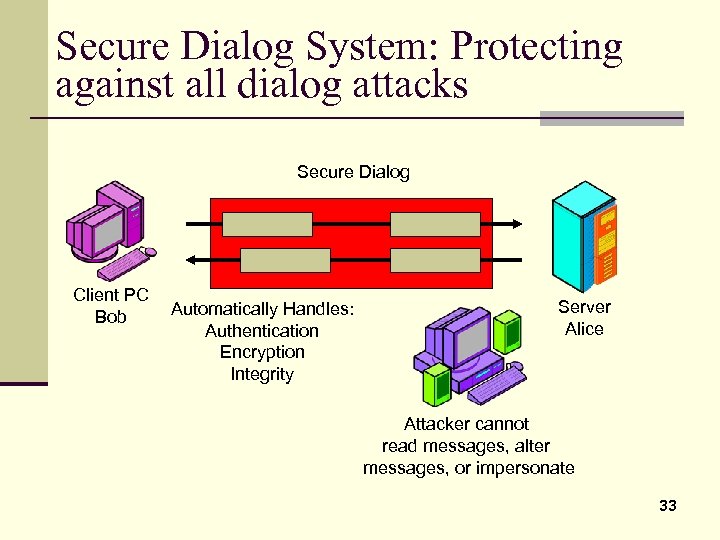 Secure Dialog System: Protecting against all dialog attacks Secure Dialog Client PC Bob Automatically Handles: Authentication Encryption Integrity Server Alice Attacker cannot read messages, alter messages, or impersonate 33
Secure Dialog System: Protecting against all dialog attacks Secure Dialog Client PC Bob Automatically Handles: Authentication Encryption Integrity Server Alice Attacker cannot read messages, alter messages, or impersonate 33
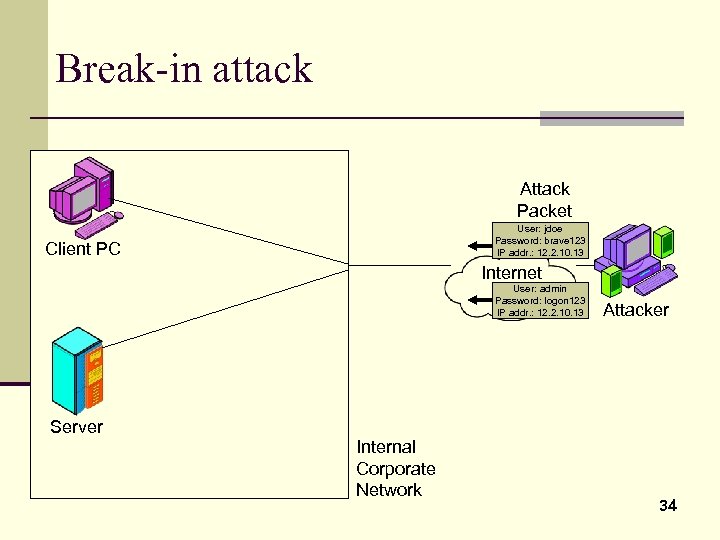 Break-in attack Attack Packet User: jdoe Password: brave 123 IP addr. : 12. 2. 10. 13 Client PC Internet User: admin Password: logon 123 IP addr. : 12. 2. 10. 13 Attacker Server Internal Corporate Network 34
Break-in attack Attack Packet User: jdoe Password: brave 123 IP addr. : 12. 2. 10. 13 Client PC Internet User: admin Password: logon 123 IP addr. : 12. 2. 10. 13 Attacker Server Internal Corporate Network 34
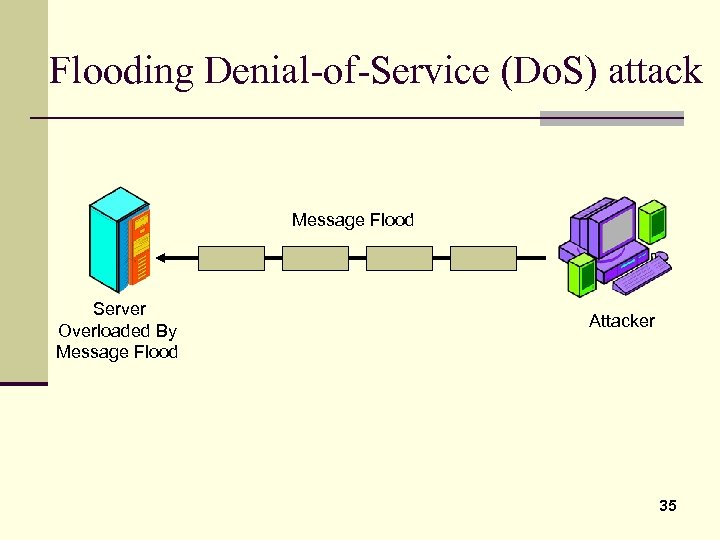 Flooding Denial-of-Service (Do. S) attack Message Flood Server Overloaded By Message Flood Attacker 35
Flooding Denial-of-Service (Do. S) attack Message Flood Server Overloaded By Message Flood Attacker 35
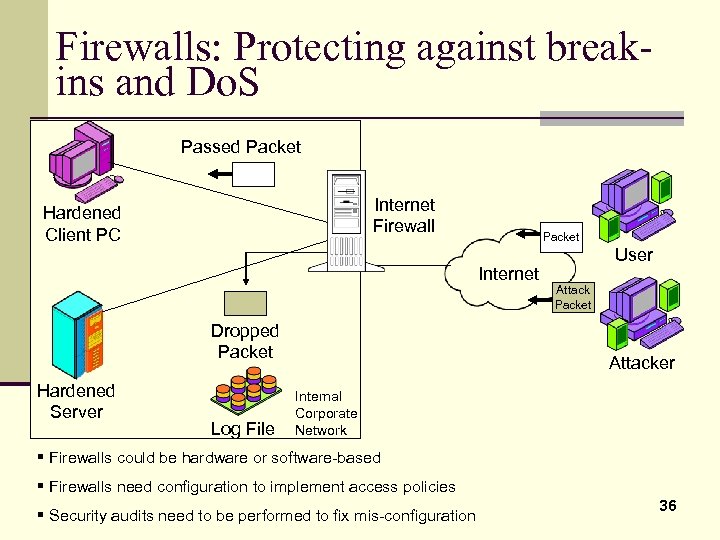 Firewalls: Protecting against breakins and Do. S Passed Packet Internet Firewall Hardened Client PC Packet Internet Dropped Packet Hardened Server Log File User Attack Packet Attacker Internal Corporate Network § Firewalls could be hardware or software-based § Firewalls need configuration to implement access policies § Security audits need to be performed to fix mis-configuration 36
Firewalls: Protecting against breakins and Do. S Passed Packet Internet Firewall Hardened Client PC Packet Internet Dropped Packet Hardened Server Log File User Attack Packet Attacker Internal Corporate Network § Firewalls could be hardware or software-based § Firewalls need configuration to implement access policies § Security audits need to be performed to fix mis-configuration 36
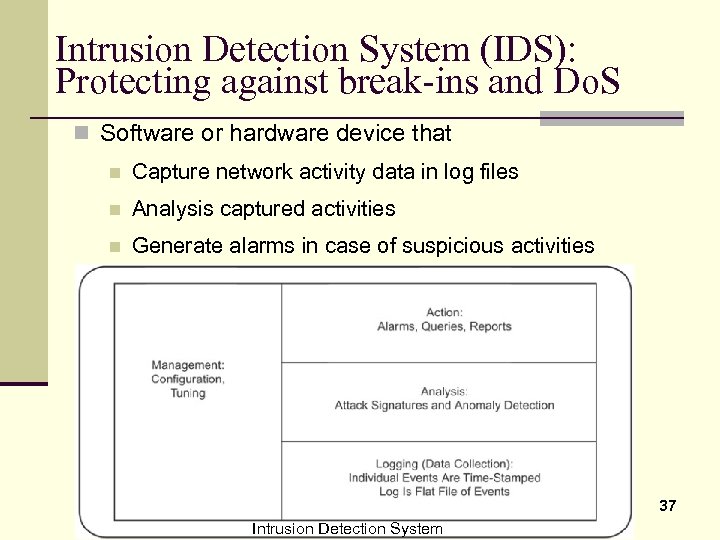 Intrusion Detection System (IDS): Protecting against break-ins and Do. S n Software or hardware device that n Capture network activity data in log files n Analysis captured activities n Generate alarms in case of suspicious activities 37 Intrusion Detection System
Intrusion Detection System (IDS): Protecting against break-ins and Do. S n Software or hardware device that n Capture network activity data in log files n Analysis captured activities n Generate alarms in case of suspicious activities 37 Intrusion Detection System
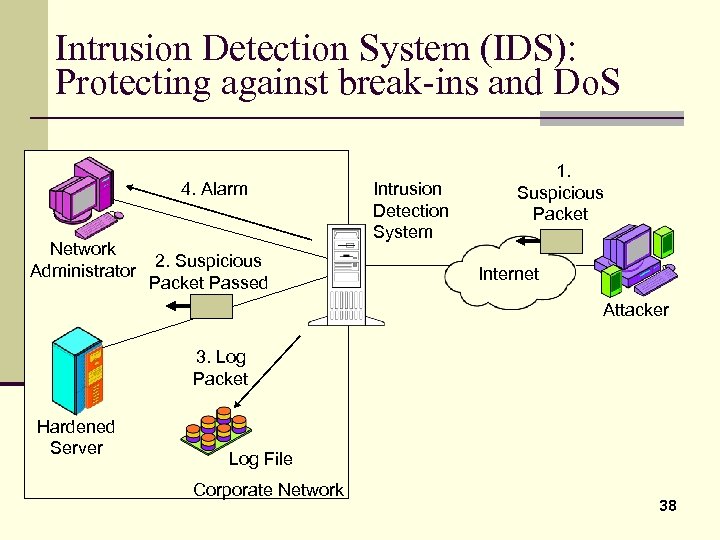 Intrusion Detection System (IDS): Protecting against break-ins and Do. S 4. Alarm Network Administrator 2. Suspicious Packet Passed Intrusion Detection System 1. Suspicious Packet Internet Attacker 3. Log Packet Hardened Server Log File Corporate Network 38
Intrusion Detection System (IDS): Protecting against break-ins and Do. S 4. Alarm Network Administrator 2. Suspicious Packet Passed Intrusion Detection System 1. Suspicious Packet Internet Attacker 3. Log Packet Hardened Server Log File Corporate Network 38
 Other defense measures n Good Access Control policies n Strong passwords n Good access rights implementation for resources (computer, folders, printers, etc. ) n Good group policies n Installing patches for n Operating systems n Most important Application software 39
Other defense measures n Good Access Control policies n Strong passwords n Good access rights implementation for resources (computer, folders, printers, etc. ) n Good group policies n Installing patches for n Operating systems n Most important Application software 39
 Summary Questions (Part 3) 1. What do ping messages allow? Why are ping scans often not effective? 2. What does social engineering mean? 3. What is meant by eavesdropping? Message alteration? 4. What kind of techniques could be used to protect against eavesdropping? 5. What is meant by Do. S? 6. What kind of tools could be used to protect a system against Do. S? 40
Summary Questions (Part 3) 1. What do ping messages allow? Why are ping scans often not effective? 2. What does social engineering mean? 3. What is meant by eavesdropping? Message alteration? 4. What kind of techniques could be used to protect against eavesdropping? 5. What is meant by Do. S? 6. What kind of tools could be used to protect a system against Do. S? 40


