df9913e4f971255d8481ff8f14c0898b.ppt
- Количество слайдов: 28

Introduction to Public Key Infrastructure (PKI) and Mobile PKI concept Pengenalan kepada Prasarana Kekunci Awam (PKI) dan Konsep Mobile PKI By: Ami Azrul bin Abdullah

Notes Dengan izin, the content of this presentation will be in English for the ease of understanding.
A G E N D A PREAMBLE BACKGROUND OF ENCRYPTION PKI IN A NUTSHELL PKI IN A MACRO LEVEL MOBILE PKI CONCEPT QUESTION AND ANSWER 3

PREAMBLE 1:
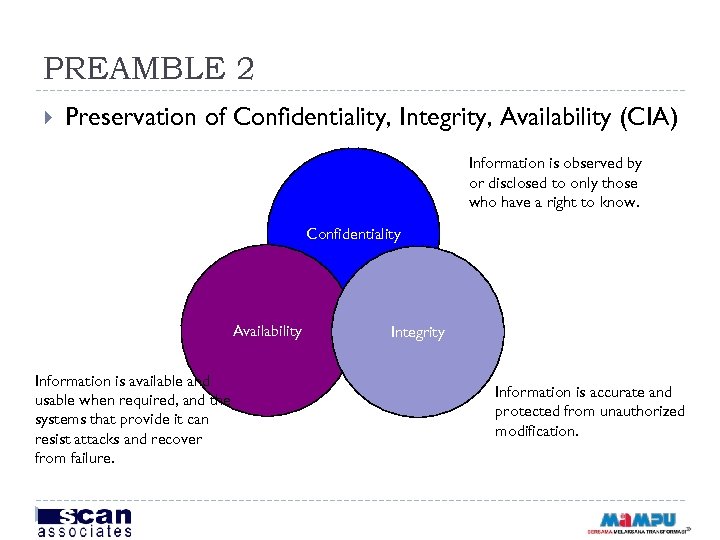
PREAMBLE 2 Preservation of Confidentiality, Integrity, Availability (CIA) Information is observed by or disclosed to only those who have a right to know. Confidentiality Availability Information is available and usable when required, and the systems that provide it can resist attacks and recover from failure. Integrity Information is accurate and protected from unauthorized modification.

HISTORY OF ENCRYPTION

In the beginning The needs to encrypt/decrypt message E. g. Ami Azrul - gqi 18 qhoi Creation of Keys are drived from an algorithm/set of formulas At first symmetric key is used
Next The flaws of symmetric key The Creation of Assymetric Key Two keys are not the same yet interrelated One cannot exist without the other Always term as key pairs – private and public The process done by private (secret) can only be reversed by public (and vice versa)
Intermezzo Symmetric – Key Pairs are the same; encrypt and decrypt Common Algorithm : AES · Blowfish · DES · Triple DES · Serpent · Twofish Assymmetric – Public and Private Key Pairs Common examples: Diffie-Helman, ECC, RSA Further reading: http: //en. wikipedia. org/wiki/RSA or http: //en. wikipedia. org/wiki/Assymetric_key_cryptography
And so. . "private key" means the key of a key pair used to create a digital signature; "public key" means the key of a key pair used to verify a digital signature; Definitions from DSA 1997

But Keys are only algorithms ->numbers The numbers -> keys are unique Associate identity with keys The birth of the Certification Authority, Registration Authority, and of course our regulator.

PKI IN A NUTSHELL

Digital Certificates Electronic counterparts to driver licenses, passports, membership cards or any legal identification documents: Proof of identity when communicating online Contain information about the owner i. e Name, Public Key, Issuer Name, Validity Date etc Contain a pair of key: Private Key and Public Key • Kept securely and safely by the owner • Use to generate digital signature • Kept by the relying party, CA or anybody who want to transact with the owner • Use to verify the digital signature
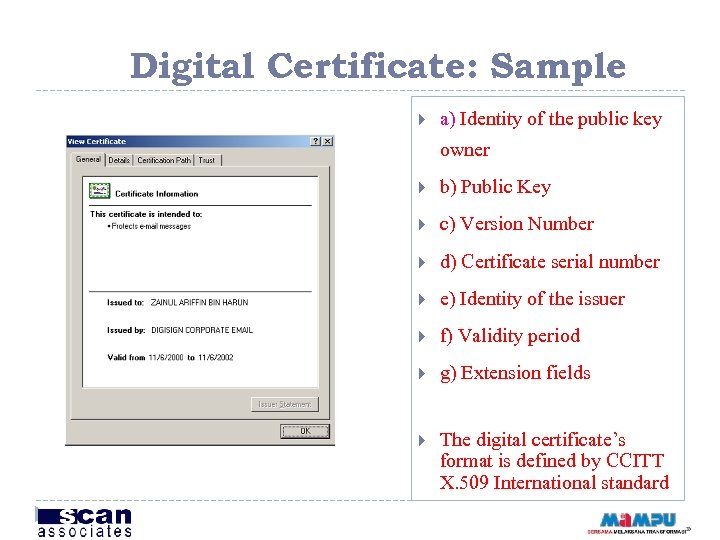
Digital Certificate: Sample a) Identity of the public key owner b) Public Key c) Version Number d) Certificate serial number e) Identity of the issuer f) Validity period g) Extension fields The digital certificate’s format is defined by CCITT X. 509 International standard

The story continues. . digital signature" means a transformation of a message using an asymmetric cryptosystem such that a person having the initial message and the signer's public key can accurately determine" (a) whether the transformation was created using the private key that corresponds to the signer's public key; and (b) whether the message has been altered since the transformation was made;
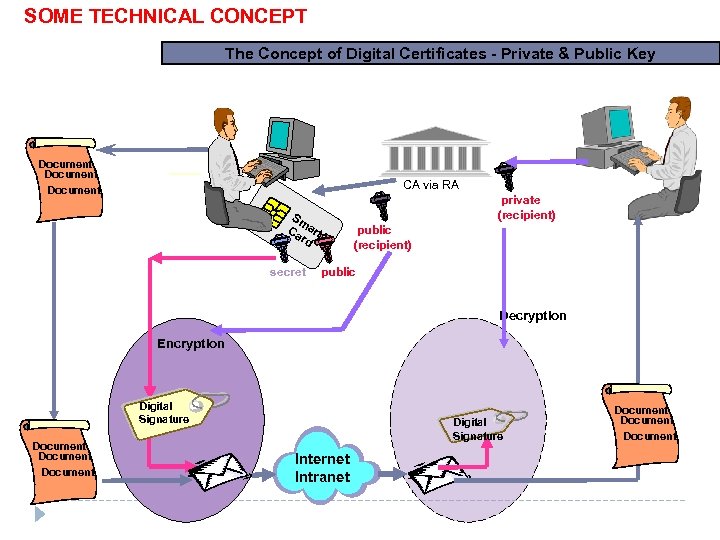
SOME TECHNICAL CONCEPT The Concept of Digital Certificates - Private & Public Key Document CA via RA private (recipient) Sm Ca art rd secret public (recipient) public Decryption Encryption Digital Signature Document Digital Signature Internet Intranet Document
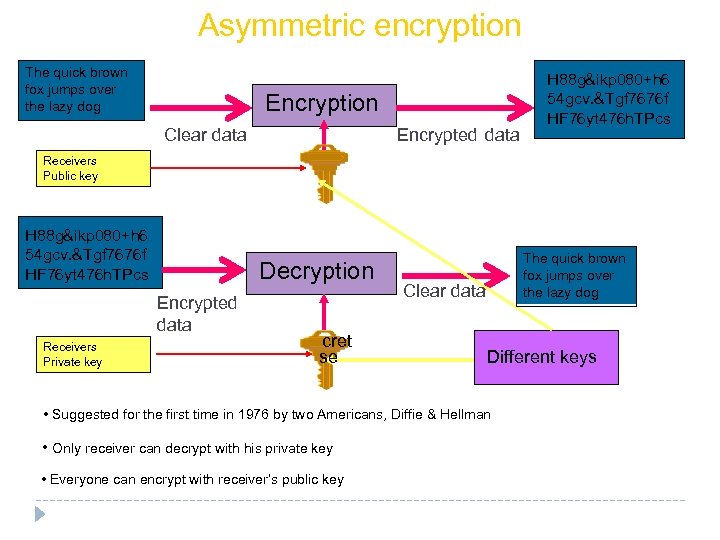
Asymmetric encryption The quick brown fox jumps over the lazy dog Encryption Encrypted data Clear data H 88 g&ikp 080+h 6 54 gcv. &Tgf 7676 f HF 76 yt 476 h. TPcs Receivers Public key H 88 g&ikp 080+h 6 54 gcv. &Tgf 7676 f HF 76 yt 476 h. TPcs Decryption Encrypted data Receivers Private key cret se The quick brown fox jumps over the lazy dog Clear data Different keys • Suggested for the first time in 1976 by two Americans, Diffie & Hellman • Only receiver can decrypt with his private key • Everyone can encrypt with receiver’s public key
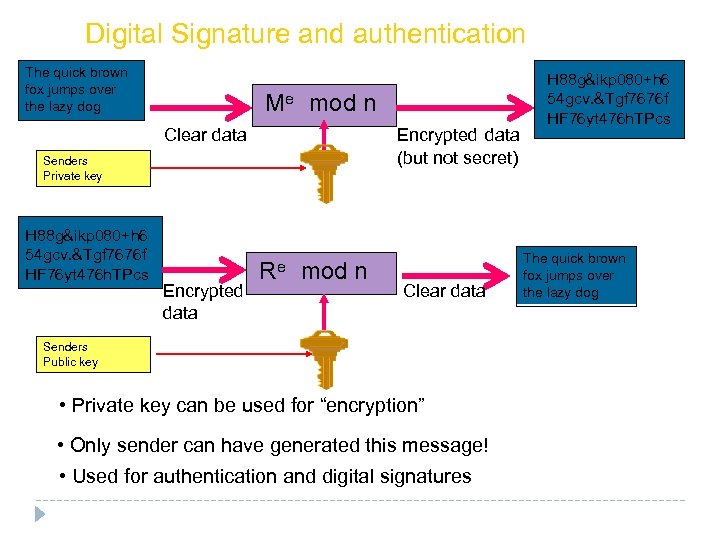
Digital Signature and authentication The quick brown fox jumps over the lazy dog Me mod n Encrypted data (but not secret) Clear data Senders Private key H 88 g&ikp 080+h 6 54 gcv. &Tgf 7676 f HF 76 yt 476 h. TPcs Encrypted data Re mod n Clear data Senders Public key • Private key can be used for “encryption” • Only sender can have generated this message! • Used for authentication and digital signatures H 88 g&ikp 080+h 6 54 gcv. &Tgf 7676 f HF 76 yt 476 h. TPcs The quick brown fox jumps over the lazy dog
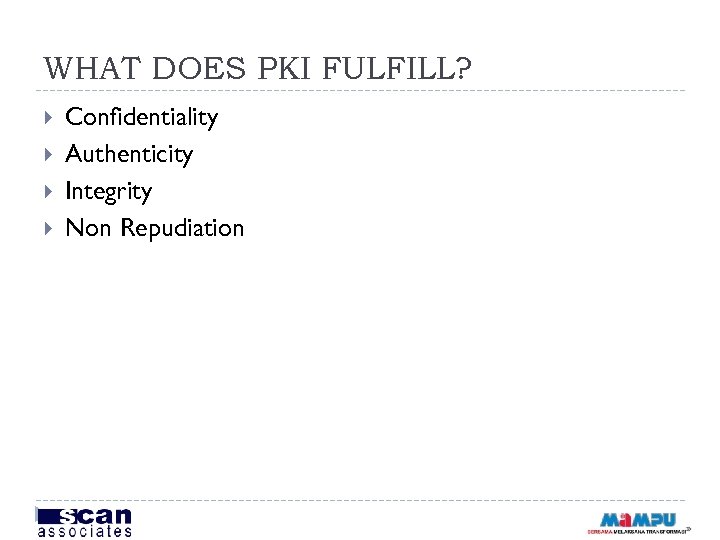
WHAT DOES PKI FULFILL? Confidentiality Authenticity Integrity Non Repudiation

PKI IN MACRO LEVEL
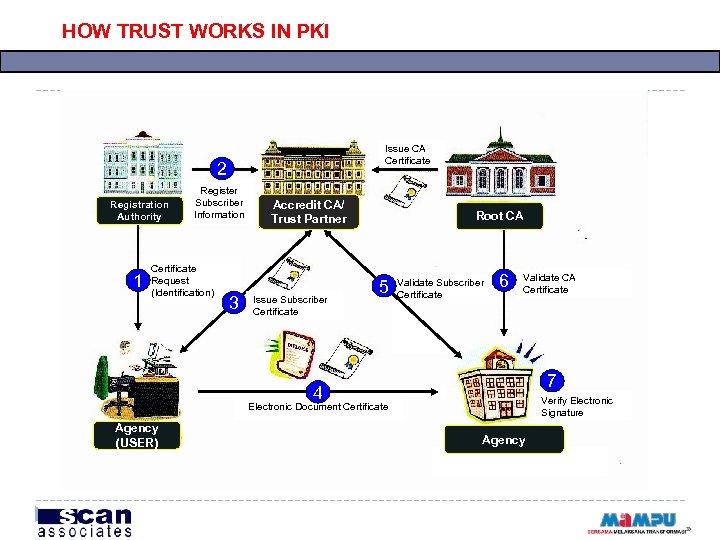
HOW TRUST WORKS IN PKI Issue CA Certificate 2 Registration Authority 1 Register Subscriber Information Certificate Request (Identification) 3 Accredit CA/ Trust Partner Issue Subscriber Certificate Root CA 5 Validate Subscriber Certificate 6 Validate CA Certificate 7 4 Verify Electronic Signature Electronic Document Certificate Agency (USER) Agency
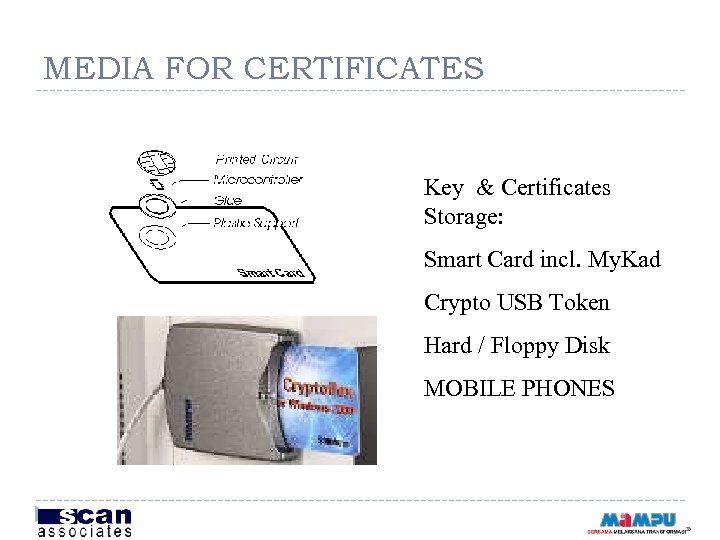
MEDIA FOR CERTIFICATES Key & Certificates Storage: Smart Card incl. My. Kad Crypto USB Token Hard / Floppy Disk MOBILE PHONES
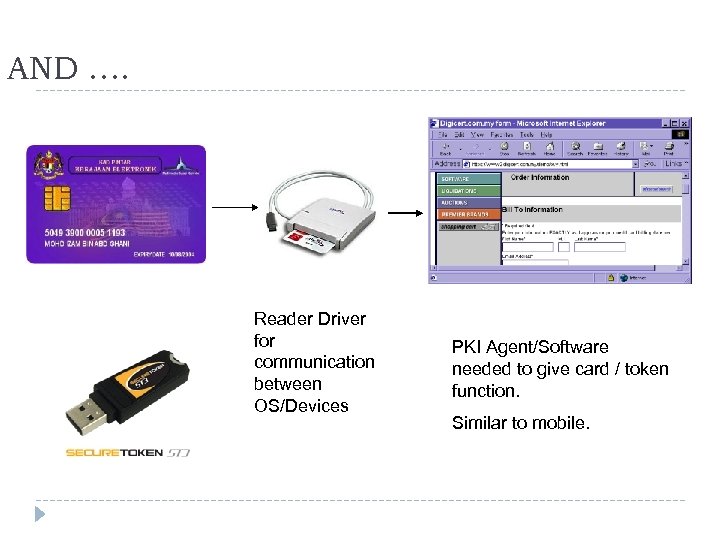
AND …. Reader Driver for communication between OS/Devices PKI Agent/Software needed to give card / token function. Similar to mobile.

MOBILE PKI CONCEPT

Background There are more users of smart phones than PC On the go transaction Concept wise: User download Agent on mobile phone: Android, i. OS, Windows and Blackberry
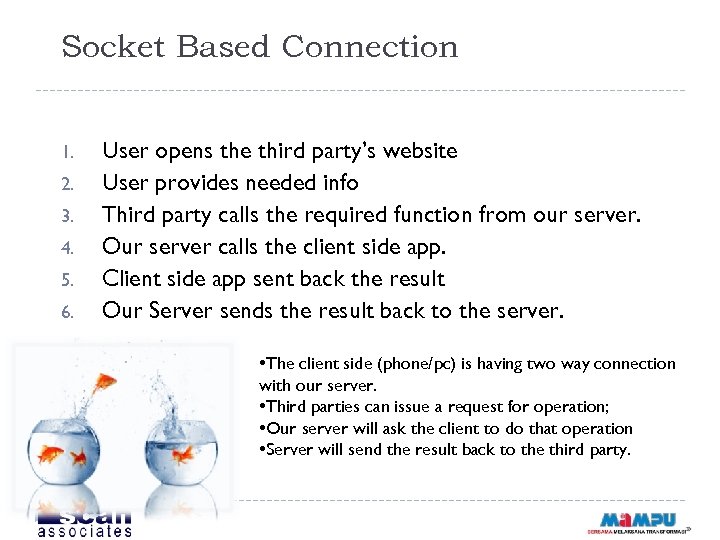
Socket Based Connection 1. 2. 3. 4. 5. 6. User opens the third party’s website User provides needed info Third party calls the required function from our server. Our server calls the client side app. Client side app sent back the result Our Server sends the result back to the server. • The client side (phone/pc) is having two way connection with our server. • Third parties can issue a request for operation; • Our server will ask the client to do that operation • Server will send the result back to the third party.
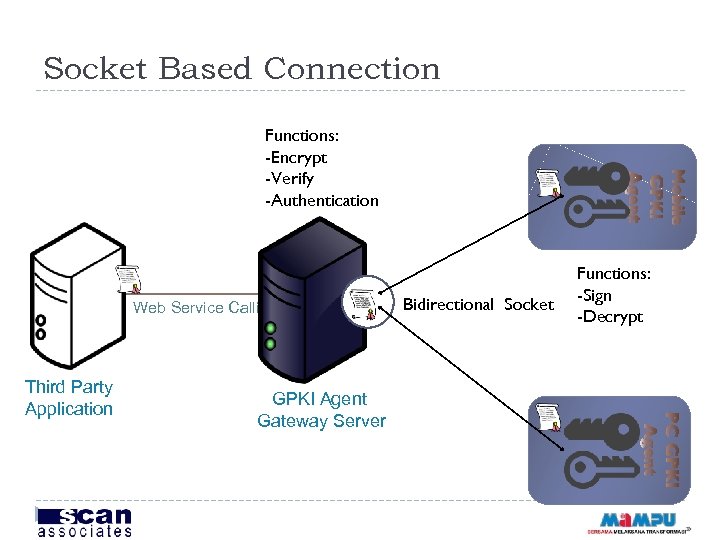
Socket Based Connection Functions: -Encrypt -Verify -Authentication Web Service Calling Third Party Application GPKI Agent Gateway Server Bidirectional Socket Functions: -Sign -Decrypt

Question and Answers TERIMA KASIH
df9913e4f971255d8481ff8f14c0898b.ppt